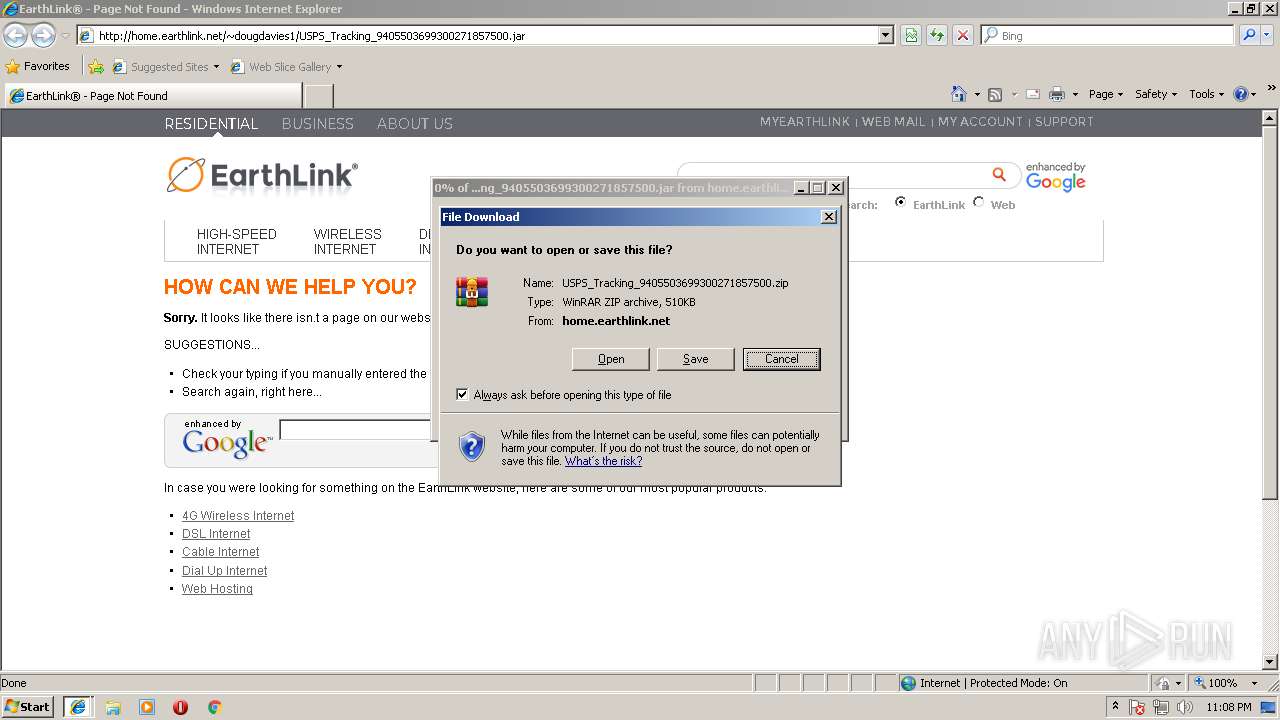
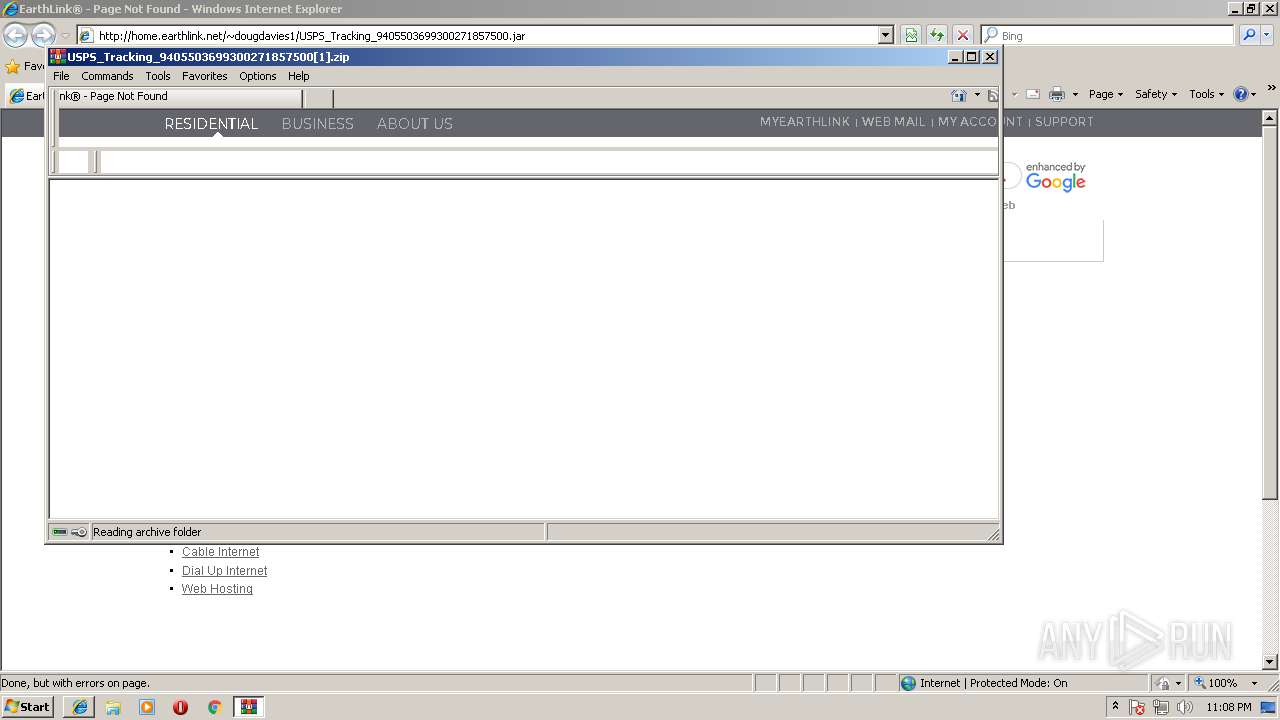
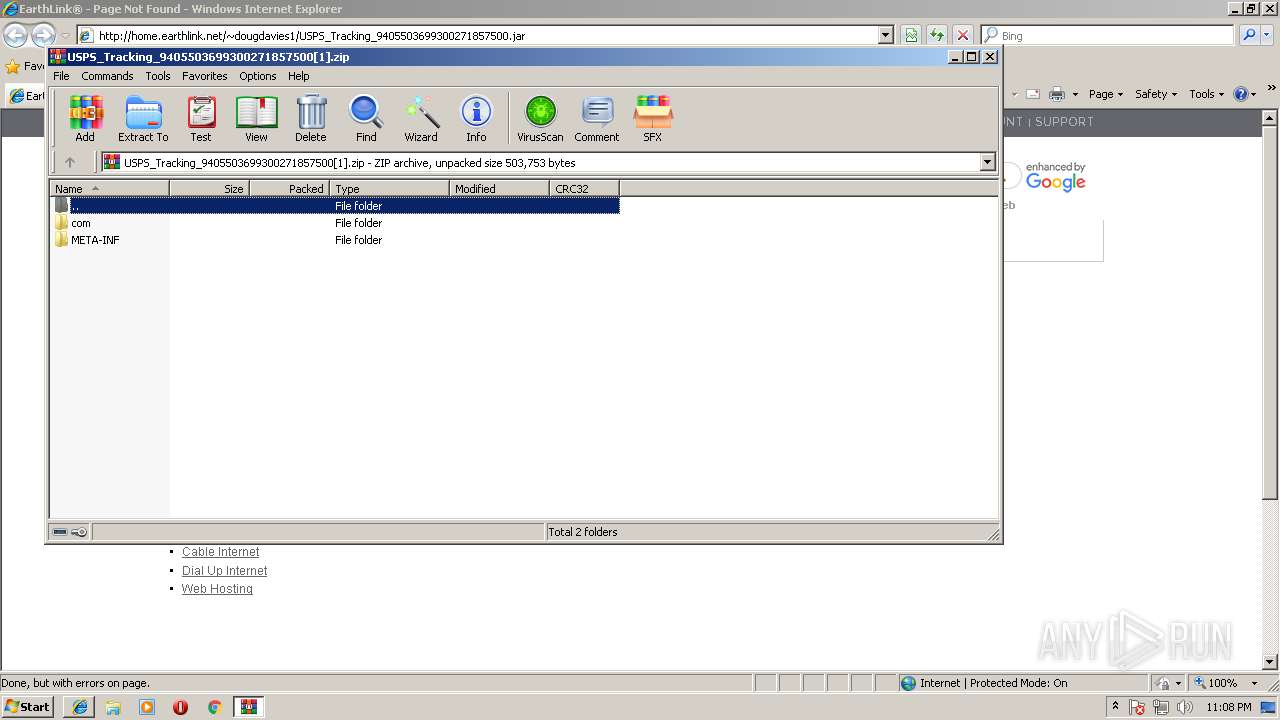
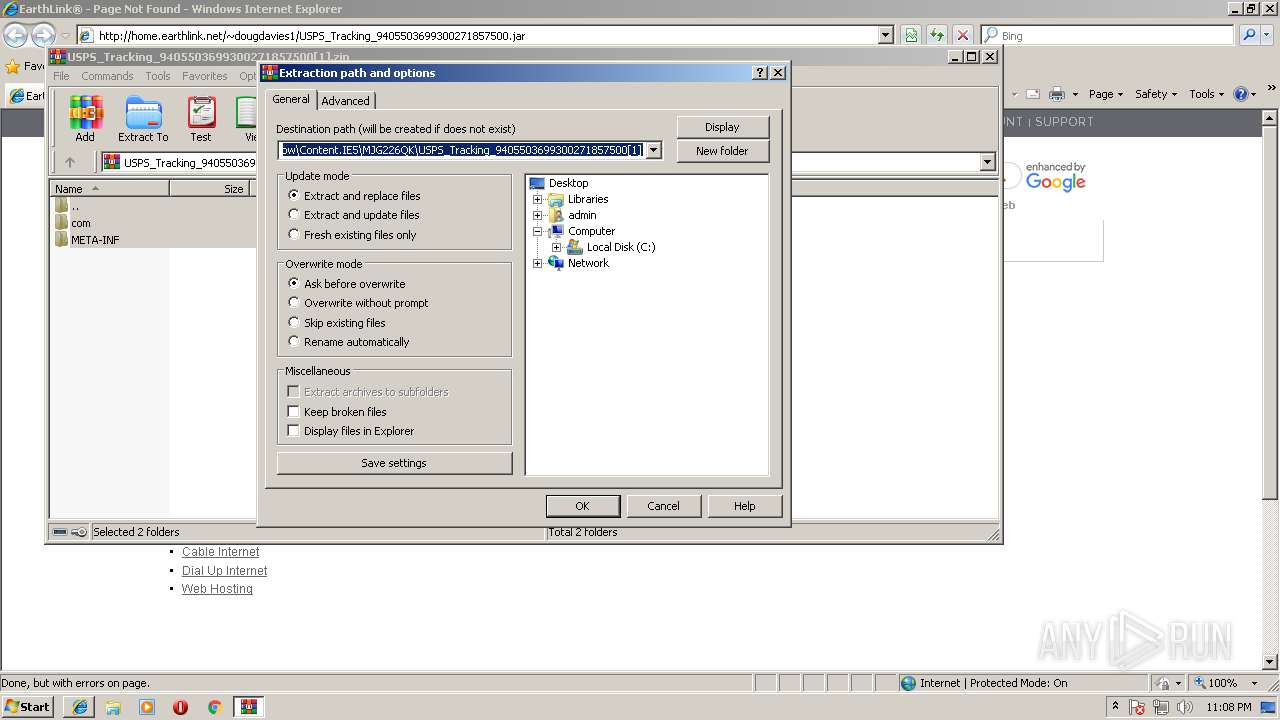
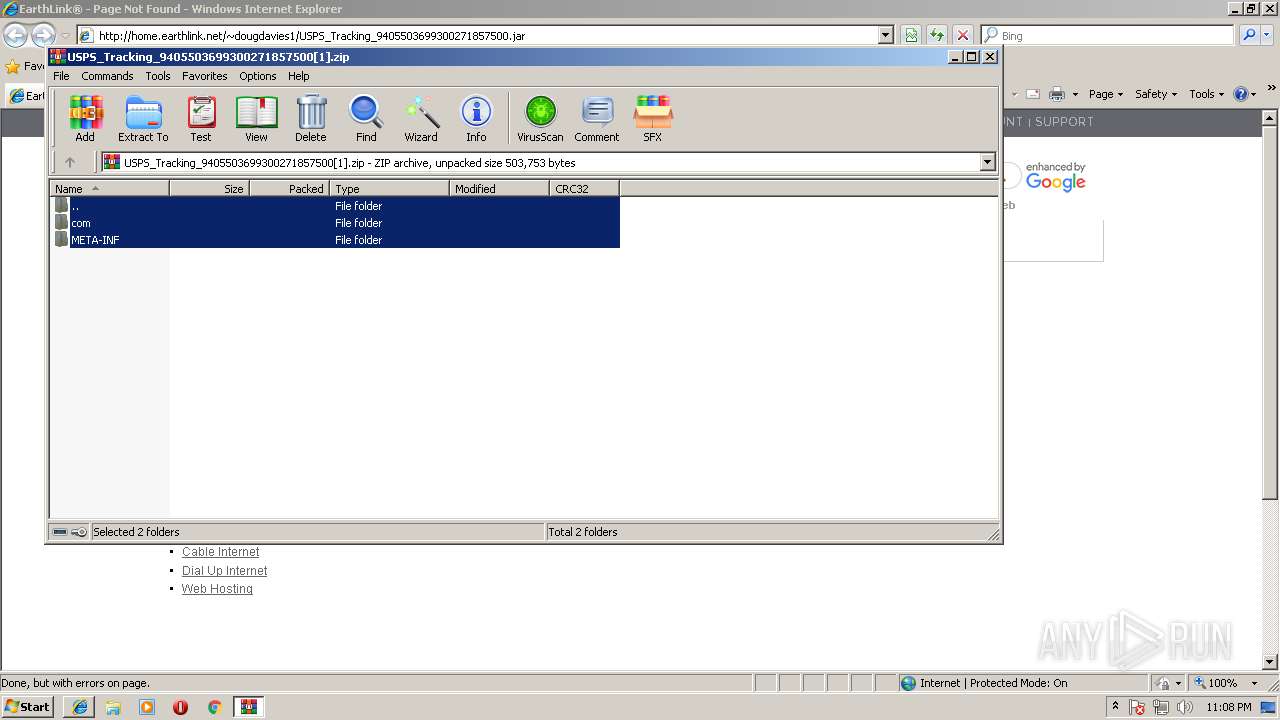
| download: | USPS_Tracking_9405503699300271857500.jar |
| Full analysis: | https://app.any.run/tasks/d8b95999-0b4a-471b-a3d7-a857e6d4a20b |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | August 07, 2018, 22:05:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | 2A8692CCC6728BD2F01F8B10E77438C3 |
| SHA1: | A928CB05D5E88F58972C1E680550B6045DB4F6CE |
| SHA256: | 5F6A89367EA3A4CA396022BC3179891D49BD732437270E7C7C62417696A3823E |
| SSDEEP: | 6144:CSkbuMdrv39MBOrhOt5WP462zLvHijnL9sSRjkiWhSkuv9M1h9vjgNvFPKY84//X:C3HFv39kO46ELv+nL9sGTSTk83HhgZd |
MALICIOUS
AdWind was detected
- java.exe (PID: 3464)
- java.exe (PID: 2000)
Changes the autorun value in the registry
- reg.exe (PID: 792)
Loads dropped or rewritten executable
- java.exe (PID: 3464)
- javaw.exe (PID: 2424)
- svchost.exe (PID: 836)
- explorer.exe (PID: 1380)
- javaw.exe (PID: 3708)
- java.exe (PID: 2000)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 3844)
- iexplore.exe (PID: 3668)
Application was dropped or rewritten from another process
- javaw.exe (PID: 2424)
- javaw.exe (PID: 3708)
- java.exe (PID: 3464)
- java.exe (PID: 2000)
SUSPICIOUS
Starts CMD.EXE for commands execution
- javaw.exe (PID: 2424)
- java.exe (PID: 3464)
- javaw.exe (PID: 3708)
- java.exe (PID: 2000)
Executes JAVA applets
- explorer.exe (PID: 1380)
- javaw.exe (PID: 2424)
Executes scripts
- cmd.exe (PID: 1180)
- cmd.exe (PID: 2240)
- cmd.exe (PID: 3788)
- cmd.exe (PID: 1652)
- cmd.exe (PID: 2376)
- cmd.exe (PID: 2760)
- cmd.exe (PID: 3416)
- cmd.exe (PID: 2692)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 2424)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 2424)
Starts itself from another location
- javaw.exe (PID: 2424)
Executable content was dropped or overwritten
- xcopy.exe (PID: 3720)
- javaw.exe (PID: 3708)
Creates files in the user directory
- xcopy.exe (PID: 3720)
- explorer.exe (PID: 1380)
- vlc.exe (PID: 3700)
- vlc.exe (PID: 1464)
Connects to unusual port
- javaw.exe (PID: 3708)
Starts Internet Explorer
- explorer.exe (PID: 1380)
- rundll32.exe (PID: 2332)
- rundll32.exe (PID: 3192)
Reads Internet Cache Settings
- explorer.exe (PID: 1380)
INFO
Creates files in the user directory
- firefox.exe (PID: 1224)
- iexplore.exe (PID: 1032)
- iexplore.exe (PID: 2204)
Application launched itself
- firefox.exe (PID: 1224)
- iexplore.exe (PID: 3256)
- iexplore.exe (PID: 2396)
- iexplore.exe (PID: 3864)
Reads CPU info
- firefox.exe (PID: 1224)
Dropped object may contain URL's
- iexplore.exe (PID: 3668)
- firefox.exe (PID: 1224)
- xcopy.exe (PID: 3720)
- vlc.exe (PID: 3700)
- vlc.exe (PID: 1464)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 3256)
- iexplore.exe (PID: 1032)
Changes internet zones settings
- iexplore.exe (PID: 1032)
- iexplore.exe (PID: 3256)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 3124)
Reads settings of System Certificates
- iexplore.exe (PID: 3668)
- pingsender.exe (PID: 2240)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1032)
- iexplore.exe (PID: 3256)
Reads Internet Cache Settings
- iexplore.exe (PID: 1032)
- iexplore.exe (PID: 2204)
- iexplore.exe (PID: 3668)
Reads internet explorer settings
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 2204)
Dropped object may contain TOR URL's
- iexplore.exe (PID: 3668)
Changes settings of System certificates
- iexplore.exe (PID: 1032)
- iexplore.exe (PID: 3256)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2204)
Modifies the open verb of a shell class
- rundll32.exe (PID: 3192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:08:07 15:42:18 |
| ZipCRC: | 0xd916bc64 |
| ZipCompressedSize: | 78 |
| ZipUncompressedSize: | 80 |
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
97
Monitored processes
44
Malicious processes
6
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | attrib +h "C:\Users\admin\zUTiCPgiyej\*.*" | C:\Windows\system32\attrib.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 792 | reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v PVrFmROmykD /t REG_EXPAND_SZ /d "\"C:\Users\admin\AppData\Roaming\Oracle\bin\javaw.exe\" -jar \"C:\Users\admin\zUTiCPgiyej\fOLRUVNBuSQ.yJqYNq\"" /f | C:\Windows\system32\reg.exe | javaw.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 836 | C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1180 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive5850616778466785587.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1224 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 55.0.3 Modules
| |||||||||||||||
| 1380 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1464 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Desktop\com\objectivated\hippocaust\Typhosis.mpg" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 2.2.6 Modules
| |||||||||||||||
| 1652 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8577679445477551878.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1660 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive5850616778466785587.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
5 873
Read events
5 045
Write events
819
Delete events
9
Modification events
| (PID) Process: | (792) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | PVrFmROmykD |
Value: "C:\Users\admin\AppData\Roaming\Oracle\bin\javaw.exe" -jar "C:\Users\admin\zUTiCPgiyej\fOLRUVNBuSQ.yJqYNq" | |||
| (PID) Process: | (1380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | 308046O0NS4N39PO |
Value: 0000000003000000070000009EDA0100000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF30C420C49A2ED40100000000 | |||
| (PID) Process: | (1380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000004D00000071000000E4D018000A00000009000000B64206007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C0072006500670065006400690074002E0065007800650000004D00D8674D003076B90618AB4E000100000068E9E101F0E9E101FCEFE101EDE00B77347B1800FEFFFFFFE72F0F77822E0F770000000004EBE1010000000078EAE1010000000078EAE1017800000030EAE101FE720F773CEBE10160EDE101780000001800000078EAE101000000004CEAE10151EE0F77F48EF6760000000004EBE1011E00000070EAE10120EF0F773076B9060AA50E771E0000000000000004EBE10100000000F88EF676F0EAE101D6A810778CEAE101A4EAE101000000000000000000004D003076B9065A008A004E76B9060A001900011B8A11A4EAE10100000000010500001876B90611000000A045500098455000E82C0F7754EBE1011000000034EB0000A2F8B40EE4EAE1018291597534EBE101049300008EF8B40EF8EAE101B69C597508934D025C0000000401000098F5E10158F5E10111000000A04550009845500098F5E101785BE203FA4FEE730000000088EB00004EF9B40E38EBE1018291597588EBE1013CEBE101279559750000000004934D0264EBE101CD94597504934D0210ECE101788E4D02E194597500000000788E4D0210ECE1016CEBE101070000002B000000BA2904007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070EAE101FFFFFFFFE0B55100FFFFFFFF90492B7500000000000000000CEAE101D5742775000400000000000070EAE101FFFFFFFFE0B55100FFFFFFFFD0155200D4165200D8B551003CEAE1012FB1587580B08B757CF7E101381E597514635975A016500070EAE101308351007000000052F8B40E50EAE101BE6A5975A016500070EAE101000000007CECE1016F625975A016500070EAE10100000400000000807C625975A016500063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E00670011000000A04550009845500073006F00660074005C00690034EB0000A2F8B40EE4EAE1018291597534EBE101049300008EF8B40EF8EAE101B69C597508934D024C06000010EBE101788E4D021CEBE10111000000A04550009845500010EBE101BCEBE101B8EBE101988E4D0288EB00004EF9B40E38EBE1018291597588EBE1013CEBE101279559750000000004934D0264EBE101CD94597504934D0210ECE101788E4D02E194597500000000788E4D0210ECE1016CEBE101070000002B000000BA2904007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070EAE101FFFFFFFFE0B55100FFFFFFFF90492B7500000000000000000CEAE101D5742775000400000000000070EAE101FFFFFFFFE0B55100FFFFFFFFD0155200D4165200D8B551003CEAE1012FB1587580B08B757CF7E101381E597514635975A016500070EAE101308351007000000052F8B40E50EAE101BE6A5975A016500070EAE101000000007CECE1016F625975A016500070EAE10100000400000000807C625975A016500063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E00670011000000A04550009845500073006F00660074005C00690034EB0000A2F8B40EE4EAE1018291597534EBE101049300008EF8B40EF8EAE101B69C597508934D024C06000010EBE101788E4D021CEBE10111000000A04550009845500010EBE101BCEBE101B8EBE101988E4D0288EB00004EF9B40E38EBE1018291597588EBE1013CEBE101279559750000000004934D0264EBE101CD94597504934D0210ECE101788E4D02E194597500000000788E4D0210ECE1016CEBE101 | |||
| (PID) Process: | (1380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | P:\Hfref\Choyvp\Qrfxgbc\Zbmvyyn Sversbk.yax |
Value: 00000000030000000000000002000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF30C420C49A2ED40100000000 | |||
| (PID) Process: | (1380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002A00000000000000290000000800000000000000080000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000004D0088003F0700000000F0F1C706F0805600F0F1C706000000000000000045200000C28C620214D57D0433AB0F77C2F47BD3FB0B0000102700000F000000B653020048D57D04F8AA0F77B6530200C28C620268D57D0430A84D02E8D57D0400000000A2010000A8D500002EC7280B58D57D0482915975A8D57D045CD57D042795597500000000BCAC4D0284D57D04CD945975BCAC4D0230D67D0430A84D02E19459750000000030A84D0230D67D048CD57D040800000000000000080000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000004D0088003F0700000000F0F1C706F0805600F0F1C706000000000000000045200000C28C620214D57D0433AB0F77C2F47BD3FB0B0000102700000F000000B653020048D57D04F8AA0F77B6530200C28C620268D57D0430A84D02E8D57D0400000000A2010000A8D500002EC7280B58D57D0482915975A8D57D045CD57D042795597500000000BCAC4D0284D57D04CD945975BCAC4D0230D67D0430A84D02E19459750000000030A84D0230D67D048CD57D040800000000000000080000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000004D0088003F0700000000F0F1C706F0805600F0F1C706000000000000000045200000C28C620214D57D0433AB0F77C2F47BD3FB0B0000102700000F000000B653020048D57D04F8AA0F77B6530200C28C620268D57D0430A84D02E8D57D0400000000A2010000A8D500002EC7280B58D57D0482915975A8D57D045CD57D042795597500000000BCAC4D0284D57D04CD945975BCAC4D0230D67D0430A84D02E19459750000000030A84D0230D67D048CD57D04 | |||
| (PID) Process: | (1380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | P:\Hfref\Choyvp\Qrfxgbc\Zbmvyyn Sversbk.yax |
Value: 00000000030000000000000003000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF30C420C49A2ED40100000000 | |||
| (PID) Process: | (1380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002A000000000000002A0000000800000000000000080000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000004D0088003F0700000000F0F1C706F0805600F0F1C706000000000000000045200000C28C620214D57D0433AB0F77C2F47BD3FB0B0000102700000F000000B653020048D57D04F8AA0F77B6530200C28C620268D57D0430A84D02E8D57D0400000000A2010000A8D500002EC7280B58D57D0482915975A8D57D045CD57D042795597500000000BCAC4D0284D57D04CD945975BCAC4D0230D67D0430A84D02E19459750000000030A84D0230D67D048CD57D040800000000000000080000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000004D0088003F0700000000F0F1C706F0805600F0F1C706000000000000000045200000C28C620214D57D0433AB0F77C2F47BD3FB0B0000102700000F000000B653020048D57D04F8AA0F77B6530200C28C620268D57D0430A84D02E8D57D0400000000A2010000A8D500002EC7280B58D57D0482915975A8D57D045CD57D042795597500000000BCAC4D0284D57D04CD945975BCAC4D0230D67D0430A84D02E19459750000000030A84D0230D67D048CD57D040800000000000000080000007B00390045003300390039003500410042002D0031004600390043002D0034004600310033002D0042003800320037002D003400380042003200340042003600430037003100370034007D005C005400610073006B004200610072005C0049006E007400650072006E006500740020004500780070006C006F007200650072002E006C006E006B0000006C006E006B0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000987880574F8C6244BB6371042380B109000000000000000000004D0088003F0700000000F0F1C706F0805600F0F1C706000000000000000045200000C28C620214D57D0433AB0F77C2F47BD3FB0B0000102700000F000000B653020048D57D04F8AA0F77B6530200C28C620268D57D0430A84D02E8D57D0400000000A2010000A8D500002EC7280B58D57D0482915975A8D57D045CD57D042795597500000000BCAC4D0284D57D04CD945975BCAC4D0230D67D0430A84D02E19459750000000030A84D0230D67D048CD57D04 | |||
| (PID) Process: | (1224) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1224) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000048000000010000000000000000000000000000000000000000000000B096B68868EBD301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000D8BFD602040000000000000000000000000000000000000000000000F4BFD602040000000000000000000000000000000000000000000000D8372A0000000000FFFFFFFF000000000000000000000000010000002E00000000000000000000000000000002000000C0A801640000000000000000D84ED505AC02000005000000010000000000000000000000010000000000000000000000BF060000000000000000000000000000000000001000000088C0D60204000000000000000000000000000000000000000000000000000000C8E40C00000000000C0000000000000000000000 | |||
| (PID) Process: | (1380) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | 308046O0NS4N39PO |
Value: 0000000003000000080000009EDA0100000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF30C420C49A2ED40100000000 | |||
Executable files
112
Suspicious files
242
Text files
181
Unknown types
125
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2424 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3464 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2424 | javaw.exe | C:\Users\admin\AppData\Local\Temp\_0.132812575605584247522059171407252789.class | java | |
MD5:781FB531354D6F291F1CCAB48DA6D39F | SHA256:97D585B6AFF62FB4E43E7E6A5F816DCD7A14BE11A88B109A9BA9E8CD4C456EB9 | |||
| 3720 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\COPYRIGHT | text | |
MD5:89F660D2B7D58DA3EFD2FECD9832DA9C | SHA256:F6A08C9CC04D7C6A86576C1EF50DD0A690AE5CB503EFD205EDB2E408BD8D557B | |||
| 3720 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\bin\bci.dll | executable | |
MD5:6D8D8A26450EE4BA0BE405629EA0A511 | SHA256:7945365A3CD40D043DAE47849E6645675166920958300E64DEA76A865BC479AF | |||
| 2424 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Retrive5850616778466785587.vbs | text | |
MD5:A32C109297ED1CA155598CD295C26611 | SHA256:45BFE34AA3EF932F75101246EB53D032F5E7CF6D1F5B4E495334955A255F32E7 | |||
| 3720 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\README.txt | text | |
MD5:0F1123976B959AC5E8B89EB8C245C4BD | SHA256:963095CF8DB76FB8071FD19A3110718A42F2AB42B27A3ADFD9EC58981C3E88D2 | |||
| 2424 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Retrive9036956868913966174.vbs | text | |
MD5:3BDFD33017806B85949B6FAA7D4B98E4 | SHA256:9DA575DD2D5B7C1E9BAB8B51A16CDE457B3371C6DCDB0537356CF1497FA868F6 | |||
| 3720 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\Welcome.html | html | |
MD5:27CF299B6D93FACA73FBCDCF4AECFD93 | SHA256:3F1F0EE75588DBBA3B143499D08AA9AB431E4A34E483890CFAC94A8E1061B7CF | |||
| 3720 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\bin\eula.dll | executable | |
MD5:6F1188DF337E62427791C77EA36E6EEF | SHA256:DEC4F2F32EDC45F70E7119C9E52C4CEF44BB9AA627DBEC1EE70F61D37468556B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
83
TCP/UDP connections
89
DNS requests
116
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1224 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1224 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1224 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1224 | firefox.exe | POST | 200 | 172.217.168.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
1224 | firefox.exe | POST | 200 | 172.217.168.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
1224 | firefox.exe | POST | 200 | 172.217.168.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
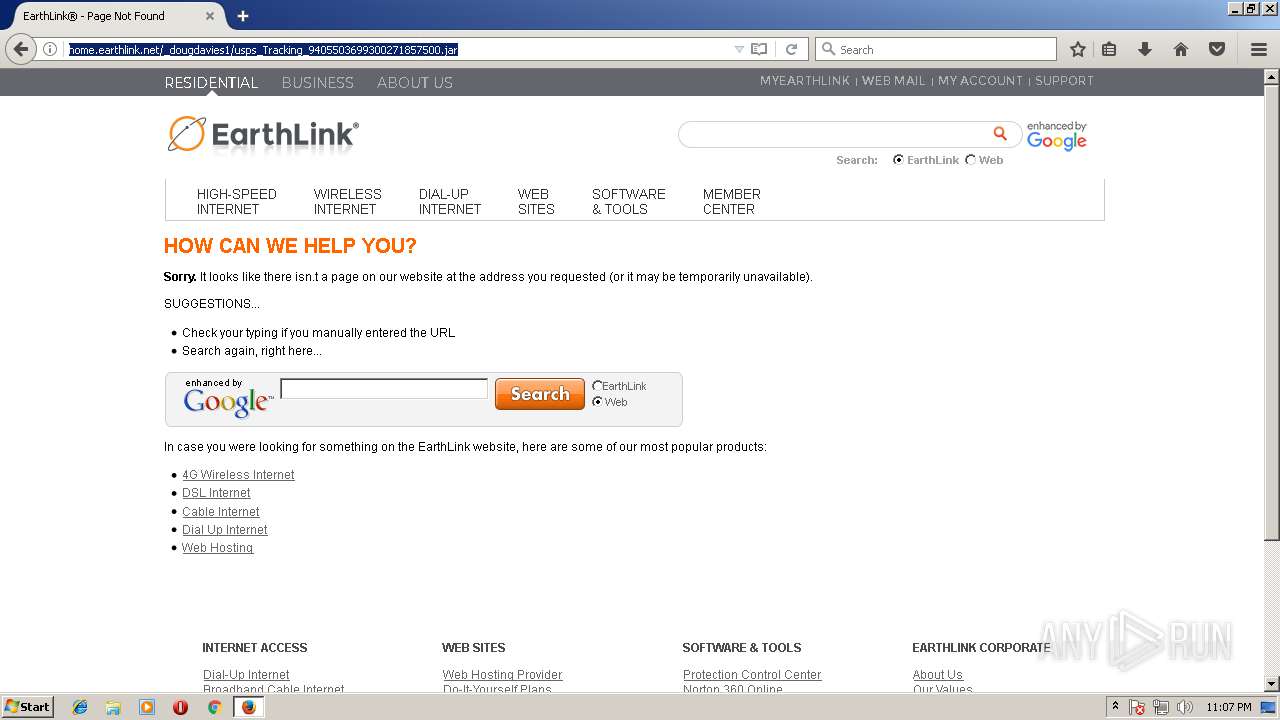
1224 | firefox.exe | GET | 200 | 23.185.0.2:80 | http://www.earthlink.net/css/core.css | US | text | 3.41 Kb | malicious |
1224 | firefox.exe | POST | 200 | 172.217.168.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
1224 | firefox.exe | POST | 200 | 172.217.168.14:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
1224 | firefox.exe | GET | 200 | 23.185.0.2:80 | http://www.earthlink.net/js/nav.js | US | html | 443 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1224 | firefox.exe | 2.16.186.50:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
1224 | firefox.exe | 52.37.53.20:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
1224 | firefox.exe | 52.41.78.152:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
1224 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1224 | firefox.exe | 54.230.46.9:443 | snippets.cdn.mozilla.net | Amazon.com, Inc. | US | whitelisted |
1224 | firefox.exe | 216.58.207.78:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
3708 | javaw.exe | 95.168.176.139:4534 | didobanty1.ddns.net | — | TR | malicious |
1224 | firefox.exe | 172.217.168.14:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1224 | firefox.exe | 216.58.215.238:443 | safebrowsing-cache.google.com | Google Inc. | US | whitelisted |
1224 | firefox.exe | 172.217.23.164:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
aus5.mozilla.org |
| whitelisted |
a1089.d.akamai.net |
| whitelisted |
balrog-aus5.r53-2.services.mozilla.com |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
drcwo519tnci7.cloudfront.net |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3708 | javaw.exe | A Network Trojan was detected | ET TROJAN Possible Adwind SSL Cert (assylias.Inc) |
Process | Message |
|---|---|
vlc.exe | core libvlc: one instance mode ENABLED
|
vlc.exe | core libvlc: Running vlc with the default interface. Use 'cvlc' to use vlc without interface.
|
vlc.exe | es demux error: cannot peek
|
vlc.exe | es demux error: cannot peek
|
vlc.exe | es demux error: cannot peek
|
vlc.exe | es demux error: cannot peek
|
vlc.exe | es demux error: cannot peek
|
vlc.exe | es demux error: cannot peek
|
vlc.exe | es demux error: cannot peek
|
vlc.exe | es demux error: cannot peek
|