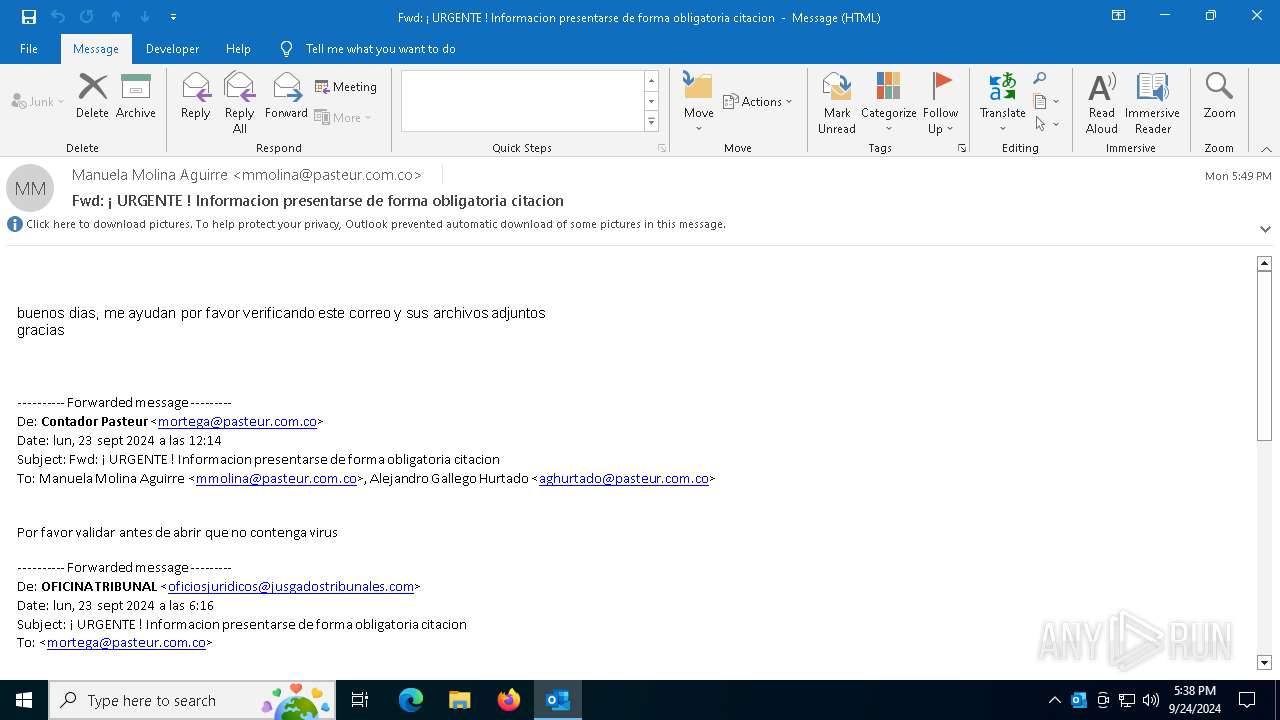
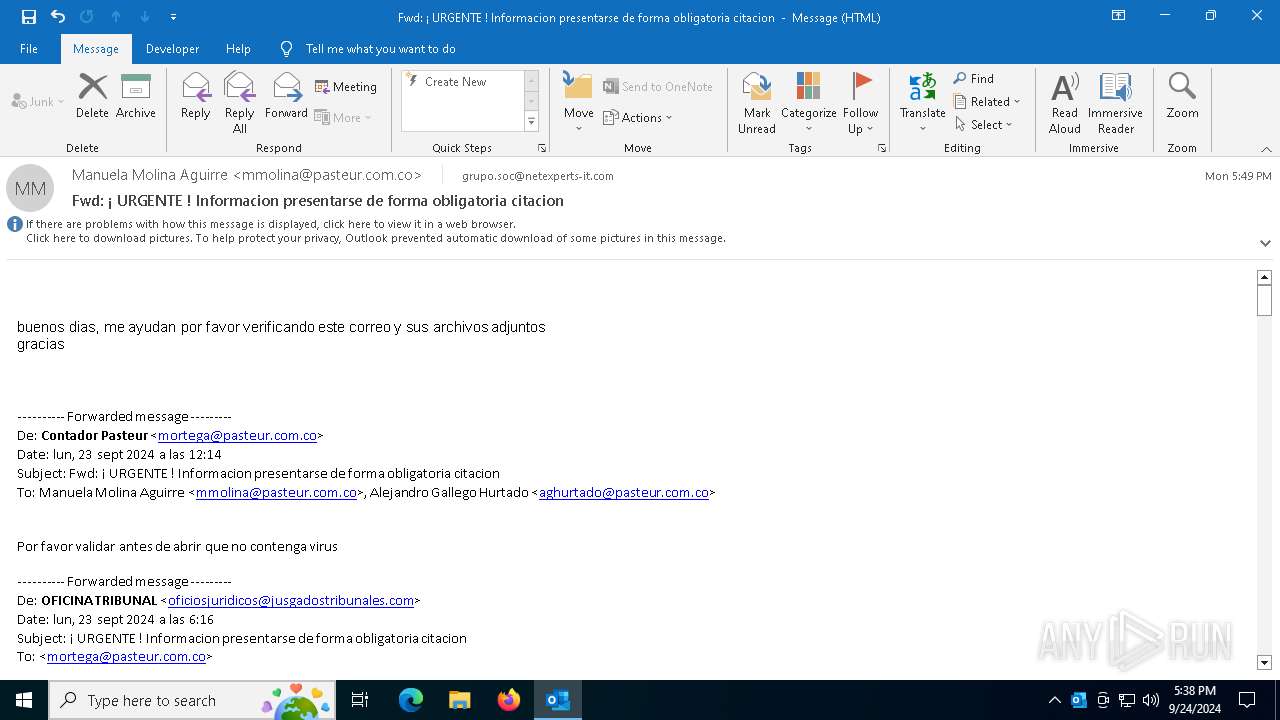
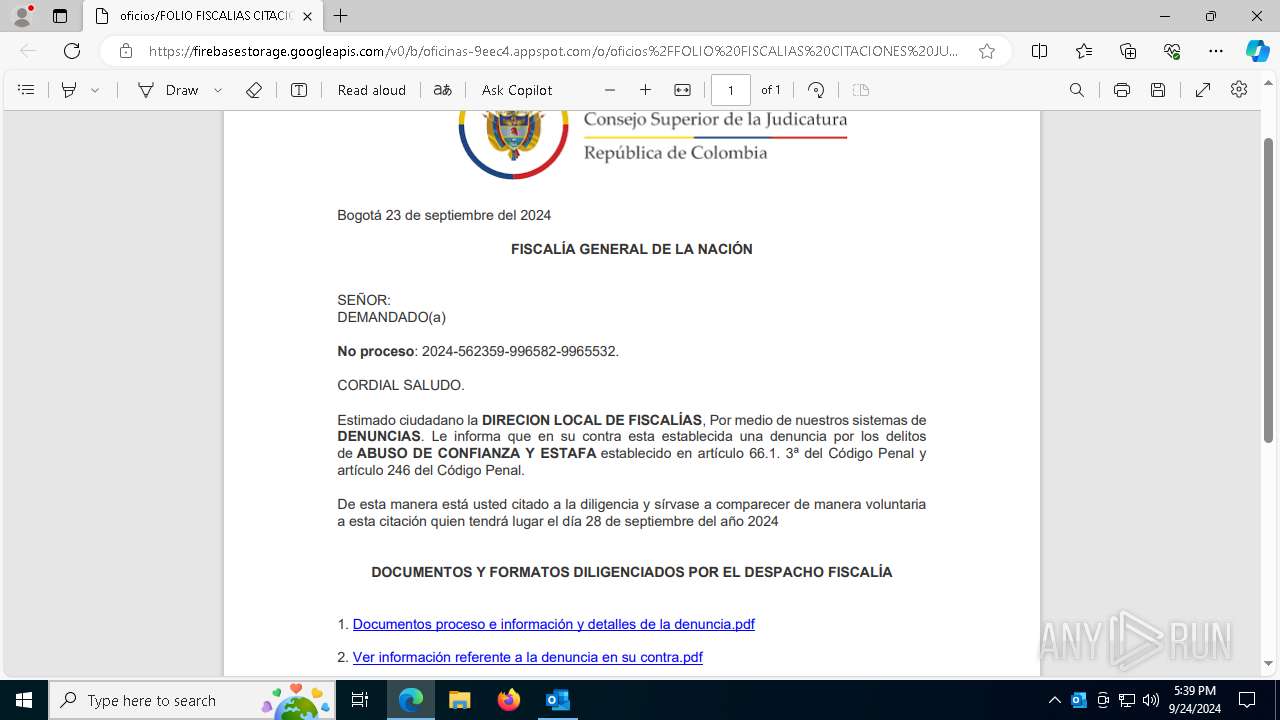
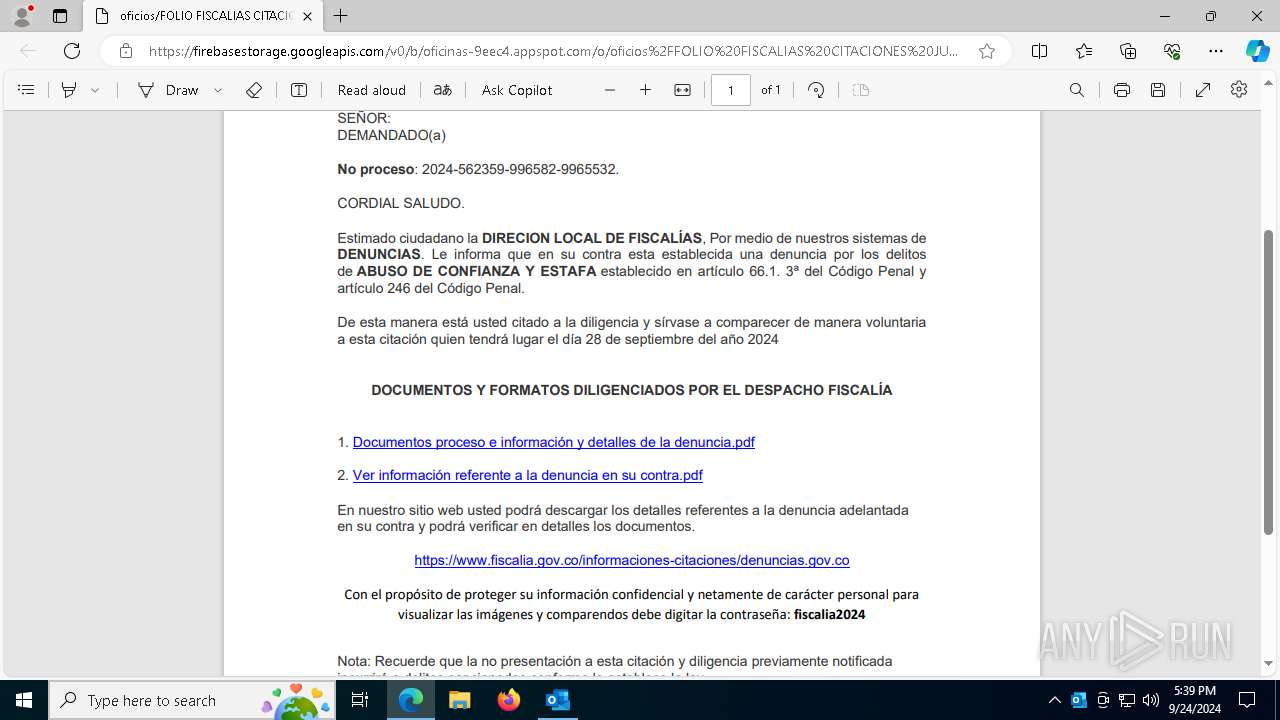
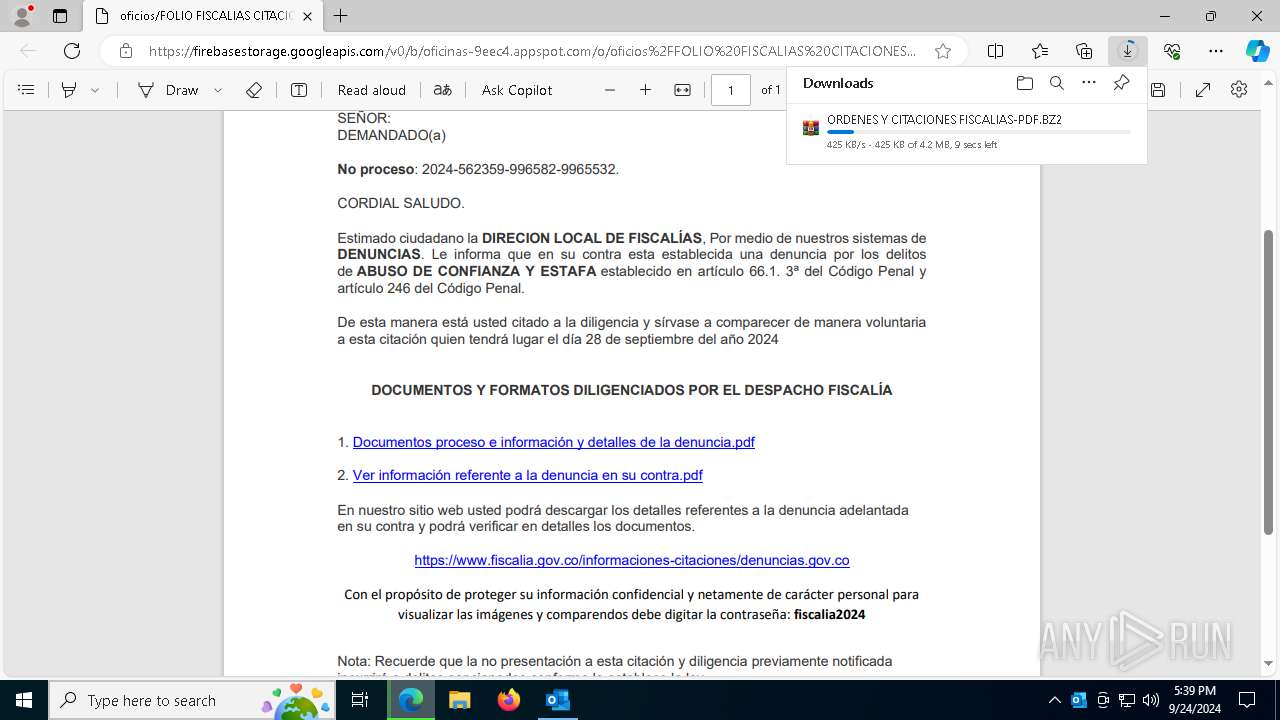
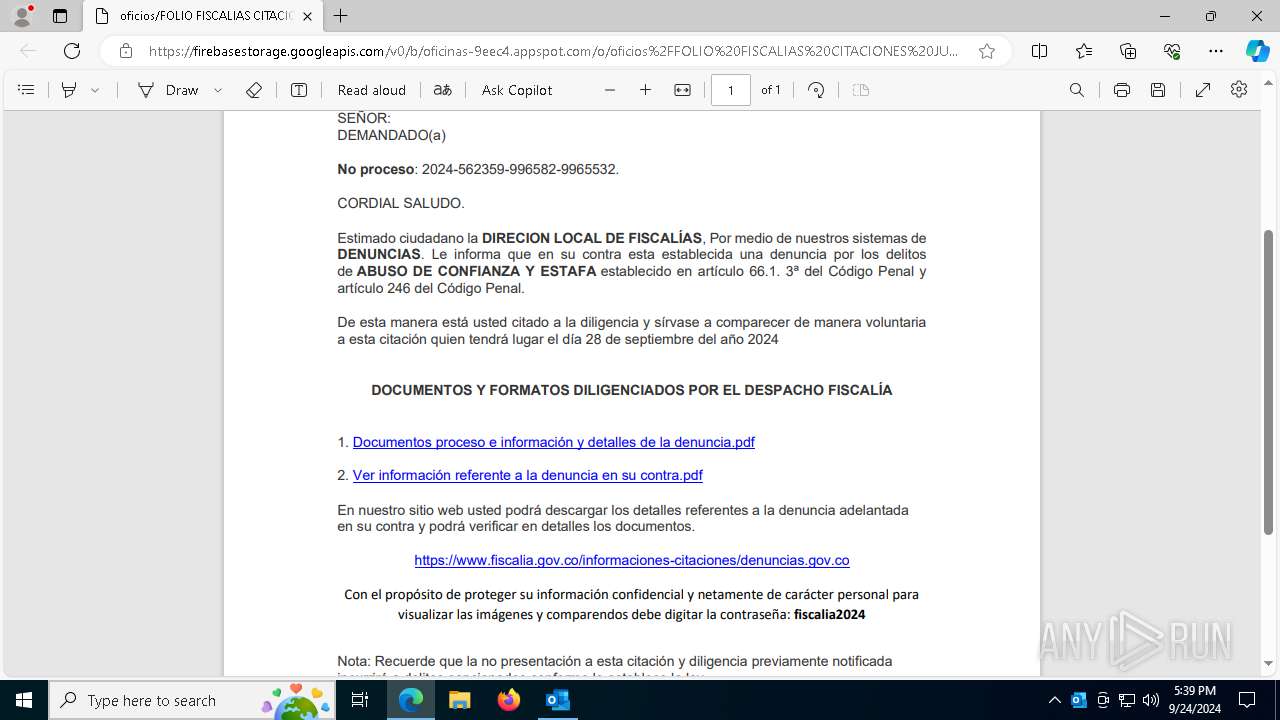
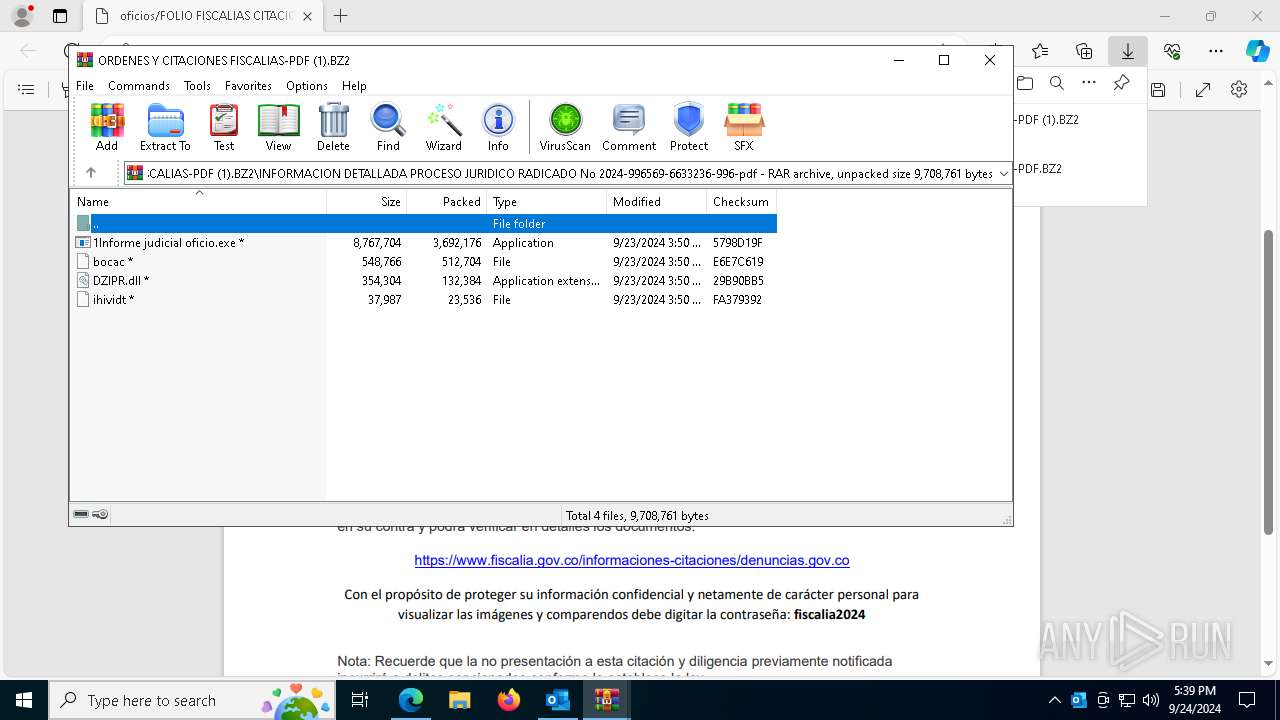
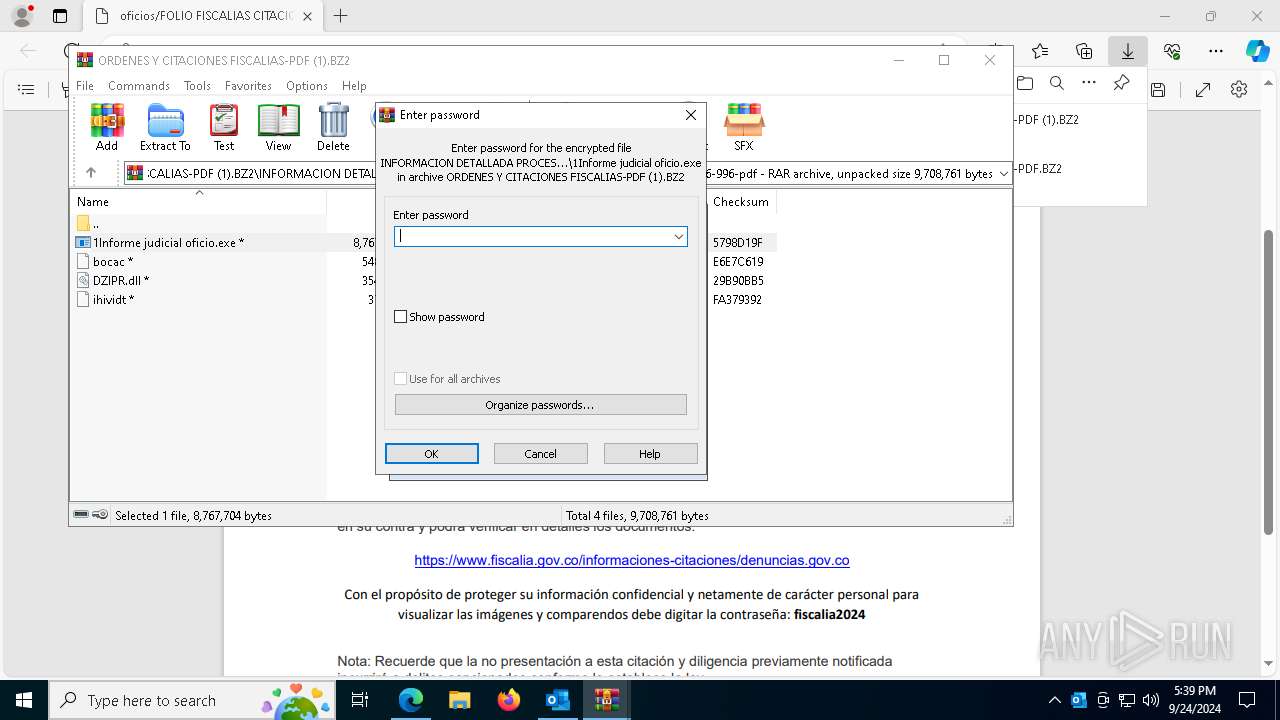
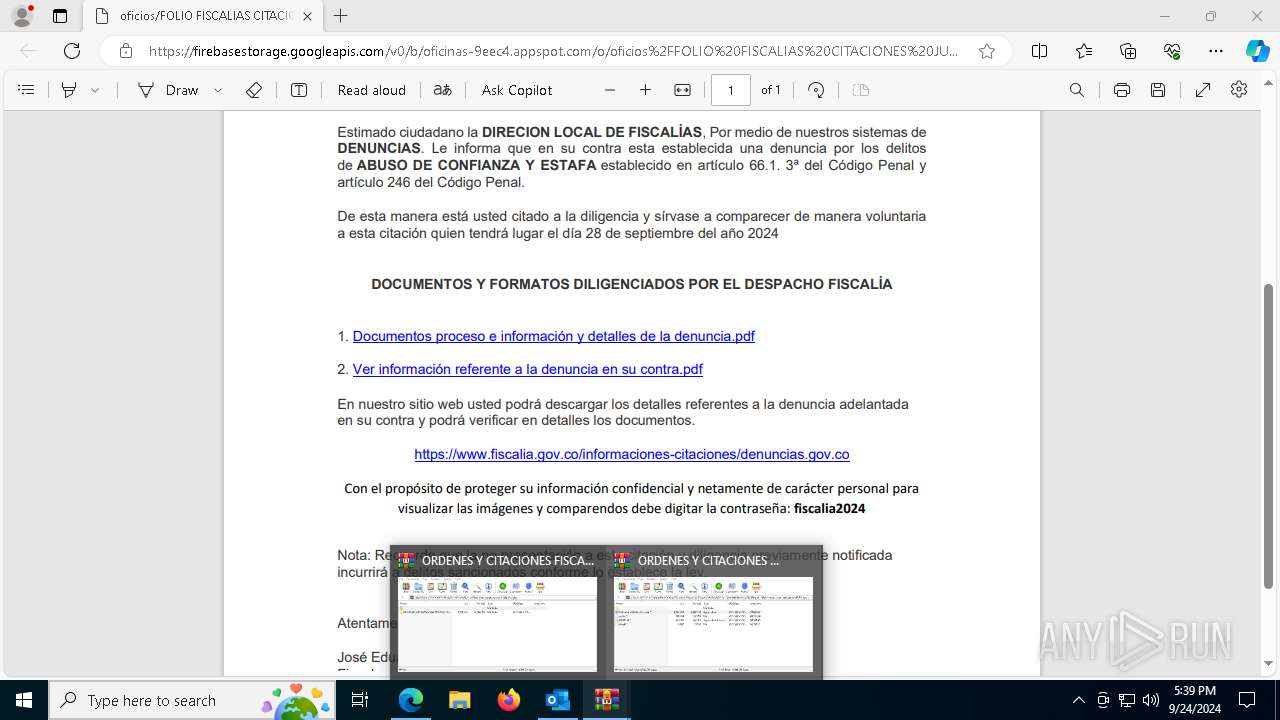
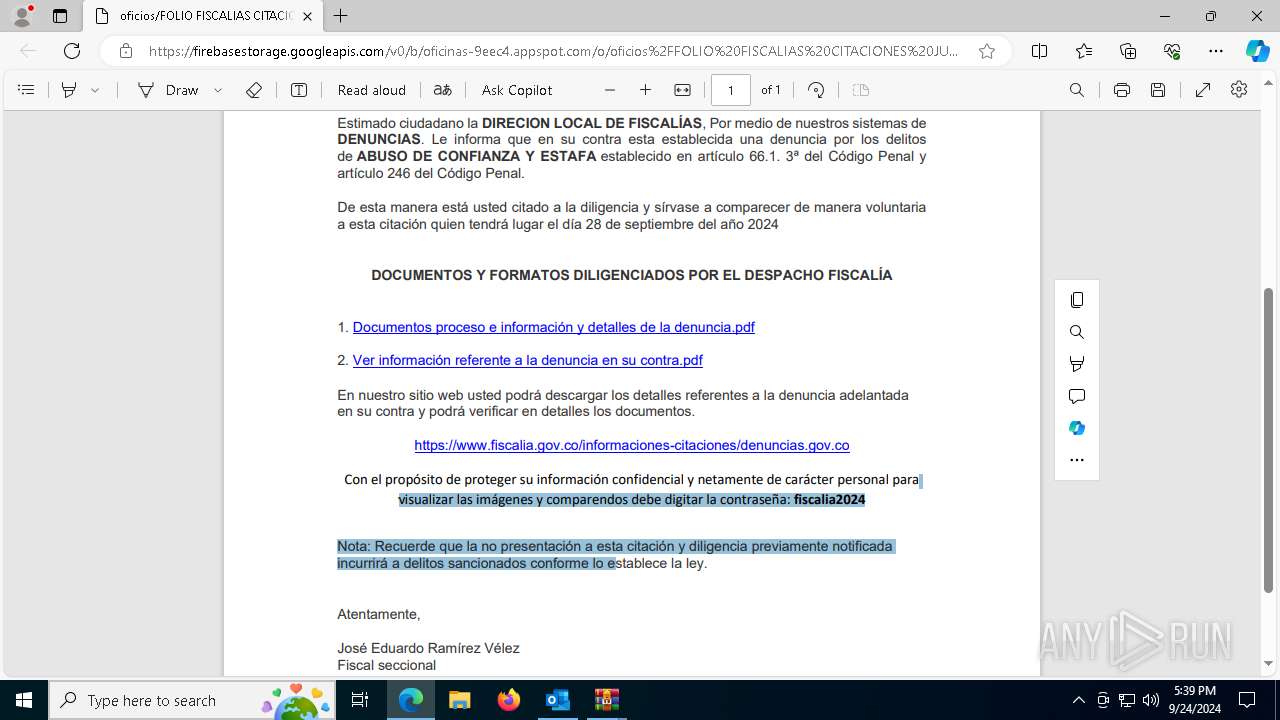
| File name: | Fwd_ ¡ URGENTE ! Informacion presentarse de forma obligatoria citacion.eml |
| Full analysis: | https://app.any.run/tasks/a08ad4f9-49fc-4be1-a3e3-e7ab9330cc50 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | September 24, 2024, 17:38:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines (345), with CRLF line terminators |
| MD5: | 6109C9DBA76700AD4F1D7C740326B9F3 |
| SHA1: | 3369636121316EACEED3842122CEB41914FBAED5 |
| SHA256: | 5DAE482F7E7D8763E6AD76A7A4B8E7F687E21FAE566C154530564BD701683B29 |
| SSDEEP: | 384:8OrjFLhH64qPEgmJQPcszbWvkng8Xt7kBEPG8NYlrYlNYbYA7ijYAnqAiDNYbYAs:8oFLhH6xEgmJQDCv07tjGQDSN |
MALICIOUS
ASYNCRAT has been detected (YARA)
- MSBuild.exe (PID: 7524)
ASYNCRAT has been detected (SURICATA)
- MSBuild.exe (PID: 7524)
SUSPICIOUS
Starts CMD.EXE for commands execution
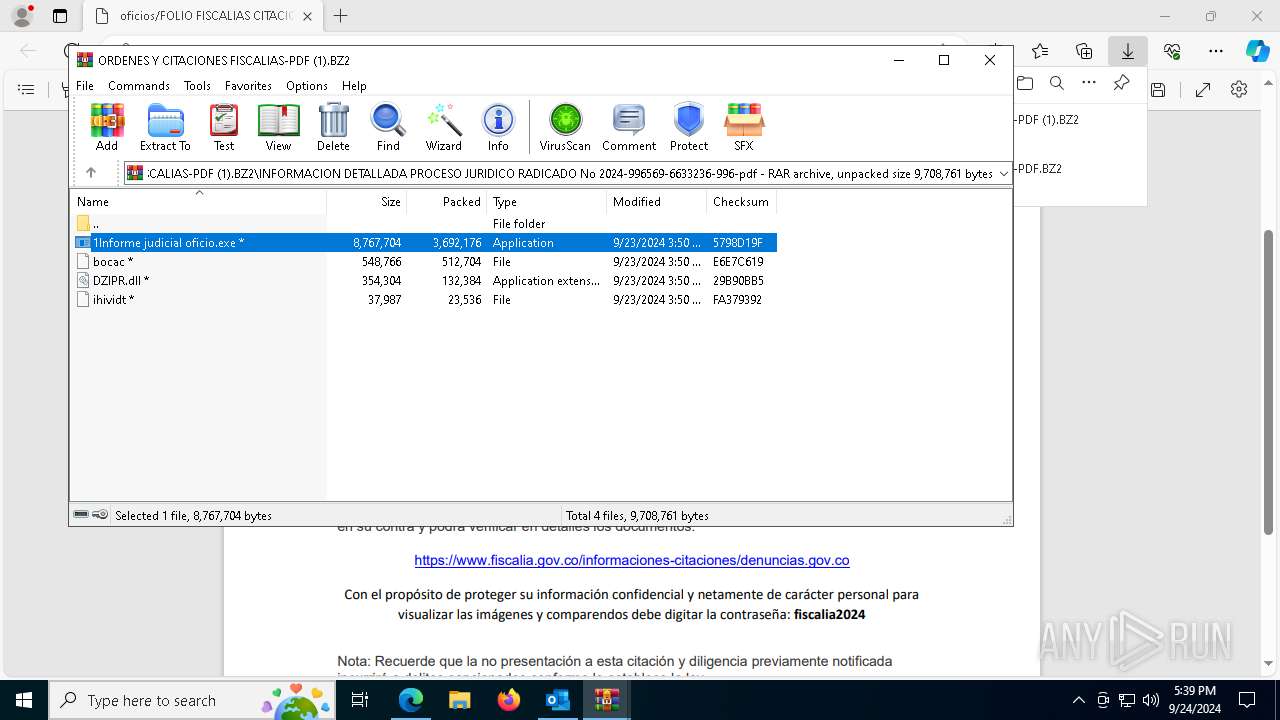
- 1Informe judicial oficio.exe (PID: 7900)
Executable content was dropped or overwritten
- 1Informe judicial oficio.exe (PID: 7900)
Connects to unusual port
- MSBuild.exe (PID: 7524)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 7524)
INFO
Application launched itself
- msedge.exe (PID: 5180)
Sends debugging messages
- msedge.exe (PID: 7176)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7544)
Checks supported languages
- identity_helper.exe (PID: 7428)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 4772)
Reads the computer name
- identity_helper.exe (PID: 7428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(7524) MSBuild.exe
C2 (2)sanchezsanchez2024.duckdns.org
Ports (1)2222
Version1.0.7
Options
AutoRunfalse
Mutexasdfasd654g54
InstallFolder%AppData%
Certificates
Cert1MIICKzCCAZSgAwIBAgIVAKBgFhql6o2v14nWIx79lpt+pSsTMA0GCSqGSIb3DQEBDQUAMF8xEDAOBgNVBAMMB3N2Y2hvc3QxEzARBgNVBAsMCnF3cWRhbmNodW4xHDAaBgNVBAoME0RjUmF0IEJ5IHF3cWRhbmNodW4xCzAJBgNVBAcMAlNIMQswCQYDVQQGEwJDTjAeFw0yMTA0MTAxNDM3NTlaFw0zMjAxMTgxNDM3NTlaMBAxDjAMBgNVBAMMBURjUmF0MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKB...
Server_SignaturePqrTJKLhXvTVdZrS28Q4L3ZkPitt3T/TanM3CROMdmJasumpbjAnbAX6XDyzp4fIo3Ps2q6HBhj0H6L7It/x7HiOQ5OwwMkANwoPkwDDeUU2DBdy4pHPl1bjJtnQSy6mVhNVj3QTIUYI0yElr8QbRkVpYmJK4tMs60cNVmhNOfI=
Keys
AES8e62d7e7a8e4816b5d25420fe9d4c8bc5a1d409836077ced3a9c1dfe24c1768f
SaltDcRatByqwqdanchun
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
179
Monitored processes
50
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1884 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5568 --field-trial-handle=2336,i,16236932100027195607,7348135037761478322,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2812 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5988 --field-trial-handle=2336,i,16236932100027195607,7348135037761478322,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3584 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2184 --field-trial-handle=2336,i,16236932100027195607,7348135037761478322,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
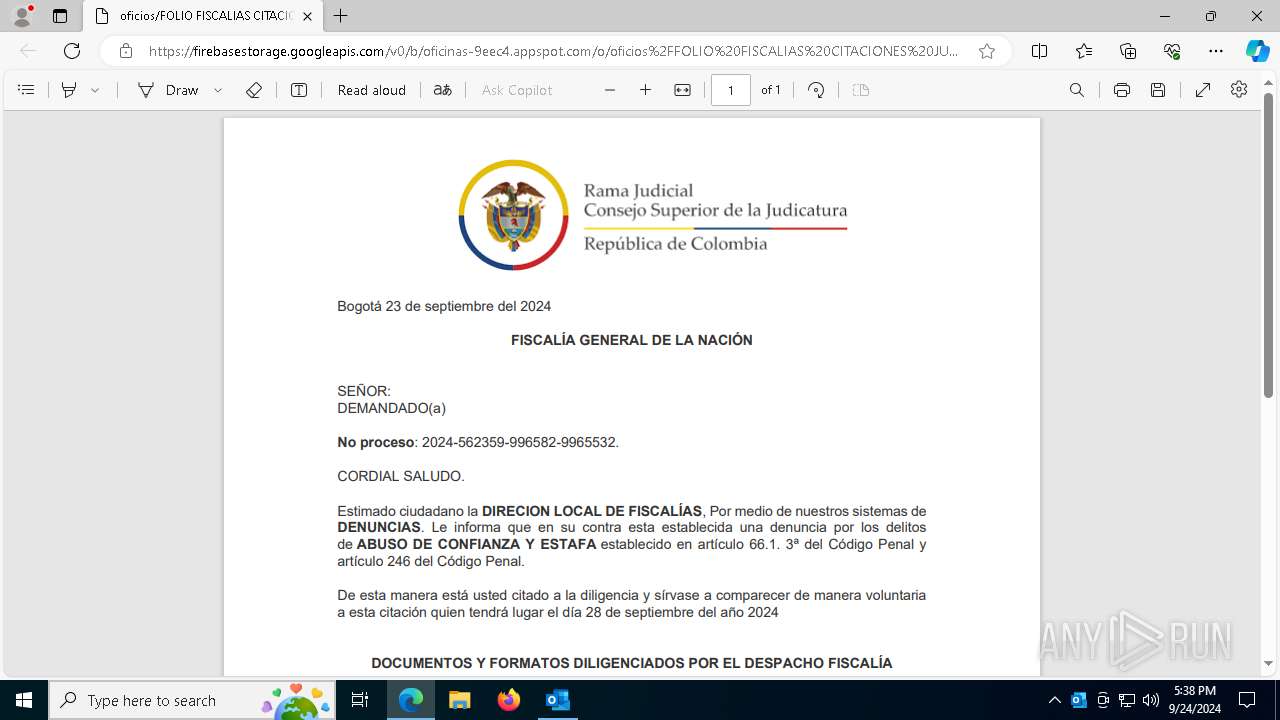
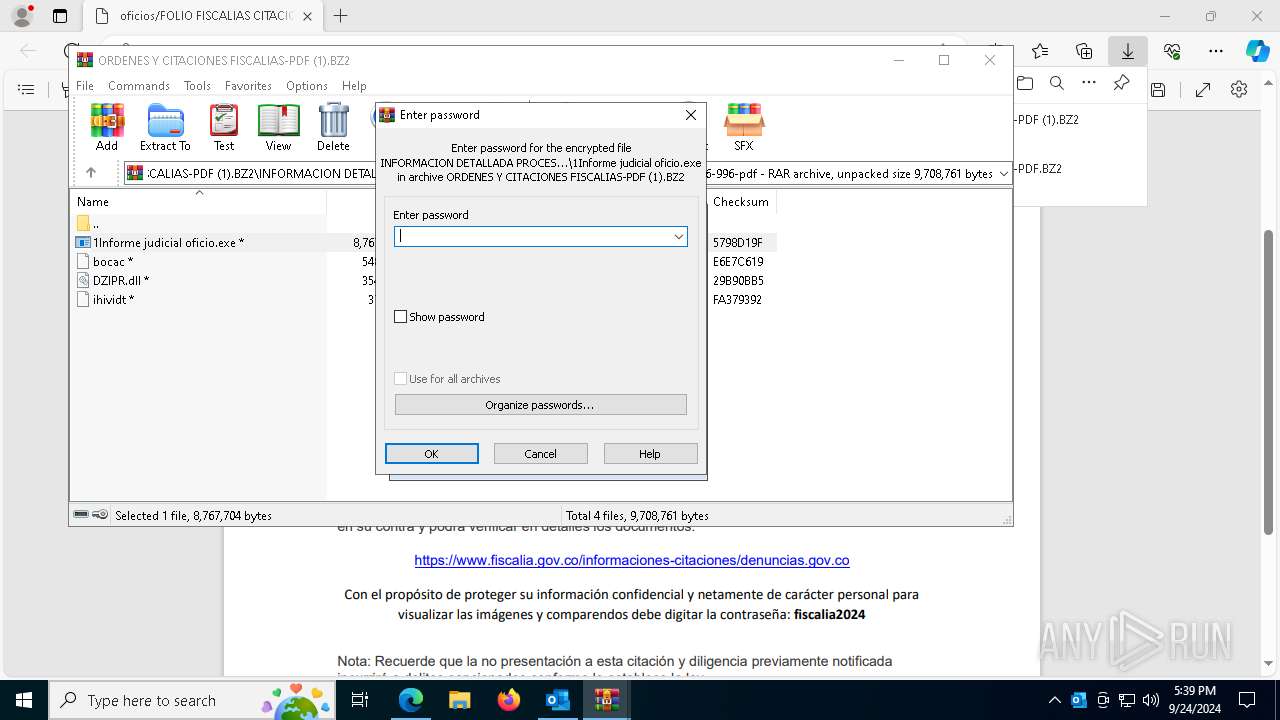
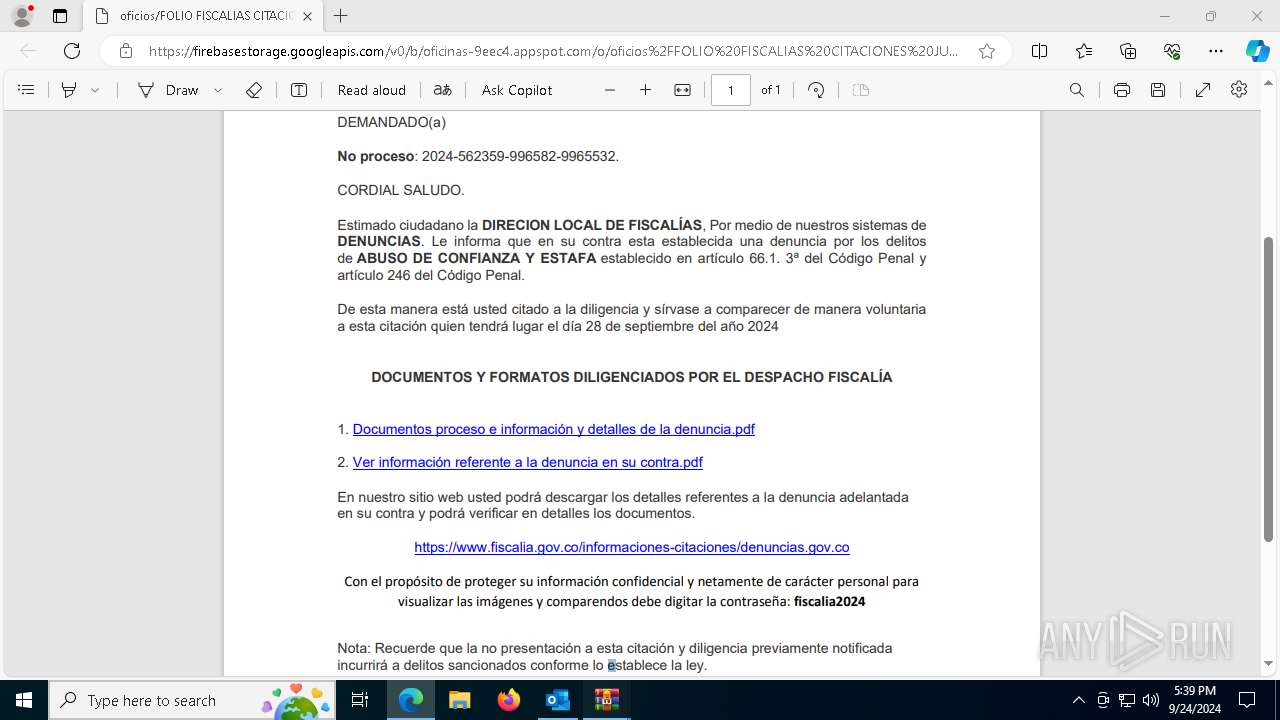
| 4772 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Fwd_ ¡ URGENTE ! Informacion presentarse de forma obligatoria citacion.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4832 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ec,0x2f0,0x2f4,0x2e8,0x2fc,0x7fffd2ca5fd8,0x7fffd2ca5fe4,0x7fffd2ca5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://firebasestorage.googleapis.com/v0/b/oficinas-9eec4.appspot.com/o/oficios%2FFOLIO%20FISCALIAS%20CITACIONES%20JUDICIALES.pdf?alt=media&token=5dcc63cf-f2f3-4dad-a318-c3a1c2126fae | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5212 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2332 --field-trial-handle=2336,i,16236932100027195607,7348135037761478322,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
22 366
Read events
21 899
Write events
399
Delete events
68
Modification events
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\4772 |
| Operation: | write | Name: | 0 |
Value: 0B0E102FACD8EB5936F64CA2A61FF648415072230046819381BA89D5C3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511A425D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (4772) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
3
Suspicious files
236
Text files
74
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4772 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4772 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:85C13DADA57C8132B4B3BE57811108CE | SHA256:C51C257DA943440AE847215EEB941377020A242906490B7EA53B064D37EA6F3D | |||
| 4772 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_8A8CDED7F92D9D47B8BCB283B7B0E6B4.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 5180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF200330.TMP | — | |
MD5:— | SHA256:— | |||
| 5180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF200340.TMP | — | |
MD5:— | SHA256:— | |||
| 5180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF200340.TMP | — | |
MD5:— | SHA256:— | |||
| 5180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4772 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:A2232B63310BBA942FE5A356BF502B6F | SHA256:75DD35EE237609B8A35B1FE2003ECBB2BAEC23A089E151C2F2909B09E75E6E4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
70
DNS requests
64
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5512 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1727399903&P2=404&P3=2&P4=hXxXPIDPV3rIdvkXJJ2aa85Sk3hTVBGv5airxPvHMpTjxW9S5bshdm%2byzHJrrMFlWGt7c%2fnZStdcLNdsBIM%2b9Q%3d%3d | unknown | — | — | whitelisted |
5512 | svchost.exe | HEAD | 200 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1727399903&P2=404&P3=2&P4=hXxXPIDPV3rIdvkXJJ2aa85Sk3hTVBGv5airxPvHMpTjxW9S5bshdm%2byzHJrrMFlWGt7c%2fnZStdcLNdsBIM%2b9Q%3d%3d | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7072 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5512 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1727399903&P2=404&P3=2&P4=hXxXPIDPV3rIdvkXJJ2aa85Sk3hTVBGv5airxPvHMpTjxW9S5bshdm%2byzHJrrMFlWGt7c%2fnZStdcLNdsBIM%2b9Q%3d%3d | unknown | — | — | whitelisted |
5512 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1727399903&P2=404&P3=2&P4=hXxXPIDPV3rIdvkXJJ2aa85Sk3hTVBGv5airxPvHMpTjxW9S5bshdm%2byzHJrrMFlWGt7c%2fnZStdcLNdsBIM%2b9Q%3d%3d | unknown | — | — | whitelisted |
5512 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ea79963f-51af-4930-ab74-50e807a8950b?P1=1727399903&P2=404&P3=2&P4=hXxXPIDPV3rIdvkXJJ2aa85Sk3hTVBGv5airxPvHMpTjxW9S5bshdm%2byzHJrrMFlWGt7c%2fnZStdcLNdsBIM%2b9Q%3d%3d | unknown | — | — | whitelisted |
5512 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/781d3be2-1fde-42a1-acd7-583bc34d9d2f?P1=1727399903&P2=404&P3=2&P4=ns94zn%2b%2baz1WdYJ250%2bqKTsTPgu4T8UrWkGq8%2fNSUsaqz2H1GVFB1cP%2bWwSJUFiLDdl%2baZ28%2bFCJ9qTY7e4wmg%3d%3d | unknown | — | — | whitelisted |
5512 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/781d3be2-1fde-42a1-acd7-583bc34d9d2f?P1=1727399903&P2=404&P3=2&P4=ns94zn%2b%2baz1WdYJ250%2bqKTsTPgu4T8UrWkGq8%2fNSUsaqz2H1GVFB1cP%2bWwSJUFiLDdl%2baZ28%2bFCJ9qTY7e4wmg%3d%3d | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
740 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6652 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7072 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7072 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3584 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to connect to TLS FireBase Storage |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
7524 | MSBuild.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
7524 | MSBuild.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1 ETPRO signatures available at the full report