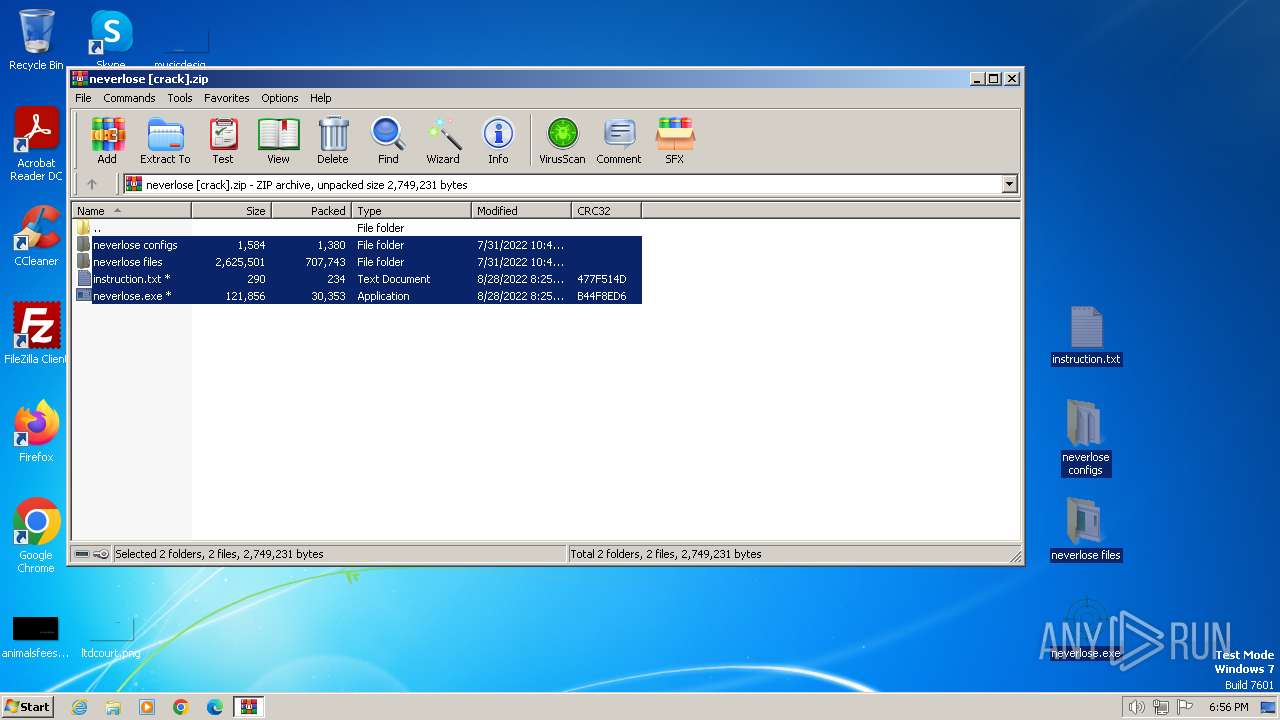
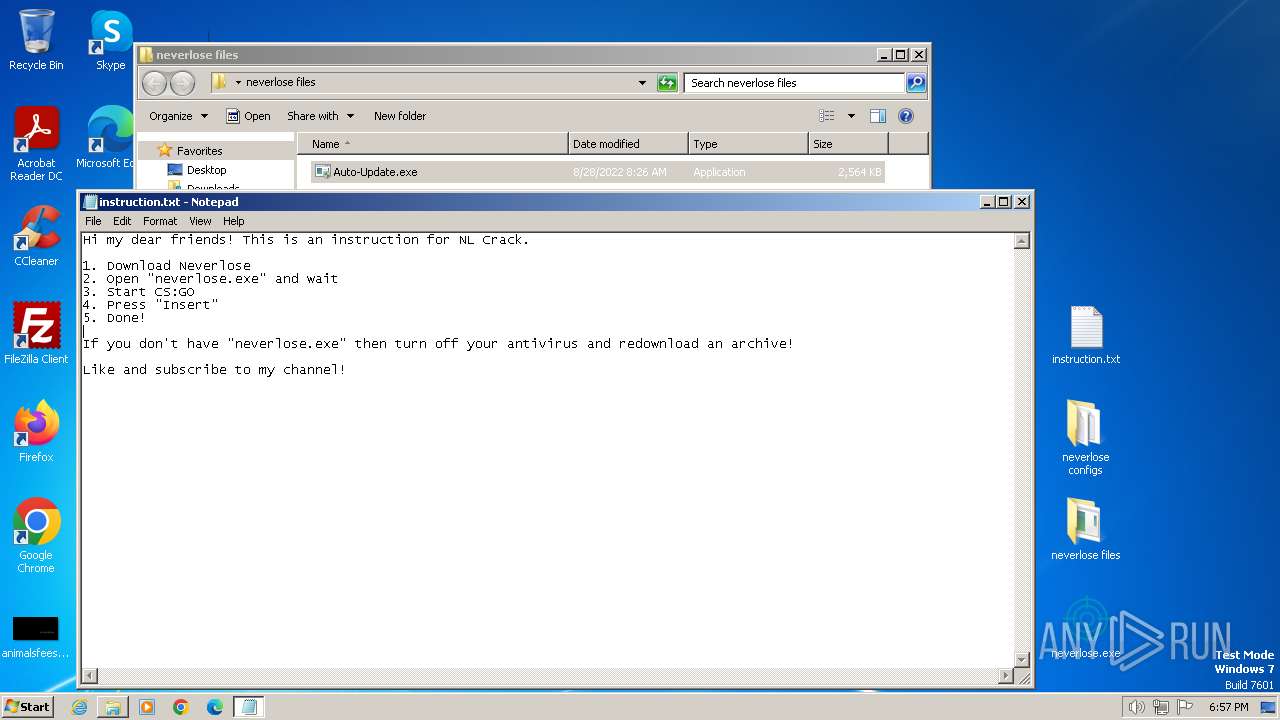
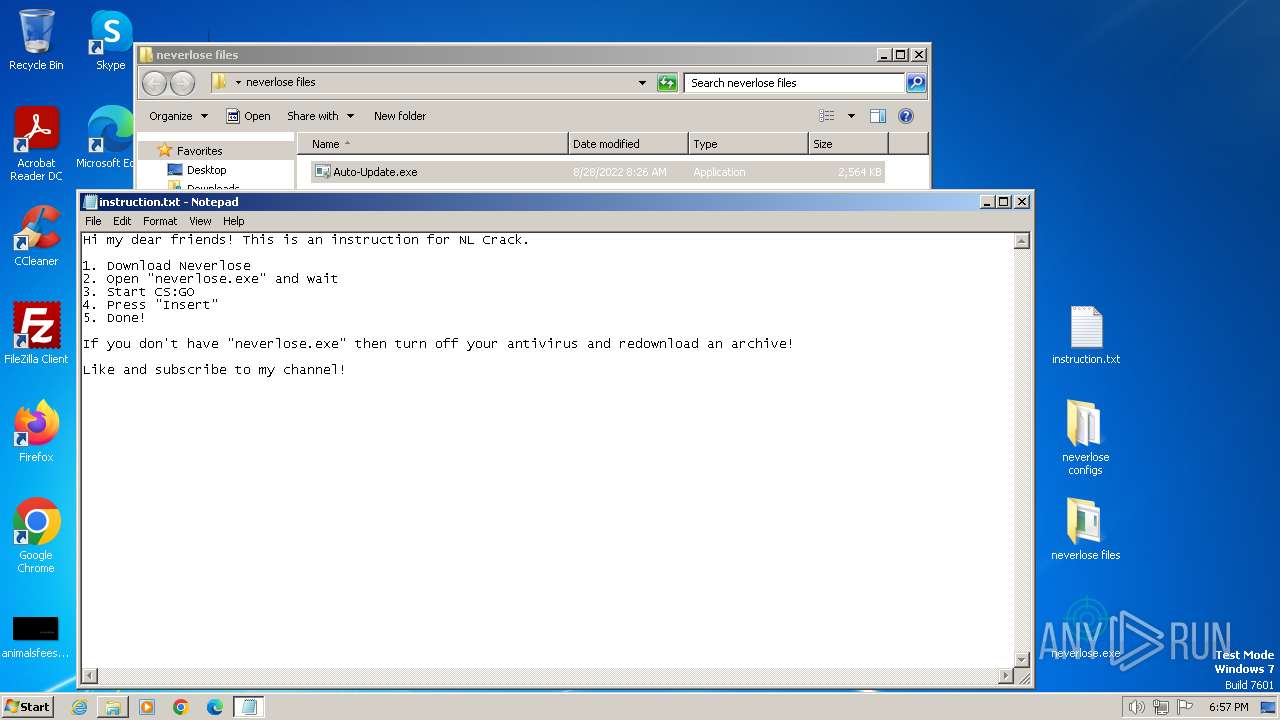
| File name: | neverlose [crack].zip |
| Full analysis: | https://app.any.run/tasks/9d889ce1-0aa5-46a8-bae5-606b5da01904 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | March 09, 2024, 18:56:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | E9BD3013D722C04894F09C263859A167 |
| SHA1: | 4B634DF91C84A7D34FCF5428AC8559172B1641E1 |
| SHA256: | 5D97C7165EBF81E693B1DFB82EB5747BBE48395A695114705601FF0D93205C6C |
| SSDEEP: | 24576:bEpgizU3/Ef8PM7LYCRR/kthNrWEuJRloPIXwv2ap7czjAdfu88TjYV3GtF:bEpgizU3/Ef807LYCRR/kthNrWEuJRlL |
MALICIOUS
REDLINE has been detected (YARA)
- AppLaunch.exe (PID: 195396)
SUSPICIOUS
Adds/modifies Windows certificates
- neverlose.exe (PID: 2636)
Reads the Internet Settings
- neverlose.exe (PID: 2636)
Reads settings of System Certificates
- neverlose.exe (PID: 2636)
Reads security settings of Internet Explorer
- neverlose.exe (PID: 2636)
Connects to unusual port
- AppLaunch.exe (PID: 195396)
INFO
Manual execution by a user
- neverlose.exe (PID: 2636)
- Auto-Update.exe (PID: 2064)
- Auto-Update.exe (PID: 1560)
- notepad.exe (PID: 195452)
- notepad.exe (PID: 35944)
Reads the machine GUID from the registry
- neverlose.exe (PID: 2636)
- AppLaunch.exe (PID: 195396)
Checks supported languages
- neverlose.exe (PID: 2636)
- Auto-Update.exe (PID: 1560)
- AppLaunch.exe (PID: 195396)
Reads the computer name
- neverlose.exe (PID: 2636)
- AppLaunch.exe (PID: 195396)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3672)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3672)
Reads the software policy settings
- neverlose.exe (PID: 2636)
Create files in a temporary directory
- neverlose.exe (PID: 2636)
Reads Environment values
- neverlose.exe (PID: 2636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(195396) AppLaunch.exe
C2 (1)62.204.41.141:24758
Botnet@dwqmosh
Options
ErrorMessageError: DirectX
Keys
XorGrislier
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:07:31 12:42:26 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | neverlose files/ |
Total processes
51
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1560 | "C:\Users\admin\Desktop\neverlose files\Auto-Update.exe" | C:\Users\admin\Desktop\neverlose files\Auto-Update.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\Desktop\neverlose files\Auto-Update.exe" | C:\Users\admin\Desktop\neverlose files\Auto-Update.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2636 | "C:\Users\admin\Desktop\neverlose.exe" | C:\Users\admin\Desktop\neverlose.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 6.6.6.6 Modules
| |||||||||||||||
| 3672 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\neverlose [crack].zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 35944 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\instruction.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 195396 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | Auto-Update.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
RedLine(PID) Process(195396) AppLaunch.exe C2 (1)62.204.41.141:24758 Botnet@dwqmosh Options ErrorMessageError: DirectX Keys XorGrislier | |||||||||||||||
| 195452 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\instruction.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
9 616
Read events
9 548
Write events
63
Delete events
5
Modification events
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\neverlose [crack].zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3672.8927\neverlose configs\hvh-blue.cfg.txt | text | |
MD5:AE827469B92E852D276DA1802AB46925 | SHA256:0200CBFC6E4CAA3B356AF34F12BBDAE6BCCE315EA67DF1AF5D5C3A6A26C6CB0C | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3672.8927\neverlose configs\wenzo-semirage.cfg.txt | text | |
MD5:2938B3F5101ECD9BE54F0F0A0479B3B8 | SHA256:660805E60DFDE3D939A8F0E21999DBBAD0F5E6DC715691901BCA8C1FCC5F1CB7 | |||
| 2636 | neverlose.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:DE0DD450F062D2D3E47AF18F6D5BD245 | SHA256:C2A6868055E69E8964BF95A349CDACDA51CF3B115A61AB071520FFCC7CBF6844 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3672.8927\neverlose.exe | executable | |
MD5:400D6A22A9A537D1478AE7F0AD06D2A2 | SHA256:42CE6778EB502B202EF32C613DE63593235E84A52205E272A1C736E7023F1BE6 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3672.8927\neverlose configs\KuCJloTa_Rage.cfg.txt | text | |
MD5:843D8125681737405AD732845FB6D3C0 | SHA256:CBBFF6F262CC87B0D2B7EB3F7B48577D9F6D843456737FCEDE8081E14A469570 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3672.8927\neverlose files\Auto-Update.exe | executable | |
MD5:3B79BEAC84E1AD501995B6AC9751A5F3 | SHA256:C59CA9813B70A01DB508B91E69DA06CEEDB2BA7FD49244AD5A7ED9F4ECEA0C42 | |||
| 2636 | neverlose.exe | C:\Users\admin\AppData\Local\Temp\Cab482F.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 2636 | neverlose.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 2636 | neverlose.exe | C:\Users\admin\AppData\Local\Temp\Tar4830.tmp | binary | |
MD5:DD73CEAD4B93366CF3465C8CD32E2796 | SHA256:A6752B7851B591550E4625B832A393AABCC428DE18D83E8593CD540F7D7CAE22 | |||
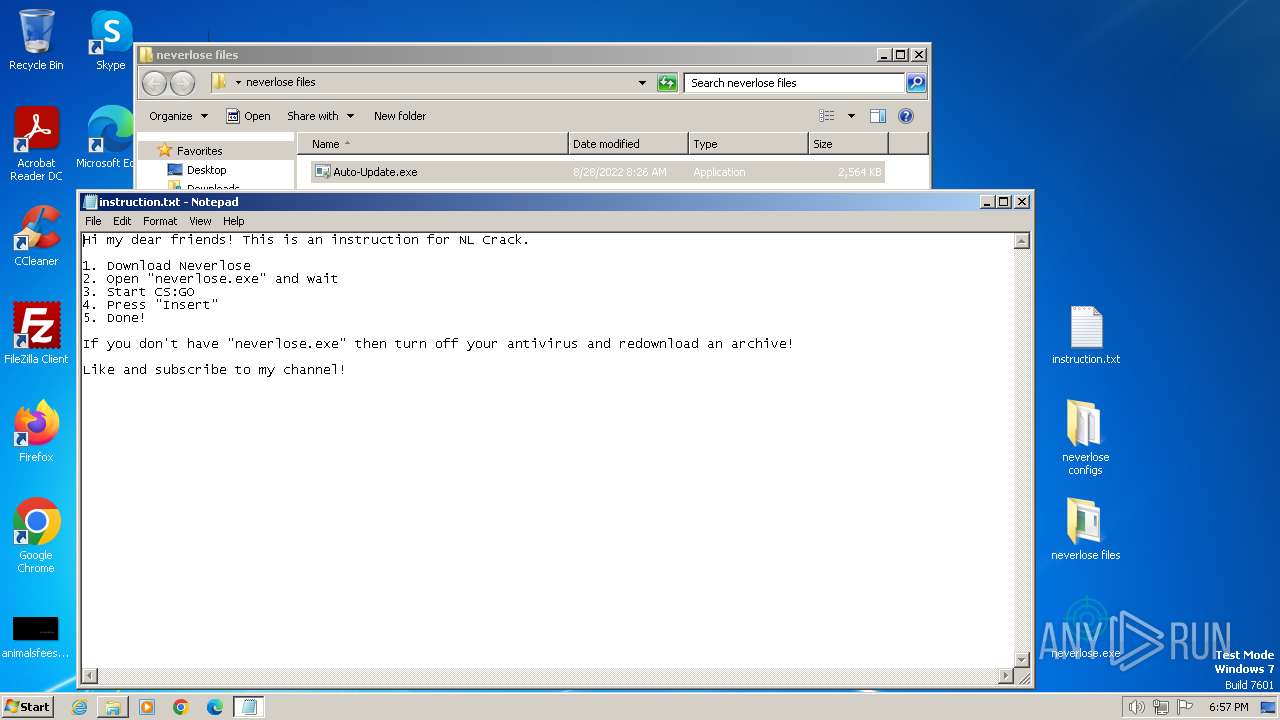
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3672.8927\instruction.txt | text | |
MD5:159691165E2A588E34CA69ABA17EFA32 | SHA256:473F446B2CBD55655D43131A98A4BA69EA2942396F67D72C4FF86F2B04F3D17C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
9
DNS requests
3
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2636 | neverlose.exe | GET | 200 | 173.222.108.226:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e9668845e7527770 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2636 | neverlose.exe | 104.21.69.65:443 | ipapi.co | CLOUDFLARENET | — | unknown |
2636 | neverlose.exe | 173.222.108.226:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
2636 | neverlose.exe | 162.159.134.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
195396 | AppLaunch.exe | 62.204.41.141:24758 | — | Horizon LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ipapi.co |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
cdn.discordapp.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup Domain (ipapi .co in DNS lookup) |
1080 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2636 | neverlose.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2636 | neverlose.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |