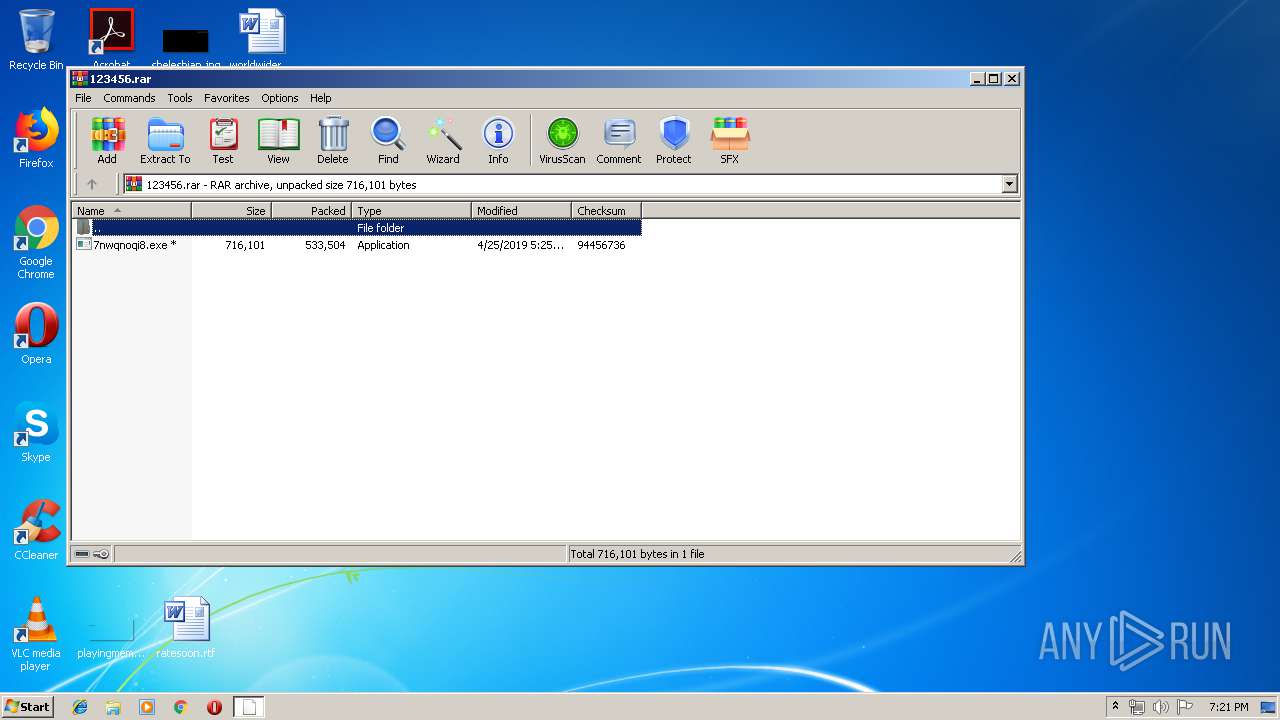
| File name: | 123456.rar |
| Full analysis: | https://app.any.run/tasks/334c883f-6599-4b27-adda-181df8fc1beb |
| Verdict: | Malicious activity |
| Threats: | TrickBot is an advanced banking trojan that attackers can use to steal payment credentials from the victims. It can redirect the victim to a fake banking cabinet and retrieve credentials typed in on the webpage. |
| Analysis date: | April 25, 2019, 18:21:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1760DDE79193CBC3A8B3A152668AE006 |
| SHA1: | BA470940C569695AB08AF0DFDE82E47FB8F31372 |
| SHA256: | 630CA2C784D257B9A854A0956DB34ADFD918A5CDA62E6B767134E2B8E40F0D11 |
| SSDEEP: | 12288:YZx6+ePHcXGDvg6xHw5188C9PbagirbZljOQriwIs:YZ8tRg6xQv8H9tEbHKQ4s |
MALICIOUS
Stops/Deletes Windows Defender service
- cmd.exe (PID: 2800)
- cmd.exe (PID: 1684)
- cmd.exe (PID: 3896)
- cmd.exe (PID: 1140)
Application was dropped or rewritten from another process
- 7nwqnoqi8.exe (PID: 2324)
- 9pwspqsi8.exe (PID: 1088)
- 9pwspqsi8.exe (PID: 2656)
- 7nwqnoqi8.exe (PID: 3828)
Known privilege escalation attack
- DllHost.exe (PID: 2504)
Loads the Task Scheduler COM API
- 9pwspqsi8.exe (PID: 1088)
- 9pwspqsi8.exe (PID: 2656)
Changes settings of System certificates
- 9pwspqsi8.exe (PID: 2656)
TRICKBOT was detected
- 9pwspqsi8.exe (PID: 2656)
SUSPICIOUS
Starts CMD.EXE for commands execution
- 9pwspqsi8.exe (PID: 1088)
- 7nwqnoqi8.exe (PID: 2324)
Executes PowerShell scripts
- cmd.exe (PID: 2596)
- cmd.exe (PID: 2328)
Executable content was dropped or overwritten
- 7nwqnoqi8.exe (PID: 2324)
- 7nwqnoqi8.exe (PID: 3828)
Creates files in the user directory
- 7nwqnoqi8.exe (PID: 2324)
- powershell.exe (PID: 3068)
- 9pwspqsi8.exe (PID: 2656)
- powershell.exe (PID: 1956)
Starts itself from another location
- 7nwqnoqi8.exe (PID: 3828)
Adds / modifies Windows certificates
- 9pwspqsi8.exe (PID: 2656)
Checks for external IP
- 9pwspqsi8.exe (PID: 2656)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
60
Monitored processes
18
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\123456.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1088 | "C:\Users\admin\AppData\Roaming\gpuDriver\9pwspqsi8.exe" | C:\Users\admin\AppData\Roaming\gpuDriver\9pwspqsi8.exe | — | DllHost.exe | |||||||||||
User: admin Integrity Level: HIGH Description: RoundWindow MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 1140 | /c sc delete WinDefend | C:\Windows\system32\cmd.exe | — | 9pwspqsi8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1484 | sc stop WinDefend | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1656 | sc delete WinDefend | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1684 | /c sc stop WinDefend | C:\Windows\system32\cmd.exe | — | 9pwspqsi8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1062 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1956 | powershell Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | "C:\Users\admin\Desktop\7nwqnoqi8.exe" | C:\Users\admin\Desktop\7nwqnoqi8.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RoundWindow MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 2328 | /c powershell Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\system32\cmd.exe | — | 9pwspqsi8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2504 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 202
Read events
1 065
Write events
137
Delete events
0
Modification events
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\123456.rar | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (916) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3068) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
2
Suspicious files
12
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 916 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb916.1059\7nwqnoqi8.exe | — | |
MD5:— | SHA256:— | |||
| 3068 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OJ5VUP0SU7YZAHBKOQT3.temp | — | |
MD5:— | SHA256:— | |||
| 1956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\9C9WXN7NL7LDF1ATX35R.temp | — | |
MD5:— | SHA256:— | |||
| 2656 | 9pwspqsi8.exe | C:\Users\admin\AppData\Local\Temp\CabE77F.tmp | — | |
MD5:— | SHA256:— | |||
| 2656 | 9pwspqsi8.exe | C:\Users\admin\AppData\Local\Temp\TarE780.tmp | — | |
MD5:— | SHA256:— | |||
| 2656 | 9pwspqsi8.exe | C:\Users\admin\AppData\Local\Temp\CabE7AF.tmp | — | |
MD5:— | SHA256:— | |||
| 2656 | 9pwspqsi8.exe | C:\Users\admin\AppData\Local\Temp\TarE7B0.tmp | — | |
MD5:— | SHA256:— | |||
| 2656 | 9pwspqsi8.exe | C:\Users\admin\AppData\Local\Temp\CabE7D1.tmp | — | |
MD5:— | SHA256:— | |||
| 2656 | 9pwspqsi8.exe | C:\Users\admin\AppData\Local\Temp\TarE7D2.tmp | — | |
MD5:— | SHA256:— | |||
| 2656 | 9pwspqsi8.exe | C:\Users\admin\AppData\Local\Temp\CabE86F.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
7
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2656 | 9pwspqsi8.exe | GET | 200 | 205.185.216.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.6 Kb | whitelisted |
2656 | 9pwspqsi8.exe | GET | 200 | 52.202.139.131:80 | http://checkip.amazonaws.com/ | US | text | 14 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2656 | 9pwspqsi8.exe | 177.105.235.17:449 | — | Internet Pinheirense Ltda - ME | BR | malicious |
2656 | 9pwspqsi8.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2656 | 9pwspqsi8.exe | 200.122.209.78:449 | — | EPM Telecomunicaciones S.A. E.S.P. | CO | malicious |
2656 | 9pwspqsi8.exe | 52.202.139.131:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
2656 | 9pwspqsi8.exe | 198.12.71.40:447 | — | ColoCrossing | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |
checkip.amazonaws.com |
| malicious |
22.69.192.185.zen.spamhaus.org |
| unknown |
22.69.192.185.cbl.abuseat.org |
| unknown |
22.69.192.185.b.barracudacentral.org |
| unknown |
22.69.192.185.dnsbl-1.uceprotect.net |
| unknown |
22.69.192.185.spam.dnsbl.sorbs.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2656 | 9pwspqsi8.exe | Misc activity | SUSPICIOUS TEST [PTsecurity] Suspicious SSL certificate detected |
2656 | 9pwspqsi8.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
2656 | 9pwspqsi8.exe | Misc activity | SUSPICIOUS TEST [PTsecurity] Suspicious SSL certificate detected |
2656 | 9pwspqsi8.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dyre/Trickbot/Dridex SSL connection |
2656 | 9pwspqsi8.exe | Misc activity | SUSPICIOUS TEST [PTsecurity] Suspicious SSL certificate detected |
2656 | 9pwspqsi8.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
2656 | 9pwspqsi8.exe | Misc activity | SUSPICIOUS TEST [PTsecurity] Suspicious SSL certificate detected |
2656 | 9pwspqsi8.exe | A Network Trojan was detected | MALWARE [PTsecurity] Dyre/Trickbot/Dridex SSL connection |
1 ETPRO signatures available at the full report