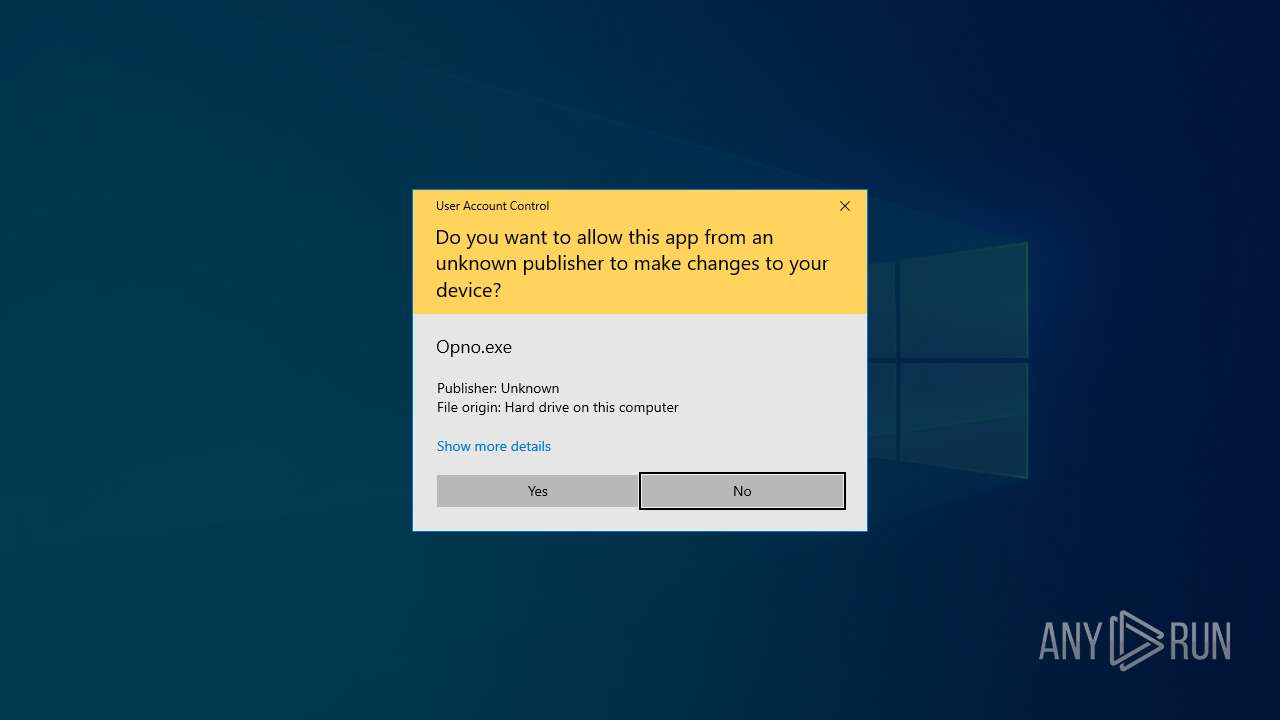
| File name: | Opno.exe |
| Full analysis: | https://app.any.run/tasks/40261bd0-45b4-417f-a000-1d38466715a4 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | April 21, 2025, 16:58:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | B9331FFD9C08CD1A0344CDD14484052A |
| SHA1: | 75DD61AA9FE2392E8F1F7942C5154843427F03F8 |
| SHA256: | 61F304797E8F464EAE5906E327EC0120142EF95AE048F96D3D799EF444CA3882 |
| SSDEEP: | 98304:CCYzBRvab/ncfRkzKVfq7AnYRO4Y6ZhkDQet54netUjZUj0vYtHfktEzafhOsE+L:CvfknrZYewE1MUQ881mwe/ki5BIwA |
MALICIOUS
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 7736)
RUSTDESK has been detected (SURICATA)
- svchost.exe (PID: 2192)
- svchost.exe (PID: 2148)
SUSPICIOUS
Starts a Microsoft application from unusual location
- Opno.exe (PID: 1280)
- Opno.exe (PID: 7440)
- Opno.exe (PID: 7544)
Process drops legitimate windows executable
- Opno.exe (PID: 7440)
- Opno.exe (PID: 7544)
- rustdesk.exe (PID: 6584)
Process drops python dynamic module
- Opno.exe (PID: 7440)
- netpolicy.exe (PID: 4188)
- netpolicy.exe (PID: 2792)
Executable content was dropped or overwritten
- Opno.exe (PID: 7440)
- Opno.exe (PID: 7544)
- netpolicy.exe (PID: 4188)
- rustdesk.exe (PID: 6584)
- netpolicy.exe (PID: 6524)
- netpolicy.exe (PID: 2792)
Loads Python modules
- Opno.exe (PID: 7544)
- netpolicy.exe (PID: 6524)
- netpolicy.exe (PID: 6664)
The process drops C-runtime libraries
- Opno.exe (PID: 7440)
- netpolicy.exe (PID: 4188)
- netpolicy.exe (PID: 2792)
Application launched itself
- Opno.exe (PID: 7440)
- netpolicy.exe (PID: 4188)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6960)
- netpolicy.exe (PID: 2792)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6888)
Starts CMD.EXE for commands execution
- Opno.exe (PID: 7544)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
The system shut down or reboot
- cmd.exe (PID: 7828)
The process executes via Task Scheduler
- netpolicy.exe (PID: 4188)
- PLUGScheduler.exe (PID: 4180)
- PLUGScheduler.exe (PID: 3940)
- netpolicy.exe (PID: 2792)
Reads the date of Windows installation
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6704)
Uses ICACLS.EXE to modify access control lists
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
Reads security settings of Internet Explorer
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
Reads the Windows owner or organization settings
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6704)
Uses TASKKILL.EXE to kill process
- rustdesk.exe (PID: 6584)
- cmd.exe (PID: 7044)
- cmd.exe (PID: 6996)
Adds/modifies Windows certificates
- rustdesk.exe (PID: 6772)
Connects to unusual port
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
The process checks if it is being run in the virtual environment
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1376)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 2444)
- cmd.exe (PID: 6448)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 5280)
- cmd.exe (PID: 6420)
- cmd.exe (PID: 6396)
- cmd.exe (PID: 1720)
- cmd.exe (PID: 6884)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 3052)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 4300)
- cmd.exe (PID: 5388)
- cmd.exe (PID: 1996)
- cmd.exe (PID: 2468)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 6436)
- cmd.exe (PID: 6184)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 6996)
- cmd.exe (PID: 6184)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 1140)
- cmd.exe (PID: 4380)
- cmd.exe (PID: 6568)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 4548)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 5808)
- cmd.exe (PID: 3348)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 5264)
- cmd.exe (PID: 2308)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 7156)
- cmd.exe (PID: 4384)
- cmd.exe (PID: 1976)
- cmd.exe (PID: 4400)
- cmd.exe (PID: 2848)
- cmd.exe (PID: 2712)
- cmd.exe (PID: 2848)
- cmd.exe (PID: 6788)
- cmd.exe (PID: 3348)
- cmd.exe (PID: 72)
- cmd.exe (PID: 5116)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 6104)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 3616)
- cmd.exe (PID: 5288)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 5748)
- cmd.exe (PID: 7164)
- cmd.exe (PID: 4740)
- cmd.exe (PID: 4396)
- cmd.exe (PID: 1720)
- cmd.exe (PID: 6784)
- cmd.exe (PID: 2100)
- cmd.exe (PID: 4568)
Get information on the list of running processes
- rustdesk.exe (PID: 6772)
- cmd.exe (PID: 6448)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 1376)
- cmd.exe (PID: 2444)
- cmd.exe (PID: 2780)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 6980)
- cmd.exe (PID: 5280)
- cmd.exe (PID: 6420)
- cmd.exe (PID: 6396)
- cmd.exe (PID: 1720)
- cmd.exe (PID: 1040)
- cmd.exe (PID: 3052)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 6884)
- cmd.exe (PID: 4300)
- cmd.exe (PID: 5388)
- cmd.exe (PID: 1996)
- cmd.exe (PID: 1196)
- cmd.exe (PID: 2468)
- cmd.exe (PID: 6184)
- rustdesk.exe (PID: 6772)
- cmd.exe (PID: 6436)
- cmd.exe (PID: 4548)
- cmd.exe (PID: 6996)
- cmd.exe (PID: 4776)
- cmd.exe (PID: 1140)
- cmd.exe (PID: 6184)
- cmd.exe (PID: 4380)
- cmd.exe (PID: 6568)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 2680)
- cmd.exe (PID: 2620)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 4920)
- cmd.exe (PID: 5264)
- cmd.exe (PID: 2308)
- cmd.exe (PID: 4400)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 5808)
- cmd.exe (PID: 3348)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 2072)
- cmd.exe (PID: 7156)
- cmd.exe (PID: 4384)
- cmd.exe (PID: 1976)
- cmd.exe (PID: 6104)
- cmd.exe (PID: 2848)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 6788)
- cmd.exe (PID: 3348)
- cmd.exe (PID: 72)
- cmd.exe (PID: 5116)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 2712)
- cmd.exe (PID: 2848)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 3616)
- cmd.exe (PID: 5288)
- cmd.exe (PID: 5260)
- cmd.exe (PID: 5748)
- cmd.exe (PID: 7164)
- cmd.exe (PID: 4740)
- cmd.exe (PID: 7140)
- cmd.exe (PID: 4396)
- cmd.exe (PID: 6784)
- cmd.exe (PID: 2100)
- cmd.exe (PID: 4568)
- cmd.exe (PID: 1720)
INFO
Create files in a temporary directory
- Opno.exe (PID: 7440)
- netpolicy.exe (PID: 4188)
- rustdesk.exe (PID: 6584)
- rustdesk.exe (PID: 6772)
- netpolicy.exe (PID: 2792)
- rustdesk.exe (PID: 6772)
Reads the computer name
- Opno.exe (PID: 7440)
- Opno.exe (PID: 7544)
- rustdesk.exe (PID: 6584)
- PLUGScheduler.exe (PID: 4180)
- rustdesk.exe (PID: 6960)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 7088)
- rustdesk.exe (PID: 5184)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- PLUGScheduler.exe (PID: 3940)
- rustdesk.exe (PID: 6888)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 3944)
- rustdesk.exe (PID: 7056)
- rustdesk.exe (PID: 6704)
Checks supported languages
- Opno.exe (PID: 7440)
- Opno.exe (PID: 7544)
- PLUGScheduler.exe (PID: 4180)
- rustdesk.exe (PID: 6584)
- rustdesk.exe (PID: 6960)
- rustdesk.exe (PID: 7088)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 5184)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- PLUGScheduler.exe (PID: 3940)
- rustdesk.exe (PID: 6692)
- rustdesk.exe (PID: 6888)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 3944)
- rustdesk.exe (PID: 7056)
- rustdesk.exe (PID: 6704)
The sample compiled with english language support
- Opno.exe (PID: 7440)
- netpolicy.exe (PID: 4188)
- Opno.exe (PID: 7544)
- rustdesk.exe (PID: 6584)
- netpolicy.exe (PID: 6524)
- netpolicy.exe (PID: 2792)
Checks proxy server information
- Opno.exe (PID: 7544)
- netpolicy.exe (PID: 6524)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
- netpolicy.exe (PID: 6664)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4180)
- rustdesk.exe (PID: 6772)
- PLUGScheduler.exe (PID: 3940)
Creates files or folders in the user directory
- rustdesk.exe (PID: 6584)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6960)
- rustdesk.exe (PID: 7088)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6888)
- rustdesk.exe (PID: 7056)
- rustdesk.exe (PID: 6704)
Reads security settings of Internet Explorer
- RuntimeBroker.exe (PID: 5228)
- RuntimeBroker.exe (PID: 5528)
- RuntimeBroker.exe (PID: 4164)
- RuntimeBroker.exe (PID: 5332)
- RuntimeBroker.exe (PID: 4152)
Process checks computer location settings
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
Reads the machine GUID from the registry
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6704)
Reads product name
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6704)
Reads Windows Product ID
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6704)
Reads Environment values
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 856)
- rustdesk.exe (PID: 2588)
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6704)
Reads the software policy settings
- rustdesk.exe (PID: 6772)
- rustdesk.exe (PID: 6772)
Local mutex for internet shortcut management
- RuntimeBroker.exe (PID: 5332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:21 09:44:23+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 173568 |
| InitializedDataSize: | 95232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xce30 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.0.19041.5553 |
| ProductVersionNumber: | 10.0.19041.5553 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Network Policy Configuration Utility |
| FileVersion: | 10.0.19041.5553 (WinBuild.160101.0800) |
| InternalName: | netpolicy |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | netpolicy.exe |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 10.0.19041.5553 |
Total processes
718
Monitored processes
335
Malicious processes
12
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 72 | "cmd" /C "tasklist | findstr consent.exe" | C:\Windows\System32\cmd.exe | — | rustdesk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 428 | findstr consent.exe | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 544 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | findstr consent.exe | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 652 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | findstr consent.exe | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 824 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\rustdesk\.\rustdesk.exe" --cm | C:\Users\admin\AppData\Local\rustdesk\rustdesk.exe | — | rustdesk.exe | |||||||||||
User: admin Company: Purslane Ltd Integrity Level: HIGH Description: RustDesk Remote Desktop Exit code: 0 Version: 1.3.9+57 Modules
| |||||||||||||||
| 884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 943
Read events
38 925
Write events
16
Delete events
2
Modification events
| (PID) Process: | (5228) RuntimeBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\Subscriptions\338388 |
| Operation: | write | Name: | LastAccessed |
Value: 5FC3A8CFDEB2DB01 | |||
| (PID) Process: | (5228) RuntimeBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\Subscriptions\314559 |
| Operation: | write | Name: | LastAccessed |
Value: 5FC3A8CFDEB2DB01 | |||
| (PID) Process: | (5528) RuntimeBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\S-1-15-2-536077884-713174666-1066051701-3219990555-339840825-1966734348-1611281757 |
| Operation: | write | Name: | DeviceTicket |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB01000000E73178C5C247454B9C491C089CDB64D300000000020000000000106600000001000020000000E903032E22A7558D7D01F1433DC85E349EB7547CA924935A8A9DC10F914C2A96000000000E8000000002000020000000D3FA61EB2110B15264D1ADAE634AE36C6E577C6443DC4C7D8F2C661950DF071FD00A0000AB44FE2ADA2552E75ACDD22D1A71D70CB1EC2B3374496248E9C1BD0C232E4B1DFA49A6E7A0BC5B34E74499ECEE6899F17C3AF53FF13A0100AD99383253E9F0E5FD43E86FFE9921847CAC6B0A30ACF8F4DF1F4CC520496ED2115776B5B36C2156E468B5CA328D0C216B77A6D65FF3173A72DB6C2423CBAAEE03777F51A4BCC959633CE3A3D50F4E3705A661E9E05E417EB088B696446424805F106D0C1276958AB10C7DE8232640B023A2B16AAA4DF74665B04C693AD6BA28EE4FCBA8E93BDE4AEFF363842836C751C18BCFD41E0450F5EACA5A5805FF91763AF9E577D890C2A184F4378E188C323574A02BE152D7B6BFFE0CC19C47C0A69A1074ED318CD973C9EAF3B94E0FE84F4E8116632D6BFB4091F0509577C91E6C808979BC542339708651C9A11DB7D680DA1EFB9E1B760CC3320A12FBB23969E6FE3DC80E19AC3505C602D6CAC9BEE9F21B89AA1392AFE40A1BA77328C35EFD8209339DC857CD8986060867C427CD56B1D7B585819A0315AD1F602278D348CB8ACA4433A7EE6593BC24AA7C58BAB6D6C61DE644B9172F70C8ADA484EB85F888397555B5B6E057B0A7A7AA93A6F4E650DEE467BFC509C19FA50E91A098027C8AEA73CDF77B6E68695CDBE6E6780F9A3F2C3BBBDB19FC1BE74D4D74F5D9EE5C0B7CFDE37883F52AFCDD43B56E1536DAA8FA734453AD94334842E064D9C979036DA903FCFE0020EDB3EFAE04DD3A447574B84134232D63BCC5E1697D99D20A93BE60FF2ED9E6E5474E6983C69EF40AD17C7DB17EED4AB1BF31DE426A57D95A1AE5313C75AB0E910EDFAAA4AC44C5D66D940D2EFCDE9722D3E87010D3DB3221419B3C7D77ABD4ACAACCEBC0181627F4E75AC3CA24124A260773BF71F15941025545E6001D9D3E207B544A86AEB90BC88066AA68831E25EF871BAF37BFD78CC2CF0936FC2976F7E0A89E9715B758618A6E6565B594F98F18EC2DBC8932964BCEC7A17C9A7FD1CF7F7C82A294DEBFF4504CD48BDACFD9D80CE786C5C8A8446F6B97685A7D9C13C4A10AA048312ECEF64BDF7C4D1FFE961820B244EA3E091CA032F2784C394A6E18006D09F5A5B148E0F78C1E271477CE04A7AE4A515ED8DE4B24A8C791496F3E1F5E097DC01B49FCABBF6244F4942784F80DFF8E9F6B301EA0B6F35509949255E59895F5B097ACF6B47CADEB6E44710A8A56D064F689BE8F8013D0C292D0C1097053D7521071C1AE546D9C9CE9116273C7367A0A4D509226EDDE051D3454DEB59E7A669222EF56306C51ED5C2A06A7DC73C44D149D52E3412945572C0086A29D6E43796081D711595195F1B83952867105B0AAF0CF69E4CF7CB5EC4A8704E68A4B6946675F9B049BB5E0C2CF92486A31968A7E4C14FF3B2D01D88D59F61997D459829CDC1580B052A12A77BBF85C39D06DD9321B9A3FD7558B1DFA44A203A9C920EE69D2C048066000710C23ACA9A2667DD78AC6EBF559EBEFBB78CC1C7E2B46AFDC1505392C403A443115A1E7CAB760D9034E2B229F35D5BD41A15B3F02A593C266149E4C7B7872661328A48DA9551BA31DA461B53C06E4847D704288F1EBB6F270EA9135F2DF3223C2E2F36FAD0ADF94B6398710D1821220BE9AFBB469A895EF360B097B60681FE9E0B3E81C77B8EED9CDA4367783E1CE1BFC1BDD9138DD404C791F62A3495B59E259C0ECEBA322982F45309D20211C7FE92EBC455081AA0FE8155FC925C640FB5CA594D8A8F1DD6AF9A72F8BFFB2CD44A750FBEF2E47860E0041652508B38239FACE0E5BC9BA57C740C8548B9F274F781CD6D542A72ADD34402AD21003071CAC4D4F2CB055663CC18A9F00AFB67B7A644088DA794DE53A37CA143EBA987AB9F2D1C60A1F8F3E62DE7DFFE5D58A3033049D9BCE23F78C8BBA471566C00F51B8A6D33906273E4CF3111B2D7BAC1F65662BC477C6474C8BD1F1FDF396B5F15901B72204F3069D6F8DE8DAA1C739BFDA023F66694989C73EDE384574C1375B91E594F964D9EAFB1EAED2C417E5B8730786FEE1044FA06F198BBC0DD41B03835E9BD2F40F43EEAFB3A9BA32B38E6577D93A897B595095B45101E2680514E7D8BDD777C7F6BDD791AE58A3FCD6CF034EE2A236CC16E7D55083D513EAE3045D74C911B28113A6F3FA893970F8A109BCEC53A3FBA7D40D925639F189AEE8B80373F6F4B65236A06492066509CC05A993FFDDBD00410F34D44D14441EF6B218F3A580DCE91D1700EF42F9A180AC9E0D4C3DF0F3BB2A01E2926DA14663F74790880FDCEA2AC50C457B767310CF69FADE38639AF8D24958EAC208413C69790B86AB5EF7B109DFBF0FF9717ED2887E4A7452AB88F6792532298F0D0342124EA7E2FDBD26E8868444B61162CA7E9C180A9E4CFE3D6BC3CA6EF800C49CDE801C2CB749A7700D8F2EC0B14F9E27176B82F79B23C2158944FB72799B0121085E5664DA00D8FE5364DAA228BACC9817DA298702094612AD338CB6E99AB7AA240481BB737F59FC2C4E7C0090A862CA061385A2FCCD435C1E67B0C2AAF78E06E72EE868D2D8F569659B43817C4C6F247B2FBFD28DEA763163BCFB7B5B507D0FDF284525F4D1E42D8A86DA5E9089506DE7C00BBB32E143201E3BC0FFB285FECF184C4C5307A39BA2CD935DCC7154C390295012CD679F6E69F40F7D02FC9E7CF0C9976F60C04E8FC54B6AFEBB29D7F16A75F2762CF995109C35C3A8EE1226E917EE2955A53FD60C0649C796FC14DD96865D2FE7DA6EE42565B584BE8FF192BC1CF17EEB0F8D293A4FF6D9A6AD20AE731E5CC01EB4BCF4F45D90038888983B430368C72AB315D60204778ADF0DBEF20723B5BC91D35AE8DE6F62C0C5B6D8DAE2A5356222154070A4438871A681BC481D8F0E2A7256210CBF30364B7762B494AA2C1B29DD89724C1D96E36EBA7045570676587699CB66F9EAAFEAAD0CC835403637EA287B9CEC98252122566B2ED7765E9E18E296D8D460F105ED430E96F35BD1B29DF0127188074A99390905AE361A4ACC400122EC2EF0F4262E7037ACEC8E7CB437323B14DF6687602C4B638C095D37FC5995E22CB75E398973A24DFC6EBA8EB0C5541005CB47A15CF99FF446FE0450771C121237013D7CF1A4C69FCD69BDFB26DAEEFD5841BC303488CE2AB0AB12A00D0871110A2ED0A5E1E331ACE563E4CAC53FF9EBB1B3A5BBEA2D25A63A4AA1AFF474E21AC02D591E9CD629E6B46B153C9ADBC7AC8CB2C34C98D3E9451BB6E723BA34D8B31114E9B08DEC78AF4DB46A83F618FE78CBB7557529D90A28227593CD00C758D97477112C2D95578C2E1759BF59971424637BFC7E5CE921BEDA399EC76E59EA14059FE659D5736508301E10AD6D8CEA2C6E4C0502160B09D523C6F6A4DB7BB7B232B93710C57A8802EF7052805D887107C2FDF276CCCB2CB8B761A77B6B994EE41A2218760BD5A28A096A7A45FCD9E649D53E5B0EE39B37FB8B1877FF10E686D33C5714522F8A7879466263B71F797CD8AD0A55BFB0088D4885D3E5B11A0F11B34F05823C2DA0F65B216F2D6B3D7D5A89C53A61734057F90F466094B1BA0EDAD56477EB5799ECC27378662B0F735D682FDB0029D184A30961B8A6EBD400B9FC77A846536BCF98B02C8536CDC6194C8BDB71FCB339C321B2C6D80369321C3A0AF7AECC7C2B412A9C106E9EAC16C1A5C17AD1D720CC6A34C76845A977DC69C8F02E95C8399A802AD45A41D0CE55B98E1D61D80B3314BBA871C7C3C59FC0D9831171F67F4716C284AADA8F677BF505E9A866CF7EB6BEA7920466C1C102176A35DCD19BF73AFDF889ADFD3D7207046D4C77FCCA018C0F056F06233996930448DD1B3D6C372C5466958532427369FE74C4BB29986CF1A366D5E42F52DEC6517D81A367C60B3ACE80541A79D48A80EA816D09292063548AF4A7964395F33E63F6E7AF134D136E5F4D400000006DE94A1DA1D810A07D15D8F79EC96CDB9D77A5D9E4217EC3C3A3A2E4FC11B5B17EF27E4CEC94D4EAAC044F6B34C98544EBEEE58732D5519E402220262D1B80FD | |||
| (PID) Process: | (5528) RuntimeBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\S-1-15-2-536077884-713174666-1066051701-3219990555-339840825-1966734348-1611281757 |
| Operation: | write | Name: | DeviceId |
Value: 0018401272CE21DA | |||
| (PID) Process: | (5528) RuntimeBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\S-1-15-2-536077884-713174666-1066051701-3219990555-339840825-1966734348-1611281757 |
| Operation: | write | Name: | ApplicationFlags |
Value: 1 | |||
| (PID) Process: | (6772) rustdesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
Value: | |||
| (PID) Process: | (6772) rustdesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000001BFE69D191B71933A372A80FE155E5B51D0000000100000010000000885010358D29A38F059B028559C95F90620000000100000020000000E793C9B02FD8AA13E21C31228ACCB08119643B749C898964B1746D46C3D4CBD2090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F000000010000003000000066B764A96581128168CF208E374DDA479D54E311F32457F4AEE0DBD2A6C8D171D531289E1CD22BFDBBD4CFD9796254830300000001000000140000002B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E190000000100000010000000EA6089055218053DD01E37E1D806EEDF53000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C01400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB0B00000001000000100000005300650063007400690067006F0000002000000001000000E2050000308205DE308203C6A003020102021001FD6D30FCA3CA51A81BBC640E35032D300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A3423040301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201005CD47C0DCFF7017D4199650C73C5529FCBF8CF99067F1BDA43159F9E0255579614F1523C27879428ED1F3A0137A276FC5350C0849BC66B4EBA8C214FA28E556291F36915D8BC88E3C4AA0BFDEFA8E94B552A06206D55782919EE5F305C4B241155FF249A6E5E2A2BEE0B4D9F7FF70138941495430709FB60A9EE1CAB128CA09A5EA7986A596D8B3F08FBC8D145AF18156490120F73282EC5E2244EFC58ECF0F445FE22B3EB2F8ED2D9456105C1976FA876728F8B8C36AFBF0D05CE718DE6A66F1F6CA67162C5D8D083720CF16711890C9C134C7234DFBCD571DFAA71DDE1B96C8C3C125D65DABD5712B6436BFFE5DE4D661151CF99AEEC17B6E871918CDE49FEDD3571A21527941CCF61E326BB6FA36725215DE6DD1D0B2E681B3B82AFEC836785D4985174B1B9998089FF7F78195C794A602E9240AE4C372A2CC9C762C80E5DF7365BCAE0252501B4DD1A079C77003FD0DCD5EC3DD4FABB3FCC85D66F7FA92DDFB902F7F5979AB535DAC367B0874AA9289E238EFF5C276BE1B04FF307EE002ED45987CB524195EAF447D7EE6441557C8D590295DD629DC2B9EE5A287484A59BB790C70C07DFF589367432D628C1B0B00BE09C4CC31CD6FCE369B54746812FA282ABD3634470C48DFF2D33BAAD8F7BB57088AE3E19CF4028D8FCC890BB5D9922F552E658C51F883143EE881DD7C68E3C436A1DA718DE7D3D16F162F9CA90A8FD | |||
| (PID) Process: | (6772) rustdesk.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\2B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000001000000B00000001000000100000005300650063007400690067006F0000001400000001000000140000005379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB53000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000EA6089055218053DD01E37E1D806EEDF0300000001000000140000002B8F1B57330DBBA2D07A6C51F70EE90DDAB9AD8E0F000000010000003000000066B764A96581128168CF208E374DDA479D54E311F32457F4AEE0DBD2A6C8D171D531289E1CD22BFDBBD4CFD979625483090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B06010505070308620000000100000020000000E793C9B02FD8AA13E21C31228ACCB08119643B749C898964B1746D46C3D4CBD21D0000000100000010000000885010358D29A38F059B028559C95F900400000001000000100000001BFE69D191B71933A372A80FE155E5B52000000001000000E2050000308205DE308203C6A003020102021001FD6D30FCA3CA51A81BBC640E35032D300D06092A864886F70D01010C0500308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F72697479301E170D3130303230313030303030305A170D3338303131383233353935395A308188310B3009060355040613025553311330110603550408130A4E6577204A6572736579311430120603550407130B4A65727365792043697479311E301C060355040A131554686520555345525452555354204E6574776F726B312E302C06035504031325555345525472757374205253412043657274696669636174696F6E20417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A028202010080126517360EC3DB08B3D0AC570D76EDCD27D34CAD508361E2AA204D092D6409DCCE899FCC3DA9ECF6CFC1DCF1D3B1D67B3728112B47DA39C6BC3A19B45FA6BD7D9DA36342B676F2A93B2B91F8E26FD0EC162090093EE2E874C918B491D46264DB7FA306F188186A90223CBCFE13F087147BF6E41F8ED4E451C61167460851CB8614543FBC33FE7E6C9CFF169D18BD518E35A6A766C87267DB2166B1D49B7803C0503AE8CCF0DCBC9E4CFEAF0596351F575AB7FFCEF93DB72CB6F654DDC8E7123A4DAE4C8AB75C9AB4B7203DCA7F2234AE7E3B68660144E7014E46539B3360F794BE5337907343F332C353EFDBAAFE744E69C76B8C6093DEC4C70CDFE132AECC933B517895678BEE3D56FE0CD0690F1B0FF325266B336DF76E47FA7343E57E0EA566B1297C3284635589C40DC19354301913ACD37D37A7EB5D3A6C355CDB41D712DAA9490BDFD8808A0993628EB566CF2588CD84B8B13FA4390FD9029EEB124C957CF36B05A95E1683CCB867E2E8139DCC5B82D34CB3ED5BFFDEE573AC233B2D00BF3555740949D849581A7F9236E651920EF3267D1C4D17BCC9EC4326D0BF415F40A94444F499E757879E501F5754A83EFD74632FB1506509E658422E431A4CB4F0254759FA041E93D426464A5081B2DEBE78B7FC6715E1C957841E0F63D6E962BAD65F552EEA5CC62808042539B80E2BA9F24C971C073F0D52F5EDEF2F820F0203010001A3423040301D0603551D0E041604145379BF5AAA2B4ACF5480E1D89BC09DF2B20366CB300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010C050003820201005CD47C0DCFF7017D4199650C73C5529FCBF8CF99067F1BDA43159F9E0255579614F1523C27879428ED1F3A0137A276FC5350C0849BC66B4EBA8C214FA28E556291F36915D8BC88E3C4AA0BFDEFA8E94B552A06206D55782919EE5F305C4B241155FF249A6E5E2A2BEE0B4D9F7FF70138941495430709FB60A9EE1CAB128CA09A5EA7986A596D8B3F08FBC8D145AF18156490120F73282EC5E2244EFC58ECF0F445FE22B3EB2F8ED2D9456105C1976FA876728F8B8C36AFBF0D05CE718DE6A66F1F6CA67162C5D8D083720CF16711890C9C134C7234DFBCD571DFAA71DDE1B96C8C3C125D65DABD5712B6436BFFE5DE4D661151CF99AEEC17B6E871918CDE49FEDD3571A21527941CCF61E326BB6FA36725215DE6DD1D0B2E681B3B82AFEC836785D4985174B1B9998089FF7F78195C794A602E9240AE4C372A2CC9C762C80E5DF7365BCAE0252501B4DD1A079C77003FD0DCD5EC3DD4FABB3FCC85D66F7FA92DDFB902F7F5979AB535DAC367B0874AA9289E238EFF5C276BE1B04FF307EE002ED45987CB524195EAF447D7EE6441557C8D590295DD629DC2B9EE5A287484A59BB790C70C07DFF589367432D628C1B0B00BE09C4CC31CD6FCE369B54746812FA282ABD3634470C48DFF2D33BAAD8F7BB57088AE3E19CF4028D8FCC890BB5D9922F552E658C51F883143EE881DD7C68E3C436A1DA718DE7D3D16F162F9CA90A8FD | |||
| (PID) Process: | (4164) RuntimeBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\Subscriptions\314559 |
| Operation: | write | Name: | LastAccessed |
Value: A018461CDFB2DB01 | |||
| (PID) Process: | (4164) RuntimeBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\Subscriptions\338388 |
| Operation: | write | Name: | LastAccessed |
Value: A018461CDFB2DB01 | |||
Executable files
231
Suspicious files
102
Text files
132
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_asyncio.pyd | executable | |
MD5:56F958EEBBC62305B4BF690D61C78E28 | SHA256:50631361EF074BE42D788818AF91D0301D22FA24A970F41F496D8272B92CFE31 | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_bz2.pyd | executable | |
MD5:684D656AADA9F7D74F5A5BDCF16D0EDB | SHA256:A5DFB4A663DEF3D2276B88866F6D220F6D30CC777B5D841CF6DBB15C6858017C | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_hashlib.pyd | executable | |
MD5:3E540EF568215561590DF215801B0F59 | SHA256:0ED7A6ED080499BC6C29D7113485A8A61BDBA93087B010FCA67D9B8289CBE6FA | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_socket.pyd | executable | |
MD5:566CB4D39B700C19DBD7175BD4F2B649 | SHA256:77EBA293FE03253396D7BB6E575187CD026C80766D7A345EB72AD92F0BBBC3AA | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_ctypes.pyd | executable | |
MD5:29873384E13B0A78EE9857604161514B | SHA256:3CC8500A958CC125809B0467930EBCCE88A09DCC0CEDD7A45FACF3E332F7DB33 | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:EB0978A9213E7F6FDD63B2967F02D999 | SHA256:AB25A1FE836FC68BCB199F1FE565C27D26AF0C390A38DA158E0D8815EFE1103E | |||
| 7440 | Opno.exe | C:\Users\admin\AppData\Local\Temp\_MEI74402\_multiprocessing.pyd | executable | |
MD5:807DD90BE59EA971DAC06F3AAB4F2A7E | SHA256:B20DD6F5FAB31476D3D8D7F40CB5AB098117FA5612168C0FF4044945B6156D47 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
85
DNS requests
48
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6824 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6824 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6232 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7544 | Opno.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
— | — | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
github.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |
2192 | svchost.exe | Misc activity | ET INFO RustDesk Relay Domain in DNS Lookup |
2192 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |
2192 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |
2148 | svchost.exe | Misc activity | ET INFO RustDesk Relay Domain in DNS Lookup |
2148 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |
2148 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |
2148 | svchost.exe | Misc activity | ET INFO RustDesk Domain in DNS Lookup |