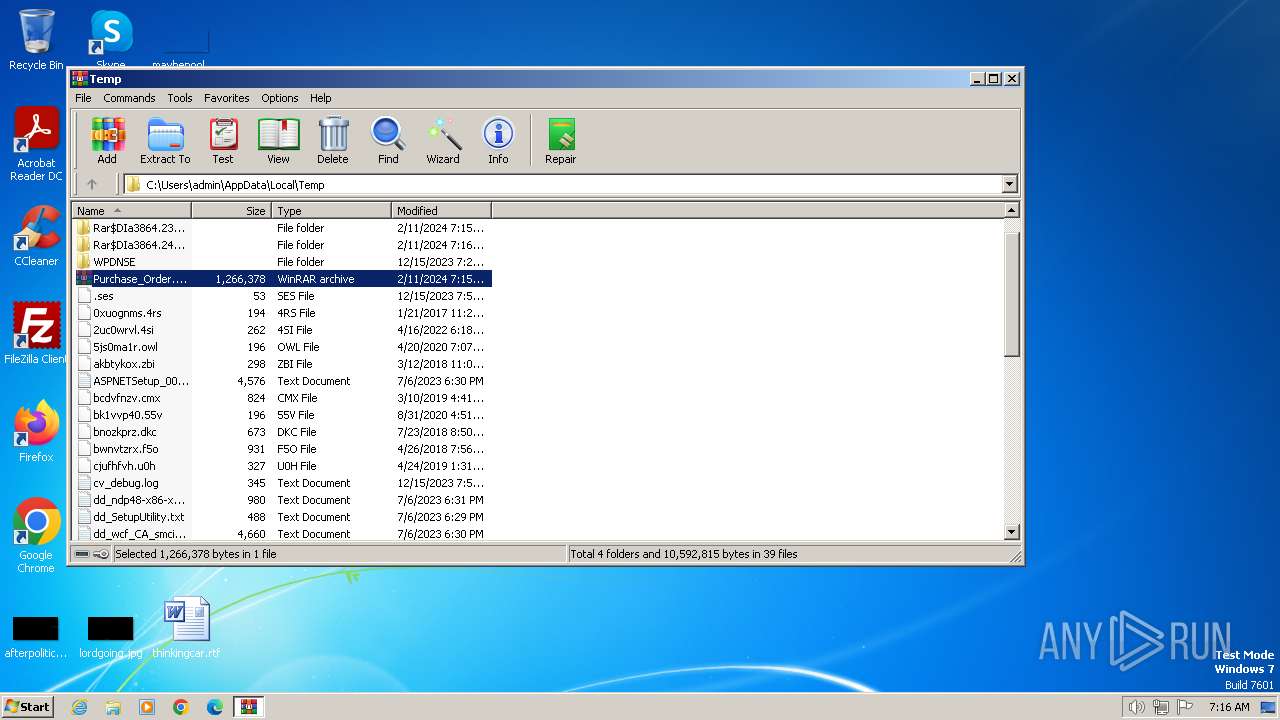
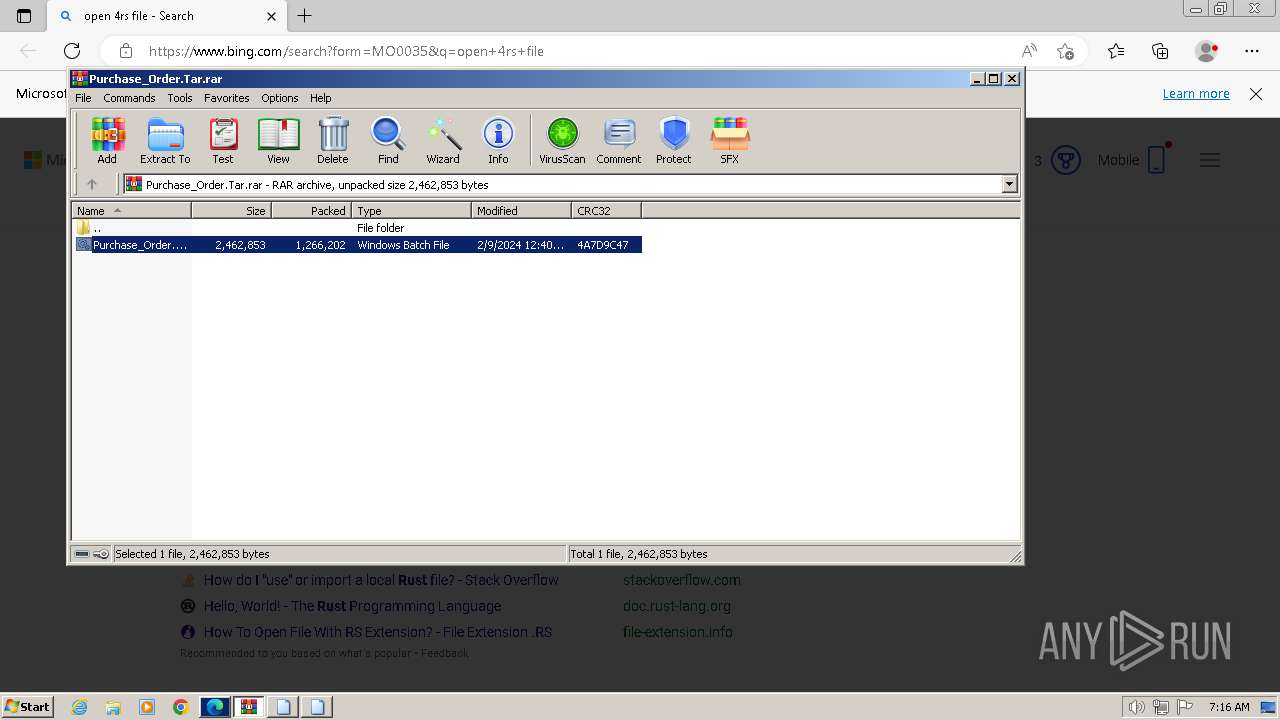
| File name: | Purchase_Order.Tar |
| Full analysis: | https://app.any.run/tasks/46606c79-a426-4cff-90e3-04abcdfdff94 |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | February 11, 2024, 07:15:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 093389E2241D09DC50661B02204D1F67 |
| SHA1: | 94F07ACAA3BF4AD44A8ACEE0DB1AF86094B3DCC8 |
| SHA256: | 5F24B1097A00C529B41E99D0BB108EEAA12A4EA99A4AF8576460435C9B42C4B3 |
| SSDEEP: | 49152:kGp7Oigws+JHFoRG1Ir6ilc9kksPCezng5dkOLQGsD66pSDWMH5e6CopN4gW5F/6:VtFr1cln3PCUCdJQGsDLoW+5xFujE4A3 |
MALICIOUS
DBATLOADER has been detected (YARA)
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- pointer.com (PID: 3724)
- pointer.com (PID: 1376)
Drops the executable file immediately after the start
- pointer.com (PID: 1040)
Actions looks like stealing of personal data
- colorcpl.exe (PID: 2592)
FORMBOOK has been detected (YARA)
- colorcpl.exe (PID: 2592)
Connects to the CnC server
- explorer.exe (PID: 1164)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 1164)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3864)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 2860)
- cmd.exe (PID: 1348)
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- cmd.exe (PID: 1236)
- pointer.com (PID: 3724)
- pointer.com (PID: 1376)
- cmd.exe (PID: 3736)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3864)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 3772)
- certutil.exe (PID: 3660)
- pointer.com (PID: 1040)
- cmd.exe (PID: 2332)
- certutil.exe (PID: 4004)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 1348)
- pointer.com (PID: 1644)
- cmd.exe (PID: 2832)
- xzdfhdfY.pif (PID: 2488)
- xzdfhdfY.pif (PID: 2972)
- cmd.exe (PID: 2648)
- certutil.exe (PID: 4000)
- pointer.com (PID: 3724)
- cmd.exe (PID: 2100)
- certutil.exe (PID: 2732)
- cmd.exe (PID: 3560)
- pointer.com (PID: 1376)
- xzdfhdfY.pif (PID: 3448)
- xzdfhdfY.pif (PID: 1644)
- cmd.exe (PID: 2168)
Executable content was dropped or overwritten
- certutil.exe (PID: 3660)
- pointer.com (PID: 1040)
- xcopy.exe (PID: 848)
- xcopy.exe (PID: 2152)
- certutil.exe (PID: 4000)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2964)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 4004)
- cmd.exe (PID: 2728)
Application launched itself
- cmd.exe (PID: 3720)
- cmd.exe (PID: 2860)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 1236)
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 3720)
- cmd.exe (PID: 2860)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 1236)
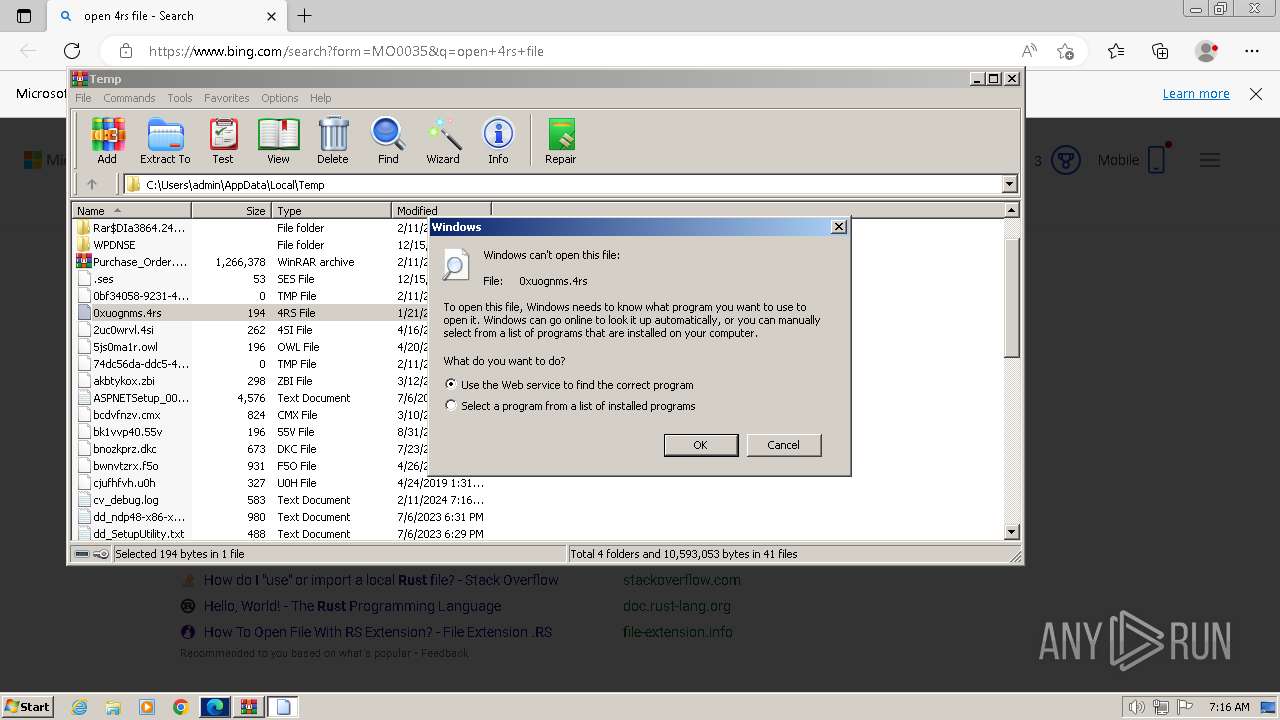
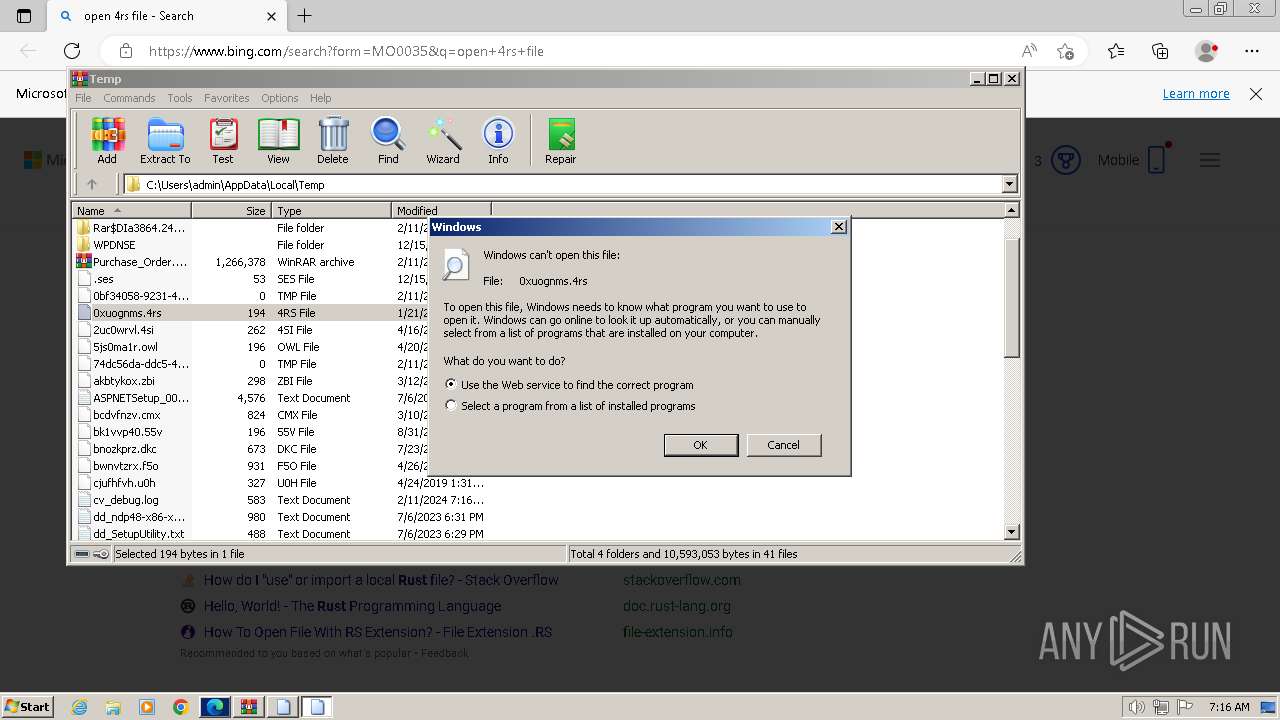
Starts application with an unusual extension
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2832)
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- cmd.exe (PID: 2168)
- cmd.exe (PID: 3560)
- pointer.com (PID: 3724)
- pointer.com (PID: 1376)
Reads the Internet Settings
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- colorcpl.exe (PID: 2592)
- rundll32.exe (PID: 2504)
- pointer.com (PID: 1376)
- pointer.com (PID: 3724)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3864)
- pointer.com (PID: 1040)
Reads settings of System Certificates
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- pointer.com (PID: 1376)
- pointer.com (PID: 3724)
Drops a system driver (possible attempt to evade defenses)
- pointer.com (PID: 1040)
Process drops legitimate windows executable
- xcopy.exe (PID: 848)
- pointer.com (PID: 1040)
Drops a file with a rarely used extension (PIF)
- pointer.com (PID: 1040)
Loads DLL from Mozilla Firefox
- colorcpl.exe (PID: 2592)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3864)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
Drops the executable file immediately after the start
- certutil.exe (PID: 3660)
- xcopy.exe (PID: 848)
- xcopy.exe (PID: 2152)
- certutil.exe (PID: 4000)
Checks supported languages
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- xzdfhdfY.pif (PID: 2488)
- xzdfhdfY.pif (PID: 2972)
- pointer.com (PID: 1376)
- xzdfhdfY.pif (PID: 3448)
- xzdfhdfY.pif (PID: 1644)
- pointer.com (PID: 3724)
Reads the computer name
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- xzdfhdfY.pif (PID: 2488)
- xzdfhdfY.pif (PID: 2972)
- pointer.com (PID: 3724)
- pointer.com (PID: 1376)
- xzdfhdfY.pif (PID: 3448)
- xzdfhdfY.pif (PID: 1644)
Checks proxy server information
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- pointer.com (PID: 3724)
- pointer.com (PID: 1376)
Reads the machine GUID from the registry
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- pointer.com (PID: 3724)
- pointer.com (PID: 1376)
Reads the software policy settings
- pointer.com (PID: 1040)
- pointer.com (PID: 1644)
- pointer.com (PID: 1376)
- pointer.com (PID: 3724)
Manual execution by a user
- colorcpl.exe (PID: 2592)
- raserver.exe (PID: 2560)
Creates files or folders in the user directory
- colorcpl.exe (PID: 2592)
Application launched itself
- msedge.exe (PID: 968)
Reads the Internet Settings
- explorer.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DBatLoader
(PID) Process(1040) pointer.com
C2 (1)https://onedrive.live.com/download?resid=653A5056738F1A02%21143&authkey=!AJ7ivrX4x61Gz-4
(PID) Process(1644) pointer.com
C2 (1)https://onedrive.live.com/download?resid=653A5056738F1A02%21143&authkey=!AJ7ivrX4x61Gz-4
(PID) Process(3724) pointer.com
C2 (1)https://onedrive.live.com/download?resid=653A5056738F1A02%21143&authkey=!AJ7ivrX4x61Gz-4
(PID) Process(1376) pointer.com
C2 (1)https://onedrive.live.com/download?resid=653A5056738F1A02%21143&authkey=!AJ7ivrX4x61Gz-4
Formbook
(PID) Process(2592) colorcpl.exe
C2www.938579.top/fd05/
Strings (79)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)rancangrumah.com
liposuction-54947.bond
9smp.studio
tranquilos.club
slknb9x4.shop
huidvh.xyz
59638.bet
611422.cc
gurdwarakaramsar.com
level42data.com
remedydx.com
aagmal.pro
aicertifiedpro.com
reeoumcuoarriron.shop
syrianphotographers.com
findasideproject.com
frontierconnects.co
cliphothomnay.top
vbywehjri3.top
hydrogenwaterbottles.co
beauty-bloom.online
flowautomations.info
odakegitimaraclari.xyz
wtevans.com
szkrp.com
vellagroup.dev
eyelearnfrommasters.com
weeklythepaper.com
meineinfacheslernbuch.com
6224narlingtonblvd.com
mcchoi.art
dreamcarsgiveaway.com
singlesmatchmaker.com
fi11cc65.com
myvapbnc.top
greattechinc.com
elevatece.co
dkswl.uno
lindellbank.top
grandmarinaluxuryresidences.com
sulekirkguzellik.net
4second-life.info
realestaterunnerwyo.com
veripost.net
krypto.uno
angelhues.store
avagedin.site
vadym-shapran.com
lovesummitreplay.com
lvdco.com
primeroch.com
loadsong.site
wozel.vip
kenielacouture.com
transmigrationholdings.com
thenemolabs.com
personal-loans-11122.bond
selochrono.com
lemonadeux.com
hiv0851.com
paternina100jahre.com
screehab.com
procyoninnovations.cloud
coachmindchange.com
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
131
Monitored processes
83
Malicious processes
16
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3224 --field-trial-handle=1372,i,4353460111254510921,5022922702425074029,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1580 --field-trial-handle=1372,i,4353460111254510921,5022922702425074029,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 748 | xcopy "KDECO.bat" "C:\Windows \System32\" /K /D /H /Y | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1308 --field-trial-handle=1372,i,4353460111254510921,5022922702425074029,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | xcopy "easinvoker.exe" "C:\Windows \System32\" /K /D /H /Y | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 968 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://go.microsoft.com/fwlink/?LinkId=57426&Ext=4rs | C:\Program Files\Microsoft\Edge\Application\msedge.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2236 --field-trial-handle=1372,i,4353460111254510921,5022922702425074029,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2180 --field-trial-handle=1372,i,4353460111254510921,5022922702425074029,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1040 | C:\Users\Public\pointer.com | C:\Users\Public\pointer.com | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
DBatLoader(PID) Process(1040) pointer.com C2 (1)https://onedrive.live.com/download?resid=653A5056738F1A02%21143&authkey=!AJ7ivrX4x61Gz-4 | |||||||||||||||
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
28 120
Read events
27 871
Write events
195
Delete events
54
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C47000000000200000000001066000000010000200000001F7D8CA698F3B06D0A85CF38F29EA8465212AA378E7F8159F76C252A21C9AD83000000000E8000000002000020000000C6B4D2BB76EED05EAEC250917E678BA17DE0642C50E4F24154637076875678CF300000005B5D5386C9A14ACD5E1BA30E63213DDC9618EE76E72A3EA5E0712F6ECB3863B420918DCFD78D968DD32E52AE426EC6FD400000008A5C9405DC3A392CF00F7785B06747DA39F7E5169EB44438A65E902891F4151688EB69449DAD28E1DD3654C163657923B9BEC6B61BC632AFF829F6DD21C9AB17 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Purchase_Order.Tar.rar | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
11
Suspicious files
38
Text files
41
Unknown types
67
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3864.23472\Purchase_Order.bat | text | |
MD5:80041429B667D63A95A6DAEA0811C709 | SHA256:63BC1A678B12904E176BD25551238D0E2FE91CCADBBAFF7B77577C995A85C88E | |||
| 1040 | pointer.com | C:\Users\Public\Libraries\Null | text | |
MD5:778300BD8587672716B777C1C3F07C14 | SHA256:CC40D093B4B0AA5F9CE40061B3489183AAB268DA0BE0400DEE53E5A6480D9346 | |||
| 1040 | pointer.com | C:\Users\Public\Libraries\netutils.dll | executable | |
MD5:EF43F3E84500F2528FF56B144C07C8A2 | SHA256:— | |||
| 848 | xcopy.exe | C:\Windows \System32\easinvoker.exe | executable | |
MD5:231CE1E1D7D98B44371FFFF407D68B59 | SHA256:30951DB8BFC21640645AA9144CFEAA294BB7C6980EF236D28552B6F4F3F92A96 | |||
| 3660 | certutil.exe | C:\Users\Public\pointer.com | executable | |
MD5:6CB3D9A12002C27E8DF8EC3316DDA075 | SHA256:1BFB2A750022169E269B020C3C3ED7994644AC8257039EBDC8DF0271D861FBFF | |||
| 1040 | pointer.com | C:\Users\Public\Libraries\truesight.sys | executable | |
MD5:F53FA44C7B591A2BE105344790543369 | SHA256:BFC2EF3B404294FE2FA05A8B71C7F786B58519175B7202A69FE30F45E607FF1C | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3864.24777\Purchase_Order.bat | text | |
MD5:80041429B667D63A95A6DAEA0811C709 | SHA256:63BC1A678B12904E176BD25551238D0E2FE91CCADBBAFF7B77577C995A85C88E | |||
| 968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18ea6b.TMP | — | |
MD5:— | SHA256:— | |||
| 968 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1040 | pointer.com | C:\Users\Public\Libraries\easinvoker.exe | executable | |
MD5:231CE1E1D7D98B44371FFFF407D68B59 | SHA256:30951DB8BFC21640645AA9144CFEAA294BB7C6980EF236D28552B6F4F3F92A96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
41
DNS requests
38
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2588 | msedge.exe | GET | 302 | 69.192.162.125:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=4rs | unknown | — | — | unknown |
2588 | msedge.exe | GET | 301 | 2.21.20.150:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=4rs | unknown | — | — | unknown |
1164 | explorer.exe | POST | 404 | 203.161.46.83:80 | http://www.huidvh.xyz/fd05/ | unknown | html | 276 b | unknown |
1164 | explorer.exe | POST | 404 | 203.161.46.83:80 | http://www.huidvh.xyz/fd05/ | unknown | html | 276 b | unknown |
1164 | explorer.exe | POST | 404 | 203.161.46.83:80 | http://www.huidvh.xyz/fd05/ | unknown | html | 276 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1040 | pointer.com | 13.107.139.11:443 | onedrive.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1040 | pointer.com | 13.107.42.12:443 | yjdbuq.sn.files.1drv.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1644 | pointer.com | 13.107.139.11:443 | onedrive.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1644 | pointer.com | 13.107.42.12:443 | yjdbuq.sn.files.1drv.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
968 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
2588 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2588 | msedge.exe | 69.192.162.125:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onedrive.live.com |
| shared |
yjdbuq.sn.files.1drv.com |
| unknown |
config.edge.skype.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.microsoftonline.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1164 | explorer.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1164 | explorer.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1164 | explorer.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2 ETPRO signatures available at the full report