| File name: | 11.exe |
| Full analysis: | https://app.any.run/tasks/b56e0787-da1e-4764-900c-3c45f81acd32 |
| Verdict: | Malicious activity |
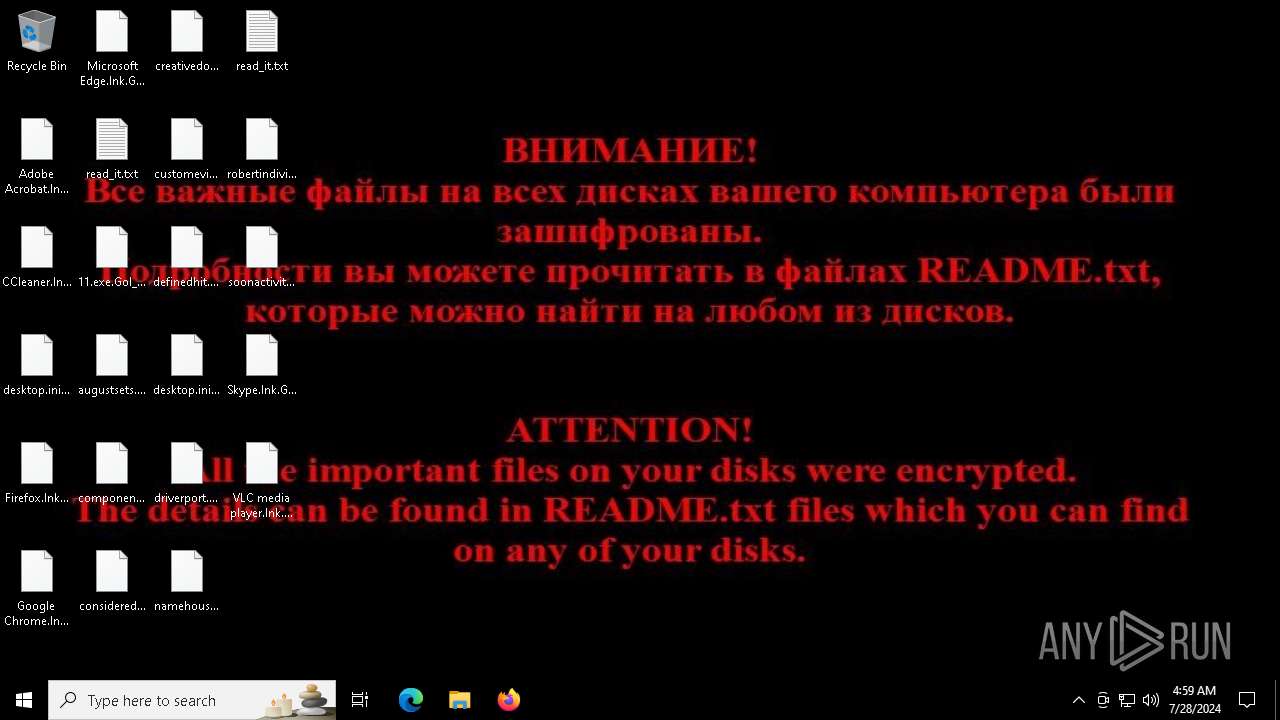
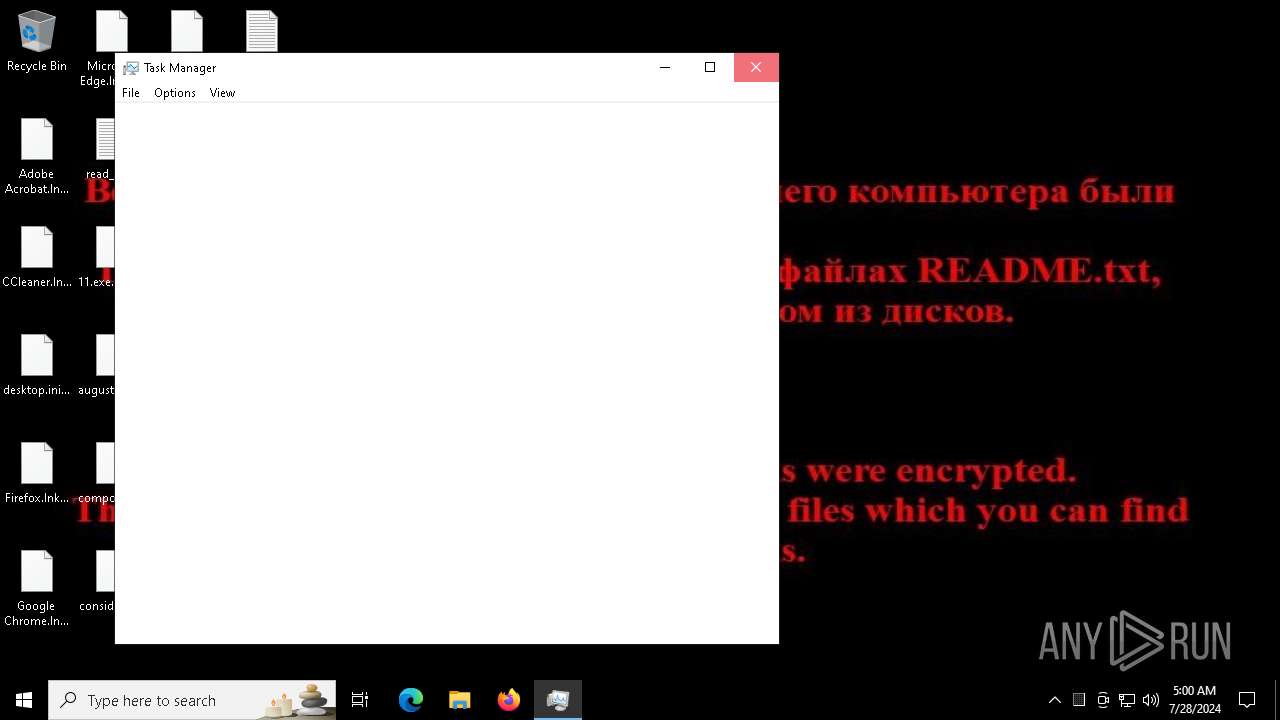
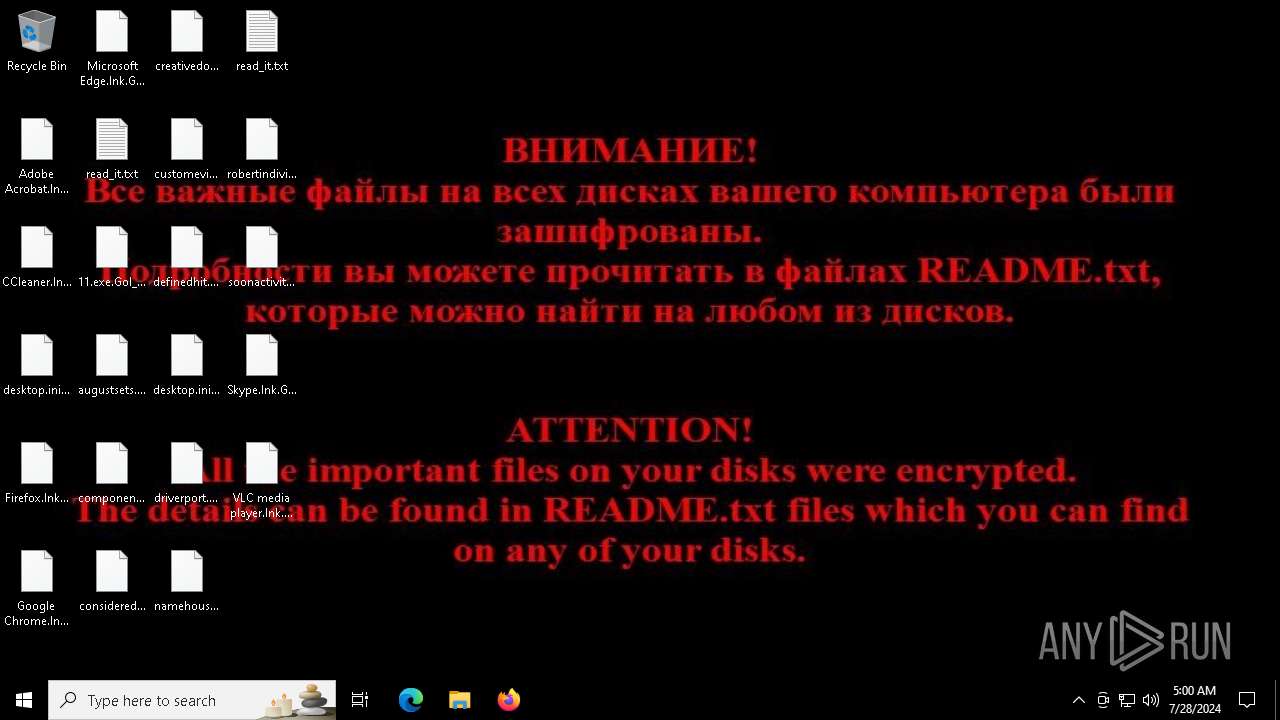
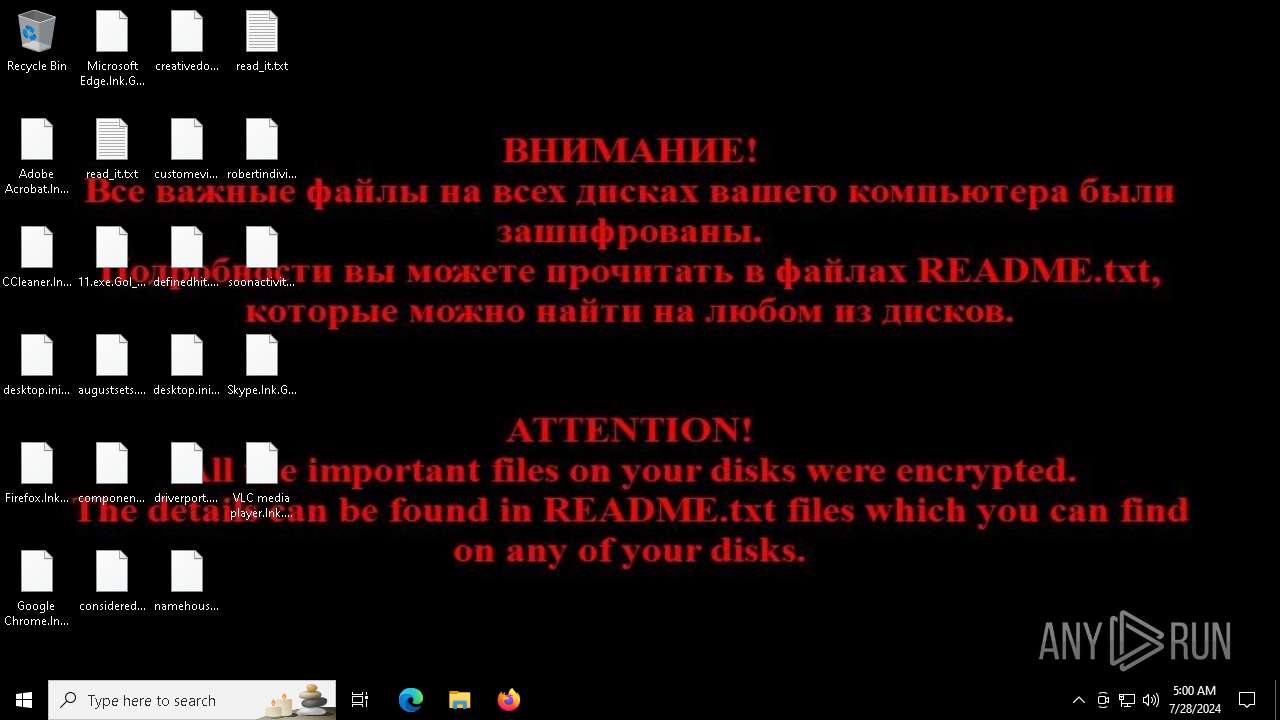
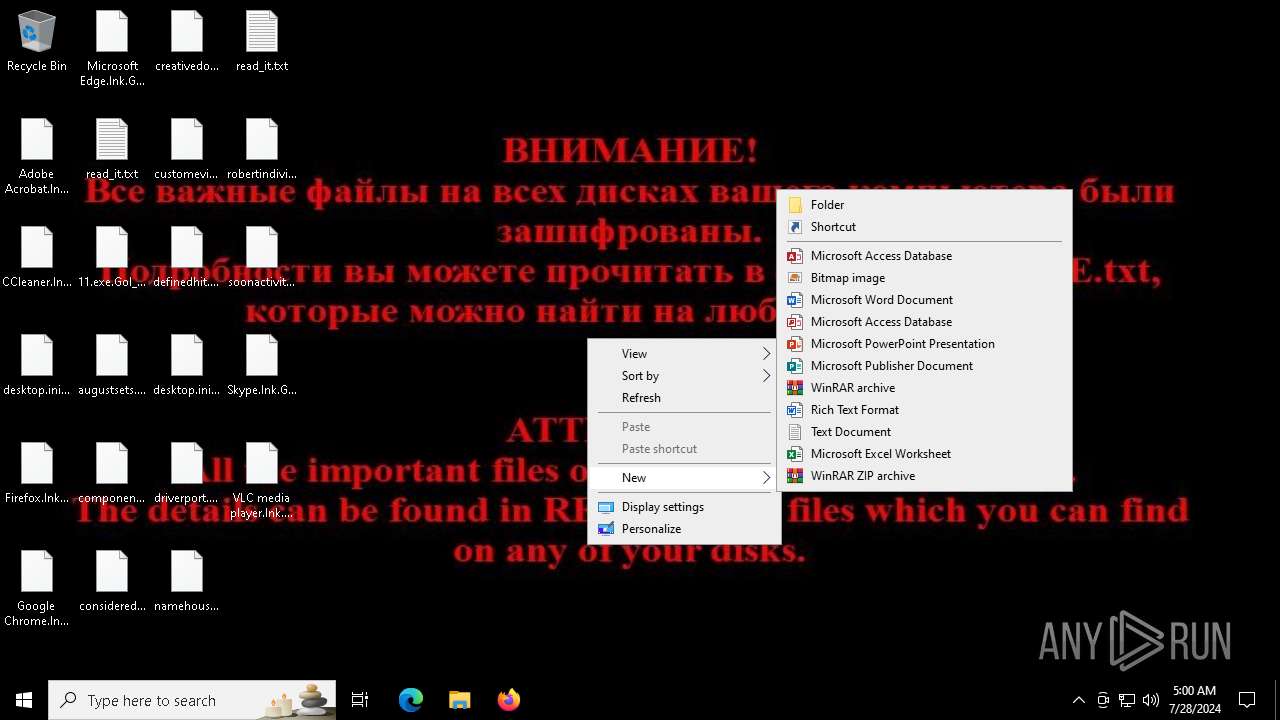
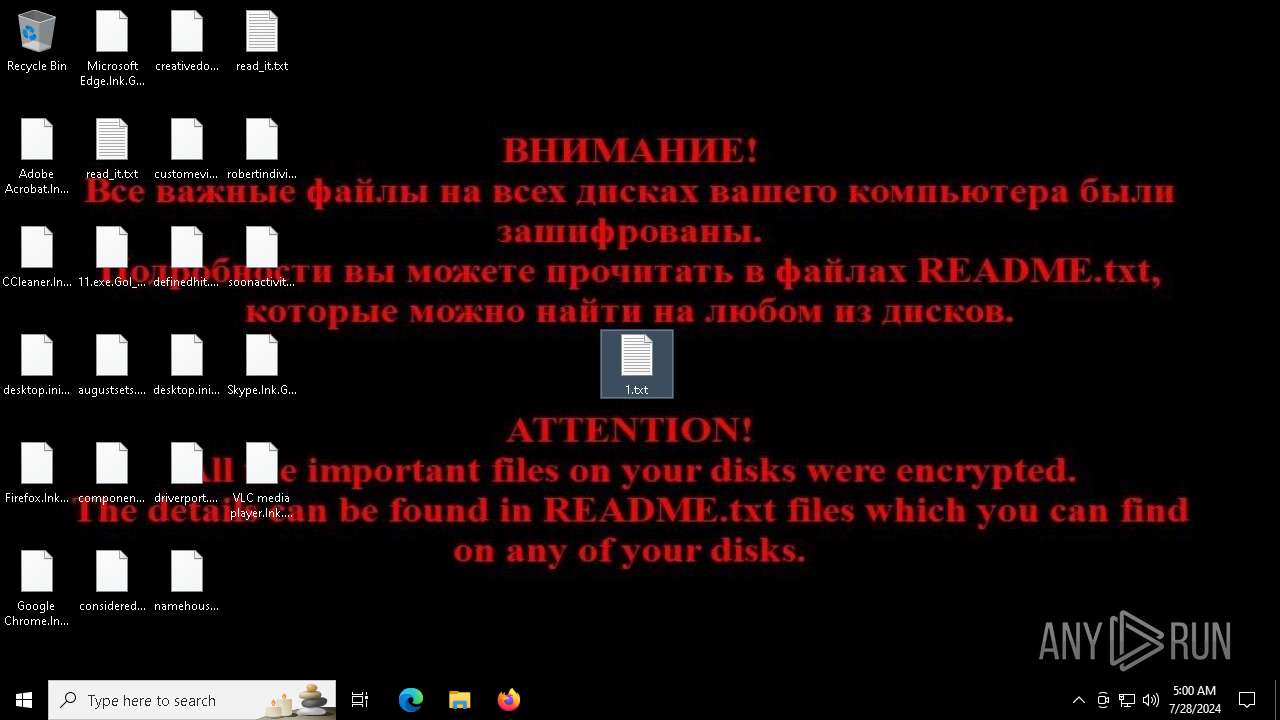
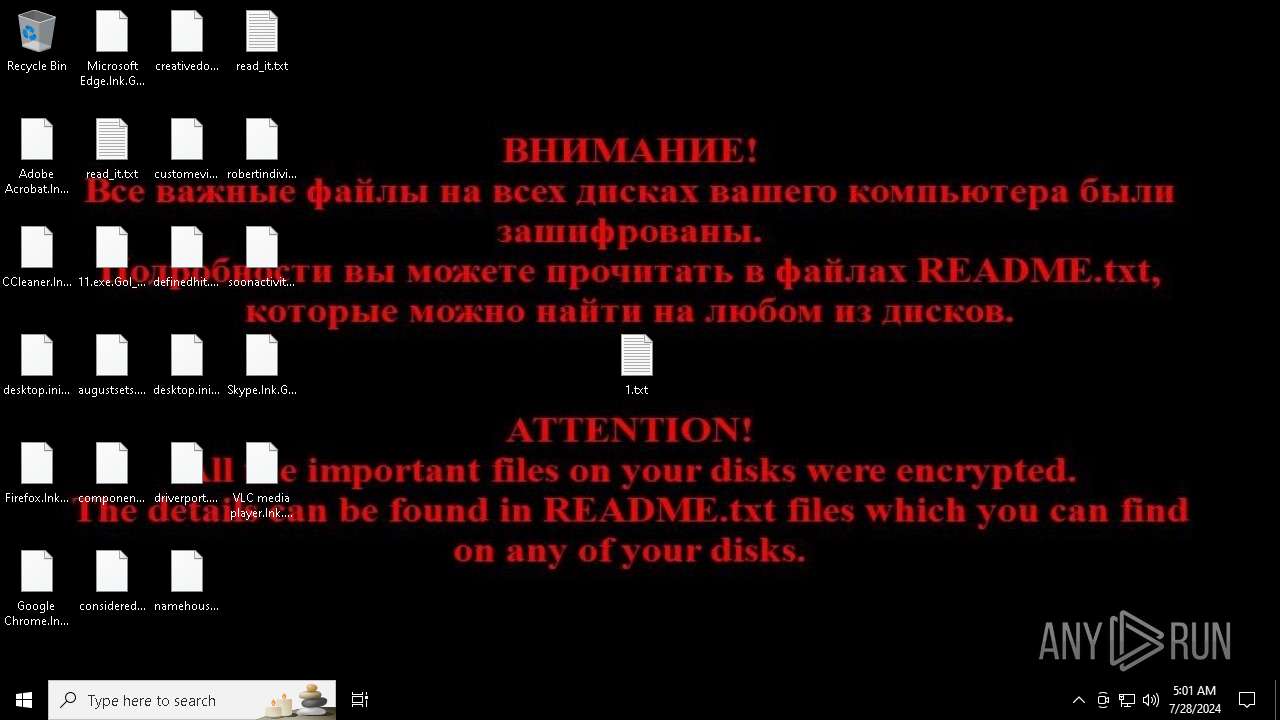
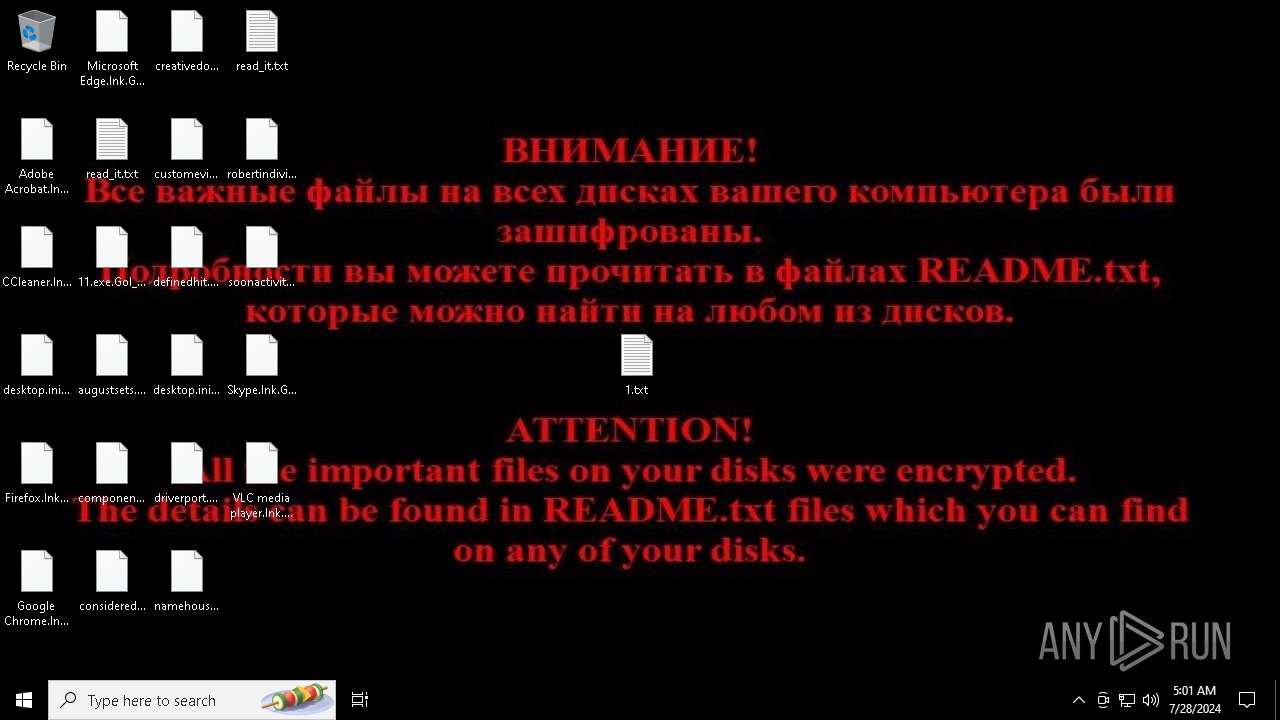
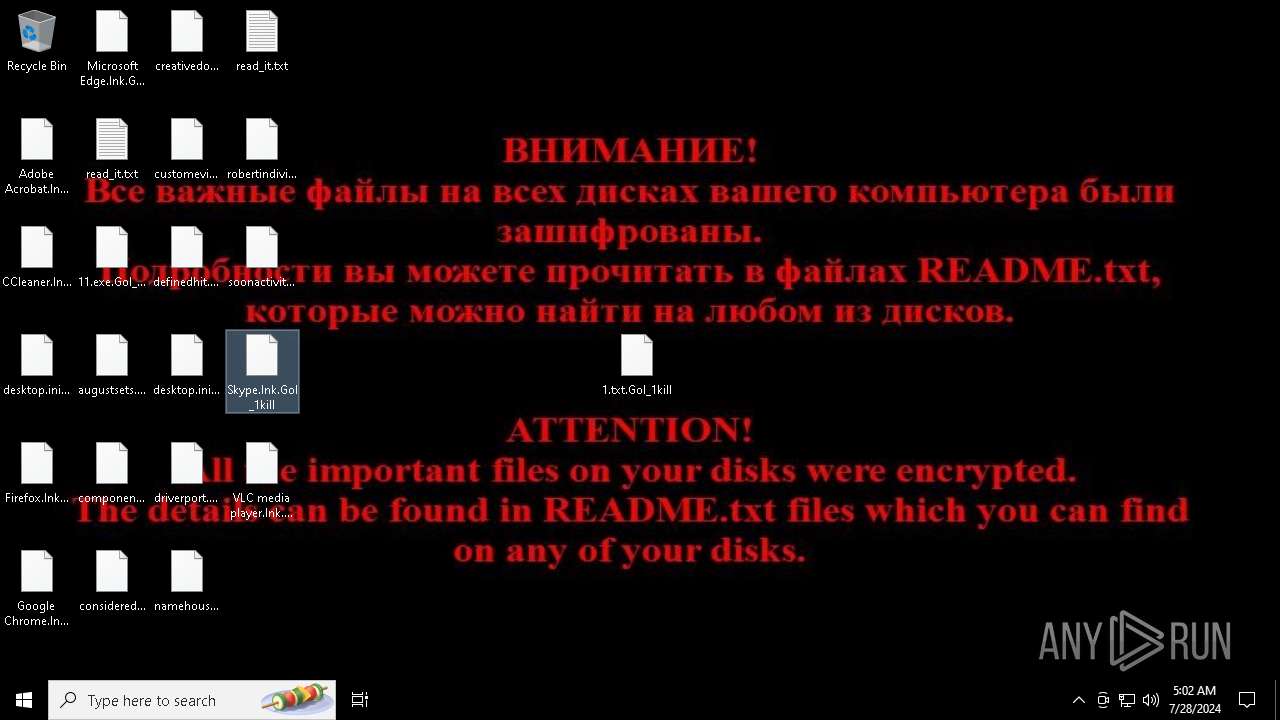
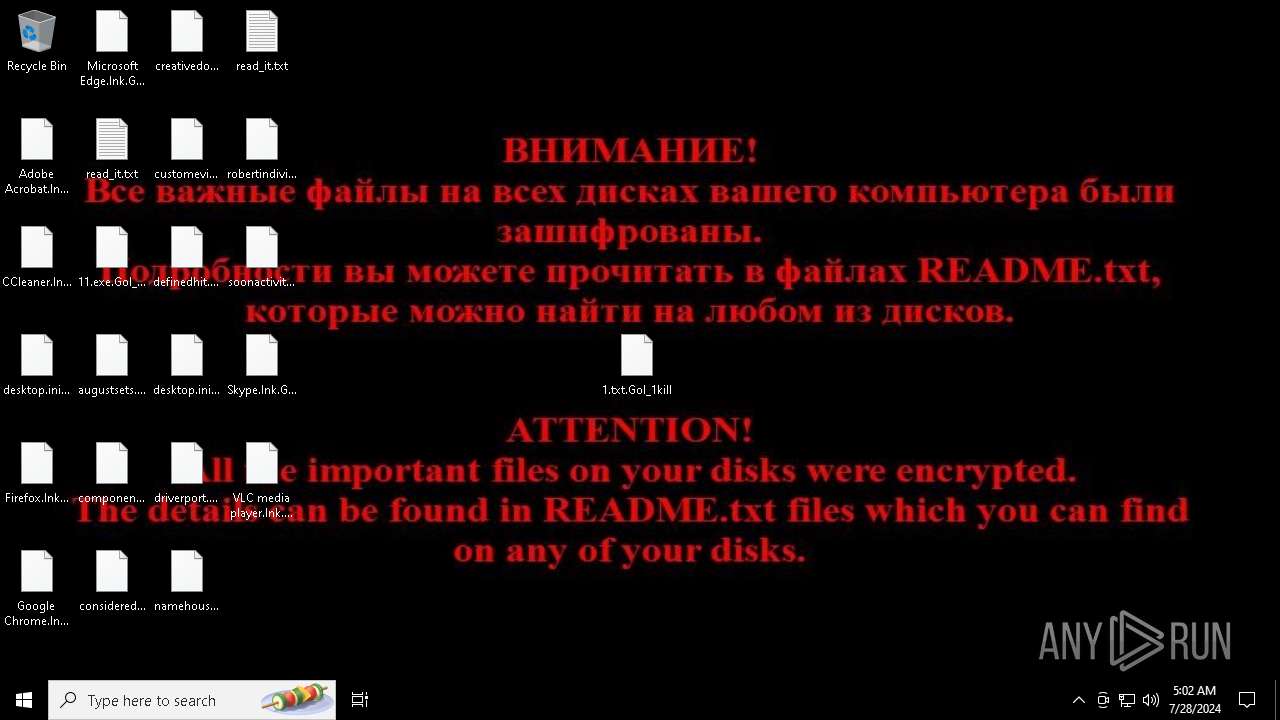
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | July 28, 2024, 04:58:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 99177A95442CB3CD77F9359C948C9FBE |
| SHA1: | 764AF2058A89C8FFA7E704BDB84D4492BCAE5BE2 |
| SHA256: | 612EB5C3269A264D1516904E24FE1BDFA17CB8A06441F03C483216EB52A9F526 |
| SSDEEP: | 3072:vd9Qr9cIB/WcwALWP+nWVWRzO/LZLYq5r+6BQJAjrEzUV7kMq3LBl:cr9ck+KWP+nqei/Gq5aIjiUxFqt |
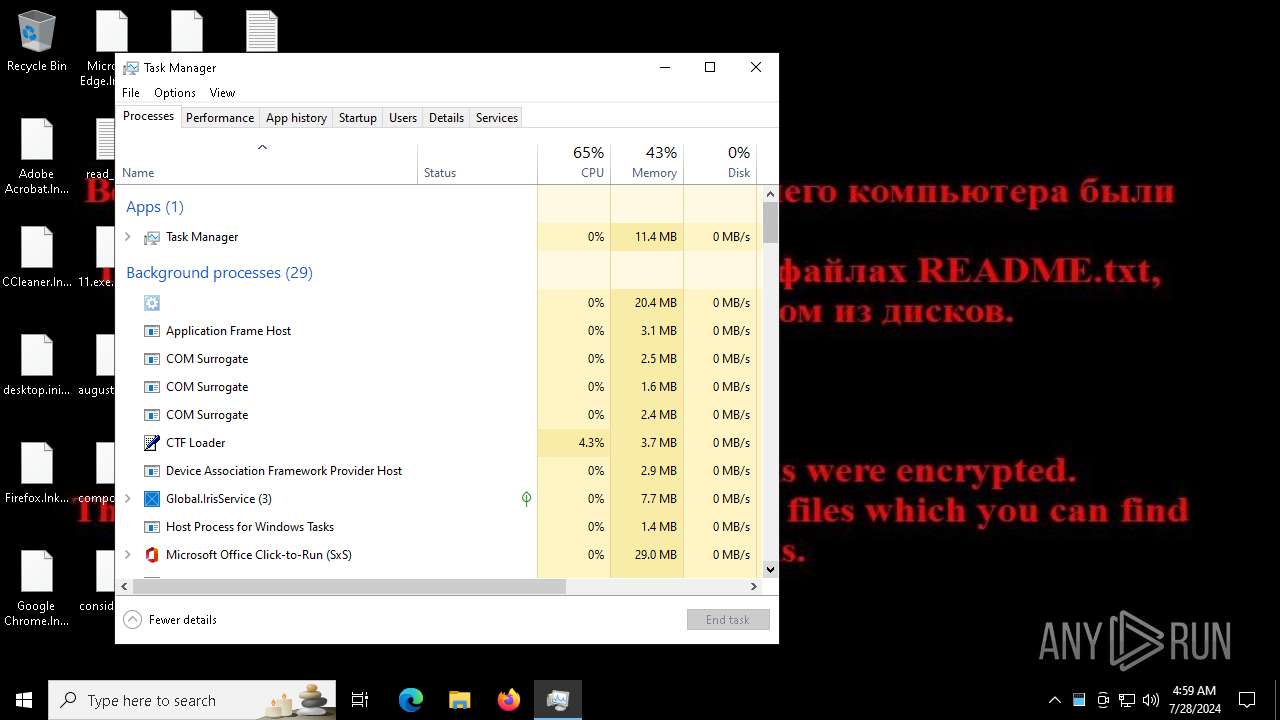
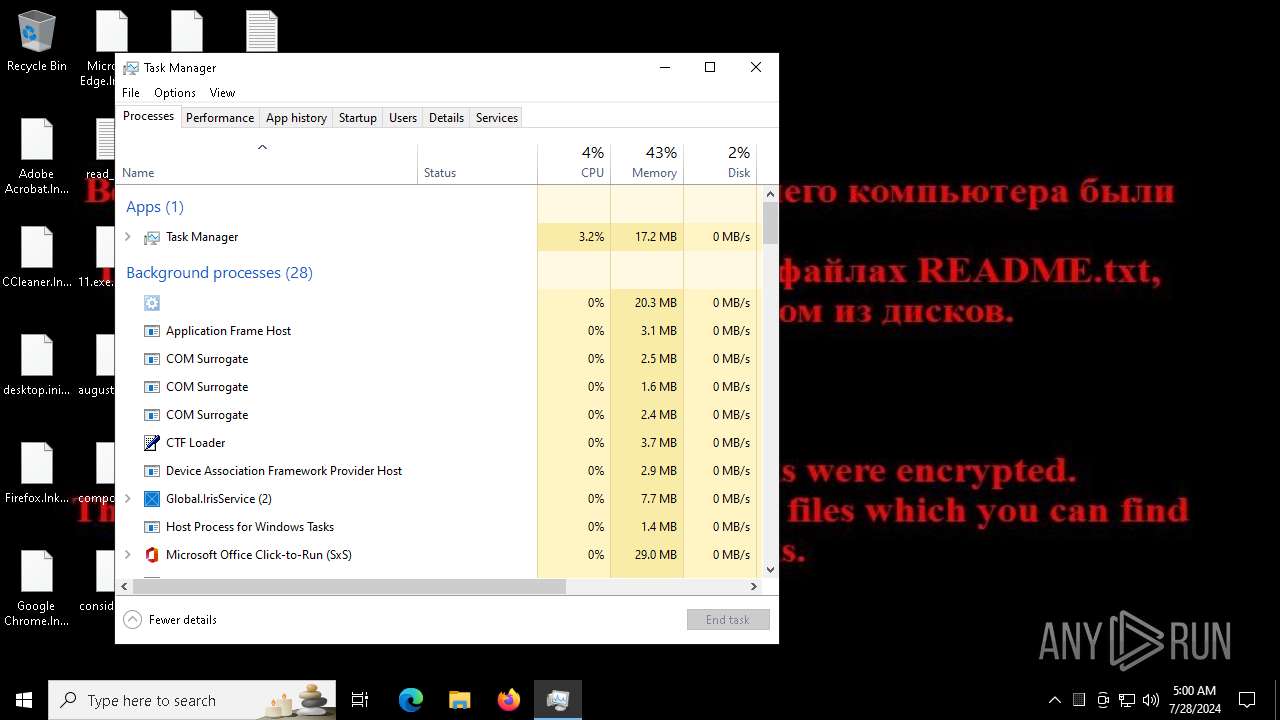
MALICIOUS
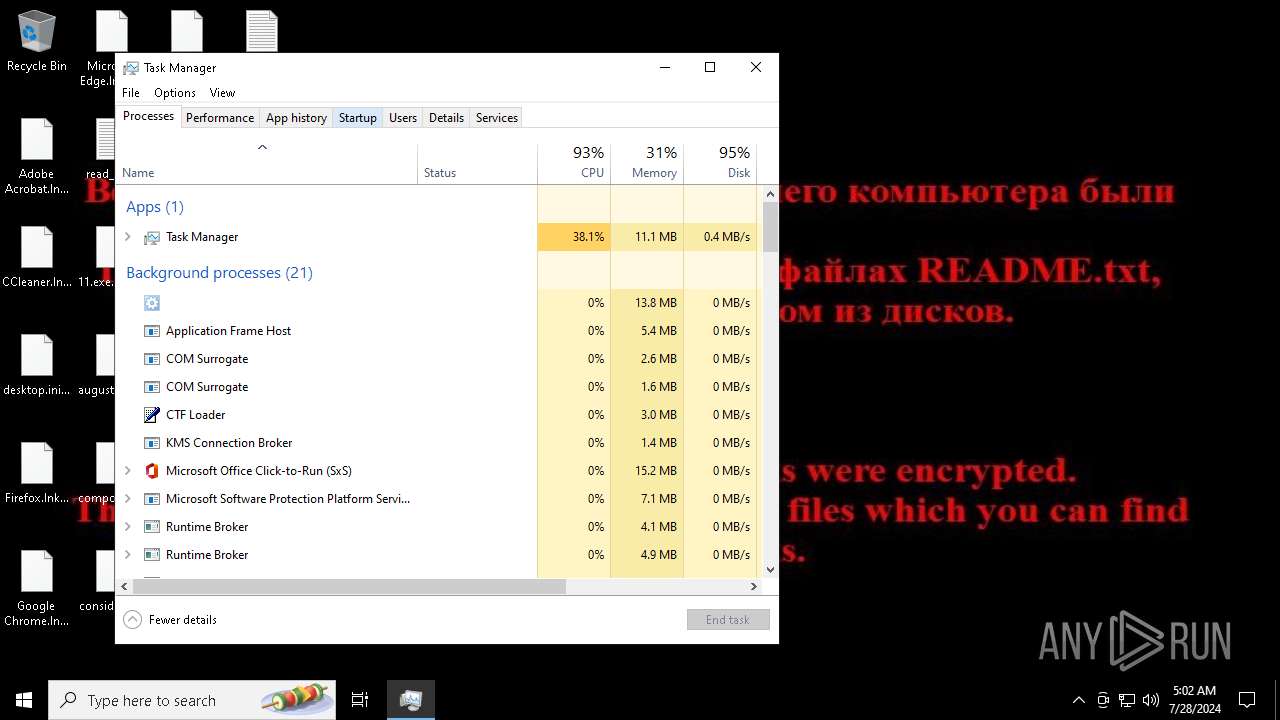
Drops the executable file immediately after the start
- 11.exe (PID: 6696)
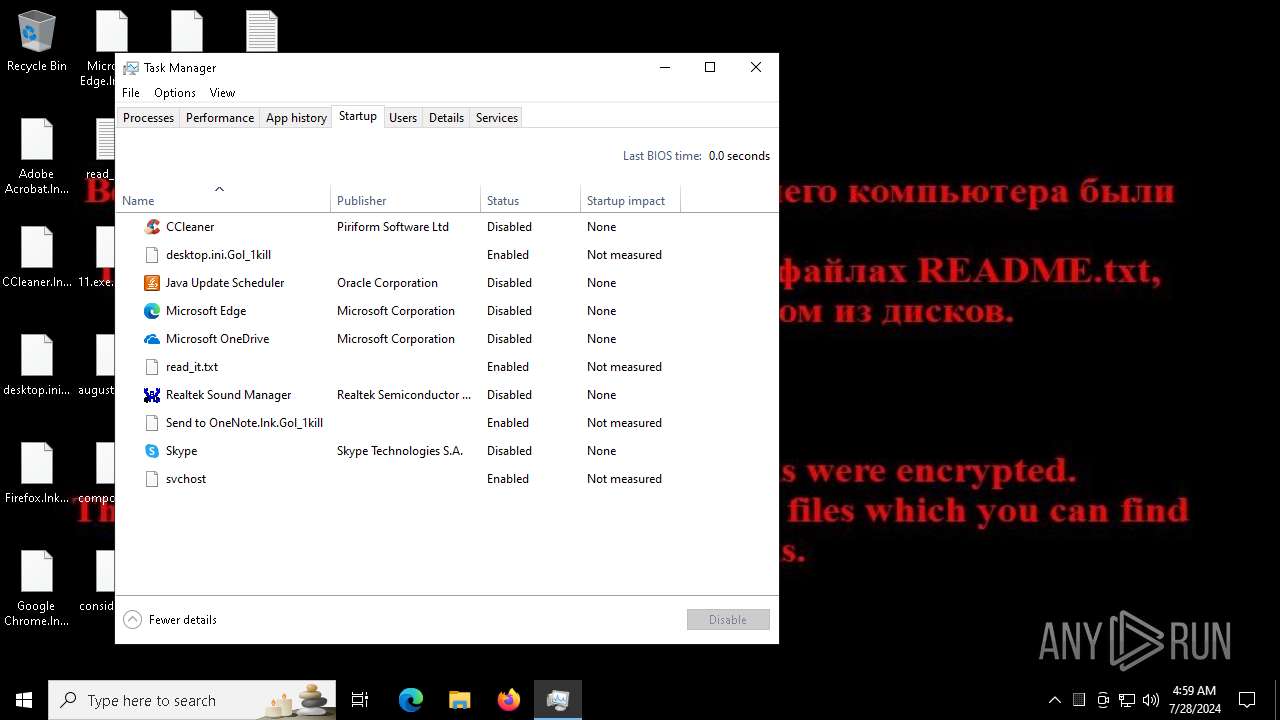
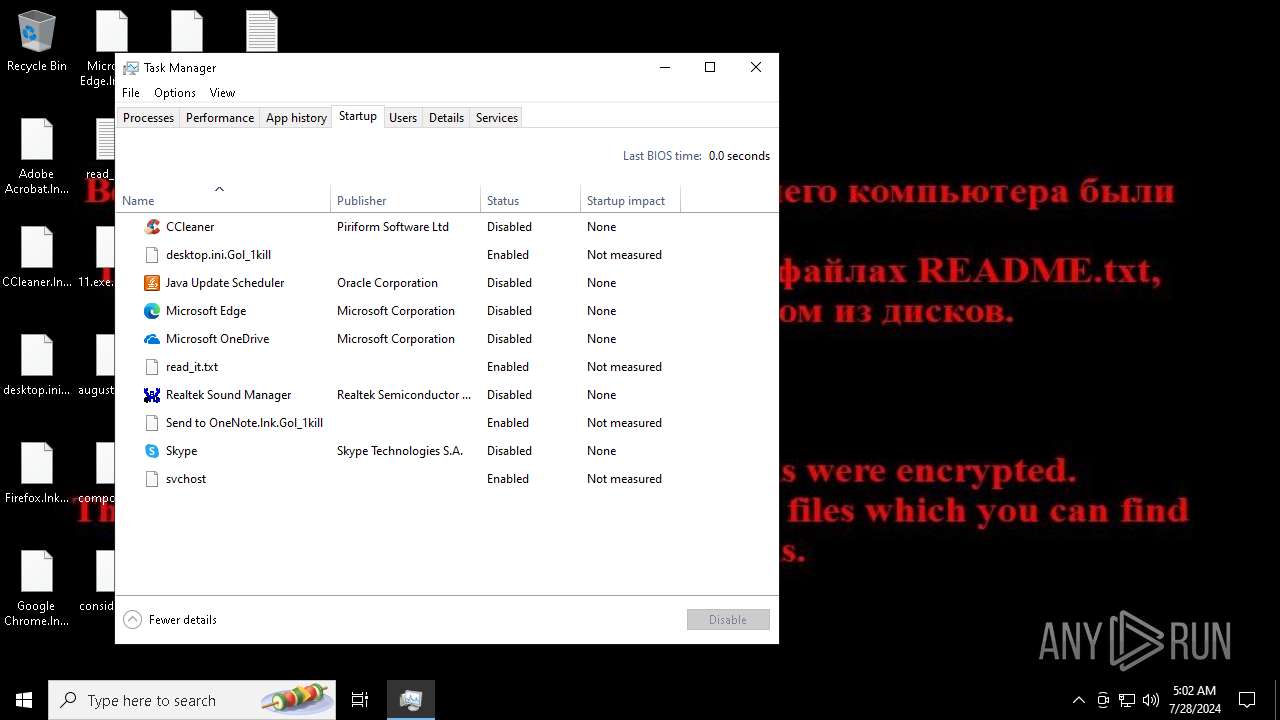
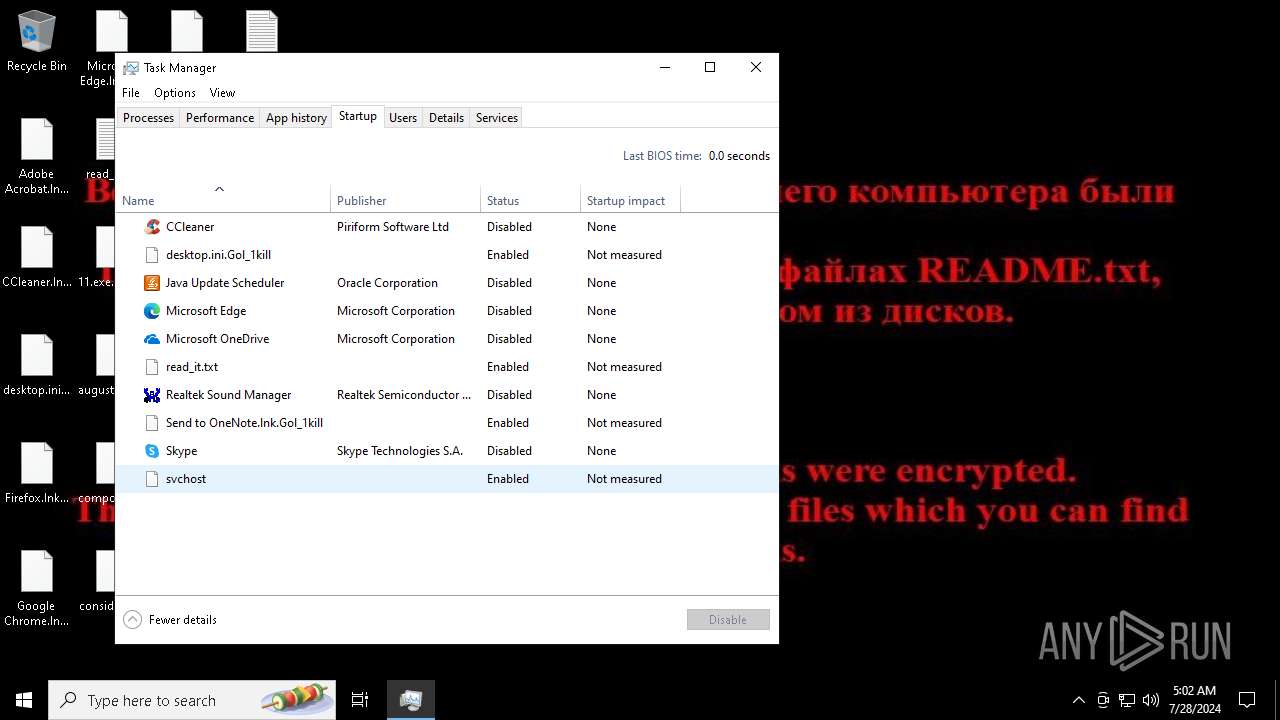
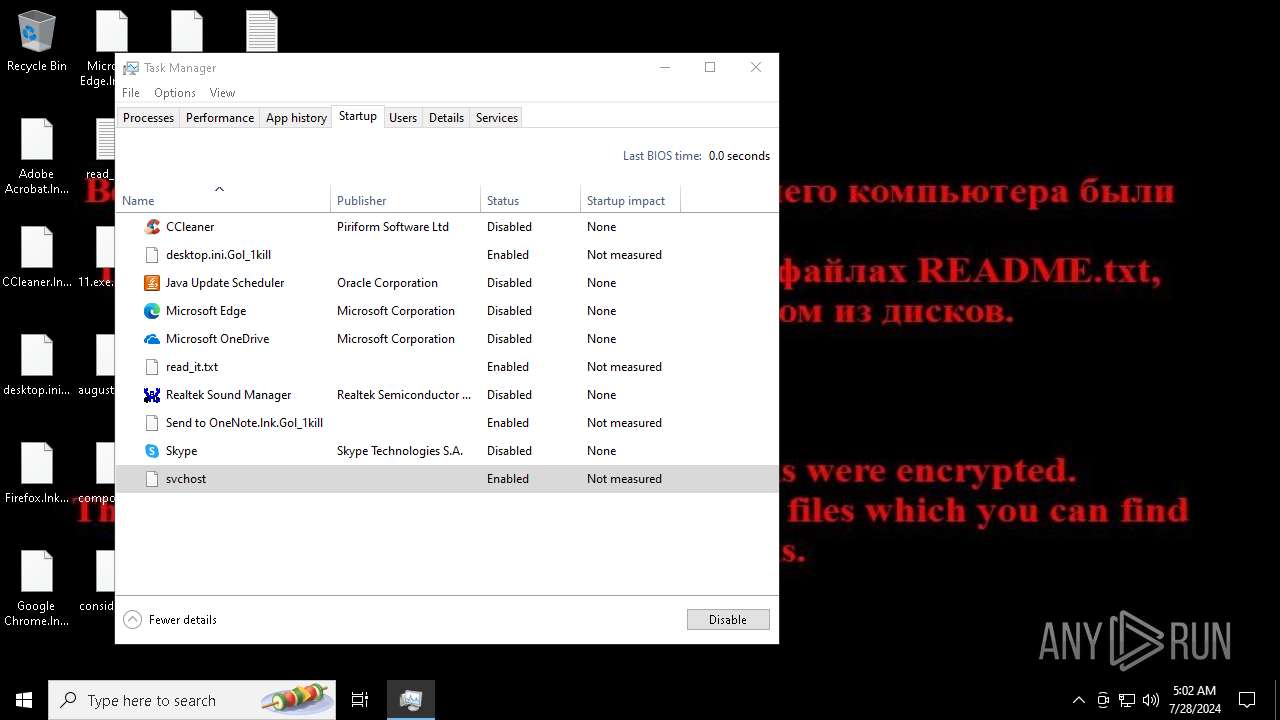
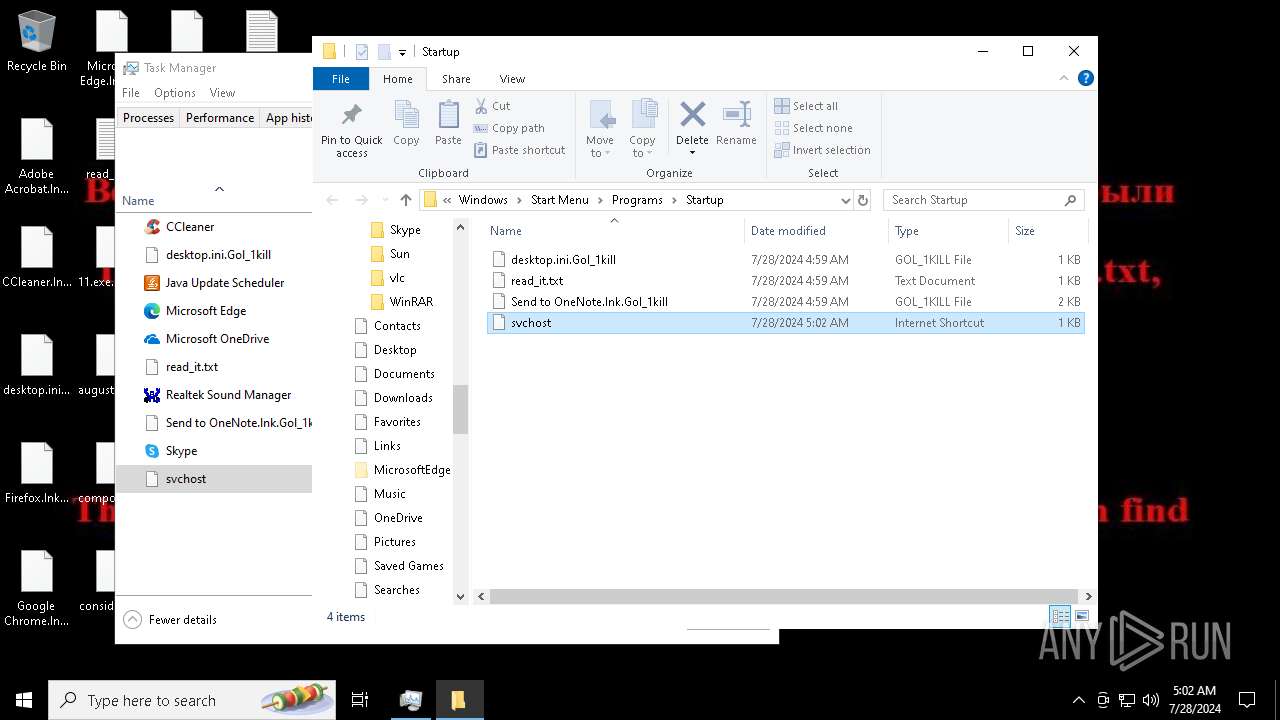
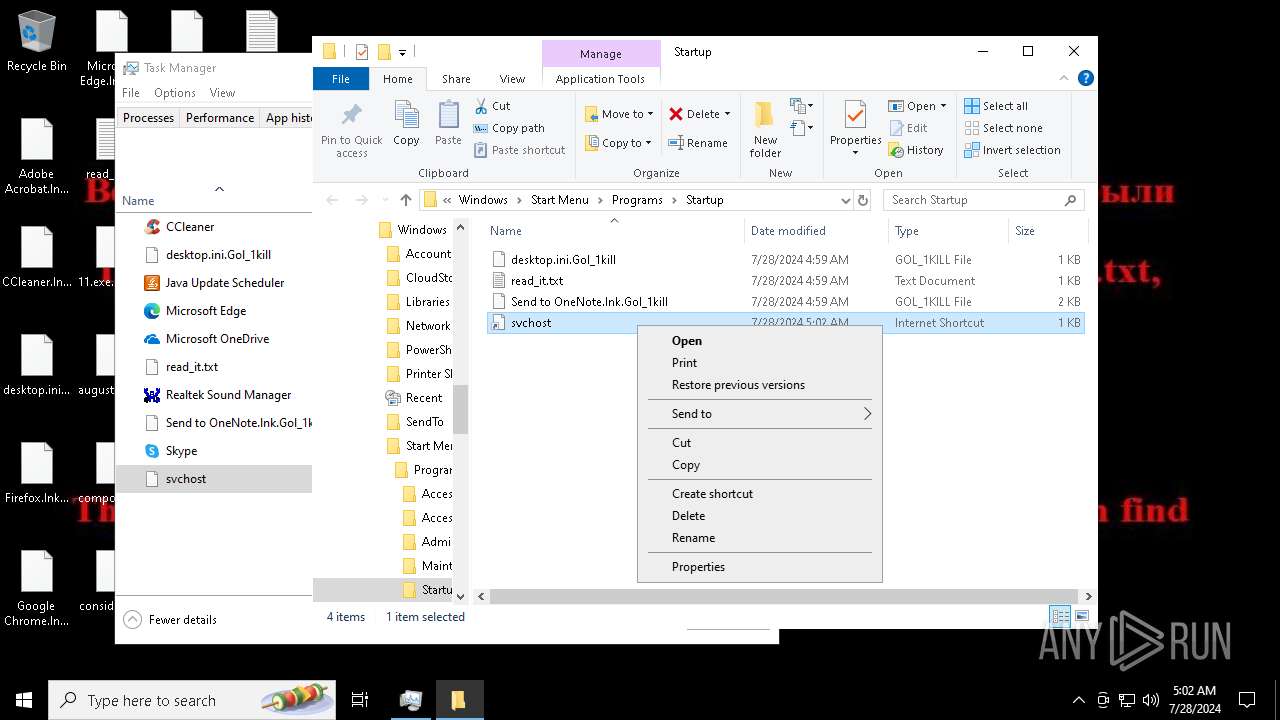
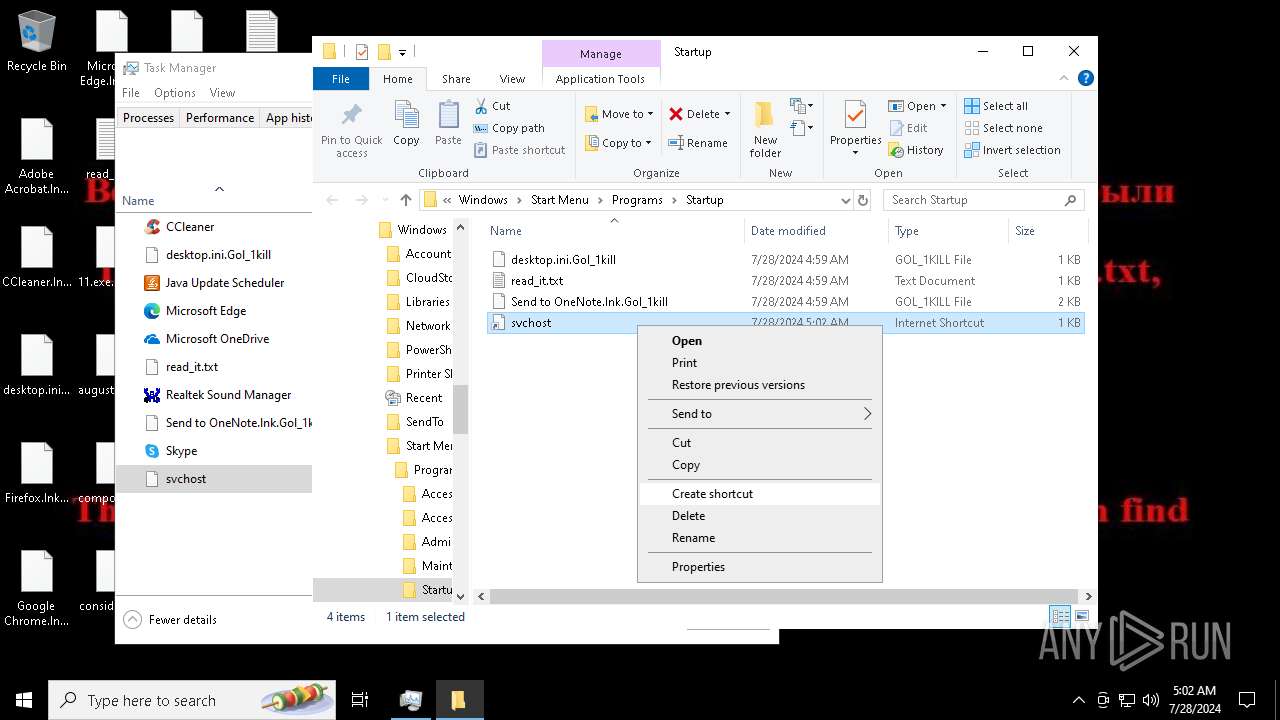
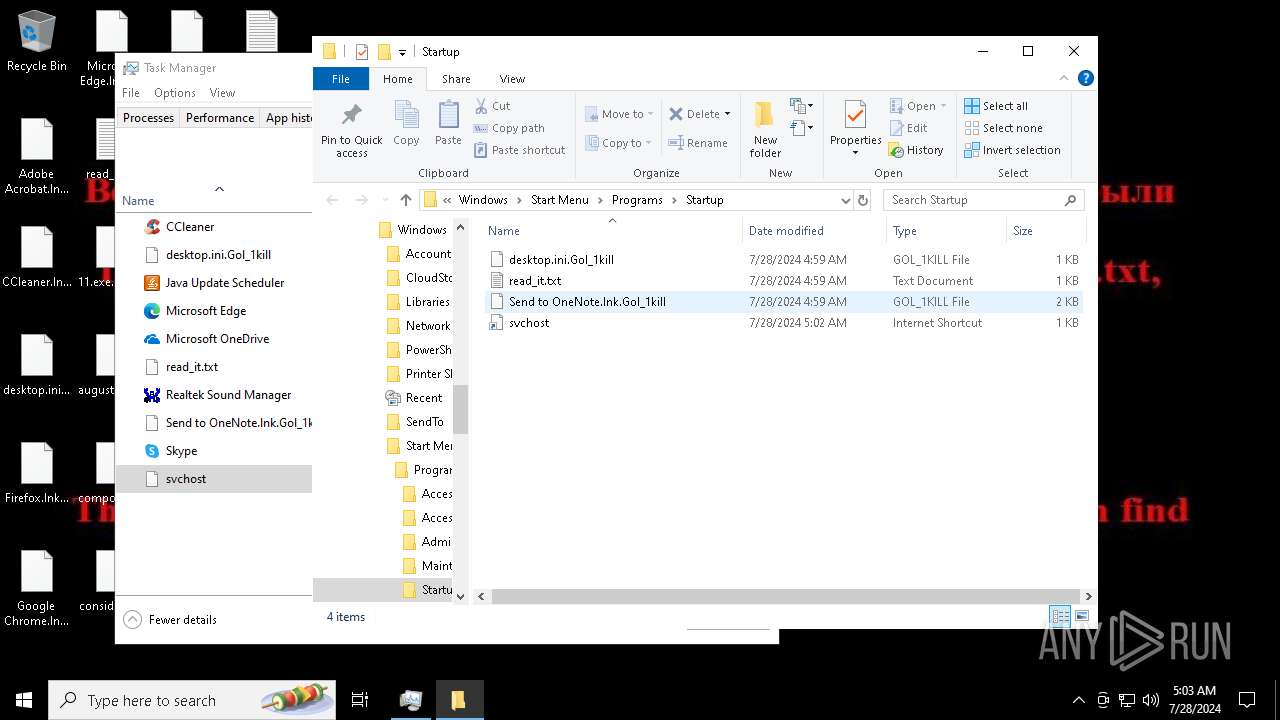
Create files in the Startup directory
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
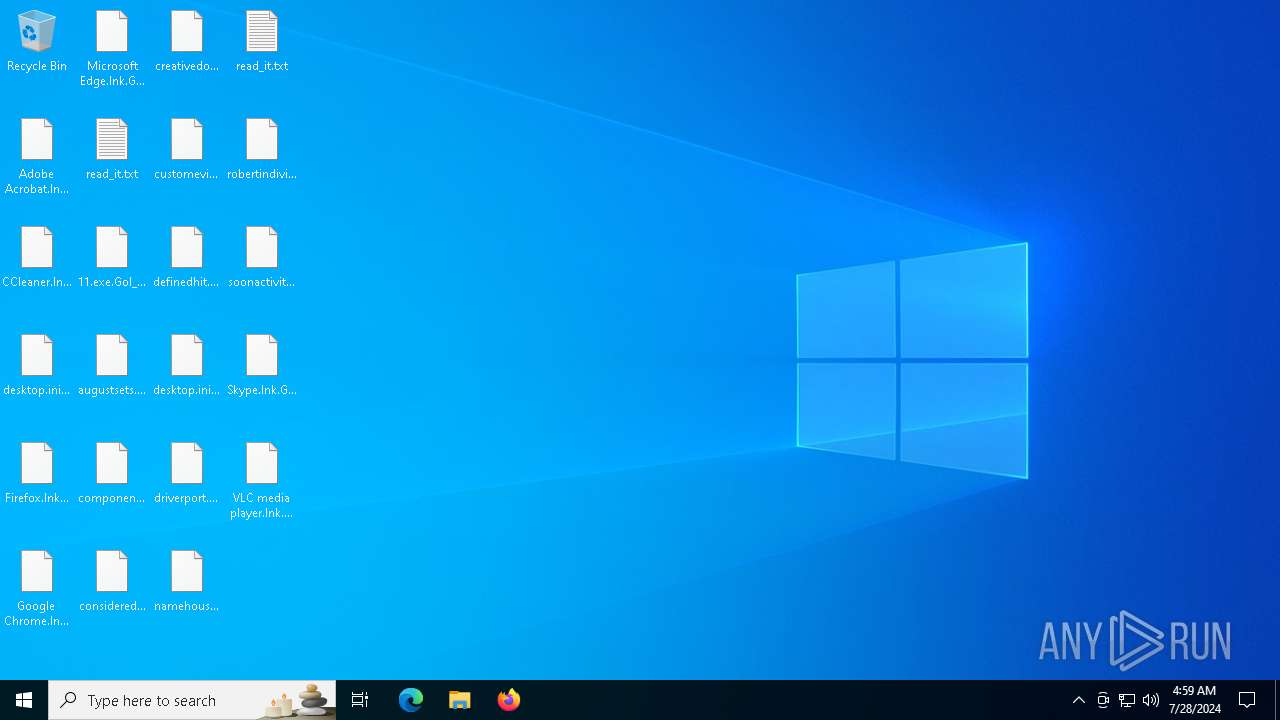
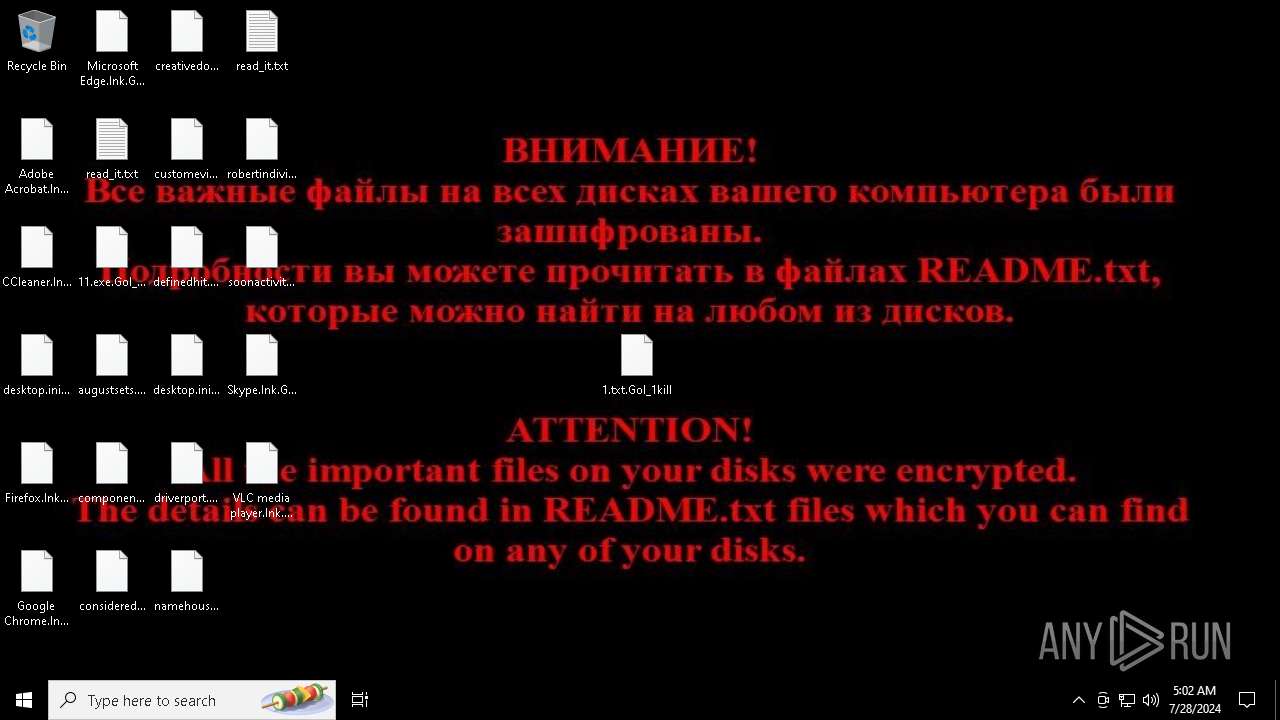
Renames files like ransomware
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
CHAOS has been detected (YARA)
- svchost.exe (PID: 7396)
Deletes shadow copies
- cmd.exe (PID: 7788)
- cmd.exe (PID: 7184)
- cmd.exe (PID: 6024)
- cmd.exe (PID: 5948)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 8088)
- cmd.exe (PID: 5336)
Actions looks like stealing of personal data
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
SUSPICIOUS
Starts itself from another location
- 11.exe (PID: 6696)
Executable content was dropped or overwritten
- 11.exe (PID: 6696)
The process creates files with name similar to system file names
- 11.exe (PID: 6696)
Reads security settings of Internet Explorer
- 11.exe (PID: 6696)
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Reads the date of Windows installation
- 11.exe (PID: 6696)
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Write to the desktop.ini file (may be used to cloak folders)
- svchost.exe (PID: 7396)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Executes as Windows Service
- VSSVC.exe (PID: 7876)
- wbengine.exe (PID: 3384)
- vds.exe (PID: 2492)
Found regular expressions for crypto-addresses (YARA)
- svchost.exe (PID: 7396)
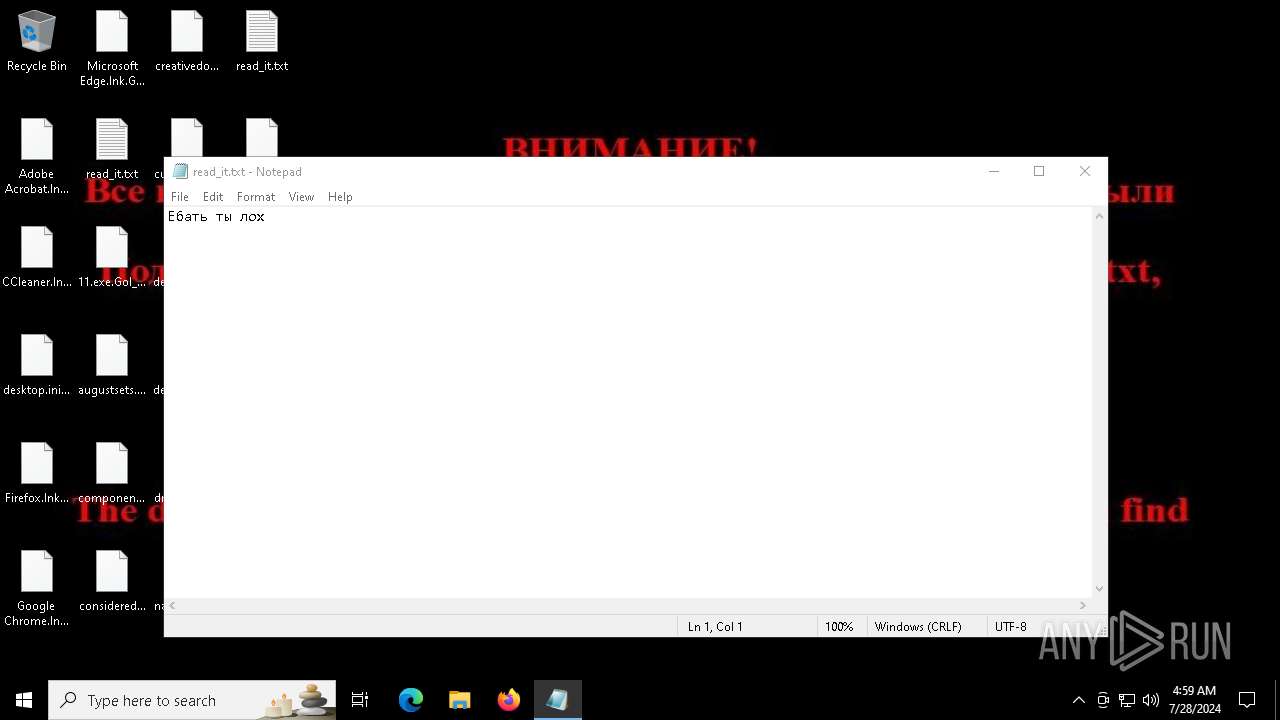
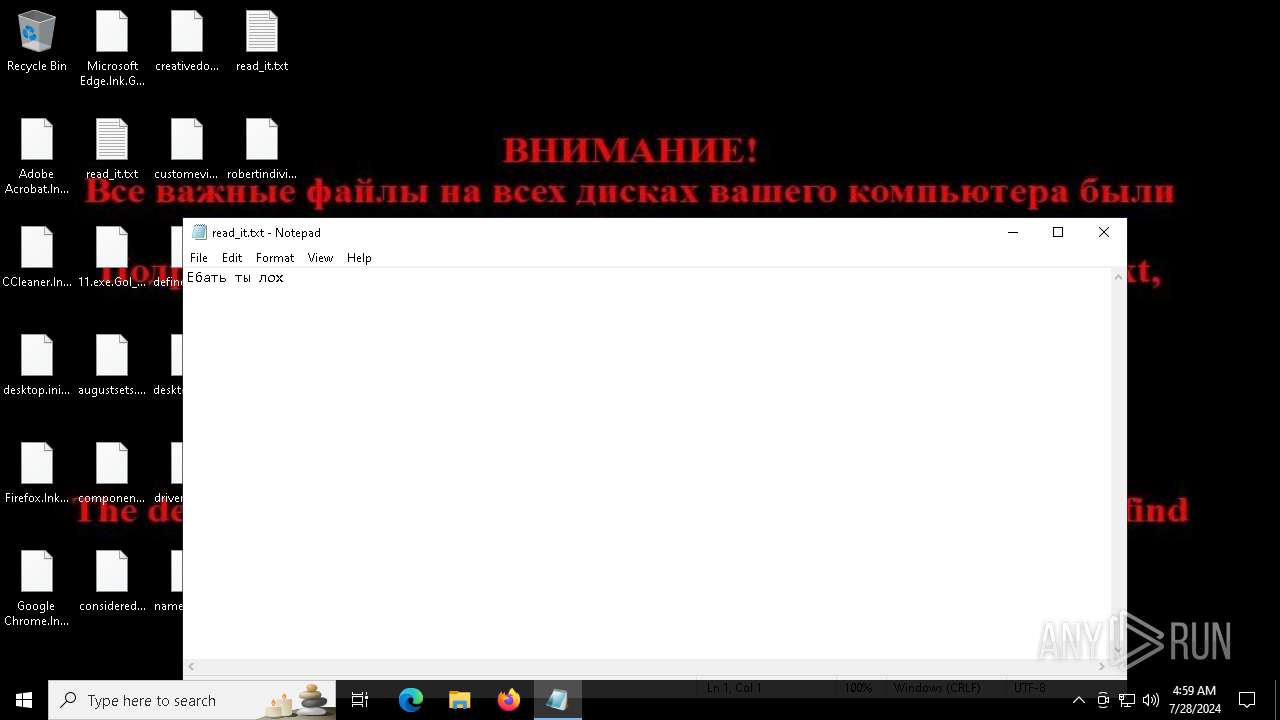
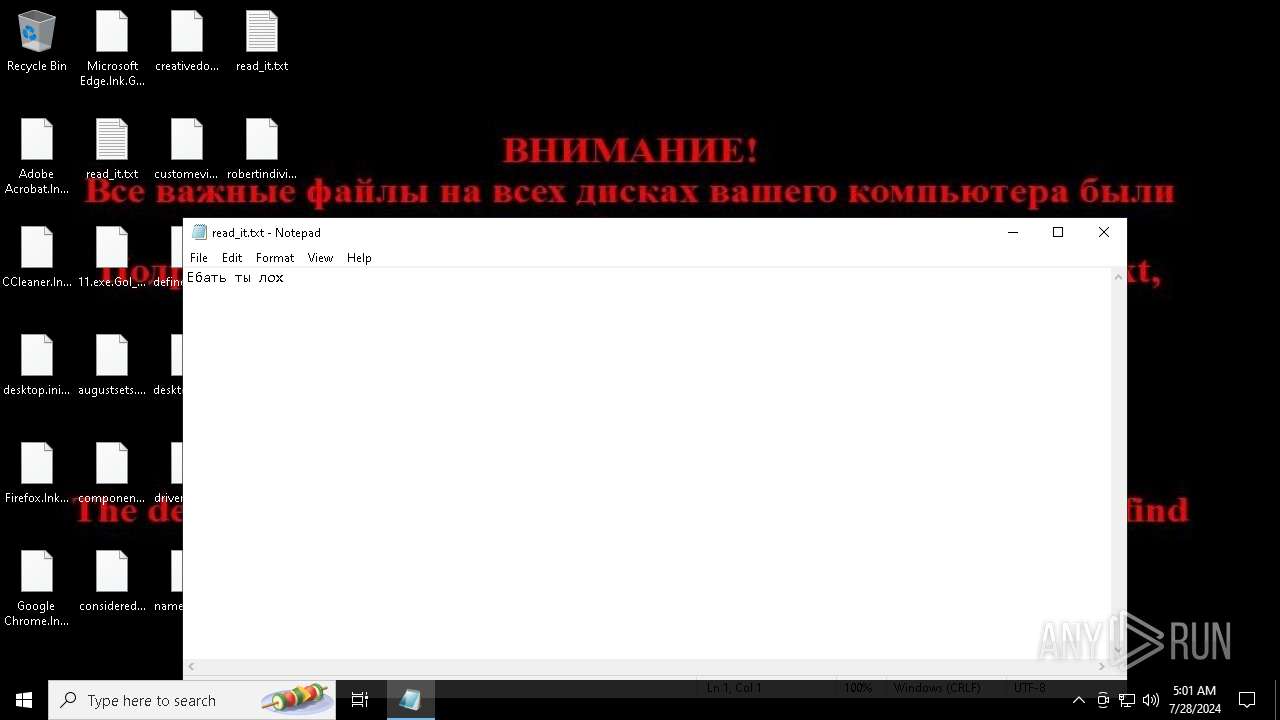
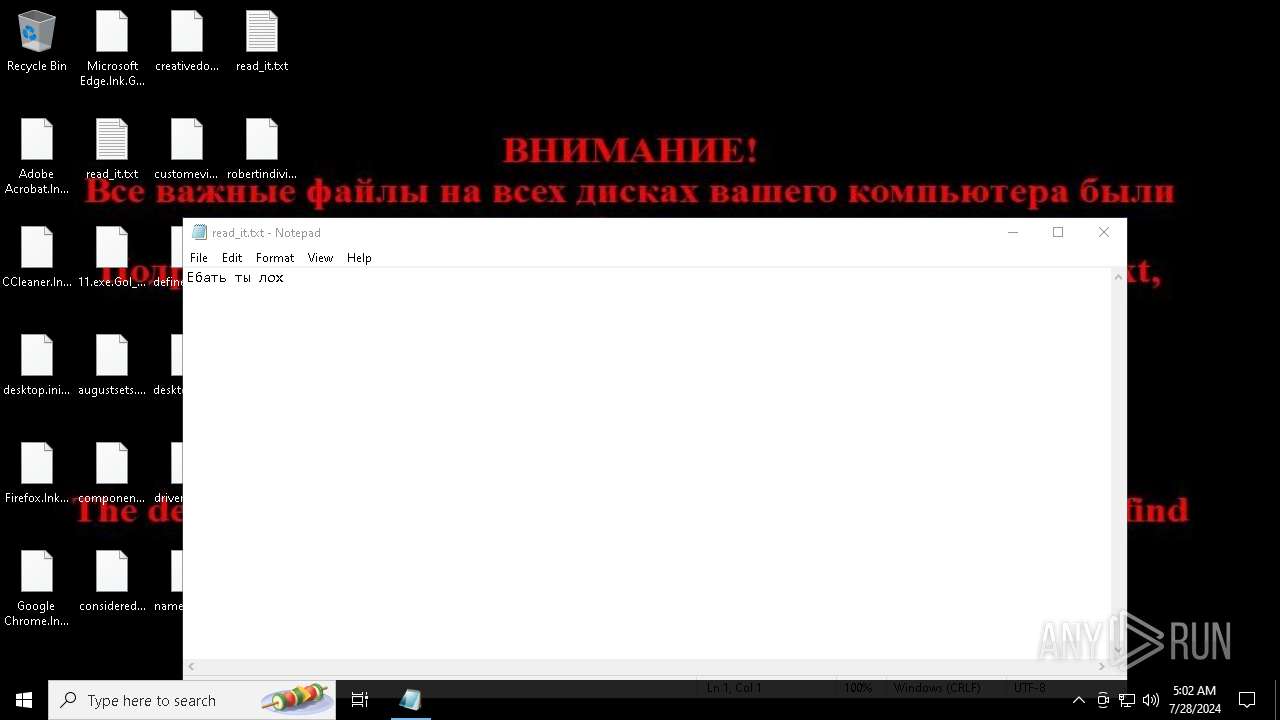
Start notepad (likely ransomware note)
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4164)
INFO
Creates files or folders in the user directory
- 11.exe (PID: 6696)
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Checks supported languages
- 11.exe (PID: 6696)
- svchost.exe (PID: 7396)
- PLUGScheduler.exe (PID: 4164)
- svchost.exe (PID: 5712)
- svchost.exe (PID: 6696)
Reads the computer name
- 11.exe (PID: 6696)
- PLUGScheduler.exe (PID: 4164)
- svchost.exe (PID: 5712)
- svchost.exe (PID: 6696)
Process checks computer location settings
- 11.exe (PID: 6696)
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Reads the machine GUID from the registry
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7984)
- notepad.exe (PID: 464)
- Taskmgr.exe (PID: 7336)
- notepad.exe (PID: 7592)
- notepad.exe (PID: 1196)
- WMIC.exe (PID: 5924)
- notepad.exe (PID: 6064)
- Taskmgr.exe (PID: 1076)
Create files in a temporary directory
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Reads Microsoft Office registry keys
- svchost.exe (PID: 7396)
- svchost.exe (PID: 5712)
Manual execution by a user
- Taskmgr.exe (PID: 4648)
- Taskmgr.exe (PID: 7336)
- notepad.exe (PID: 7592)
- svchost.exe (PID: 5712)
- notepad.exe (PID: 1196)
- Taskmgr.exe (PID: 468)
- Taskmgr.exe (PID: 1076)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:28 04:58:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 189952 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3042e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 11.exe |
| LegalCopyright: | |
| OriginalFileName: | 11.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
314
Monitored processes
39
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 464 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\read_it.txt | C:\Windows\System32\notepad.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 468 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\read_it.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2340 | wbadmin delete catalog -quiet | C:\Windows\System32\wbadmin.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® BLB Backup Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | C:\WINDOWS\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3384 | "C:\WINDOWS\system32\wbengine.exe" | C:\Windows\System32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3848 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Boot Configuration Data Editor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 026
Read events
26 911
Write events
93
Delete events
22
Modification events
| (PID) Process: | (6696) 11.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6696) 11.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6696) 11.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6696) 11.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (7396) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7396) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7396) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7396) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (8144) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (8144) bcdedit.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Description |
| Operation: | write | Name: | FirmwareModified |
Value: 1 | |||
Executable files
1
Suspicious files
23
Text files
622
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7396 | svchost.exe | C:\Users\admin\Desktop\11.exe | text | |
MD5:C2AACBFB823EE7EDD3A66D9AD2342295 | SHA256:B60CBBA2BACEA667EA19AF859D2556F898BD07D78CE7DD1EBEF779EF8A32D699 | |||
| 6696 | 11.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:99177A95442CB3CD77F9359C948C9FBE | SHA256:612EB5C3269A264D1516904E24FE1BDFA17CB8A06441F03C483216EB52A9F526 | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\augustsets.rtf | text | |
MD5:34270D3919013EE8AA9436E671A91A72 | SHA256:0B1D4EB31BA764E566AF7FAB67EEED643C95DD5BC6FDC724C47FFDBAD9E5C1E2 | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\componentsonly.jpg | text | |
MD5:4A873C2C3C1A1F4FE01F87C382A72D79 | SHA256:C42DFC1FBD6C0FEFD25A4BAF5253C5F3221B061BA1FCA5060F12BEB9B095CD9A | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\driverport.jpg | text | |
MD5:4745C72057BC17C2683F16EB1404672F | SHA256:A8F761E8CFA11AA435840D361D16B4742FCA8766811AB6E00CB5DB528C4E66F8 | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\read_it.txt | text | |
MD5:FD81F4F12C2E9ECC21818DE1C27A84F0 | SHA256:AD8408438868D3A62F80E9BE24839DF806D7196358C71CC9A7340486A528639C | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\desktop.ini.Gol_1kill | text | |
MD5:2F6004D8F7AD0E840C8486EFEF28C406 | SHA256:76EB4A95EF679D059FA41465F444AC7400C83AB0FE87A24A456EEEEE49E60D81 | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\creativedownload.rtf | text | |
MD5:32FB6DA2156FE67F27CAEA916AEDB930 | SHA256:8C6F18C36052E7811BA6F8E74F6EBF4AC59562E8E0DCD4531E1F65018FA6FE10 | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\consideredapple.jpg | text | |
MD5:763430154CE49957F495C1359F8502DF | SHA256:06D9BA77855CB4081A863C939CB3BF459175482785ACFE26EA1CDDD18143DCB8 | |||
| 7396 | svchost.exe | C:\Users\admin\Desktop\augustsets.rtf.Gol_1kill | text | |
MD5:34270D3919013EE8AA9436E671A91A72 | SHA256:0B1D4EB31BA764E566AF7FAB67EEED643C95DD5BC6FDC724C47FFDBAD9E5C1E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
53
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2444 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5168 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5368 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 92.123.104.33:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5692 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6396 | slui.exe | 20.83.72.98:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
s-ring.msedge.net |
| unknown |
Threats
Process | Message |
|---|---|
wbadmin.exe | Invalid parameter passed to C runtime function.
|