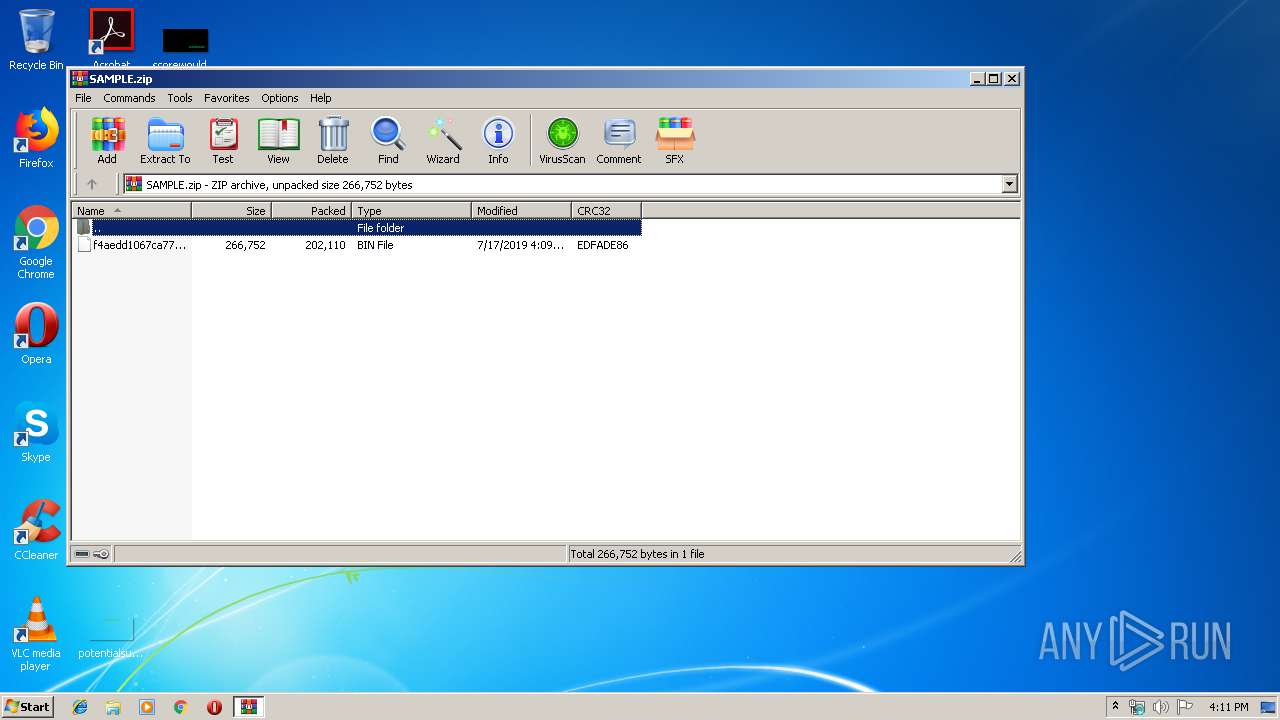
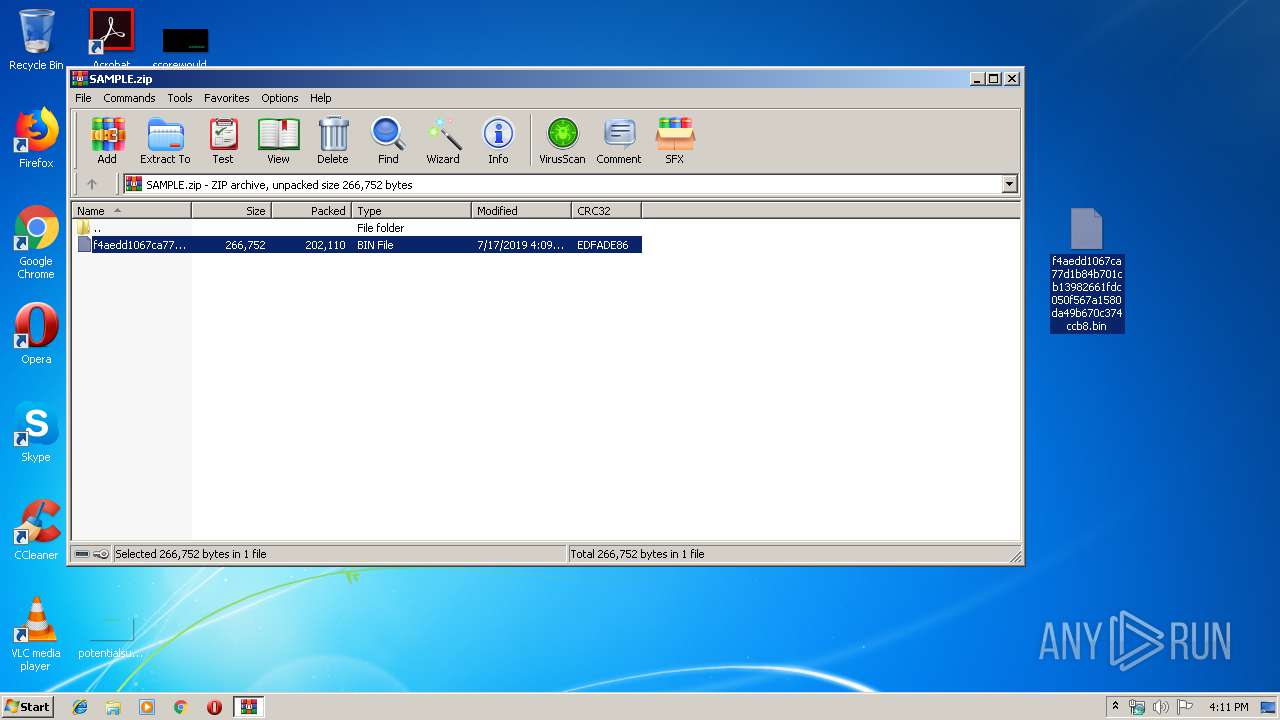
| File name: | SAMPLE.zip |
| Full analysis: | https://app.any.run/tasks/369cbebc-2773-440a-b00f-9a331781981b |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | July 17, 2019, 15:10:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3CFFF30FD98F3FEE5C7828303DE9F506 |
| SHA1: | 057FC760FDD6CA3B078C165B5F0D4AF84C0E5F34 |
| SHA256: | 5F9BD9790B769A78E3C2B844C386AB936576926C53AB0A9293EA5EEA9F1136A7 |
| SSDEEP: | 6144:xuJBkOyrBWzs7Jz3fuLQv8DHx1Jmgqno4hOGf:sBidr7JxUHhlG |
MALICIOUS
Application was dropped or rewritten from another process
- 921.exe (PID: 2468)
FORMBOOK was detected
- explorer.exe (PID: 284)
Changes the autorun value in the registry
- wscript.exe (PID: 3364)
Formbook was detected
- wscript.exe (PID: 3364)
- Firefox.exe (PID: 3136)
Actions looks like stealing of personal data
- wscript.exe (PID: 3364)
Connects to CnC server
- explorer.exe (PID: 284)
Stealing of credential data
- wscript.exe (PID: 3364)
SUSPICIOUS
Executes scripts
- explorer.exe (PID: 284)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3364)
Creates files in the user directory
- wscript.exe (PID: 3364)
Loads DLL from Mozilla Firefox
- wscript.exe (PID: 3364)
INFO
Manual execution by user
- 921.exe (PID: 2468)
- autofmt.exe (PID: 3180)
- autoconv.exe (PID: 3236)
- autofmt.exe (PID: 3300)
- wscript.exe (PID: 3364)
Creates files in the user directory
- Firefox.exe (PID: 3136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:07:17 15:09:15 |
| ZipCRC: | 0xedfade86 |
| ZipCompressedSize: | 202110 |
| ZipUncompressedSize: | 266752 |
| ZipFileName: | f4aedd1067ca77d1b84b701cb13982661fdc050f567a1580da49b670c374ccb8.bin |
Total processes
45
Monitored processes
9
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | SearchFilterHost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\Desktop\921.exe" | C:\Users\admin\Desktop\921.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2880 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SAMPLE.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3136 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | wscript.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
| 3180 | "C:\Windows\System32\autofmt.exe" | C:\Windows\System32\autofmt.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Format Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3236 | "C:\Windows\System32\autoconv.exe" | C:\Windows\System32\autoconv.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Conversion Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3300 | "C:\Windows\System32\autofmt.exe" | C:\Windows\System32\autofmt.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Format Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3364 | "C:\Windows\System32\wscript.exe" | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 4012 | /c del "C:\Users\admin\Desktop\921.exe" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 022
Read events
2 996
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SAMPLE.zip | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
2
Suspicious files
77
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2880.27825\f4aedd1067ca77d1b84b701cb13982661fdc050f567a1580da49b670c374ccb8.bin | — | |
MD5:— | SHA256:— | |||
| 284 | explorer.exe | C:\Users\admin\Desktop\f4aedd1067ca77d1b84b701cb13982661fdc050f567a1580da49b670c374ccb8.bin | executable | |
MD5:— | SHA256:— | |||
| 3364 | wscript.exe | C:\Users\admin\AppData\Roaming\N8M0605S\N8Mlogrc.ini | binary | |
MD5:— | SHA256:— | |||
| 284 | explorer.exe | C:\Users\admin\Desktop\921.exe | executable | |
MD5:— | SHA256:— | |||
| 3364 | wscript.exe | C:\Users\admin\AppData\Roaming\N8M0605S\N8Mlogri.ini | binary | |
MD5:D63A82E5D81E02E399090AF26DB0B9CB | SHA256:EAECE2EBA6310253249603033C744DD5914089B0BB26BDE6685EC9813611BAAE | |||
| 3136 | Firefox.exe | C:\Users\admin\AppData\Roaming\N8M0605S\N8Mlogrf.ini | binary | |
MD5:— | SHA256:— | |||
| 3364 | wscript.exe | C:\Users\admin\AppData\Roaming\N8M0605S\N8Mlogim.jpeg | image | |
MD5:— | SHA256:— | |||
| 3364 | wscript.exe | C:\Users\admin\AppData\Roaming\N8M0605S\N8Mlogrv.ini | binary | |
MD5:BA3B6BC807D4F76794C4B81B09BB9BA5 | SHA256:6EEBF968962745B2E9DE2CA969AF7C424916D4E3FE3CC0BB9B3D414ABFCE9507 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
17
DNS requests
13
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
284 | explorer.exe | GET | — | 162.247.99.144:80 | http://www.cntpypay.com/n22/?V4bxV=6lGfjjTIVntkc8xtg+kwq4Y6ABvtmuCGuduhKdzAT79fVtUoAZeTj5oZvFp5a8YcsDZ+7A==&RPx=7no4CHT | US | — | — | malicious |
284 | explorer.exe | GET | — | 184.168.221.35:80 | http://www.carepath-insurance.com/n22/?V4bxV=CjkAUQC0W5EdB5lDmXkABzaDVmN0gONkYT8fTCqi5HXuk+UI82JU5zgoZFRs1jxxp4ZtJA==&RPx=7no4CHT&sql=1 | US | — | — | malicious |
284 | explorer.exe | GET | — | 50.63.202.55:80 | http://www.mvrecordsmusic.com/n22/?V4bxV=3RR4DTk18MLNu7nIpOevN63L4HXsHxC3lSHBfTVJAySaX4Zi2F21cAjd4y0f0cTvYjQnFQ==&RPx=7no4CHT&sql=1 | US | — | — | malicious |
284 | explorer.exe | GET | — | 198.54.117.216:80 | http://www.toplinesurvival.com/n22/?V4bxV=lkz/yEJa8p4tbXAPD4bwxyreki3AfopjMGncVAjBRaTMUnHuIzKY93/lQThX7CzVMUsbDw==&RPx=7no4CHT&sql=1 | US | — | — | malicious |
284 | explorer.exe | POST | — | 198.54.117.216:80 | http://www.toplinesurvival.com/n22/ | US | — | — | malicious |
284 | explorer.exe | POST | — | 172.246.81.11:80 | http://www.64ydd.com/n22/ | US | — | — | malicious |
284 | explorer.exe | POST | — | 172.246.81.11:80 | http://www.64ydd.com/n22/ | US | — | — | malicious |
284 | explorer.exe | POST | — | 50.63.202.55:80 | http://www.mvrecordsmusic.com/n22/ | US | — | — | malicious |
284 | explorer.exe | POST | — | 184.168.221.35:80 | http://www.carepath-insurance.com/n22/ | US | — | — | malicious |
284 | explorer.exe | POST | — | 184.168.221.35:80 | http://www.carepath-insurance.com/n22/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
284 | explorer.exe | 172.246.81.11:80 | www.64ydd.com | Enzu Inc | US | malicious |
284 | explorer.exe | 162.247.99.144:80 | www.cntpypay.com | Cloud Iv Limited | US | malicious |
284 | explorer.exe | 184.168.221.35:80 | www.carepath-insurance.com | GoDaddy.com, LLC | US | malicious |
284 | explorer.exe | 50.63.202.55:80 | www.mvrecordsmusic.com | GoDaddy.com, LLC | US | malicious |
284 | explorer.exe | 198.54.117.216:80 | www.toplinesurvival.com | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bugattilive.com |
| unknown |
www.raydad.com |
| unknown |
www.cntpypay.com |
| malicious |
www.64ydd.com |
| malicious |
www.carepath-insurance.com |
| malicious |
www.mvrecordsmusic.com |
| malicious |
www.ahmadipourpub.com |
| unknown |
www.toplinesurvival.com |
| malicious |
www.gangguige.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
284 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
11 ETPRO signatures available at the full report