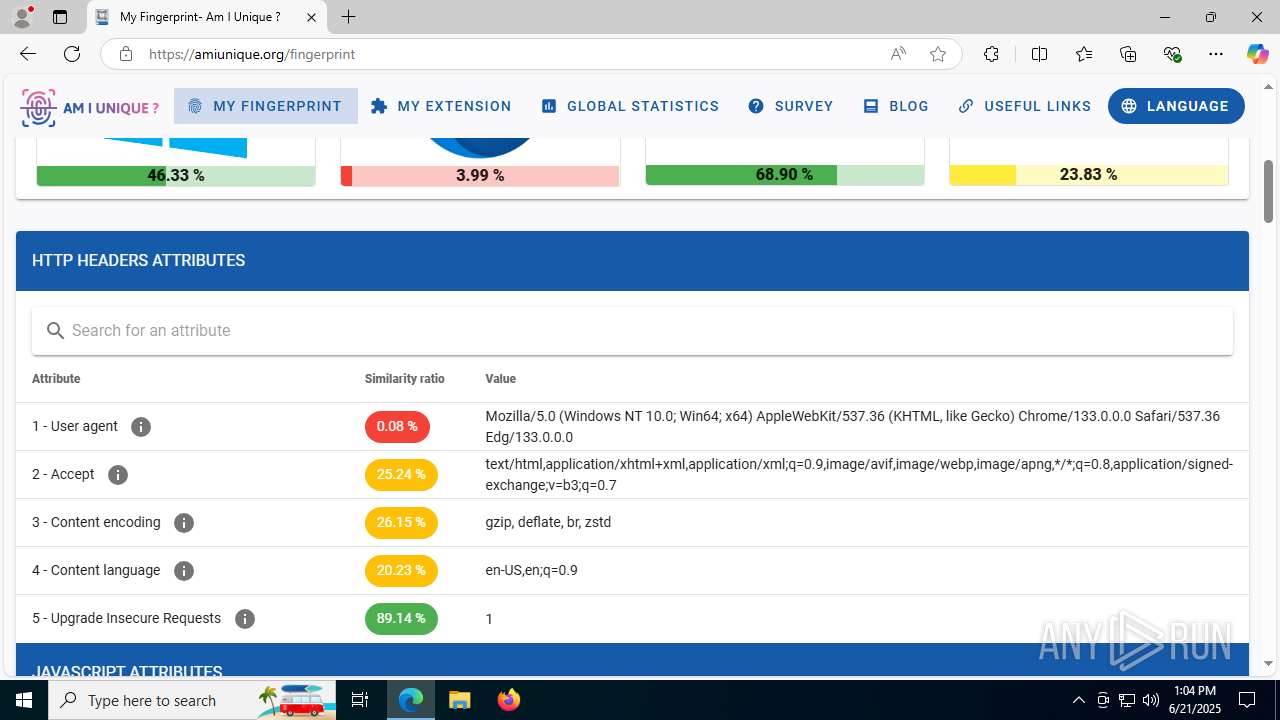
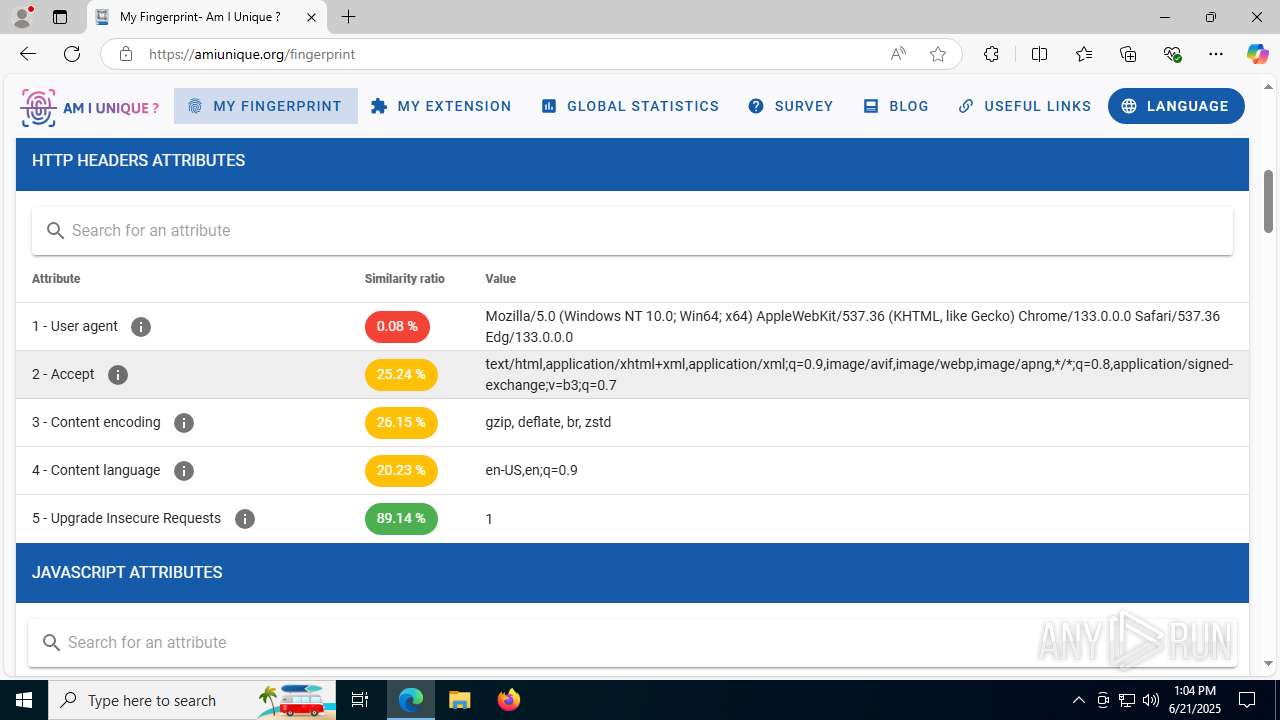
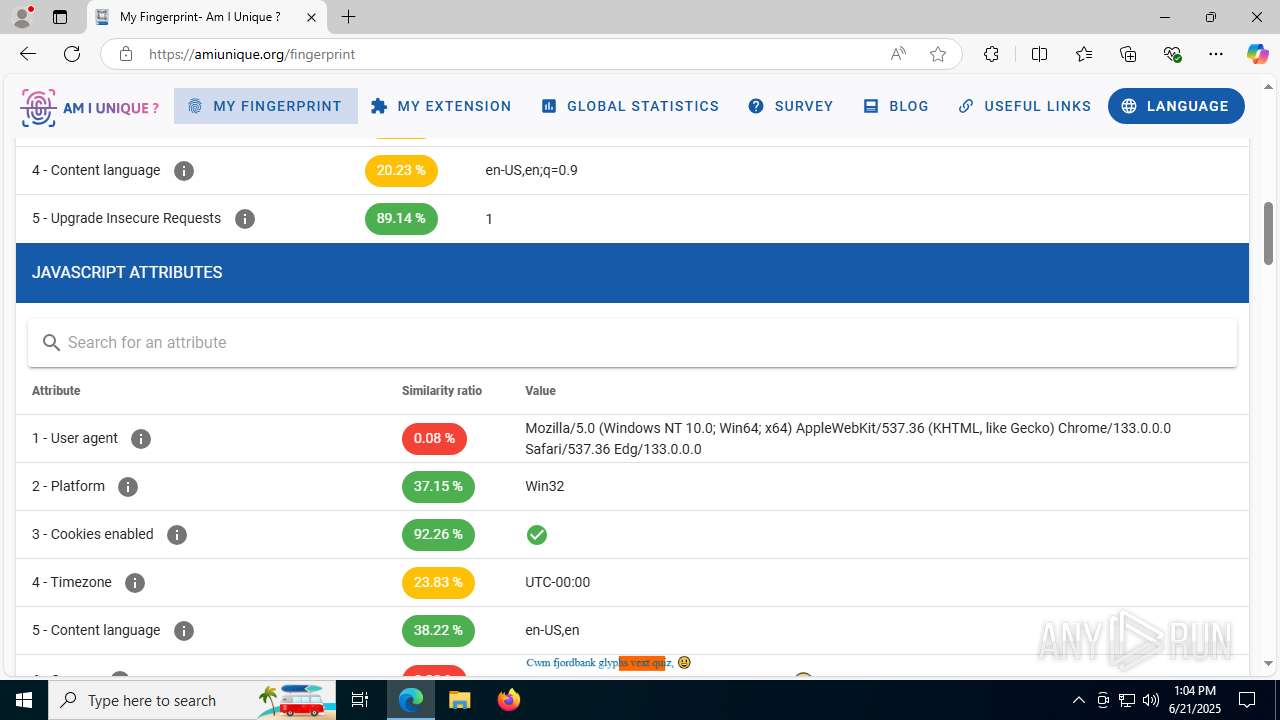
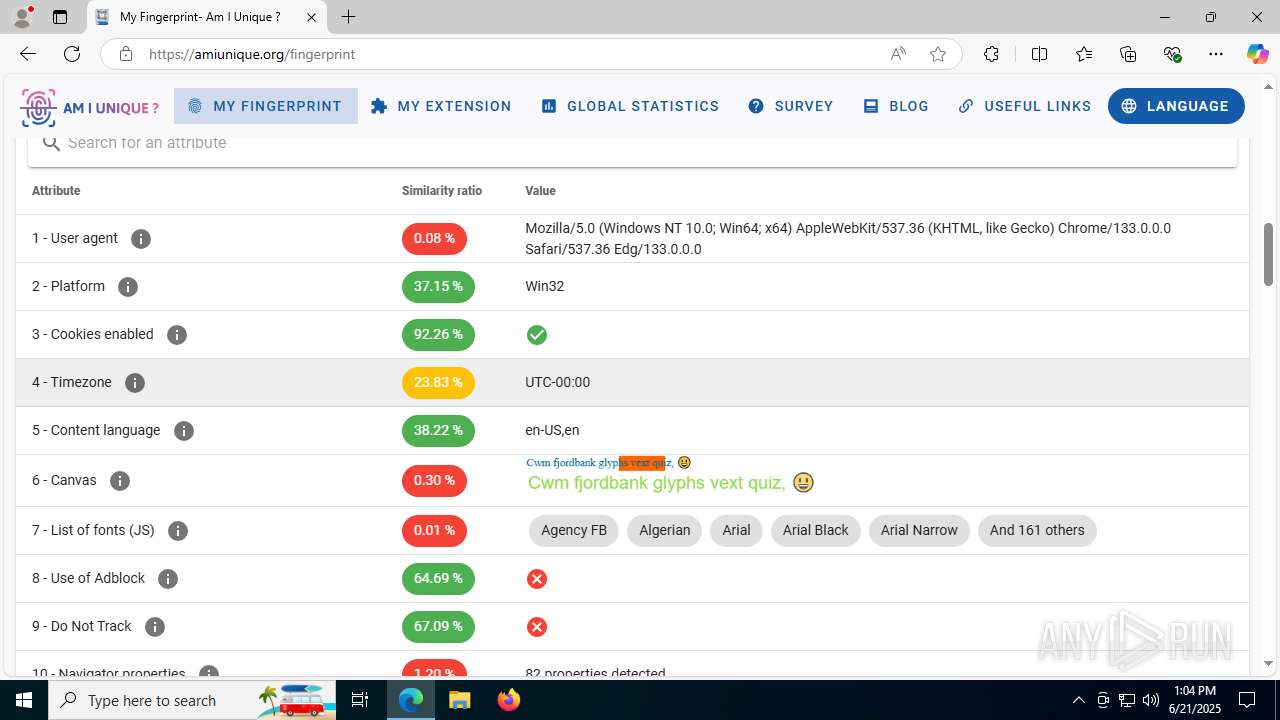
| File name: | Client-built-appdata.exe |
| Full analysis: | https://app.any.run/tasks/c192c061-e23f-40d8-9a57-57fecd5fda37 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | June 21, 2025, 13:01:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | AEC658DAECC20E123B815D7F07A750B1 |
| SHA1: | E4F06DE96C0711997148AB35E2EAC808239DDBA0 |
| SHA256: | 61C02EF5FECCDA0461966793E2BD93CC4B3CEE97E3B0B5DCF1A856398BF4AAFC |
| SSDEEP: | 98304:Y2uiieRyd72QsLDil92m3GJEDgqcCr2dX:lmgc |
MALICIOUS
Changes the autorun value in the registry
- Client-built-appdata.exe (PID: 6584)
- Client-appdata.exe (PID: 6508)
QUASAR has been detected (SURICATA)
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
Connects to the CnC server
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
QUASAR has been detected (YARA)
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
Uses Task Scheduler to autorun other applications
- Client-appdata.exe (PID: 1560)
Steals credentials from Web Browsers
- Client-appdata.exe (PID: 1560)
Actions looks like stealing of personal data
- Client-appdata.exe (PID: 1560)
SUSPICIOUS
Executable content was dropped or overwritten
- Client-built-appdata.exe (PID: 6584)
Starts itself from another location
- Client-built-appdata.exe (PID: 6584)
Connects to unusual port
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
Reads security settings of Internet Explorer
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
- StartMenuExperienceHost.exe (PID: 4984)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2200)
Checks for external IP
- svchost.exe (PID: 2200)
Reads the date of Windows installation
- Client-appdata.exe (PID: 6508)
- StartMenuExperienceHost.exe (PID: 4984)
- SearchApp.exe (PID: 1232)
Contacting a server suspected of hosting an CnC
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
There is functionality for taking screenshot (YARA)
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
Starts CMD.EXE for commands execution
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
The executable file from the user directory is run by the CMD process
- Client-appdata.exe (PID: 1560)
Starts application with an unusual extension
- cmd.exe (PID: 6004)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6004)
The process executes via Task Scheduler
- explorer.exe (PID: 2552)
Loads DLL from Mozilla Firefox
- Client-appdata.exe (PID: 1560)
Deletes system .NET executable
- Client-appdata.exe (PID: 1560)
INFO
Reads the machine GUID from the registry
- Client-built-appdata.exe (PID: 6584)
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
- SearchApp.exe (PID: 1232)
- Client-appdata.exe (PID: 5820)
Creates files or folders in the user directory
- Client-built-appdata.exe (PID: 6584)
- explorer.exe (PID: 2552)
- Client-appdata.exe (PID: 1560)
Reads the computer name
- Client-built-appdata.exe (PID: 6584)
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
- StartMenuExperienceHost.exe (PID: 4984)
- TextInputHost.exe (PID: 4864)
- SearchApp.exe (PID: 1232)
- Client-appdata.exe (PID: 5820)
- identity_helper.exe (PID: 6876)
- identity_helper.exe (PID: 420)
Checks supported languages
- Client-built-appdata.exe (PID: 6584)
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
- chcp.com (PID: 1156)
- StartMenuExperienceHost.exe (PID: 4984)
- TextInputHost.exe (PID: 4864)
- SearchApp.exe (PID: 1232)
- Client-appdata.exe (PID: 5820)
- identity_helper.exe (PID: 6876)
- identity_helper.exe (PID: 420)
Reads Environment values
- Client-built-appdata.exe (PID: 6584)
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
- SearchApp.exe (PID: 1232)
- Client-appdata.exe (PID: 5820)
- identity_helper.exe (PID: 420)
- identity_helper.exe (PID: 6876)
Launching a file from a Registry key
- Client-built-appdata.exe (PID: 6584)
- Client-appdata.exe (PID: 6508)
Disables trace logs
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
Reads the software policy settings
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
- SearchApp.exe (PID: 1232)
- slui.exe (PID: 6016)
Checks proxy server information
- Client-appdata.exe (PID: 6508)
- Client-appdata.exe (PID: 1560)
- SearchApp.exe (PID: 1232)
- explorer.exe (PID: 2552)
- slui.exe (PID: 6016)
Process checks computer location settings
- Client-appdata.exe (PID: 6508)
- StartMenuExperienceHost.exe (PID: 4984)
- SearchApp.exe (PID: 1232)
Changes the display of characters in the console
- cmd.exe (PID: 6004)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2552)
Reads the time zone
- runonce.exe (PID: 6120)
Application launched itself
- chrome.exe (PID: 5328)
- msedge.exe (PID: 5400)
- msedge.exe (PID: 6700)
- msedge.exe (PID: 2044)
- msedge.exe (PID: 3580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(6508) Client-appdata.exe
Version1.4.1
C2 (2)lmn347583-61457.portmap.io:61457
Sub_DirSystem3Z
Install_NameClient-appdata.exe
Mutex6dded8b6-7f84-480c-b2f8-bb911a832ed2
Startupwwahost boot
TagR30115
LogDirLogs
SignaturecxbzvHwRe/n0qGA3V//ZORe0hT9hJuGN+PApbWIbFv2vsTeAo2oFfIrXx1DXFdDl//gYE4sUYFiZo8FWGJjTe7A5hkPKVEuUvex+RZRhSLwDKIldGCfnqpVSVdAVUqhXQWcBgq+imCaR//agp0FSChR7ht4Cw1k+16xfv1Mo5sXoLmqVXJb0J8Gq2Cxq2V9GEFGgvAtvhUpckBcmzOE7AbCmoAZM/FPDdGeQDFymdjTVfs3lpUn0fNidSjWqFsNNvU7KyO354V/35Q+5hrLIFh+/YlaltQLGVzKtZMlXJtpx...
CertificateMIIE9DCCAtygAwIBAgIQAJybIcqk3akDxnhNu6jB9TANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDYxNzE3MzU0MFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAuIKPABH+6nPTE9GPRW9OWv8ktHVk4ry6aXguYpsKcbHoh8UqahaBSouG/LPSWAlABAaq5Ary...
(PID) Process(1560) Client-appdata.exe
Version1.4.1
C2 (2)lmn347583-61457.portmap.io:61457
Sub_DirSystem3Z
Install_NameClient-appdata.exe
Mutex6dded8b6-7f84-480c-b2f8-bb911a832ed2
Startupwwahost boot
TagR30115
LogDirLogs
SignaturecxbzvHwRe/n0qGA3V//ZORe0hT9hJuGN+PApbWIbFv2vsTeAo2oFfIrXx1DXFdDl//gYE4sUYFiZo8FWGJjTe7A5hkPKVEuUvex+RZRhSLwDKIldGCfnqpVSVdAVUqhXQWcBgq+imCaR//agp0FSChR7ht4Cw1k+16xfv1Mo5sXoLmqVXJb0J8Gq2Cxq2V9GEFGgvAtvhUpckBcmzOE7AbCmoAZM/FPDdGeQDFymdjTVfs3lpUn0fNidSjWqFsNNvU7KyO354V/35Q+5hrLIFh+/YlaltQLGVzKtZMlXJtpx...
CertificateMIIE9DCCAtygAwIBAgIQAJybIcqk3akDxnhNu6jB9TANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDYxNzE3MzU0MFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAuIKPABH+6nPTE9GPRW9OWv8ktHVk4ry6aXguYpsKcbHoh8UqahaBSouG/LPSWAlABAaq5Ary...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:03:12 16:16:39+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 3261952 |
| InitializedDataSize: | 3584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x31e45e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.1.0 |
| ProductVersionNumber: | 1.4.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Quasar Client |
| FileVersion: | 1.4.1 |
| InternalName: | Client.exe |
| LegalCopyright: | Copyright © MaxXor 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | Client.exe |
| ProductName: | Quasar |
| ProductVersion: | 1.4.1 |
| AssemblyVersion: | 1.4.1.0 |
Total processes
229
Monitored processes
78
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1996,i,10896402537068255975,15284167448465379887,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=1980 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 420 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4804,i,3849344973769167530,4128406481577757440,262144 --variations-seed-version --mojo-platform-channel-handle=4824 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4928,i,10896402537068255975,15284167448465379887,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4920 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=4744,i,10896402537068255975,15284167448465379887,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4724 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 864 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Exit code: 0 Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | CHCP 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6876,i,12740373943567463406,3492435754904604585,262144 --variations-seed-version --mojo-platform-channel-handle=5976 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
53 169
Read events
52 480
Write events
288
Delete events
401
Modification events
| (PID) Process: | (6584) Client-built-appdata.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | wwahost boot |
Value: "C:\Users\admin\AppData\Roaming\System3Z\Client-appdata.exe" | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6508) Client-appdata.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Client-appdata_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
18
Suspicious files
383
Text files
139
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\Init[1].htm | html | |
MD5:EF710CD94E42180BC51F58CDC6D5E438 | SHA256:9F32707750C9DEDD5077C9138331B48F0C42C99EC8A4B174CB75E0E58D8C40F1 | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:99B2C924EA9FCDA277BACD2496A2139E | SHA256:8B1D106599E9497E37259BAFA963B695463B7819A1709C01E82244A2D1A5EF6D | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:C6A28F0A469820EE75CE0094B5E05D62 | SHA256:BF3C9FE8FDE4D296C0B91D494820385887C72DDE05FC7819042E4CEF57289842 | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:DF367B9525354CC5543C9247210072ED | SHA256:68511E58CC309F2895652008EF4A7C0B18C023D5EDBC435BCE4E83F8BE640D09 | |||
| 864 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:84A3682006478204A9D4939E56725A23 | SHA256:611E5319A1D427E4A42F0D32DA1F300881945B5CF8E6EC7AF8053F997C94DD72 | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:F1766B47BE16456EB459D5DD8C9974A3 | SHA256:3EED49780152DAA2551D56FDE02B1451FB5FE443787B89DEA1652D27C2B9EFE6 | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\LJVpDXTkWDgGwVlLgxLZkLutWKw[1].css | text | |
MD5:B9727BBC2A77C4A60AADDCA163365575 | SHA256:8B23E288F4D6BF19C88B4F60AF45515C1D637D795430F150E4BC7C76FAD95CBD | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\Q84V0JUH\6hU_LneafI_NFLeDvM367ebFaKQ[1].js | s | |
MD5:C6C21B7634D82C53FB86080014D86E66 | SHA256:D39E9BA92B07F4D50B11A49965E9B162452D7B9C9F26D9DCB07825727E31057E | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:29DE55D0A7A581B230CC2D70686CD03A | SHA256:D9F161C1FE8751953E4F3819993C16C2A61A0121B527E09862C34C89E7B6C677 | |||
| 1232 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\77\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:93C2665E2C62E2143F4D5063836B688A | SHA256:2842068E32CE3298230718DD40915A3C5D8F24B97B2A0801B2B0FD4FDEF79244 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
110
DNS requests
118
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2292 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6876 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6876 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1232 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
2168 | chrome.exe | GET | 200 | 142.250.186.78:80 | http://clients2.google.com/time/1/current?cup2key=8:SQtM6U-puxp-HZQTi4OGEMXJuXQUcyLEEaWSFIa56Ak&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5732 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:c1x96TfEMxdbKtia2TG0CDFA8junK1RXsaNdTNbsklI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2732 | svchost.exe | HEAD | 200 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751066851&P2=404&P3=2&P4=PsCzt%2breW7ZUxvz%2fOO2cjaay%2bb%2fM%2bOpQ%2b3RdGg465GyrdJVuPJ8lLs8dl5f6bSS%2f9p8IXFjTkm%2bdS5VdiCescQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6960 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6508 | Client-appdata.exe | 193.161.193.99:61457 | lmn347583-61457.portmap.io | OOO Bitree Networks | RU | malicious |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6508 | Client-appdata.exe | 136.243.53.56:443 | ipwho.is | Hetzner Online GmbH | DE | malicious |
2292 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2292 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
lmn347583-61457.portmap.io |
| malicious |
ipwho.is |
| malicious |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potential Corporate Privacy Violation | ET INFO DNS Query to a Reverse Proxy Service Observed |
2200 | svchost.exe | Misc activity | ET INFO DNS Query for Port Mapping/Tunneling Service Domain (.portmap .io) |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
6508 | Client-appdata.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
6508 | Client-appdata.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (Quasar CnC) |
6508 | Client-appdata.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (GCM_SHA384) |
1560 | Client-appdata.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
1560 | Client-appdata.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (Quasar CnC) |
1560 | Client-appdata.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (GCM_SHA384) |