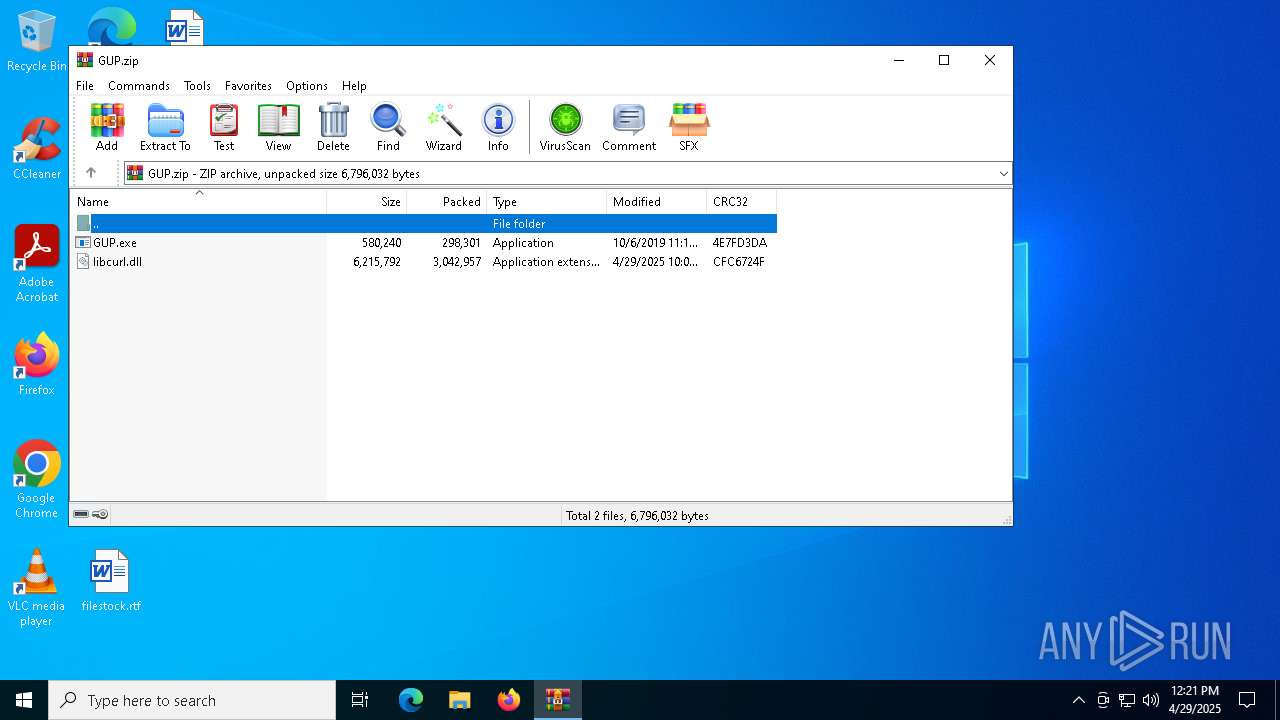
| File name: | GUP.zip |
| Full analysis: | https://app.any.run/tasks/d5a7b492-f6bb-412e-9f89-c4fec3b02666 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 29, 2025, 12:21:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 415BE2E09BBDD6B364DE2A4381DE6DD2 |
| SHA1: | F907BE532DE39B775FFEDDCB04BB0C76865E25AA |
| SHA256: | 617BF8FE09E9ED7A5139F9FC5B7633E0D31FBDA9944FDA5B10544B653725CBB5 |
| SSDEEP: | 98304:kwWhI7vnxsnaoQ/cZekPFyC/HX4LdKElJhyYonQwFlZ3M+5jW/Avf346N7a+PFUw:1jajf |
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 5492)
Runs injected code in another process
- GUP.exe (PID: 6264)
- GUP.exe (PID: 6424)
Changes the autorun value in the registry
- GUP.exe (PID: 6264)
- GUP.exe (PID: 6424)
Actions looks like stealing of personal data
- GUP.exe (PID: 6264)
ASYNCRAT has been detected (SURICATA)
- GUP.exe (PID: 6264)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- GUP.exe (PID: 6264)
Write to the desktop.ini file (may be used to cloak folders)
- GUP.exe (PID: 6264)
Executable content was dropped or overwritten
- GUP.exe (PID: 6264)
Connects to unusual port
- GUP.exe (PID: 6264)
Contacting a server suspected of hosting an CnC
- GUP.exe (PID: 6264)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5380)
- WinRAR.exe (PID: 5552)
- GUP.exe (PID: 6264)
Manual execution by a user
- GUP.exe (PID: 6264)
- WinRAR.exe (PID: 5552)
- GUP.exe (PID: 6424)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5552)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Reads the computer name
- GUP.exe (PID: 6264)
Creates files or folders in the user directory
- GUP.exe (PID: 6264)
Reads the machine GUID from the registry
- GUP.exe (PID: 6264)
Reads the software policy settings
- GUP.exe (PID: 6264)
- slui.exe (PID: 1132)
Checks proxy server information
- slui.exe (PID: 1132)
Checks supported languages
- GUP.exe (PID: 6424)
- GUP.exe (PID: 6264)
Compiled with Borland Delphi (YARA)
- GUP.exe (PID: 6264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:10:07 02:14:06 |
| ZipCRC: | 0x4e7fd3da |
| ZipCompressedSize: | 298301 |
| ZipUncompressedSize: | 580240 |
| ZipFileName: | GUP.exe |
Total processes
154
Monitored processes
10
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3992 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 5380 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\GUP.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5552 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\GUP.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6264 | "C:\Users\admin\Desktop\GUP.exe" | C:\Users\admin\Desktop\GUP.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: HIGH Description: WinGup for Notepad++ Exit code: 0 Version: 5.1 Modules
| |||||||||||||||
| 6424 | C:\WINDOWS\Explorer.EXE | C:\Users\admin\Desktop\GUP.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: WinGup for Notepad++ Version: 5.1 Modules
| |||||||||||||||
Total events
10 657
Read events
10 615
Write events
40
Delete events
2
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000004028A |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\GUP.zip | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5380) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
4
Suspicious files
5
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\filestock.rtf | text | |
MD5:EB0768CA61AAC5E4D3F920D701B07C4F | SHA256:0A8EE4E17C59DF8CDFD7FAE4D97EBF28FC8E56767E7C3BA0D57EEA722E78427E | |||
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\edgealways.png | binary | |
MD5:807482FA95B3DFE5AA77E368A355123A | SHA256:6767B84A13A560FEF9A5B192C2F19D8BF3EF04D6A8D26188CF9171F5E11470CC | |||
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\GUP.exe | executable | |
MD5:5F983177F3F9CE6CB72088F3DA96435D | SHA256:9863AC60B92FAD160CE88353760C7C4F21F8E9C3190B18B374BDBCA3A7D1A3FB | |||
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\eurmilf.rtf | text | |
MD5:F953F4EA35E841EB50E637821B385FB1 | SHA256:E3B2C8FE8838A54570FE495254A55BB8476FD9BFC51F5F77066AB7E96A7C2CA3 | |||
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\headkeywords.rtf | text | |
MD5:F5D520A3D97B0B7F61AD333D49DF84A6 | SHA256:A499CD8C820A27EC8411C0A67116C8DD82BCA2BCF604F62C6D8CC95FBD3489B2 | |||
| 5552 | WinRAR.exe | C:\Users\admin\Desktop\GUP.exe | executable | |
MD5:5F983177F3F9CE6CB72088F3DA96435D | SHA256:9863AC60B92FAD160CE88353760C7C4F21F8E9C3190B18B374BDBCA3A7D1A3FB | |||
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\actsize.jpg | binary | |
MD5:000436118BB587232EB6460DB99364A7 | SHA256:7CFCC36AFD1E438DF60AAD6555564F6E495EA3BA31FEBCD53889A29F7977628C | |||
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\libcurl.dll | executable | |
MD5:9CB437AC38C65911BEC93F8FE01B7F1B | SHA256:93BD28C2C23740C8F08AE1C3E110B1818D5E093378B2D9FF4F1103198DA1D07C | |||
| 6264 | GUP.exe | C:\Users\admin\AppData\Roaming\desktop.ini | text | |
MD5:9E36CC3537EE9EE1E3B10FA4E761045B | SHA256:4B9D687AC625690FD026ED4B236DAD1CAC90EF69E7AD256CC42766A065B50026 | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
95
DNS requests
21
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 13.95.31.18:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
2268 | SIHClient.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 4.175.87.197:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
2268 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
2268 | SIHClient.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.32.68:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
2268 | SIHClient.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
2268 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.32.68:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.67:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6264 | GUP.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 31 |
6264 | GUP.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
6264 | GUP.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |