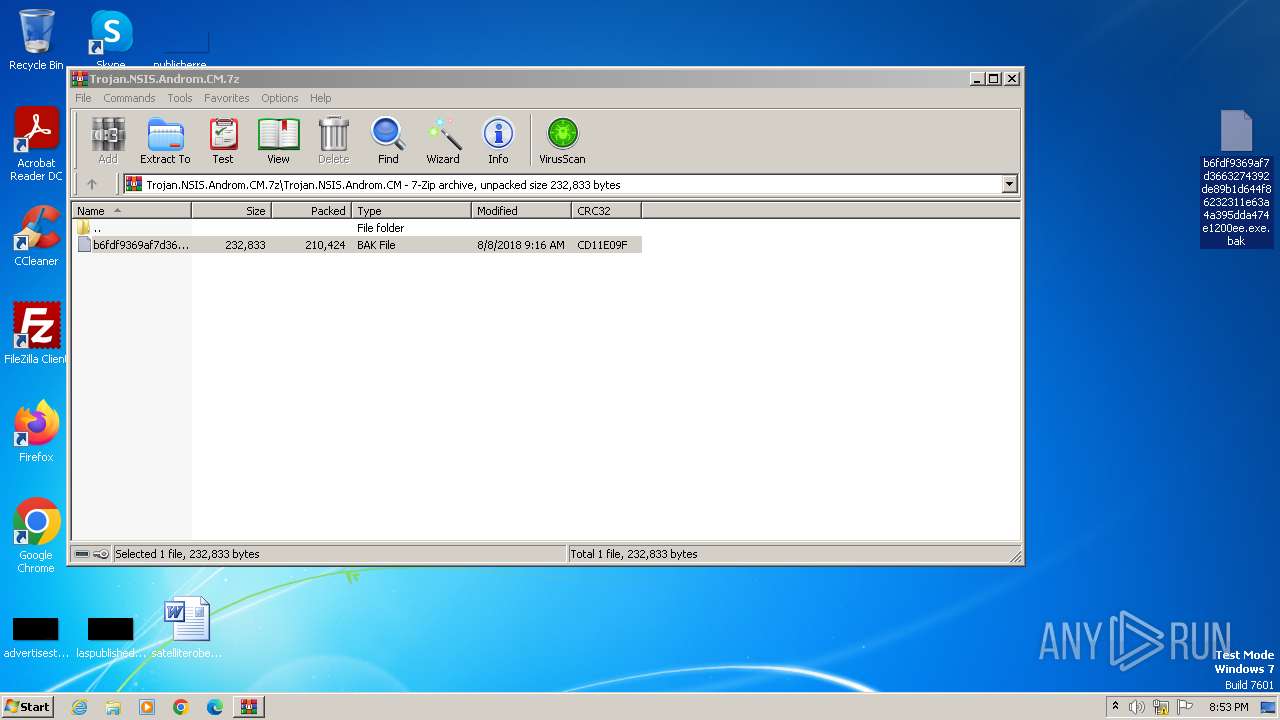
| File name: | Trojan.NSIS.Androm.CM.7z |
| Full analysis: | https://app.any.run/tasks/e5222480-5f52-43ec-8ba6-f3796c285852 |
| Verdict: | Malicious activity |
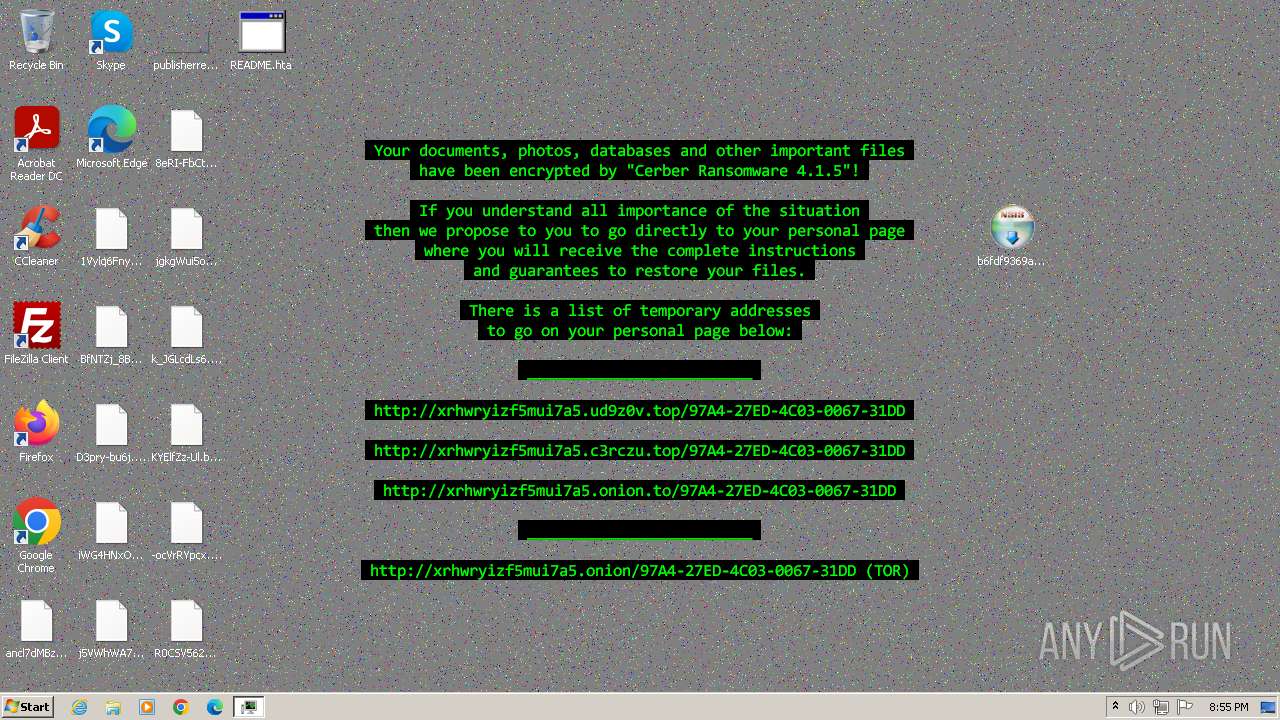
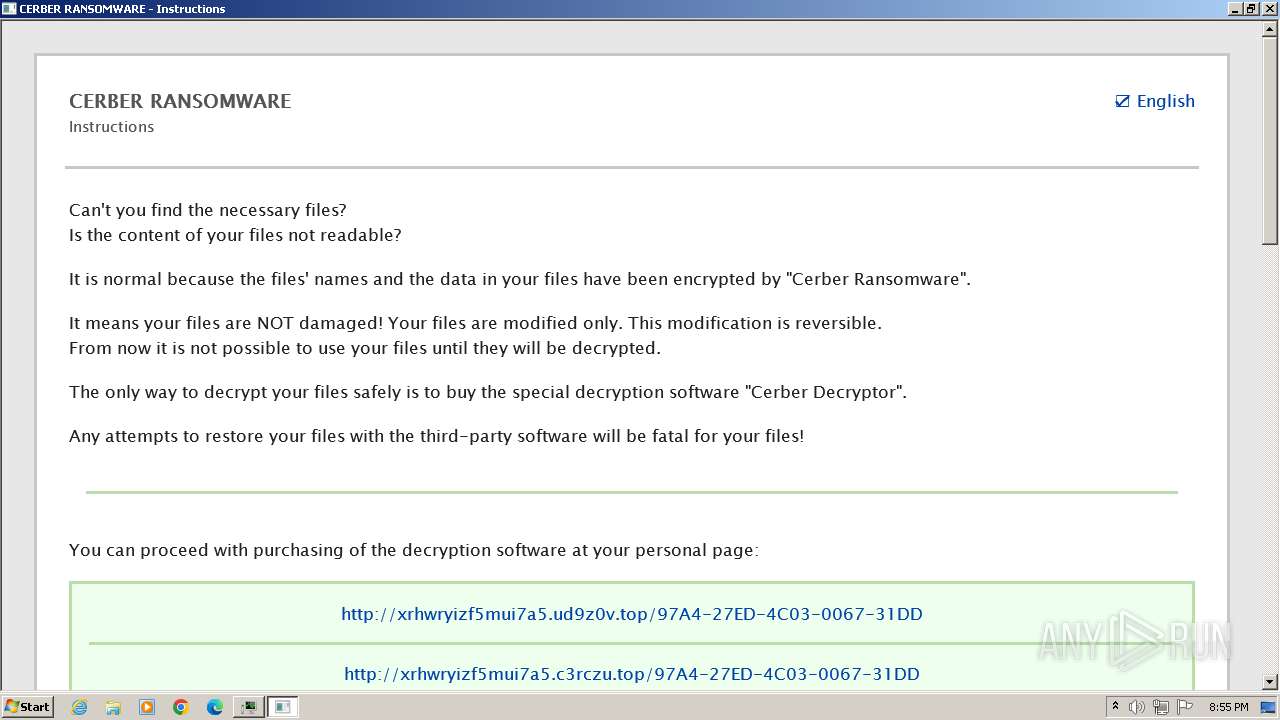
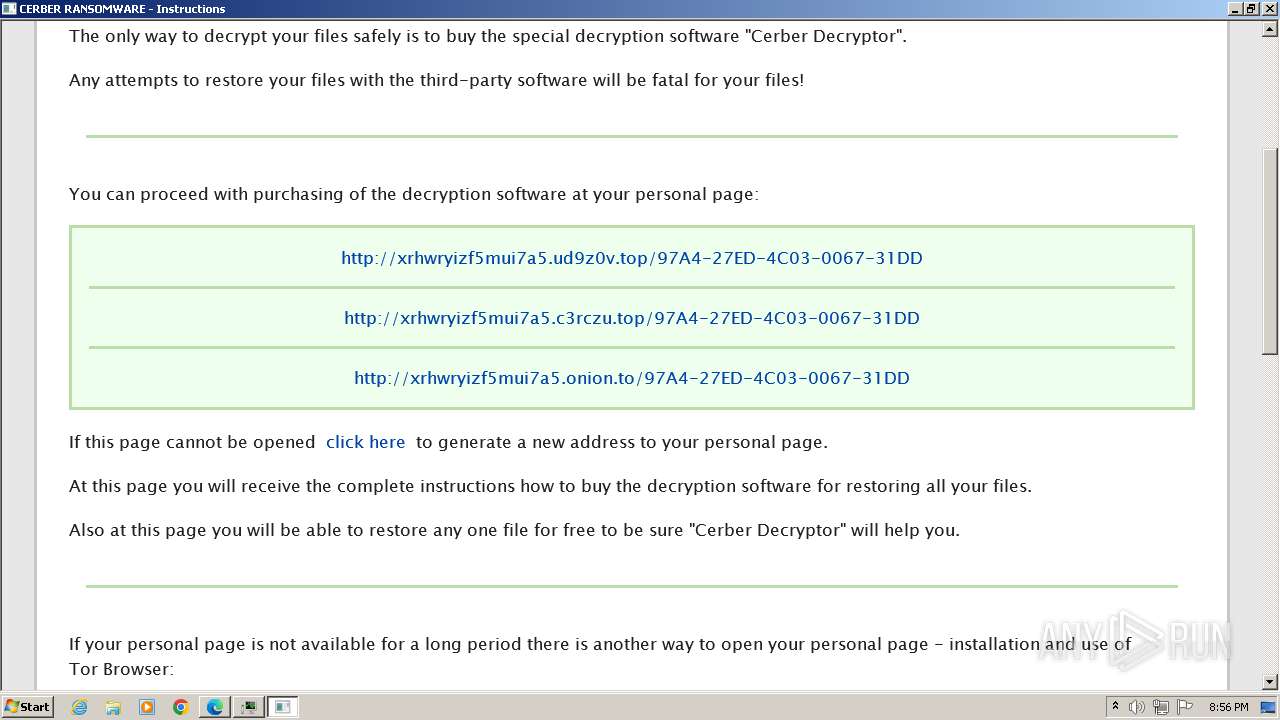
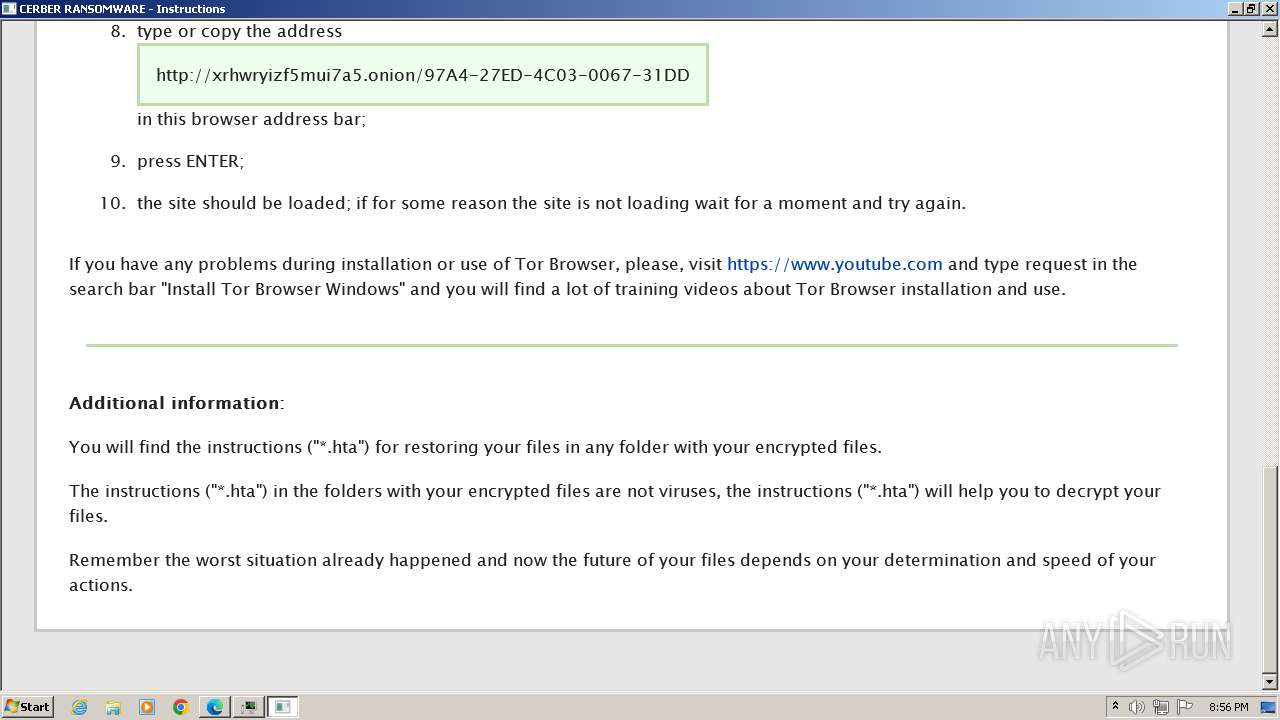
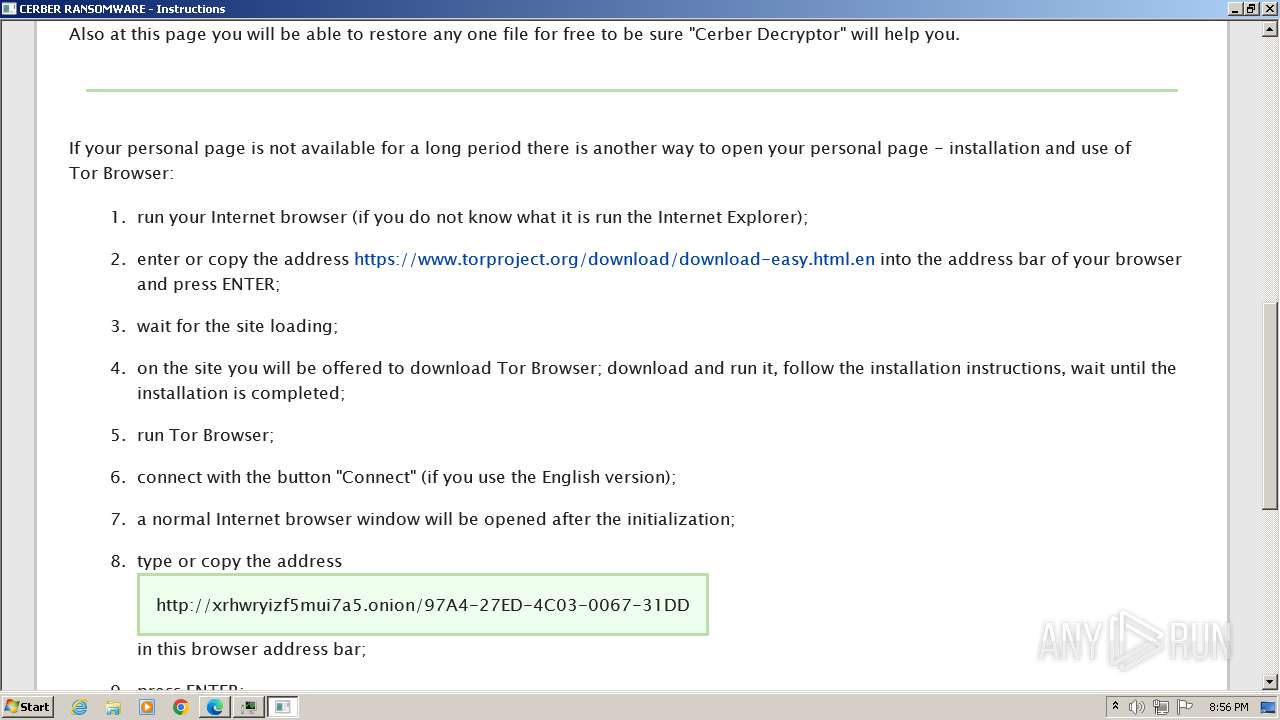
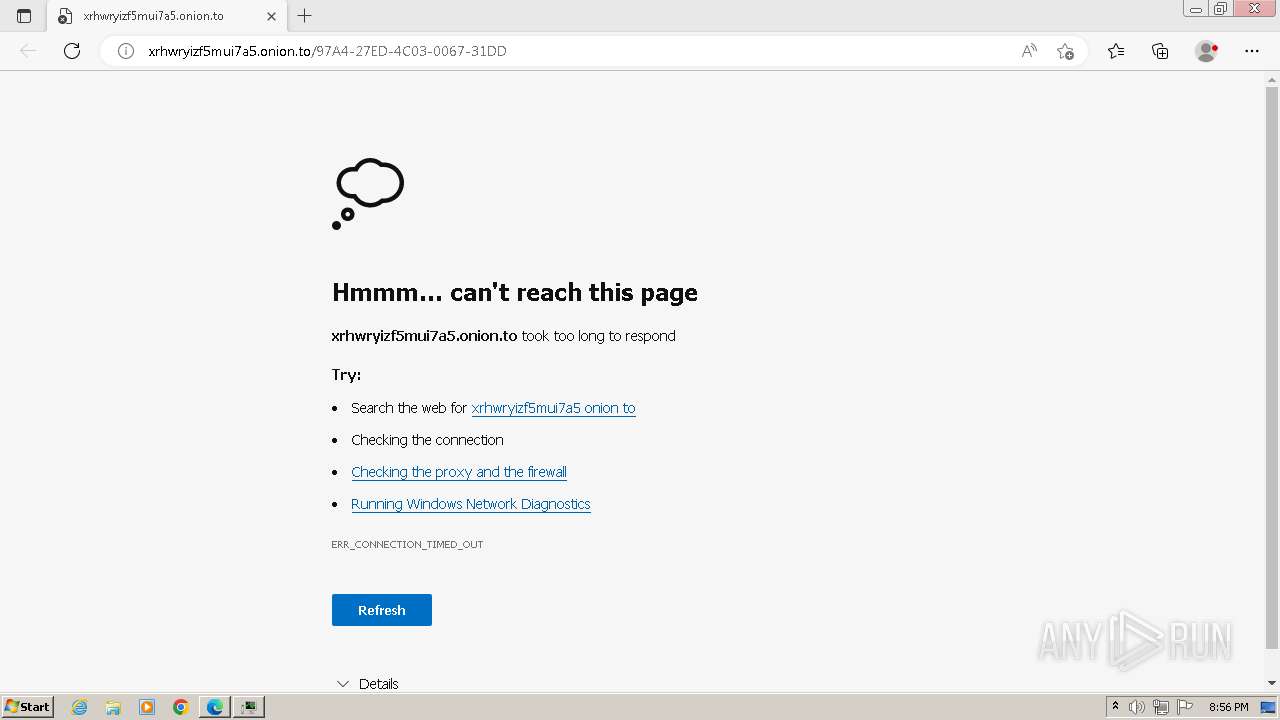
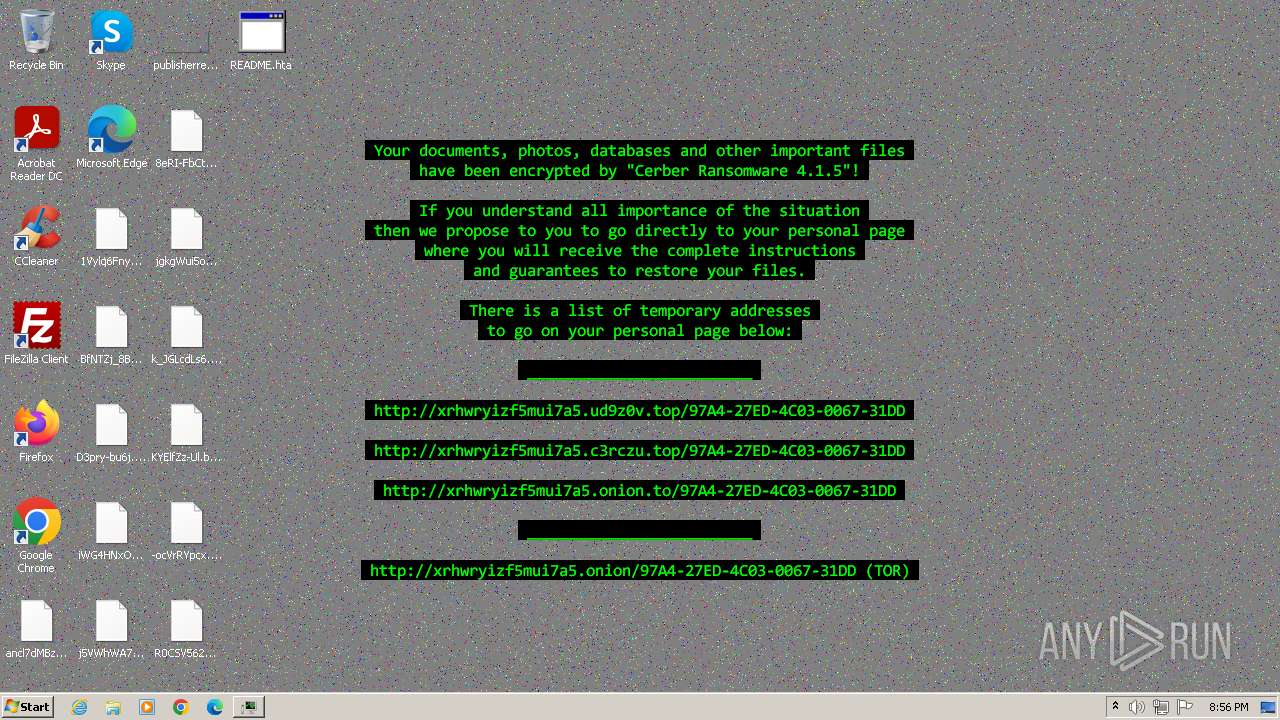
| Threats: | Cerber is a Ransomware-as-a-Service (RaaS) that appeared in 2016, spread quickly and has been evolving since. It became well-known for its file encryption, offline capabilities, and sophisticated evasion techniques. It primarily targets enterprises, financial institutions, and government entities, encrypting their data and demanding ransom payments in Bitcoin. It also targets everyday users encrypting personal files (photos, documents) with the risk of their permanent loss. |
| Analysis date: | November 20, 2023, 20:53:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | FDFFB8E3F1D4D0AC7637D37A8D001E51 |
| SHA1: | 286C0EABBFB465387C6E8E82FB0DBC8C8B1B6681 |
| SHA256: | 5FCC0C39AFFE5A135D07383A29EBF9414093E39161990A627E1417B482C227FA |
| SSDEEP: | 6144:78OOkTWFPHQiwB6GZZeWqg3ewjYQxAsb98FAHJDN1ezVr:78OOoSE5Fqg3ewjYqFbmFmJDT8r |
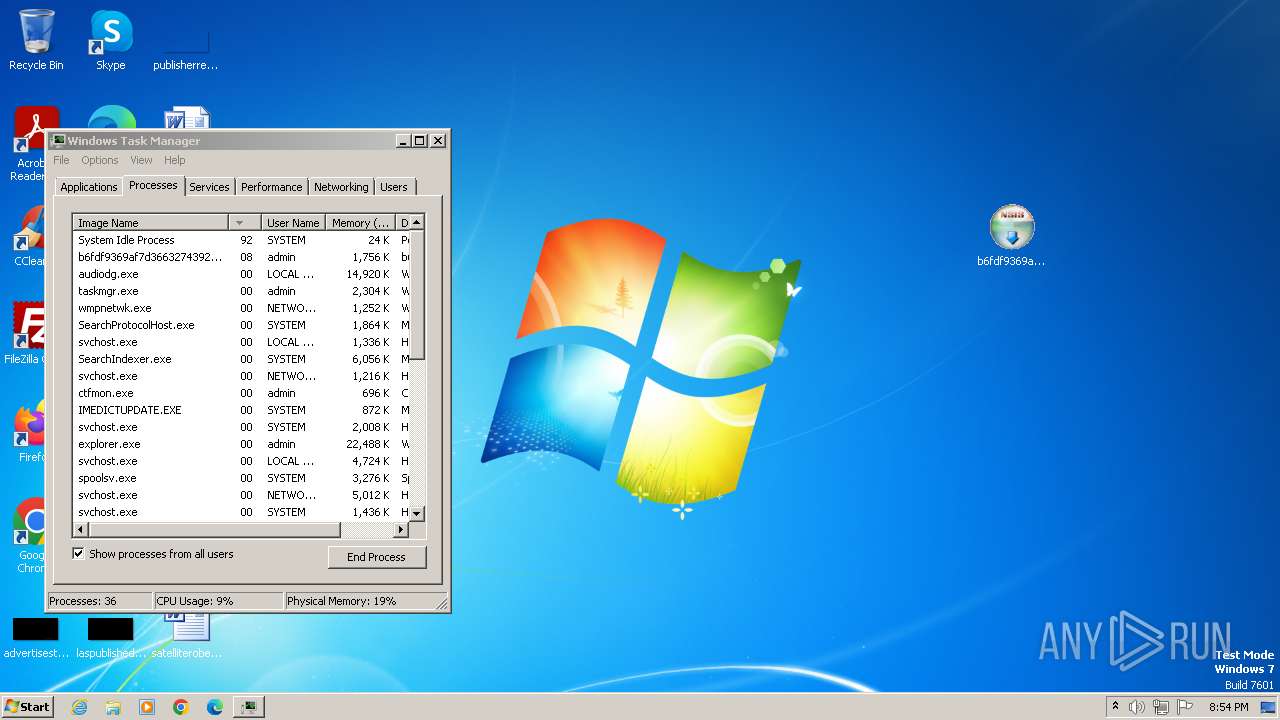
MALICIOUS
Drops the executable file immediately after the start
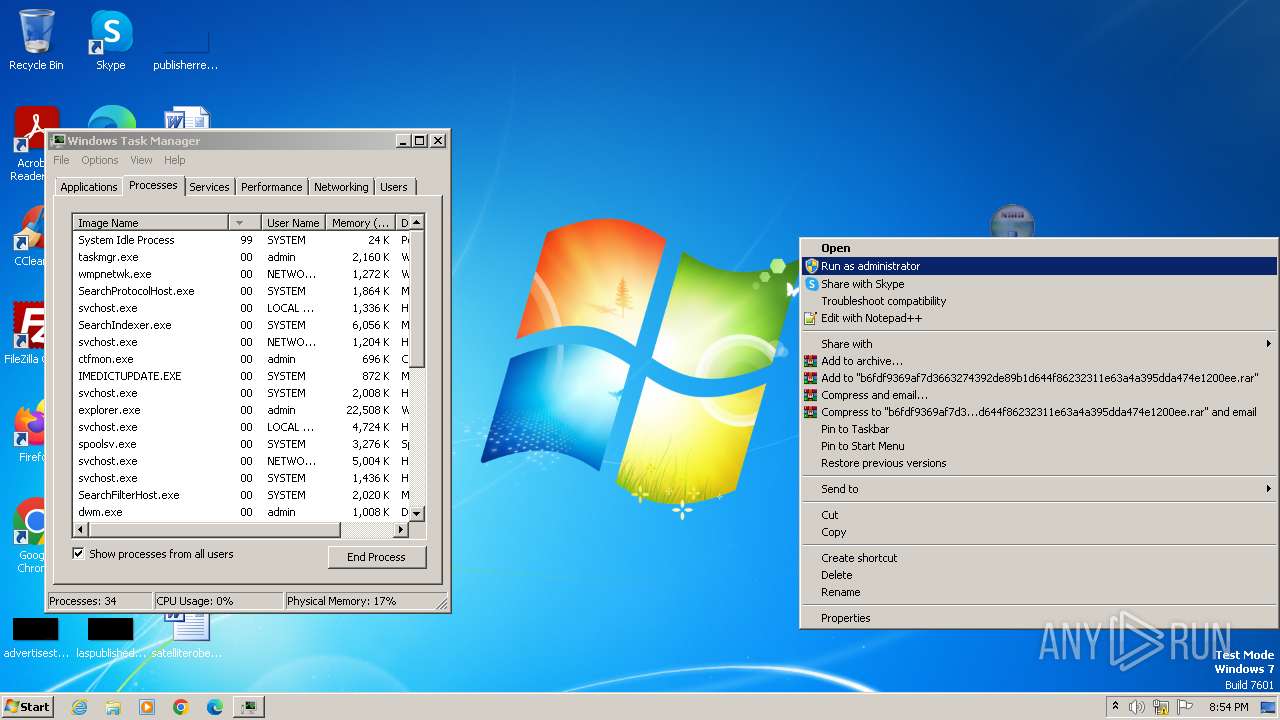
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
CERBER has been detected (SURICATA)
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
- msedge.exe (PID: 2900)
Connects to the CnC server
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Deletes shadow copies
- cmd.exe (PID: 1352)
Probably malicious OneNote attachment is found
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Actions looks like stealing of personal data
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
SUSPICIOUS
Reads the Internet Settings
- taskmgr.exe (PID: 3464)
- WMIC.exe (PID: 788)
- mshta.exe (PID: 2864)
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
- mshta.exe (PID: 3900)
Application launched itself
- taskmgr.exe (PID: 3464)
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
The process creates files with name similar to system file names
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
Malware-specific behavior (creating "System.dll" in Temp)
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
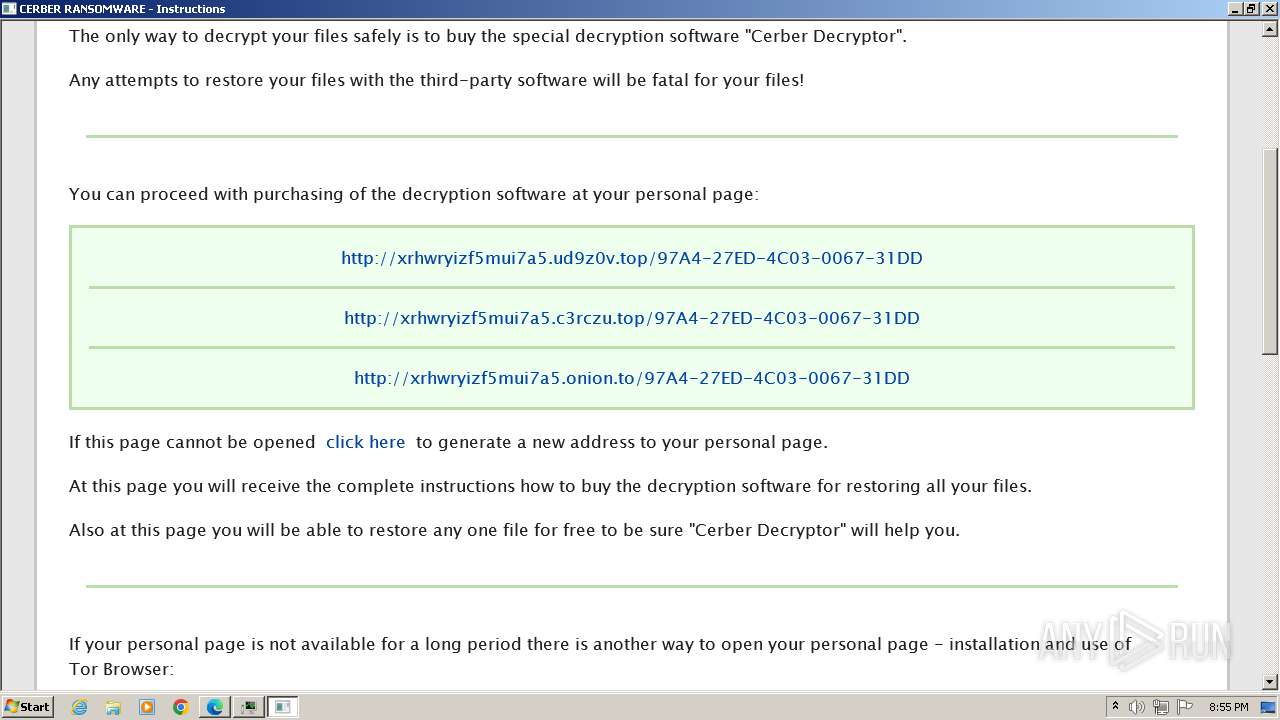
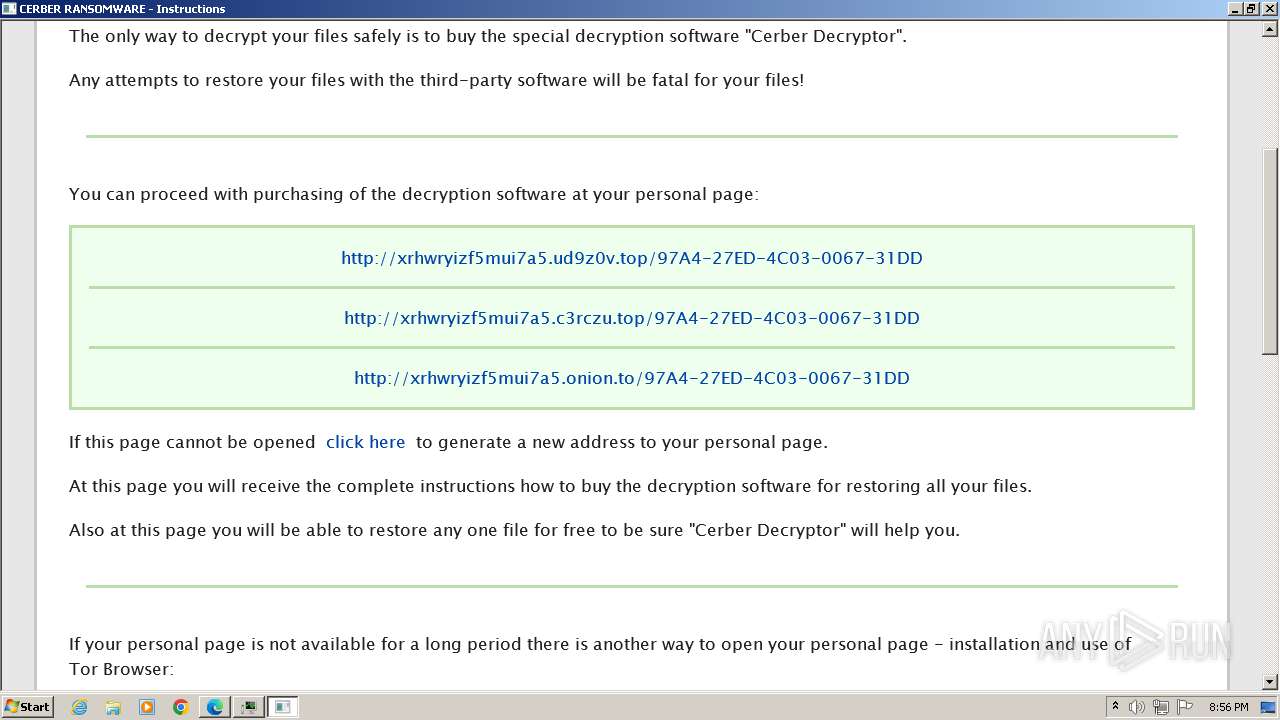
Creates files like ransomware instruction
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Starts CMD.EXE for commands execution
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Executes as Windows Service
- VSSVC.exe (PID: 1348)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3504)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3504)
INFO
Reads the computer name
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
- wmpnscfg.exe (PID: 1628)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3440)
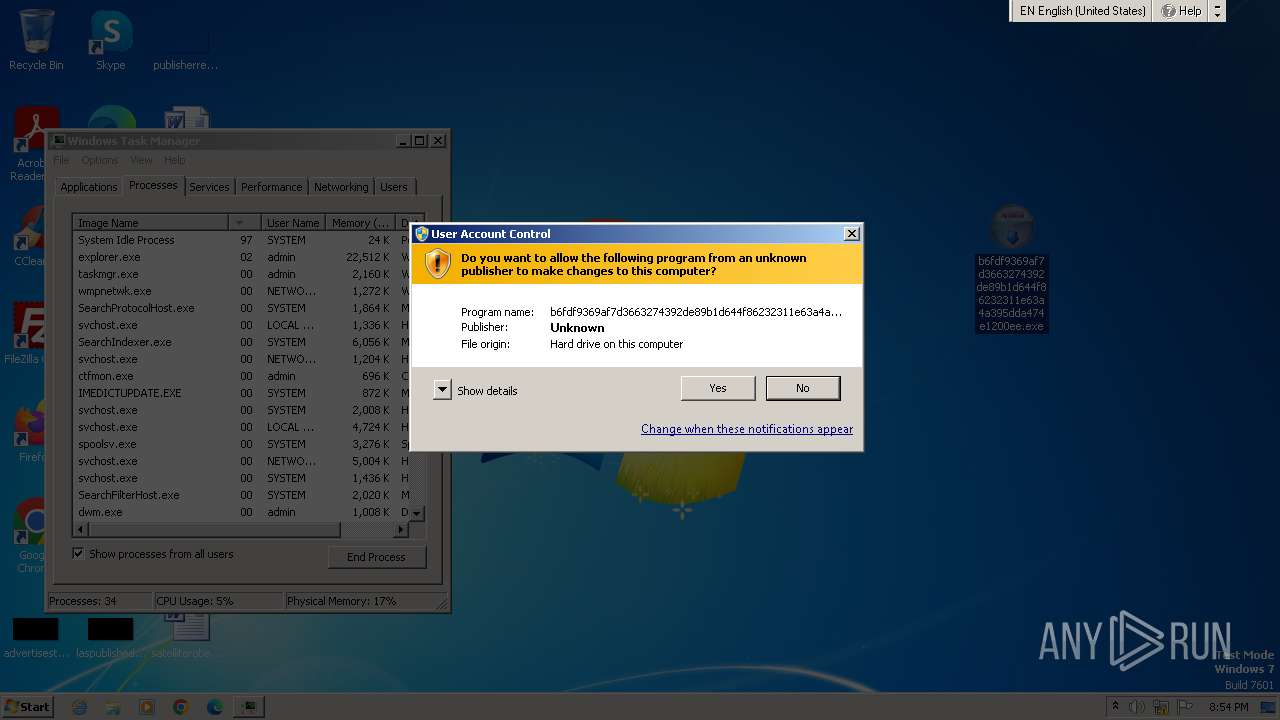
Manual execution by a user
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
- taskmgr.exe (PID: 3464)
- wmpnscfg.exe (PID: 1628)
- mshta.exe (PID: 2864)
Checks supported languages
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
- wmpnscfg.exe (PID: 1628)
Create files in a temporary directory
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 3672)
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Reads the machine GUID from the registry
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
- wmpnscfg.exe (PID: 1628)
Creates files in the program directory
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Creates files or folders in the user directory
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Checks proxy server information
- mshta.exe (PID: 2864)
- mshta.exe (PID: 3900)
Application launched itself
- msedge.exe (PID: 2112)
- msedge.exe (PID: 3060)
- msedge.exe (PID: 3340)
Reads Internet Explorer settings
- mshta.exe (PID: 3900)
- mshta.exe (PID: 2864)
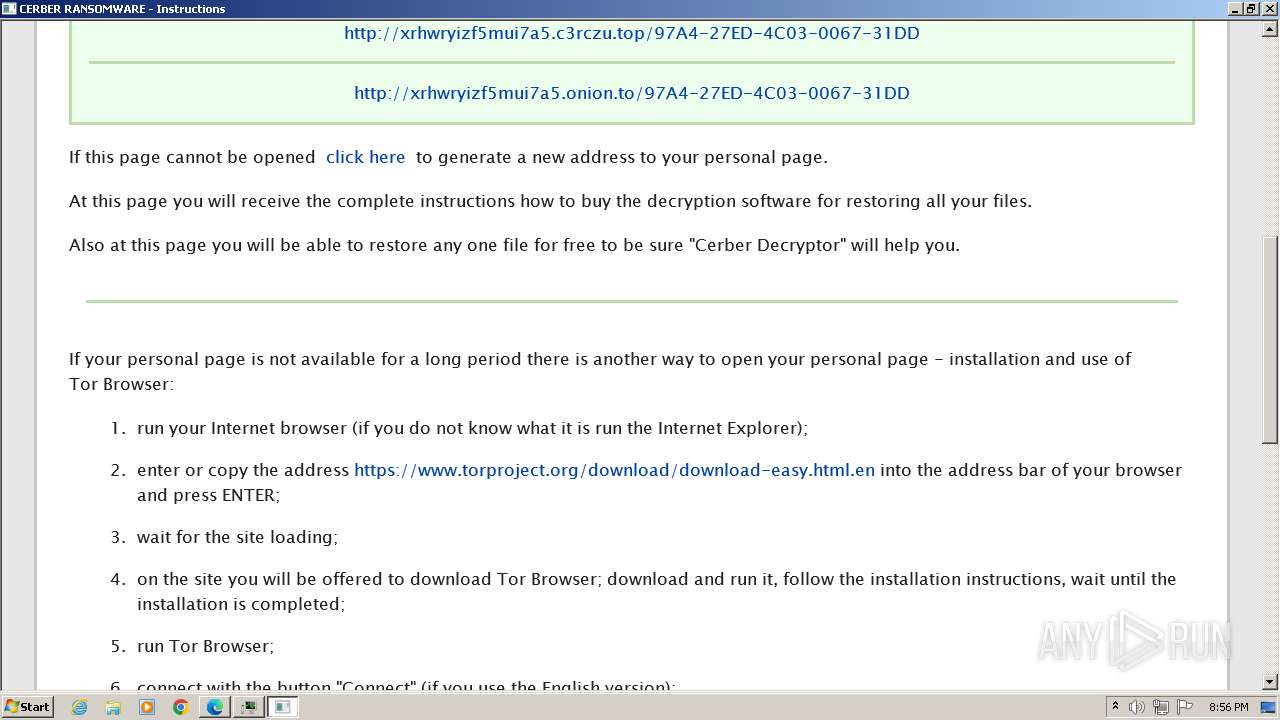
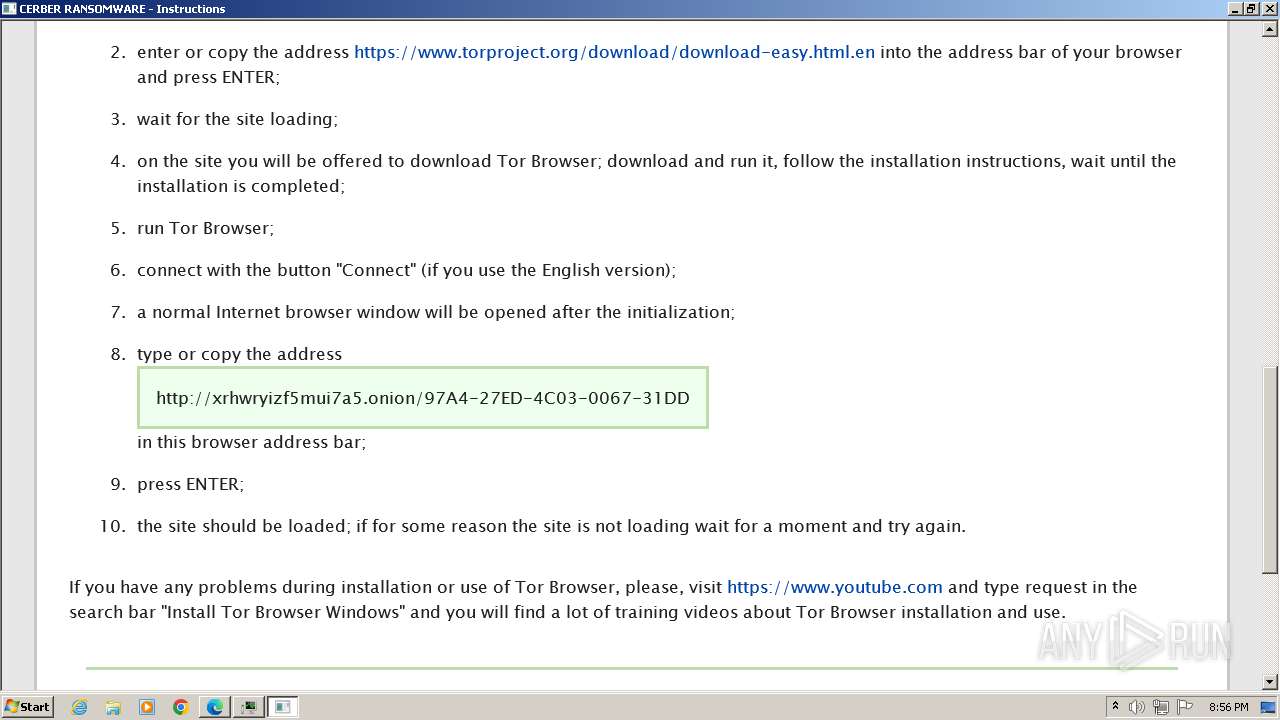
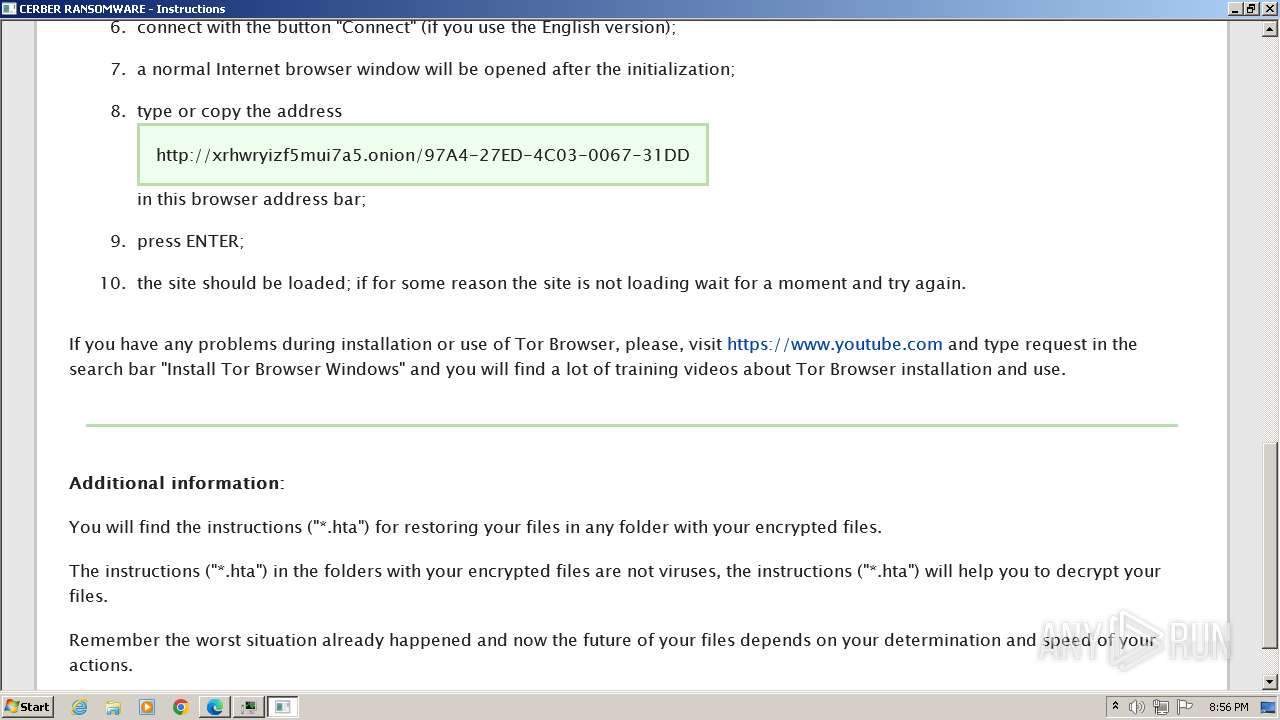
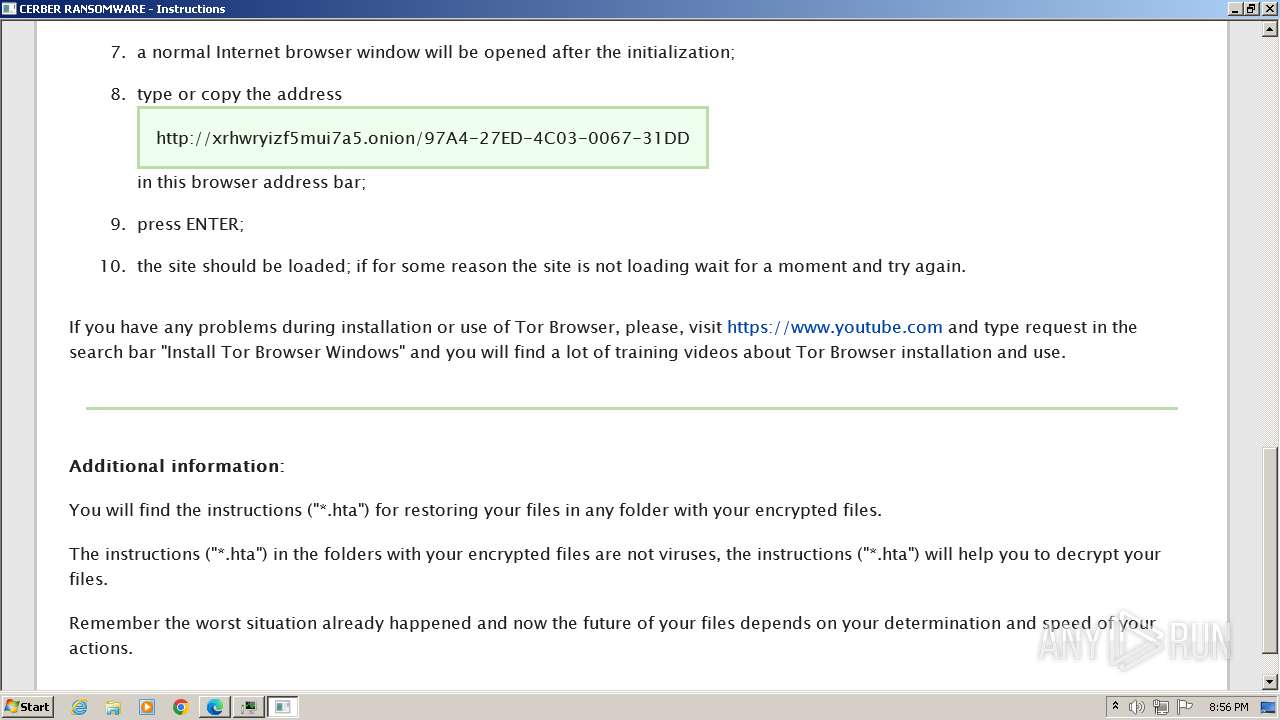
The dropped object may contain a URL to Tor Browser
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Dropped object may contain TOR URL's
- b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe (PID: 916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
97
Monitored processes
45
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=2532 --field-trial-handle=1128,i,10033223277736203375,2685887415399655616,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 788 | C:\Windows\system32\wbem\wmic.exe shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | "C:\Users\admin\Desktop\b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe" | C:\Users\admin\Desktop\b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=940 --field-trial-handle=1128,i,10033223277736203375,2685887415399655616,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1348 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1352 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=3428 --field-trial-handle=1128,i,10033223277736203375,2685887415399655616,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1364 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x69a6f598,0x69a6f5a8,0x69a6f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1588 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=3832 --field-trial-handle=1128,i,10033223277736203375,2685887415399655616,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1628 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 191
Read events
23 002
Write events
185
Delete events
4
Modification events
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
4
Suspicious files
406
Text files
266
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\AppData\Roaming\FileZilla\sKralEgEdf.b58d | binary | |
MD5:891890D5BB7F79A08EC4C7037CDF74AE | SHA256:573EF3629B57C2C52DD3379DB72158734FE9643A6C9ADA3D8B7E6D278E8A1257 | |||
| 916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Program Files\Microsoft Office\Templates\1055\ONENOTE\14\Stationery\README.hta | html | |
MD5:0FBD56E07F1895F81B00A79957ED8BED | SHA256:37ECBD4D785C1CA4F1134D31B8F460C43F90A406C75363B959A115F00221BB9A | |||
| 916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\AppData\Local\Temp\90059c37\41a4.tmp | text | |
MD5:97A427ED4C0376630BDD6B6E8B1D95CB | SHA256:C298C22622858218960A09D6B780FDD8BECA199719D45775E9E554208154449F | |||
| 3672 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\AppData\Local\Temp\Devoir.2yv | binary | |
MD5:13EC7322B0E73FAEF660A81D772E5B14 | SHA256:ABA40EB19E6EB60D7DF4AE1AF4D4B098B3FB3E15AB8818C32961FC45D465EE0E | |||
| 916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\AppData\Roaming\FileZilla\README.hta | html | |
MD5:0FBD56E07F1895F81B00A79957ED8BED | SHA256:37ECBD4D785C1CA4F1134D31B8F460C43F90A406C75363B959A115F00221BB9A | |||
| 916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\AppData\Local\Temp\90059c37\1320.tmp | binary | |
MD5:D25321900073C50B8ADFF22799076A40 | SHA256:2AE4572B0A36CAAA02130EA5F7321501C7994B45CE94FFD70C44C92E8AED0144 | |||
| 3440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3440.10652\Trojan.NSIS.Androm.CM\b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe.bak | executable | |
MD5:5CF53FF2D717D768C88FA264934F3361 | SHA256:B6FDF9369AF7D3663274392DE89B1D644F86232311E63A4A395DDA474E1200EE | |||
| 3672 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\AppData\Local\Temp\nspDB62.tmp\System.dll | executable | |
MD5:A436DB0C473A087EB61FF5C53C34BA27 | SHA256:75ED40311875312617D6711BAED0BE29FCAEE71031CA27A8D308A72B15A51E49 | |||
| 916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\AppData\Roaming\FileZilla\queue.sqlite3 | binary | |
MD5:891890D5BB7F79A08EC4C7037CDF74AE | SHA256:573EF3629B57C2C52DD3379DB72158734FE9643A6C9ADA3D8B7E6D278E8A1257 | |||
| 916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | C:\Users\admin\Documents\OneNote Notebooks\Personal\Unfiled Notes.one | one | |
MD5:94EED19B0FC5BE20710A0FC863D7096C | SHA256:5068D02B93CEFA0B09A224493D277FD3F268A6A01E2266E12E7BFBF2A3640E55 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3 296
DNS requests
52
Threats
66
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2864 | mshta.exe | GET | 403 | 104.20.21.251:80 | http://api.blockcypher.com/v1/btc/main/addrs/17gd1msp5FnMcEMF1MitTNSsYs7w7AQyCt?_=1700513749827 | unknown | binary | 98 b | unknown |
2864 | mshta.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e955e4dfd357a11c | unknown | compressed | 4.66 Kb | unknown |
2864 | mshta.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
2864 | mshta.exe | GET | 403 | 104.20.21.251:80 | http://api.blockcypher.com/v1/btc/main/addrs/17gd1msp5FnMcEMF1MitTNSsYs7w7AQyCt?_=1700513767819 | unknown | binary | 98 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | 65.55.50.1:6892 | — | — | — | whitelisted |
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | 65.55.50.2:6892 | — | — | — | whitelisted |
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | 65.55.50.6:6892 | — | — | — | whitelisted |
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | 65.55.50.5:6892 | — | — | — | whitelisted |
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | 65.55.50.0:6892 | — | — | — | whitelisted |
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | 65.55.50.4:6892 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xrhwryizf5mui7a5.ud9z0v.top |
| unknown |
btc.blockr.io |
| unknown |
api.blockcypher.com |
| whitelisted |
chain.so |
| whitelisted |
xrhwryizf5mui7a5.c3rczu.top |
| unknown |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | Malware Command and Control Activity Detected | ET MALWARE Ransomware/Cerber Checkin 2 |
916 | b6fdf9369af7d3663274392de89b1d644f86232311e63a4a395dda474e1200ee.exe | Malware Command and Control Activity Detected | ET MALWARE Ransomware/Cerber Checkin M3 (10) |
1080 | svchost.exe | A Network Trojan was detected | ET MALWARE Ransomware/Cerber Onion Domain Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2900 | msedge.exe | A Network Trojan was detected | ET MALWARE Ransomware/Cerber Onion Domain Lookup |
2900 | msedge.exe | A Network Trojan was detected | ET MALWARE Ransomware/Cerber Onion Domain Lookup |
2900 | msedge.exe | A Network Trojan was detected | ET MALWARE Ransomware/Cerber Onion Domain Lookup |
2900 | msedge.exe | A Network Trojan was detected | ET MALWARE Ransomware/Cerber Onion Domain Lookup |
1080 | svchost.exe | A Network Trojan was detected | ET MALWARE Ransomware/Cerber Onion Domain Lookup |
2900 | msedge.exe | A Network Trojan was detected | ET MALWARE Ransomware/Cerber Onion Domain Lookup |
33 ETPRO signatures available at the full report
Process | Message |
|---|---|
msedge.exe | [1120/205559.804:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|
msedge.exe | [1120/205610.154:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|