| File name: | random.exe |
| Full analysis: | https://app.any.run/tasks/fa07294f-f853-44d9-9a92-dd9a30fe61cc |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 23, 2025, 21:55:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 477FD1BEA314518E53027340B109EEB6 |
| SHA1: | 324A6C68224320E8D6642B59B1433F0E53E02532 |
| SHA256: | 5DC148C8CD3FABC1F1D10C56585BF8CB011CC27A14AF1C421A64D7E553DB5610 |
| SSDEEP: | 98304:Cn2qYGTRvGzoW6EguErOsvAdLBJTM5asoDS7t2MBN6fzR6zqLCr9iswT3mfluC2a:Livw |
MALICIOUS
AMADEY mutex has been found
- 1a55b8.exe (PID: 7532)
- namez.exe (PID: 7648)
- namez.exe (PID: 1912)
- namez.exe (PID: 720)
LUMMA has been detected (SURICATA)
- 2t6983.exe (PID: 7660)
- svchost.exe (PID: 2196)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
Connects to the CnC server
- svchost.exe (PID: 2196)
- saved.exe (PID: 6392)
Steals credentials from Web Browsers
- 2t6983.exe (PID: 7660)
- MSBuild.exe (PID: 5588)
- KDUmpUI.exe (PID: 1040)
- 9ad92fb87e.exe (PID: 7768)
- 9ad92fb87e.exe (PID: 3300)
- MSBuild.exe (PID: 1568)
- e134d2cad1.exe (PID: 5260)
- core.exe (PID: 684)
- HVoSsE7NPKxcz.exe (PID: 8792)
- elpyrorrerz.exe (PID: 3100)
- ge0NTgK.exe (PID: 4120)
- Florist.com (PID: 8444)
LUMMA mutex has been found
- 2t6983.exe (PID: 7660)
- KDUmpUI.exe (PID: 1040)
- MSBuild.exe (PID: 5588)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- MSBuild.exe (PID: 1568)
- e134d2cad1.exe (PID: 5260)
- core.exe (PID: 684)
- HVoSsE7NPKxcz.exe (PID: 8792)
- elpyrorrerz.exe (PID: 3100)
- Florist.com (PID: 8444)
Actions looks like stealing of personal data
- 2t6983.exe (PID: 7660)
- ge0NTgK.exe (PID: 4120)
- MSBuild.exe (PID: 5588)
- KDUmpUI.exe (PID: 1040)
- 9ad92fb87e.exe (PID: 7768)
- 9ad92fb87e.exe (PID: 3300)
- MSBuild.exe (PID: 1568)
- e134d2cad1.exe (PID: 5260)
- core.exe (PID: 684)
- HVoSsE7NPKxcz.exe (PID: 8792)
- elpyrorrerz.exe (PID: 3100)
- Florist.com (PID: 8444)
AMADEY has been detected (YARA)
- namez.exe (PID: 7648)
- saved.exe (PID: 6392)
LUMMA has been detected (YARA)
- 2t6983.exe (PID: 7660)
- MSBuild.exe (PID: 5588)
AMADEY has been detected (SURICATA)
- saved.exe (PID: 6392)
- namez.exe (PID: 7648)
GROWTOPIA has been detected (YARA)
- ge0NTgK.exe (PID: 4120)
Changes the autorun value in the registry
- saved.exe (PID: 6392)
- x5l4kAD.exe (PID: 7452)
- cVEHCL4.exe (PID: 8508)
Disables Windows Defender
- 1bab3e99c3.exe (PID: 7760)
Executing a file with an untrusted certificate
- core.exe (PID: 684)
- yuNBaP5SaKB.exe (PID: 8512)
Possible tool for stealing has been detected
- bdfba07db4.exe (PID: 8072)
- firefox.exe (PID: 5380)
- firefox.exe (PID: 7760)
- firefox.exe (PID: 7728)
- bdfba07db4.exe (PID: 8156)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 5260)
- cmd.exe (PID: 5680)
Run PowerShell with an invisible window
- powershell.exe (PID: 7732)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 4424)
- powershell.exe (PID: 8352)
- powershell.exe (PID: 3028)
- powershell.exe (PID: 8760)
- powershell.exe (PID: 9060)
Changes the Windows auto-update feature
- 1bab3e99c3.exe (PID: 7760)
GENERIC has been found (auto)
- 05b95a6d88.exe (PID: 1764)
- svchost015.exe (PID: 856)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 4424)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5576)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 4424)
GCLEANER has been detected (SURICATA)
- svchost015.exe (PID: 856)
Changes Windows Defender settings
- mmc.exe (PID: 3796)
- Mvyo43T.exe (PID: 8948)
- BKbClfr.exe (PID: 8892)
Adds path to the Windows Defender exclusion list
- mmc.exe (PID: 3796)
- Mvyo43T.exe (PID: 8948)
- BKbClfr.exe (PID: 8892)
RHADAMANTHYS mutex has been found
- 41e7a26e74.exe (PID: 5624)
- svchost.exe (PID: 8488)
Changes powershell execution policy (Bypass)
- core.exe (PID: 684)
Bypass execution policy to execute commands
- powershell.exe (PID: 9004)
The DLL Hijacking
- ipconfig.exe (PID: 3992)
XWORM has been detected (SURICATA)
- cVEHCL4.exe (PID: 8508)
SUSPICIOUS
Reads security settings of Internet Explorer
- 1a55b8.exe (PID: 7532)
- namez.exe (PID: 7648)
- MELNE06FNPFT30X3450ZAVO3S6JG2.exe (PID: 8188)
- saved.exe (PID: 6392)
- 3d8369a4e7.tmp (PID: 2340)
- svchost015.exe (PID: 856)
- dupfilesfreecleaner11.exe (PID: 7104)
- yuNBaP5SaKB.exe (PID: 8512)
- Mvyo43T.exe (PID: 8672)
- Mvyo43T.exe (PID: 8948)
- BKbClfr.exe (PID: 7216)
- BKbClfr.exe (PID: 8892)
Starts a Microsoft application from unusual location
- random.exe (PID: 7512)
- WwrZHbF.exe (PID: 7700)
Executable content was dropped or overwritten
- 1a55b8.exe (PID: 7532)
- random.exe (PID: 7512)
- 2t6983.exe (PID: 7660)
- MELNE06FNPFT30X3450ZAVO3S6JG2.exe (PID: 8188)
- saved.exe (PID: 6392)
- ge0NTgK.exe (PID: 4120)
- 3d8369a4e7.exe (PID: 5968)
- 3d8369a4e7.tmp (PID: 2340)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- 05b95a6d88.exe (PID: 1764)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 4424)
- svchost015.exe (PID: 856)
- usn4cb68tur.exe (PID: 540)
- usn4cb68tur.tmp (PID: 8104)
- dupfilesfreecleaner11.exe (PID: 7104)
- mmc.exe (PID: 3796)
- cVEHCL4.exe (PID: 8508)
- HVoSsE7NPKxcz.exe (PID: 8792)
- powershell.exe (PID: 3028)
- ku9ZDO7.exe (PID: 9064)
- ku9ZDO7.exe (PID: 9124)
- SystemZenith.exe (PID: 1600)
- powershell.exe (PID: 9060)
- ge0NTgK.exe (PID: 8640)
Process drops legitimate windows executable
- random.exe (PID: 7512)
- saved.exe (PID: 6392)
- usn4cb68tur.tmp (PID: 8104)
- msiexec.exe (PID: 5860)
- ku9ZDO7.exe (PID: 9064)
- SystemZenith.exe (PID: 1600)
Starts itself from another location
- 1a55b8.exe (PID: 7532)
- MELNE06FNPFT30X3450ZAVO3S6JG2.exe (PID: 8188)
- ku9ZDO7.exe (PID: 9124)
- SystemZenith.exe (PID: 1600)
Reads the BIOS version
- 2t6983.exe (PID: 7660)
- ge0NTgK.exe (PID: 4120)
- 9ad92fb87e.exe (PID: 3300)
- 1bab3e99c3.exe (PID: 7760)
- 9ad92fb87e.exe (PID: 7768)
- 05b95a6d88.exe (PID: 1764)
- e134d2cad1.exe (PID: 5260)
- HVoSsE7NPKxcz.exe (PID: 8792)
- 41e7a26e74.exe (PID: 5624)
- ge0NTgK.exe (PID: 8640)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- 2t6983.exe (PID: 7660)
- namez.exe (PID: 7648)
- saved.exe (PID: 6392)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- cVEHCL4.exe (PID: 8508)
There is functionality for enable RDP (YARA)
- namez.exe (PID: 7648)
- saved.exe (PID: 6392)
There is functionality for taking screenshot (YARA)
- namez.exe (PID: 7648)
- saved.exe (PID: 6392)
- ge0NTgK.exe (PID: 4120)
- MSBuild.exe (PID: 5588)
- KDUmpUI.exe (PID: 1040)
Searches for installed software
- 2t6983.exe (PID: 7660)
- KDUmpUI.exe (PID: 1040)
- MSBuild.exe (PID: 5588)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- MSBuild.exe (PID: 1568)
- core.exe (PID: 684)
- e134d2cad1.exe (PID: 5260)
- HVoSsE7NPKxcz.exe (PID: 8792)
- ge0NTgK.exe (PID: 4120)
- elpyrorrerz.exe (PID: 3100)
- Florist.com (PID: 8444)
Potential Corporate Privacy Violation
- 2t6983.exe (PID: 7660)
- saved.exe (PID: 6392)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 4424)
- powershell.exe (PID: 5576)
- svchost015.exe (PID: 856)
- HVoSsE7NPKxcz.exe (PID: 8792)
Connects to the server without a host name
- namez.exe (PID: 7648)
- 2t6983.exe (PID: 7660)
- saved.exe (PID: 6392)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- powershell.exe (PID: 4424)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 8056)
- svchost015.exe (PID: 856)
- HVoSsE7NPKxcz.exe (PID: 8792)
Process requests binary or script from the Internet
- 2t6983.exe (PID: 7660)
- saved.exe (PID: 6392)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- powershell.exe (PID: 4424)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5576)
- HVoSsE7NPKxcz.exe (PID: 8792)
Connects to unusual port
- ge0NTgK.exe (PID: 4120)
- x5l4kAD.exe (PID: 7452)
- svchost.exe (PID: 8488)
- cVEHCL4.exe (PID: 8508)
- ge0NTgK.exe (PID: 8640)
The process executes via Task Scheduler
- saved.exe (PID: 7288)
- namez.exe (PID: 1912)
- saved.exe (PID: 7704)
- namez.exe (PID: 720)
Multiple wallet extension IDs have been found
- ge0NTgK.exe (PID: 4120)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 5588)
- cVEHCL4.exe (PID: 8508)
- elpyrorrerz.exe (PID: 3100)
- Florist.com (PID: 8444)
- bmoqczjxpzwhz.exe (PID: 8796)
Reads the Windows owner or organization settings
- 3d8369a4e7.tmp (PID: 2340)
- usn4cb68tur.tmp (PID: 8104)
- msiexec.exe (PID: 5860)
Uses TASKKILL.EXE to kill Browsers
- bdfba07db4.exe (PID: 8072)
- bdfba07db4.exe (PID: 8156)
Uses TASKKILL.EXE to kill process
- bdfba07db4.exe (PID: 8072)
- bdfba07db4.exe (PID: 8156)
Starts CMD.EXE for commands execution
- fb82e63a4c.exe (PID: 4208)
- fb82e63a4c.exe (PID: 6824)
- yuNBaP5SaKB.exe (PID: 8512)
- cmd.exe (PID: 8596)
- Mvyo43T.exe (PID: 8948)
- ge0NTgK.exe (PID: 4120)
- BKbClfr.exe (PID: 8892)
Starts process via Powershell
- powershell.exe (PID: 7732)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 4424)
Probably download files using WebClient
- mshta.exe (PID: 7468)
- mshta.exe (PID: 6676)
- mshta.exe (PID: 7224)
- mshta.exe (PID: 2104)
Found IP address in command line
- powershell.exe (PID: 7732)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 4424)
Manipulates environment variables
- powershell.exe (PID: 7732)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 4424)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 6676)
- mshta.exe (PID: 7468)
- mshta.exe (PID: 7224)
- mshta.exe (PID: 2104)
- mmc.exe (PID: 3796)
- dupfilesfreecleaner11.exe (PID: 7104)
- Mvyo43T.exe (PID: 8948)
- cmd.exe (PID: 8648)
- core.exe (PID: 684)
- BKbClfr.exe (PID: 8892)
- cmd.exe (PID: 7472)
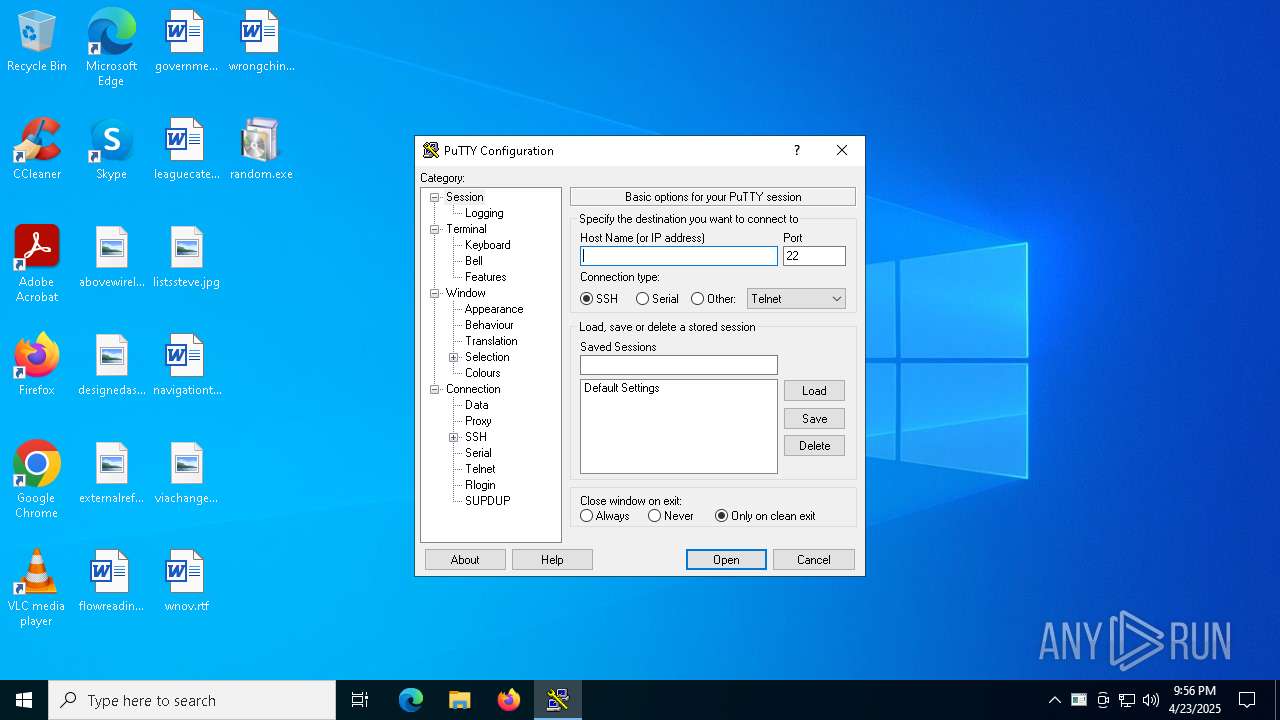
PUTTY has been detected
- putty.exe (PID: 5936)
Script adds exclusion path to Windows Defender
- mmc.exe (PID: 3796)
- Mvyo43T.exe (PID: 8948)
- BKbClfr.exe (PID: 8892)
The process drops C-runtime libraries
- usn4cb68tur.tmp (PID: 8104)
- ku9ZDO7.exe (PID: 9064)
- SystemZenith.exe (PID: 1600)
Executing commands from a ".bat" file
- yuNBaP5SaKB.exe (PID: 8512)
Get information on the list of running processes
- cmd.exe (PID: 8596)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8596)
Creates or modifies Windows services
- mmc.exe (PID: 3796)
Drops a system driver (possible attempt to evade defenses)
- mmc.exe (PID: 3796)
Reads the date of Windows installation
- Mvyo43T.exe (PID: 8672)
- Mvyo43T.exe (PID: 8948)
- BKbClfr.exe (PID: 7216)
- BKbClfr.exe (PID: 8892)
Application launched itself
- Mvyo43T.exe (PID: 8672)
- cmd.exe (PID: 8596)
- BKbClfr.exe (PID: 7216)
Executes application which crashes
- 41e7a26e74.exe (PID: 5624)
Starts application with an unusual extension
- cmd.exe (PID: 8596)
Starts the AutoIt3 executable file
- cmd.exe (PID: 8596)
The executable file from the user directory is run by the CMD process
- Florist.com (PID: 8444)
Downloads file from URI via Powershell
- powershell.exe (PID: 3028)
- powershell.exe (PID: 9060)
The process checks if it is being run in the virtual environment
- svchost.exe (PID: 8488)
The process creates files with name similar to system file names
- msiexec.exe (PID: 5860)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 8580)
INFO
The sample compiled with english language support
- random.exe (PID: 7512)
- saved.exe (PID: 6392)
- 3d8369a4e7.tmp (PID: 2340)
- 05b95a6d88.exe (PID: 1764)
- usn4cb68tur.tmp (PID: 8104)
- dupfilesfreecleaner11.exe (PID: 7104)
- msiexec.exe (PID: 5860)
- ku9ZDO7.exe (PID: 9124)
- ku9ZDO7.exe (PID: 9064)
- SystemZenith.exe (PID: 1600)
Create files in a temporary directory
- random.exe (PID: 7512)
- 1a55b8.exe (PID: 7532)
- MELNE06FNPFT30X3450ZAVO3S6JG2.exe (PID: 8188)
- 2t6983.exe (PID: 7660)
- saved.exe (PID: 6392)
- ge0NTgK.exe (PID: 4120)
- 3d8369a4e7.exe (PID: 5968)
- fb82e63a4c.exe (PID: 4208)
- fb82e63a4c.exe (PID: 6824)
- 3d8369a4e7.tmp (PID: 2340)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- 05b95a6d88.exe (PID: 1764)
- usn4cb68tur.exe (PID: 540)
- usn4cb68tur.tmp (PID: 8104)
- yuNBaP5SaKB.exe (PID: 8512)
- extrac32.exe (PID: 9116)
- powershell.exe (PID: 9004)
- HVoSsE7NPKxcz.exe (PID: 8792)
- svchost015.exe (PID: 856)
- ku9ZDO7.exe (PID: 9064)
- ku9ZDO7.exe (PID: 9124)
- SystemZenith.exe (PID: 9040)
- ge0NTgK.exe (PID: 8640)
Reads the computer name
- 1a55b8.exe (PID: 7532)
- namez.exe (PID: 7648)
- 2t6983.exe (PID: 7660)
- saved.exe (PID: 6392)
- MELNE06FNPFT30X3450ZAVO3S6JG2.exe (PID: 8188)
- MSBuild.exe (PID: 5588)
- KDUmpUI.exe (PID: 1040)
- ge0NTgK.exe (PID: 4120)
- 3d8369a4e7.tmp (PID: 2340)
- 9ad92fb87e.exe (PID: 3300)
- 1bab3e99c3.exe (PID: 7760)
- 9ad92fb87e.exe (PID: 7768)
- putty.exe (PID: 5936)
- bdfba07db4.exe (PID: 8072)
- bdfba07db4.exe (PID: 8156)
- info.exe (PID: 5024)
- fb82e63a4c.exe (PID: 4208)
- fb82e63a4c.exe (PID: 6824)
- core.exe (PID: 684)
- 05b95a6d88.exe (PID: 1764)
- x5l4kAD.exe (PID: 7452)
- MSBuild.exe (PID: 1568)
- x5l4kAD.exe (PID: 2520)
- svchost015.exe (PID: 856)
- WwrZHbF.exe (PID: 7700)
- usn4cb68tur.tmp (PID: 8104)
- e134d2cad1.exe (PID: 5260)
- dupfilesfreecleaner11.exe (PID: 7104)
- yuNBaP5SaKB.exe (PID: 8512)
- DupFilesFreeCleaner.exe (PID: 8652)
- Mvyo43T.exe (PID: 8672)
- HVoSsE7NPKxcz.exe (PID: 8792)
- extrac32.exe (PID: 9116)
- Mvyo43T.exe (PID: 8948)
- Florist.com (PID: 8444)
- cVEHCL4.exe (PID: 8508)
- elpyrorrerz.exe (PID: 3100)
- BKbClfr.exe (PID: 7216)
- ipconfig.exe (PID: 3992)
- BKbClfr.exe (PID: 8892)
- ku9ZDO7.exe (PID: 9064)
- SystemZenith.exe (PID: 1600)
- XClient.exe (PID: 9200)
- bmoqczjxpzwhz.exe (PID: 8796)
Checks supported languages
- 1a55b8.exe (PID: 7532)
- random.exe (PID: 7512)
- namez.exe (PID: 7648)
- 2t6983.exe (PID: 7660)
- MELNE06FNPFT30X3450ZAVO3S6JG2.exe (PID: 8188)
- ge0NTgK.exe (PID: 4120)
- saved.exe (PID: 6392)
- namez.exe (PID: 1912)
- saved.exe (PID: 7288)
- KDUmpUI.exe (PID: 1040)
- d2f34596d5.exe (PID: 7808)
- MSBuild.exe (PID: 5588)
- 3d8369a4e7.exe (PID: 5968)
- 3d8369a4e7.tmp (PID: 2340)
- 9ad92fb87e.exe (PID: 3300)
- 1bab3e99c3.exe (PID: 7760)
- 9ad92fb87e.exe (PID: 7768)
- putty.exe (PID: 5936)
- bdfba07db4.exe (PID: 8072)
- bdfba07db4.exe (PID: 8156)
- core.exe (PID: 684)
- info.exe (PID: 5024)
- fb82e63a4c.exe (PID: 4208)
- fb82e63a4c.exe (PID: 6824)
- 05b95a6d88.exe (PID: 1764)
- 7ADFG6KV48BSFVLAACQTKUL.exe (PID: 4648)
- U3EP43USXFZQAGX0QG.exe (PID: 4208)
- svchost015.exe (PID: 856)
- 47Q6wZM.exe (PID: 7444)
- TempRY9SYVHA3N3JQ1HLVI4AONYMOENMLZXX.EXE (PID: 7292)
- Temp8ORFZPKMXARGAH5SAJCVKZYJEI2T7WV0.EXE (PID: 6852)
- TempRY9SYVHA3N3JQ1HLVI4AONYMOENMLZXX.EXE (PID: 3156)
- x5l4kAD.exe (PID: 7452)
- MSBuild.exe (PID: 1568)
- x5l4kAD.exe (PID: 2520)
- saved.exe (PID: 7704)
- Temp8ORFZPKMXARGAH5SAJCVKZYJEI2T7WV0.EXE (PID: 8016)
- namez.exe (PID: 720)
- WwrZHbF.exe (PID: 7700)
- usn4cb68tur.tmp (PID: 8104)
- usn4cb68tur.exe (PID: 540)
- dupfilesfreecleaner11.exe (PID: 7104)
- e134d2cad1.exe (PID: 5260)
- Mvyo43T.exe (PID: 8672)
- DupFilesFreeCleaner.exe (PID: 8652)
- yuNBaP5SaKB.exe (PID: 8512)
- HVoSsE7NPKxcz.exe (PID: 8792)
- Mvyo43T.exe (PID: 8948)
- extrac32.exe (PID: 9116)
- 41e7a26e74.exe (PID: 5624)
- Florist.com (PID: 8444)
- cVEHCL4.exe (PID: 8508)
- msiexec.exe (PID: 5860)
- elpyrorrerz.exe (PID: 3100)
- BKbClfr.exe (PID: 7216)
- ipconfig.exe (PID: 3992)
- BKbClfr.exe (PID: 8892)
- ku9ZDO7.exe (PID: 9124)
- SystemZenith.exe (PID: 1600)
- ku9ZDO7.exe (PID: 9064)
- SystemZenith.exe (PID: 9040)
- zb7jDew.exe (PID: 5740)
- XClient.exe (PID: 9200)
- bmoqczjxpzwhz.exe (PID: 8796)
- ge0NTgK.exe (PID: 8640)
Process checks computer location settings
- 1a55b8.exe (PID: 7532)
- saved.exe (PID: 6392)
- MELNE06FNPFT30X3450ZAVO3S6JG2.exe (PID: 8188)
- 3d8369a4e7.tmp (PID: 2340)
- dupfilesfreecleaner11.exe (PID: 7104)
- yuNBaP5SaKB.exe (PID: 8512)
- Mvyo43T.exe (PID: 8672)
- Mvyo43T.exe (PID: 8948)
- BKbClfr.exe (PID: 7216)
- BKbClfr.exe (PID: 8892)
Reads the software policy settings
- 2t6983.exe (PID: 7660)
- MSBuild.exe (PID: 5588)
- KDUmpUI.exe (PID: 1040)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- core.exe (PID: 684)
- MSBuild.exe (PID: 1568)
- e134d2cad1.exe (PID: 5260)
- HVoSsE7NPKxcz.exe (PID: 8792)
- x5l4kAD.exe (PID: 7452)
- powershell.exe (PID: 9004)
- slui.exe (PID: 2568)
- cVEHCL4.exe (PID: 8508)
- msiexec.exe (PID: 5860)
- elpyrorrerz.exe (PID: 3100)
- Florist.com (PID: 8444)
- bmoqczjxpzwhz.exe (PID: 8796)
Checks proxy server information
- namez.exe (PID: 7648)
- saved.exe (PID: 6392)
- powershell.exe (PID: 4424)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 8056)
- svchost015.exe (PID: 856)
- slui.exe (PID: 2568)
Reads the machine GUID from the registry
- 2t6983.exe (PID: 7660)
- MSBuild.exe (PID: 5588)
- KDUmpUI.exe (PID: 1040)
- 9ad92fb87e.exe (PID: 3300)
- 9ad92fb87e.exe (PID: 7768)
- core.exe (PID: 684)
- x5l4kAD.exe (PID: 7452)
- x5l4kAD.exe (PID: 2520)
- MSBuild.exe (PID: 1568)
- svchost015.exe (PID: 856)
- e134d2cad1.exe (PID: 5260)
- HVoSsE7NPKxcz.exe (PID: 8792)
- cVEHCL4.exe (PID: 8508)
- elpyrorrerz.exe (PID: 3100)
- XClient.exe (PID: 9200)
- Florist.com (PID: 8444)
Themida protector has been detected
- 2t6983.exe (PID: 7660)
- ge0NTgK.exe (PID: 4120)
Creates files or folders in the user directory
- saved.exe (PID: 6392)
- ge0NTgK.exe (PID: 4120)
- 3d8369a4e7.tmp (PID: 2340)
- svchost015.exe (PID: 856)
- usn4cb68tur.tmp (PID: 8104)
- cVEHCL4.exe (PID: 8508)
- msiexec.exe (PID: 5860)
Application launched itself
- chrome.exe (PID: 680)
- chrome.exe (PID: 6108)
- chrome.exe (PID: 3008)
- msedge.exe (PID: 7916)
- msedge.exe (PID: 2192)
- msedge.exe (PID: 2432)
- firefox.exe (PID: 5380)
- firefox.exe (PID: 2240)
- firefox.exe (PID: 7728)
- firefox.exe (PID: 7760)
- firefox.exe (PID: 7100)
- chrome.exe (PID: 8800)
- chrome.exe (PID: 7828)
Attempting to use instant messaging service
- MSBuild.exe (PID: 5588)
- svchost.exe (PID: 2196)
- Florist.com (PID: 8444)
- bmoqczjxpzwhz.exe (PID: 8796)
Auto-launch of the file from Registry key
- saved.exe (PID: 6392)
- x5l4kAD.exe (PID: 7452)
- cVEHCL4.exe (PID: 8508)
Manual execution by a user
- 9ad92fb87e.exe (PID: 7768)
- 1bab3e99c3.exe (PID: 8176)
- bdfba07db4.exe (PID: 8156)
- mshta.exe (PID: 7468)
- fb82e63a4c.exe (PID: 6824)
- mshta.exe (PID: 2104)
- x5l4kAD.exe (PID: 2520)
- DupFilesFreeCleaner.exe (PID: 8652)
- svchost.exe (PID: 8488)
- XClient.exe (PID: 9200)
Creates a software uninstall entry
- 3d8369a4e7.tmp (PID: 2340)
- usn4cb68tur.tmp (PID: 8104)
Reads mouse settings
- bdfba07db4.exe (PID: 8072)
- bdfba07db4.exe (PID: 8156)
- fb82e63a4c.exe (PID: 4208)
- fb82e63a4c.exe (PID: 6824)
- Florist.com (PID: 8444)
Auto-launch of the file from Task Scheduler
- cmd.exe (PID: 5260)
- cmd.exe (PID: 5680)
Reads Internet Explorer settings
- mshta.exe (PID: 6676)
- mshta.exe (PID: 7468)
- mshta.exe (PID: 7224)
- mshta.exe (PID: 2104)
Disables trace logs
- powershell.exe (PID: 4424)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 3028)
- powershell.exe (PID: 9060)
The executable file from the user directory is run by the Powershell process
- TempRY9SYVHA3N3JQ1HLVI4AONYMOENMLZXX.EXE (PID: 7292)
- TempRY9SYVHA3N3JQ1HLVI4AONYMOENMLZXX.EXE (PID: 3156)
- Temp8ORFZPKMXARGAH5SAJCVKZYJEI2T7WV0.EXE (PID: 6852)
- Temp8ORFZPKMXARGAH5SAJCVKZYJEI2T7WV0.EXE (PID: 8016)
Reads Environment values
- x5l4kAD.exe (PID: 7452)
- x5l4kAD.exe (PID: 2520)
- msiexec.exe (PID: 5576)
- ge0NTgK.exe (PID: 4120)
Changes the registry key values via Powershell
- dupfilesfreecleaner11.exe (PID: 7104)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 8352)
- powershell.exe (PID: 8760)
Creates files in the program directory
- dupfilesfreecleaner11.exe (PID: 7104)
- SystemZenith.exe (PID: 1600)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 8352)
- powershell.exe (PID: 9004)
- powershell.exe (PID: 8760)
Creates a new folder
- cmd.exe (PID: 9104)
Reads security settings of Internet Explorer
- powershell.exe (PID: 9004)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5860)
The sample compiled with german language support
- msiexec.exe (PID: 5860)
The sample compiled with spanish language support
- msiexec.exe (PID: 5860)
The sample compiled with french language support
- msiexec.exe (PID: 5860)
The sample compiled with Indonesian language support
- msiexec.exe (PID: 5860)
The sample compiled with portuguese language support
- msiexec.exe (PID: 5860)
The sample compiled with korean language support
- msiexec.exe (PID: 5860)
The sample compiled with swedish language support
- msiexec.exe (PID: 5860)
The sample compiled with polish language support
- msiexec.exe (PID: 5860)
The sample compiled with slovak language support
- msiexec.exe (PID: 5860)
The sample compiled with chinese language support
- msiexec.exe (PID: 5860)
The sample compiled with arabic language support
- msiexec.exe (PID: 5860)
Reads product name
- ge0NTgK.exe (PID: 4120)
Reads CPU info
- ge0NTgK.exe (PID: 4120)
The sample compiled with Italian language support
- msiexec.exe (PID: 5860)
The sample compiled with japanese language support
- msiexec.exe (PID: 5860)
The sample compiled with russian language support
- msiexec.exe (PID: 5860)
The sample compiled with turkish language support
- msiexec.exe (PID: 5860)
Python executable
- SystemZenith.exe (PID: 1600)
- SystemZenith.exe (PID: 9040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(7648) namez.exe
C2185.215.113.59
URLhttp://185.215.113.59/Dy5h4kus/index.php
Version5.34
Options
Drop directoryf1e82329e5
Drop namenamez.exe
Strings (125)S-%lu-
og:
clip.dll
ProgramData\
shell32.dll
<c>
vs:
Programs
&&
VideoID
ESET
av:
\App
0000043f
Doctor Web
:::
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
------
rundll32.exe
00000422
0123456789
st=s
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
msi
ar:
GetNativeSystemInfo
Norton
-%lu
Sophos
zip
SOFTWARE\Microsoft\Windows NT\CurrentVersion
"
Content-Type: application/octet-stream
|
+++
" && ren
pc:
#
d1
cmd /C RMDIR /s/q
Bitdefender
Comodo
<d>
Kaspersky Lab
DefaultSettings.YResolution
Main
/Dy5h4kus/index.php
-executionpolicy remotesigned -File "
&& Exit"
ProductName
&unit=
2022
Panda Security
=
Rem
cmd
\0000
id:
sd:
--
185.215.113.59
/quiet
rundll32
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%-lu
random
GET
"taskkill /f /im "
Content-Disposition: form-data; name="data"; filename="
00000423
5.34
2016
?scr=1
ComputerName
Keyboard Layout\Preload
Powershell.exe
POST
http://
AVAST Software
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
ps1
DefaultSettings.XResolution
Startup
CurrentBuild
e3
cred.dll|clip.dll|
------
WinDefender
wb
https://
Avira
2025
" && timeout 1 && del
cred.dll
un:
SYSTEM\ControlSet001\Services\BasicDisplay\Video
rb
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
360TotalSecurity
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e1
lv:
shutdown -s -t 0
/k
e2
f1e82329e5
namez.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
exe
%USERPROFILE%
-unicode-
r=
.jpg
dll
Content-Type: multipart/form-data; boundary=----
2019
bi:
\
"
kernel32.dll
os:
abcdefghijklmnopqrstuvwxyz0123456789-_
dm:
AVG
(PID) Process(6392) saved.exe
C2185.39.17.163
URLhttp://185.39.17.163/Su8kud7i/index.php
Version5.34
Options
Drop directoryc13dbdc4fa
Drop namesaved.exe
Strings (125)S-%lu-
og:
clip.dll
ProgramData\
shell32.dll
<c>
vs:
Programs
&&
VideoID
ESET
av:
\App
0000043f
Doctor Web
:::
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
------
rundll32.exe
00000422
185.39.17.163
0123456789
st=s
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
msi
ar:
GetNativeSystemInfo
Norton
-%lu
Sophos
zip
SOFTWARE\Microsoft\Windows NT\CurrentVersion
"
Content-Type: application/octet-stream
|
+++
" && ren
pc:
#
d1
cmd /C RMDIR /s/q
Bitdefender
Comodo
<d>
Kaspersky Lab
DefaultSettings.YResolution
Main
c13dbdc4fa
-executionpolicy remotesigned -File "
&& Exit"
ProductName
&unit=
2022
Panda Security
=
Rem
cmd
\0000
id:
sd:
--
/quiet
rundll32
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%-lu
random
GET
"taskkill /f /im "
Content-Disposition: form-data; name="data"; filename="
00000423
5.34
2016
?scr=1
ComputerName
Keyboard Layout\Preload
Powershell.exe
POST
http://
AVAST Software
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
ps1
DefaultSettings.XResolution
Startup
CurrentBuild
e3
cred.dll|clip.dll|
------
WinDefender
wb
https://
Avira
2025
" && timeout 1 && del
cred.dll
un:
SYSTEM\ControlSet001\Services\BasicDisplay\Video
rb
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
360TotalSecurity
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
saved.exe
e1
lv:
/Su8kud7i/index.php
shutdown -s -t 0
/k
e2
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
exe
%USERPROFILE%
-unicode-
r=
.jpg
dll
Content-Type: multipart/form-data; boundary=----
2019
bi:
\
"
kernel32.dll
os:
abcdefghijklmnopqrstuvwxyz0123456789-_
dm:
AVG
Lumma
(PID) Process(7660) 2t6983.exe
C2 (6)hemispherexz.top/xapp
climatologfy.top/kbud
equatorf.run/reiq
clarmodq.top/qoxo
longitudde.digital/wizu
latitudert.live/teui
(PID) Process(5588) MSBuild.exe
C2 (7)hemispherexz.top/xapp
climatologfy.top/kbud
equatorf.run/reiq
longitudde.digital/wizu
meerkaty.digital/sagf
latitudert.live/teui
https://t.me/coba128
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:05:24 22:49:06+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.13 |
| CodeSize: | 25600 |
| InitializedDataSize: | 2176512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a60 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.17763.1 |
| ProductVersionNumber: | 11.0.17763.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.17763.1 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.17763.1 |
Total processes
361
Monitored processes
226
Malicious processes
53
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Users\admin\AppData\Roaming\vSZS85\usn4cb68tur.exe" | C:\Users\admin\AppData\Roaming\vSZS85\usn4cb68tur.exe | svchost015.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: DupFiles Free Cleaner Setup Version: Modules
| |||||||||||||||
| 680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --headless --no-first-run | C:\Program Files\Google\Chrome\Application\chrome.exe | — | ge0NTgK.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Roaming\MyApp\core.exe" | C:\Users\admin\AppData\Roaming\MyApp\core.exe | 3d8369a4e7.tmp | ||||||||||||
User: admin Company: EC Software GmbH Integrity Level: MEDIUM Description: eViewer for Windows Version: 2.5.0.0 Modules
| |||||||||||||||
| 720 | "C:\Users\admin\AppData\Local\Temp\f1e82329e5\namez.exe" | C:\Users\admin\AppData\Local\Temp\f1e82329e5\namez.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\Temp\10004110101\05b95a6d88.exe" | C:\Users\admin\AppData\Local\Temp\svchost015.exe | 05b95a6d88.exe | ||||||||||||
User: admin Company: X-Ways Software Technology AG Integrity Level: MEDIUM Description: WinHex Exit code: 0 Version: 21.1 Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\AppData\Local\Temp\10003850101\KDUmpUI.exe" | C:\Users\admin\AppData\Local\Temp\10003850101\KDUmpUI.exe | saved.exe | ||||||||||||
User: admin Company: Responsive Strategy Group Integrity Level: MEDIUM Description: Provides Schedule Workflow capabilities Exit code: 0 Version: 1.3.16.1765 Modules
| |||||||||||||||
| 1052 | taskkill /F /IM firefox.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | bdfba07db4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2044 -parentBuildID 20240213221259 -prefsHandle 2036 -prefMapHandle 2024 -prefsLen 31088 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {59286ab1-01e8-4c8d-8afd-80b3209eaedc} 7100 "\\.\pipe\gecko-crash-server-pipe.7100" 20f40b82310 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
165 224
Read events
164 890
Write events
325
Delete events
9
Modification events
| (PID) Process: | (7648) namez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7648) namez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7648) namez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6392) saved.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6392) saved.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6392) saved.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (680) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (680) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (680) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6108) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
207
Suspicious files
219
Text files
64
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6392 | saved.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\random[1].exe | — | |
MD5:— | SHA256:— | |||
| 6392 | saved.exe | C:\Users\admin\AppData\Local\Temp\10004060101\3d8369a4e7.exe | — | |
MD5:— | SHA256:— | |||
| 7532 | 1a55b8.exe | C:\Users\admin\AppData\Local\Temp\f1e82329e5\namez.exe | executable | |
MD5:3EC886E81B3A5649FF9DAC6D88BABA96 | SHA256:ECC4CDE448FA9B09BFFC77555B878E1656AC4E5C6C4218B08078EE85B1B8F8D5 | |||
| 7512 | random.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\1a55b8.exe | executable | |
MD5:3EC886E81B3A5649FF9DAC6D88BABA96 | SHA256:ECC4CDE448FA9B09BFFC77555B878E1656AC4E5C6C4218B08078EE85B1B8F8D5 | |||
| 7512 | random.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\2t6983.exe | executable | |
MD5:088E2224B89964E741B60E9470C26D36 | SHA256:4D2BA30865EBF3D9DB0E79E7B6A61C6BE86087DE6438FDDC045904AF0DDCEF16 | |||
| 8188 | MELNE06FNPFT30X3450ZAVO3S6JG2.exe | C:\Windows\Tasks\saved.job | binary | |
MD5:0FC5EDBCEB855AE50DD4B61383437F5E | SHA256:B8DC74AE8B6E3189730593BA14987024046016E69DFF2C7558ABA4D63FEDDBB4 | |||
| 6392 | saved.exe | C:\Users\admin\AppData\Local\Temp\10004050101\d2f34596d5.exe | executable | |
MD5:854417B1BA014546C4E867F9EFA148A1 | SHA256:9FEABCF103475DA8F1C125C162542A36A60B8C99F02F9D6D1388FAA5802C8D6F | |||
| 6392 | saved.exe | C:\Users\admin\AppData\Local\Temp\10003850101\KDUmpUI.exe | executable | |
MD5:72ACC275E2659C2AFA995FA855F03CAB | SHA256:30810C2FA79E24D7835CB4FAAC6470885530491CBB2410E938E5A073B3C9BAEF | |||
| 6392 | saved.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\random[1].exe | executable | |
MD5:854417B1BA014546C4E867F9EFA148A1 | SHA256:9FEABCF103475DA8F1C125C162542A36A60B8C99F02F9D6D1388FAA5802C8D6F | |||
| 4120 | ge0NTgK.exe | C:\Users\admin\AppData\Local\Google_Chrome_MASTERKEY.txt | text | |
MD5:B36CA1699A3441AAB90AACEF71C2597A | SHA256:C934D19EC1A5FCC5BFF7C8B7BC1059812F1F7F92CAA225215691ABF3EC1891E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
336
TCP/UDP connections
733
DNS requests
168
Threats
213
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8140 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8140 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
4208 | RUXIMICS.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4208 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7648 | namez.exe | POST | — | 185.215.113.59:80 | http://185.215.113.59/Dy5h4kus/index.php | unknown | — | — | malicious |
7660 | 2t6983.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/mine/random.exe | unknown | — | — | malicious |
— | — | GET | 304 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
6392 | saved.exe | POST | 200 | 185.39.17.163:80 | http://185.39.17.163/Su8kud7i/index.php | unknown | — | — | malicious |
8140 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4208 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7660 | 2t6983.exe | 172.67.205.184:443 | clarmodq.top | CLOUDFLARENET | US | malicious |
4208 | RUXIMICS.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4208 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
7648 | namez.exe | 185.215.113.59:80 | — | 1337team Limited | SC | malicious |
7660 | 2t6983.exe | 185.39.17.162:80 | — | Joint Stock Company Tagnet | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
clarmodq.top |
| malicious |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
t.me |
| whitelisted |
meerkaty.digital |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (clarmodq .top) |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
7660 | 2t6983.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (clarmodq .top) |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
7648 | namez.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
7660 | 2t6983.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7660 | 2t6983.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7660 | 2t6983.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |
7660 | 2t6983.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (clarmodq .top in TLS SNI) |