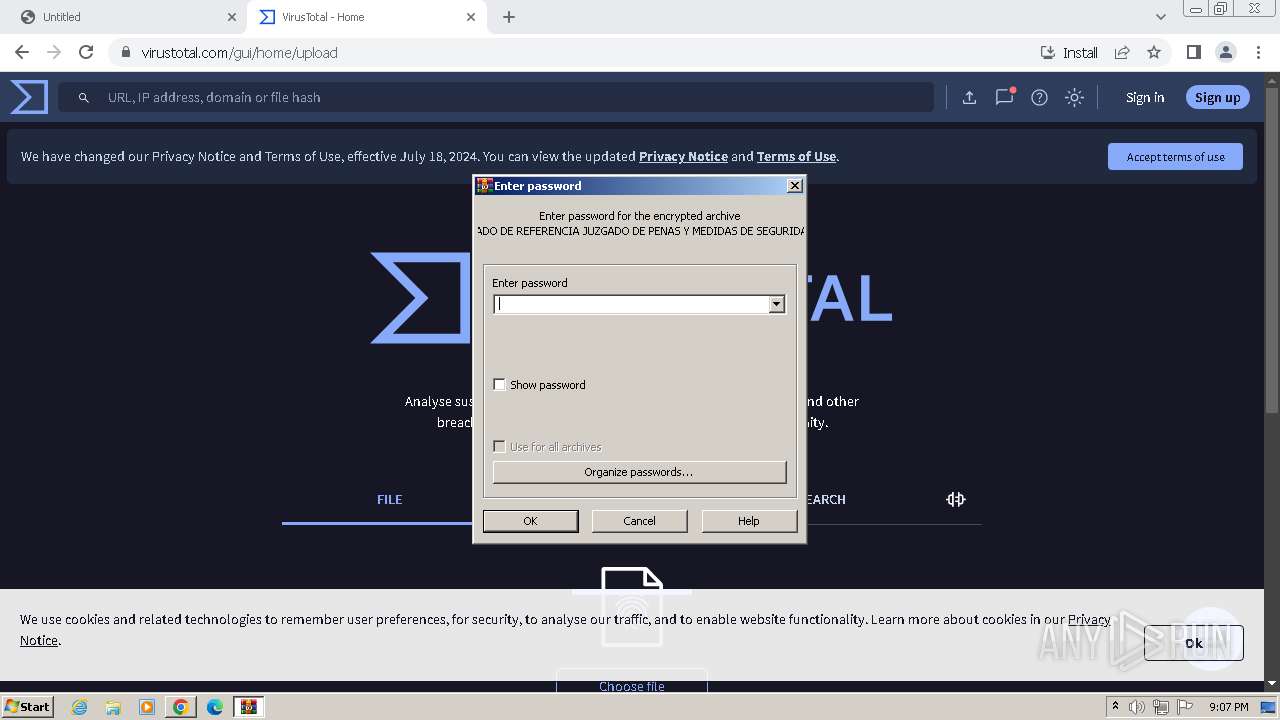
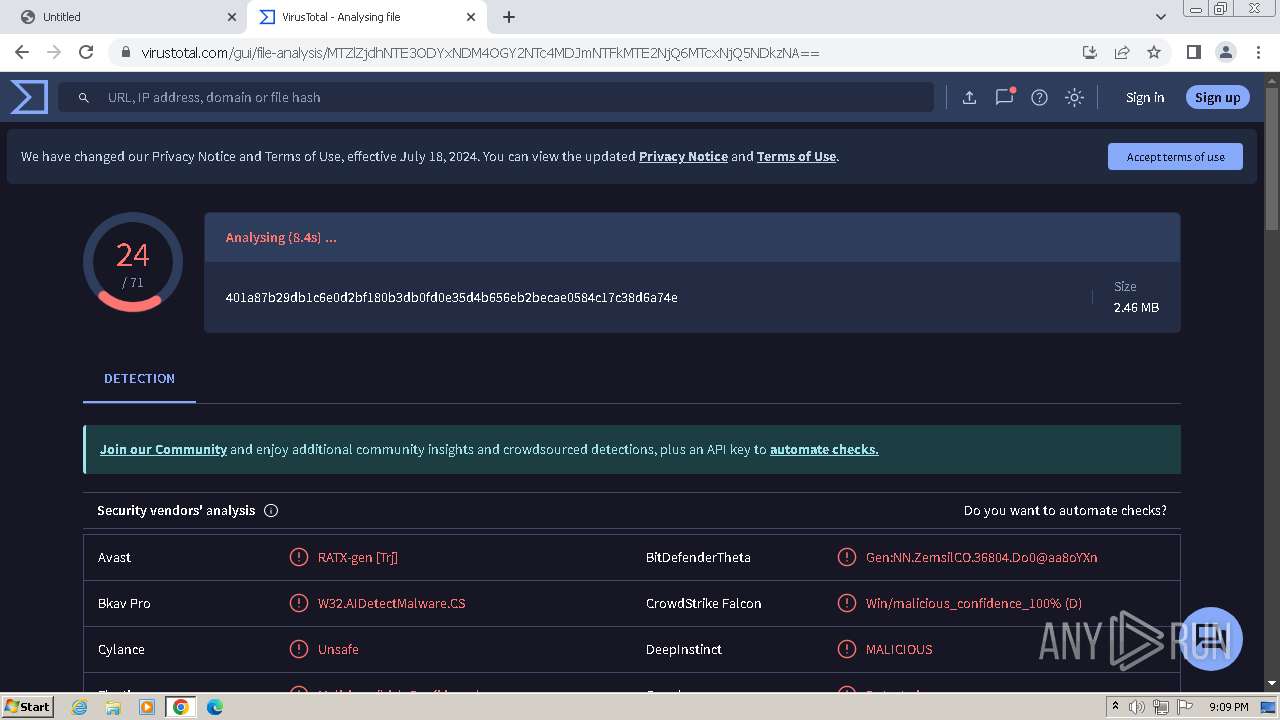
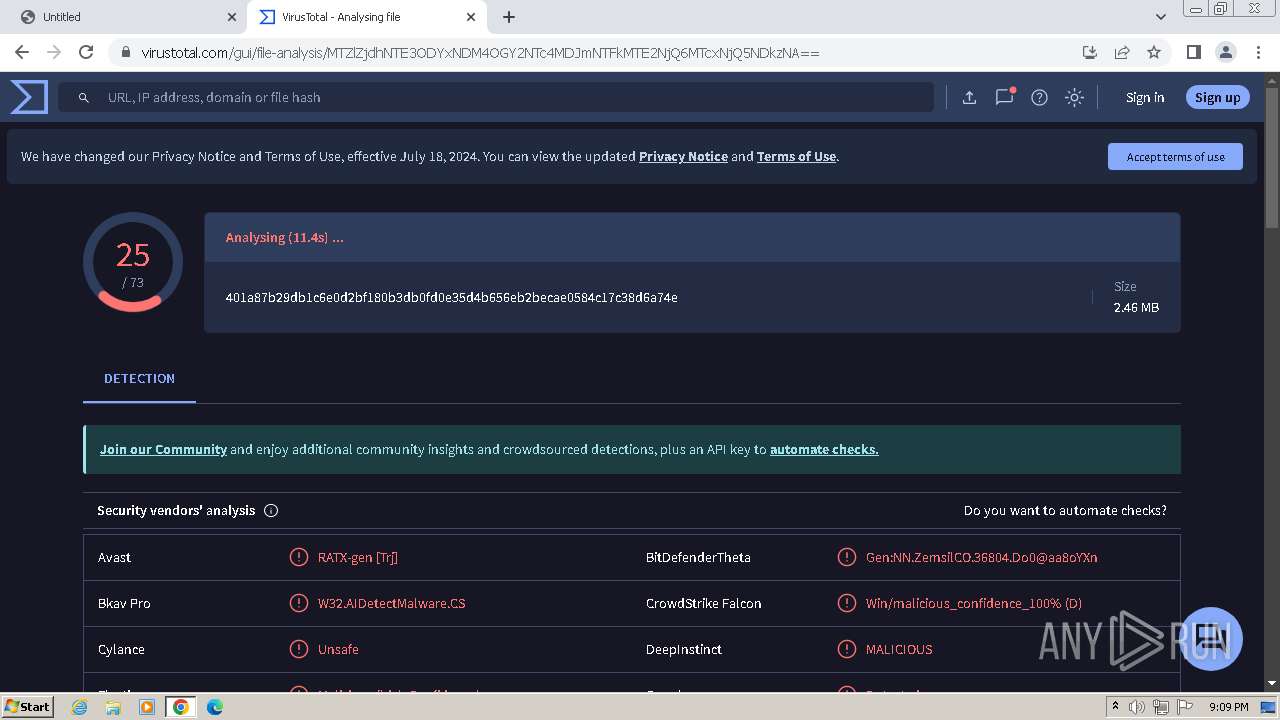
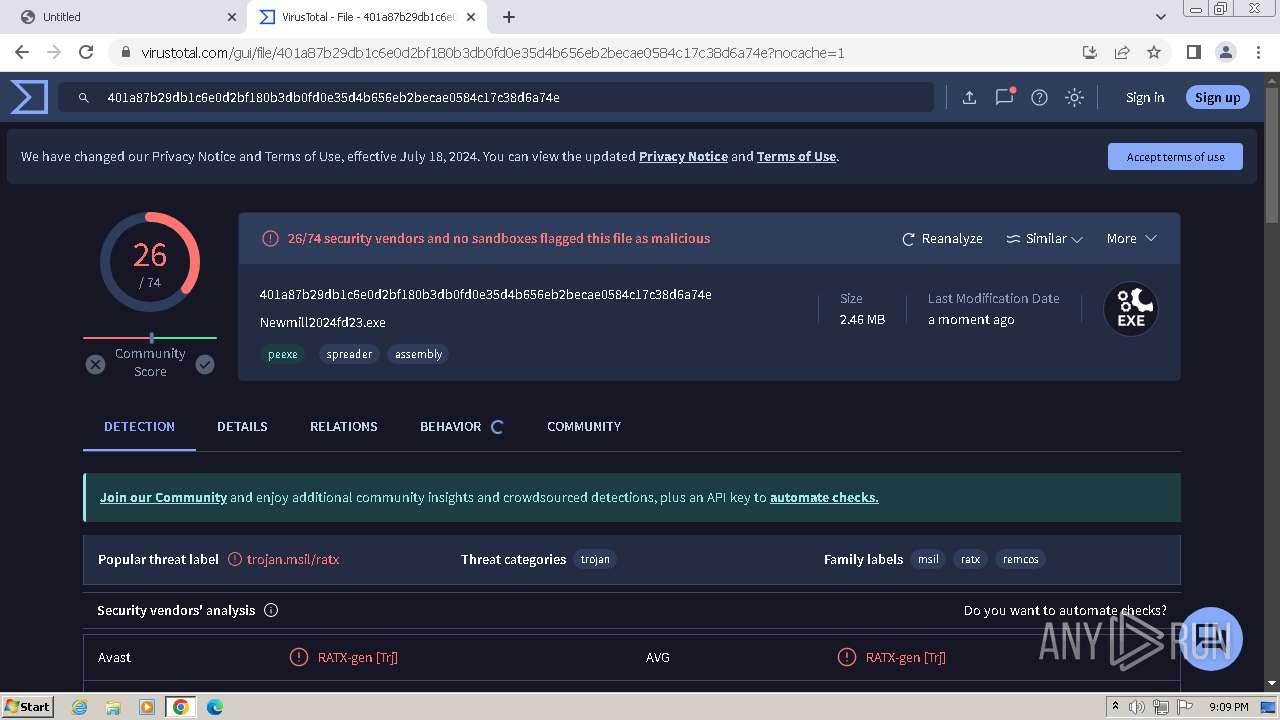
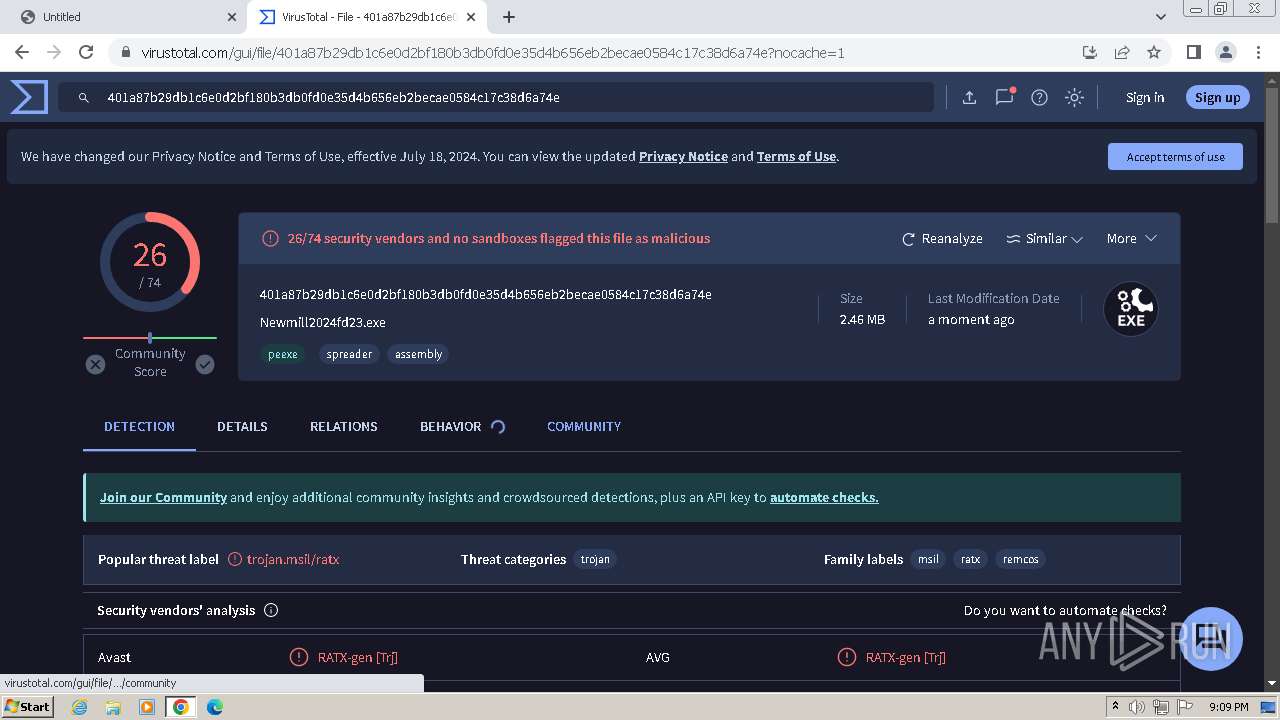
| URL: | https://drive.google.com/uc?id=1nCG72TQO2g-Ym0WrtpSl47pSFhRig_f7&export=download&authuser=0 |
| Full analysis: | https://app.any.run/tasks/dc78b473-0609-4833-90a3-454b818d5fe7 |
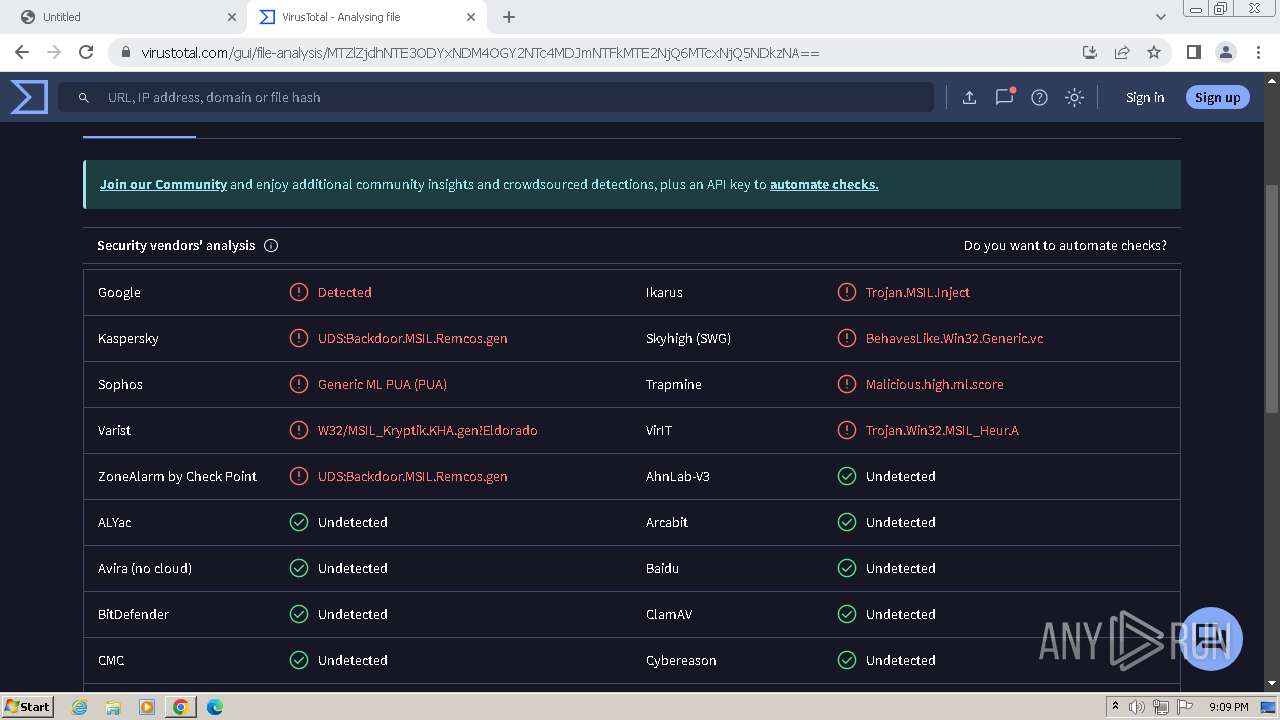
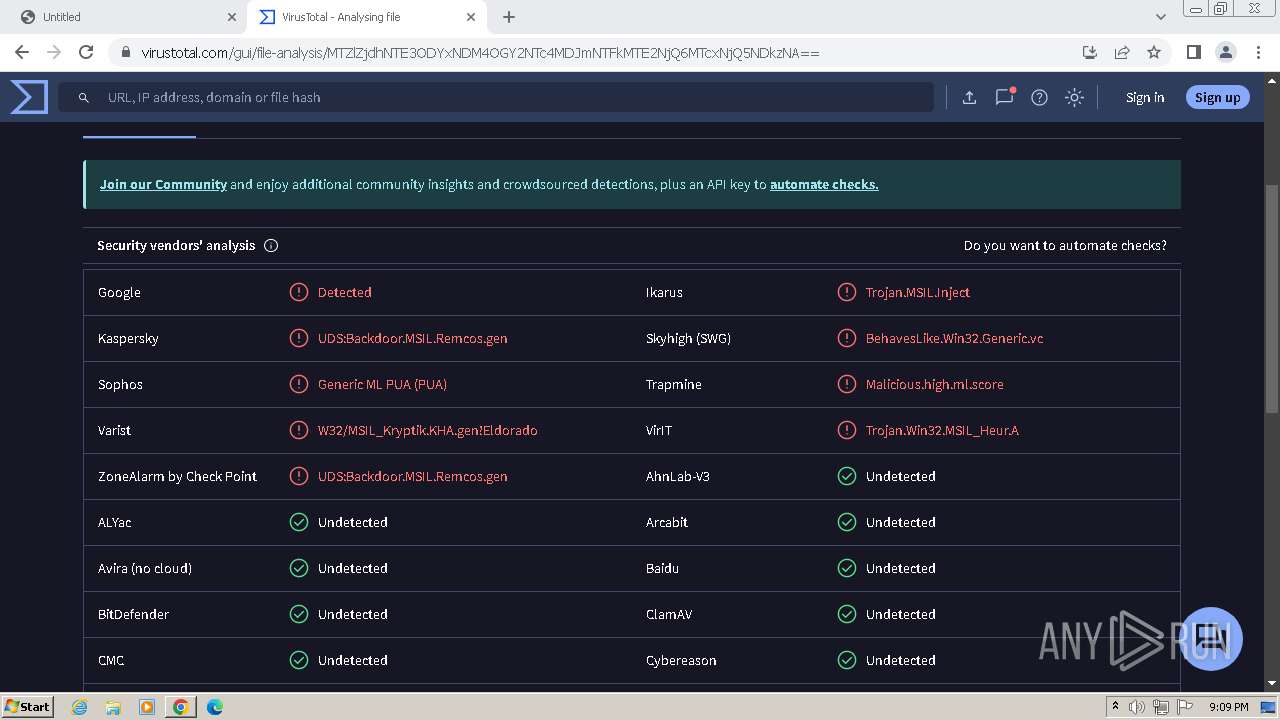
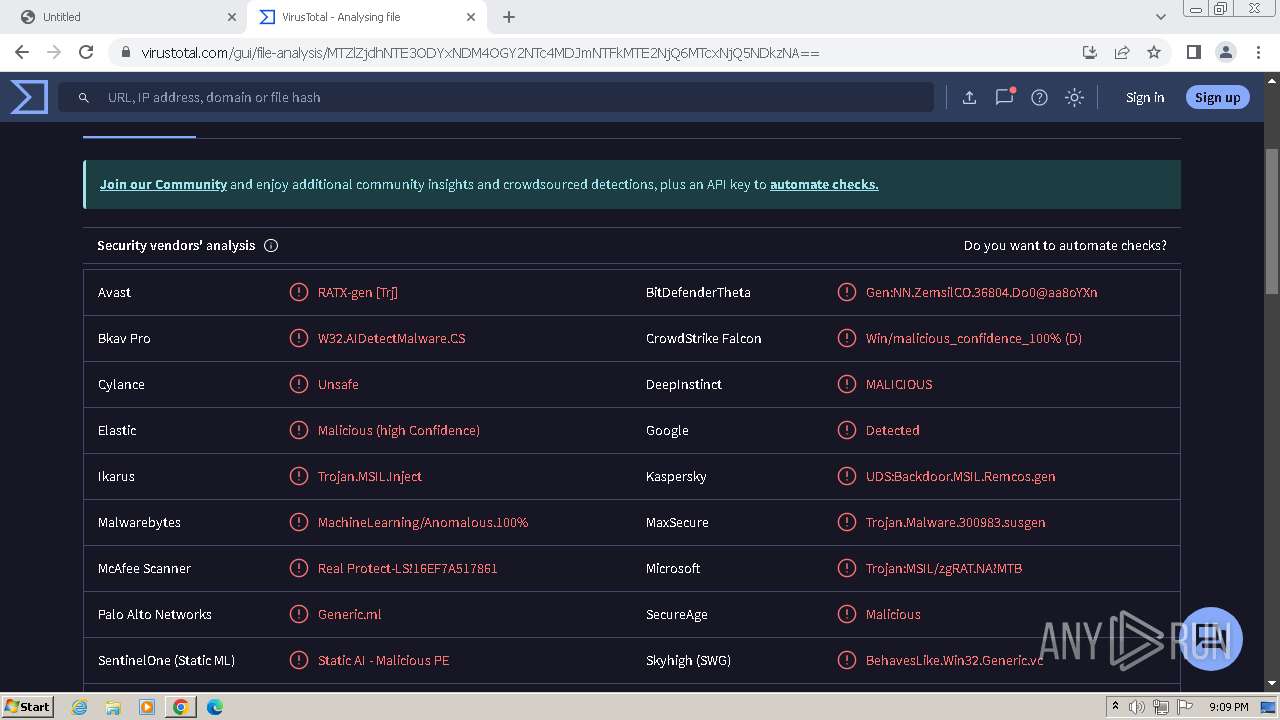
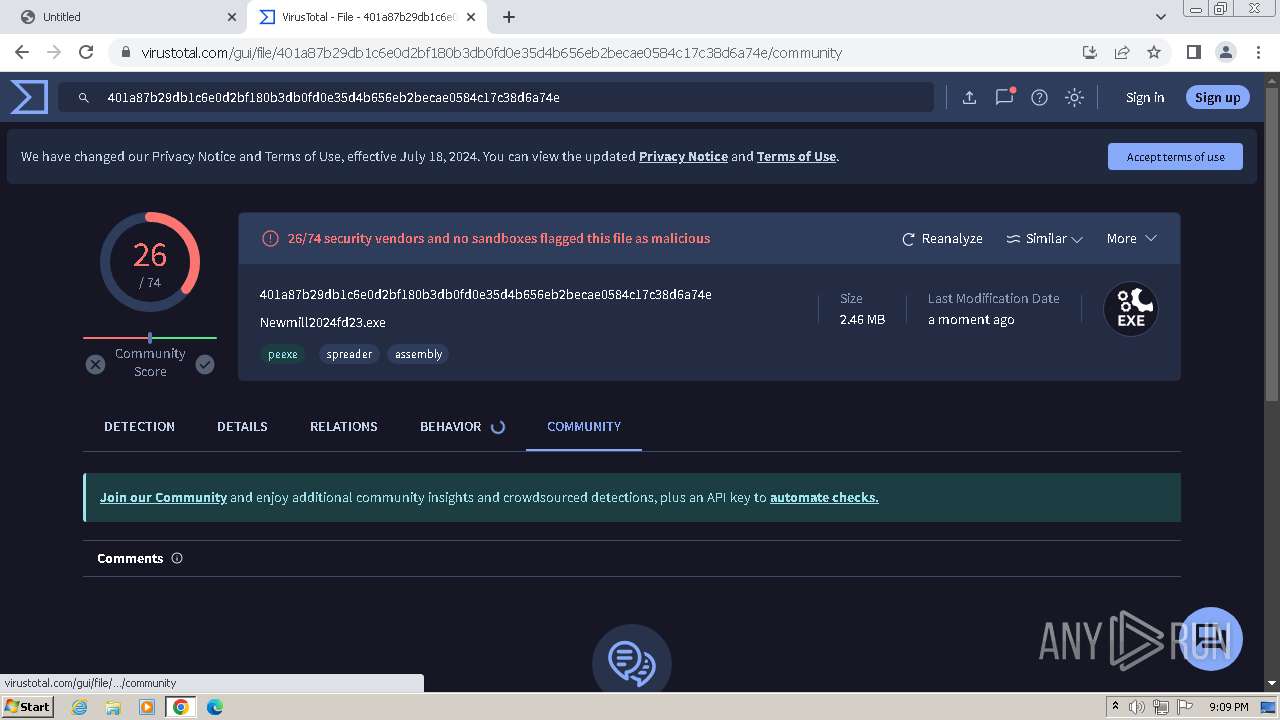
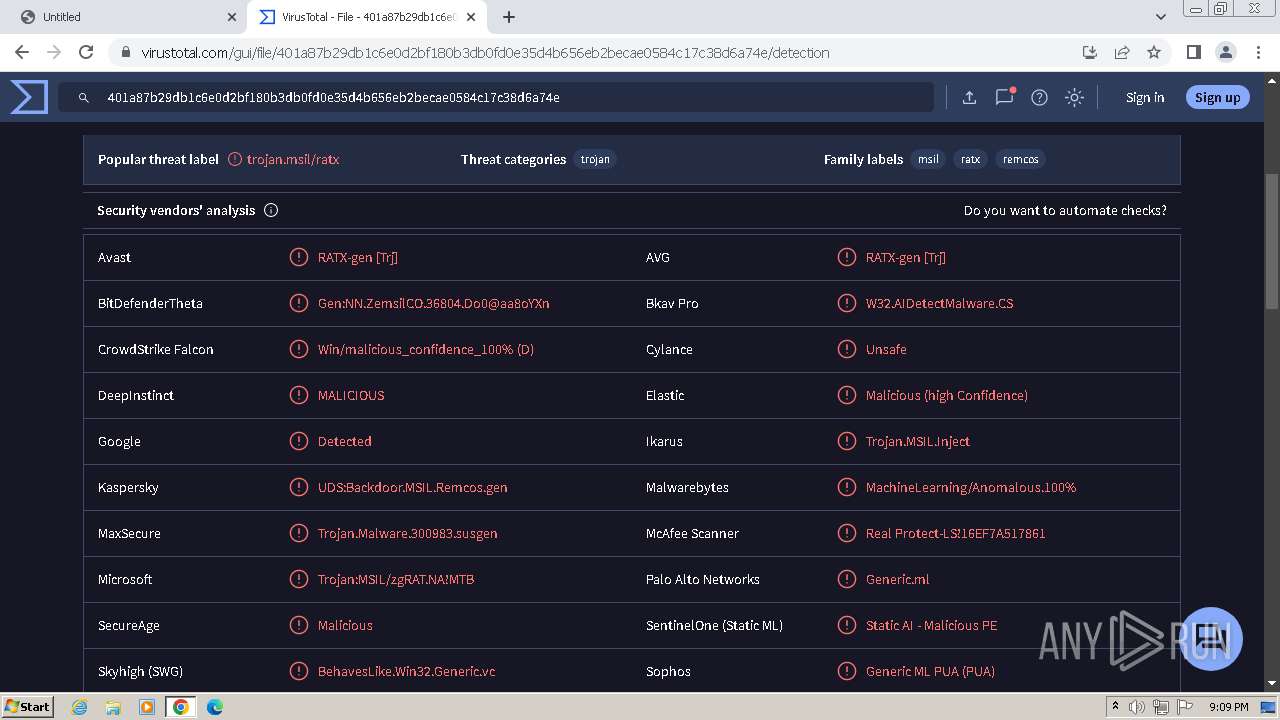
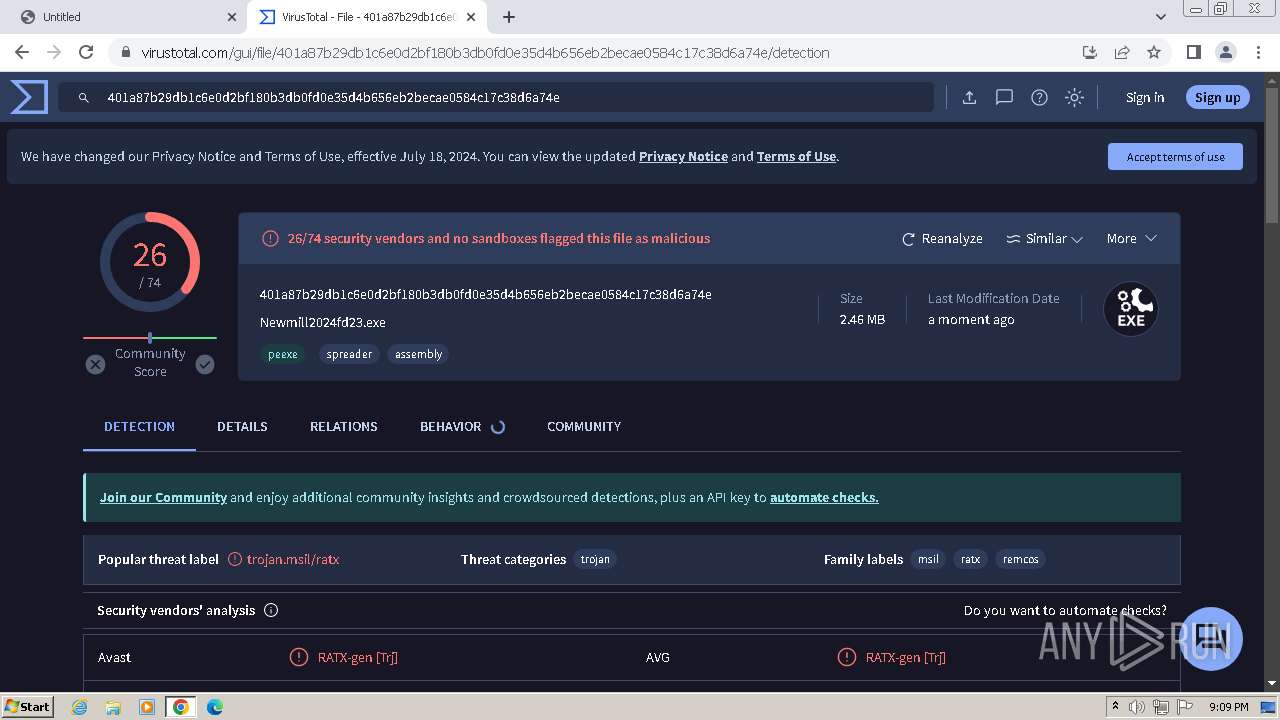
| Verdict: | Malicious activity |
| Threats: | A keylogger is a type of spyware that infects a system and has the ability to record every keystroke made on the device. This lets attackers collect personal information of victims, which may include their online banking credentials, as well as personal conversations. The most widespread vector of attack leading to a keylogger infection begins with a phishing email or link. Keylogging is also often present in remote access trojans as part of an extended set of malicious tools. |
| Analysis date: | May 23, 2024, 20:06:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 69ABA62A53AF2D5449F1E260D87CD032 |
| SHA1: | EC5BFFE760CB1DF96FF3E5A69EA7D2D2FB399782 |
| SHA256: | 60885B97304B4E1EB8EA42ADF88E9CC24E1E76667756A2DEDF91C73E966C5DFB |
| SSDEEP: | 3:N8PMMtZJu2NMuvh0sCI8PR4Rm2ELS1CaIn:2A2Hvh008PRpRSMjn |
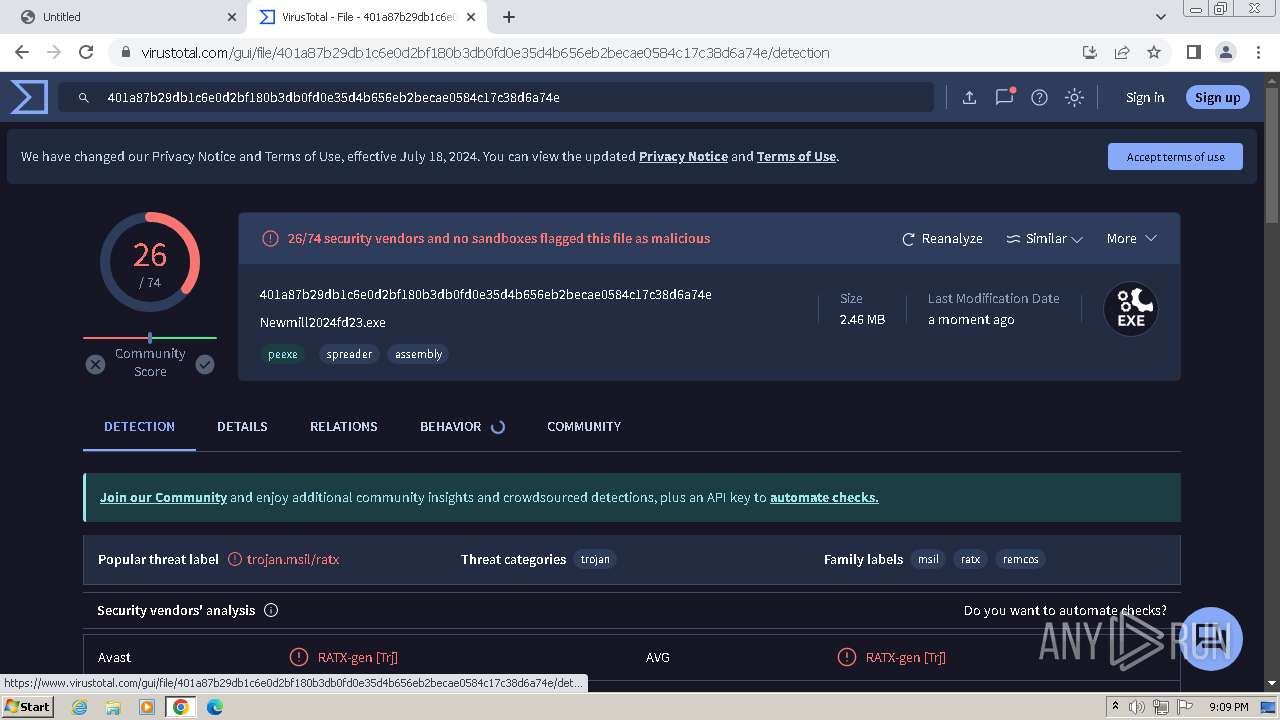
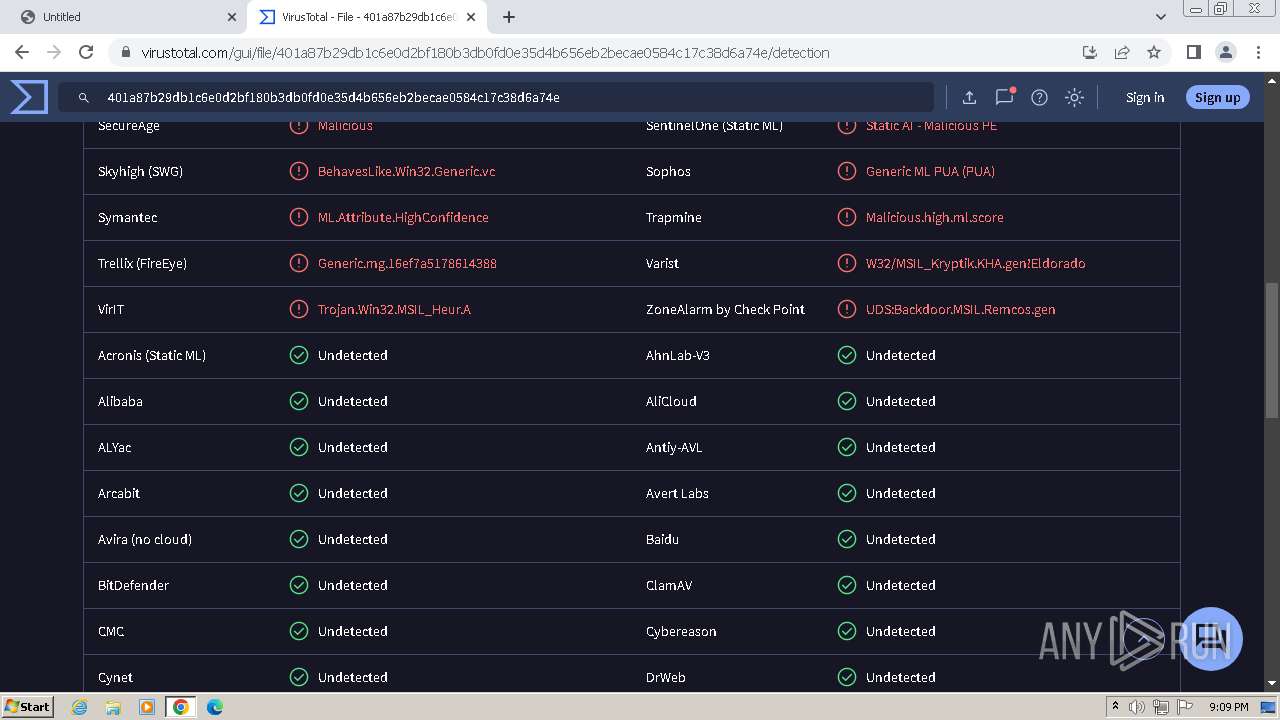
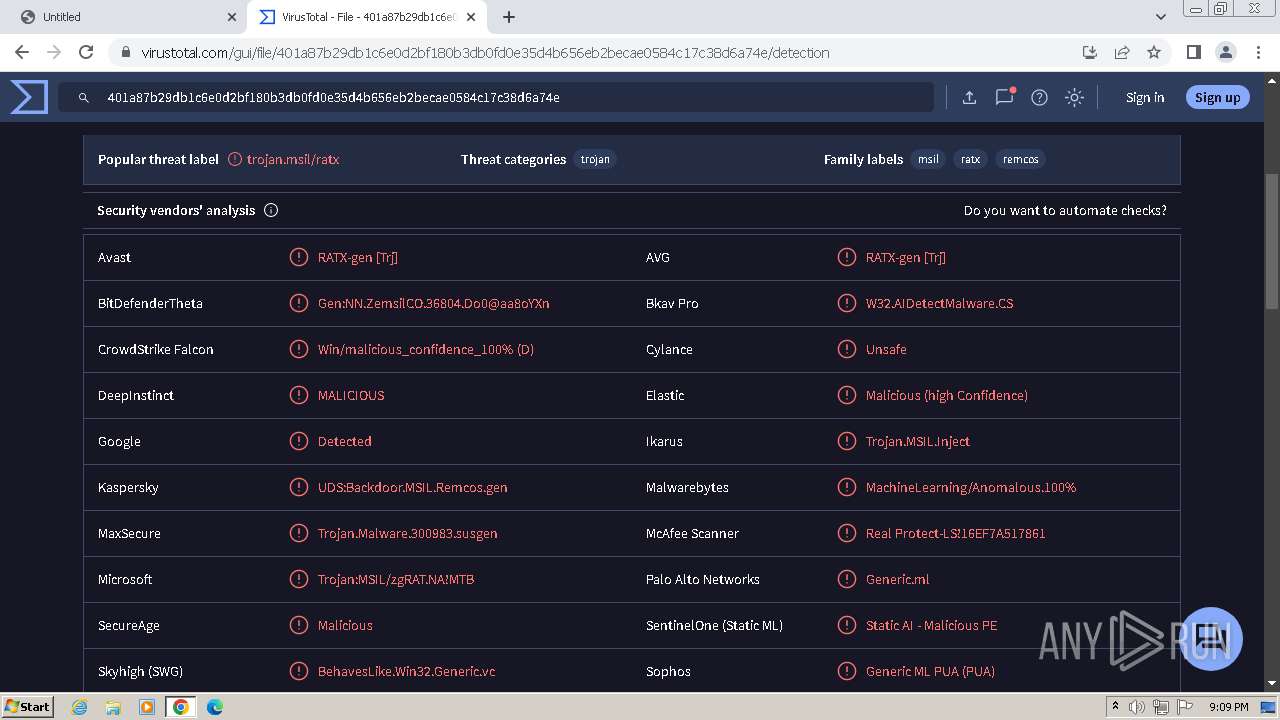
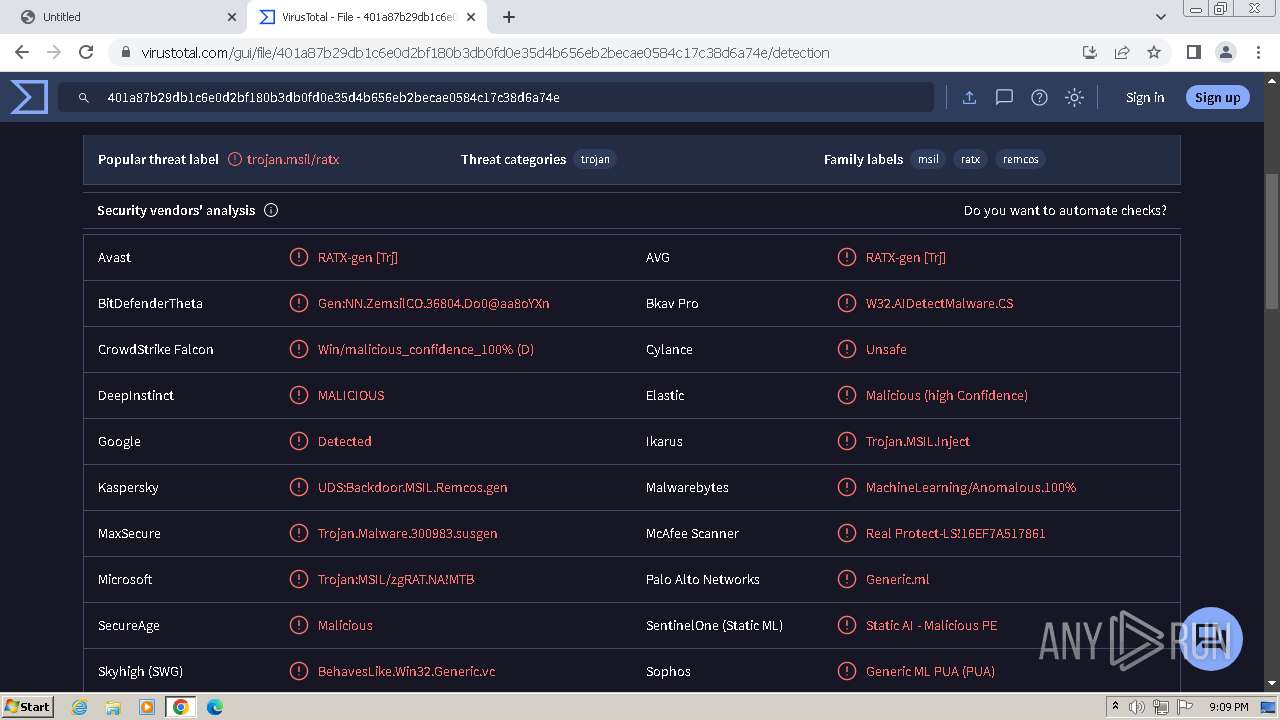
MALICIOUS
Changes the autorun value in the registry
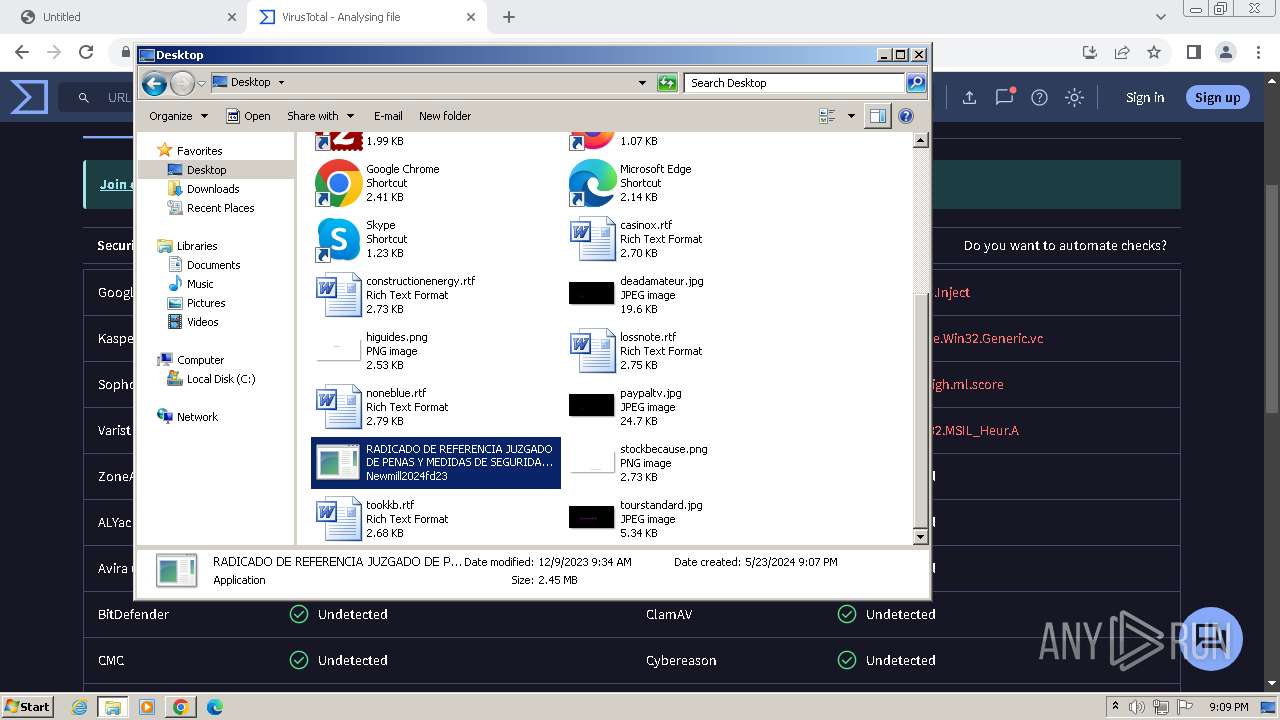
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
Drops the executable file immediately after the start
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
REMCOS has been detected (YARA)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
SUSPICIOUS
Executable content was dropped or overwritten
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
Application launched itself
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
Connects to unusual port
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Reads the Internet Settings
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Reads security settings of Internet Explorer
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Checks for external IP
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Device Retrieving External IP Address Detected
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Writes files like Keylogger logs
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 2260)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Manual execution by a user
- wmpnscfg.exe (PID: 2260)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
- explorer.exe (PID: 3528)
Checks supported languages
- wmpnscfg.exe (PID: 2260)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
The process uses the downloaded file
- chrome.exe (PID: 2252)
- WinRAR.exe (PID: 948)
Executable content was dropped or overwritten
- chrome.exe (PID: 3604)
- WinRAR.exe (PID: 948)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 948)
- chrome.exe (PID: 3604)
Reads the machine GUID from the registry
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Creates files or folders in the user directory
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 1664)
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Application launched itself
- chrome.exe (PID: 3992)
Reads Environment values
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Reads product name
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Checks proxy server information
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Creates files in the program directory
- RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(2064) RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe
C2 (1)milhouse2024.con-ip.com:2024
BotnetNEWMILL
Options
Connect_interval1
Install_flagFalse
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%LOCALAPPDATA%
Copy_fileremcos.exe
Startup_valueTrue
Hide_fileFalse
Mutex_namekyegibkfesdcsasdwqed-CW2LCL
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_fileregistros.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileCapturas de pantalla
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%ProgramFiles%
Audio_dirMicRecords
Connect_delay0
Copy_dirRemcos
Keylog_dirkhvdjke
Total processes
71
Monitored processes
34
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2016 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3660 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2040 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1124 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 948 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .rev" | C:\Program Files\WinRAR\WinRAR.exe | chrome.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1852 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1256 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3484 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1664 | "C:\Users\admin\Desktop\RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe" | C:\Users\admin\Desktop\RADICADO DE REFERENCIA JUZGADO DE PENAS Y MEDIDAS DE SEGURIDAD .exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Newmill2024fd23 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1424 --field-trial-handle=1164,i,2634960363102711592,15797143524312086572,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
25 316
Read events
24 996
Write events
298
Delete events
22
Modification events
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3992) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
6
Suspicious files
139
Text files
38
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1043e1.TMP | — | |
MD5:— | SHA256:— | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:825B582C78EC88D54C215EFDF1EAD639 | SHA256:367995D01A8F13E5C30C79499F86B034775BFD009D83DC97635DE438D47DFA37 | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RF104e9f.TMP | — | |
MD5:— | SHA256:— | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\4972caeb-e23d-4f72-891e-86c6265e1df5.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF1045a6.TMP | text | |
MD5:AD0DB8476493577A67FA94A162B646C4 | SHA256:304FB5B4FD83D4A9FF1EF4CF20232A1783169C148297BFE37ED24A1D22A74F2B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
40
DNS requests
49
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ive6ltmywihweu4kdkd5iiprfq_20240404.625479014.14/obedbbhbpmojnkanicioggnmelmoomoc_20240404.625479014.14_all_ENUS500000_h2n4frbunhedu3li224d3ntzwi.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ive6ltmywihweu4kdkd5iiprfq_20240404.625479014.14/obedbbhbpmojnkanicioggnmelmoomoc_20240404.625479014.14_all_ENUS500000_h2n4frbunhedu3li224d3ntzwi.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ive6ltmywihweu4kdkd5iiprfq_20240404.625479014.14/obedbbhbpmojnkanicioggnmelmoomoc_20240404.625479014.14_all_ENUS500000_h2n4frbunhedu3li224d3ntzwi.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ive6ltmywihweu4kdkd5iiprfq_20240404.625479014.14/obedbbhbpmojnkanicioggnmelmoomoc_20240404.625479014.14_all_ENUS500000_h2n4frbunhedu3li224d3ntzwi.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ive6ltmywihweu4kdkd5iiprfq_20240404.625479014.14/obedbbhbpmojnkanicioggnmelmoomoc_20240404.625479014.14_all_ENUS500000_h2n4frbunhedu3li224d3ntzwi.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ive6ltmywihweu4kdkd5iiprfq_20240404.625479014.14/obedbbhbpmojnkanicioggnmelmoomoc_20240404.625479014.14_all_ENUS500000_h2n4frbunhedu3li224d3ntzwi.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ive6ltmywihweu4kdkd5iiprfq_20240404.625479014.14/obedbbhbpmojnkanicioggnmelmoomoc_20240404.625479014.14_all_ENUS500000_h2n4frbunhedu3li224d3ntzwi.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | — | — | unknown |
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | — | — | unknown |
884 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adasgb6qzo3kp62542i5hyaakdua_30.2/imefjhfbkmcmebodilednhmaccmincoa_30.2_win_kwiu22sehztwd3bii7gzgq4vri.crx3 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3992 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
1136 | chrome.exe | 173.194.69.84:443 | accounts.google.com | GOOGLE | US | unknown |
1136 | chrome.exe | 142.250.186.46:443 | drive.google.com | GOOGLE | US | whitelisted |
1136 | chrome.exe | 172.217.16.129:443 | drive.usercontent.google.com | GOOGLE | US | whitelisted |
3992 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
1136 | chrome.exe | 142.250.186.132:443 | www.google.com | GOOGLE | US | whitelisted |
1136 | chrome.exe | 216.239.36.21:443 | virustotal.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
drive.google.com |
| shared |
drive.usercontent.google.com |
| unknown |
www.google.com |
| whitelisted |
virustotal.com |
| whitelisted |
www.virustotal.com |
| whitelisted |
www.recaptcha.net |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Redirection Service Domain in DNS Lookup (con-ip .com) |
— | — | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
— | — | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |
1 ETPRO signatures available at the full report