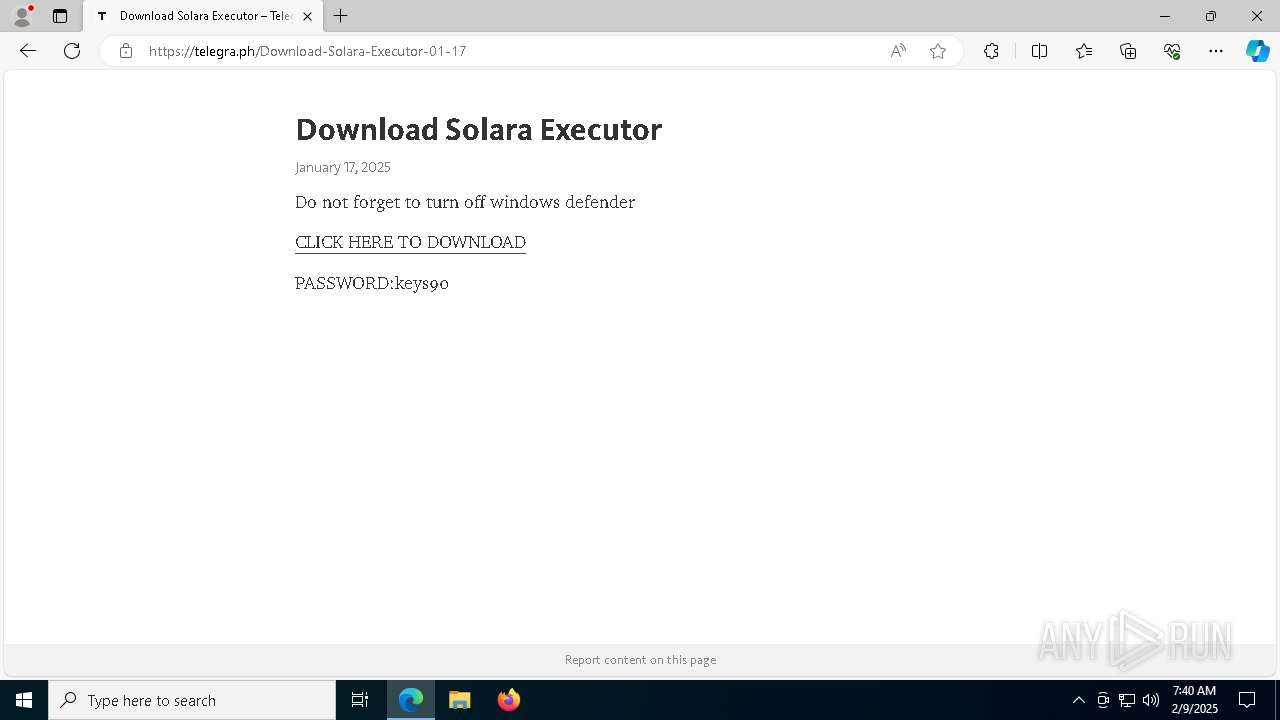
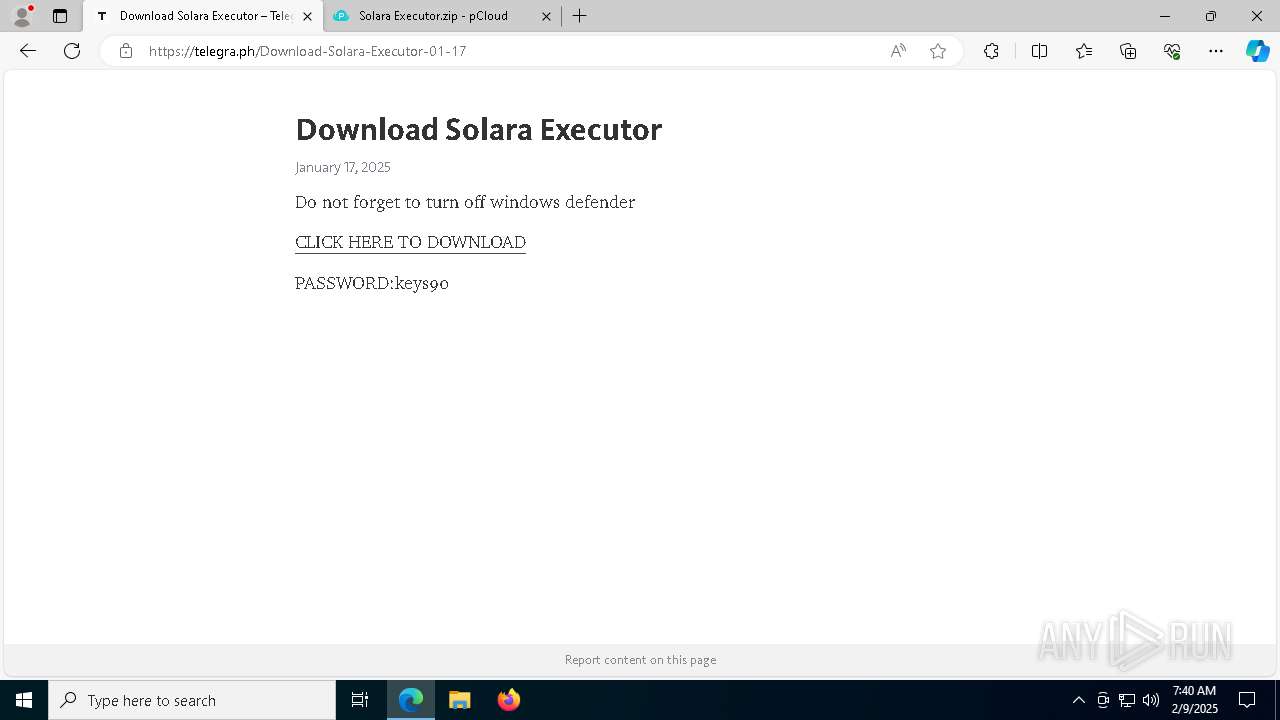
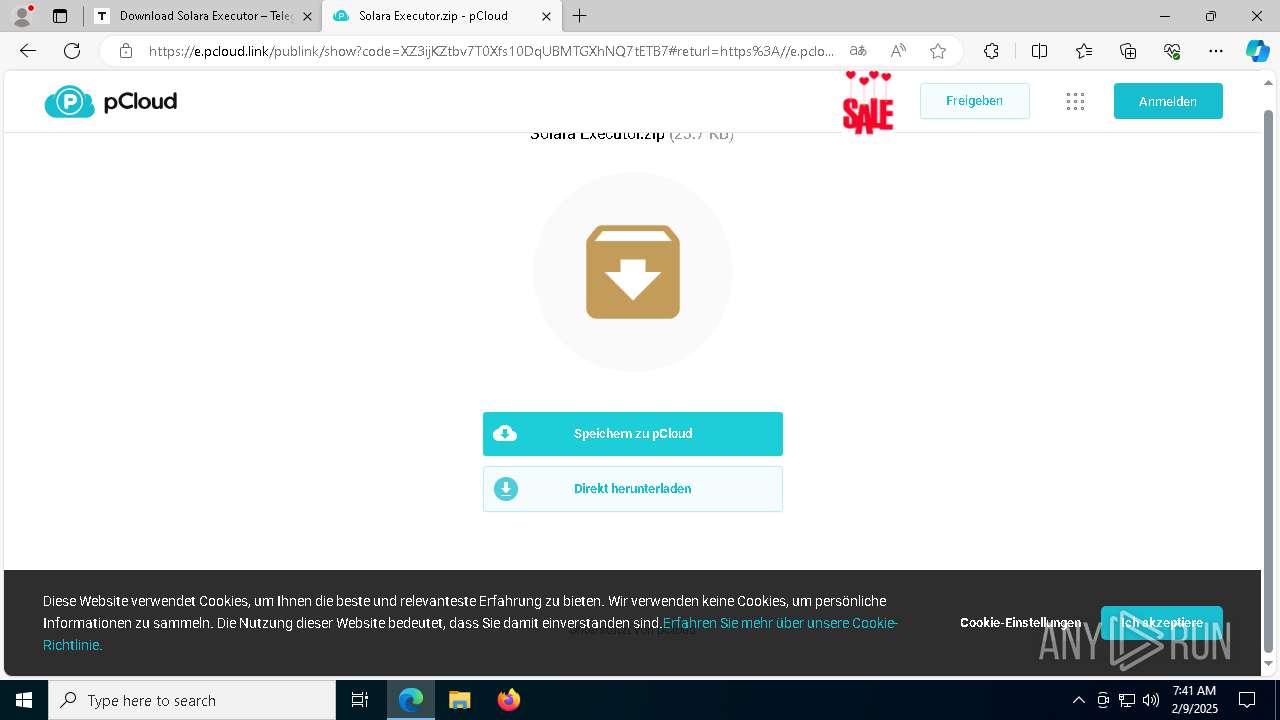
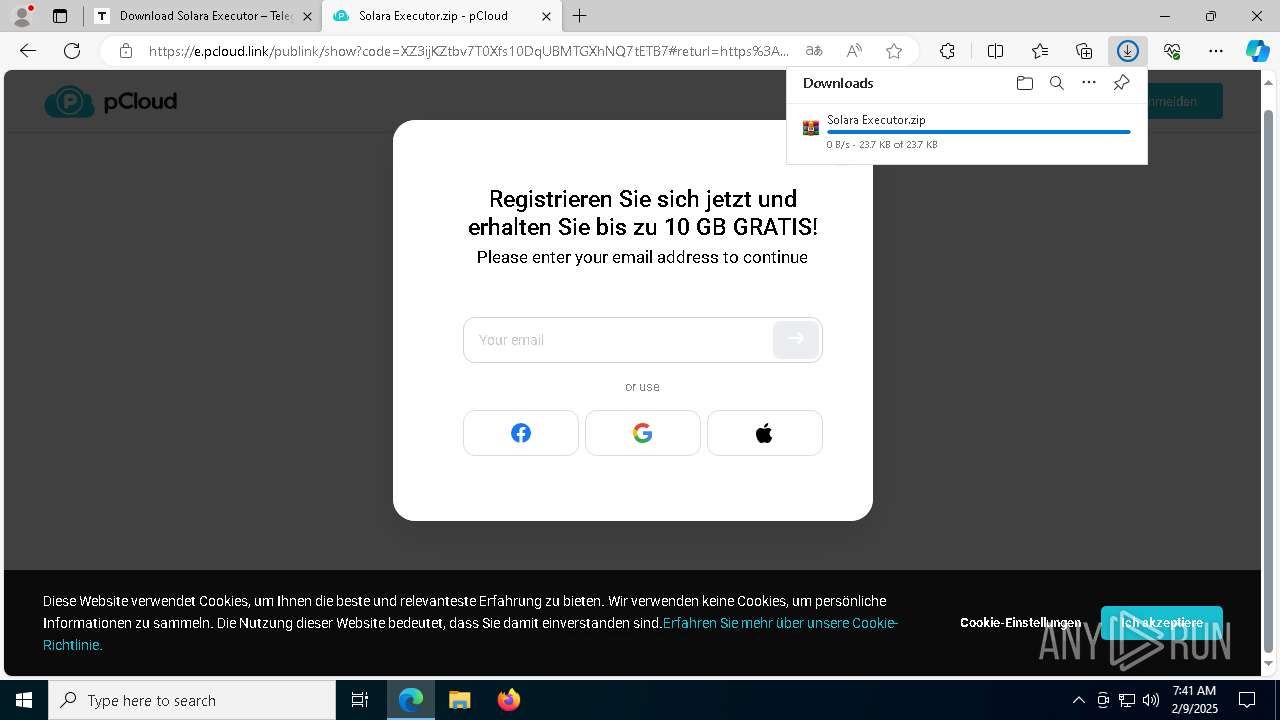
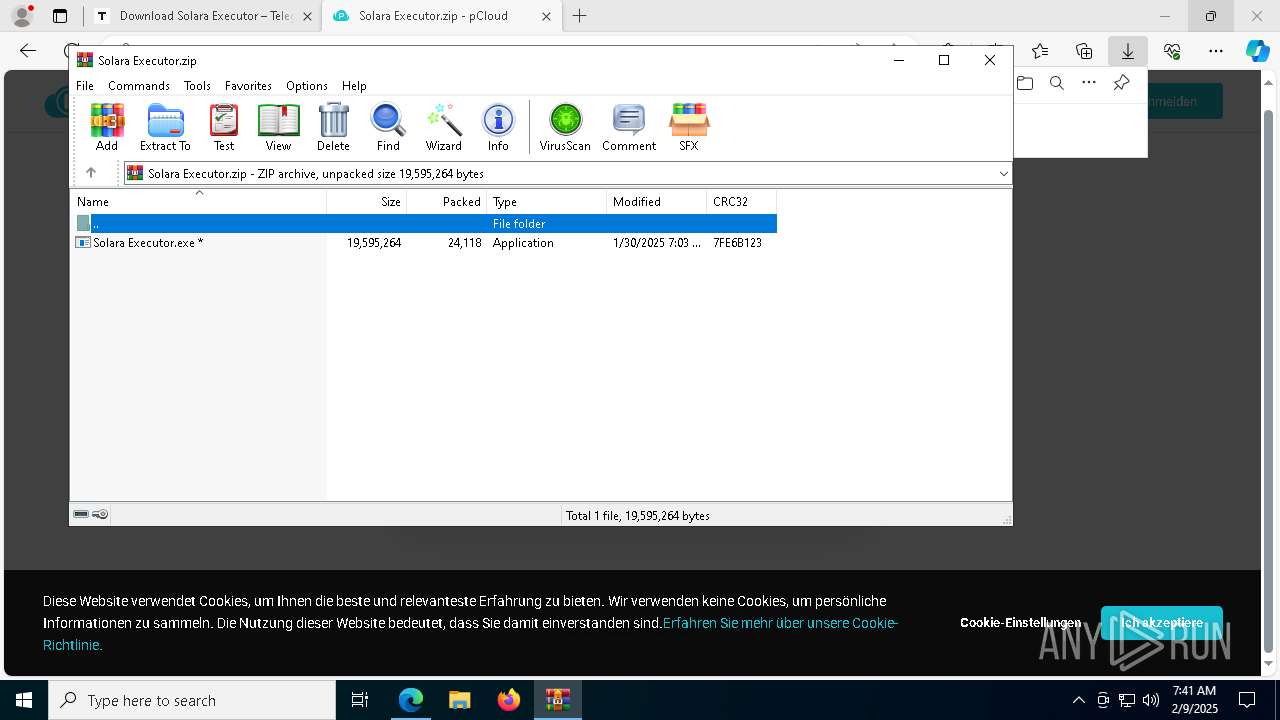
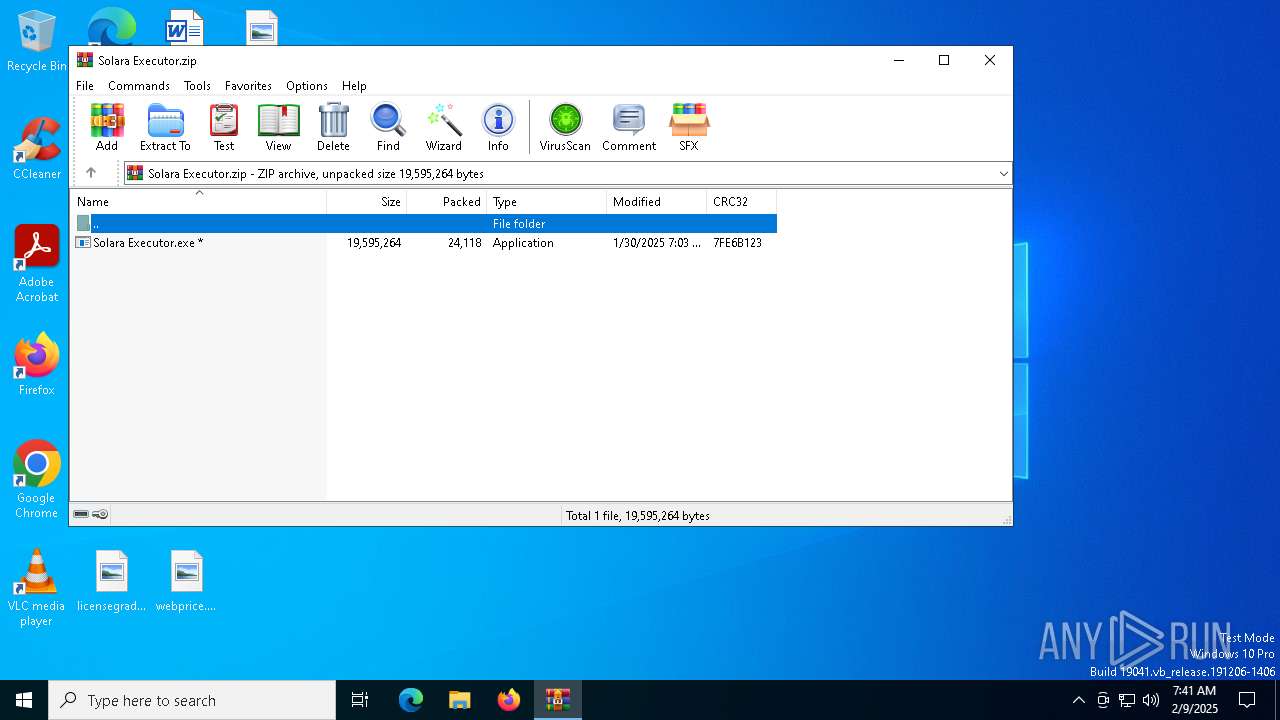
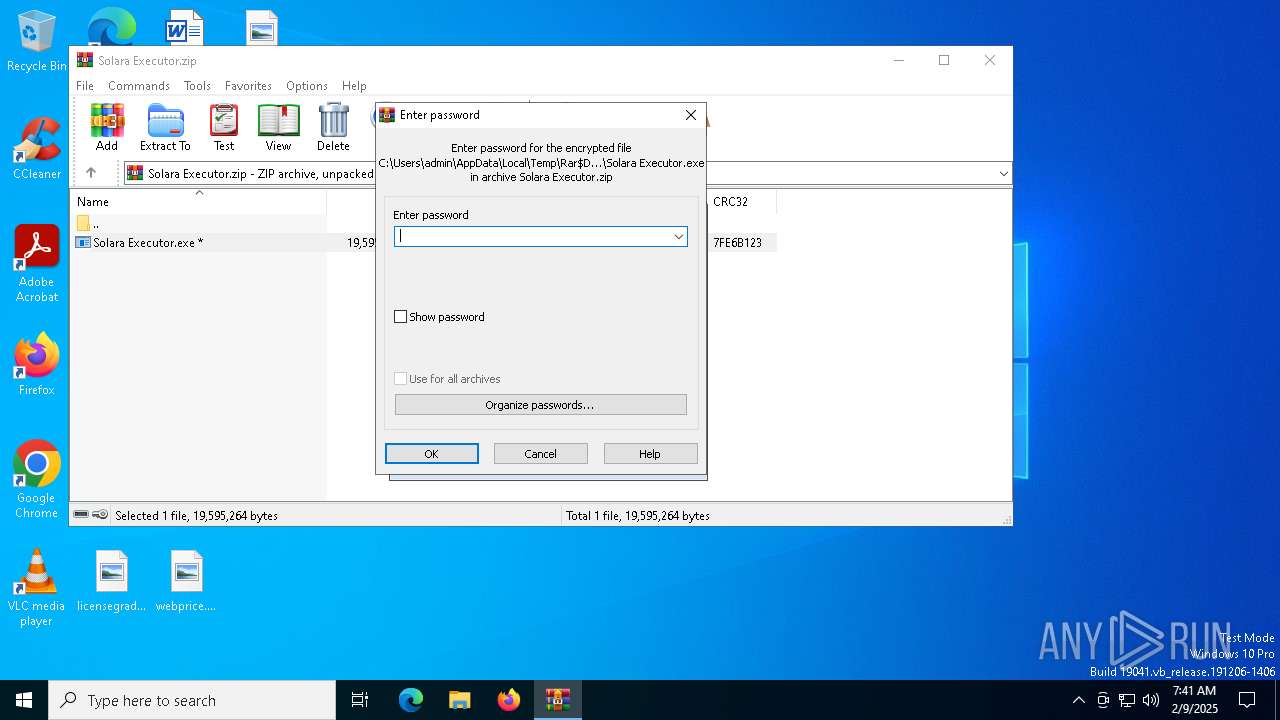
| URL: | https://menlichme.github.io/Roblox-Solara/ |
| Full analysis: | https://app.any.run/tasks/5ba2147b-e51f-42fd-880f-3b8f49370ab6 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | February 09, 2025, 07:40:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BA3E3B9104B442AB4104CC322379C3F8 |
| SHA1: | 2E5ABEA8C6C8DB53145C0A866E85FBF0C2A35CA7 |
| SHA256: | 5CC59F2159A34DA27A621D45DC09997DA5F9A6809263514A38E48797305C4E73 |
| SSDEEP: | 3:N8eapPEIKktKJEUKn:2eiEUtSO |
MALICIOUS
QUASAR has been found (auto)
- WinRAR.exe (PID: 5640)
Adds path to the Windows Defender exclusion list
- Solara Executor.exe (PID: 7920)
- Solara Executor.exe (PID: 5212)
Uses Task Scheduler to autorun other applications
- Client.exe (PID: 2132)
- shiiznmefk.exe (PID: 5880)
QUASAR has been detected (SURICATA)
- Client.exe (PID: 2132)
QUASAR has been detected (YARA)
- Client.exe (PID: 2132)
SUSPICIOUS
Reads security settings of Internet Explorer
- Solara Executor.exe (PID: 5544)
- Solara Executor.exe (PID: 7920)
- Solara Executor.exe (PID: 6684)
- Solara Executor.exe (PID: 5212)
Starts POWERSHELL.EXE for commands execution
- Solara Executor.exe (PID: 7920)
- Solara Executor.exe (PID: 5212)
Application launched itself
- Solara Executor.exe (PID: 5544)
- Solara Executor.exe (PID: 6684)
Script adds exclusion path to Windows Defender
- Solara Executor.exe (PID: 7920)
- Solara Executor.exe (PID: 5212)
Executable content was dropped or overwritten
- Solara Executor.exe (PID: 7920)
- shiiznmefk.exe (PID: 5880)
- Solara Executor.exe (PID: 5212)
Connects to unusual port
- Client.exe (PID: 2132)
Checks for external IP
- svchost.exe (PID: 2192)
Contacting a server suspected of hosting an CnC
- Client.exe (PID: 2132)
There is functionality for taking screenshot (YARA)
- Client.exe (PID: 2132)
Starts itself from another location
- shiiznmefk.exe (PID: 5880)
INFO
Checks supported languages
- identity_helper.exe (PID: 7880)
- identity_helper.exe (PID: 8060)
- Solara Executor.exe (PID: 5544)
- Solara Executor.exe (PID: 7920)
- shiiznmefk.exe (PID: 5880)
- Client.exe (PID: 2132)
- Solara Executor.exe (PID: 6684)
- Solara Executor.exe (PID: 5212)
- jzbxxone.exe (PID: 8168)
Application launched itself
- msedge.exe (PID: 6480)
- msedge.exe (PID: 6088)
Reads the computer name
- identity_helper.exe (PID: 7880)
- identity_helper.exe (PID: 8060)
- Solara Executor.exe (PID: 7920)
- Solara Executor.exe (PID: 5544)
- shiiznmefk.exe (PID: 5880)
- Client.exe (PID: 2132)
- Solara Executor.exe (PID: 6684)
- Solara Executor.exe (PID: 5212)
- jzbxxone.exe (PID: 8168)
Reads Environment values
- identity_helper.exe (PID: 7880)
- identity_helper.exe (PID: 8060)
- shiiznmefk.exe (PID: 5880)
- Client.exe (PID: 2132)
- jzbxxone.exe (PID: 8168)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6480)
Manual execution by a user
- Solara Executor.exe (PID: 5544)
- Solara Executor.exe (PID: 6684)
Process checks computer location settings
- Solara Executor.exe (PID: 5544)
- Solara Executor.exe (PID: 7920)
- Solara Executor.exe (PID: 6684)
- Solara Executor.exe (PID: 5212)
Checks proxy server information
- Solara Executor.exe (PID: 7920)
- Client.exe (PID: 2132)
- Solara Executor.exe (PID: 5212)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7200)
- powershell.exe (PID: 1572)
Reads the machine GUID from the registry
- Solara Executor.exe (PID: 7920)
- shiiznmefk.exe (PID: 5880)
- Client.exe (PID: 2132)
- Solara Executor.exe (PID: 5212)
- jzbxxone.exe (PID: 8168)
Disables trace logs
- Solara Executor.exe (PID: 7920)
- Client.exe (PID: 2132)
- Solara Executor.exe (PID: 5212)
Reads the software policy settings
- Solara Executor.exe (PID: 7920)
- Client.exe (PID: 2132)
- Solara Executor.exe (PID: 5212)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7200)
- powershell.exe (PID: 1572)
Creates files or folders in the user directory
- shiiznmefk.exe (PID: 5880)
Detects Fody packer (YARA)
- Client.exe (PID: 2132)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(2132) Client.exe
Version1.4.1
C2 (2)87.228.57.81:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex47b71fc0-b2c4-4112-b97a-39385a5399c1
Startupsvhost32
Tagsvhost32
LogDirLogs
SignatureSSSXaR44GRb6RYmfFpZjNvvxDEF0KI5jH8nAxi6KcQzCkmdFj4EmiNa7wzIn6QlTh6m9p8r0dvOdGcKp9R7a0feJ+9nftufivecVEcRMW+w9A0X3vAKDbhMDGoJK/oCpkIWanwn5htUKhAJB1lNPjwjIbjG59Xr7nQuXbI0zG8R5zUBqkB7LcDn23y9ViJS55kXsDdCMrrrzn3PsDzs0HTUE4E9W1OuqLpiq9ipYZce25NDQPlIfeAVgyRYzjvec4Uu1mthPaSYUvBiWdDBx5a+gN5tH6ZXROlVMsEMnIJhg...
CertificateMIIE9jCCAt6gAwIBAgIQAMCIrkV3lAMp6Vz+9SYptTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFQaGFudG9tIFNlcnZlciBDQTAgFw0yNTAxMjQxNzU0MjFaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRUGhhbnRvbSBTZXJ2ZXIgQ0EwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCLqDcacB918PiS52/zK8NuYRFBjeeZXbEfkolana8gflQhGUIyaXW73olgd952Z18rz4CB...
Total processes
215
Monitored processes
82
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5512 --field-trial-handle=2372,i,11515124810322987021,3277254331519777190,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 644 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5500 --field-trial-handle=2372,i,11515124810322987021,3277254331519777190,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1156 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2368 --field-trial-handle=2372,i,11515124810322987021,3277254331519777190,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1572 | "powershell.exe" -Command Add-MpPreference -ExclusionPath 'C:\yksmqge' | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | Solara Executor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1916 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Solara Executor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | shiiznmefk.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Quasar Client Version: 1.4.1 Modules
Quasar(PID) Process(2132) Client.exe Version1.4.1 C2 (2)87.228.57.81:4782 Sub_DirSubDir Install_NameClient.exe Mutex47b71fc0-b2c4-4112-b97a-39385a5399c1 Startupsvhost32 Tagsvhost32 LogDirLogs SignatureSSSXaR44GRb6RYmfFpZjNvvxDEF0KI5jH8nAxi6KcQzCkmdFj4EmiNa7wzIn6QlTh6m9p8r0dvOdGcKp9R7a0feJ+9nftufivecVEcRMW+w9A0X3vAKDbhMDGoJK/oCpkIWanwn5htUKhAJB1lNPjwjIbjG59Xr7nQuXbI0zG8R5zUBqkB7LcDn23y9ViJS55kXsDdCMrrrzn3PsDzs0HTUE4E9W1OuqLpiq9ipYZce25NDQPlIfeAVgyRYzjvec4Uu1mthPaSYUvBiWdDBx5a+gN5tH6ZXROlVMsEMnIJhg... CertificateMIIE9jCCAt6gAwIBAgIQAMCIrkV3lAMp6Vz+9SYptTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFQaGFudG9tIFNlcnZlciBDQTAgFw0yNTAxMjQxNzU0MjFaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRUGhhbnRvbSBTZXJ2ZXIgQ0EwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCLqDcacB918PiS52/zK8NuYRFBjeeZXbEfkolana8gflQhGUIyaXW73olgd952Z18rz4CB... | |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3880 --field-trial-handle=2372,i,11515124810322987021,3277254331519777190,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3128 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6372 --field-trial-handle=2312,i,7856592079478628679,10983482938979625353,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3620 --field-trial-handle=2372,i,11515124810322987021,3277254331519777190,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
28 694
Read events
28 611
Write events
83
Delete events
0
Modification events
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8BAC10FD468C2F00 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 842920FD468C2F00 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328426 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D84D9A2A-2A95-4F8B-BD86-D6FDA65B7954} | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 6E2167FD468C2F00 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\Profiles |
| Operation: | write | Name: | EnhancedLinkOpeningDefault |
Value: Default | |||
Executable files
17
Suspicious files
366
Text files
84
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF13574b.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13576a.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF13577a.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13576a.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13576a.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
105
DNS requests
103
Threats
44
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6424 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5536 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6972 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1739286601&P2=404&P3=2&P4=kvgB1sVDXQBTv8uRQ64mWBkydaw1Ou2ZXj%2fc%2fXrEZ252Od8kuRKeaMcCBV0aJWTxKkfp319gddrXozgCE4aqSQ%3d%3d | unknown | — | — | whitelisted |
5536 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6972 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1739286601&P2=404&P3=2&P4=kvgB1sVDXQBTv8uRQ64mWBkydaw1Ou2ZXj%2fc%2fXrEZ252Od8kuRKeaMcCBV0aJWTxKkfp319gddrXozgCE4aqSQ%3d%3d | unknown | — | — | whitelisted |
6972 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1739286601&P2=404&P3=2&P4=kvgB1sVDXQBTv8uRQ64mWBkydaw1Ou2ZXj%2fc%2fXrEZ252Od8kuRKeaMcCBV0aJWTxKkfp319gddrXozgCE4aqSQ%3d%3d | unknown | — | — | whitelisted |
6972 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e30939f9-8764-4977-9b5d-f865df373b71?P1=1739286603&P2=404&P3=2&P4=mzurvu9iW4pqBdj9zz5aW5okwGK4xTgLY%2fXFdPJTGHd3rcEFjHeCVFr8HeWD64UAAT834yvcBCDG3Jnbu9JUhw%3d%3d | unknown | — | — | whitelisted |
6972 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e30939f9-8764-4977-9b5d-f865df373b71?P1=1739286603&P2=404&P3=2&P4=mzurvu9iW4pqBdj9zz5aW5okwGK4xTgLY%2fXFdPJTGHd3rcEFjHeCVFr8HeWD64UAAT834yvcBCDG3Jnbu9JUhw%3d%3d | unknown | — | — | whitelisted |
6972 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e30939f9-8764-4977-9b5d-f865df373b71?P1=1739286603&P2=404&P3=2&P4=mzurvu9iW4pqBdj9zz5aW5okwGK4xTgLY%2fXFdPJTGHd3rcEFjHeCVFr8HeWD64UAAT834yvcBCDG3Jnbu9JUhw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6480 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6832 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6832 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6832 | msedge.exe | 142.250.186.131:443 | fonts.gstatic.com | — | — | whitelisted |
6832 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6832 | msedge.exe | 185.199.108.153:443 | menlichme.github.io | FASTLY | US | shared |
6832 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
menlichme.github.io |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6832 | msedge.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
6832 | msedge.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
6832 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed in DNS Lookup (pcloud .com) |
6832 | msedge.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed in DNS Lookup (pcloud .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
6832 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
6832 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
6832 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
6832 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
6832 | msedge.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |