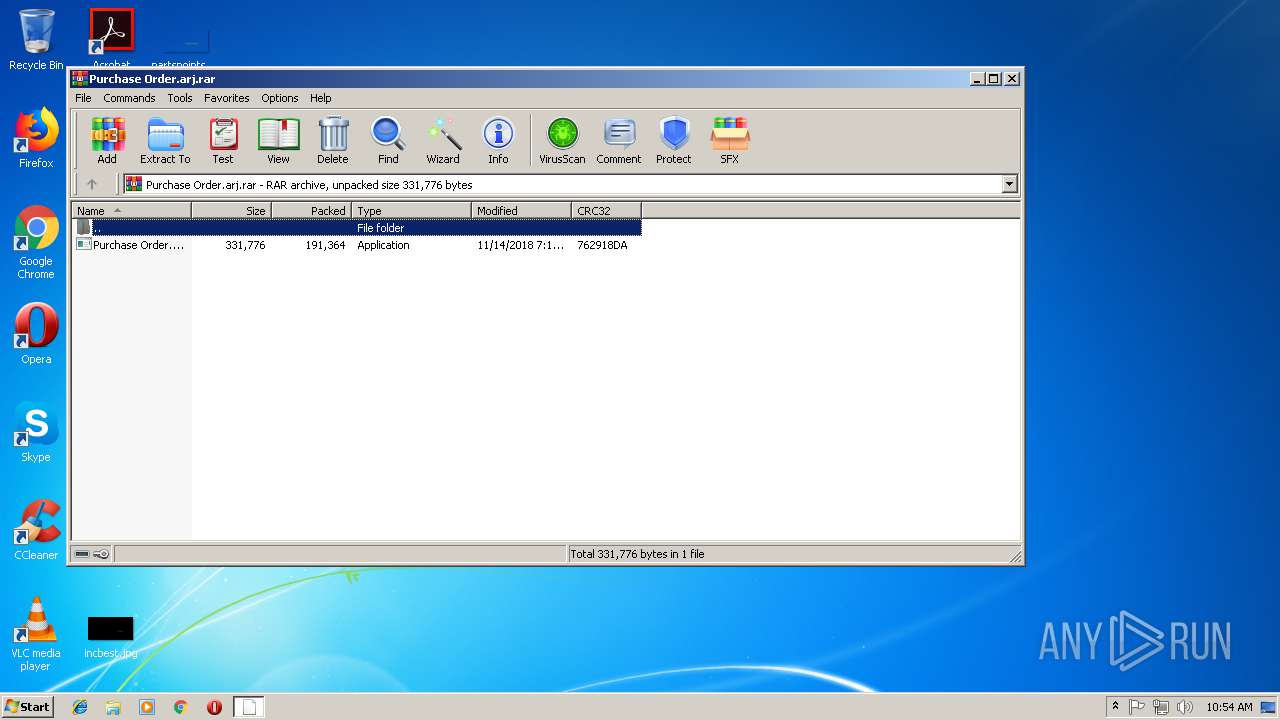
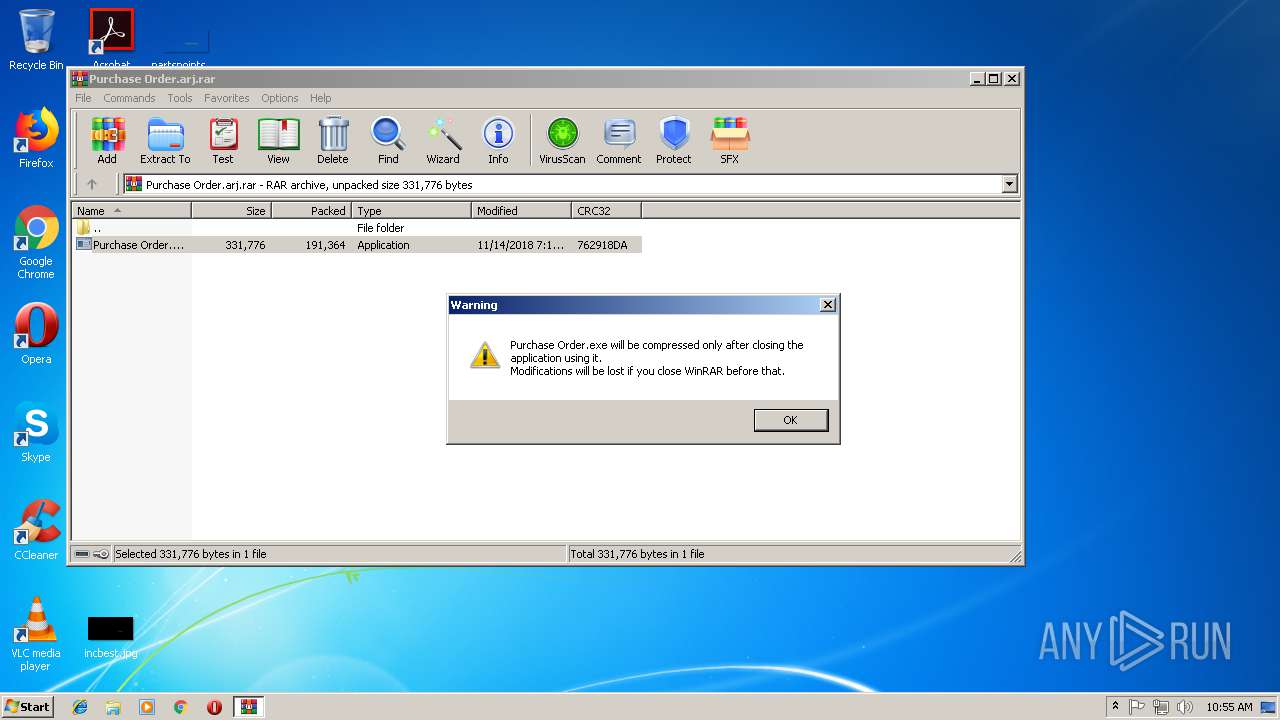
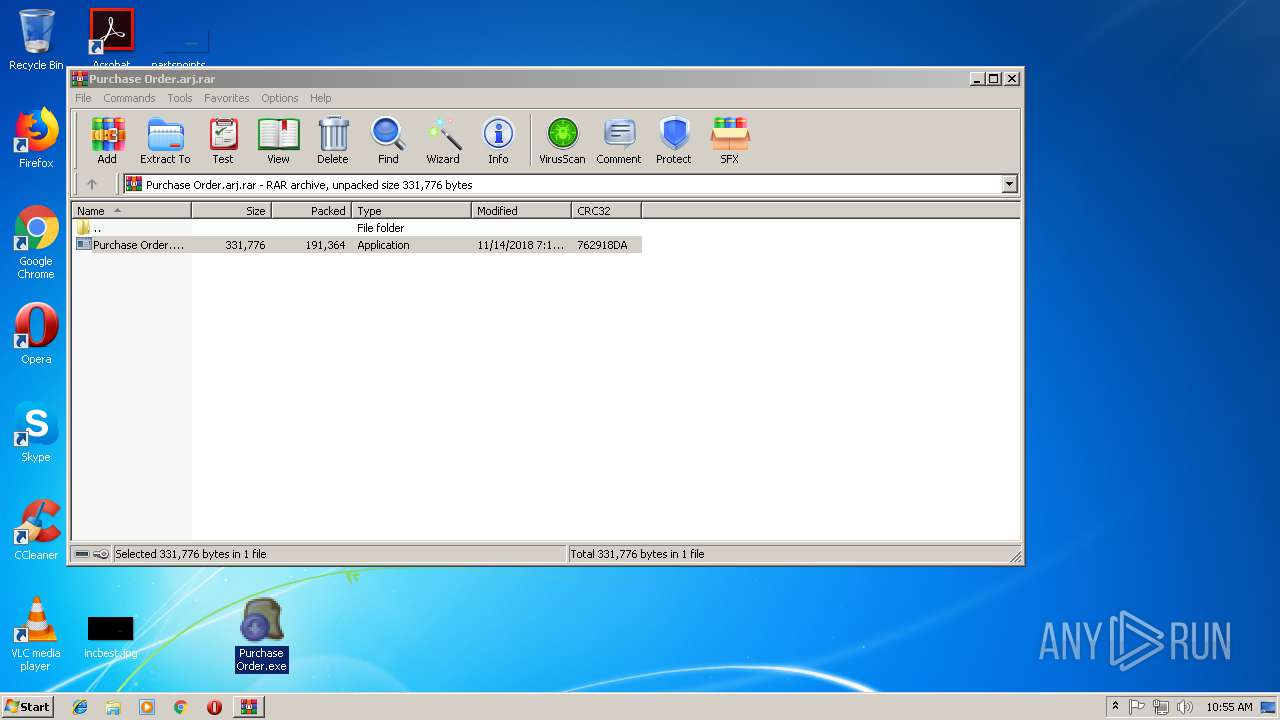
| File name: | Purchase Order.arj |
| Full analysis: | https://app.any.run/tasks/9d32b584-863a-468b-8aa7-4e4f45388e0a |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | November 15, 2018, 10:54:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8E7AC1F05894DCF6EE37A74013012AE4 |
| SHA1: | 50FE653F624F4264CEA4967E30BE64D0B38AB246 |
| SHA256: | 6248CE89DE74766D0E4A1E17BBFDF2379F644BF7C6A724E6F0D08FE0EECC0258 |
| SSDEEP: | 3072:BEQlpclrYal2pho+0HjUGaZIk7VJLc9wXHRgAaZpViHVqgG:BNKYal0hoJAhVJgqXHRBaZpV2zG |
MALICIOUS
FORMBOOK was detected
- explorer.exe (PID: 1604)
Application was dropped or rewritten from another process
- Purchase Order.exe (PID: 3492)
- Cookies8pr.exe (PID: 4008)
- Purchase Order.exe (PID: 3036)
Formbook was detected
- rundll32.exe (PID: 3096)
- Firefox.exe (PID: 2432)
Changes the autorun value in the registry
- rundll32.exe (PID: 3096)
Actions looks like stealing of personal data
- rundll32.exe (PID: 3096)
Connects to CnC server
- explorer.exe (PID: 1604)
Stealing of credential data
- rundll32.exe (PID: 3096)
SUSPICIOUS
Reads Internet Cache Settings
- explorer.exe (PID: 1604)
Creates files in the user directory
- explorer.exe (PID: 1604)
- rundll32.exe (PID: 3096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3440)
- explorer.exe (PID: 1604)
- DllHost.exe (PID: 800)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 1604)
Creates files in the program directory
- DllHost.exe (PID: 800)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 3096)
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 3096)
INFO
Creates files in the user directory
- Firefox.exe (PID: 2432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 800 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | rundll32.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2568 | "C:\Windows\System32\msiexec.exe" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2920 | /c del "C:\Users\admin\AppData\Local\Temp\Rar$EXa3440.29664\Purchase Order.exe" | C:\Windows\System32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3036 | "C:\Users\admin\Desktop\Purchase Order.exe" | C:\Users\admin\Desktop\Purchase Order.exe | — | explorer.exe | |||||||||||
User: admin Company: lexus Integrity Level: MEDIUM Description: lexus Exit code: 0 Version: 3.01.0009 Modules
| |||||||||||||||
| 3096 | "C:\Windows\System32\rundll32.exe" | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Purchase Order.arj.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3492 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3440.29664\Purchase Order.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3440.29664\Purchase Order.exe | — | WinRAR.exe | |||||||||||
User: admin Company: lexus Integrity Level: MEDIUM Description: lexus Exit code: 0 Version: 3.01.0009 Modules
| |||||||||||||||
| 3944 | "C:\Windows\System32\raserver.exe" | C:\Windows\System32\raserver.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Remote Assistance COM Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 324
Read events
2 268
Write events
54
Delete events
2
Modification events
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Purchase Order.arj.rar | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
4
Suspicious files
73
Text files
1
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3492 | Purchase Order.exe | C:\Users\admin\AppData\Local\Temp\~DF7A8E4187DDA1F19F.TMP | — | |
MD5:— | SHA256:— | |||
| 3440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3440.33216\Purchase Order.exe | — | |
MD5:— | SHA256:— | |||
| 3036 | Purchase Order.exe | C:\Users\admin\AppData\Local\Temp\~DF65952AA47F85ED11.TMP | — | |
MD5:— | SHA256:— | |||
| 4008 | Cookies8pr.exe | C:\Users\admin\AppData\Local\Temp\~DF5DBCB6EA546B8DCB.TMP | — | |
MD5:— | SHA256:— | |||
| 1604 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Purchase Order.arj.rar.lnk | lnk | |
MD5:— | SHA256:— | |||
| 1604 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | automaticdestinations-ms | |
MD5:— | SHA256:— | |||
| 1604 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012018111520181116\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3440.29664\Purchase Order.exe | executable | |
MD5:— | SHA256:— | |||
| 3096 | rundll32.exe | C:\Users\admin\AppData\Roaming\LMO8QCRE\LMOlogrc.ini | binary | |
MD5:— | SHA256:— | |||
| 800 | DllHost.exe | C:\Program Files\Mib8x\Cookies8pr.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
10
DNS requests
8
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1604 | explorer.exe | GET | 403 | 47.254.39.76:80 | http://www.zhuizhai.site/uc/?KnJHv=3CZTDHn4u0xx0D9ZJAa1wC1JYCuuoDGZd9kjSBl1n8AxfdxGv7OFiAsqh3n3RWCEM+c3rg==&ppv=K2KdTZix8vZDAFKP&sql=1 | US | html | 724 b | malicious |
1604 | explorer.exe | POST | — | 199.192.21.143:80 | http://www.sezop.com/uc/ | US | — | — | malicious |
1604 | explorer.exe | GET | 302 | 54.208.56.179:80 | http://www.clscammers.com/uc/?KnJHv=0CLUVPlbpIPwqcDS6LIOuvsVHT2eSl5h11r/r+vjFCNnSAX6B3GUHJ9Sm+eW0v5PNOCDFA==&ppv=K2KdTZix8vZDAFKP | US | html | 186 b | malicious |
1604 | explorer.exe | POST | — | 199.192.21.143:80 | http://www.sezop.com/uc/ | US | — | — | malicious |
1604 | explorer.exe | GET | 404 | 199.192.21.143:80 | http://www.sezop.com/uc/?KnJHv=zg1s9sLMXWbjwxN8cTinTb+bqQMqR9FxD0rKLxMvrlZtVXAVSUsJNdRjsBstTRhACiUHSw==&ppv=K2KdTZix8vZDAFKP&sql=1 | US | html | 326 b | malicious |
1604 | explorer.exe | POST | — | 199.192.21.143:80 | http://www.sezop.com/uc/ | US | — | — | malicious |
1604 | explorer.exe | POST | — | 47.254.39.76:80 | http://www.zhuizhai.site/uc/ | US | — | — | malicious |
1604 | explorer.exe | POST | 404 | 199.192.21.143:80 | http://www.sezop.com/uc/ | US | html | 287 b | malicious |
1604 | explorer.exe | GET | — | 51.255.102.144:80 | http://www.dentistry-apple.com/uc/?KnJHv=vQ62Y96vJbHz2CgShJfup2mhn1AxM1ZNaogWBHTfwRu/Ys9s6l7v4QF6jcXQDRlhKJKZpA==&ppv=K2KdTZix8vZDAFKP | FR | — | — | malicious |
1604 | explorer.exe | POST | — | 47.254.39.76:80 | http://www.zhuizhai.site/uc/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1604 | explorer.exe | 54.208.56.179:80 | www.clscammers.com | Amazon.com, Inc. | US | malicious |
1604 | explorer.exe | 47.254.39.76:80 | www.zhuizhai.site | Alibaba (China) Technology Co., Ltd. | US | malicious |
1604 | explorer.exe | 199.192.21.143:80 | www.sezop.com | — | US | malicious |
1604 | explorer.exe | 51.255.102.144:80 | www.dentistry-apple.com | OVH SAS | FR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.kxaww.loan |
| unknown |
www.clscammers.com |
| malicious |
www.zhuizhai.site |
| malicious |
dns.msftncsi.com |
| shared |
www.sezop.com |
| malicious |
www.jkgfiuyfujhnow.online |
| unknown |
www.dentistry-apple.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1604 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
1604 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
1604 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (POST) |
6 ETPRO signatures available at the full report