| File name: | 602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe |
| Full analysis: | https://app.any.run/tasks/14a581a4-1340-4b9e-8429-cbd065c4a207 |
| Verdict: | Malicious activity |
| Threats: | REvil, also called Sodinokibi, is a notorious ransomware strain known for its use of sophisticated encryption techniques, high-profile targeted attacks, and connections to GandCrab. |
| Analysis date: | July 07, 2025, 19:12:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 7 sections |
| MD5: | 360827EBD0AEC294B2D6F067C868438B |
| SHA1: | CC1130F1118C3648DEBFE5E74F61EABEE27443CE |
| SHA256: | 602375762D88D24AE659C47D25959E52ED5CEA1D227609EC486BD42D551CA009 |
| SSDEEP: | 768:kD51apzeRTauAtNLyZl9SOfy3aGinc/ex3yC2U3vUDQM+pI3uR46rdmSJIR2H9pN:k6VeZYgSOfIic/ZwdO3uRJ0UNdH |
MALICIOUS
SODINOKIBI has been detected (YARA)
- 602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe (PID: 984)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- 602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe (PID: 984)
Manual execution by a user
- notepad.exe (PID: 3620)
Reads the computer name
- 602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe (PID: 984)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:09:10 16:04:20+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 42496 |
| InitializedDataSize: | 75264 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x277a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Total processes
141
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Users\admin\Desktop\602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe" | C:\Users\admin\Desktop\602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\DBG_LOG.TXT | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5616 | "C:\Users\admin\Desktop\602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe" | C:\Users\admin\Desktop\602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
226
Read events
226
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 984 | 602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | C:\Users\admin\Desktop\DBG_LOG.TXT | ini | |
MD5:25E26F864B18E09A18E24EAB06D1DF44 | SHA256:28CE70E827E0B0F3977FD0E21B22E11A1A4833DC0DE2B7D98689CDFB9BD2378F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
436 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.22.33.235:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1508 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1508 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6376 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 20.44.239.154:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
1268 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 2.22.33.235:80 | www.microsoft.com | AKAMAI-AS | IT | whitelisted |
436 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
436 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
Process | Message |
|---|---|
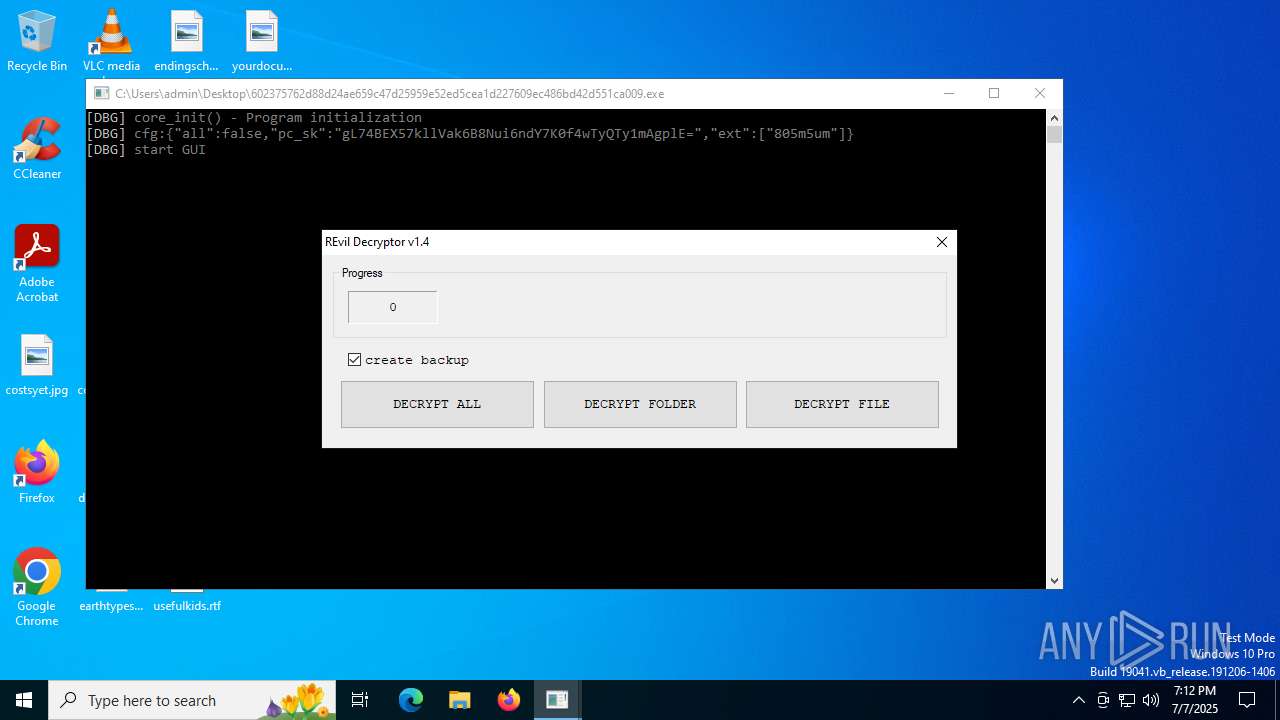
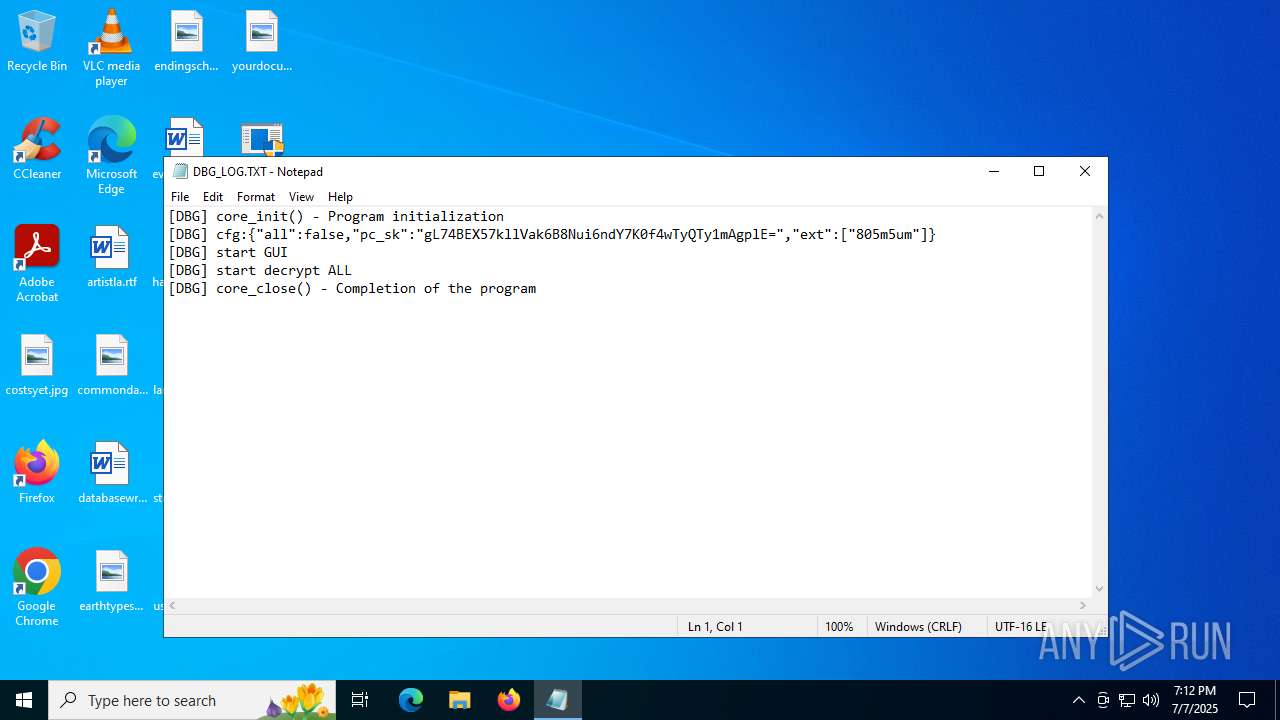
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | [DBG] |
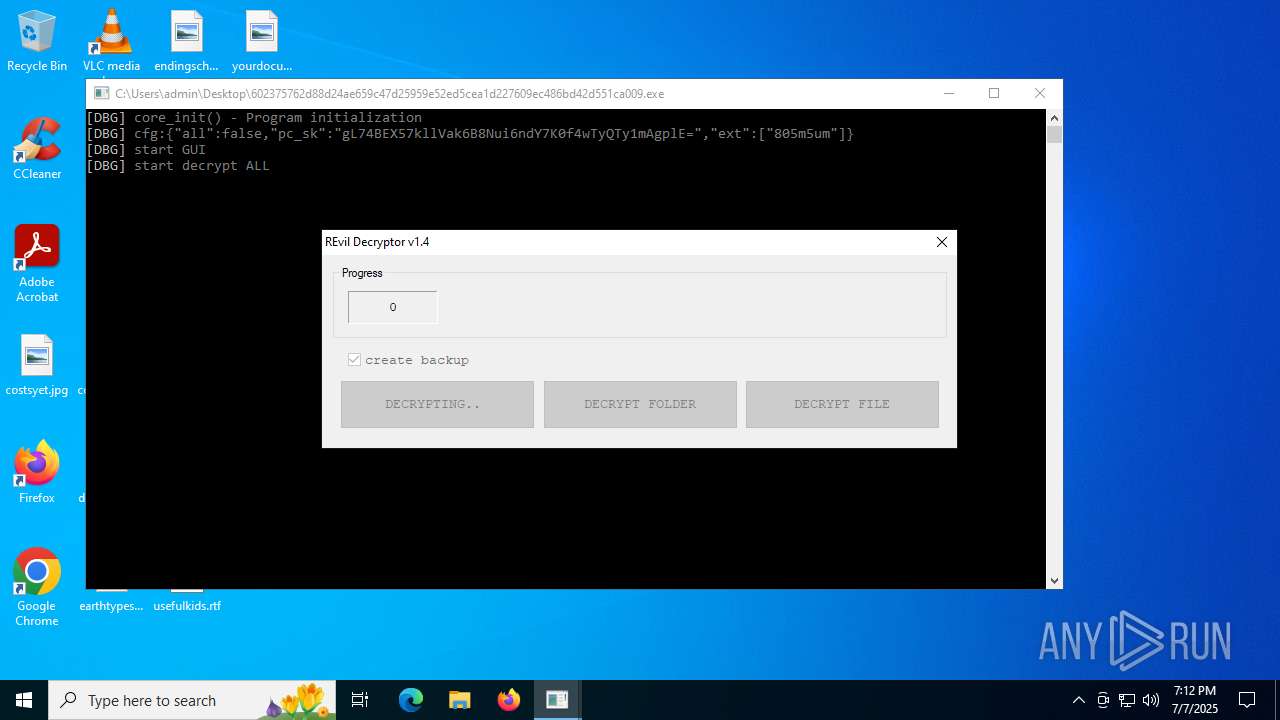
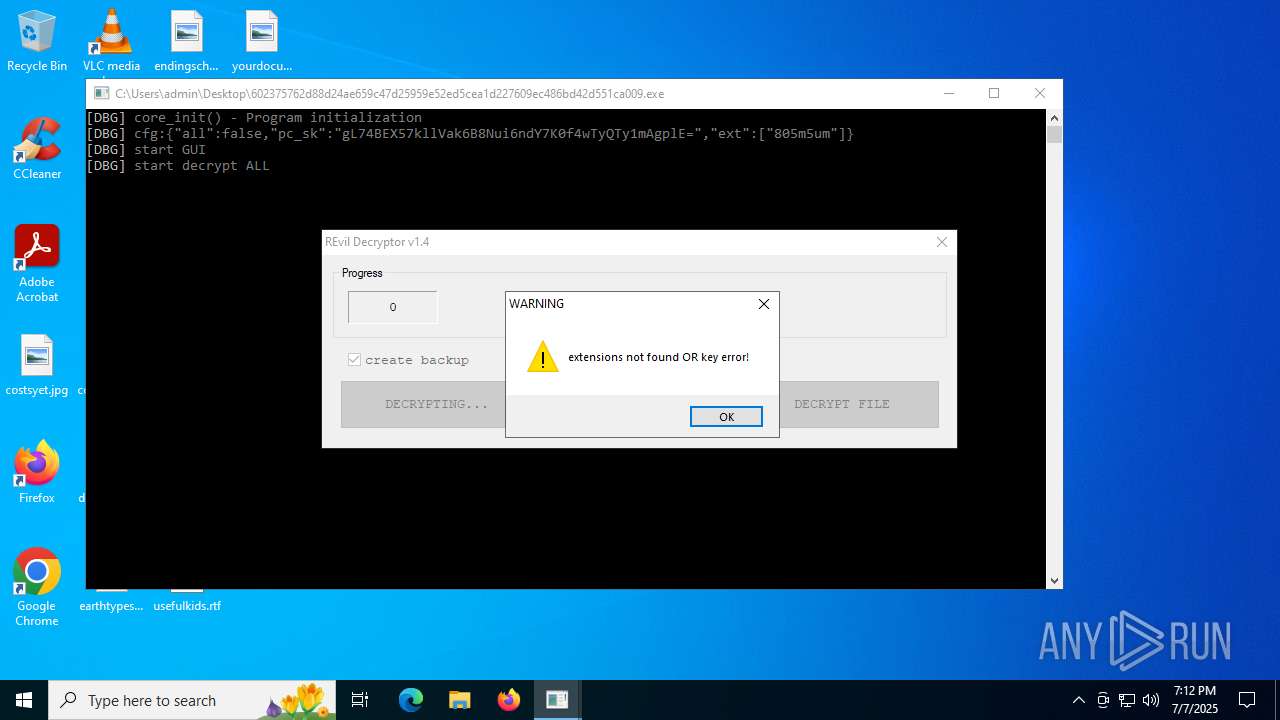
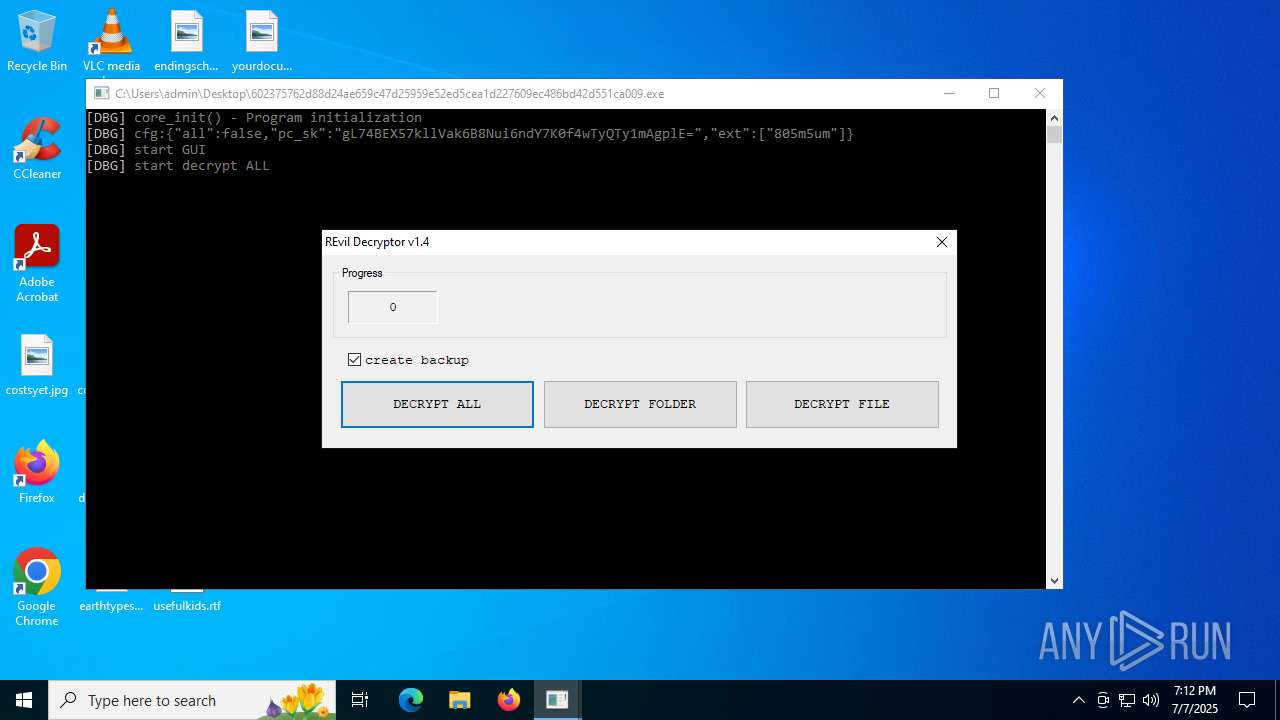
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | core_init() - Program initialization
|
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | [DBG] |
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | cfg:{"all":false,"pc_sk":"gL74BEX57kllVak6B8Nui6ndY7K0f4wTyQTy1mAgplE=","ext":["805m5um"]}
|
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | [DBG] |
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | start GUI
|
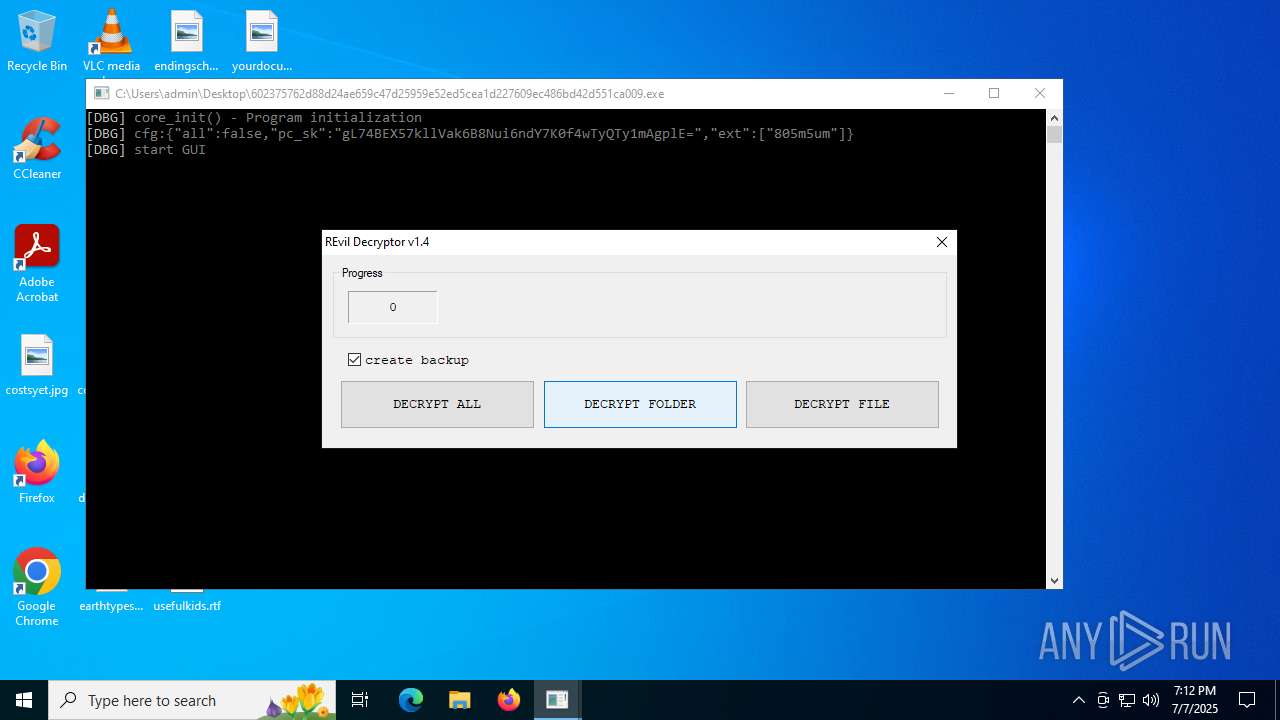
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | [DBG] |
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | start decrypt ALL
|
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | [DBG] |
602375762d88d24ae659c47d25959e52ed5cea1d227609ec486bd42d551ca009.exe | core_close() - Completion of the program
|