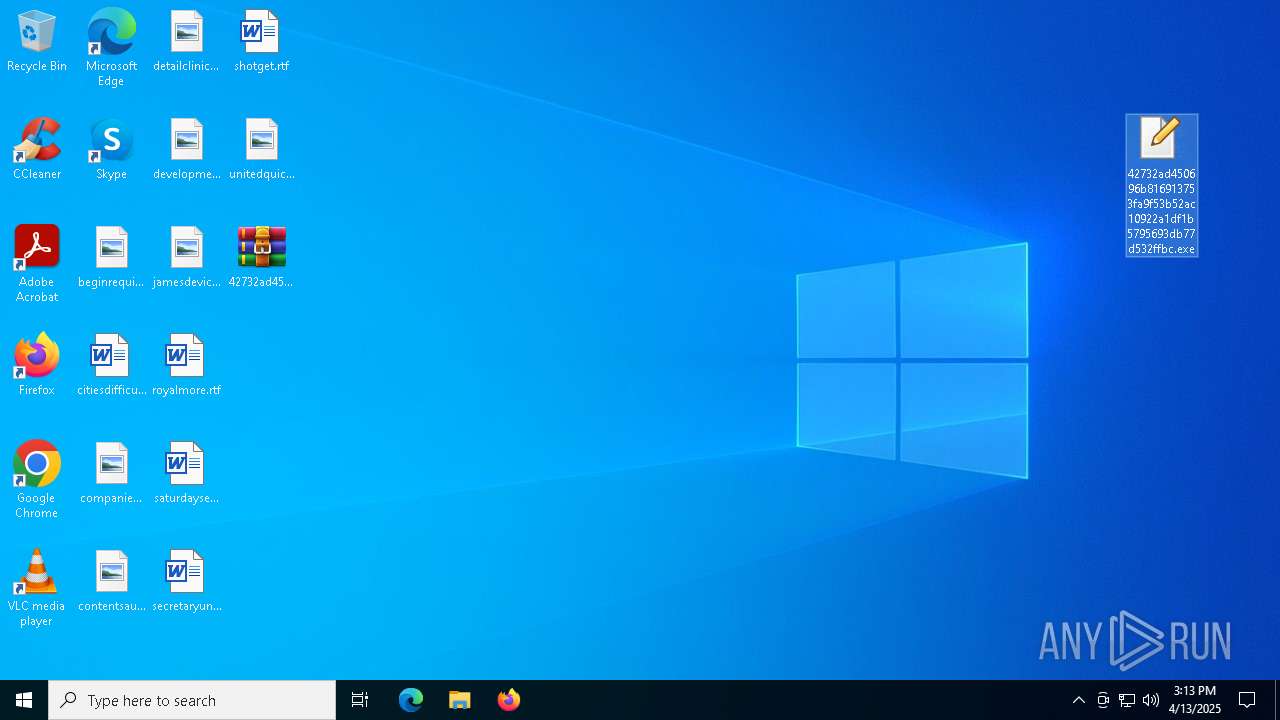
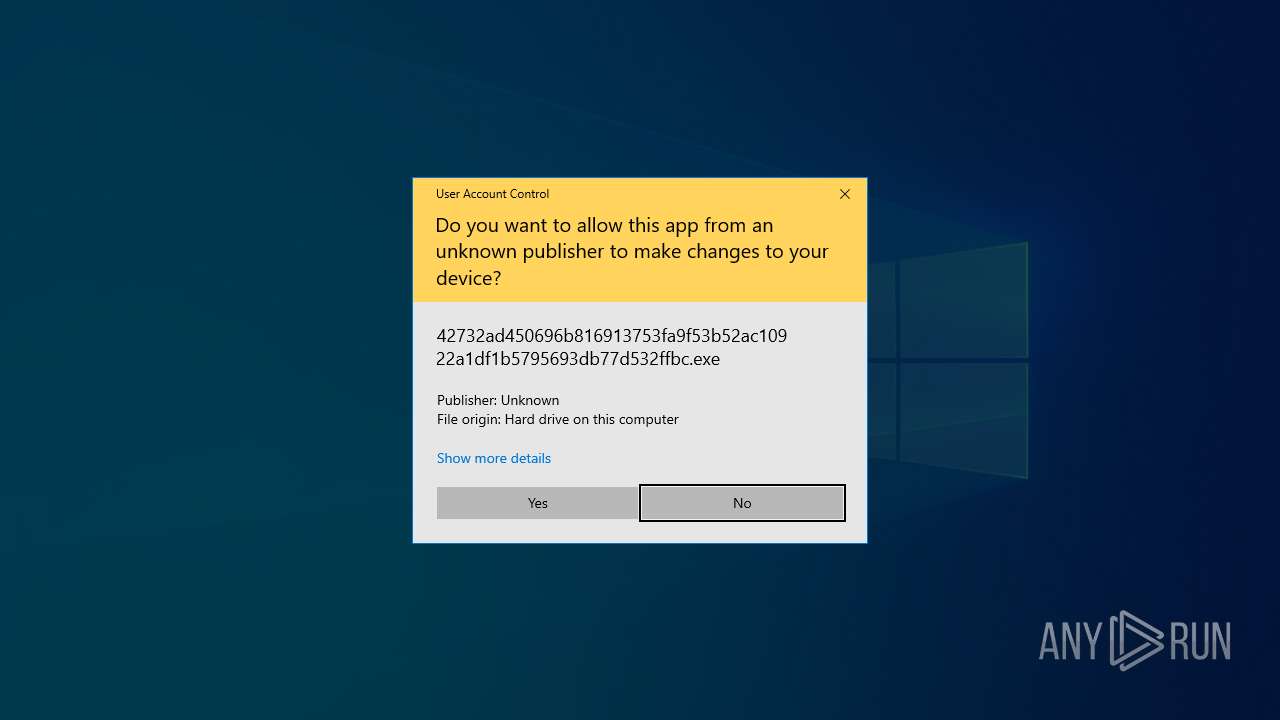
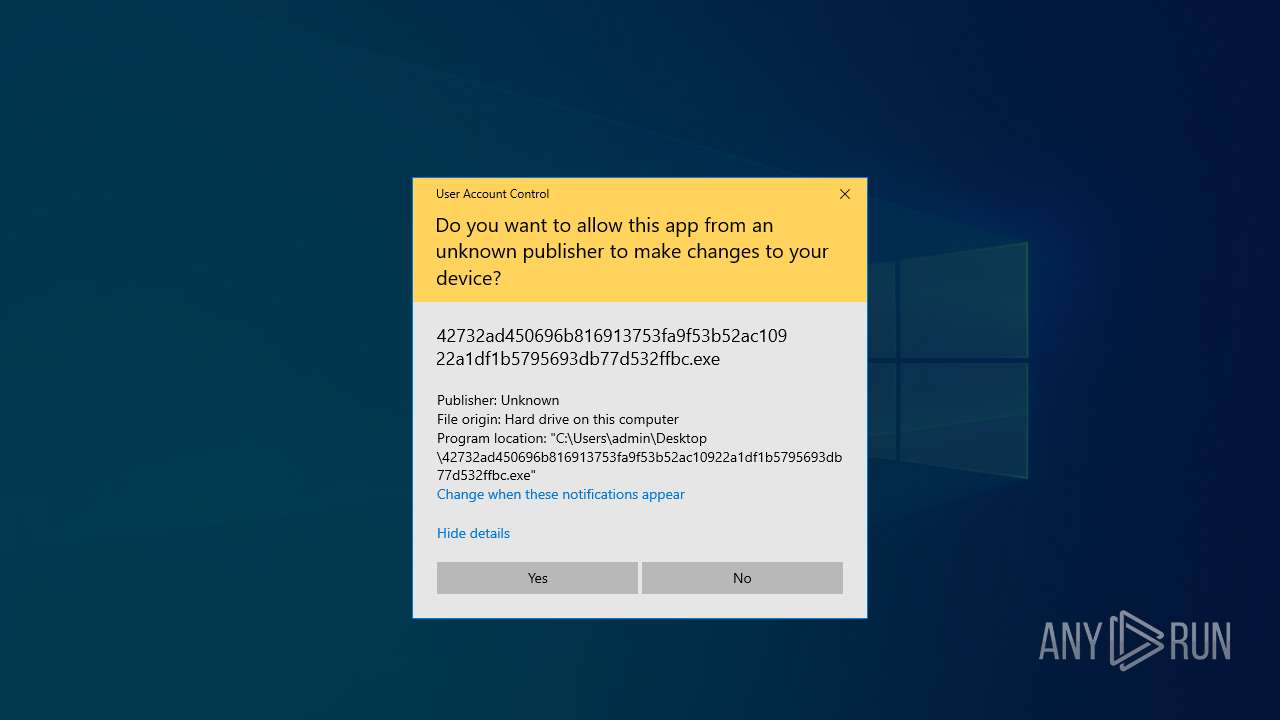
| File name: | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.7z |
| Full analysis: | https://app.any.run/tasks/8c43b3eb-7d52-4ecd-879f-db554116ea28 |
| Verdict: | Malicious activity |
| Threats: | Dharma is advanced ransomware that has been observed in the wild since 2016. It is considered to be the second most profitable RaaS operation by the FBI. The malware targets hospitals and state organizations, encrypts files, and demands a payment to restore access to lost information. |
| Analysis date: | April 13, 2025, 15:12:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 650E399931AAACEE60E732788382462A |
| SHA1: | 7CB815D02E0E371BDA6BBCE7DEB64E3F03EEAC30 |
| SHA256: | 5ED024649EF427F552C9F8774A210C02D0831BE7B4121DF99D8344F8537C59B9 |
| SSDEEP: | 6144:w/rzh6hSPH/x6hffEtJsMZvYw//fZV2FGM:LSPfAffE4svYw//uGM |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5364)
Changes the autorun value in the registry
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
DHARMA mutex has been found
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Create files in the Startup directory
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Deletes shadow copies
- cmd.exe (PID: 6724)
RANSOMWARE has been detected
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Renames files like ransomware
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
SUSPICIOUS
Executable content was dropped or overwritten
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Starts CMD.EXE for commands execution
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Creates file in the systems drive root
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Executes as Windows Service
- VSSVC.exe (PID: 1532)
The process creates files with name similar to system file names
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Process drops legitimate windows executable
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
INFO
The sample compiled with russian language support
- WinRAR.exe (PID: 5364)
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5364)
Checks supported languages
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
- mode.com (PID: 1240)
Reads the computer name
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Manual execution by a user
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Creates files or folders in the user directory
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Starts MODE.COM to configure console settings
- mode.com (PID: 1240)
Creates files in the program directory
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
The sample compiled with english language support
- 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe (PID: 4068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2020:12:04 08:06:46+00:00 |
| ArchivedFileName: | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe |
Total processes
138
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | mode con cp select=1251 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | "C:\Users\admin\Desktop\42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe" | C:\Users\admin\Desktop\42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 5364 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5544 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6724 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6800 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 820
Read events
1 800
Write events
20
Delete events
0
Modification events
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.7z | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
37
Suspicious files
586
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-500\desktop.ini | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1000\desktop.ini | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$Recycle.Bin\S-1-5-21-1693682860-607145093-2874071422-1001\desktop.ini | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$WinREAgent\Backup\location.txt | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$WinREAgent\Backup\Winre.wim.id-26B799FA.[pexdatax@gmail.com].ROGER | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$Recycle.Bin\S-1-5-18\desktop.ini | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$WinREAgent\Rollback.xml | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$WinREAgent\Scratch\update.wim.id-26B799FA.[pexdatax@gmail.com].ROGER | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\$WinREAgent\RollbackInfo.ini | — | |
MD5:— | SHA256:— | |||
| 4068 | 42732ad450696b816913753fa9f53b52ac10922a1df1b5795693db77d532ffbc.exe | C:\BOOTNXT | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1184 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1184 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |