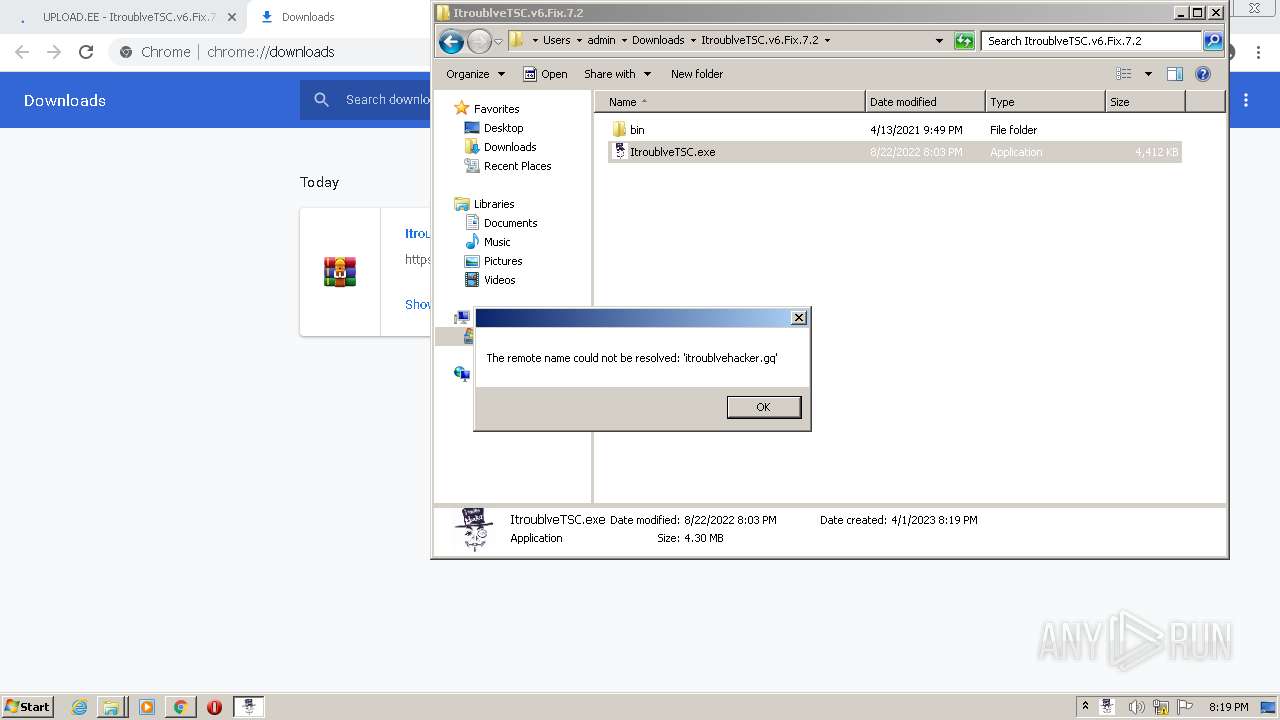
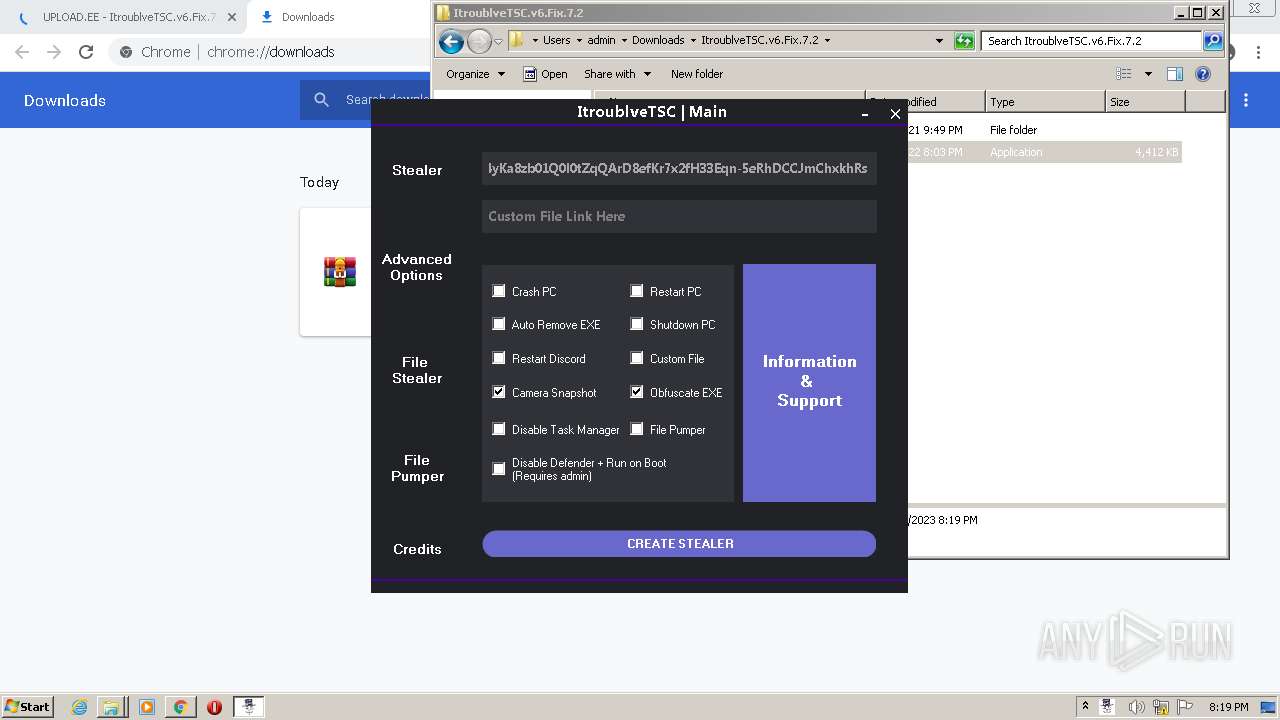
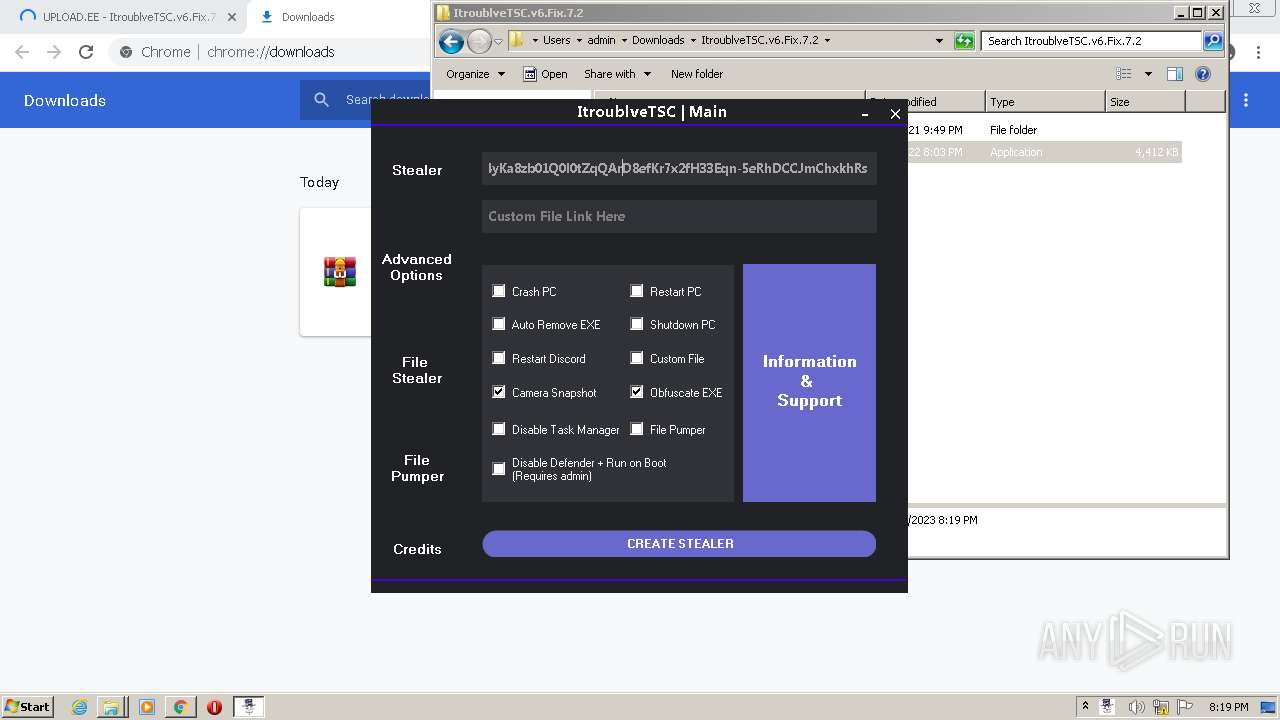
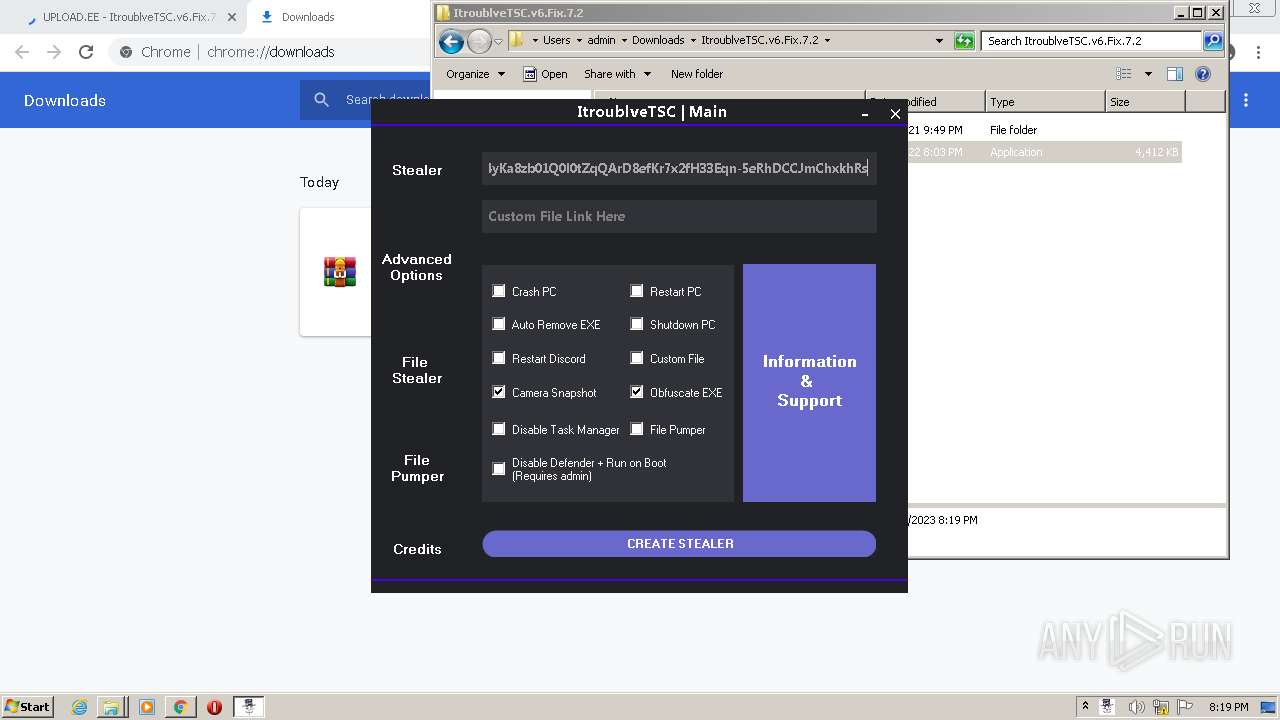
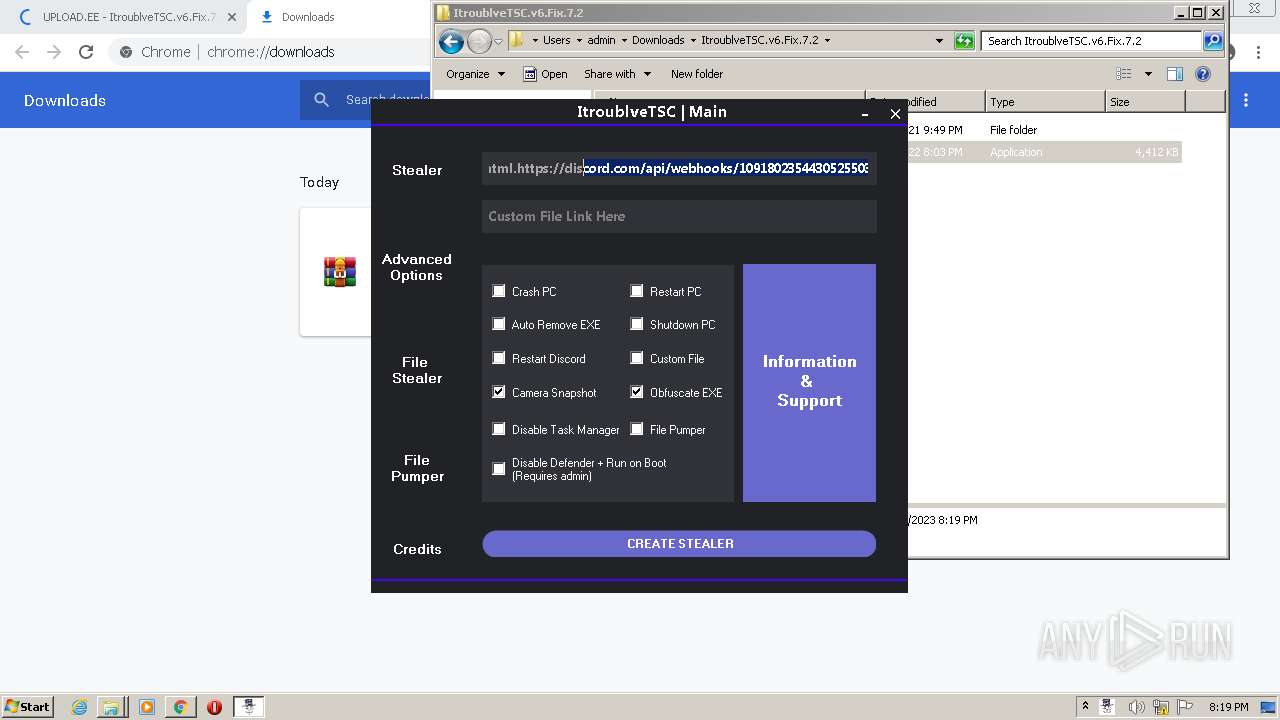
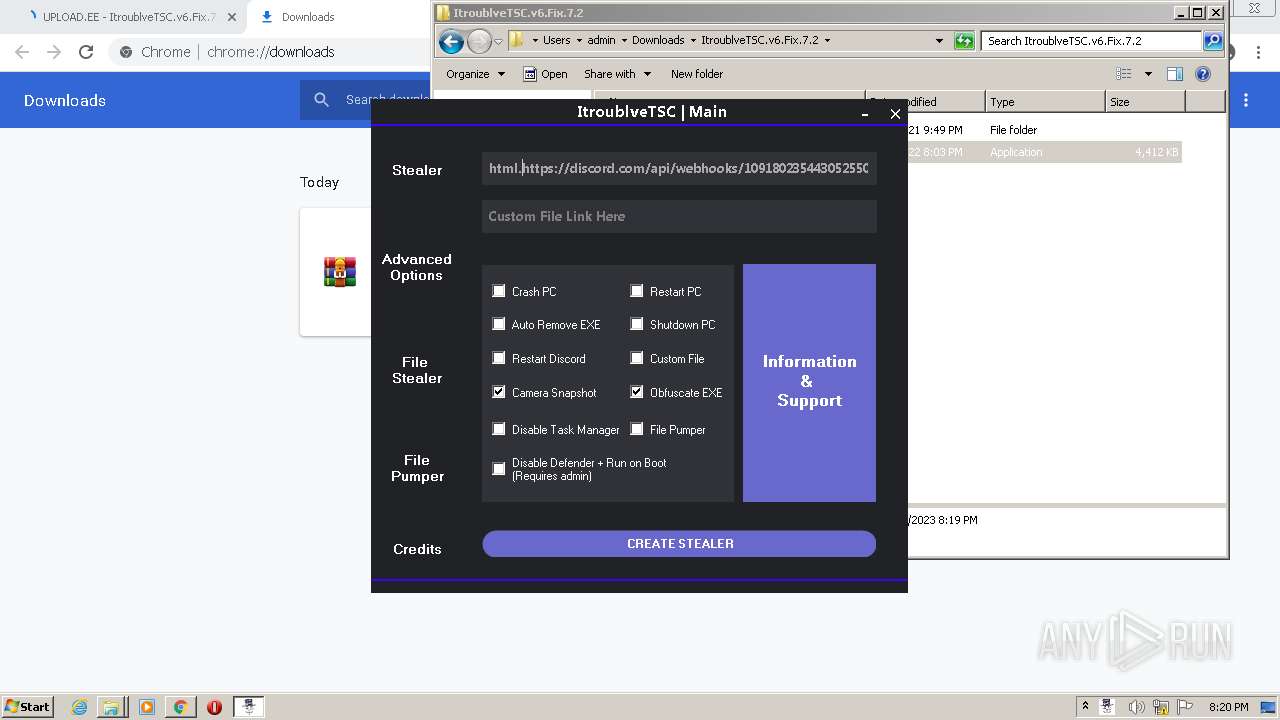
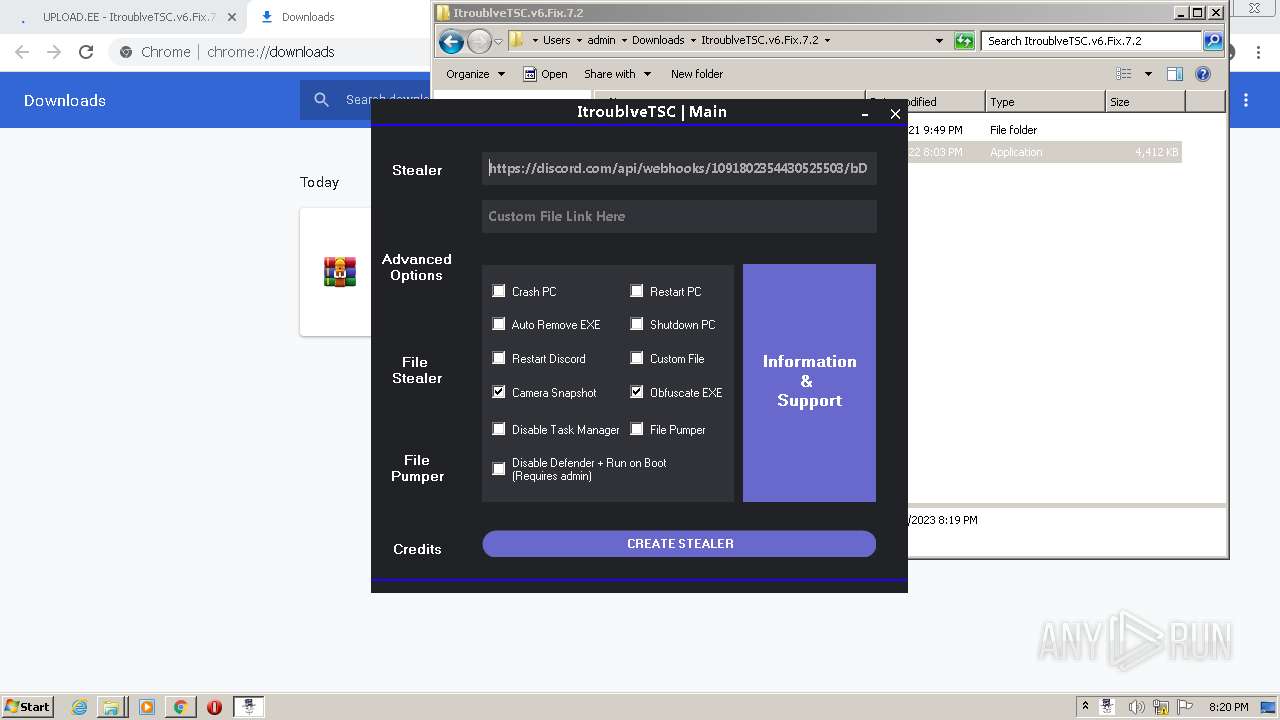
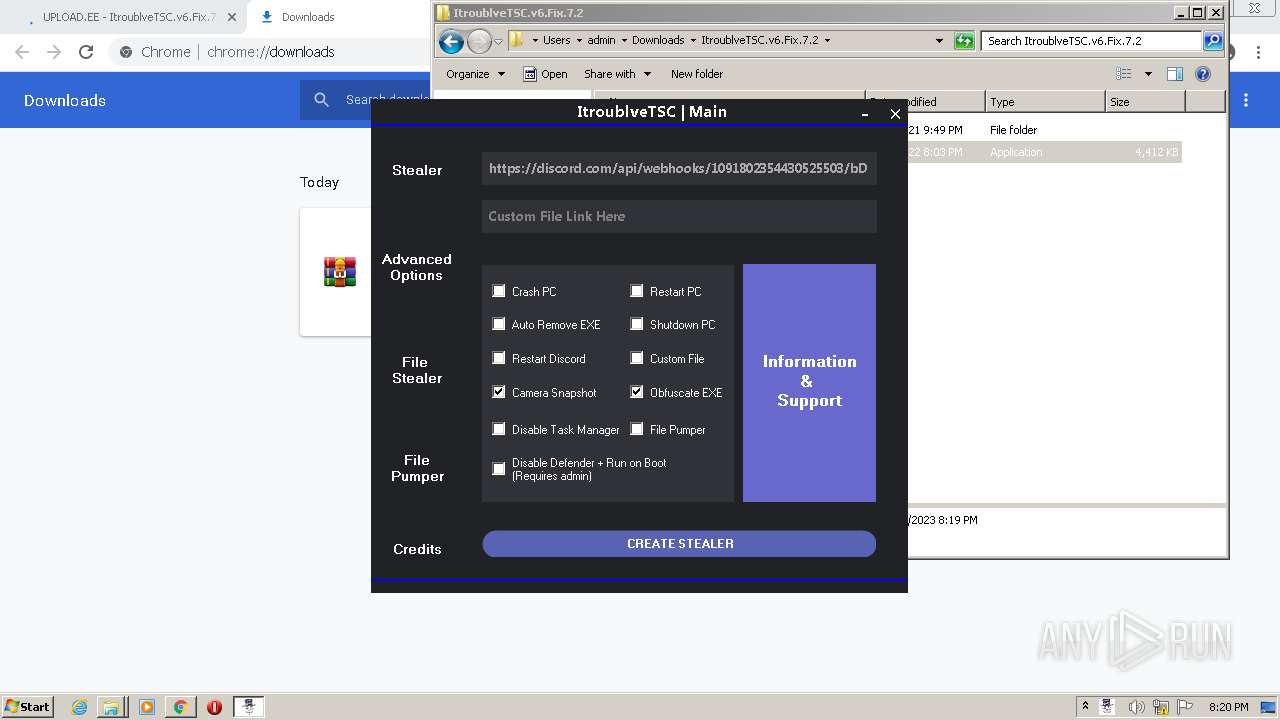
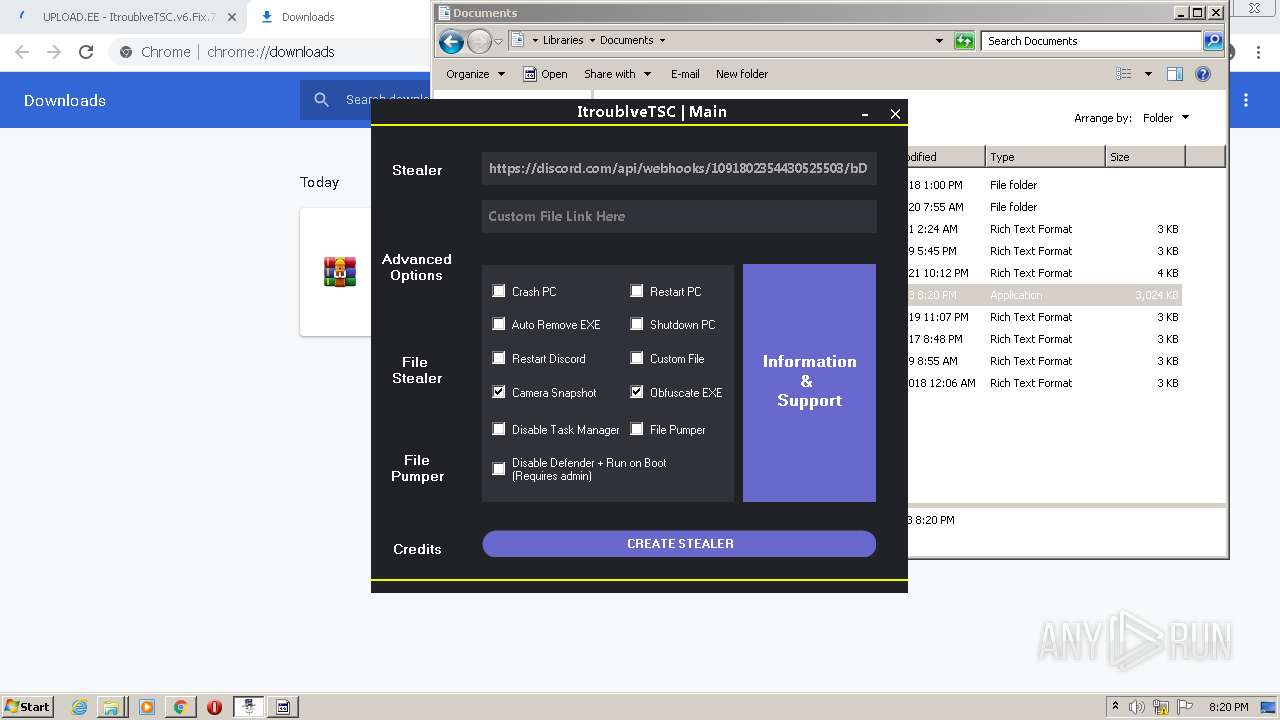
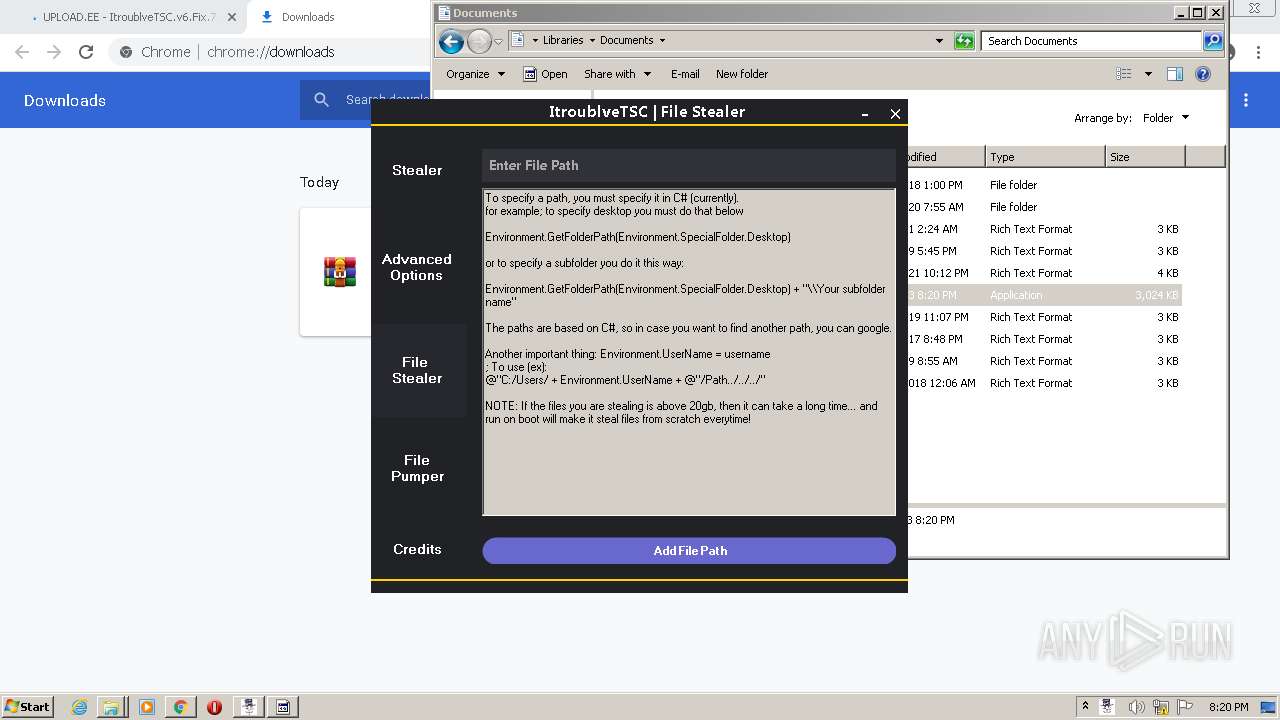
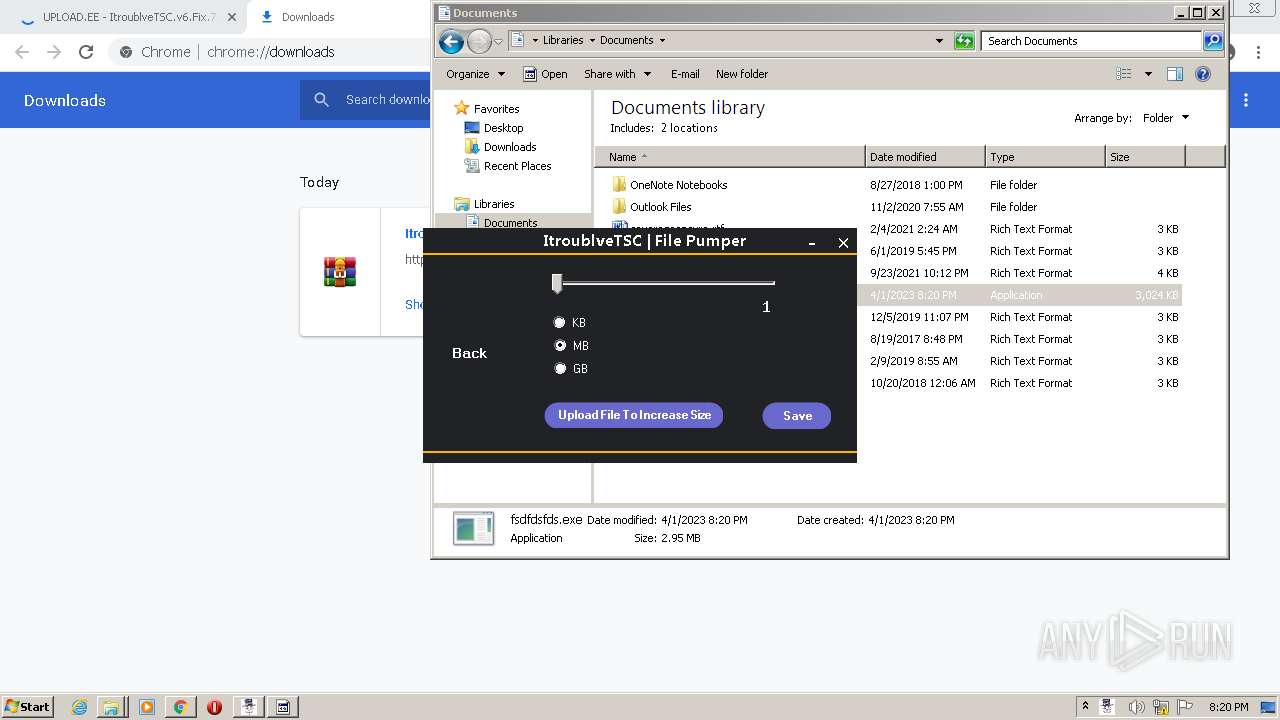
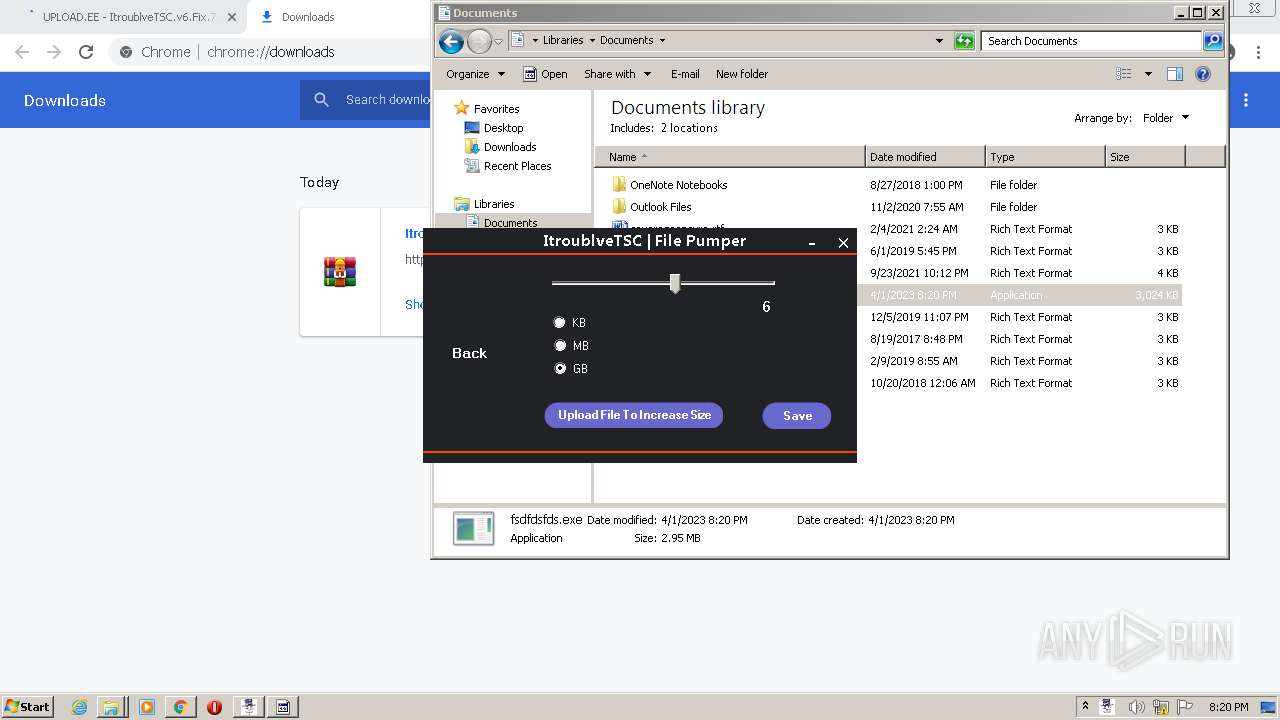
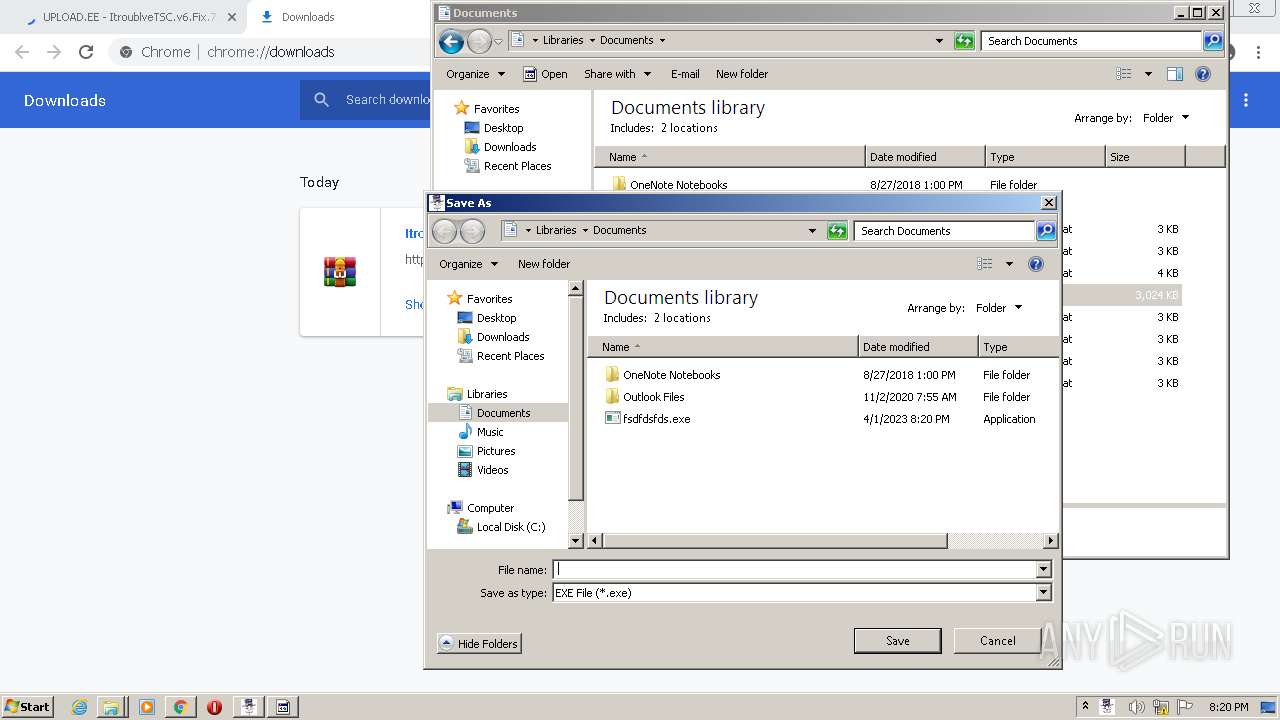
| URL: | https://www.upload.ee/files/14438830/ItroublveTSC.v6.Fix.7.2.rar.html.https://discord.com/api/webhooks/1091802354430525503/bDem94QCZ2RFPegT4yKa8zb01Q0l0tZqQArD8efKr7x2fH33Eqn-5eRhDCCJmChxkhRs |
| Full analysis: | https://app.any.run/tasks/b37eb4dd-910b-402c-b31c-8afc5cc782f5 |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | April 01, 2023, 19:18:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 89EE91F913DE12DA5443EC8A4F21974C |
| SHA1: | 45BD1C9605580B4DBE6A0AF331E76AA185B65816 |
| SHA256: | 62927F9DA0053901EC5AEB072A83115C74D2830FDB95F743693C157605C5F9F8 |
| SSDEEP: | 3:N8DSLr7MJmUDKizdU2QLWSjLzP6U8XkTFztfiQXQzQ2T1nXcLh7UpZCVD7A3apNm:2OLr0nrvQLBLzSUzUzh1Xsh7UvCW3eW |
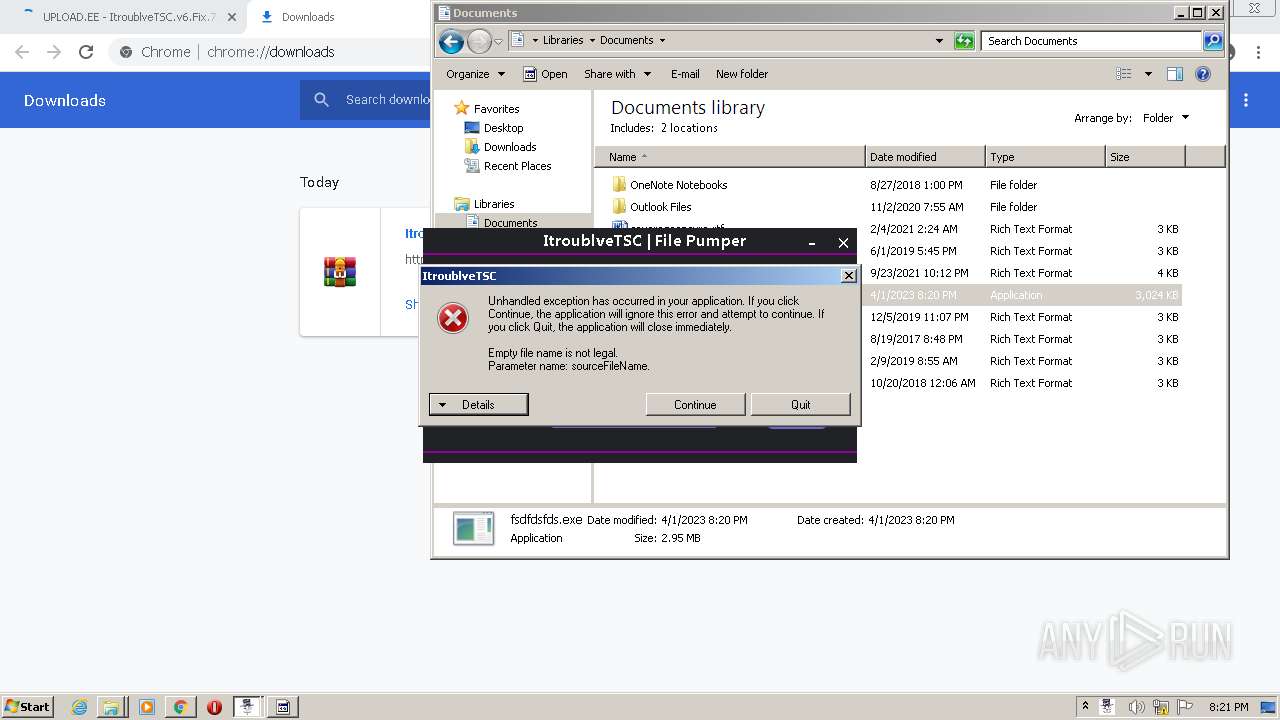
MALICIOUS
Application was dropped or rewritten from another process
- ItroublveTSC.exe (PID: 1584)
- RUN.exe (PID: 3036)
- ItroublveTSC.exe (PID: 1764)
- RealtekAudio.exe (PID: 3816)
- CLI.exe (PID: 2408)
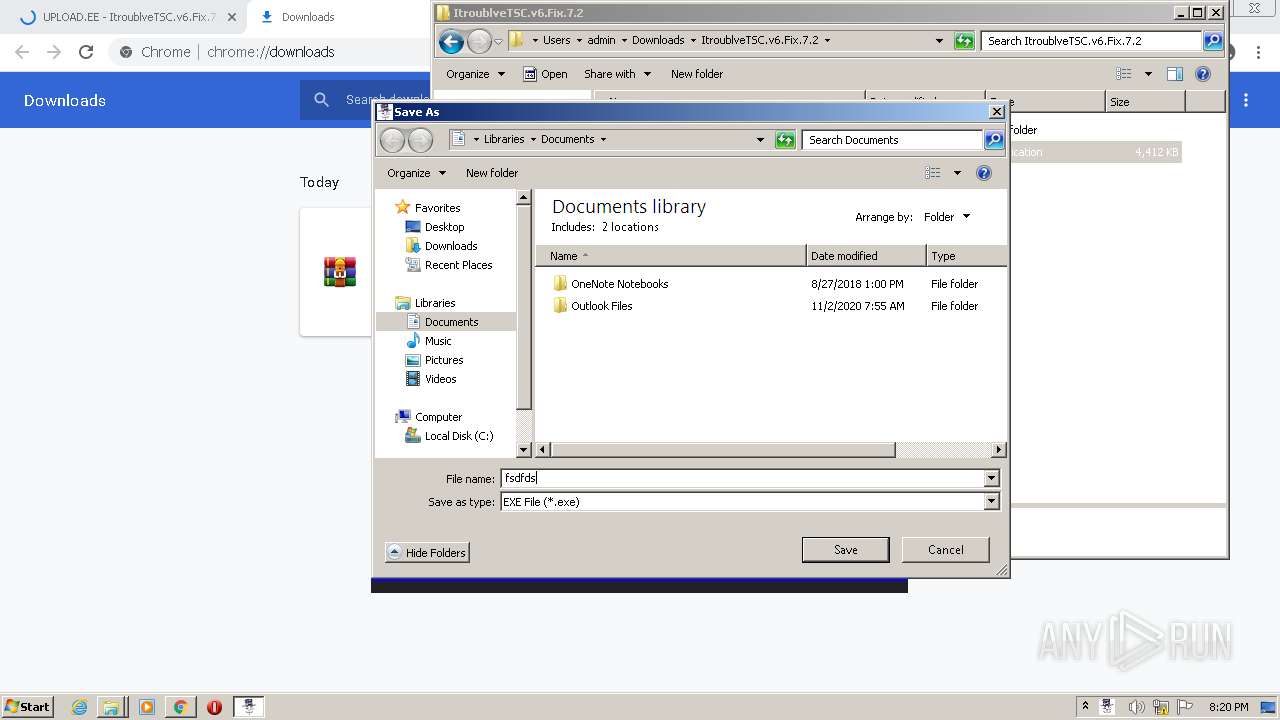
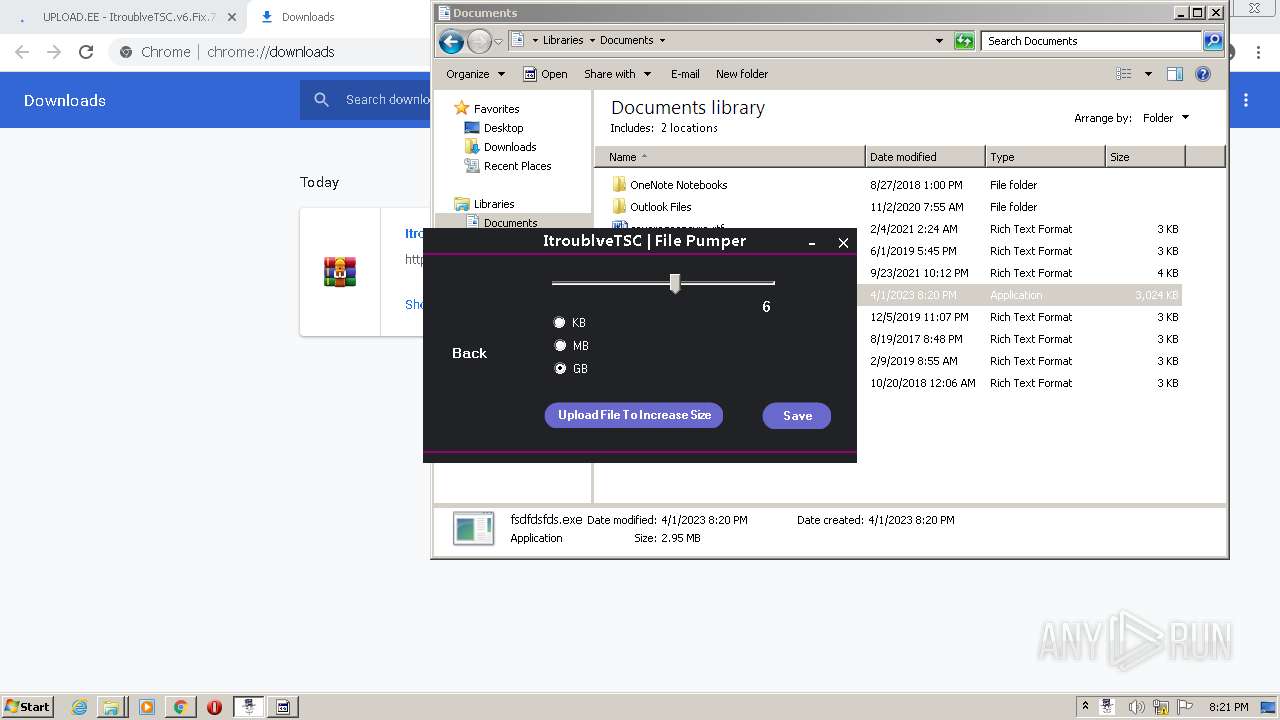
- fsdfdsfds.exe (PID: 1808)
- fsdfdsfds.exe (PID: 1648)
- RtkBtManServ.exe (PID: 3580)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1936)
Create files in the Startup directory
- RealtekAudio.exe (PID: 3816)
NJRAT detected by memory dumps
- RealtekAudio.exe (PID: 3816)
NjRAT is detected
- RealtekAudio.exe (PID: 3816)
Starts Visual C# compiler
- MSBuild.exe (PID: 1068)
Changes the autorun value in the registry
- RealtekAudio.exe (PID: 3816)
Actions looks like stealing of personal data
- RtkBtManServ.exe (PID: 3580)
SUSPICIOUS
Reads the Internet Settings
- ItroublveTSC.exe (PID: 1584)
- ItroublveTSC.exe (PID: 1764)
- RUN.exe (PID: 3036)
- wscript.exe (PID: 2640)
- CLI.exe (PID: 2408)
- fsdfdsfds.exe (PID: 1808)
- RtkBtManServ.exe (PID: 3580)
Executable content was dropped or overwritten
- ItroublveTSC.exe (PID: 1584)
- RUN.exe (PID: 3036)
- RealtekAudio.exe (PID: 3816)
- ItroublveTSC.exe (PID: 1764)
- MSBuild.exe (PID: 1068)
- csc.exe (PID: 4084)
- cmd.exe (PID: 1504)
- RtkBtManServ.exe (PID: 3580)
- fsdfdsfds.exe (PID: 1648)
Uses NETSH.EXE to add a firewall rule or allowed programs
- RealtekAudio.exe (PID: 3816)
Starts itself from another location
- RUN.exe (PID: 3036)
Executing commands from a ".bat" file
- wscript.exe (PID: 2640)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2640)
The process executes VB scripts
- ItroublveTSC.exe (PID: 1764)
Reads settings of System Certificates
- RtkBtManServ.exe (PID: 3580)
Reads browser cookies
- RtkBtManServ.exe (PID: 3580)
INFO
Application launched itself
- chrome.exe (PID: 1900)
The process checks LSA protection
- explorer.exe (PID: 3896)
- ItroublveTSC.exe (PID: 1584)
- ItroublveTSC.exe (PID: 1764)
- RUN.exe (PID: 3036)
- netsh.exe (PID: 3248)
- RealtekAudio.exe (PID: 3816)
- MSBuild.exe (PID: 1068)
- csc.exe (PID: 4084)
- cvtres.exe (PID: 2900)
- CLI.exe (PID: 2408)
- fsdfdsfds.exe (PID: 1808)
- fsdfdsfds.exe (PID: 1648)
- RtkBtManServ.exe (PID: 3580)
The process uses the downloaded file
- WinRAR.exe (PID: 2644)
- chrome.exe (PID: 2348)
Manual execution by a user
- explorer.exe (PID: 3896)
- WinRAR.exe (PID: 2644)
- ItroublveTSC.exe (PID: 1584)
- fsdfdsfds.exe (PID: 1808)
- fsdfdsfds.exe (PID: 1648)
Create files in a temporary directory
- chrome.exe (PID: 1900)
- ItroublveTSC.exe (PID: 1584)
- cvtres.exe (PID: 2900)
- MSBuild.exe (PID: 1068)
- csc.exe (PID: 4084)
- CLI.exe (PID: 2408)
- fsdfdsfds.exe (PID: 1808)
- fsdfdsfds.exe (PID: 1648)
- RtkBtManServ.exe (PID: 3580)
- ItroublveTSC.exe (PID: 1764)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2644)
Checks supported languages
- ItroublveTSC.exe (PID: 1584)
- ItroublveTSC.exe (PID: 1764)
- RUN.exe (PID: 3036)
- RealtekAudio.exe (PID: 3816)
- MSBuild.exe (PID: 1068)
- csc.exe (PID: 4084)
- cvtres.exe (PID: 2900)
- CLI.exe (PID: 2408)
- fsdfdsfds.exe (PID: 1808)
- fsdfdsfds.exe (PID: 1648)
- RtkBtManServ.exe (PID: 3580)
Reads the computer name
- ItroublveTSC.exe (PID: 1584)
- ItroublveTSC.exe (PID: 1764)
- RUN.exe (PID: 3036)
- RealtekAudio.exe (PID: 3816)
- MSBuild.exe (PID: 1068)
- CLI.exe (PID: 2408)
- fsdfdsfds.exe (PID: 1808)
- RtkBtManServ.exe (PID: 3580)
- fsdfdsfds.exe (PID: 1648)
Reads Environment values
- ItroublveTSC.exe (PID: 1764)
- RealtekAudio.exe (PID: 3816)
- RtkBtManServ.exe (PID: 3580)
Reads the machine GUID from the registry
- ItroublveTSC.exe (PID: 1764)
- RUN.exe (PID: 3036)
- RealtekAudio.exe (PID: 3816)
- MSBuild.exe (PID: 1068)
- csc.exe (PID: 4084)
- cvtres.exe (PID: 2900)
- fsdfdsfds.exe (PID: 1808)
- fsdfdsfds.exe (PID: 1648)
- CLI.exe (PID: 2408)
- RtkBtManServ.exe (PID: 3580)
Creates files or folders in the user directory
- RUN.exe (PID: 3036)
- RealtekAudio.exe (PID: 3816)
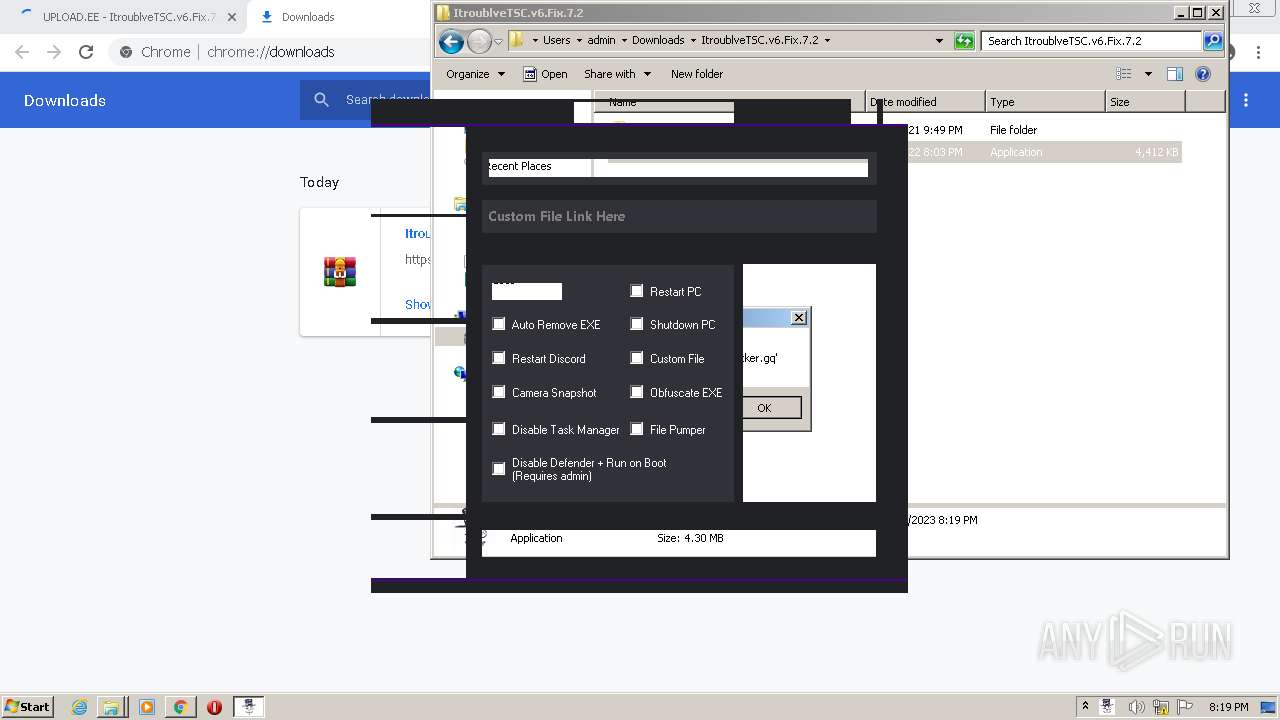
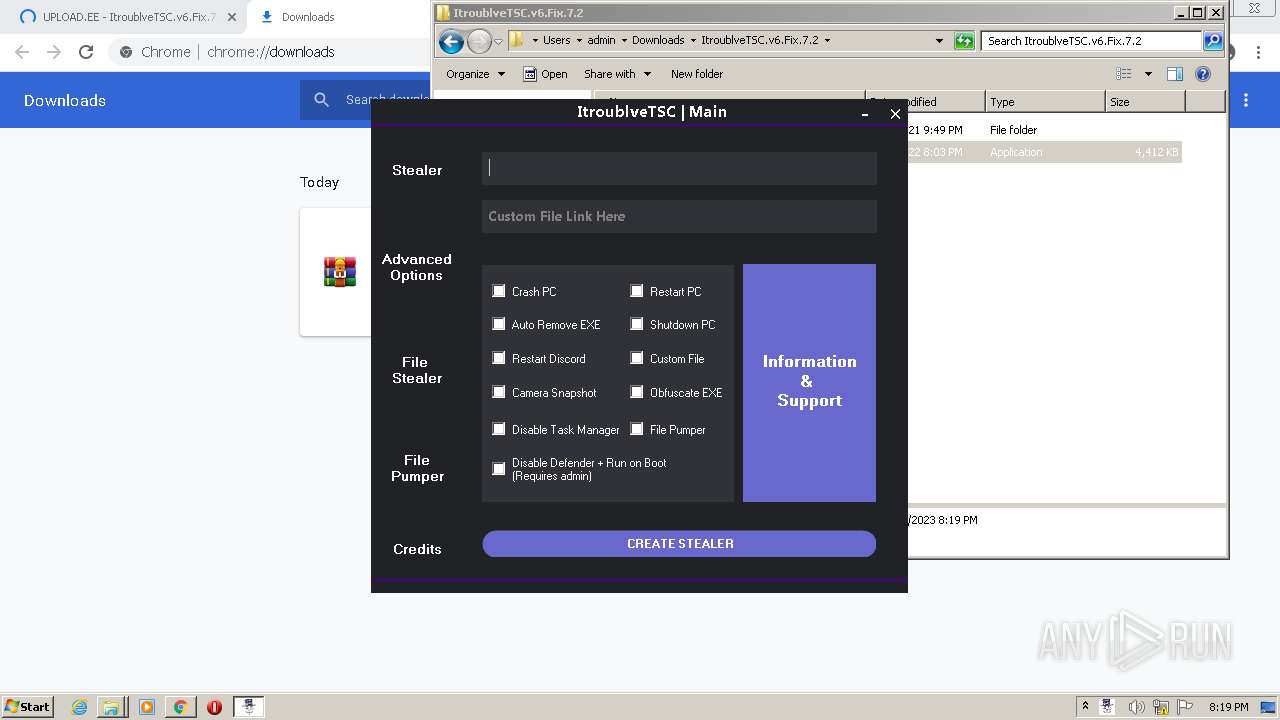
[YARA] Firewall manipulation strings were found
- RealtekAudio.exe (PID: 3816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(3816) RealtekAudio.exe
C2unrealconnection.ddns.net
Ports1194
BotnetHacKed
Options
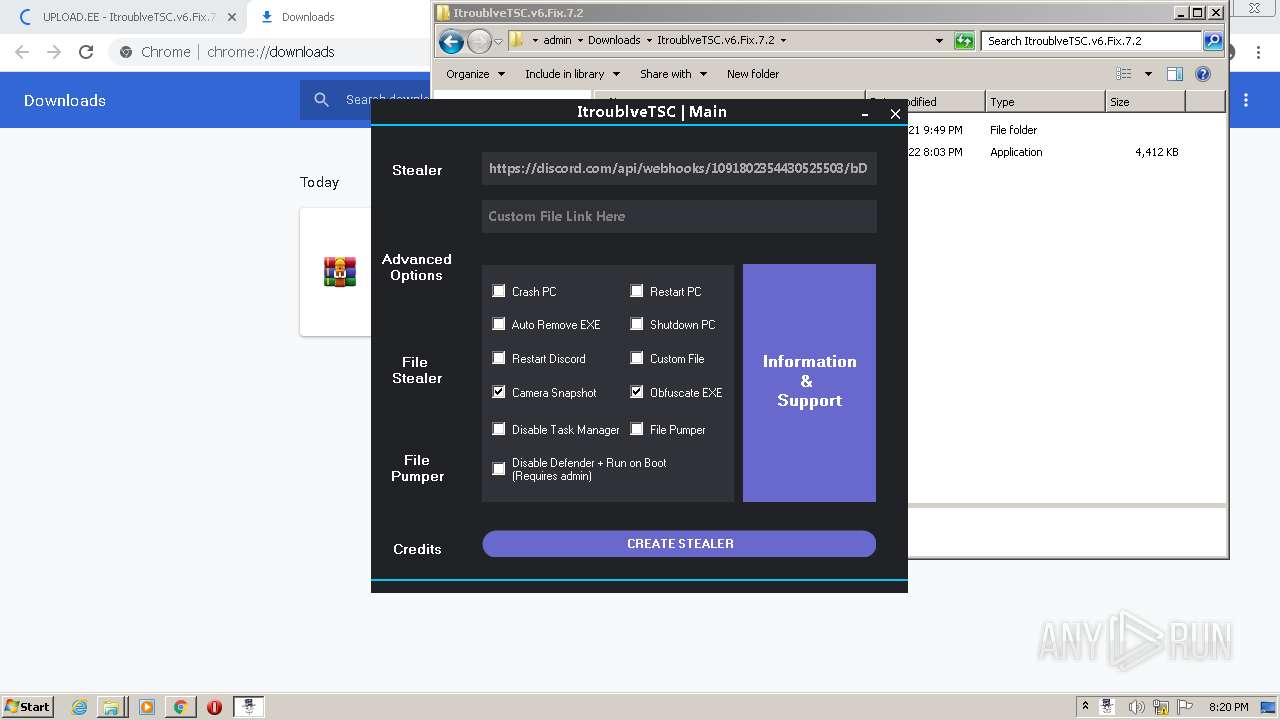
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\15d7b7890e8fe50c4b0c800e4196a491
Splitter|'|'|
Versionim523
Total processes
83
Monitored processes
38
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,15243313652361588440,6038570522072725167,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3632 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1068 | C:/Windows/Microsoft.NET/Framework/v4.0.30319/msbuild.exe TSC.sln | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 1504 | "C:\Windows\System32\cmd.exe" /c compile.bat | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1584 | "C:\Users\admin\Downloads\ItroublveTSC.v6.Fix.7.2\ItroublveTSC.exe" | C:\Users\admin\Downloads\ItroublveTSC.v6.Fix.7.2\ItroublveTSC.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
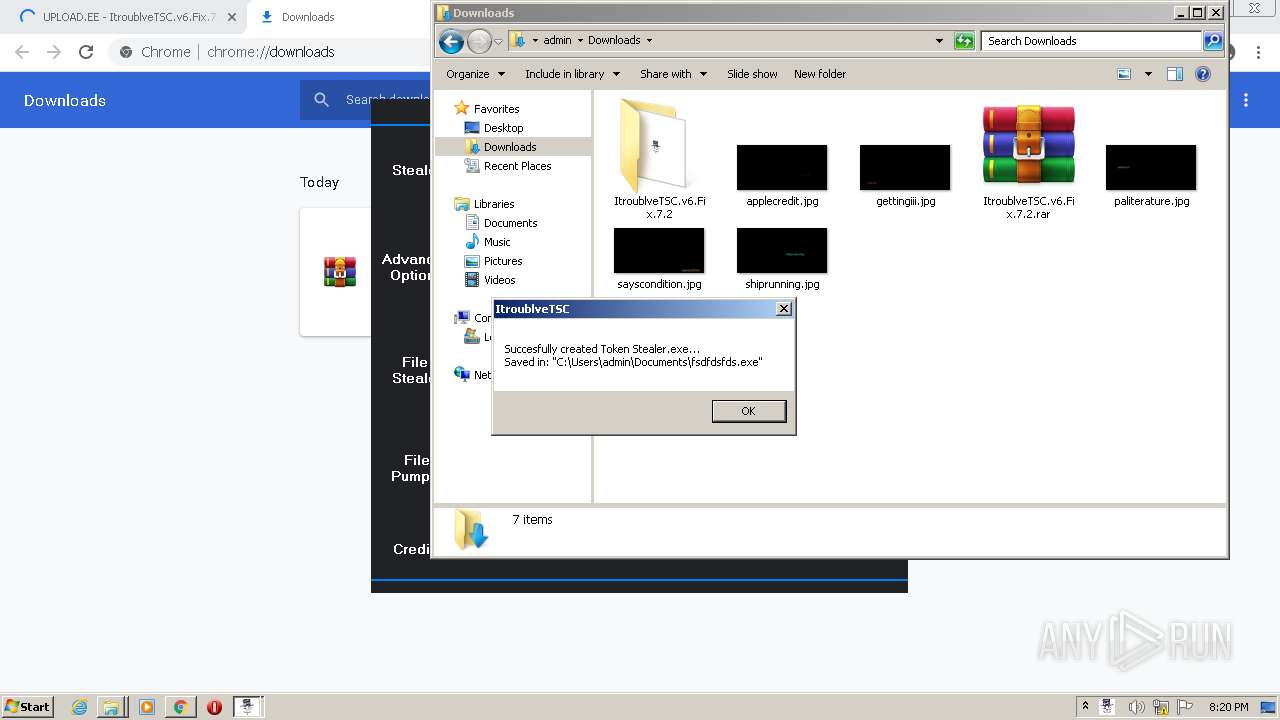
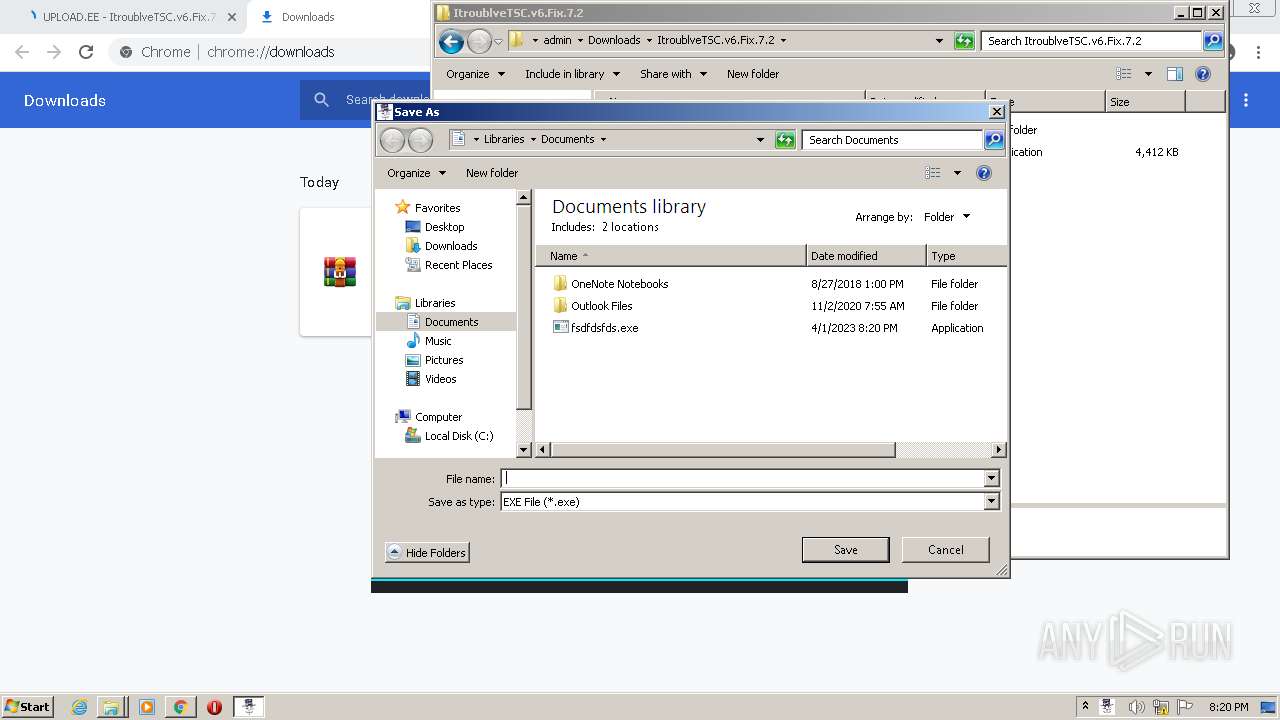
| 1648 | "C:\Users\admin\Documents\fsdfdsfds.exe" | C:\Users\admin\Documents\fsdfdsfds.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1764 | "C:\Users\admin\AppData\Local\Temp\ItroublveTSC.exe" | C:\Users\admin\AppData\Local\Temp\ItroublveTSC.exe | ItroublveTSC.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ItroublveTSC Exit code: 0 Version: 6.0.0.0 Modules
| |||||||||||||||
| 1808 | "C:\Users\admin\Documents\fsdfdsfds.exe" | C:\Users\admin\Documents\fsdfdsfds.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1900 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://www.upload.ee/files/14438830/ItroublveTSC.v6.Fix.7.2.rar.html.https://discord.com/api/webhooks/1091802354430525503/bDem94QCZ2RFPegT4yKa8zb01Q0l0tZqQArD8efKr7x2fH33Eqn-5eRhDCCJmChxkhRs" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | explorer.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1936 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1032,15243313652361588440,6038570522072725167,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2636 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
54 874
Read events
54 042
Write events
788
Delete events
44
Modification events
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
| (PID) Process: | (1900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
Executable files
116
Suspicious files
116
Text files
382
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-642883A2-76C.pma | — | |
MD5:— | SHA256:— | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\dcb7453d-6896-4870-a951-ca96fdfbca45.tmp | text | |
MD5:— | SHA256:— | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF24f2fc.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF24f31b.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF24f2fc.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\13f5d1ec-7b70-47d2-8f83-4ad3eee18e25.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 1900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
38
DNS requests
29
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 5.55 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 8.50 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 48.5 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 10.3 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 88.0 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 12.0 Kb | whitelisted |
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 5.89 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 5.89 Kb | whitelisted |
860 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | crx | 3.72 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3344 | chrome.exe | 51.91.30.159:443 | www.upload.ee | OVH SAS | FR | suspicious |
3344 | chrome.exe | 142.250.181.225:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
3344 | chrome.exe | 142.250.186.46:443 | clients2.google.com | GOOGLE | US | whitelisted |
3344 | chrome.exe | 142.250.186.104:443 | www.googletagmanager.com | GOOGLE | US | suspicious |
3344 | chrome.exe | 172.217.16.130:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
3344 | chrome.exe | 172.217.23.98:443 | googleads.g.doubleclick.net | GOOGLE | US | whitelisted |
3344 | chrome.exe | 142.250.184.234:443 | content-autofill.googleapis.com | GOOGLE | US | whitelisted |
3344 | chrome.exe | 172.217.16.206:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
3344 | chrome.exe | 142.250.186.68:443 | www.google.com | GOOGLE | US | whitelisted |
3344 | chrome.exe | 142.250.181.227:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.upload.ee |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .gq Domain |
— | — | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
3580 | RtkBtManServ.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3580 | RtkBtManServ.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |