| download: | download |
| Full analysis: | https://app.any.run/tasks/45da0e3d-626c-4b01-85c1-802a476cd8a3 |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | April 15, 2019, 08:34:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | F0969E1F99E0908029EB86F4B6DD0932 |
| SHA1: | AFBF9407DF513303D079F4FEF7EFDA3AA4029E83 |
| SHA256: | 6343D65D9BE0C8242390B26EE8F1D843505AFA9876A68A136A6DCD4BB2820646 |
| SSDEEP: | 12288:HEPxqPnl6Y+AI7uiFSrUYSdDoRiLhwMfve2CfFxbLxwvReZhVfgxcc0a1s:Xl6Y+A9LUpdDkiLf22SfbWvgHVfgxd1s |
MALICIOUS
AdWind was detected
- java.exe (PID: 3964)
- java.exe (PID: 3312)
Application was dropped or rewritten from another process
- javaw.exe (PID: 2608)
- java.exe (PID: 3964)
- javaw.exe (PID: 1496)
- java.exe (PID: 3312)
Loads dropped or rewritten executable
- svchost.exe (PID: 812)
- javaw.exe (PID: 1496)
- explorer.exe (PID: 116)
- java.exe (PID: 3964)
- javaw.exe (PID: 2608)
- java.exe (PID: 3312)
Turns off system restore
- regedit.exe (PID: 2504)
Changes the autorun value in the registry
- reg.exe (PID: 2512)
Uses TASKKILL.EXE to kill security tools
- javaw.exe (PID: 2608)
Changes Image File Execution Options
- regedit.exe (PID: 2504)
SUSPICIOUS
Executes JAVA applets
- javaw.exe (PID: 1496)
- explorer.exe (PID: 116)
Creates files in the user directory
- javaw.exe (PID: 1496)
- xcopy.exe (PID: 3764)
Starts CMD.EXE for commands execution
- java.exe (PID: 3964)
- javaw.exe (PID: 1496)
- javaw.exe (PID: 2608)
- java.exe (PID: 3312)
Executes scripts
- cmd.exe (PID: 2628)
- cmd.exe (PID: 1640)
- cmd.exe (PID: 296)
- cmd.exe (PID: 3980)
- cmd.exe (PID: 2444)
- cmd.exe (PID: 1924)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 4044)
Starts itself from another location
- javaw.exe (PID: 1496)
Executable content was dropped or overwritten
- xcopy.exe (PID: 3764)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 1496)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 1496)
Uses TASKKILL.EXE to kill process
- javaw.exe (PID: 2608)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:16 10:23:22 |
| ZipCRC: | 0x6c868ea2 |
| ZipCompressedSize: | 64 |
| ZipUncompressedSize: | 62 |
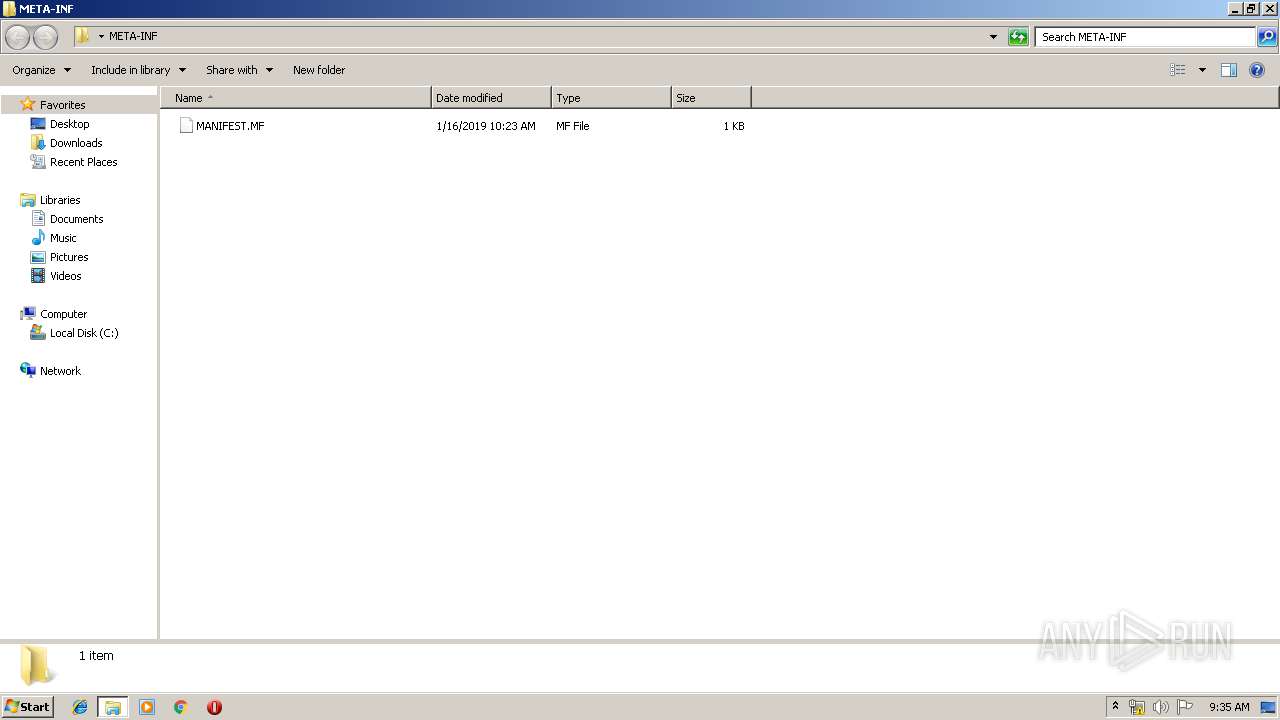
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
139
Monitored processes
59
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 272 | taskkill /IM V3Up.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8958221530133371414.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 320 | taskkill /IM AdAwareTray.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | taskkill /IM wireshark.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 336 | regedit.exe /s C:\Users\admin\AppData\Local\Temp\OCnEquUwvX5068405127600818837.reg | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | taskkill /IM V3SP.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | "C:\Windows\regedit.exe" /s C:\Users\admin\AppData\Local\Temp\OCnEquUwvX5068405127600818837.reg | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 644 | taskkill /IM tshark.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 812 | C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 717
Read events
2 360
Write events
357
Delete events
0
Modification events
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {B41DB860-8EE4-11D2-9906-E49FADC173CA} {00000122-0000-0000-C000-000000000046} 0xFFFF |
Value: 010000000000000020FB351566F3D401 | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @sendmail.dll,-21 |
Value: Desktop (create shortcut) | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\ntshrui.dll,-103 |
Value: S&hare with | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @zipfldr.dll,-10148 |
Value: Compressed (zipped) folder | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @sendmail.dll,-4 |
Value: Mail recipient | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\FXSRESM.dll,-120 |
Value: Fax recipient | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (116) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\WFS.exe |
Value: Microsoft Windows Fax and Scan | |||
Executable files
109
Suspicious files
10
Text files
77
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3964 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 1496 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3764 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\COPYRIGHT | text | |
MD5:89F660D2B7D58DA3EFD2FECD9832DA9C | SHA256:F6A08C9CC04D7C6A86576C1EF50DD0A690AE5CB503EFD205EDB2E408BD8D557B | |||
| 1496 | javaw.exe | C:\Users\admin\AppData\Local\Temp\_0.49079258840375043233130874704890814.class | java | |
MD5:781FB531354D6F291F1CCAB48DA6D39F | SHA256:97D585B6AFF62FB4E43E7E6A5F816DCD7A14BE11A88B109A9BA9E8CD4C456EB9 | |||
| 3964 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive7678821889524108420.vbs | text | |
MD5:3BDFD33017806B85949B6FAA7D4B98E4 | SHA256:9DA575DD2D5B7C1E9BAB8B51A16CDE457B3371C6DCDB0537356CF1497FA868F6 | |||
| 3764 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\LICENSE | text | |
MD5:98F46AB6481D87C4D77E0E91A6DBC15F | SHA256:23F9A5C12FA839650595A32872B7360B9E030C7213580FB27DD9185538A5828C | |||
| 3764 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\README.txt | text | |
MD5:0F1123976B959AC5E8B89EB8C245C4BD | SHA256:963095CF8DB76FB8071FD19A3110718A42F2AB42B27A3ADFD9EC58981C3E88D2 | |||
| 3964 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive5248825867668353598.vbs | text | |
MD5:A32C109297ED1CA155598CD295C26611 | SHA256:45BFE34AA3EF932F75101246EB53D032F5E7CF6D1F5B4E495334955A255F32E7 | |||
| 1496 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\83aa4cc77f591dfc2374580bbd95f6ba_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
| 3764 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\bin\dt_shmem.dll | executable | |
MD5:0744E6A5145AA945D89A16EAC835FAB2 | SHA256:C417390F681276EC0D55D81A91B87EAE75CA245045F5C23E9B43550B708FB1A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2608 | javaw.exe | 217.20.114.225:49575 | — | Leaseweb Deutschland GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |