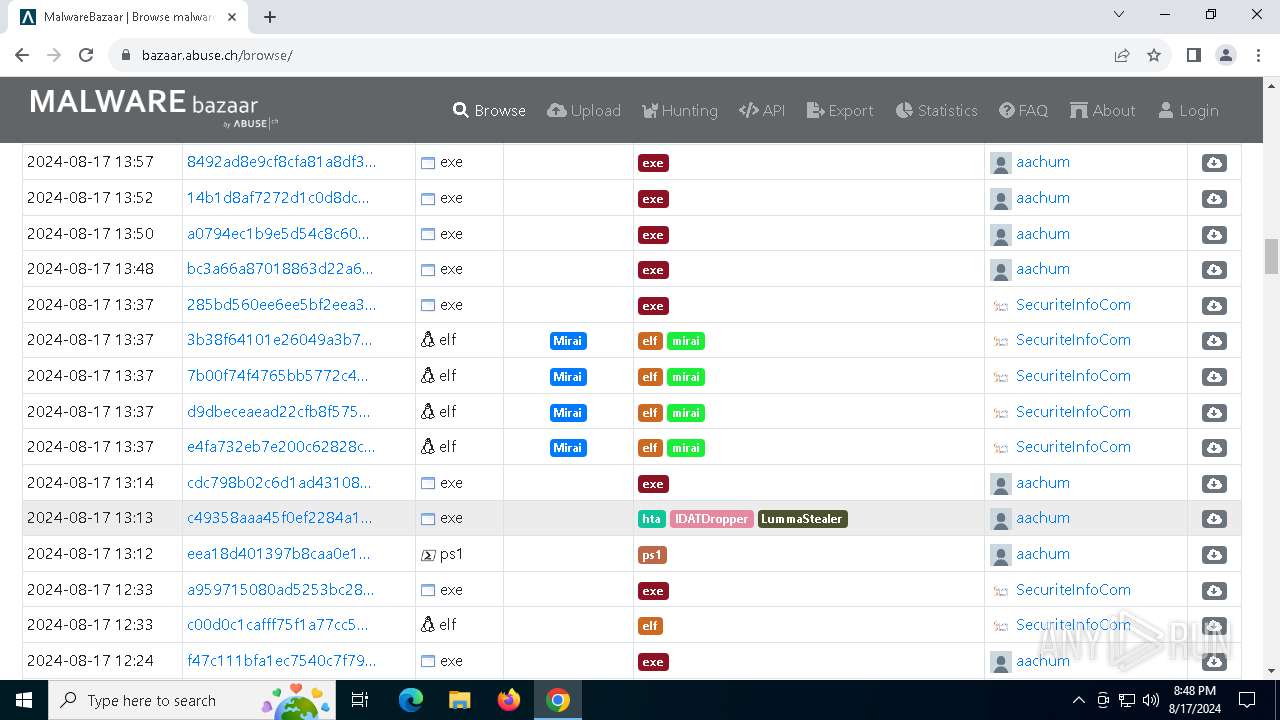
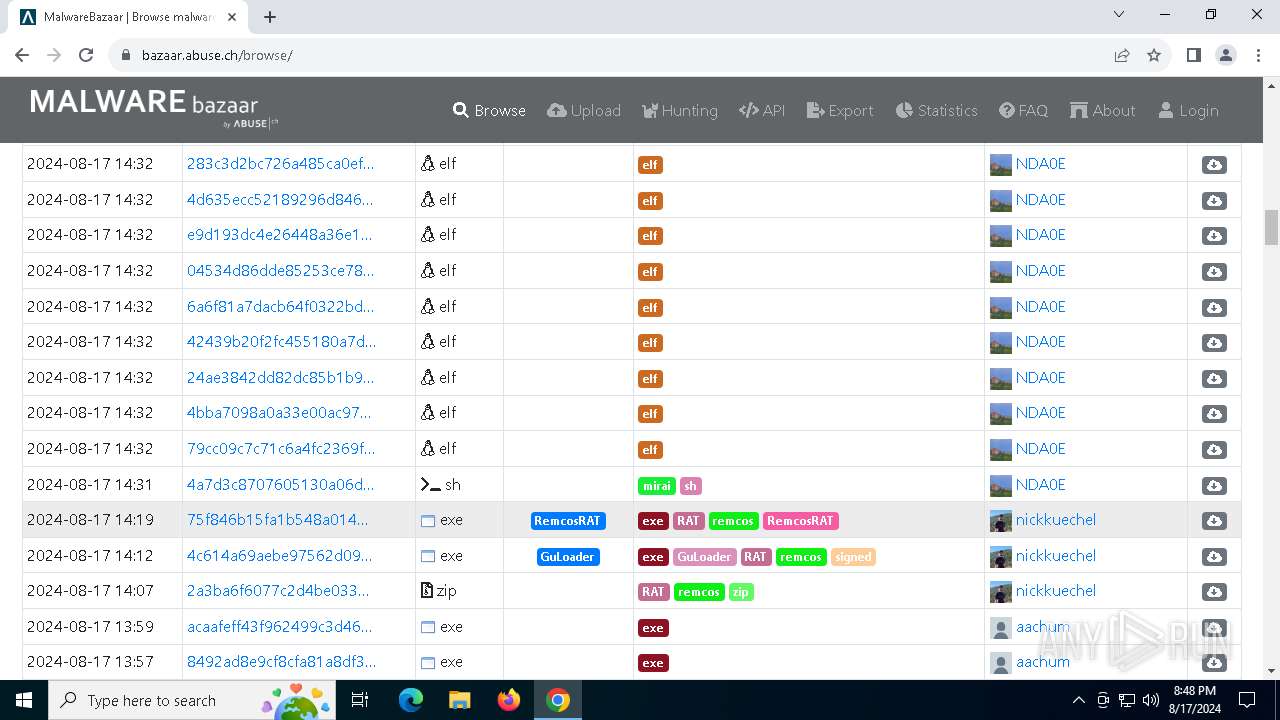
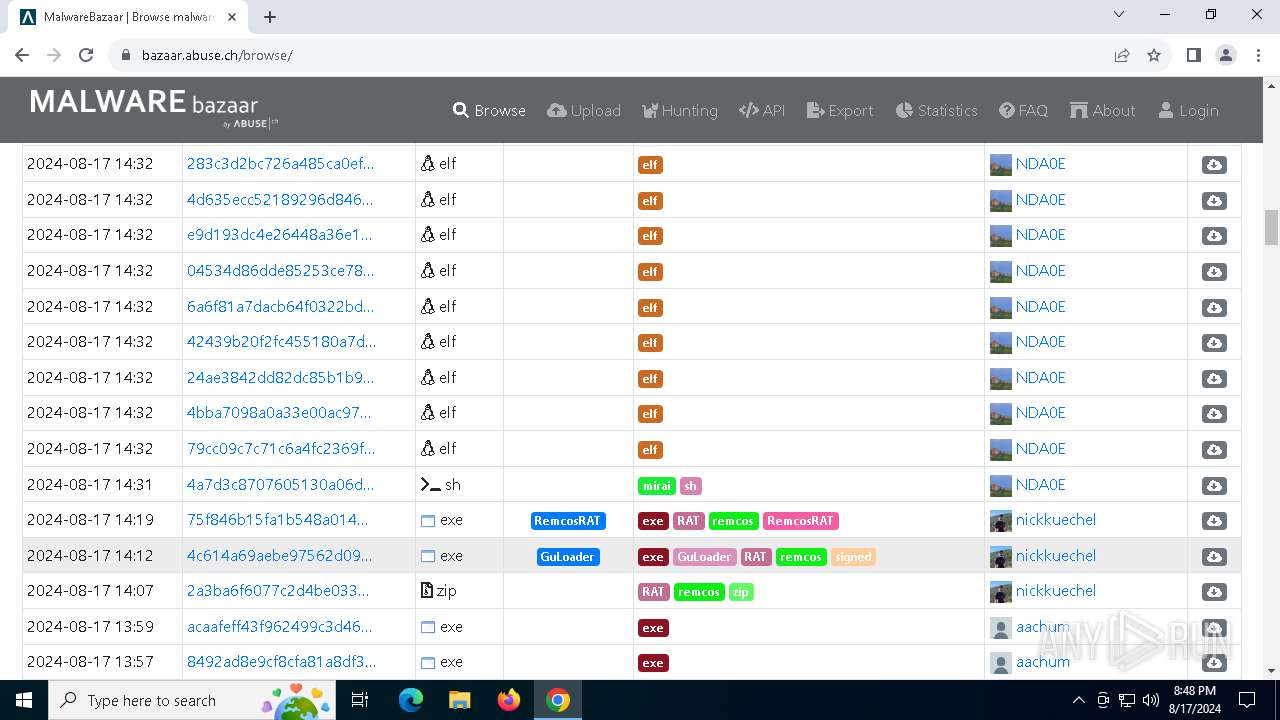
| URL: | https://bazaar.abuse.ch/browse/ |
| Full analysis: | https://app.any.run/tasks/56c9734c-f27a-4dd8-8547-792c72cc4283 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | August 17, 2024, 20:47:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 795F5641CCD3DFF86DCD367836C7B9E8 |
| SHA1: | FEA906E160EC0EE8145CCFDBD3AB0459E811CFA7 |
| SHA256: | 5FD287342B02CD1D1FE57258D81B38FFBCE8850B5E404D8B83758D9A21872C2F |
| SSDEEP: | 3:N8N0uDWHXKBn:23AaBn |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7016)
GULOADER has been detected
- 4c614a69aebe97562d09c05c5b08db70ba7cba08f6698e5a87fc85407e2fb940.exe (PID: 4008)
REMCOS has been detected (YARA)
- wab.exe (PID: 2796)
REMCOS has been detected
- wab.exe (PID: 2796)
- wab.exe (PID: 2796)
- wab.exe (PID: 2796)
REMCOS has been detected (SURICATA)
- wab.exe (PID: 2796)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4088)
- wab.exe (PID: 2796)
Starts POWERSHELL.EXE for commands execution
- 4c614a69aebe97562d09c05c5b08db70ba7cba08f6698e5a87fc85407e2fb940.exe (PID: 4008)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7016)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 7016)
Gets information about processes (POWERSHELL)
- powershell.exe (PID: 7016)
Drops the executable file immediately after the start
- powershell.exe (PID: 7016)
Executable content was dropped or overwritten
- powershell.exe (PID: 7016)
Connects to the server without a host name
- wab.exe (PID: 2796)
There is functionality for taking screenshot (YARA)
- wab.exe (PID: 2796)
Connects to unusual port
- wab.exe (PID: 2796)
Contacting a server suspected of hosting an CnC
- wab.exe (PID: 2796)
Checks for external IP
- wab.exe (PID: 2796)
Writes files like Keylogger logs
- wab.exe (PID: 2796)
INFO
Application launched itself
- chrome.exe (PID: 6296)
The process uses the downloaded file
- WinRAR.exe (PID: 4088)
- chrome.exe (PID: 6296)
- chrome.exe (PID: 5956)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4088)
Checks supported languages
- 4c614a69aebe97562d09c05c5b08db70ba7cba08f6698e5a87fc85407e2fb940.exe (PID: 4008)
- wab.exe (PID: 2796)
Reads the computer name
- 4c614a69aebe97562d09c05c5b08db70ba7cba08f6698e5a87fc85407e2fb940.exe (PID: 4008)
- wab.exe (PID: 2796)
Creates files or folders in the user directory
- 4c614a69aebe97562d09c05c5b08db70ba7cba08f6698e5a87fc85407e2fb940.exe (PID: 4008)
- wab.exe (PID: 2796)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7016)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7016)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7016)
Checks proxy server information
- wab.exe (PID: 2796)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7016)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7016)
Reads Environment values
- wab.exe (PID: 2796)
Reads the machine GUID from the registry
- wab.exe (PID: 2796)
Creates files in the program directory
- wab.exe (PID: 2796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(2796) wab.exe
C2 (1)103.67.162.233:9462
BotnetRemoteHost
Options
Connect_interval1
Install_flagFalse
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%LOCALAPPDATA%
Copy_fileremcos.exe
Startup_valueFalse
Hide_fileFalse
Mutex_nameRmc-GRR4WM
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%ProgramFiles%
Audio_dirMicRecords
Connect_delay0
Copy_dirRemcos
Keylog_dirremcos
Total processes
159
Monitored processes
25
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5208 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5216 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5324 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3036 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5320 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5008 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2796 | "C:\Program Files (x86)\windows mail\wab.exe" | C:\Program Files (x86)\Windows Mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
Remcos(PID) Process(2796) wab.exe C2 (1)103.67.162.233:9462 BotnetRemoteHost Options Connect_interval1 Install_flagFalse Install_HKCU\RunTrue Install_HKLM\RunTrue Install_HKLM\Explorer\Run1 Install_HKLM\Winlogon\Shell100000 Setup_path%LOCALAPPDATA% Copy_fileremcos.exe Startup_valueFalse Hide_fileFalse Mutex_nameRmc-GRR4WM Keylog_flag1 Keylog_path%LOCALAPPDATA% Keylog_filelogs.dat Keylog_cryptFalse Hide_keylogFalse Screenshot_flagFalse Screenshot_time5 Take_ScreenshotFalse Screenshot_path%APPDATA% Screenshot_fileScreenshots Screenshot_cryptFalse Mouse_optionFalse Delete_fileFalse Audio_record_time5 Audio_path%ProgramFiles% Audio_dirMicRecords Connect_delay0 Copy_dirRemcos Keylog_dirremcos | |||||||||||||||
| 3180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=1228 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4008 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb4088.988\4c614a69aebe97562d09c05c5b08db70ba7cba08f6698e5a87fc85407e2fb940.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb4088.988\4c614a69aebe97562d09c05c5b08db70ba7cba08f6698e5a87fc85407e2fb940.exe | WinRAR.exe | ||||||||||||
User: admin Company: recombinations remtrk Integrity Level: MEDIUM Description: endophytic forgabede Exit code: 4294967295 Modules
| |||||||||||||||
| 4024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5244 --field-trial-handle=1940,i,18029827113373196731,159544270341288025,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
29 747
Read events
25 165
Write events
4 576
Delete events
6
Modification events
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
7
Suspicious files
216
Text files
37
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFe5cf0.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RFe5cf0.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:19D1A06251A8678F85D8DE5BFAB83807 | SHA256:AA6E55DCF84CDAF0BD3F913E7B837F65500E9B71A5A7AA773D02FFBC18C7FF01 | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
56
DNS requests
50
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4920 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3800 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5980 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acq7kasl5oa3w4q75rlwwkombvea_2024.8.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.08.17.01_all_ac4pq3gxqmrypwasu2wma55qlbvq.crx3 | unknown | — | — | whitelisted |
2456 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5980 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acq7kasl5oa3w4q75rlwwkombvea_2024.8.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.08.17.01_all_ac4pq3gxqmrypwasu2wma55qlbvq.crx3 | unknown | — | — | whitelisted |
5980 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acq7kasl5oa3w4q75rlwwkombvea_2024.8.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.08.17.01_all_ac4pq3gxqmrypwasu2wma55qlbvq.crx3 | unknown | — | — | whitelisted |
5980 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acq7kasl5oa3w4q75rlwwkombvea_2024.8.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.08.17.01_all_ac4pq3gxqmrypwasu2wma55qlbvq.crx3 | unknown | — | — | whitelisted |
5980 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acq7kasl5oa3w4q75rlwwkombvea_2024.8.17.1/kiabhabjdbkjdpjbpigfodbdjmbglcoo_2024.08.17.01_all_ac4pq3gxqmrypwasu2wma55qlbvq.crx3 | unknown | — | — | whitelisted |
2796 | wab.exe | GET | 200 | 103.67.162.225:80 | http://103.67.162.225/NWdSuHibJE79.bin | unknown | — | — | unknown |
5980 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4664 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4056 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6568 | chrome.exe | 151.101.66.49:443 | bazaar.abuse.ch | FASTLY | US | unknown |
6296 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6568 | chrome.exe | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | unknown |
6568 | chrome.exe | 142.250.185.168:443 | www.googletagmanager.com | GOOGLE | US | unknown |
6568 | chrome.exe | 142.250.186.36:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
bazaar.abuse.ch |
| whitelisted |
accounts.google.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2796 | wab.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
2796 | wab.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
2796 | wab.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
1 ETPRO signatures available at the full report