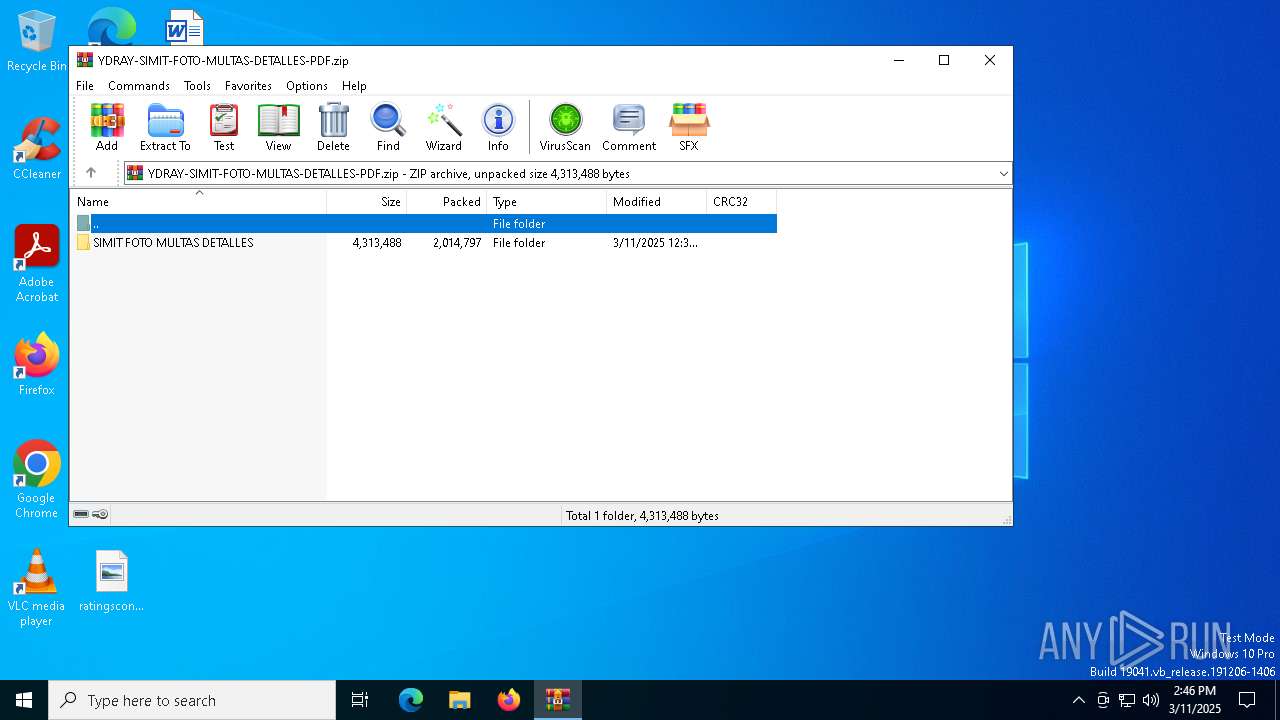
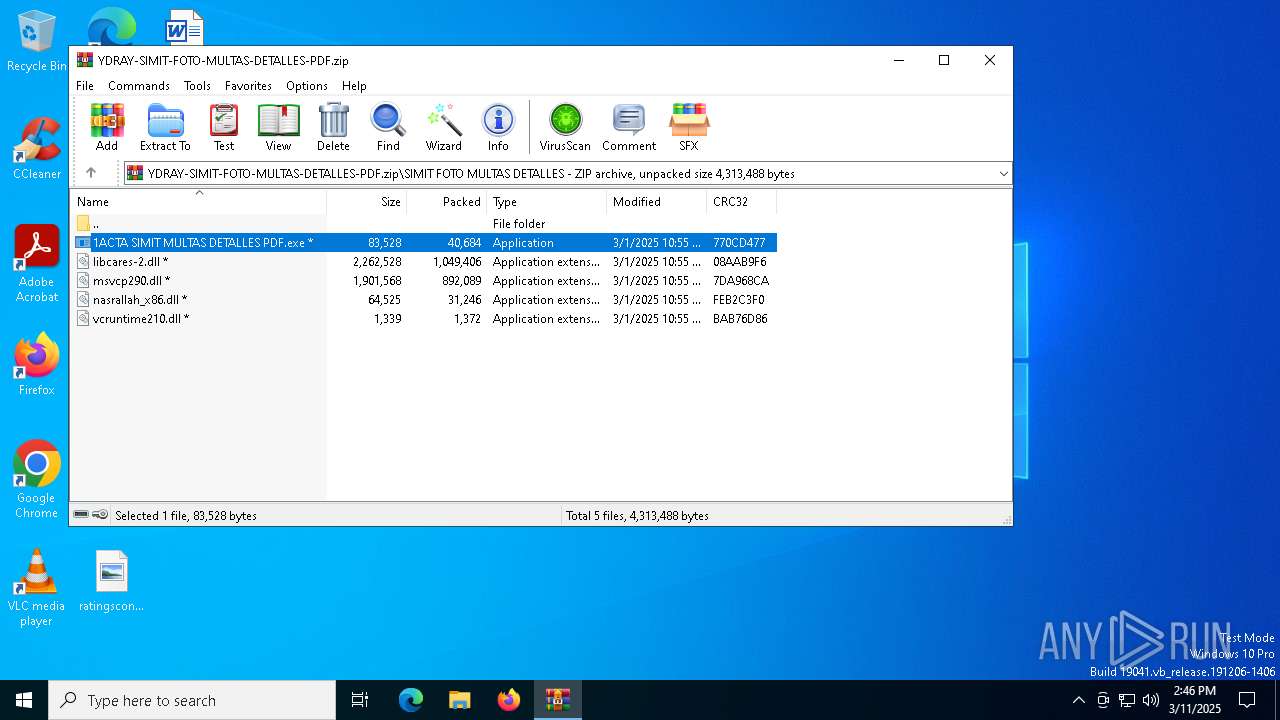
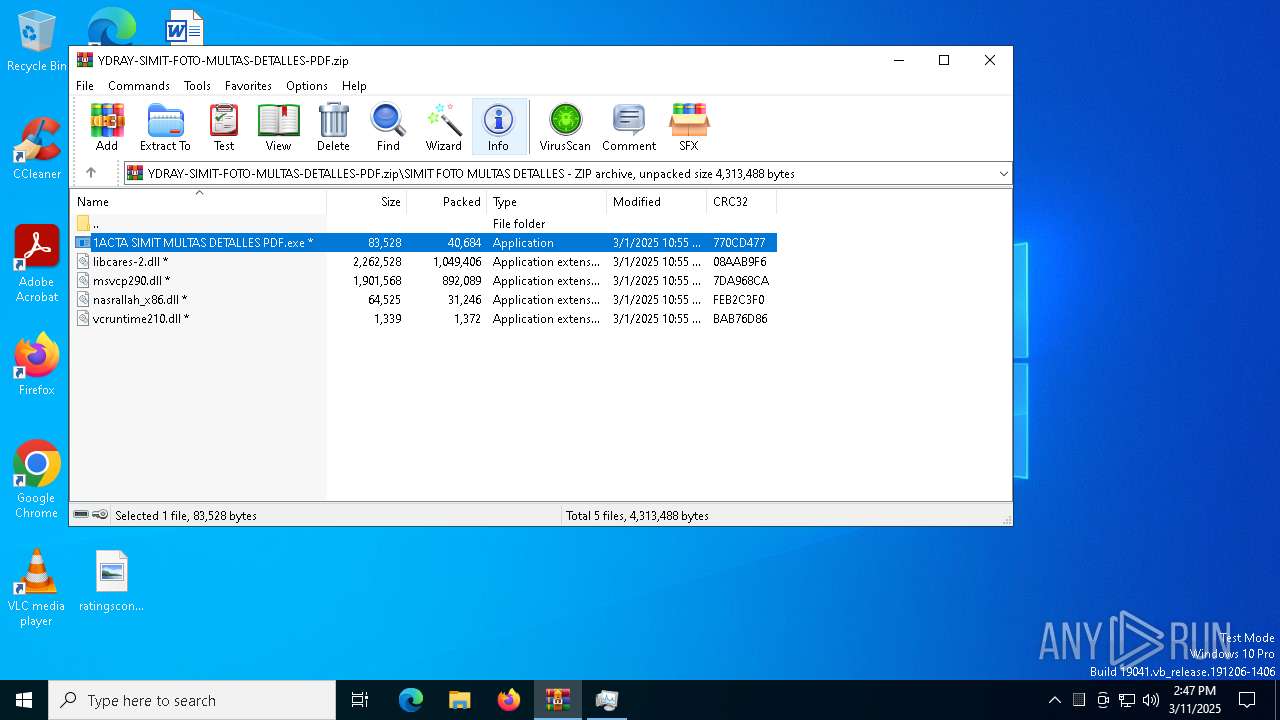
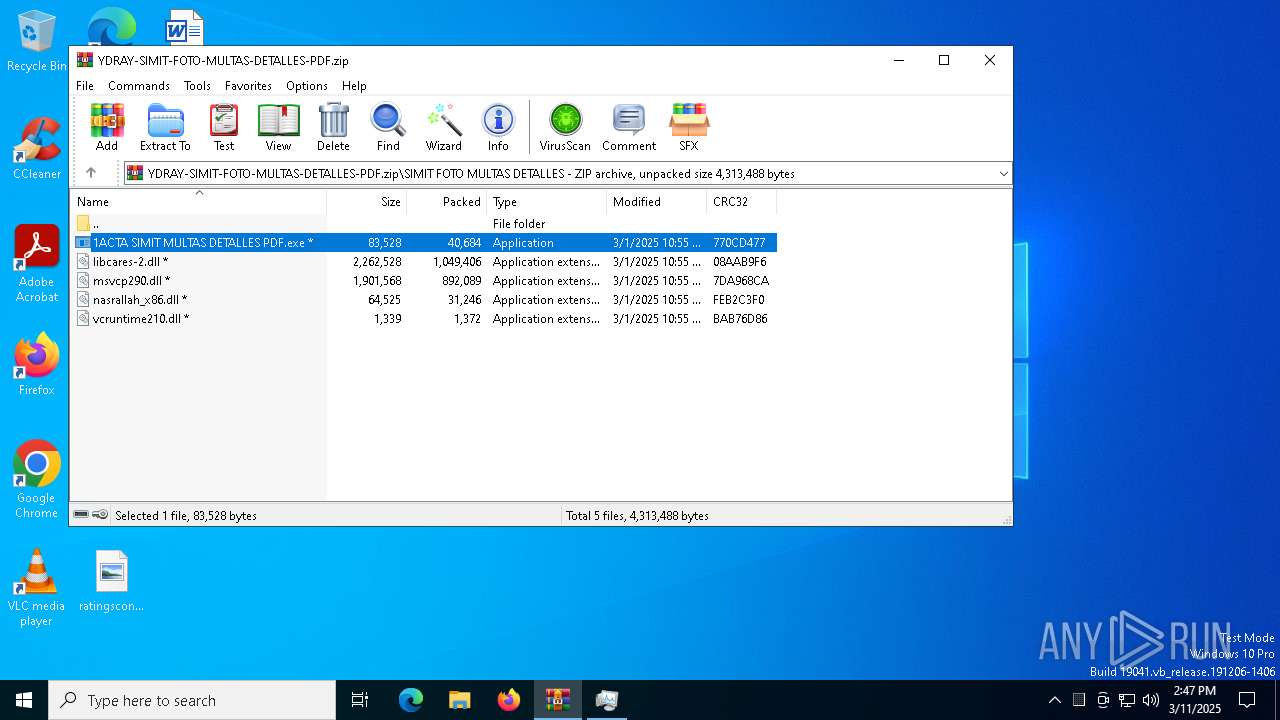
| File name: | YDRAY-SIMIT-FOTO-MULTAS-DETALLES-PDF.zip |
| Full analysis: | https://app.any.run/tasks/4b814335-4e06-432c-bd1a-00b153495a07 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 11, 2025, 14:46:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | B51F1F30A30C671569BC43B7BE9E264B |
| SHA1: | C9D0E80F1440D5DDDC3DD396E9CE8BD3B50D8875 |
| SHA256: | 5DDF049E32EC35806847699634E583CC51E57FF525611DC3AF88206A62B16E7C |
| SSDEEP: | 98304:776EK1Cn299HrmKKuuBQTzEX8mK1WyhWF3ilLW7J3ZEOjuDGtsVuO26mChuKSwxZ:GRf |
MALICIOUS
DCRAT mutex has been found
- AddInProcess32.exe (PID: 8052)
Adds path to the Windows Defender exclusion list
- 1ACTA SIMIT MULTAS DETALLES PDF.exe (PID: 7912)
ASYNCRAT has been detected (SURICATA)
- AddInProcess32.exe (PID: 8052)
SUSPICIOUS
Script adds exclusion path to Windows Defender
- 1ACTA SIMIT MULTAS DETALLES PDF.exe (PID: 7912)
Starts POWERSHELL.EXE for commands execution
- 1ACTA SIMIT MULTAS DETALLES PDF.exe (PID: 7912)
Executable content was dropped or overwritten
- 1ACTA SIMIT MULTAS DETALLES PDF.exe (PID: 7912)
Contacting a server suspected of hosting an CnC
- AddInProcess32.exe (PID: 8052)
Connects to unusual port
- AddInProcess32.exe (PID: 8052)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2140)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7988)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7988)
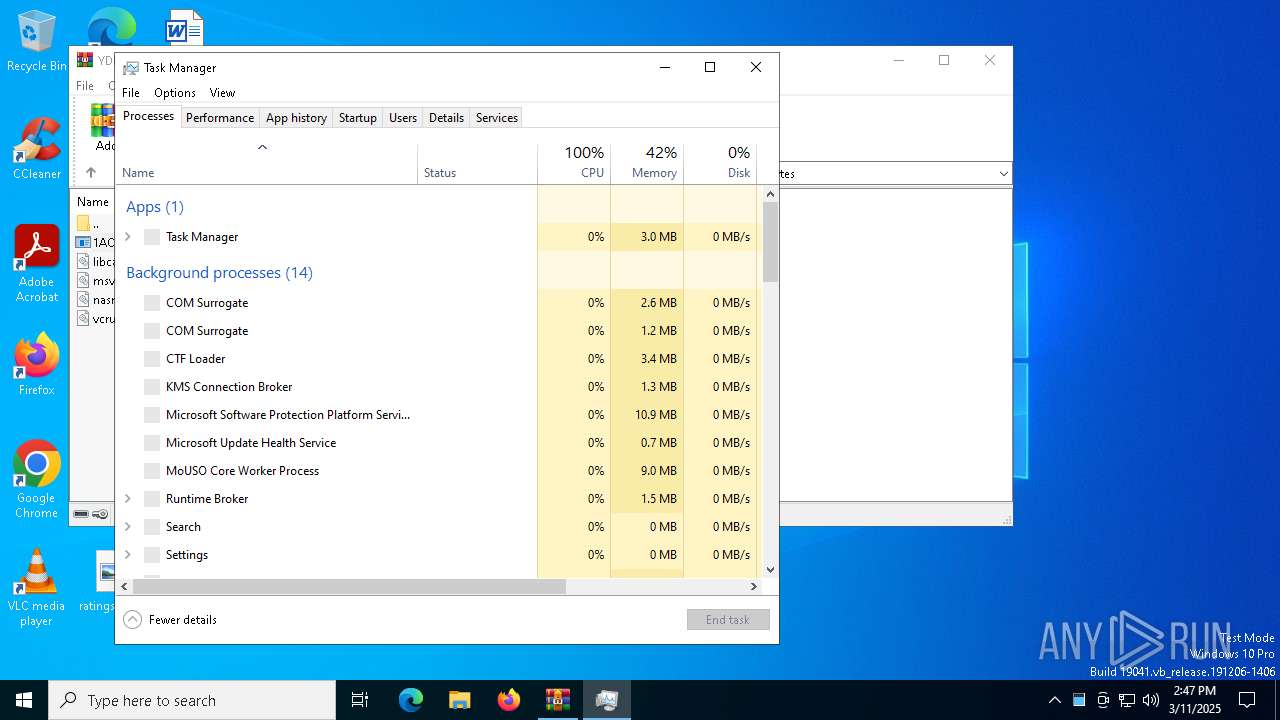
Manual execution by a user
- Taskmgr.exe (PID: 456)
- Taskmgr.exe (PID: 7328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:11 07:31:28 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | SIMIT FOTO MULTAS DETALLES/ |
Total processes
144
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\YDRAY-SIMIT-FOTO-MULTAS-DETALLES-PDF.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7252 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7328 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
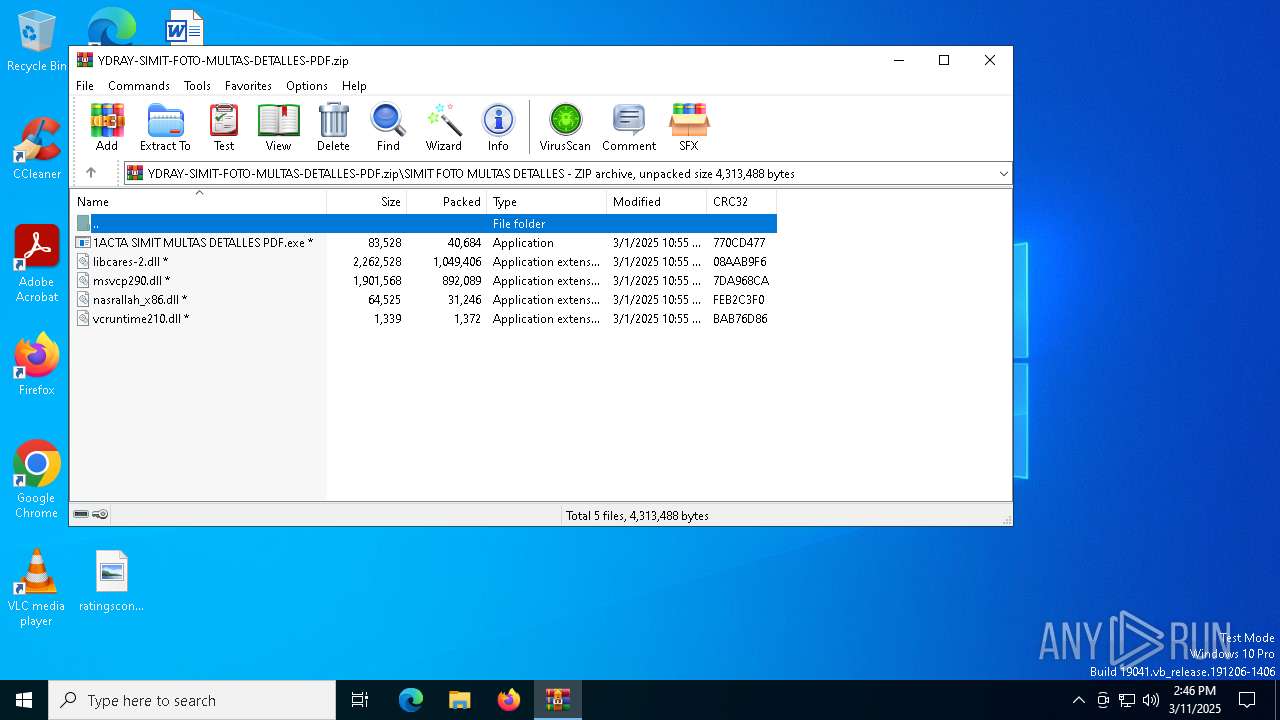
| 7912 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2140.20779\SIMIT FOTO MULTAS DETALLES\1ACTA SIMIT MULTAS DETALLES PDF.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2140.20779\SIMIT FOTO MULTAS DETALLES\1ACTA SIMIT MULTAS DETALLES PDF.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 7920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 1ACTA SIMIT MULTAS DETALLES PDF.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7988 | "powershell.exe" -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\SystemRootDoc' -Force" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 1ACTA SIMIT MULTAS DETALLES PDF.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7996 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 158
Read events
13 146
Write events
11
Delete events
1
Modification events
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\YDRAY-SIMIT-FOTO-MULTAS-DETALLES-PDF.zip | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2140) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (7912) 1ACTA SIMIT MULTAS DETALLES PDF.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 1ACTA SIMIT MULTAS DETALLES PDF |
Value: cmd.exe /C start "" /D "C:\Users\admin\SystemRootDoc" "C:\Users\admin\SystemRootDoc\1ACTA SIMIT MULTAS DETALLES PDF.exe" | |||
Executable files
6
Suspicious files
5
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2140.20779\SIMIT FOTO MULTAS DETALLES\msvcp290.dll | executable | |
MD5:1B365DBF1009F7D73A5A43E1128243B8 | SHA256:E5E073E67EB4B2E3427B10966FCDB6EEA362B80D113BC9FD5C24FB5F05C14FBB | |||
| 7328 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 2140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2140.20779\SIMIT FOTO MULTAS DETALLES\vcruntime210.dll | binary | |
MD5:008BBC53FB74D99B5B5EDE5DA74F05E2 | SHA256:B9929B65FC48BAF5E9CE7AD43AA82E52ED361597B4F190A3BEDBFD5E675B0D70 | |||
| 2140 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2140.20779\SIMIT FOTO MULTAS DETALLES\libcares-2.dll | executable | |
MD5:70C01E4E3C1CD9B3BF911214317BE70B | SHA256:EE372E36155E4AEB49BA9C3544FD77ECDE8E16206342F2A2E69CDF073055F918 | |||
| 7912 | 1ACTA SIMIT MULTAS DETALLES PDF.exe | C:\Users\admin\SystemRootDoc\vcruntime210.dll | binary | |
MD5:008BBC53FB74D99B5B5EDE5DA74F05E2 | SHA256:B9929B65FC48BAF5E9CE7AD43AA82E52ED361597B4F190A3BEDBFD5E675B0D70 | |||
| 7912 | 1ACTA SIMIT MULTAS DETALLES PDF.exe | C:\Users\admin\SystemRootDoc\libcares-2.dll | executable | |
MD5:70C01E4E3C1CD9B3BF911214317BE70B | SHA256:EE372E36155E4AEB49BA9C3544FD77ECDE8E16206342F2A2E69CDF073055F918 | |||
| 7912 | 1ACTA SIMIT MULTAS DETALLES PDF.exe | C:\Users\admin\SystemRootDoc\1ACTA SIMIT MULTAS DETALLES PDF.exe | executable | |
MD5:41C2401A4ECF9C80796E534D388E56CD | SHA256:936B1CB91D8A1CCA1F846A5433D9A0BCF91EBC9E9BAFD31C6C080E26EAB60657 | |||
| 7912 | 1ACTA SIMIT MULTAS DETALLES PDF.exe | C:\Users\admin\SystemRootDoc\nasrallah_x86.dll | binary | |
MD5:210D2C00CFB77D51B77E7EAB759F60D0 | SHA256:DC7C7821194B70296734D754BBA552A8756BDDE0448B0583D12657FB6BC85139 | |||
| 7988 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1ygtijat.b4g.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7912 | 1ACTA SIMIT MULTAS DETALLES PDF.exe | C:\Users\admin\SystemRootDoc\msvcp290.dll | executable | |
MD5:1B365DBF1009F7D73A5A43E1128243B8 | SHA256:E5E073E67EB4B2E3427B10966FCDB6EEA362B80D113BC9FD5C24FB5F05C14FBB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
14
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4976 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4976 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7516 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7516 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7516 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
8052 | AddInProcess32.exe | 46.246.84.4:9999 | australiamd2000.duckdns.org | GleSYS AB | SE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
australiamd2000.duckdns.org |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
8052 | AddInProcess32.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
8052 | AddInProcess32.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |