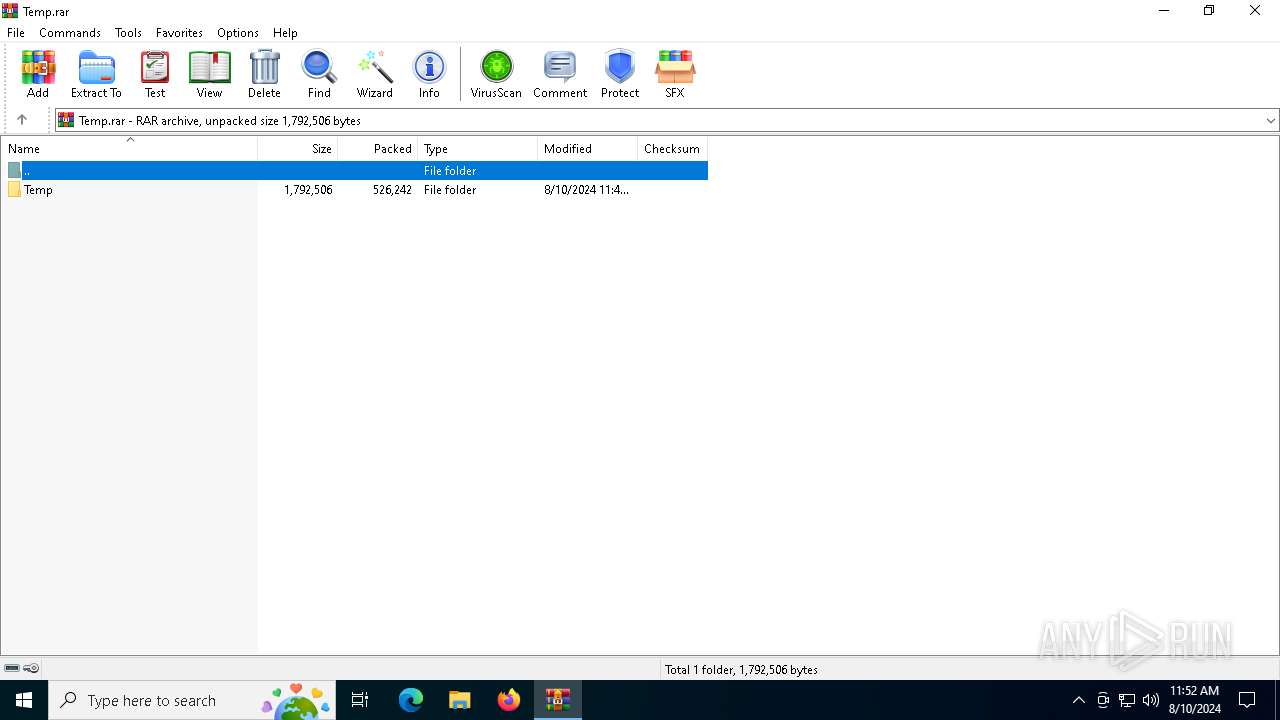
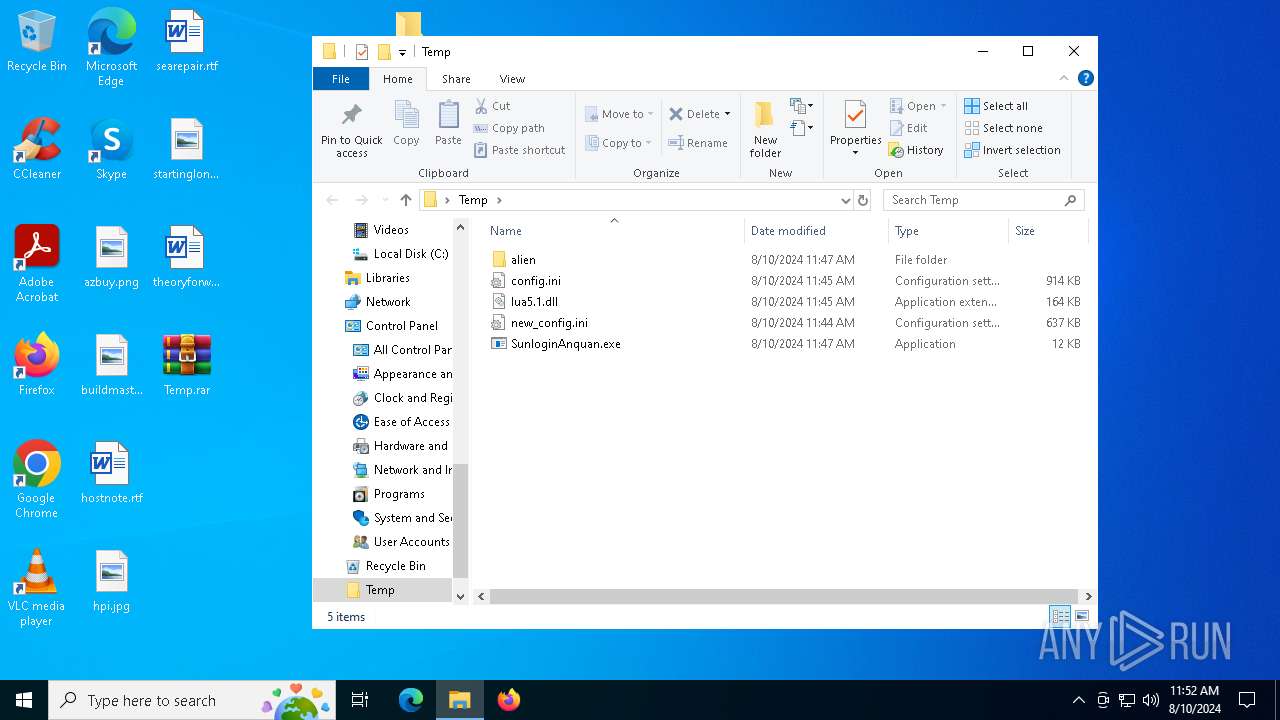
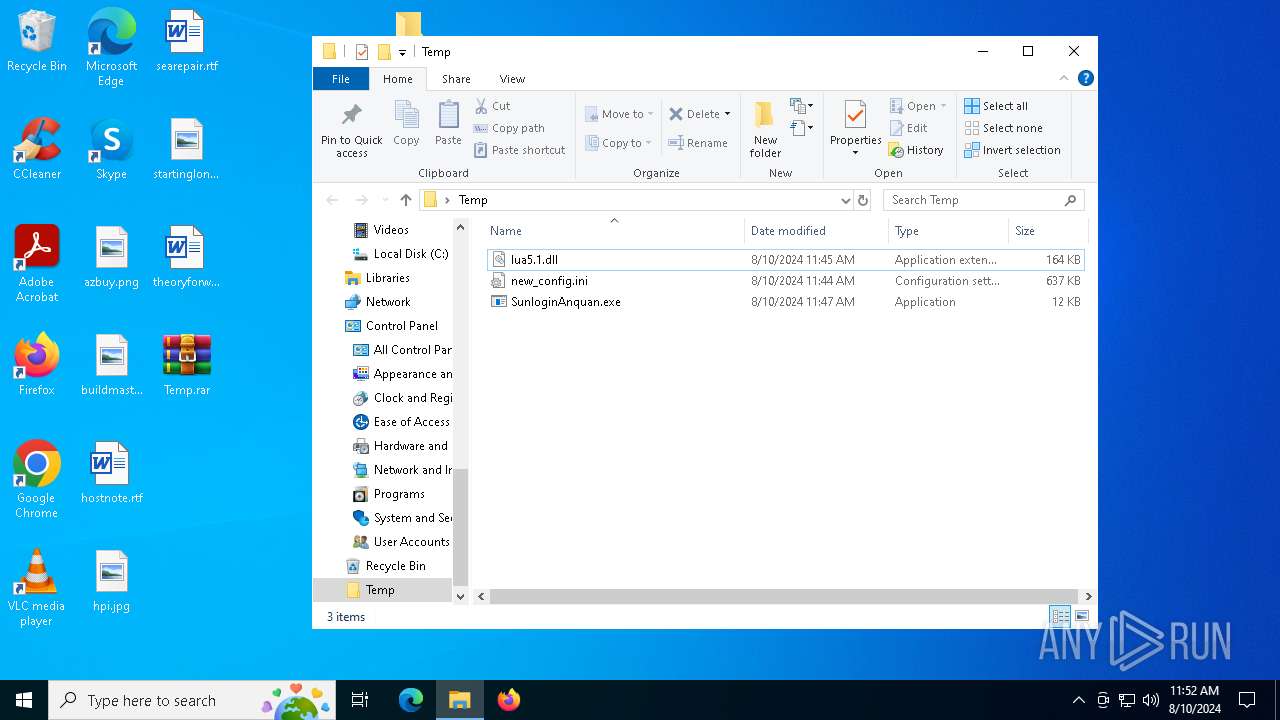
| File name: | Temp.rar |
| Full analysis: | https://app.any.run/tasks/23768a0c-39c0-4432-a744-7d19a6d8ff8a |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | August 10, 2024, 11:52:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 32B30B654AF8B44F0A56F3DCAC46A301 |
| SHA1: | E3821C7890B886E9E4E1A87D75BD474F2BC73568 |
| SHA256: | 5EC1A1D2E63D33F61E8345A6CF421A72C76A2D707E98C6C3915AE93846B26222 |
| SSDEEP: | 24576:bNHDxH0jiNqlmXIGRyxPmjFVdIuppOOR7lzy5M/cjVOu:bNHDxH0jiNqlmXIGRyxPmjFVdIuppOOE |
MALICIOUS
RHADAMANTHYS has been detected (SURICATA)
- OpenWith.exe (PID: 6200)
- OOBE-Maintenance.exe (PID: 532)
Actions looks like stealing of personal data
- OOBE-Maintenance.exe (PID: 532)
RHADAMANTHYS has been detected (YARA)
- OOBE-Maintenance.exe (PID: 532)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6356)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 6200)
Connects to unusual port
- OpenWith.exe (PID: 6200)
- OOBE-Maintenance.exe (PID: 532)
Contacting a server suspected of hosting an CnC
- OpenWith.exe (PID: 6200)
- OOBE-Maintenance.exe (PID: 532)
Loads DLL from Mozilla Firefox
- OOBE-Maintenance.exe (PID: 532)
Searches for installed software
- OOBE-Maintenance.exe (PID: 532)
INFO
Checks supported languages
- SunloginAnquan.exe (PID: 7048)
- SunloginAnquan.exe (PID: 2132)
- SunloginAnquan.exe (PID: 2700)
- SunloginAnquan.exe (PID: 3176)
- setup_wm.exe (PID: 6012)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6356)
Manual execution by a user
- OpenWith.exe (PID: 5244)
- cmd.exe (PID: 6196)
- OpenWith.exe (PID: 6200)
- OOBE-Maintenance.exe (PID: 532)
Reads the computer name
- setup_wm.exe (PID: 6012)
Reads the machine GUID from the registry
- setup_wm.exe (PID: 6012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
143
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 532 | "C:\WINDOWS\system32\OOBE-Maintenance.exe" | C:\Windows\System32\OOBE-Maintenance.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: OOBE-Maintenance Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
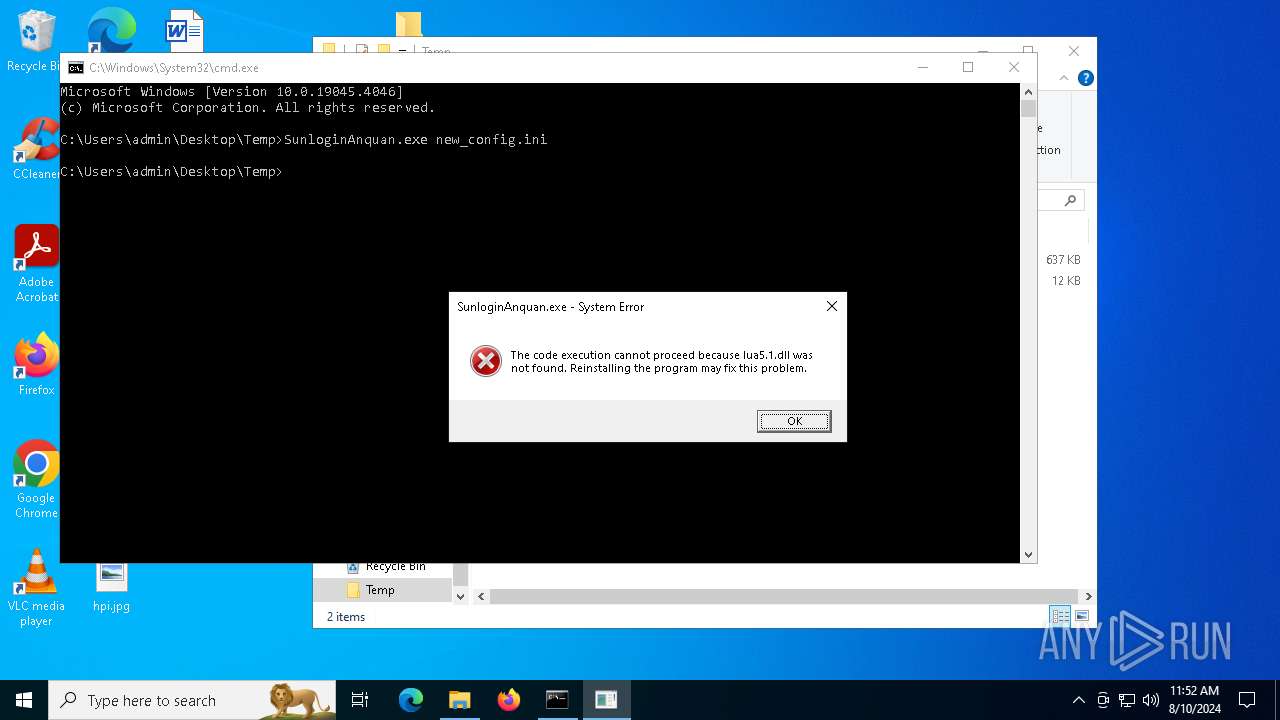
| 2132 | SunloginAnquan.exe new_config.ini | C:\Users\admin\Desktop\Temp\SunloginAnquan.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 2700 | SunloginAnquan.exe new_config.ini | C:\Users\admin\Desktop\Temp\SunloginAnquan.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 3176 | SunloginAnquan.exe new_config.ini | C:\Users\admin\Desktop\Temp\SunloginAnquan.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 5244 | "C:\WINDOWS\system32\openwith.exe" | C:\Windows\SysWOW64\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | OOBE-Maintenance.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6012 | "C:\Program Files\Windows Media Player\setup_wm.exe" | C:\Program Files\Windows Media Player\setup_wm.exe | — | OOBE-Maintenance.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Configuration Utility Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6196 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6200 | "C:\WINDOWS\system32\openwith.exe" | C:\Windows\SysWOW64\OpenWith.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 042
Read events
5 019
Write events
23
Delete events
0
Modification events
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Temp.rar | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
3
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
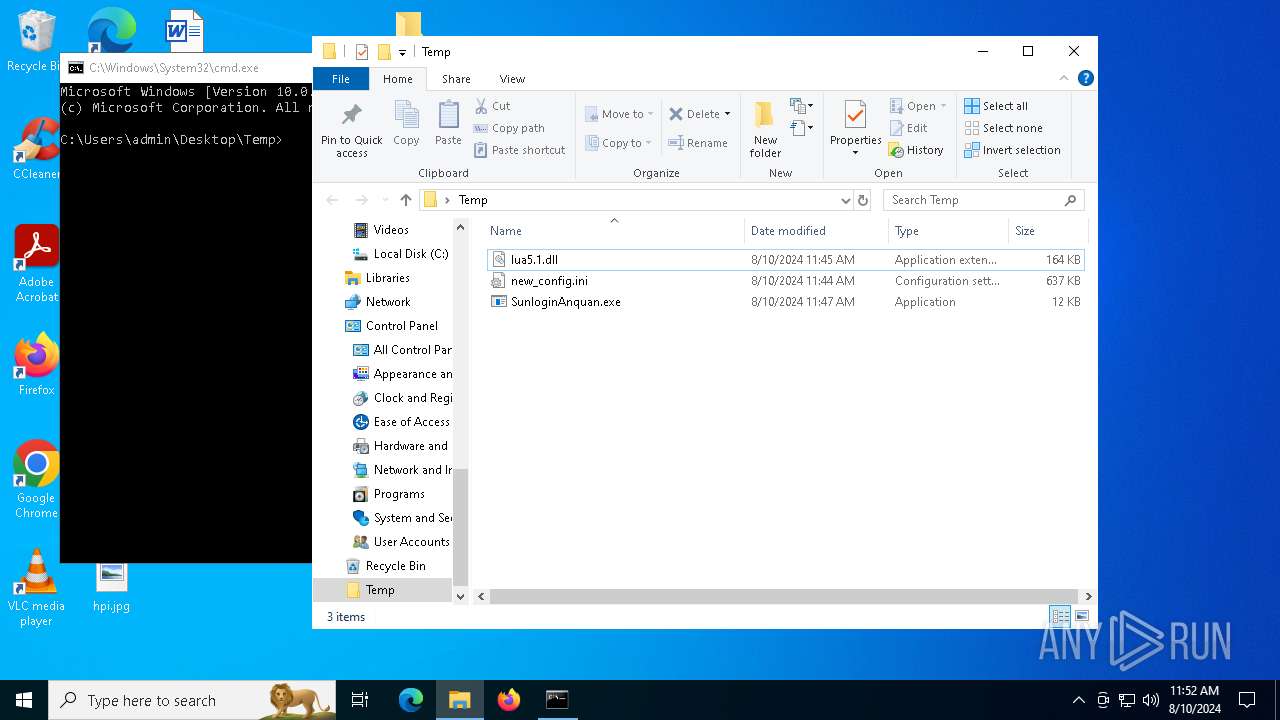
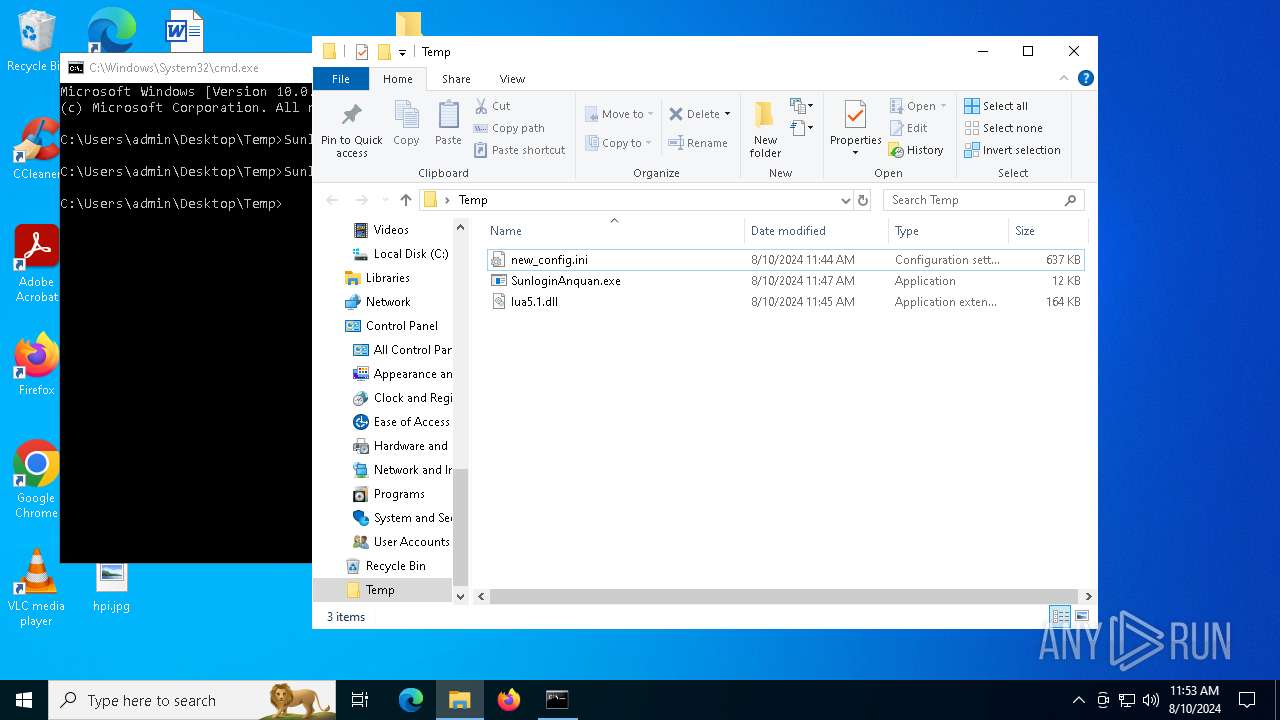
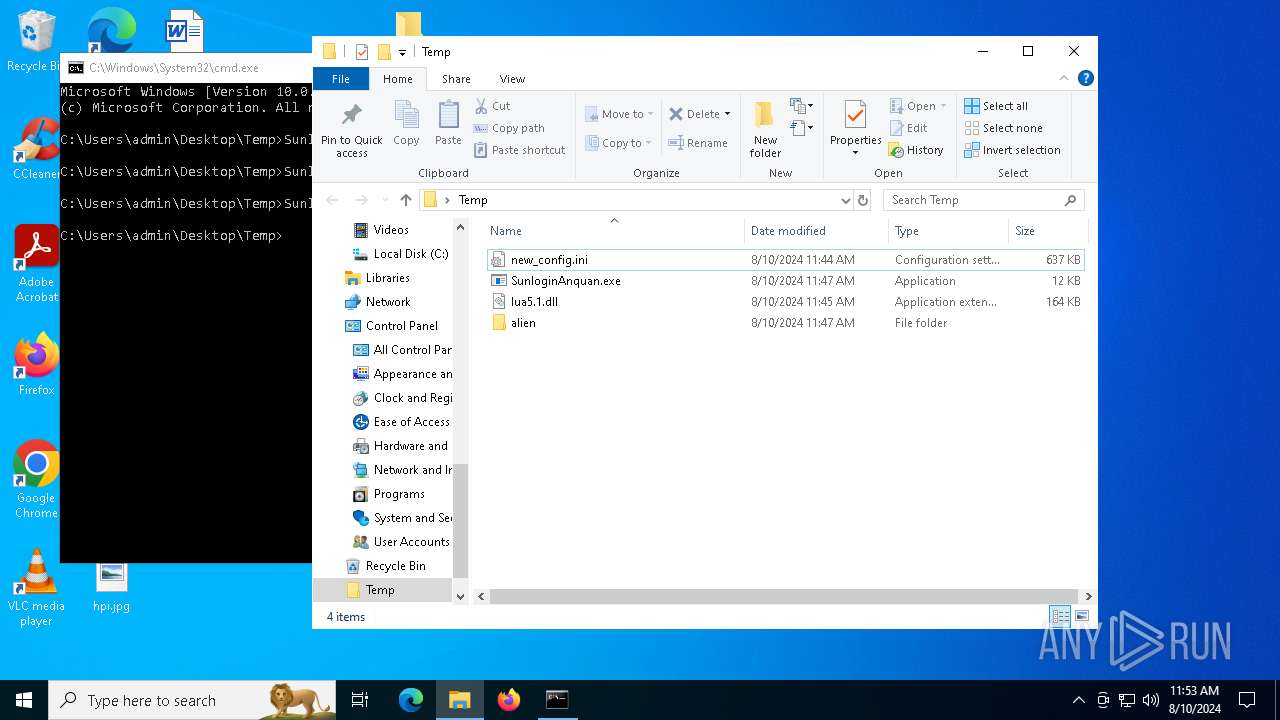
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.5321\Temp\SunloginAnquan.exe | executable | |
MD5:DE13809CD8D5D677EF620128250BFA35 | SHA256:464B033D3E0BCE708CB6AB1A082BF26EED7CF9EA39755701BD4FD501159351C0 | |||
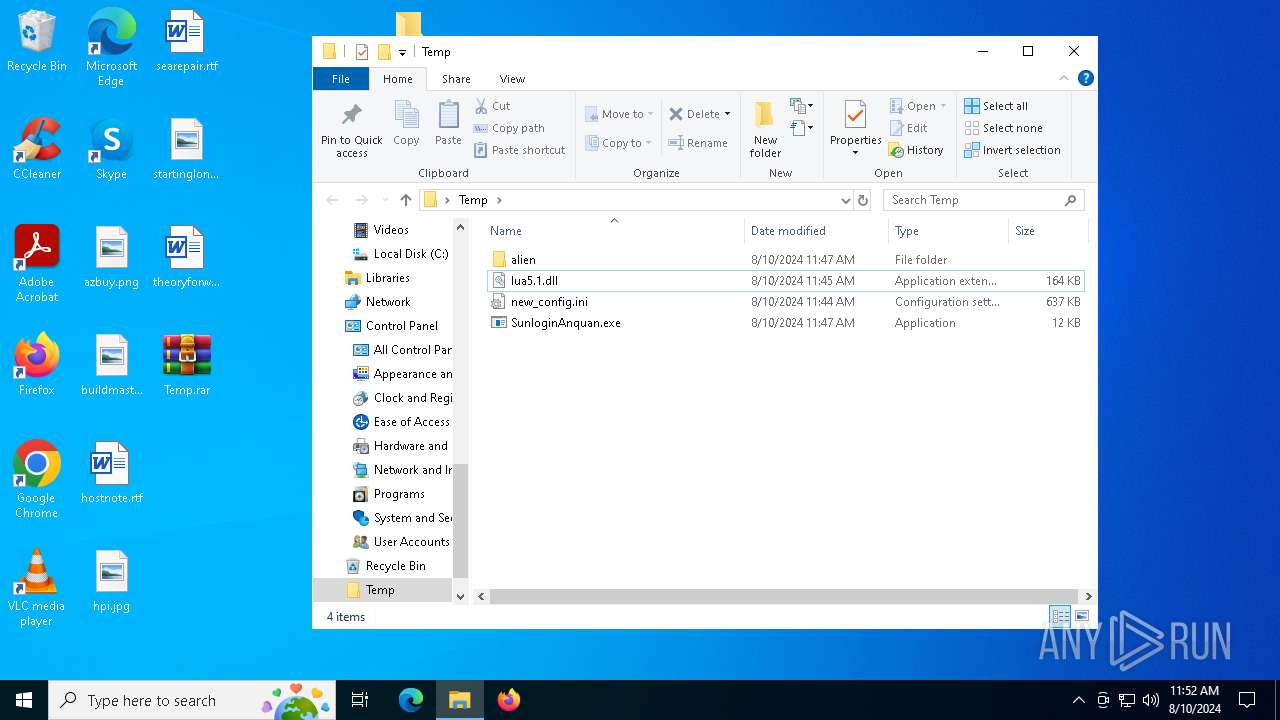
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.5321\Temp\lua5.1.dll | executable | |
MD5:24A0D2EF5B931A2A13341A2503B1DE80 | SHA256:FBBE7EE073D0290AC13C98B92A8405EA04DCC6837B4144889885DD70679E933F | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.5321\Temp\alien\core.dll | executable | |
MD5:24B6950AFD8663A46246044E6B09ADD8 | SHA256:9AA3CA96A84EB5606694ADB58776C9E926020EF184828B6F7E6F9B50498F7071 | |||
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.5321\Temp\new_config.ini | text | |
MD5:95439C50325A6CBAE6CF7F21A36C5EEA | SHA256:8DEE6D514D1F479DD156C31100910E22B6CD7359527F777DBC3986B6218FB90A | |||
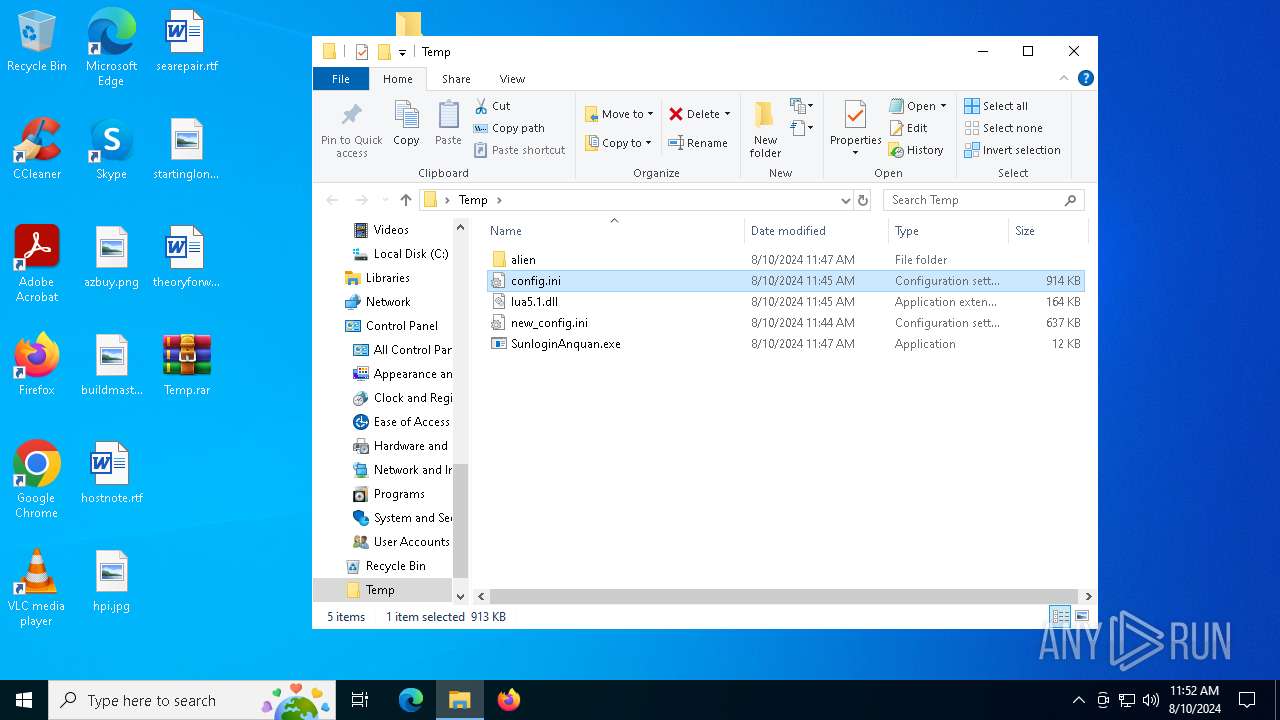
| 6356 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6356.5321\Temp\config.ini | text | |
MD5:9D0E15B1ECDFDA3D913D0FBA79DC06EF | SHA256:C9737420B3C26B226FF042672807F536C335A7BA2E25BEF41DC51542E83FE9E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
44
DNS requests
20
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2204 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6732 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2204 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6784 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5044 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4016 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5044 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2204 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
5 ETPRO signatures available at the full report