| URL: | Google.com |
| Full analysis: | https://app.any.run/tasks/bbbc0d75-8f3e-417c-9729-ce9e424f623e |
| Verdict: | Malicious activity |
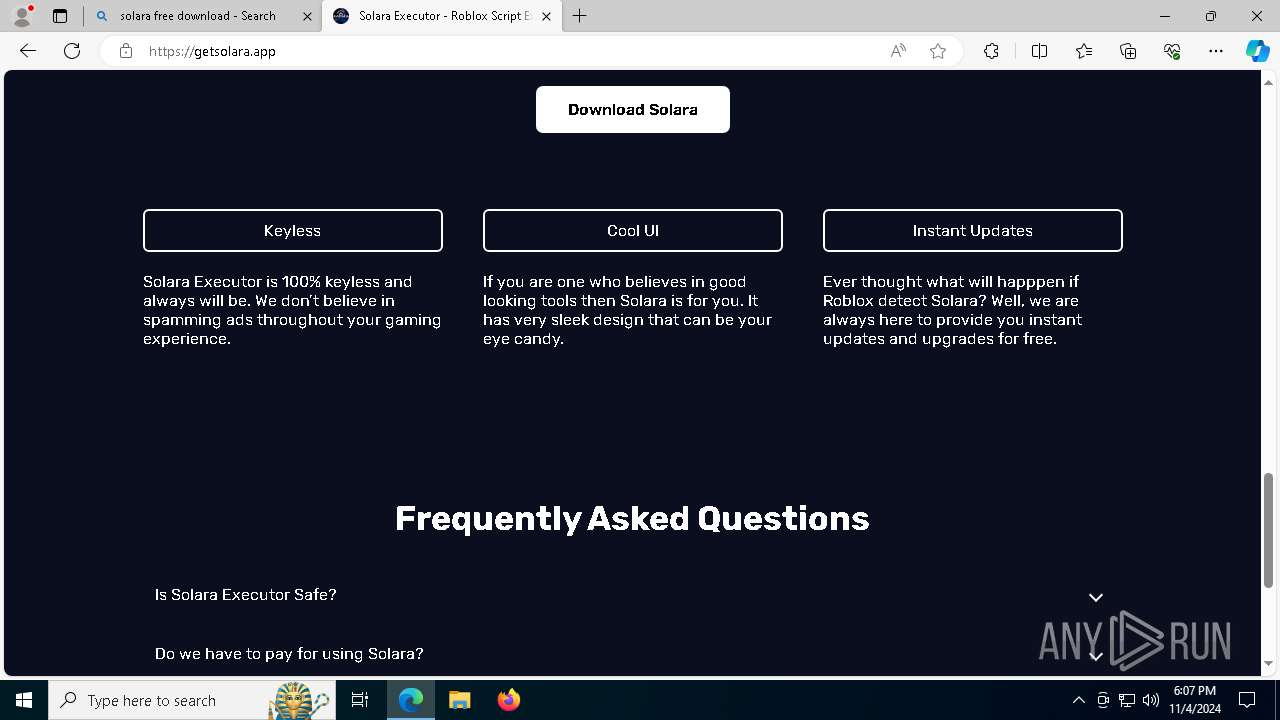
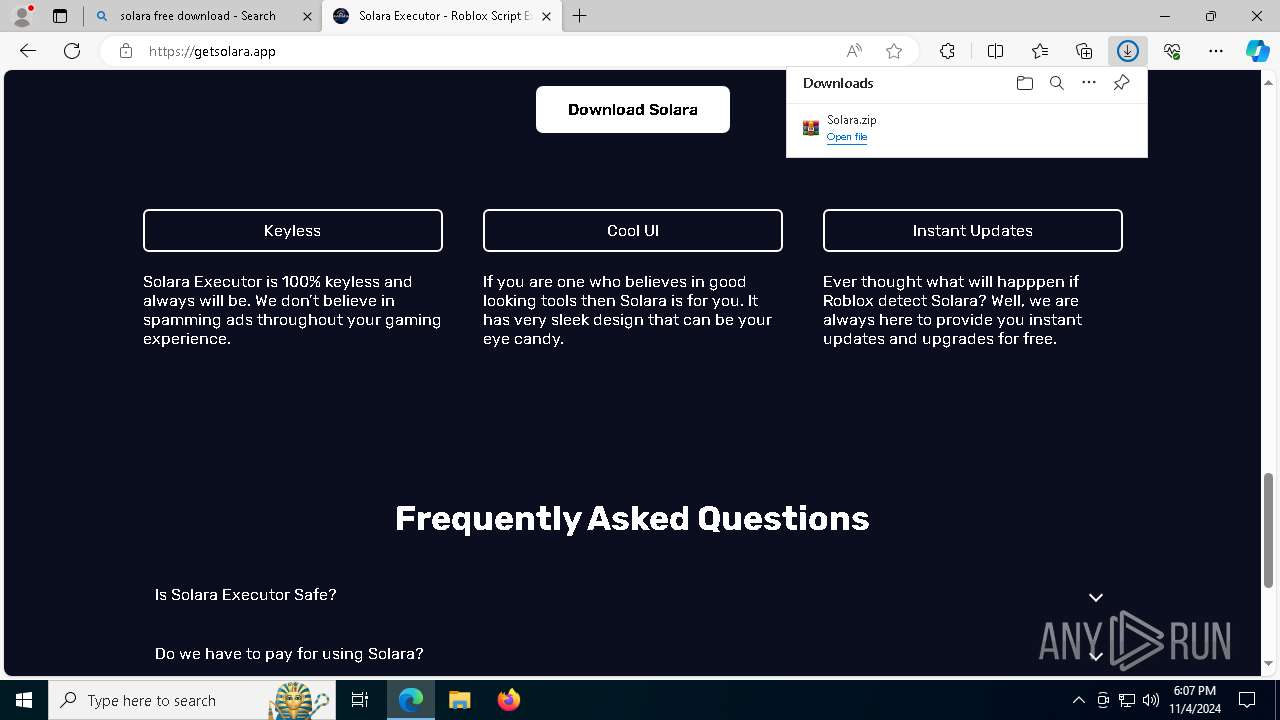
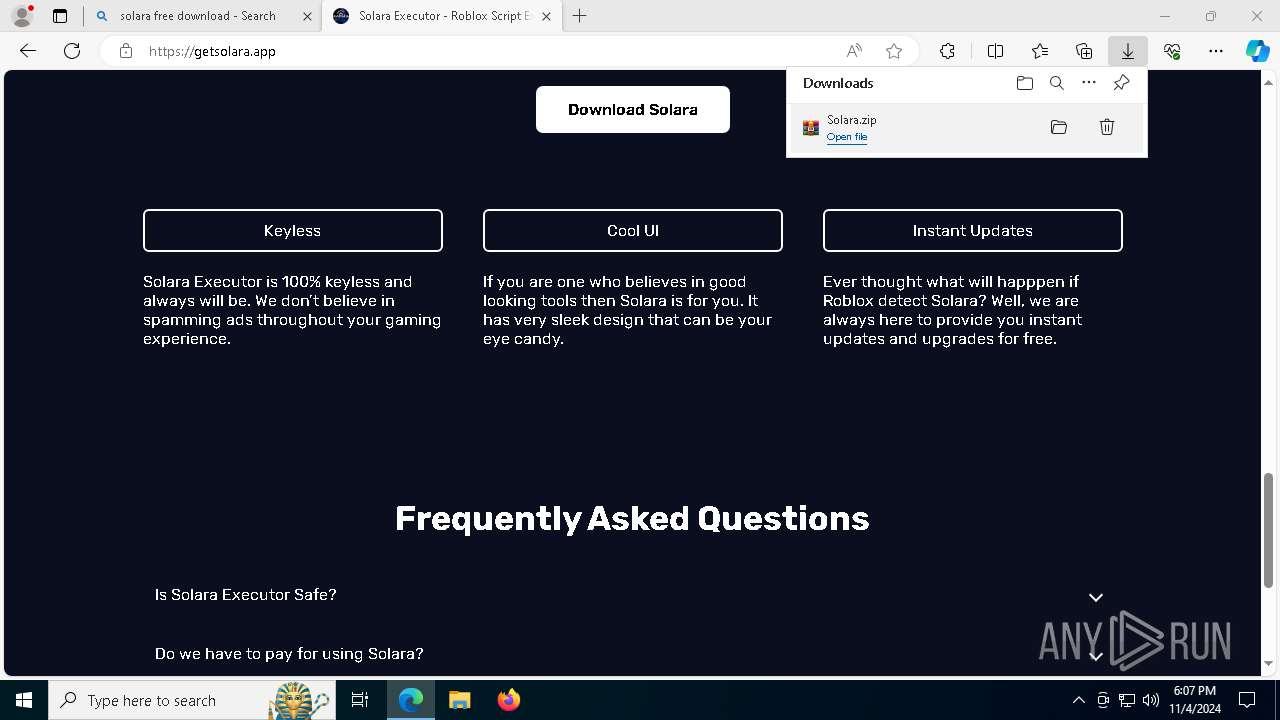
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | November 04, 2024, 18:06:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1DA5EB3D5A67C037E63D096D1631D88E |
| SHA1: | A9702BFAEE969CD73B70FEBBCBC6918F7CAC830A |
| SHA256: | 632E24BC59B0466DB8D264CE5817DF5B7BB56BBC2FC9284755B6DC8A00CDE575 |
| SSDEEP: | 3:kCO2:LO2 |
MALICIOUS
SMARTLOADER has been detected (SURICATA)
- lua.exe (PID: 7840)
Adds extension to the Windows Defender exclusion list
- lua.exe (PID: 7840)
- powershell.exe (PID: 7044)
Connects to the CnC server
- lua.exe (PID: 7840)
Run PowerShell with an invisible window
- powershell.exe (PID: 7044)
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 7044)
Changes powershell execution policy (Bypass)
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
Bypass execution policy to execute commands
- powershell.exe (PID: 5624)
- powershell.exe (PID: 5476)
Uses Task Scheduler to run other applications
- lua.exe (PID: 7840)
SUSPICIOUS
Script adds exclusion extension to Windows Defender
- lua.exe (PID: 7840)
- powershell.exe (PID: 7044)
Starts POWERSHELL.EXE for commands execution
- lua.exe (PID: 7840)
- powershell.exe (PID: 7044)
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
Starts process via Powershell
- powershell.exe (PID: 7044)
Checks for external IP
- lua.exe (PID: 7840)
- svchost.exe (PID: 2172)
Connects to the server without a host name
- lua.exe (PID: 7840)
Manipulates environment variables
- powershell.exe (PID: 7044)
- powershell.exe (PID: 3568)
Script adds exclusion path to Windows Defender
- lua.exe (PID: 7840)
- powershell.exe (PID: 7044)
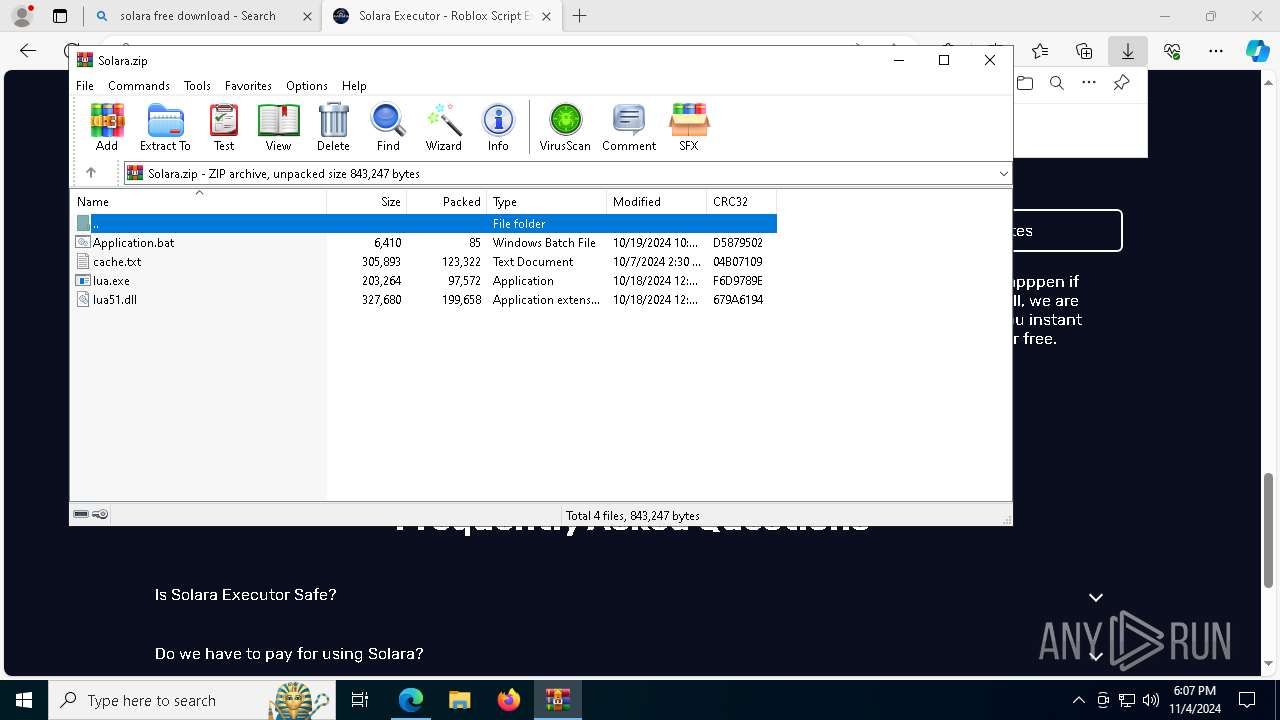
Executable content was dropped or overwritten
- lua.exe (PID: 7840)
- csc.exe (PID: 7488)
- csc.exe (PID: 4308)
Application launched itself
- powershell.exe (PID: 7044)
The process bypasses the loading of PowerShell profile settings
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
Base64-obfuscated command line is found
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
The process hide an interactive prompt from the user
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
The process hides Powershell's copyright startup banner
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
Uses WMIC.EXE to obtain Windows Installer data
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
BASE64 encoded PowerShell command has been detected
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7488)
- csc.exe (PID: 4308)
INFO
Manual execution by a user
- cmd.exe (PID: 6420)
- notepad.exe (PID: 2124)
- cmd.exe (PID: 7372)
- notepad++.exe (PID: 6552)
- cmd.exe (PID: 6228)
- Solara_Boostrapper.exe (PID: 696)
- Solara_Boostrapper.exe (PID: 6380)
Application launched itself
- msedge.exe (PID: 6684)
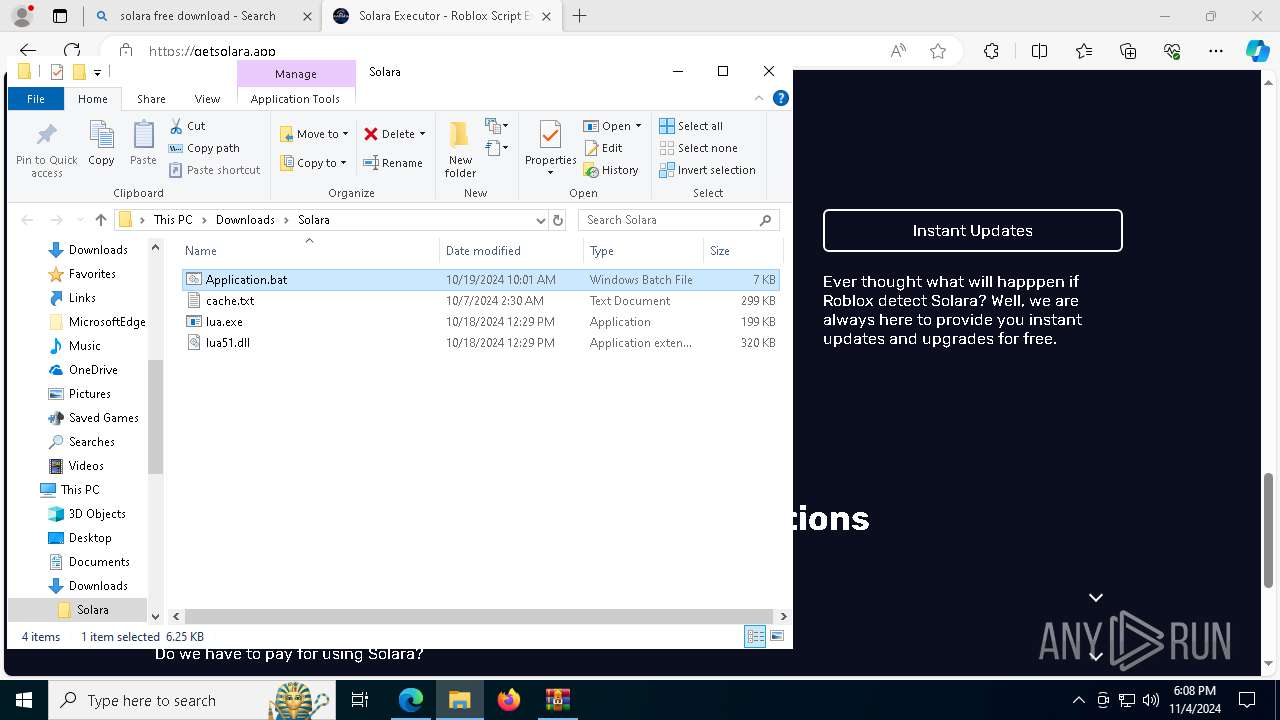
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7520)
- msedge.exe (PID: 7912)
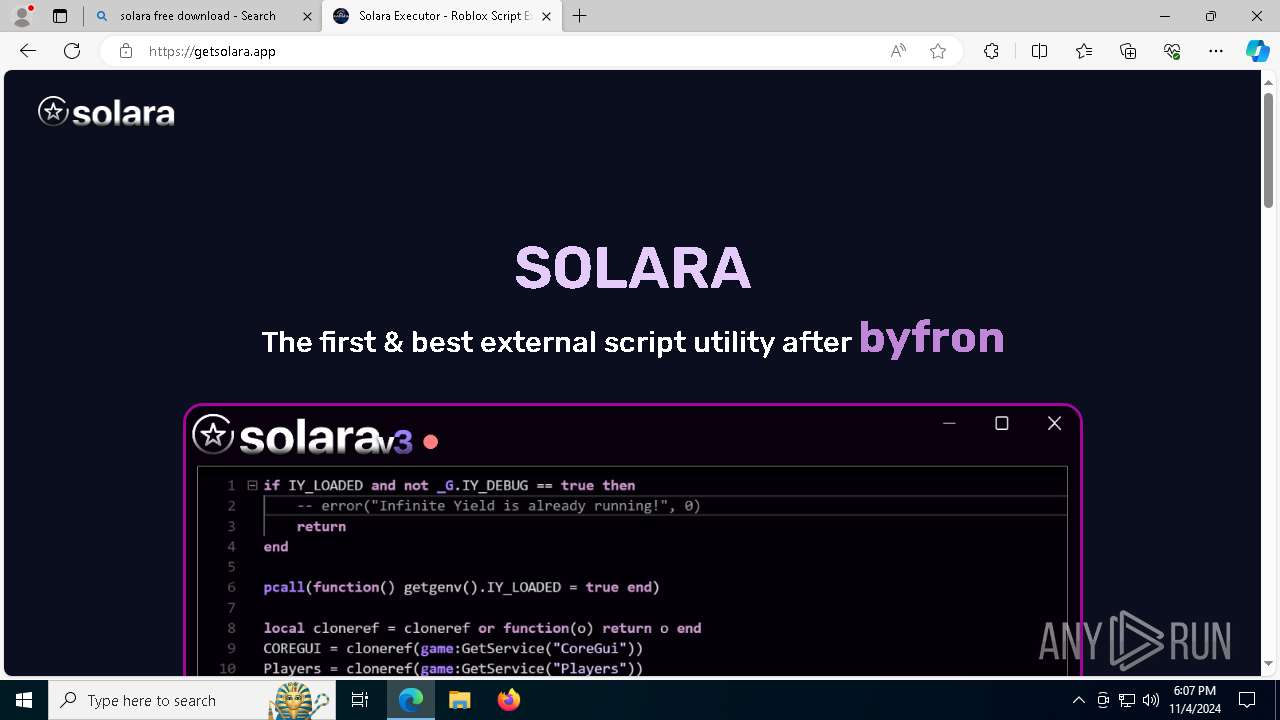
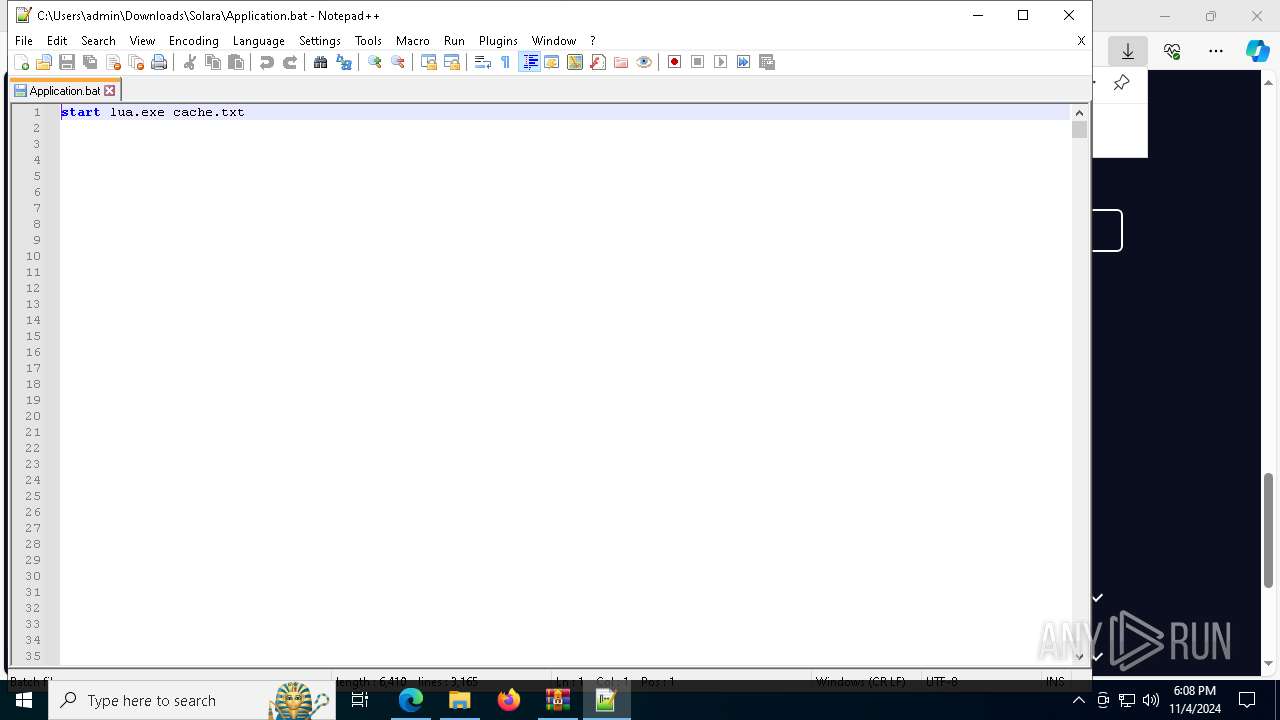
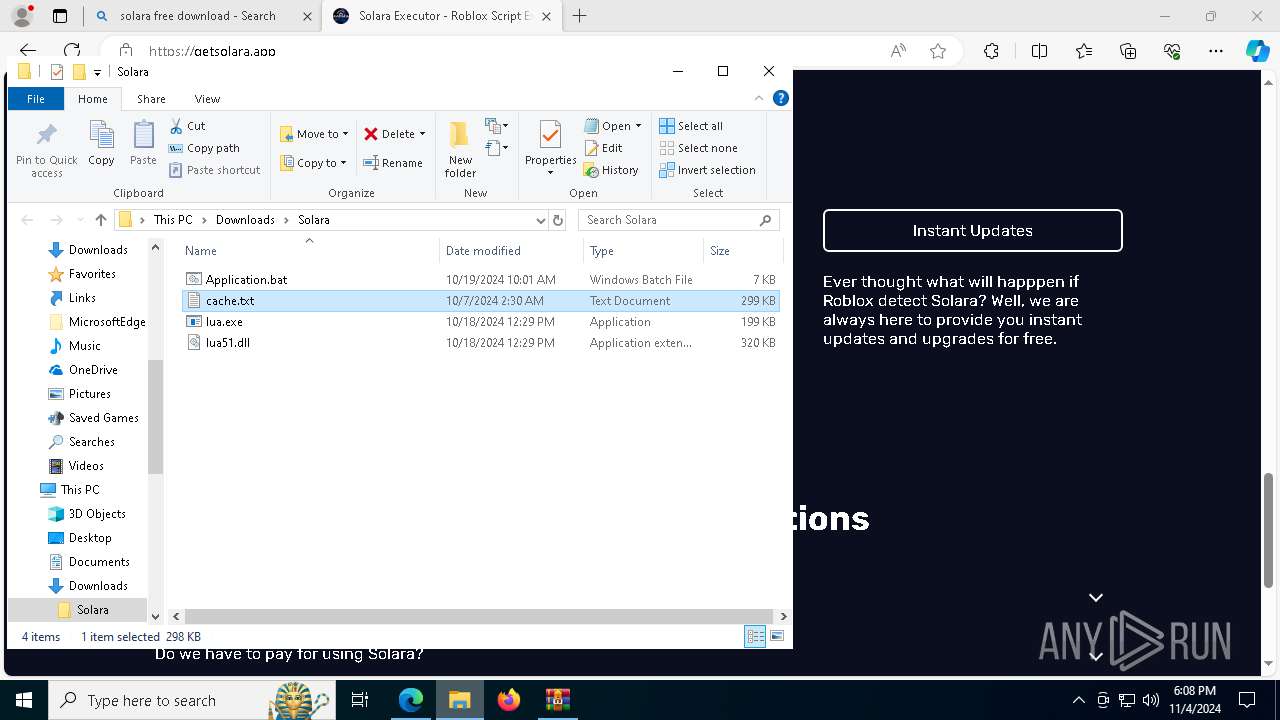
The process uses Lua
- lua.exe (PID: 7840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
253
Monitored processes
115
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 692 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=32 --mojo-platform-channel-handle=6212 --field-trial-handle=2356,i,4612134570235249107,9681520333811115108,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
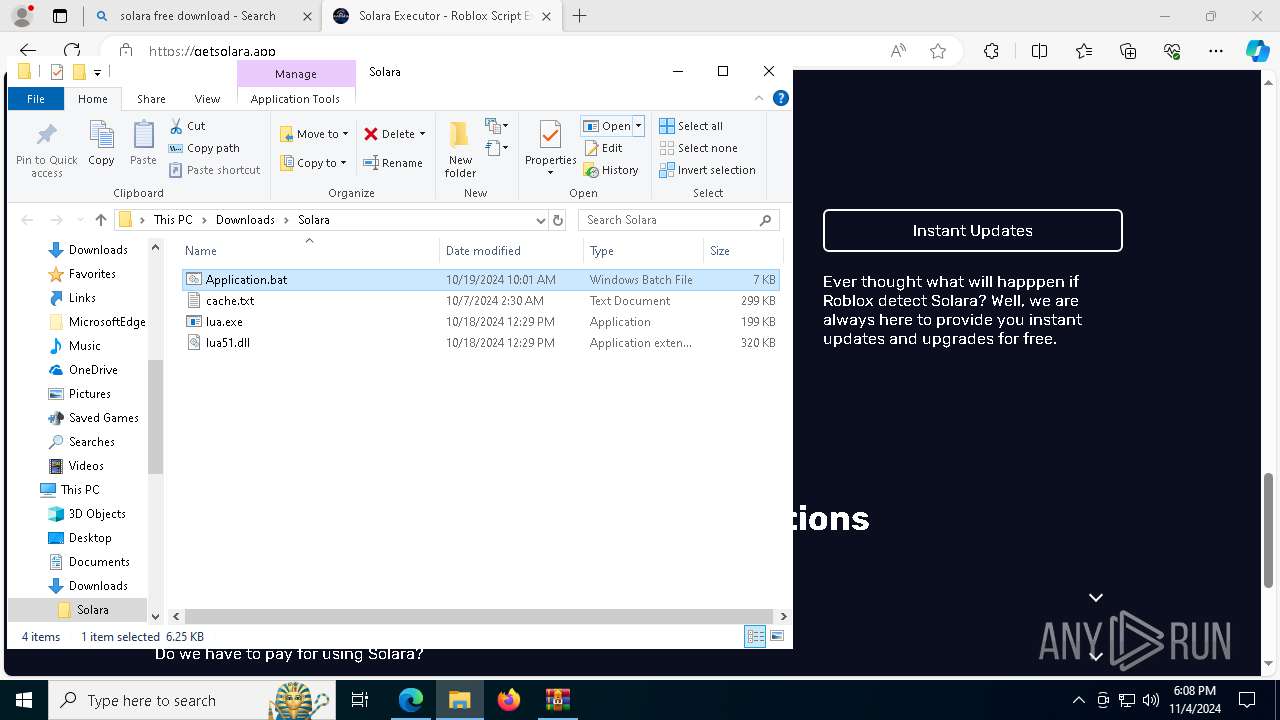
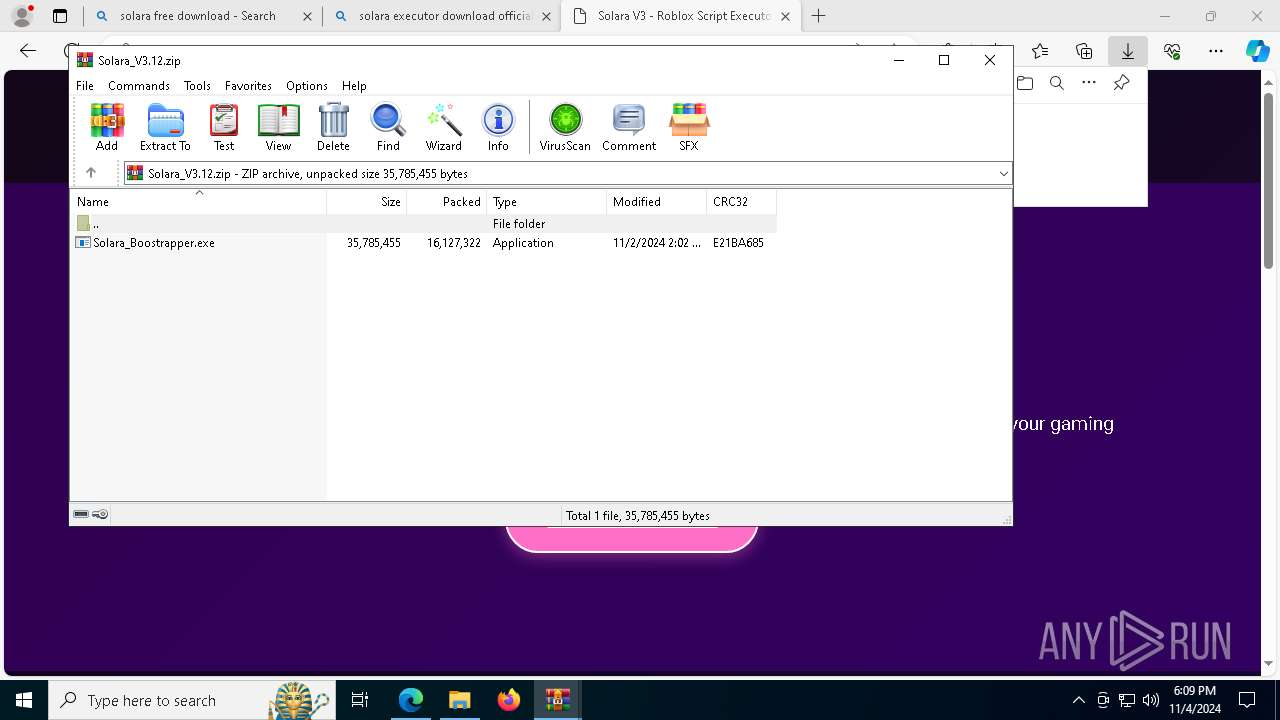
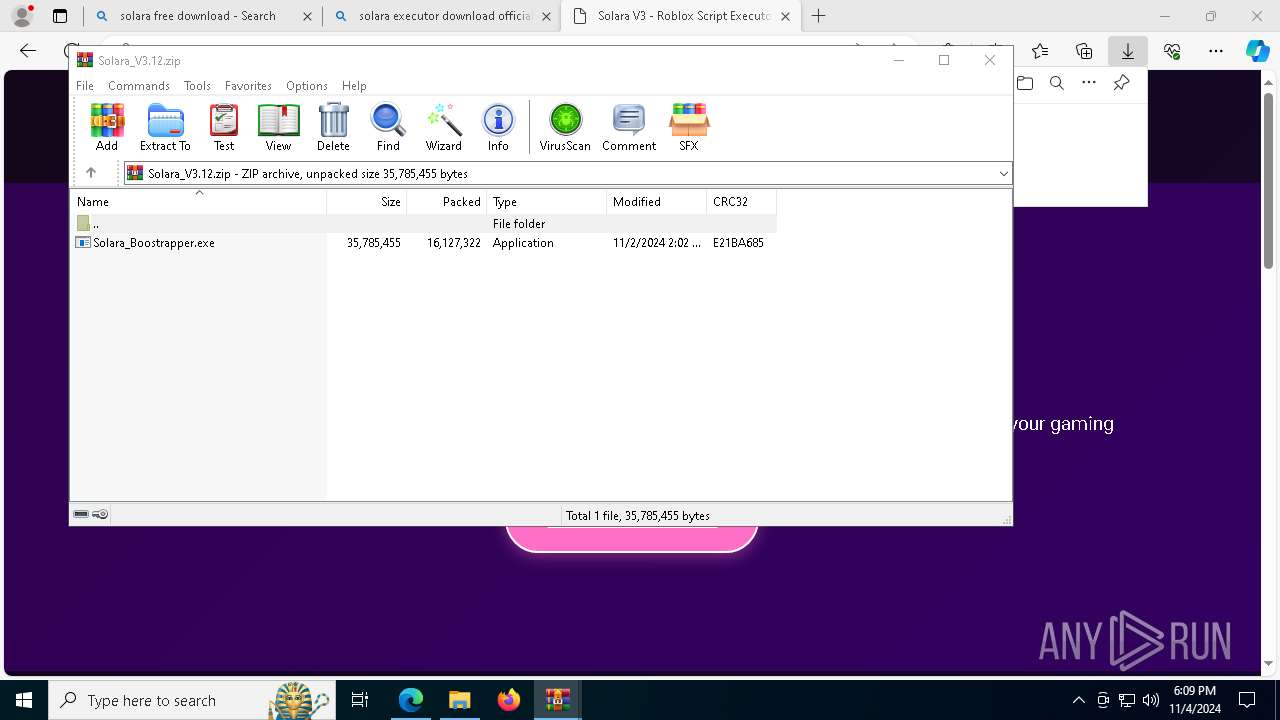
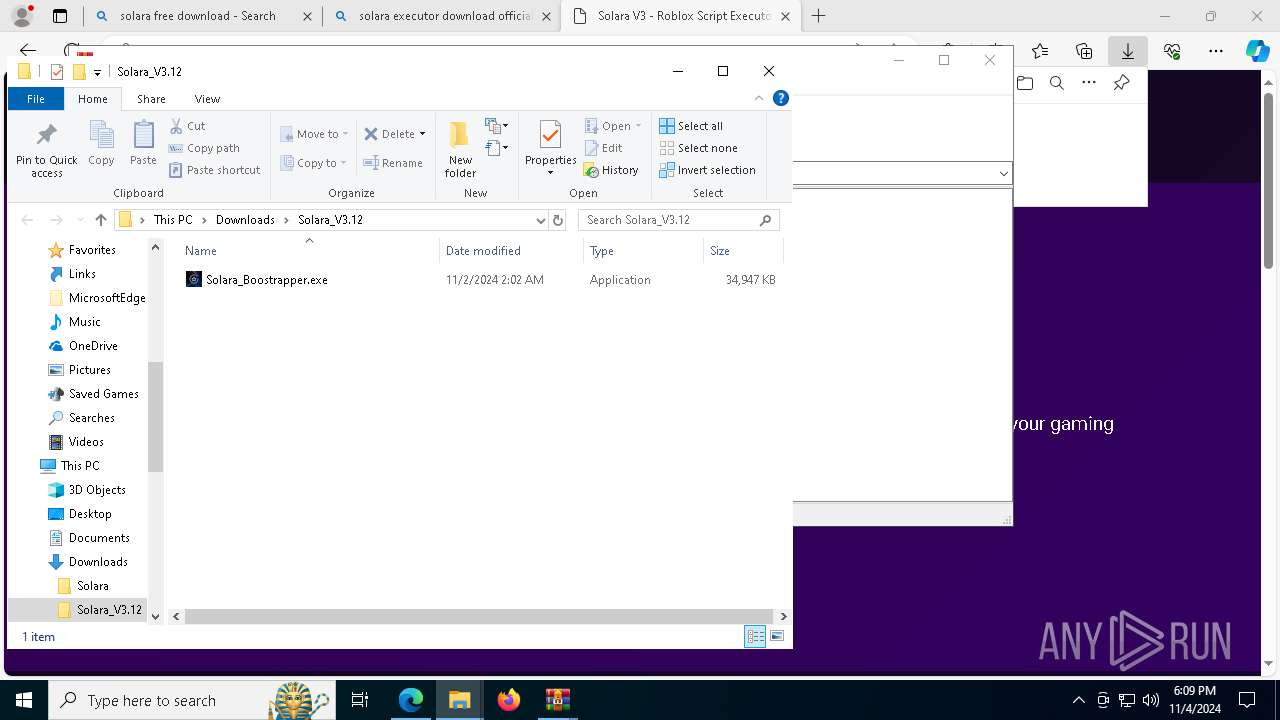
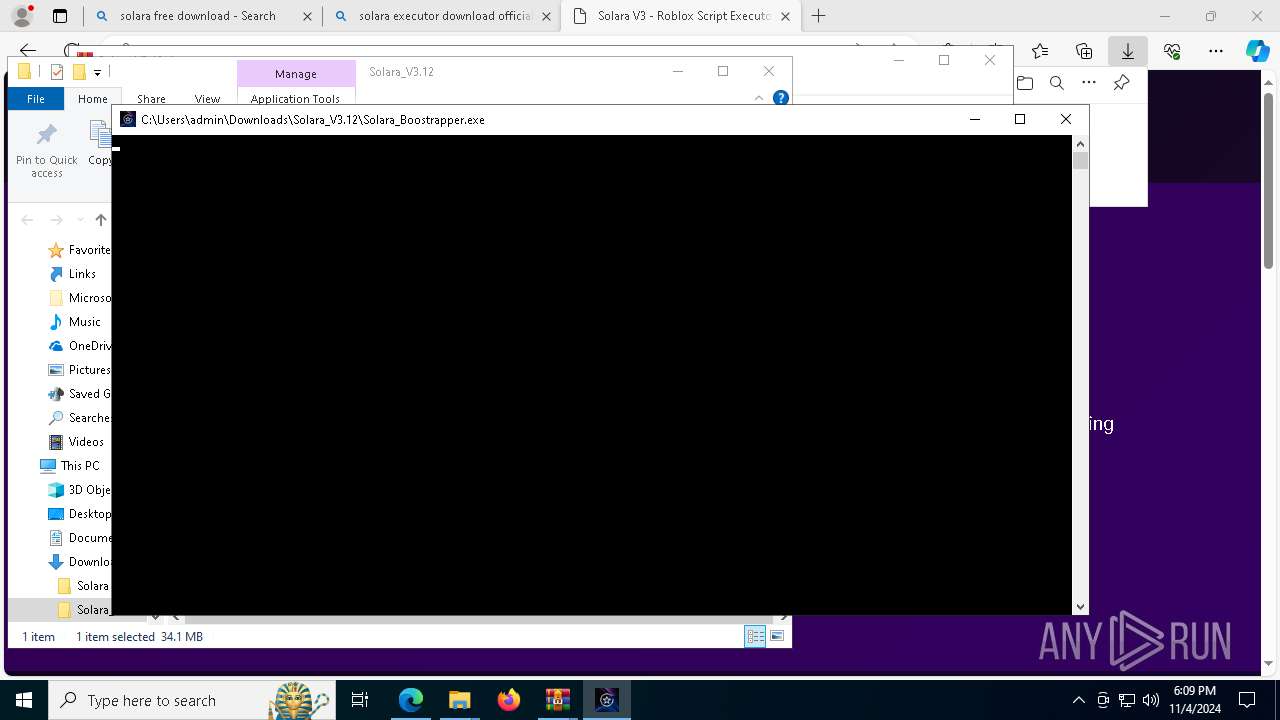
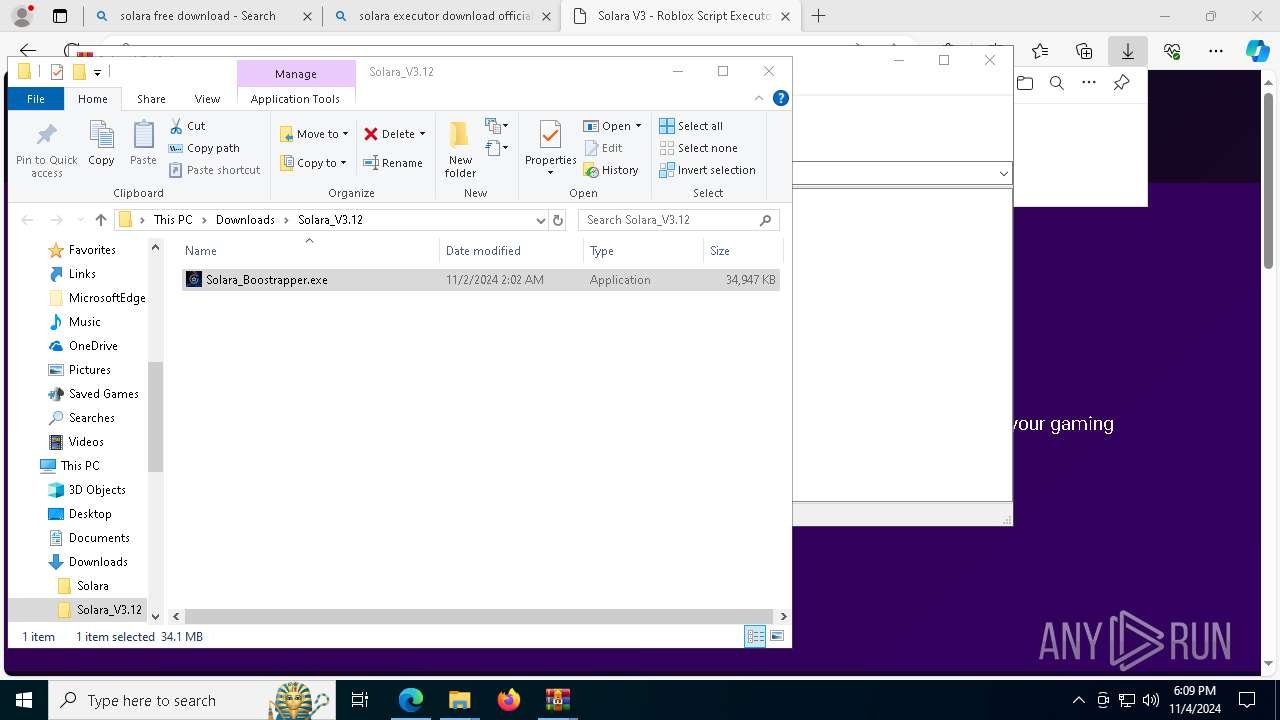
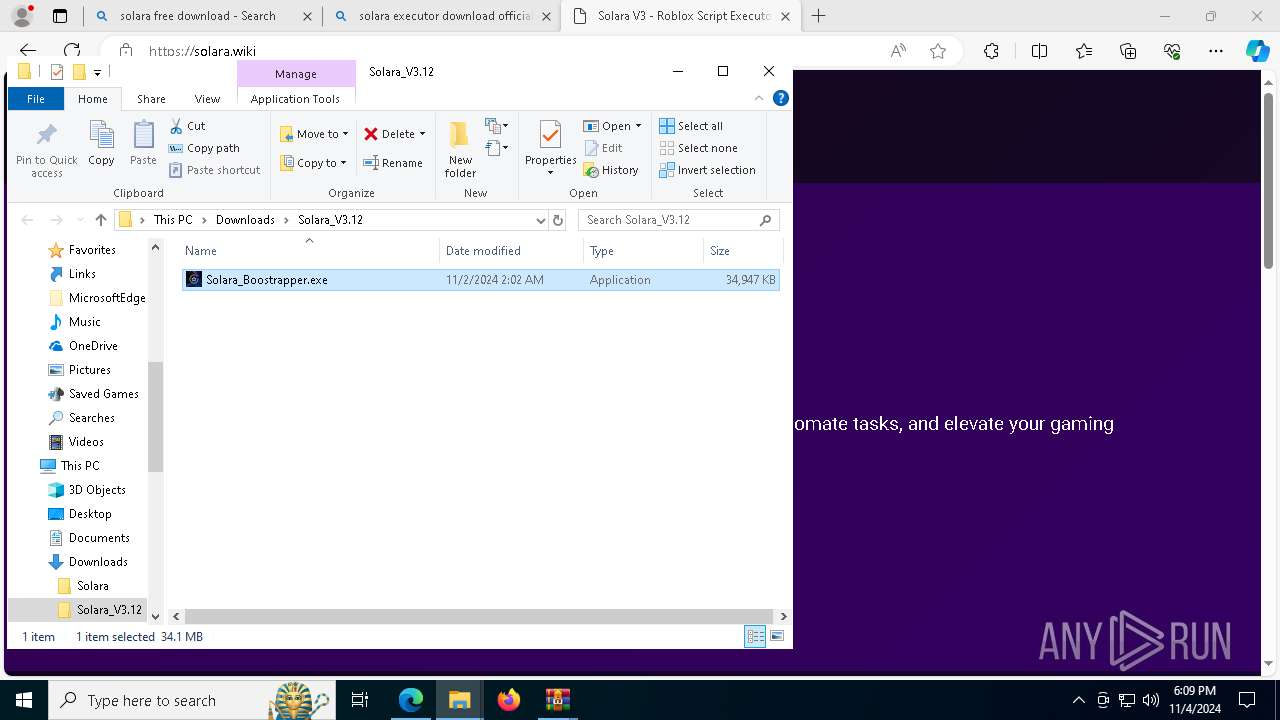
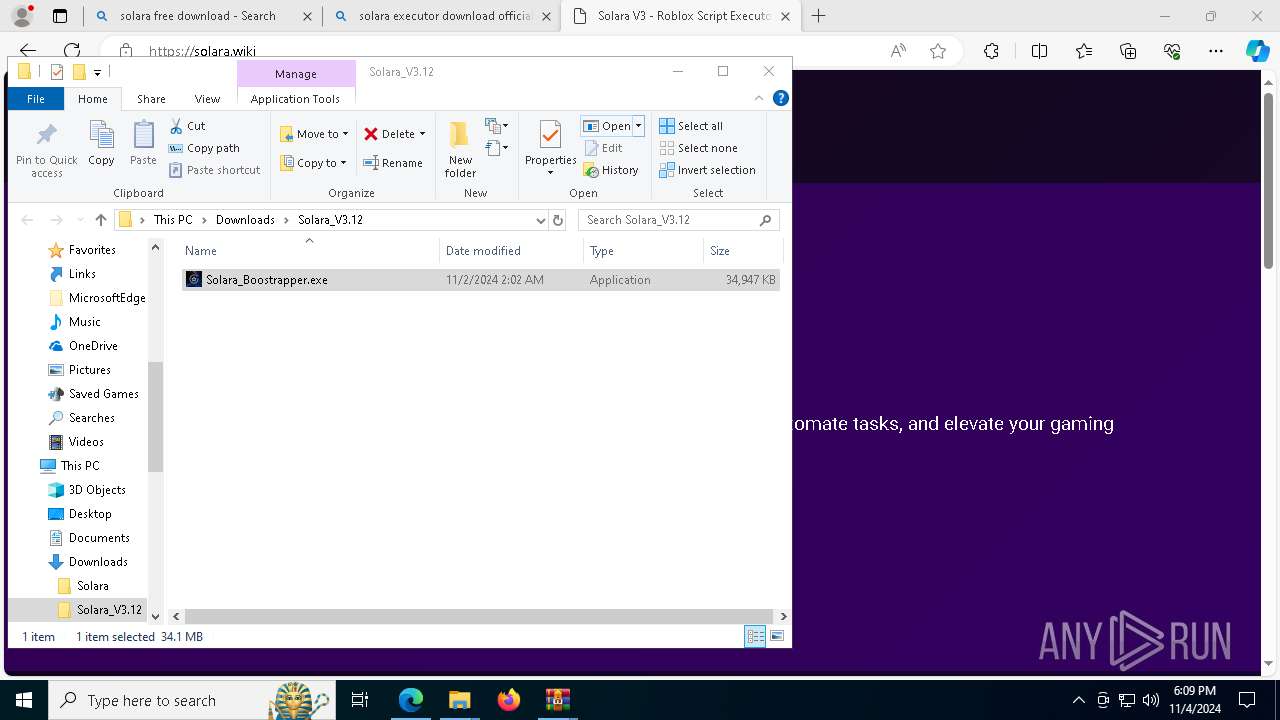
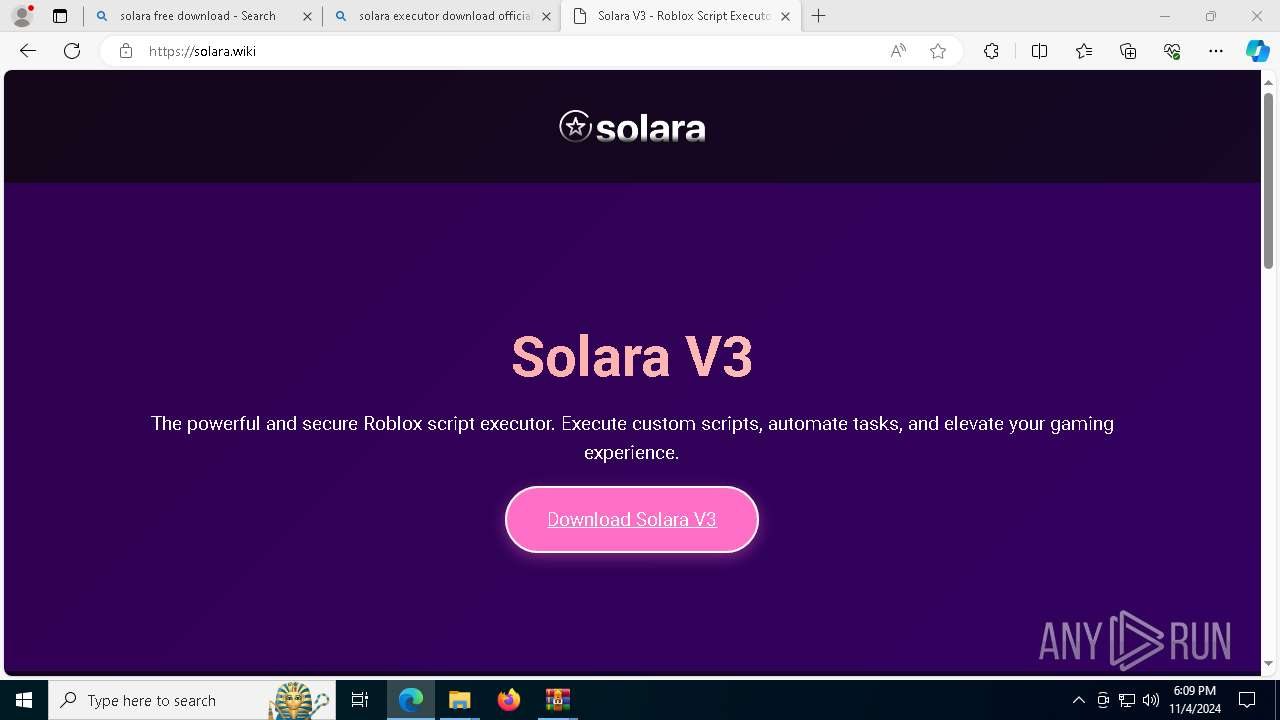
| 696 | "C:\Users\admin\Downloads\Solara_V3.12\Solara_Boostrapper.exe" | C:\Users\admin\Downloads\Solara_V3.12\Solara_Boostrapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Solara Executor Boostrapper Exit code: 0 Version: 3.12.3.47 Modules
| |||||||||||||||
| 944 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=7208 --field-trial-handle=2356,i,4612134570235249107,9681520333811115108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1008 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=39 --mojo-platform-channel-handle=7076 --field-trial-handle=2356,i,4612134570235249107,9681520333811115108,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5528 --field-trial-handle=2356,i,4612134570235249107,9681520333811115108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1252 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=7400 --field-trial-handle=2356,i,4612134570235249107,9681520333811115108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1568 | schtasks /create /sc daily /st 14:59 /f /tn BluetoothSupportService_ODA3 /tr ""C:\Users\admin\AppData\Local\ODA3\ODA3.exe" "C:\Users\admin\AppData\Local\ODA3\cache.txt"" | C:\Windows\SysWOW64\schtasks.exe | — | lua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "powershell" Expand-Archive -Path C:\WindowsTasks\Updates\Update-X8AyxReqeA.zip -DestinationPath C:\WindowsTasks\Platform\App-9Mj5ORUVoV | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Solara_Boostrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6760 --field-trial-handle=2356,i,4612134570235249107,9681520333811115108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1788 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6608 --field-trial-handle=2356,i,4612134570235249107,9681520333811115108,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
29 567
Read events
29 474
Write events
68
Delete events
25
Modification events
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 7551586FB0842F00 | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B091626FB0842F00 | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {890A427E-8517-4093-A593-84A61C84C246} | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {40F0E8E5-93ED-4738-B8AA-CE4343D4C31B} | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3386268E-A941-470B-9D0F-3791F1257203} | |||
| (PID) Process: | (6684) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A344E968-F29F-45D4-8D53-EA40695405E7} | |||
Executable files
13
Suspicious files
601
Text files
158
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF8bb98.TMP | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF8bb98.TMP | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF8bb98.TMP | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF8bba8.TMP | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF8bba8.TMP | — | |
MD5:— | SHA256:— | |||
| 6684 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
175
DNS requests
177
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5464 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c9c35960-06f1-4c4d-a7a3-3d34cf859907?P1=1730930283&P2=404&P3=2&P4=BHJQ6xDLAn8iuxFgqHPrJwPbYZDdxyRGGyihjtMpdMst3SLkEmbJ%2b6OU8CnRuI2GTdBGzbGNk6Nfyejtcf2zOA%3d%3d | unknown | — | — | whitelisted |
5464 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c08f1970-45bc-4dbe-8166-4ecef7a1f617?P1=1731019667&P2=404&P3=2&P4=CitARWzdAzhAGjEGN6Kp%2bGI0Fzn2Hr42c77rLqBtaXyDu%2bJgni0g0MyvOTAB191HiFhetBtRgkSyZzPCgN7cCg%3d%3d | unknown | — | — | whitelisted |
5464 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c9c35960-06f1-4c4d-a7a3-3d34cf859907?P1=1730930283&P2=404&P3=2&P4=BHJQ6xDLAn8iuxFgqHPrJwPbYZDdxyRGGyihjtMpdMst3SLkEmbJ%2b6OU8CnRuI2GTdBGzbGNk6Nfyejtcf2zOA%3d%3d | unknown | — | — | whitelisted |
5464 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c9c35960-06f1-4c4d-a7a3-3d34cf859907?P1=1730930283&P2=404&P3=2&P4=BHJQ6xDLAn8iuxFgqHPrJwPbYZDdxyRGGyihjtMpdMst3SLkEmbJ%2b6OU8CnRuI2GTdBGzbGNk6Nfyejtcf2zOA%3d%3d | unknown | — | — | whitelisted |
5464 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c9c35960-06f1-4c4d-a7a3-3d34cf859907?P1=1730930283&P2=404&P3=2&P4=BHJQ6xDLAn8iuxFgqHPrJwPbYZDdxyRGGyihjtMpdMst3SLkEmbJ%2b6OU8CnRuI2GTdBGzbGNk6Nfyejtcf2zOA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1880 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5464 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c08f1970-45bc-4dbe-8166-4ecef7a1f617?P1=1731019667&P2=404&P3=2&P4=CitARWzdAzhAGjEGN6Kp%2bGI0Fzn2Hr42c77rLqBtaXyDu%2bJgni0g0MyvOTAB191HiFhetBtRgkSyZzPCgN7cCg%3d%3d | unknown | — | — | whitelisted |
5604 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6684 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6720 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
6720 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
2172 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
7840 | lua.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2172 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7840 | lua.exe | A Network Trojan was detected | LOADER [ANY.RUN] SmartLoader Check-in |
6720 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6720 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|