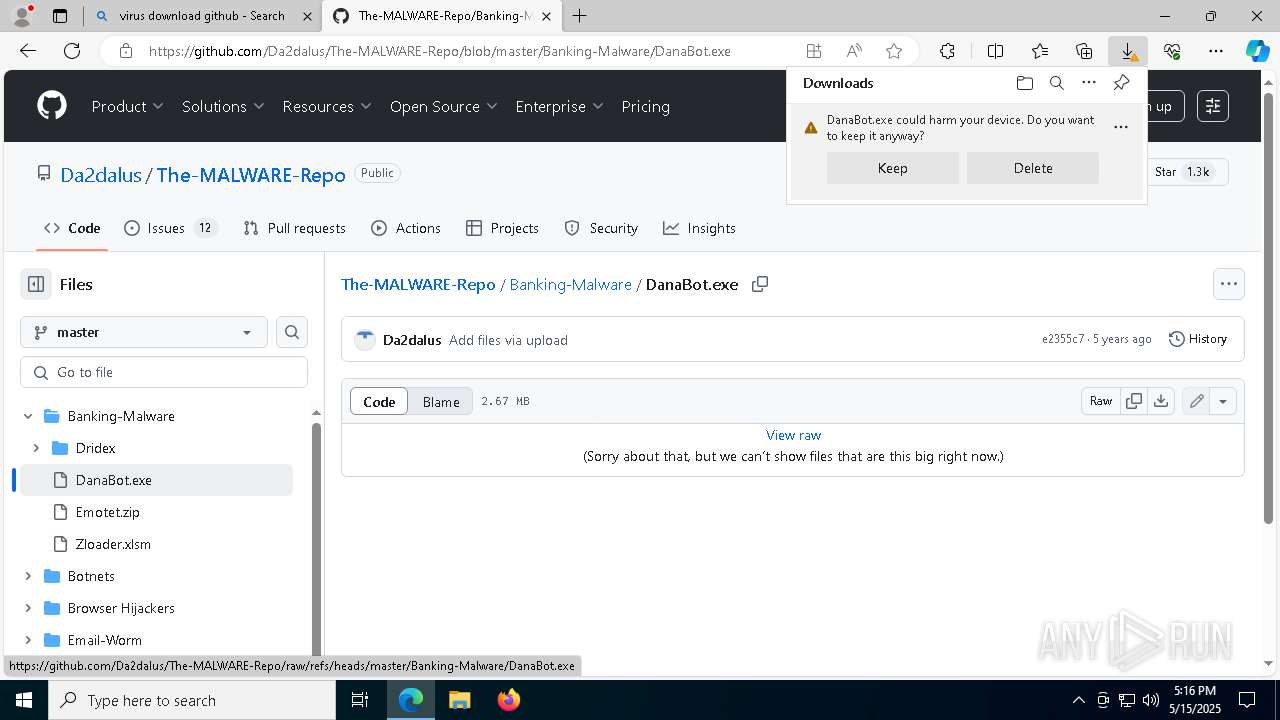
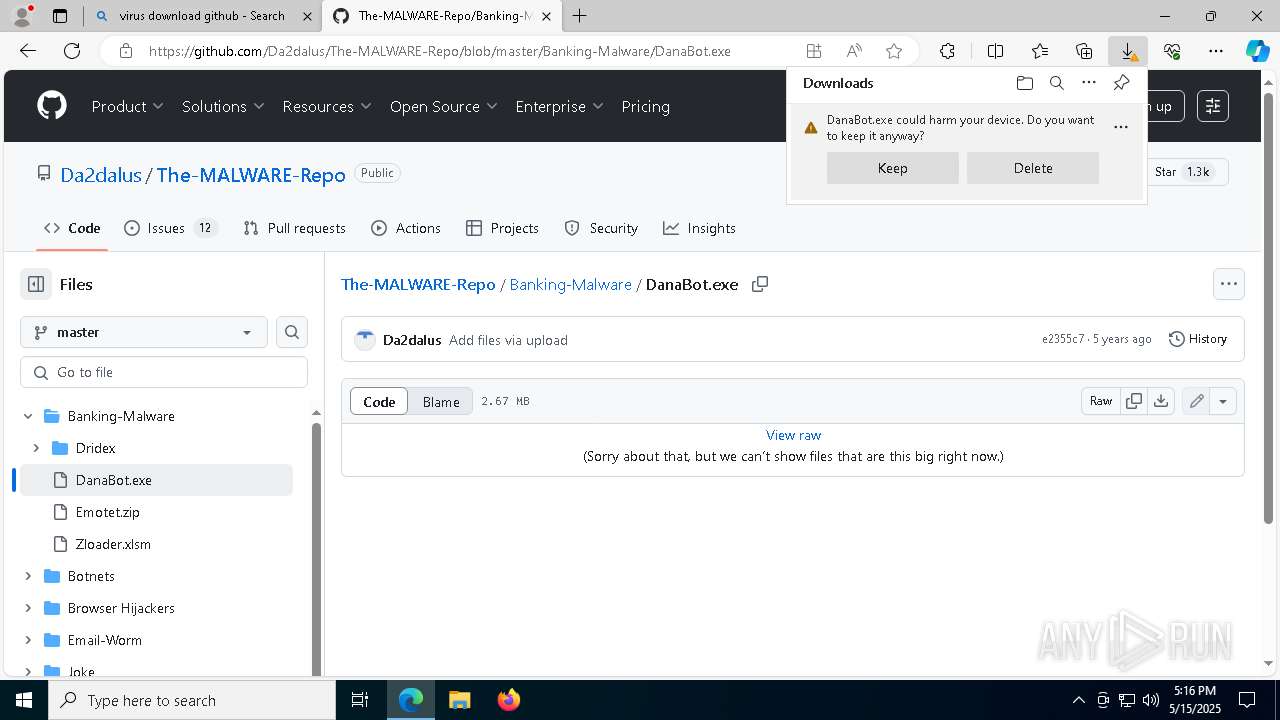
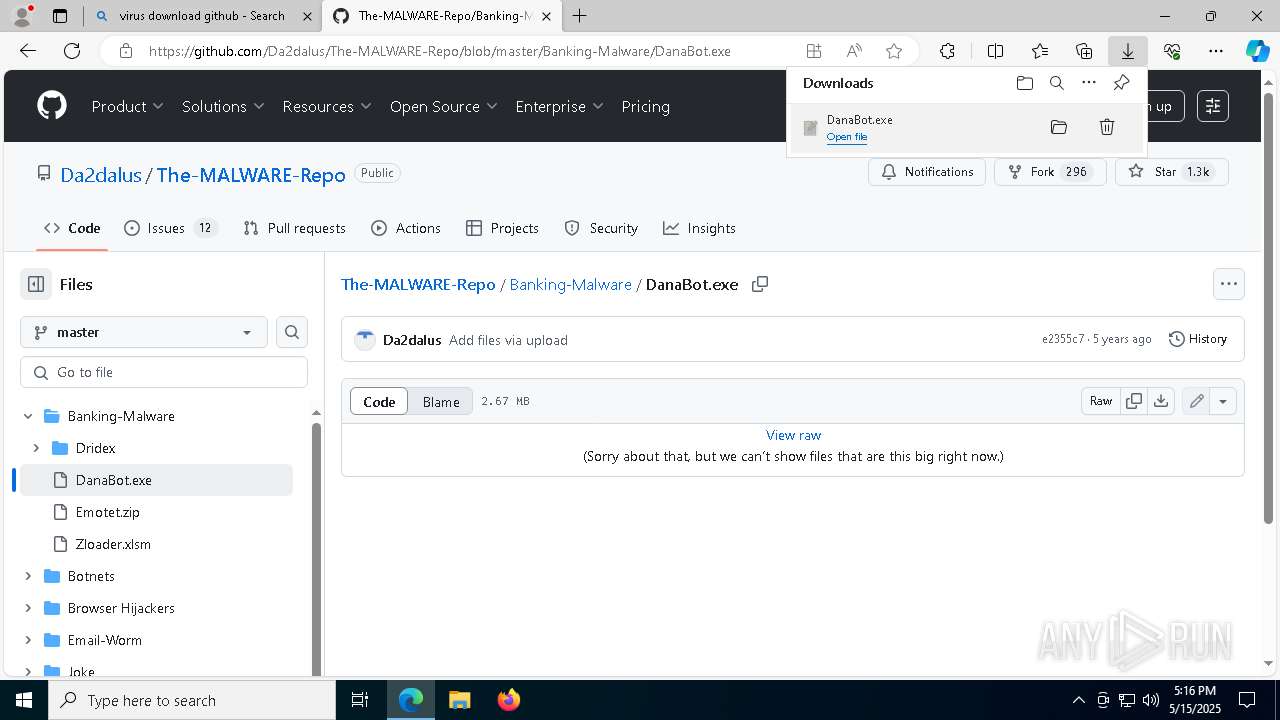
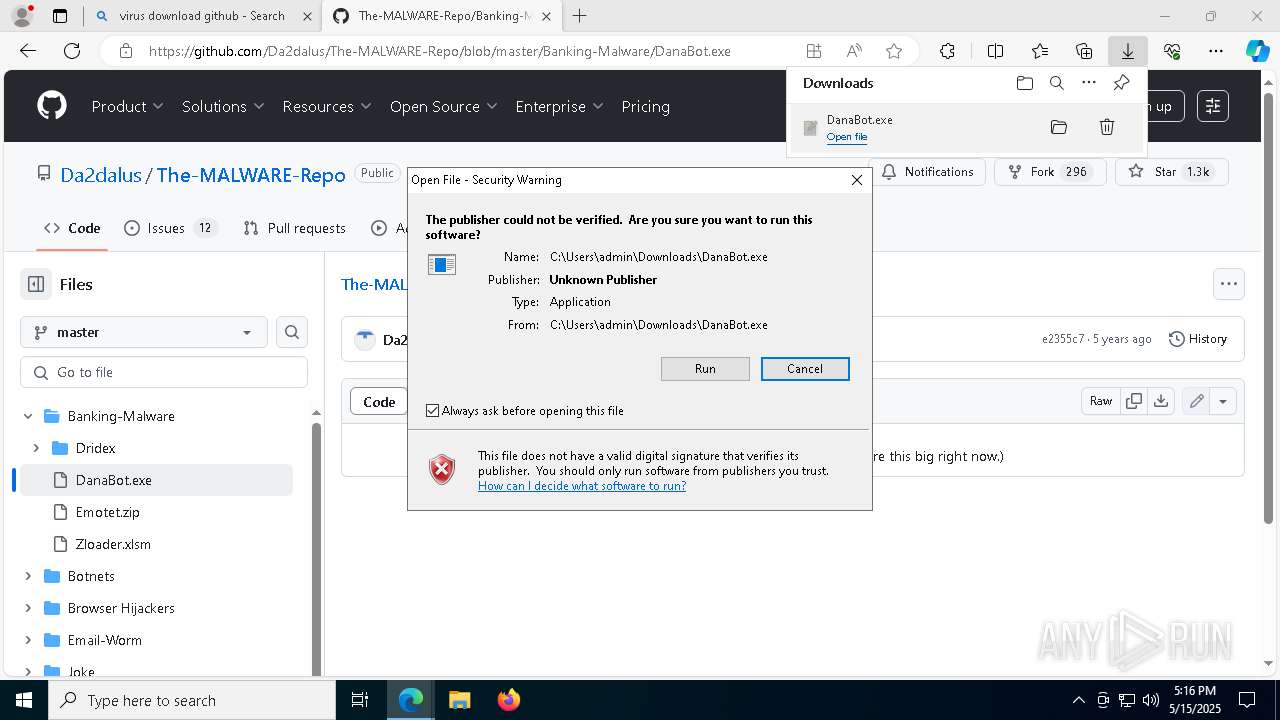
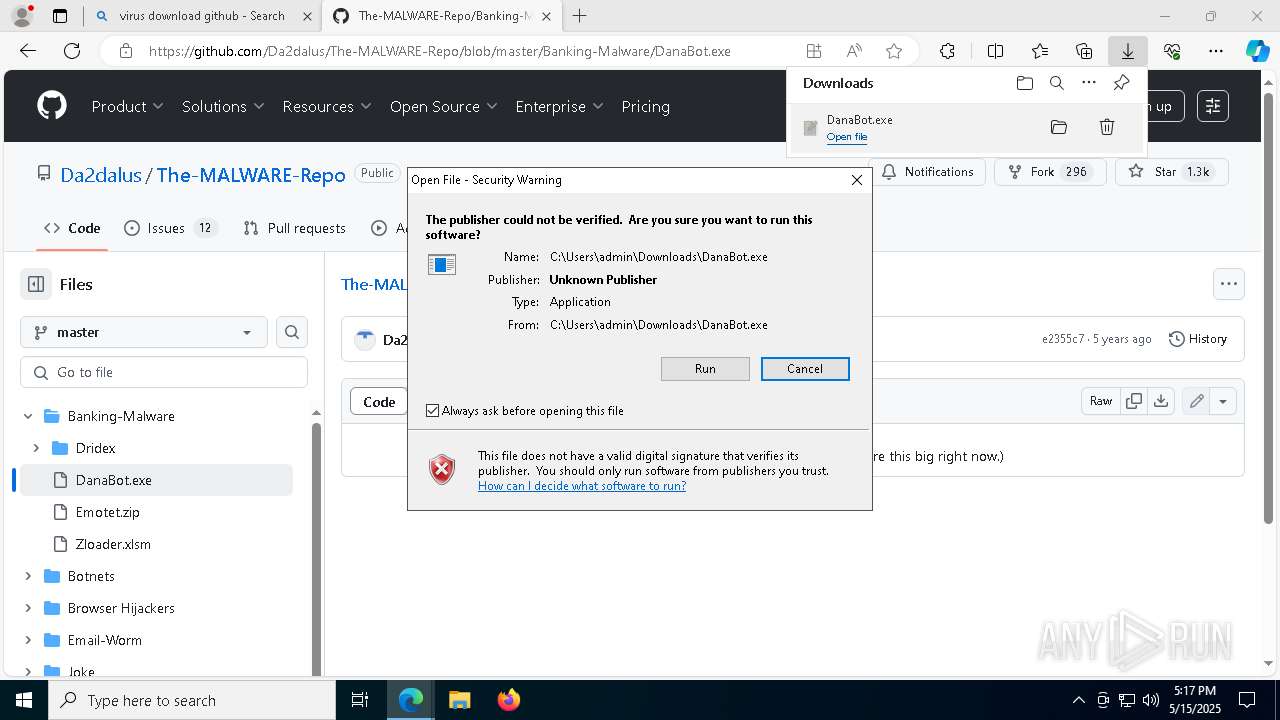
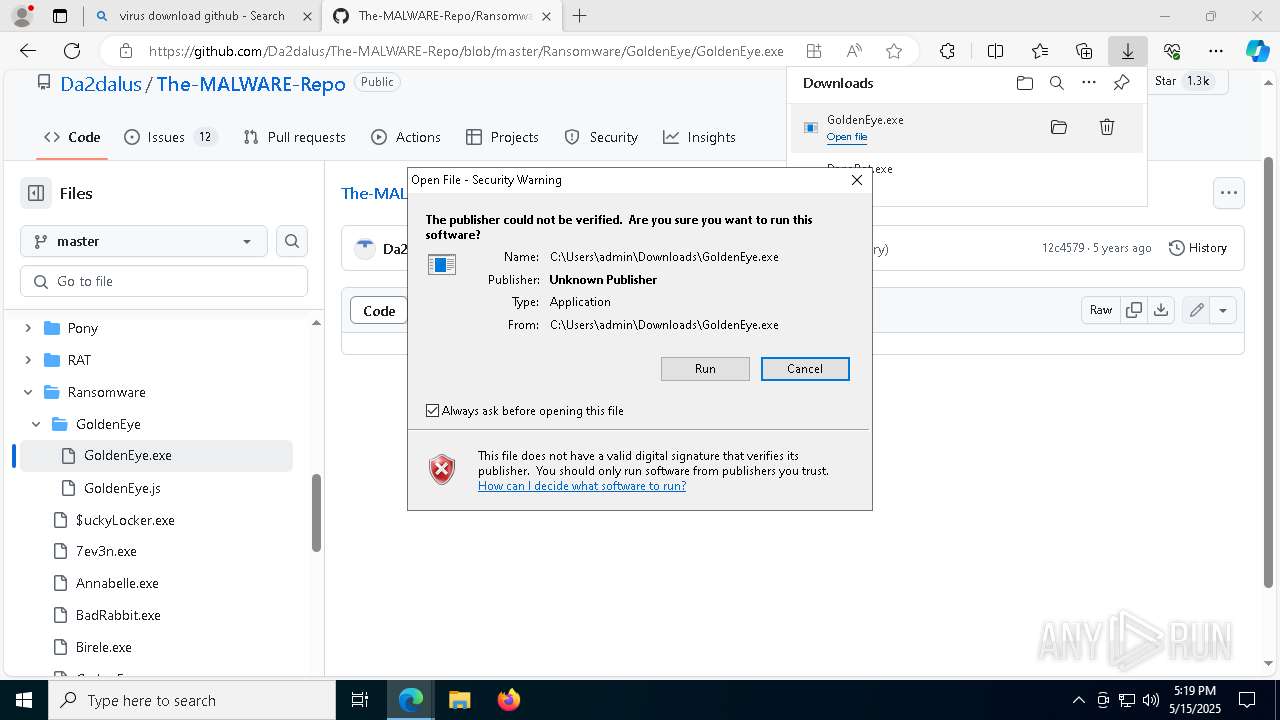
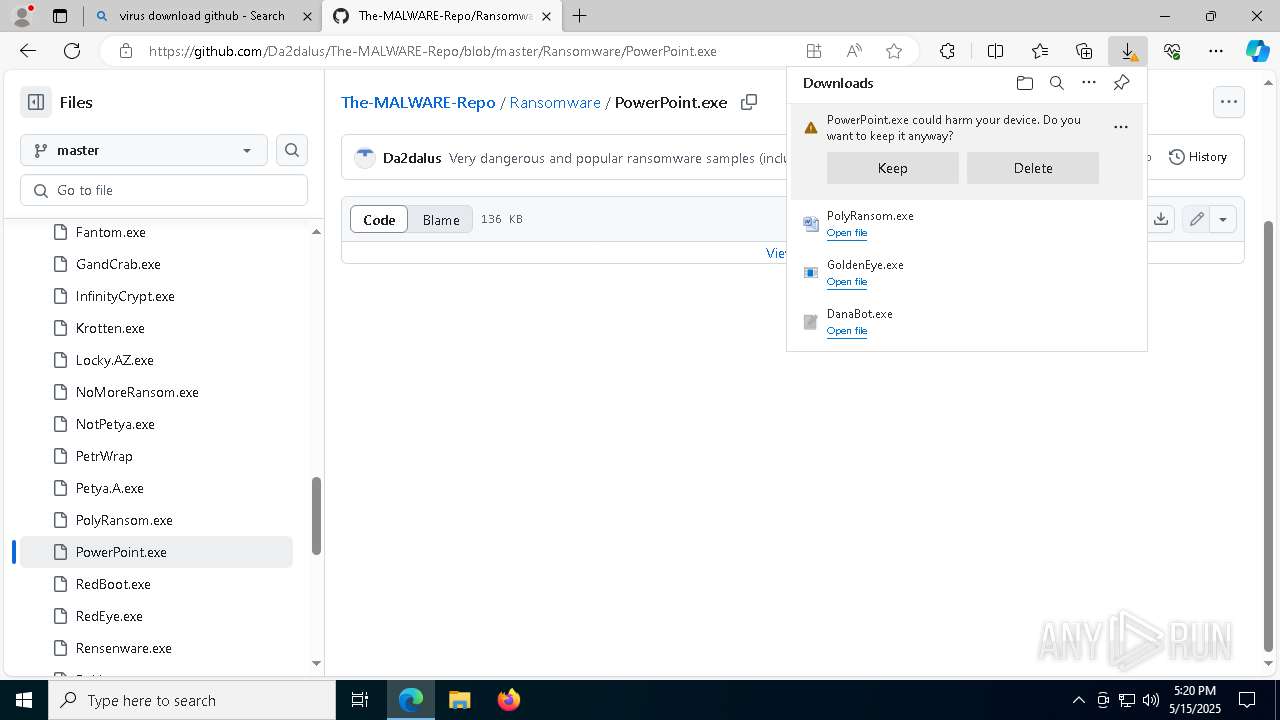
| URL: | www.youareanidioit.com |
| Full analysis: | https://app.any.run/tasks/cd641e01-9918-4183-bdc9-a2be28042a74 |
| Verdict: | Malicious activity |
| Threats: | Danabot is an advanced banking Trojan malware that was designed to steal financial information from victims. Out of the Trojans in the wild, this is one of the most advanced thanks to the modular design and a complex delivery method. |
| Analysis date: | May 15, 2025, 17:15:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C0F32397DD97E4FEADA0BD15D9AD872D |
| SHA1: | E1640B3A520FE794B370F1FC5758E088CD72FC8A |
| SHA256: | 62143675C613B5AEDF1A8422C00A9C3F47633571B1761C5DAEDD140DBB123282 |
| SSDEEP: | 3:EXQ+dpDIn:TGIn |
MALICIOUS
DANABOT has been found (auto)
- msedge.exe (PID: 1052)
- msedge.exe (PID: 5668)
Registers / Runs the DLL via REGSVR32.EXE
- DanaBot.exe (PID: 5556)
DANABOT has been detected (YARA)
- rundll32.exe (PID: 1804)
XORed URL has been found (YARA)
- SpatialAudioLicenseSrv.exe (PID: 7852)
GOLDENEYE mutex has been found
- SpatialAudioLicenseSrv.exe (PID: 7852)
Renames files like ransomware
- SpatialAudioLicenseSrv.exe (PID: 7852)
SUSPICIOUS
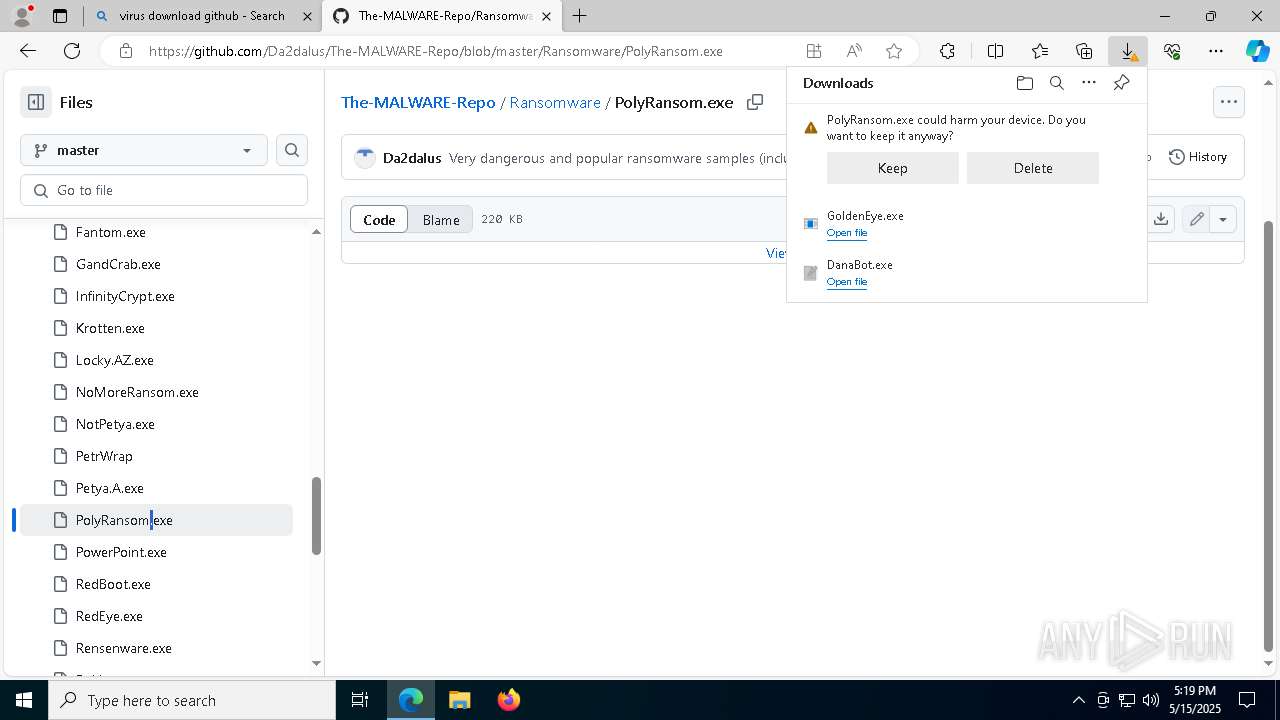
Executable content was dropped or overwritten
- DanaBot.exe (PID: 5556)
- GoldenEye.exe (PID: 7856)
- GoldenEye.exe (PID: 2104)
- PolyRansom.exe (PID: 4976)
- SwoYcckM.exe (PID: 232)
- PowerPoint.exe (PID: 1168)
Executes application which crashes
- DanaBot.exe (PID: 5556)
- DanaBot.exe (PID: 6724)
- DanaBot.exe (PID: 2504)
Cleans NTFS data stream (Zone Identifier)
- msedge.exe (PID: 5668)
There is functionality for taking screenshot (YARA)
- rundll32.exe (PID: 1804)
Process drops legitimate windows executable
- GoldenEye.exe (PID: 2104)
Starts CMD.EXE for commands execution
- PolyRansom.exe (PID: 6816)
- PolyRansom.exe (PID: 7732)
- PolyRansom.exe (PID: 4976)
- PolyRansom.exe (PID: 7756)
- PolyRansom.exe (PID: 6136)
- PolyRansom.exe (PID: 7188)
- PolyRansom.exe (PID: 7752)
- PolyRansom.exe (PID: 6268)
- PolyRansom.exe (PID: 3124)
- PolyRansom.exe (PID: 5980)
- PolyRansom.exe (PID: 4180)
- PolyRansom.exe (PID: 7360)
- PolyRansom.exe (PID: 4012)
- PolyRansom.exe (PID: 7336)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 1388)
- PolyRansom.exe (PID: 7136)
- PolyRansom.exe (PID: 1012)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 4212)
- PolyRansom.exe (PID: 2656)
- PolyRansom.exe (PID: 7644)
- PolyRansom.exe (PID: 7512)
- PolyRansom.exe (PID: 4056)
- PolyRansom.exe (PID: 5500)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 7888)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 8172)
- PolyRansom.exe (PID: 5624)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 6340)
- PolyRansom.exe (PID: 1748)
- PolyRansom.exe (PID: 6276)
- PolyRansom.exe (PID: 5600)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 7856)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 1280)
- PolyRansom.exe (PID: 4932)
- PolyRansom.exe (PID: 6852)
- PolyRansom.exe (PID: 4380)
The executable file from the user directory is run by the CMD process
- PolyRansom.exe (PID: 7732)
- PolyRansom.exe (PID: 6816)
- PolyRansom.exe (PID: 6136)
- PolyRansom.exe (PID: 7756)
- PolyRansom.exe (PID: 7188)
- PolyRansom.exe (PID: 7752)
- PolyRansom.exe (PID: 3124)
- PolyRansom.exe (PID: 4180)
- PolyRansom.exe (PID: 6268)
- PolyRansom.exe (PID: 7360)
- PolyRansom.exe (PID: 5980)
- PolyRansom.exe (PID: 4012)
- PolyRansom.exe (PID: 7336)
- PolyRansom.exe (PID: 1012)
- PolyRansom.exe (PID: 1388)
- PolyRansom.exe (PID: 7136)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 4212)
- PolyRansom.exe (PID: 2656)
- PolyRansom.exe (PID: 7644)
- PolyRansom.exe (PID: 7512)
- PolyRansom.exe (PID: 4056)
- PolyRansom.exe (PID: 5500)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 7888)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 5624)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 6276)
- PolyRansom.exe (PID: 8172)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 6340)
- PolyRansom.exe (PID: 5600)
- PolyRansom.exe (PID: 1748)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 7856)
- PolyRansom.exe (PID: 6852)
- PolyRansom.exe (PID: 4932)
- PolyRansom.exe (PID: 1280)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 4380)
- PolyRansom.exe (PID: 5592)
Uses REG/REGEDIT.EXE to modify registry
- PolyRansom.exe (PID: 4976)
- PolyRansom.exe (PID: 7732)
- PolyRansom.exe (PID: 6816)
- PolyRansom.exe (PID: 6136)
- PolyRansom.exe (PID: 7756)
- PolyRansom.exe (PID: 6268)
- PolyRansom.exe (PID: 3124)
- PolyRansom.exe (PID: 7188)
- PolyRansom.exe (PID: 7752)
- PolyRansom.exe (PID: 5980)
- PolyRansom.exe (PID: 4180)
- PolyRansom.exe (PID: 7336)
- PolyRansom.exe (PID: 7360)
- PolyRansom.exe (PID: 4012)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 1388)
- PolyRansom.exe (PID: 7136)
- PolyRansom.exe (PID: 1012)
- PolyRansom.exe (PID: 4212)
- PolyRansom.exe (PID: 7644)
- PolyRansom.exe (PID: 2656)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 7512)
- PolyRansom.exe (PID: 4056)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 7888)
- PolyRansom.exe (PID: 5500)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 8172)
- PolyRansom.exe (PID: 5624)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 6340)
- PolyRansom.exe (PID: 1748)
- PolyRansom.exe (PID: 6276)
- PolyRansom.exe (PID: 7856)
- PolyRansom.exe (PID: 5600)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 1280)
- PolyRansom.exe (PID: 6852)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 4932)
- PolyRansom.exe (PID: 4380)
Executing commands from a ".bat" file
- PolyRansom.exe (PID: 4976)
- PolyRansom.exe (PID: 7732)
- PolyRansom.exe (PID: 6136)
- PolyRansom.exe (PID: 7756)
- PolyRansom.exe (PID: 6816)
- PolyRansom.exe (PID: 7752)
- PolyRansom.exe (PID: 6268)
- PolyRansom.exe (PID: 7188)
- PolyRansom.exe (PID: 4180)
- PolyRansom.exe (PID: 3124)
- PolyRansom.exe (PID: 5980)
- PolyRansom.exe (PID: 7360)
- PolyRansom.exe (PID: 7336)
- PolyRansom.exe (PID: 4012)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 1388)
- PolyRansom.exe (PID: 7136)
- PolyRansom.exe (PID: 1012)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 4212)
- PolyRansom.exe (PID: 2656)
- PolyRansom.exe (PID: 7644)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 7512)
- PolyRansom.exe (PID: 4056)
- PolyRansom.exe (PID: 5500)
- PolyRansom.exe (PID: 4980)
- PolyRansom.exe (PID: 4028)
- PolyRansom.exe (PID: 7888)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 8172)
- PolyRansom.exe (PID: 5624)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 6276)
- PolyRansom.exe (PID: 6416)
- PolyRansom.exe (PID: 6340)
- PolyRansom.exe (PID: 5600)
- PolyRansom.exe (PID: 7356)
- PolyRansom.exe (PID: 7856)
- PolyRansom.exe (PID: 1748)
- PolyRansom.exe (PID: 6240)
- PolyRansom.exe (PID: 1280)
- PolyRansom.exe (PID: 6852)
- PolyRansom.exe (PID: 4932)
- PolyRansom.exe (PID: 4380)
The process executes VB scripts
- cmd.exe (PID: 7760)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 7532)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 7788)
- cmd.exe (PID: 1704)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 7692)
- cmd.exe (PID: 2192)
- cmd.exe (PID: 7244)
- cmd.exe (PID: 2840)
- cmd.exe (PID: 900)
- cmd.exe (PID: 6740)
- cmd.exe (PID: 7716)
- cmd.exe (PID: 4220)
- cmd.exe (PID: 300)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 7740)
- cmd.exe (PID: 7904)
- cmd.exe (PID: 8032)
- cmd.exe (PID: 7012)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 6816)
- cmd.exe (PID: 7900)
- cmd.exe (PID: 6240)
- cmd.exe (PID: 7136)
- cmd.exe (PID: 1852)
- cmd.exe (PID: 4884)
- cmd.exe (PID: 7720)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 616)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 6004)
- cmd.exe (PID: 6468)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 6340)
- cmd.exe (PID: 5232)
- cmd.exe (PID: 7692)
- cmd.exe (PID: 4784)
- cmd.exe (PID: 6416)
Connects to unusual port
- SwoYcckM.exe (PID: 232)
- XWAQAQUE.exe (PID: 8076)
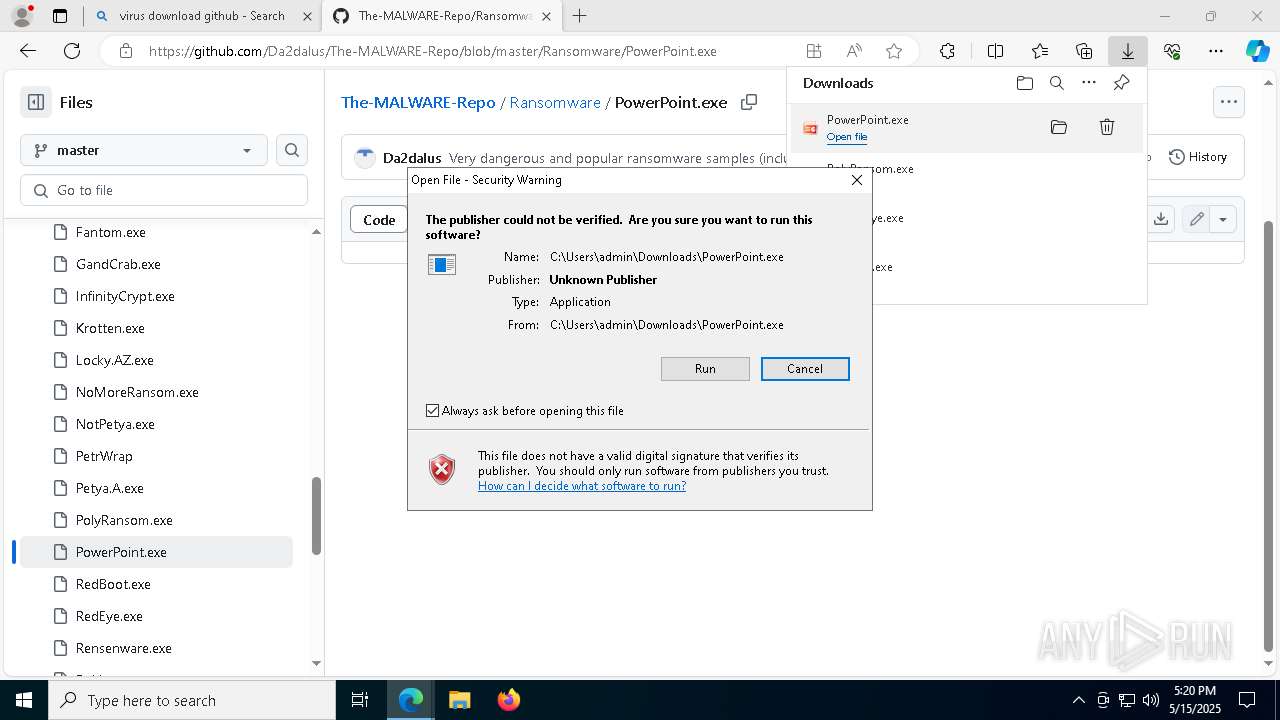
Application launched itself
- PowerPoint.exe (PID: 7864)
Starts itself from another location
- PowerPoint.exe (PID: 1168)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4116)
INFO
Checks supported languages
- identity_helper.exe (PID: 8184)
- DanaBot.exe (PID: 5556)
- DanaBot.exe (PID: 6724)
- GoldenEye.exe (PID: 7856)
- DanaBot.exe (PID: 2504)
- SpatialAudioLicenseSrv.exe (PID: 7852)
Reads Environment values
- identity_helper.exe (PID: 8184)
Reads the computer name
- identity_helper.exe (PID: 8184)
- GoldenEye.exe (PID: 7856)
Application launched itself
- msedge.exe (PID: 5668)
Executable content was dropped or overwritten
- msedge.exe (PID: 1052)
- msedge.exe (PID: 5668)
- msedge.exe (PID: 4284)
Reads the machine GUID from the registry
- DanaBot.exe (PID: 5556)
- GoldenEye.exe (PID: 7856)
- SpatialAudioLicenseSrv.exe (PID: 7852)
Creates files in the program directory
- regsvr32.exe (PID: 8188)
Checks proxy server information
- rundll32.exe (PID: 1804)
- slui.exe (PID: 7964)
Reads the software policy settings
- slui.exe (PID: 7748)
- slui.exe (PID: 7964)
Creates files or folders in the user directory
- WerFault.exe (PID: 2340)
- WerFault.exe (PID: 5408)
- WerFault.exe (PID: 4304)
- GoldenEye.exe (PID: 7856)
The sample compiled with english language support
- msedge.exe (PID: 4284)
- GoldenEye.exe (PID: 2104)
Compiled with Borland Delphi (YARA)
- rundll32.exe (PID: 1804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(7852) SpatialAudioLicenseSrv.exe
Decrypted-URLs (1)https://www.torproject.org/
Total processes
887
Monitored processes
633
Malicious processes
53
Suspicious processes
16
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=64 --mojo-platform-channel-handle=8552 --field-trial-handle=2344,i,13211135751094144211,16749695142377252014,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 232 | "C:\Users\admin\lEMYkwoU\SwoYcckM.exe" | C:\Users\admin\lEMYkwoU\SwoYcckM.exe | PolyRansom.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 236 | reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /d 0 /t REG_DWORD /f | C:\Windows\SysWOW64\reg.exe | — | PolyRansom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced /f /v Hidden /t REG_DWORD /d 2 | C:\Windows\SysWOW64\reg.exe | — | PolyRansom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | cscript C:\Users\admin\AppData\Local\Temp/file.vbs | C:\Windows\SysWOW64\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 300 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\GQgsUcUc.bat" "C:\Users\admin\Downloads\PolyRansom.exe"" | C:\Windows\SysWOW64\cmd.exe | — | PolyRansom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\Downloads\PolyRansom" | C:\Windows\SysWOW64\cmd.exe | — | PolyRansom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 444 | cscript C:\Users\admin\AppData\Local\Temp/file.vbs | C:\Windows\SysWOW64\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
44 046
Read events
43 977
Write events
69
Delete events
0
Modification events
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 6C1B2D1AC6932F00 | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 9867361AC6932F00 | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459426 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {928BF708-5F0F-4FDA-A18F-125930B51613} | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459426 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3EADCB05-E7D7-4D3F-95DA-E225E32CA82E} | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (5668) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\Profiles |
| Operation: | write | Name: | EnhancedLinkOpeningDefault |
Value: Default | |||
Executable files
79
Suspicious files
2 358
Text files
242
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10bcab.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10bcab.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10bcba.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10bcba.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10bcd9.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
165
DNS requests
193
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7876 | svchost.exe | HEAD | 200 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747703938&P2=404&P3=2&P4=bfBFDC7qg8ABF3lRuU8F4N5ll7jJ%2fMlLdssY2L9f7%2bAHo1lwOaF7WdIHmlx8eZfkshSSwJvZKYy7vmyIB%2f4Kfg%3d%3d | unknown | — | — | whitelisted |
7876 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747703938&P2=404&P3=2&P4=bfBFDC7qg8ABF3lRuU8F4N5ll7jJ%2fMlLdssY2L9f7%2bAHo1lwOaF7WdIHmlx8eZfkshSSwJvZKYy7vmyIB%2f4Kfg%3d%3d | unknown | — | — | whitelisted |
4756 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7876 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747703938&P2=404&P3=2&P4=bfBFDC7qg8ABF3lRuU8F4N5ll7jJ%2fMlLdssY2L9f7%2bAHo1lwOaF7WdIHmlx8eZfkshSSwJvZKYy7vmyIB%2f4Kfg%3d%3d | unknown | — | — | whitelisted |
4756 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7876 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747703938&P2=404&P3=2&P4=bfBFDC7qg8ABF3lRuU8F4N5ll7jJ%2fMlLdssY2L9f7%2bAHo1lwOaF7WdIHmlx8eZfkshSSwJvZKYy7vmyIB%2f4Kfg%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7876 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747703938&P2=404&P3=2&P4=bfBFDC7qg8ABF3lRuU8F4N5ll7jJ%2fMlLdssY2L9f7%2bAHo1lwOaF7WdIHmlx8eZfkshSSwJvZKYy7vmyIB%2f4Kfg%3d%3d | unknown | — | — | whitelisted |
7876 | svchost.exe | GET | 206 | 208.89.74.21:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747703938&P2=404&P3=2&P4=bfBFDC7qg8ABF3lRuU8F4N5ll7jJ%2fMlLdssY2L9f7%2bAHo1lwOaF7WdIHmlx8eZfkshSSwJvZKYy7vmyIB%2f4Kfg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5668 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1052 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1052 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1052 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1052 | msedge.exe | 13.107.253.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.youareanidioit.com |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1052 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
8076 | XWAQAQUE.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |
8076 | XWAQAQUE.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |
8076 | XWAQAQUE.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Possible automated connectivity check (www.google.com) |