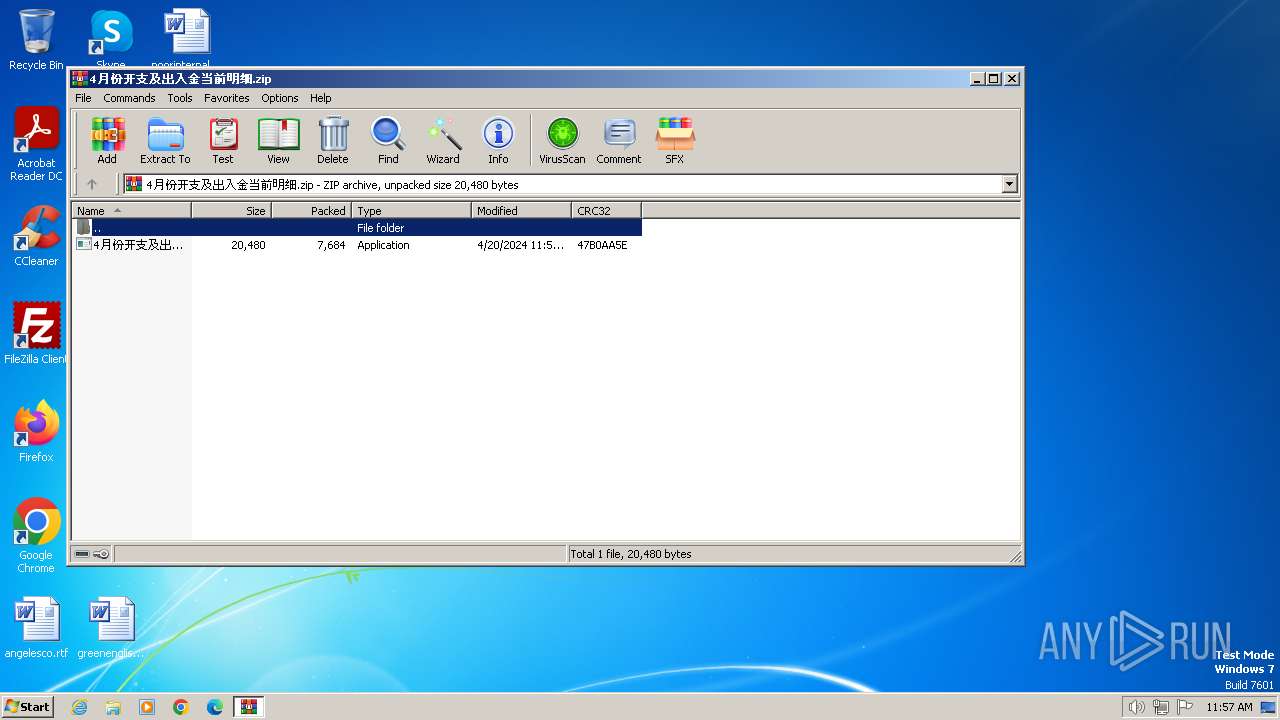
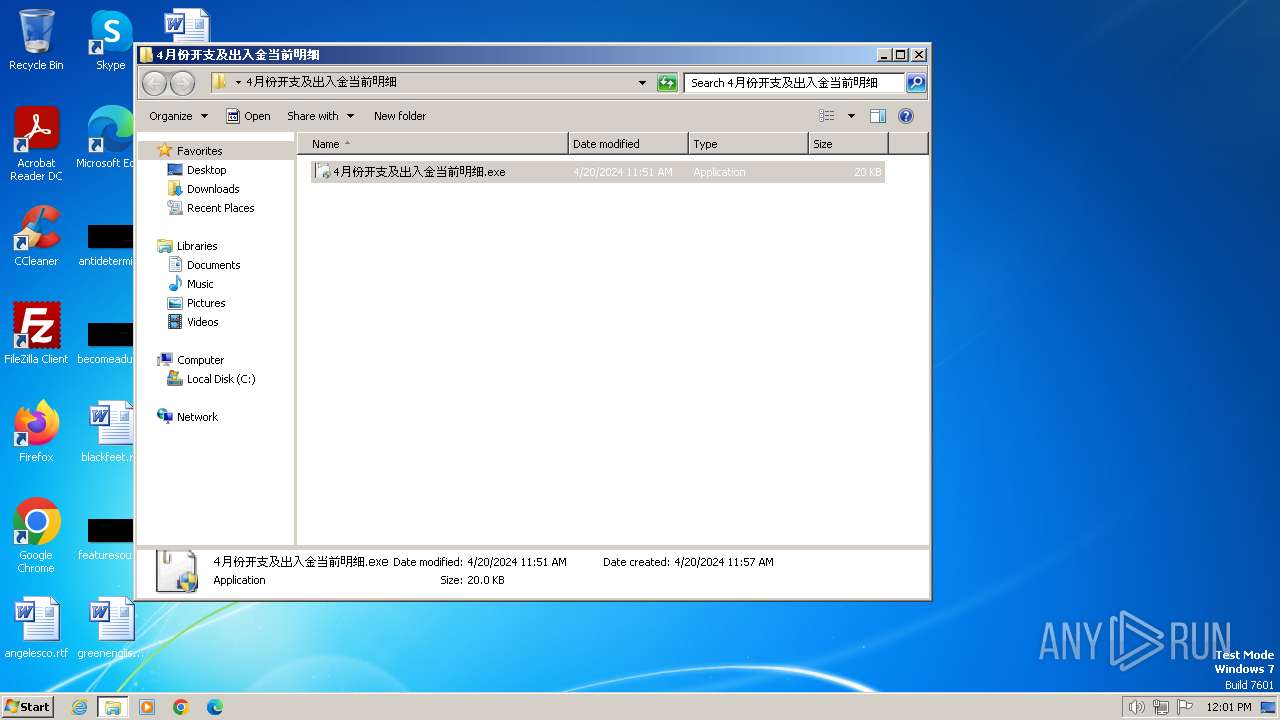
| File name: | 4月份开支及出入金当前明细.zip |
| Full analysis: | https://app.any.run/tasks/62fa30ba-5aeb-4a6a-bd5d-b9b5e8a22698 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | April 20, 2024, 10:57:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 7F30D82EF794A2BA60869D0EDF42B7EA |
| SHA1: | ECA806CA4A92F0E5E349DA701E4971E7BA639336 |
| SHA256: | 60BB79E9D40A94767BE692CFC9CF553C980C2857294F544E520CAACA147B8F55 |
| SSDEEP: | 192:q3kQVWRbI2c5kX0wRIeGdmAvYNsty21HRkCHzbHa/f5qpllgqLDUxjVtrIRk:Cu3SkXBqNRg23HTb65Pqnk39 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3416)
- 4月份开支及出入金当前明细.exe (PID: 3636)
Adds path to the Windows Defender exclusion list
- 4月份开支及出入金当前明细.exe (PID: 3636)
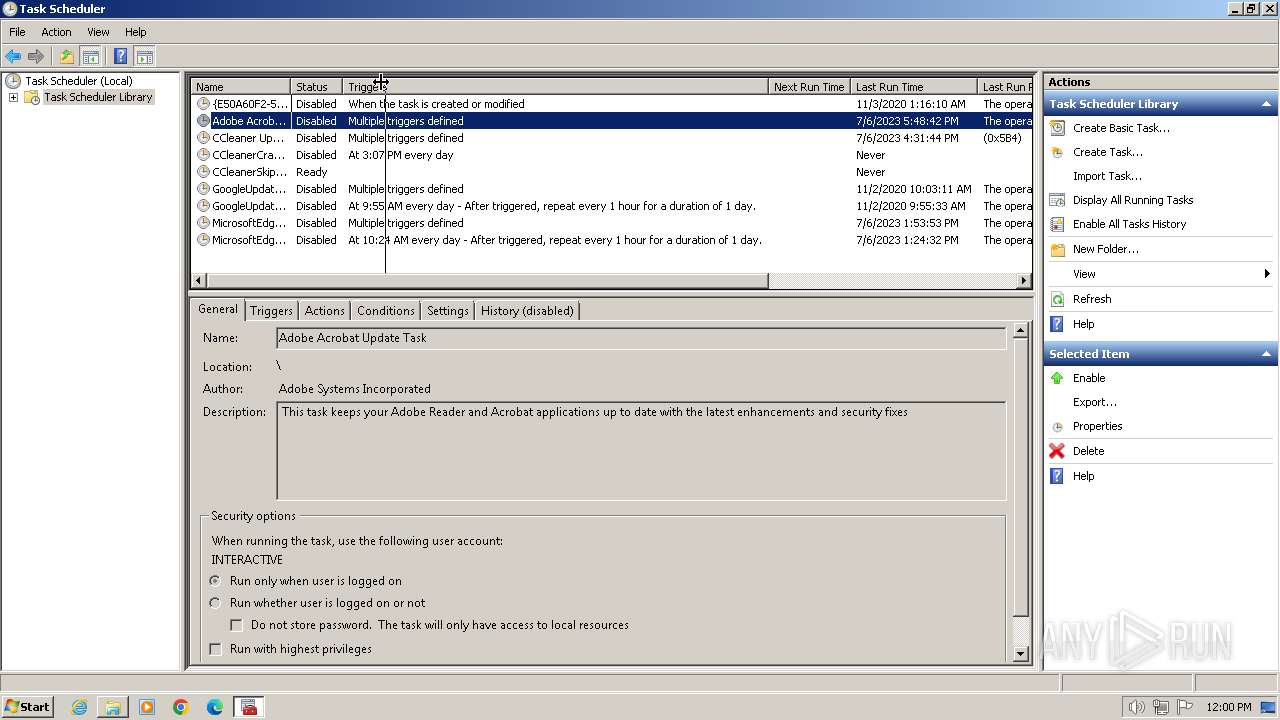
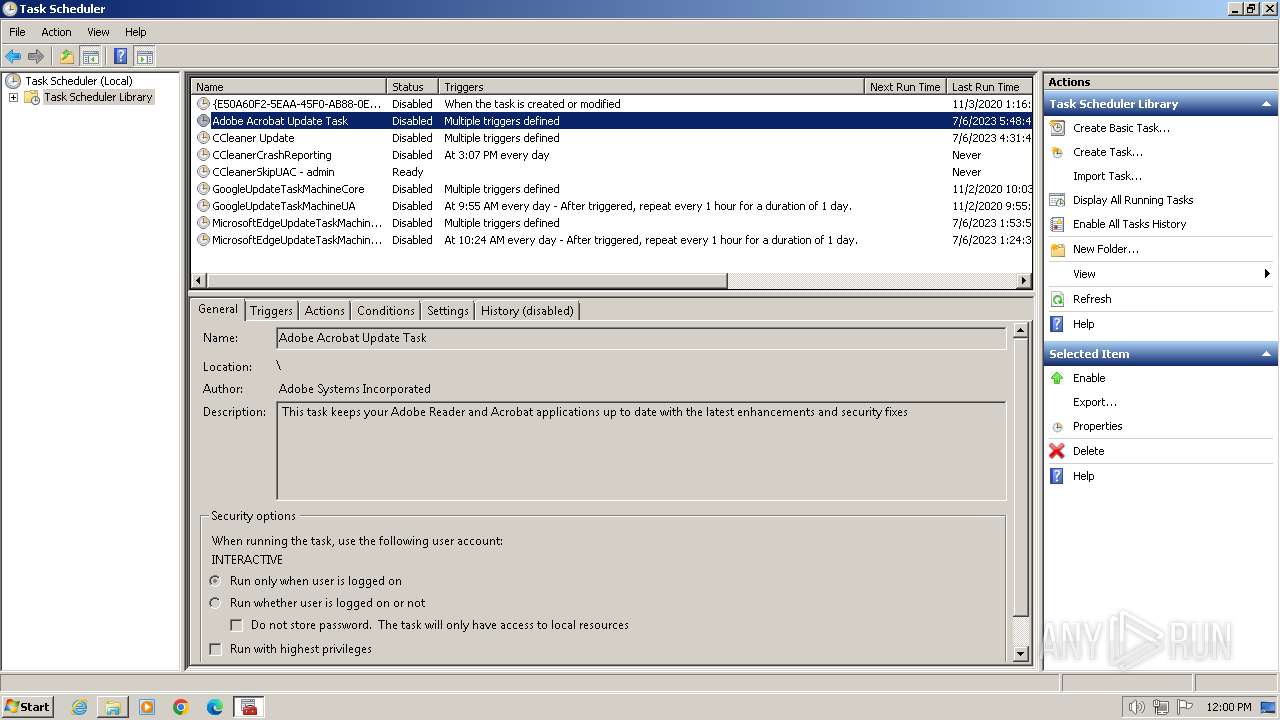
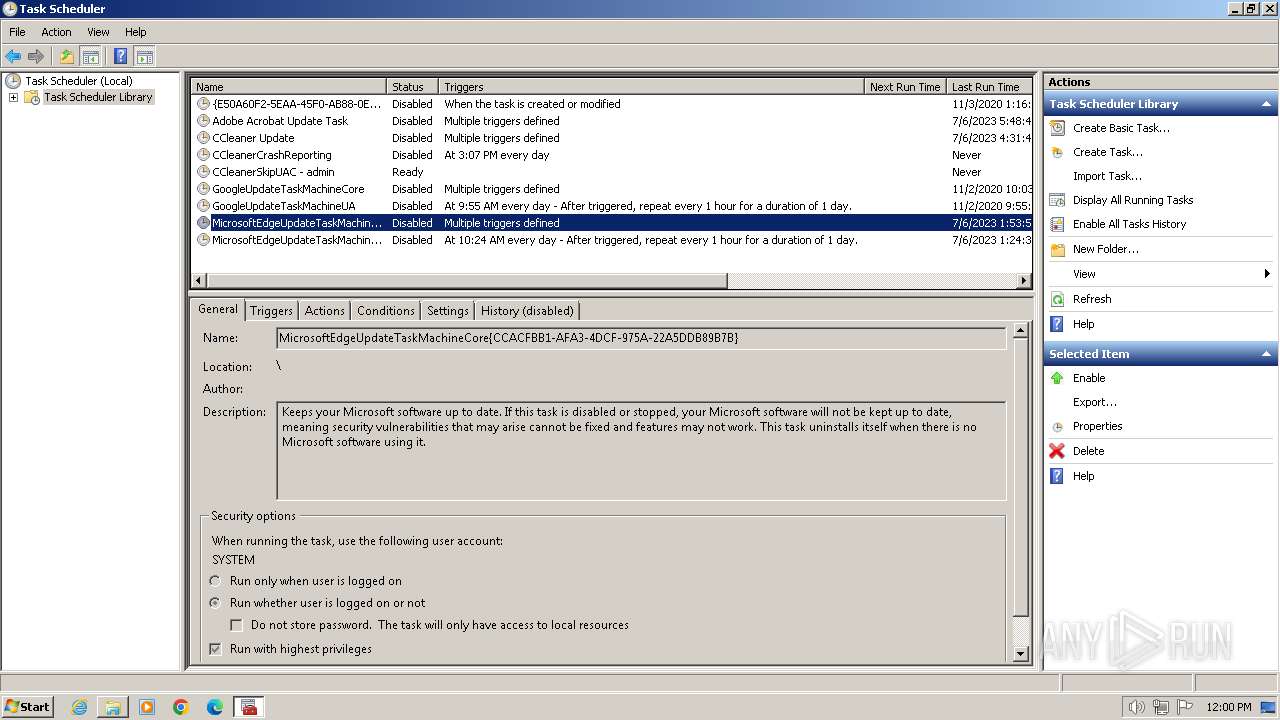
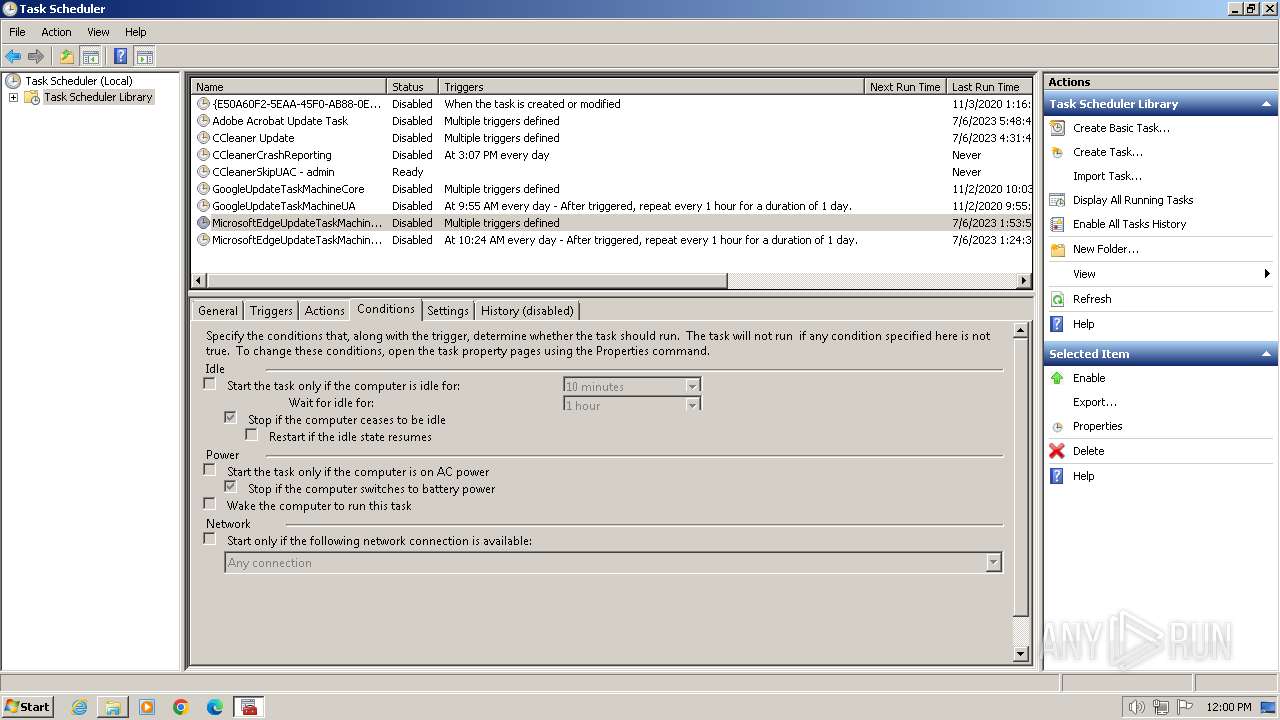
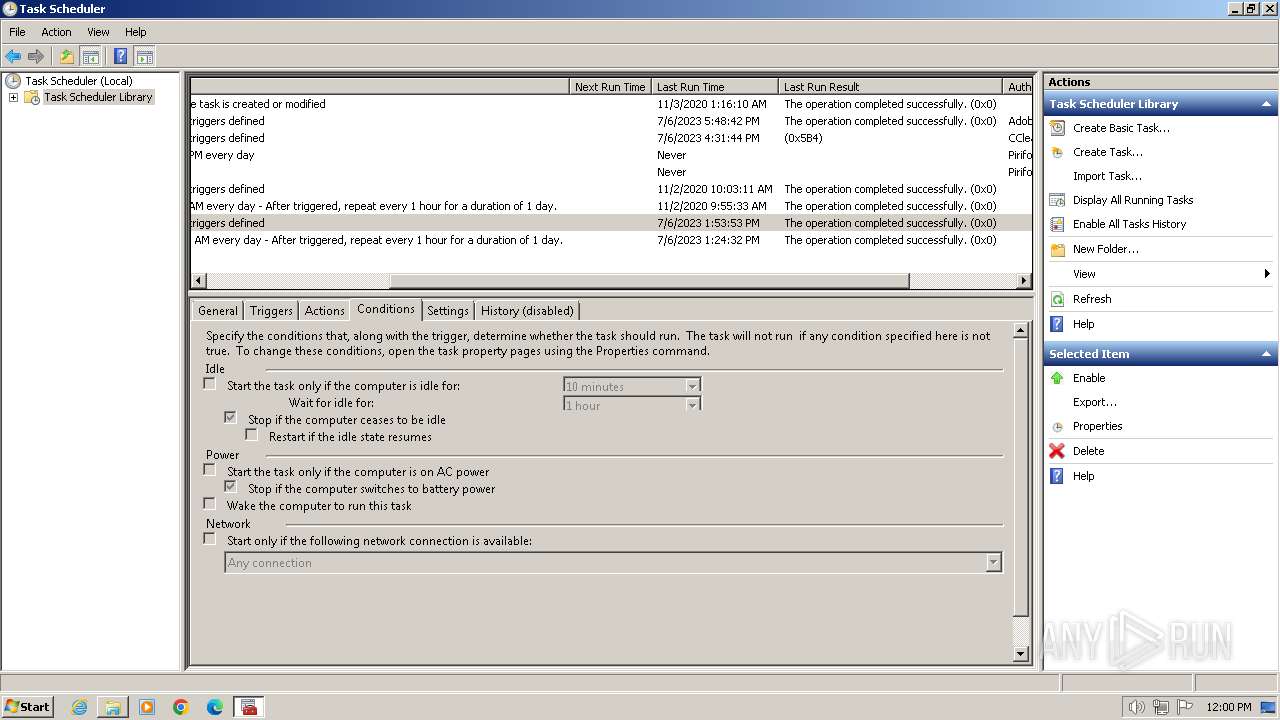
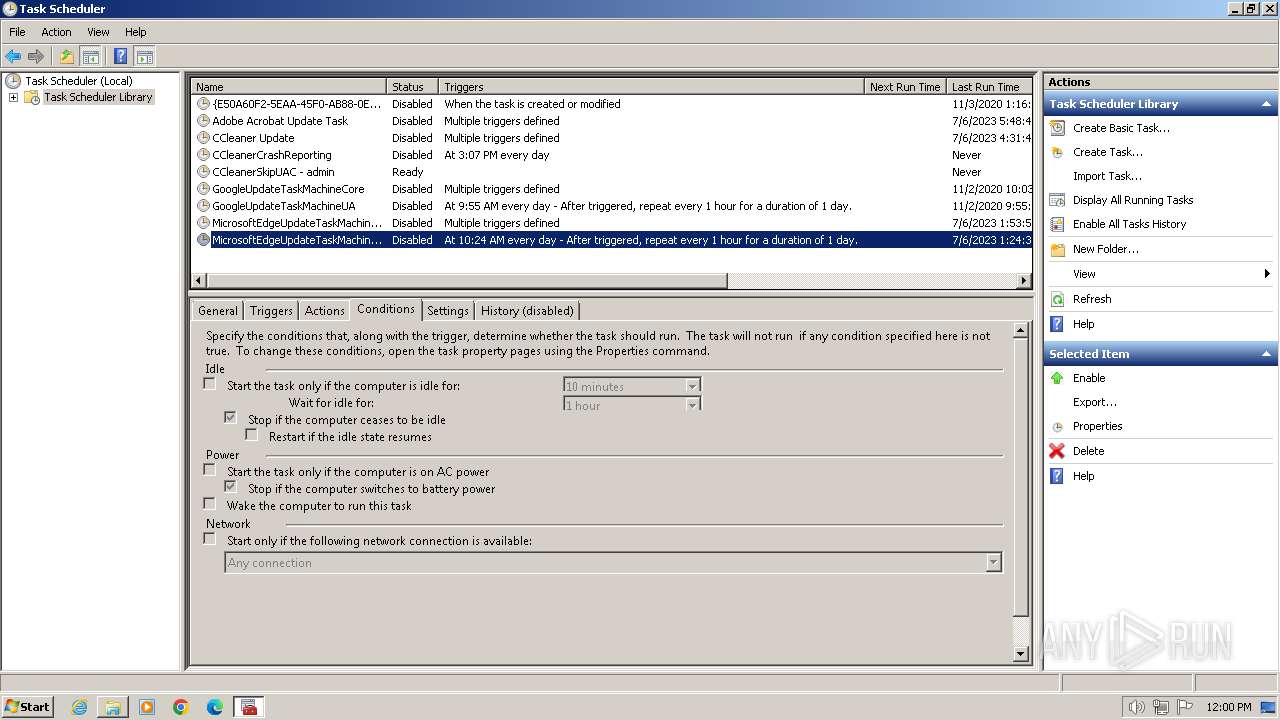
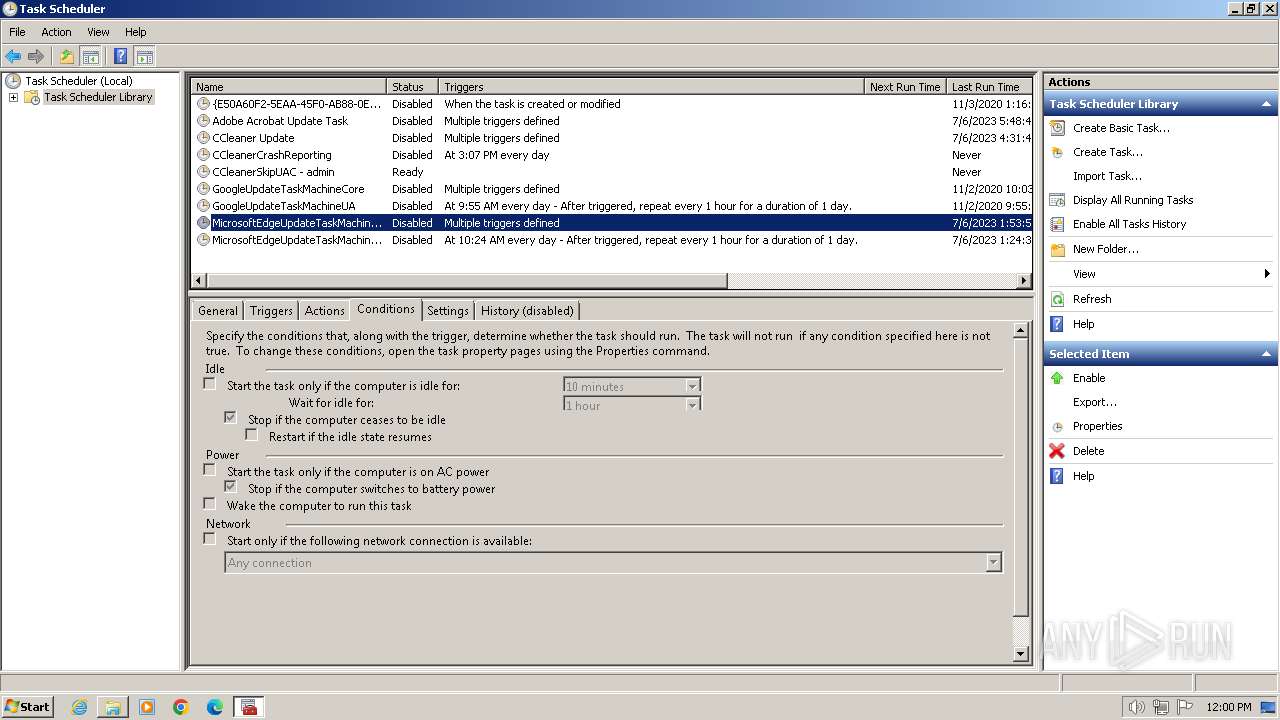
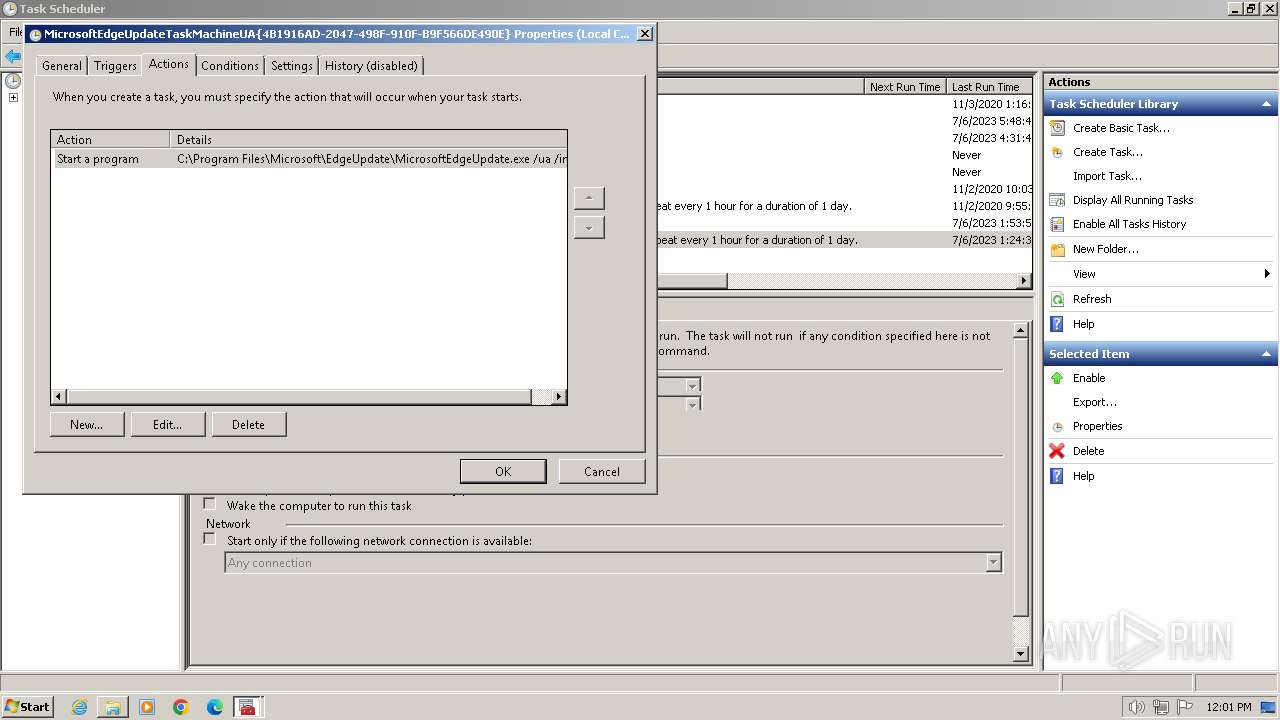
Changes the autorun value in the registry
- 4月份开支及出入金当前明细.exe (PID: 3636)
SILVERFOX has been detected (SURICATA)
- dllhost.exe (PID: 1492)
SUSPICIOUS
Executable content was dropped or overwritten
- 4月份开支及出入金当前明细.exe (PID: 3636)
The process bypasses the loading of PowerShell profile settings
- 4月份开支及出入金当前明细.exe (PID: 3636)
The process creates files with name similar to system file names
- 4月份开支及出入金当前明细.exe (PID: 3636)
Script adds exclusion path to Windows Defender
- 4月份开支及出入金当前明细.exe (PID: 3636)
Starts POWERSHELL.EXE for commands execution
- 4月份开支及出入金当前明细.exe (PID: 3636)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3404)
- notepad.exe (PID: 2172)
- dllhost.exe (PID: 1492)
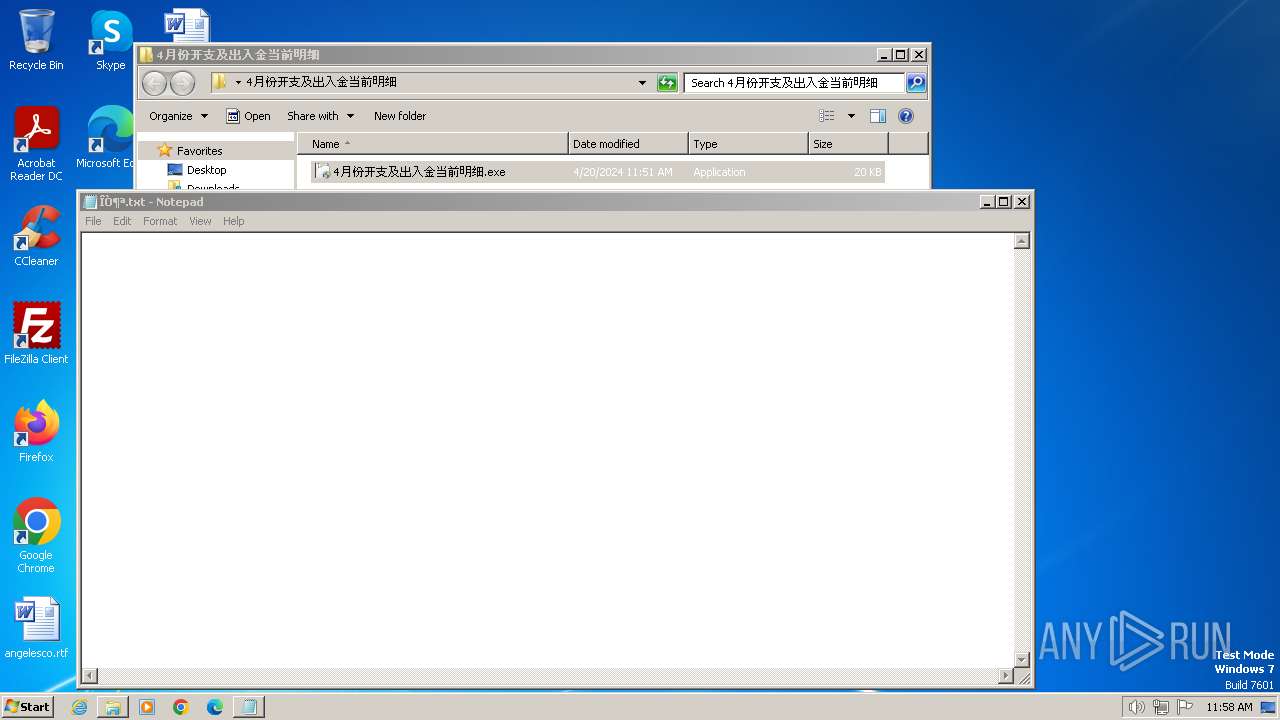
Start notepad (likely ransomware note)
- 4月份开支及出入金当前明细.exe (PID: 3636)
Reads security settings of Internet Explorer
- 4月份开支及出入金当前明细.exe (PID: 3636)
Reads the Internet Settings
- 4月份开支及出入金当前明细.exe (PID: 3636)
- powershell.exe (PID: 3404)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3404)
Connects to unusual port
- dllhost.exe (PID: 1492)
INFO
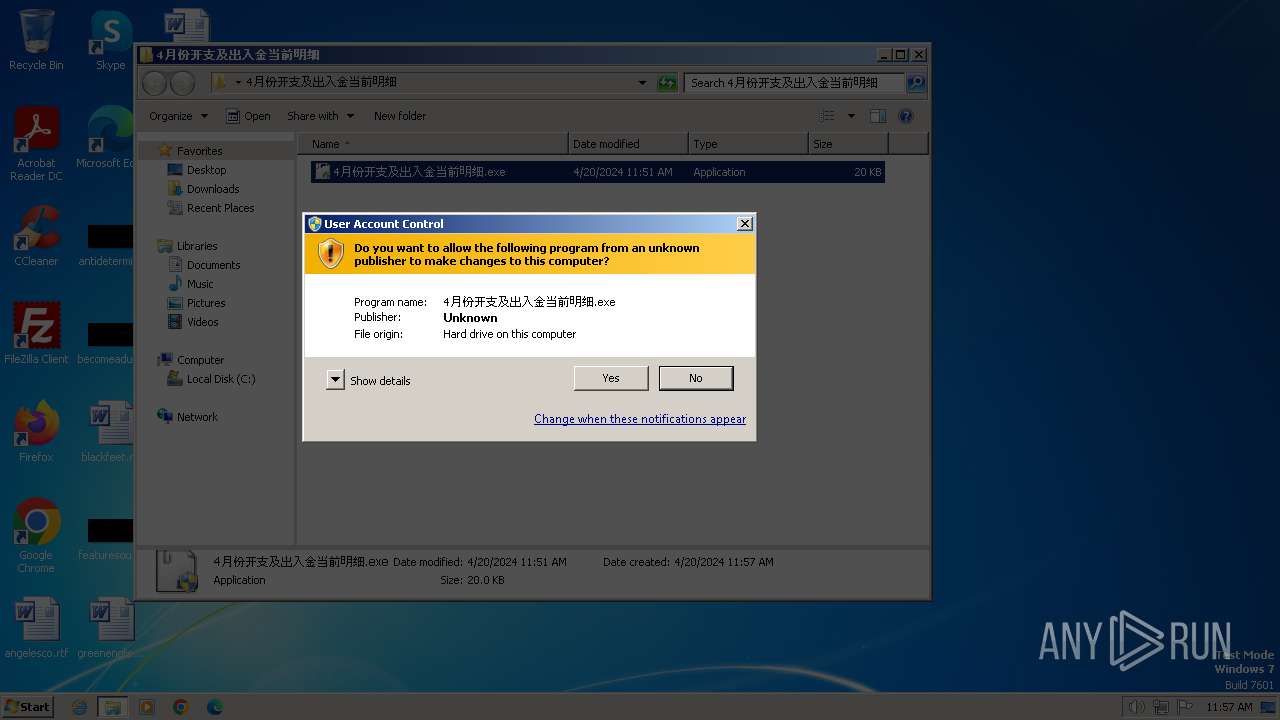
Manual execution by a user
- 4月份开支及出入金当前明细.exe (PID: 3636)
- 4月份开支及出入金当前明细.exe (PID: 2880)
- mmc.exe (PID: 4060)
- mmc.exe (PID: 900)
Checks supported languages
- 4月份开支及出入金当前明细.exe (PID: 3636)
- dllhost.exe (PID: 1492)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3416)
Reads the computer name
- 4月份开支及出入金当前明细.exe (PID: 3636)
- dllhost.exe (PID: 1492)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3404)
Reads Environment values
- dllhost.exe (PID: 1492)
Reads product name
- dllhost.exe (PID: 1492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:04:20 16:21:58 |
| ZipCRC: | 0x47b0aa5e |
| ZipCompressedSize: | 7684 |
| ZipUncompressedSize: | 20480 |
| ZipFileName: | 4月份开支及出入金当前明细.exe |
Total processes
52
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | "C:\Windows\system32\mmc.exe" C:\Windows\system32\taskschd.msc | C:\Windows\System32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | "C:\Users\Public\dllhost.exe" she | C:\Users\Public\dllhost.exe | 4月份开支及出入金当前明细.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2172 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\Public\ÎÒ¶ª.txt | C:\Windows\System32\notepad.exe | — | 4月份开支及出入金当前明细.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2880 | "C:\Users\admin\Desktop\4月份开支及出入金当前明细\4月份开支及出入金当前明细.exe" | C:\Users\admin\Desktop\4月份开支及出入金当前明细\4月份开支及出入金当前明细.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
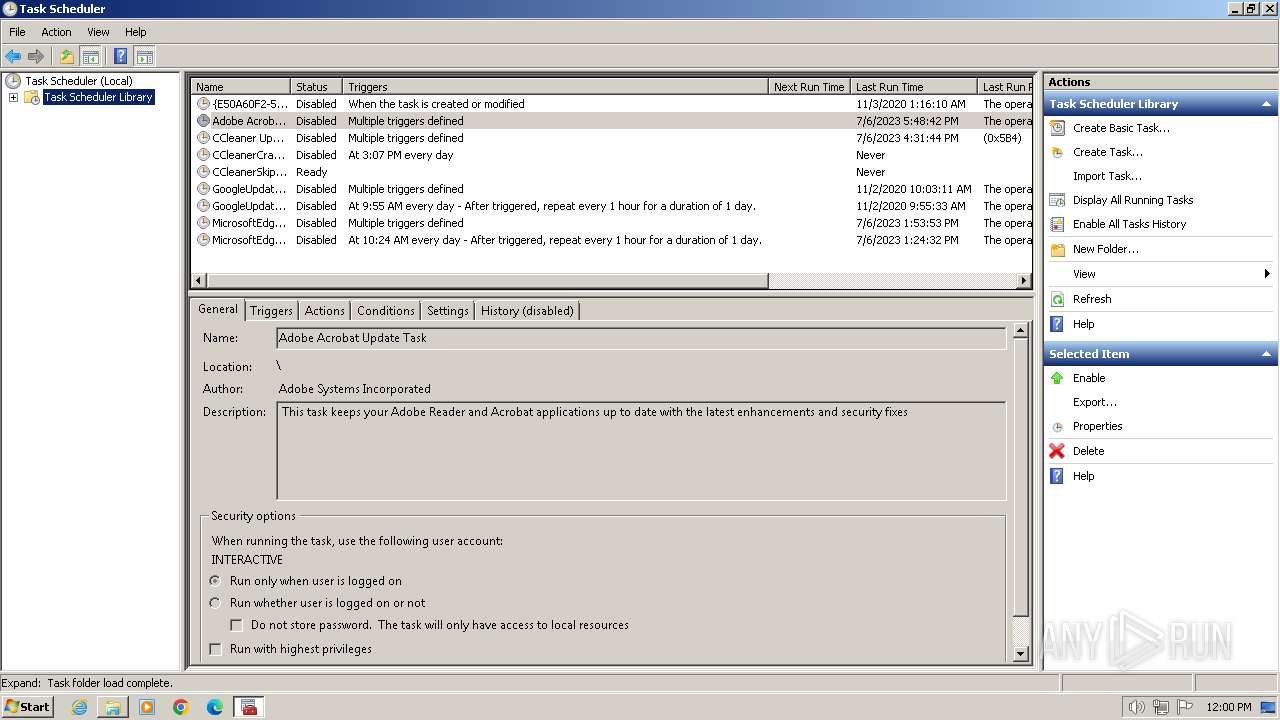
| 3404 | powershell.exe -NoProfile -Command "Add-MpPreference -ExclusionPath 'C:\Users\Public'; $xmlContent = Get-Content -Path 'C:\Users\Public\jh.xml' -Raw; Register-ScheduledTask -Xml $xmlContent -TaskName 'MicrosoftEdgeUpdateTaskUserS-1-5-21-4220318521-1419758426-78524122-1000Core{680DECD5-5011-4D3F-949A-4D7BAA279AC3}'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 4月份开支及出入金当前明细.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3416 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\4月份开支及出入金当前明细.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3636 | "C:\Users\admin\Desktop\4月份开支及出入金当前明细\4月份开支及出入金当前明细.exe" | C:\Users\admin\Desktop\4月份开支及出入金当前明细\4月份开支及出入金当前明细.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4060 | "C:\Windows\system32\mmc.exe" C:\Windows\system32\taskschd.msc | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 934
Read events
6 877
Write events
54
Delete events
3
Modification events
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\4月份开支及出入金当前明细.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3404 | powershell.exe | C:\Users\admin\AppData\Local\Temp\bjmmhadg.day.ps1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4060 | mmc.exe | C:\Users\admin\AppData\Roaming\Microsoft\MMC\taskschd | xml | |
MD5:082709FD499D624E1D84B4C2F6087B4D | SHA256:662470CFB54318358498D2D4F003FC7A3323D132F13040B49B0A3748740EBAE1 | |||
| 3636 | 4月份开支及出入金当前明细.exe | C:\Users\Public\dllhost.exe | executable | |
MD5:53D02CF0F94EF4D12D3B348BA73B776F | SHA256:14321A2BCE2E0D7C369CC0B3132B621DB5E791A3F3BD4AB81C9B7F53D4404B65 | |||
| 3404 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\4月份开支及出入金当前明细\4月份开支及出入金当前明细.exe | executable | |
MD5:D51611A0EBCF36F6A81010E9EE438D93 | SHA256:22301165607D5BC7AF2B657E2C8DE28DAD8F11D0A68BAFE81D5A736BF6382B01 | |||
| 3404 | powershell.exe | C:\Users\admin\AppData\Local\Temp\c1mt4u1h.5kq.psm1 | — | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3636 | 4月份开支及出入金当前明细.exe | C:\Users\Public\jh.xml | xml | |
MD5:CD5BC9CCAB0D9219FF5DCC000005E2ED | SHA256:362B880E1750968C6D2188C9CF7150D0839C2A036EB3A485ADFCA9A9FCCBDDB7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
8
DNS requests
1
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3636 | 4月份开支及出入金当前明细.exe | GET | 200 | 149.129.12.38:80 | http://zffsg.oss-ap-northeast-2.aliyuncs.com/154.log | unknown | — | — | unknown |
3636 | 4月份开支及出入金当前明细.exe | GET | 200 | 149.129.12.38:80 | http://zffsg.oss-ap-northeast-2.aliyuncs.com/jh.xml | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3636 | 4月份开支及出入金当前明细.exe | 149.129.12.38:80 | zffsg.oss-ap-northeast-2.aliyuncs.com | Alibaba US Technology Co., Ltd. | KR | unknown |
1492 | dllhost.exe | 154.204.60.33:6666 | — | LUCIDACLOUD LIMITED | HK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zffsg.oss-ap-northeast-2.aliyuncs.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Packed Executable Download |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | A Network Trojan was detected | ET MALWARE Possible Windows executable sent when remote host claims to send a Text File |
1492 | dllhost.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] XORed Windows executable has been loaded |
1492 | dllhost.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox |
— | — | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox Encrypted Client Packet |
— | — | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox Keep-Alive Client Packet |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|