| File name: | SecuriteInfo.com.Win32.Malware-gen.24050.20684 |
| Full analysis: | https://app.any.run/tasks/6ee52b55-ee2f-4be1-931f-c6ce6d203eb4 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 19, 2025, 03:56:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
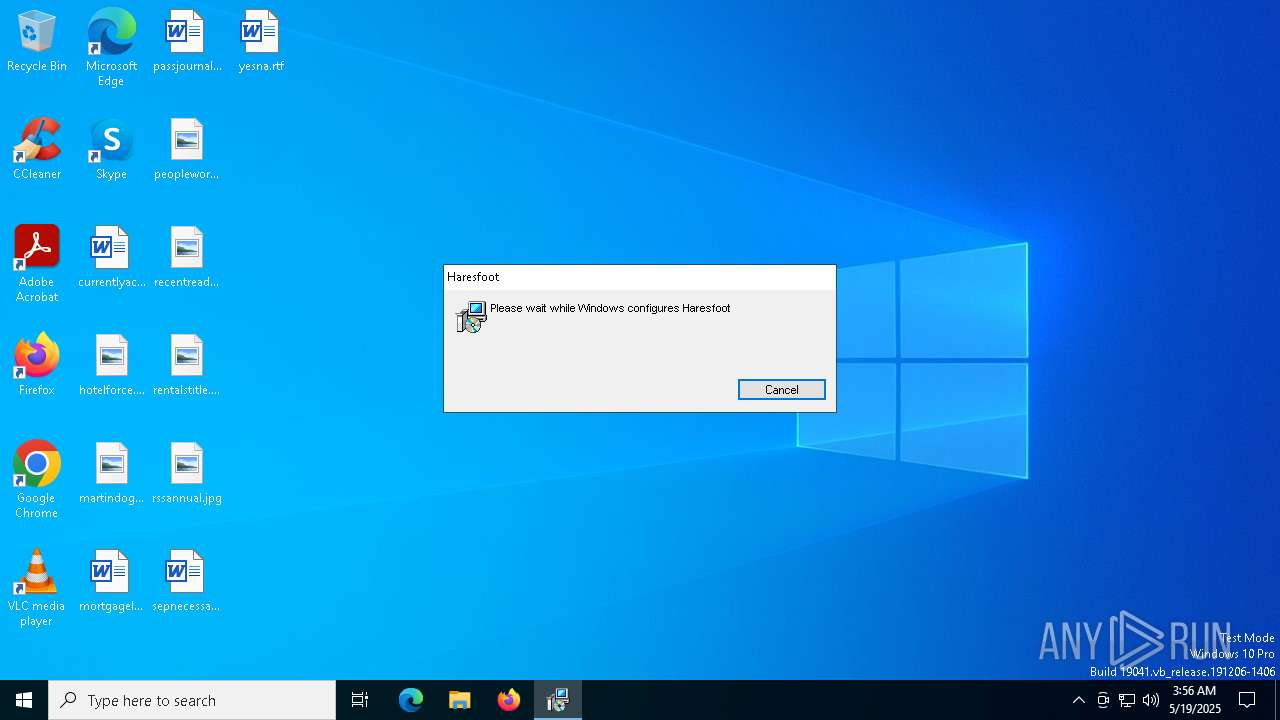
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Haresfoot, Author: Royal Sago, Keywords: Installer, Comments: This installer database contains the logic and data required to install Haresfoot., Template: Intel;1033, Revision Number: {71B4DCC1-8B49-48FD-91C3-056E1BABEE03}, Create Time/Date: Tue May 13 07:23:28 2025, Last Saved Time/Date: Tue May 13 07:23:28 2025, Number of Pages: 500, Number of Words: 10, Name of Creating Application: WiX Toolset (4.0.0.0), Security: 2 |
| MD5: | E84DB67F8F30CD4BA03A0C9E6952628B |
| SHA1: | C24C01CC464DB661EC5F5910411B7049793FC1E6 |
| SHA256: | 5CA4552216DDC3B276E3CF2684CC5041B31931181A54D5CB62113BF6AABA1575 |
| SSDEEP: | 98304:t7KltuUF/1KdhUj+Rt2URMTUOyV59Avpj31mvrBvSSRkYhYYzjOMrdBg5HJKxqi3:tu3aAt6twV7WIps |
MALICIOUS
Executing a file with an untrusted certificate
- SF32.exe (PID: 780)
- SF32.exe (PID: 5408)
- SF32.exe (PID: 5548)
- ISBEW64.exe (PID: 5400)
- ISBEW64.exe (PID: 2852)
- ISBEW64.exe (PID: 7968)
- ISBEW64.exe (PID: 8144)
- Hashrate_Vorte.exe (PID: 7208)
- Hashrate_Vorte.exe (PID: 720)
- Hashrate_Vorte.exe (PID: 4892)
- ISBEW64.exe (PID: 2984)
- ISBEW64.exe (PID: 6032)
- Hashrate_Vorte.exe (PID: 3888)
- ByteS.exe (PID: 7148)
- Hashrate_Vorte.exe (PID: 8136)
- Hashrate_Vorte.exe (PID: 668)
Known privilege escalation attack
- dllhost.exe (PID: 7544)
RHADAMANTHYS has been detected (YARA)
- svchost.exe (PID: 8060)
RHADAMANTHYS has been detected (SURICATA)
- svchost.exe (PID: 8060)
PURECRYPTER has been detected (SURICATA)
- ByteS.exe (PID: 7148)
Bypass execution policy to execute commands
- powershell.exe (PID: 7932)
AMADEY has been detected (SURICATA)
- ThrIndex.exe (PID: 7896)
Connects to the CnC server
- ThrIndex.exe (PID: 7896)
- AddInProcess.exe (PID: 4988)
MINER has been detected (SURICATA)
- AddInProcess.exe (PID: 4988)
ASYNCRAT has been detected (SURICATA)
- SScheduler.exe (PID: 6108)
Run PowerShell with an invisible window
- powershell.exe (PID: 7932)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- AdaptiveDisp.exe (PID: 7896)
Possibly patching Antimalware Scan Interface function (YARA)
- AdaptiveDisp.exe (PID: 7896)
Starts CMD.EXE for commands execution
- SF32.exe (PID: 5548)
- SF32.exe (PID: 780)
- Hashrate_Vorte.exe (PID: 3888)
- Hashrate_Vorte.exe (PID: 720)
- Hashrate_Vorte.exe (PID: 668)
Executable content was dropped or overwritten
- SF32.exe (PID: 780)
- SF32.exe (PID: 5408)
- svchost.exe (PID: 8060)
- Of7~.exe (PID: 7192)
- Of7~.exe (PID: 6072)
- Hashrate_Vorte.exe (PID: 7208)
- Hashrate_Vorte.exe (PID: 4892)
- Hashrate_Vorte.exe (PID: 720)
- Hashrate_Vorte.exe (PID: 3888)
- Hashrate_Vorte.exe (PID: 8136)
- Hashrate_Vorte.exe (PID: 668)
Starts itself from another location
- SF32.exe (PID: 5408)
- Of7~.exe (PID: 7192)
- Hashrate_Vorte.exe (PID: 7208)
- Hashrate_Vorte.exe (PID: 4892)
- Hashrate_Vorte.exe (PID: 8136)
Executes as Windows Service
- VSSVC.exe (PID: 7448)
Connects to unusual port
- svchost.exe (PID: 7976)
- svchost.exe (PID: 8060)
- ByteS.exe (PID: 7148)
- AddInProcess.exe (PID: 4988)
- SScheduler.exe (PID: 6108)
Multiple wallet extension IDs have been found
- svchost.exe (PID: 8060)
The process drops C-runtime libraries
- Of7~.exe (PID: 6072)
- Hashrate_Vorte.exe (PID: 7208)
- msiexec.exe (PID: 7388)
- Hashrate_Vorte.exe (PID: 4892)
- Hashrate_Vorte.exe (PID: 8136)
Process drops legitimate windows executable
- Of7~.exe (PID: 6072)
- Hashrate_Vorte.exe (PID: 7208)
- msiexec.exe (PID: 7388)
- Hashrate_Vorte.exe (PID: 4892)
- Hashrate_Vorte.exe (PID: 8136)
Starts a Microsoft application from unusual location
- Hashrate_Vorte.exe (PID: 7208)
Contacting a server suspected of hosting an CnC
- ByteS.exe (PID: 7148)
- ThrIndex.exe (PID: 7896)
- SScheduler.exe (PID: 6108)
The process executes via Task Scheduler
- powershell.exe (PID: 7932)
Connects to the server without a host name
- ThrIndex.exe (PID: 7896)
Potential Corporate Privacy Violation
- AddInProcess.exe (PID: 4988)
INFO
Compiled with Borland Delphi (YARA)
- SF32.exe (PID: 780)
The sample compiled with english language support
- SF32.exe (PID: 780)
- msiexec.exe (PID: 7388)
- SF32.exe (PID: 5408)
- msiexec.exe (PID: 7312)
- svchost.exe (PID: 8060)
- Of7~.exe (PID: 7192)
- Of7~.exe (PID: 6072)
- Hashrate_Vorte.exe (PID: 7208)
- Hashrate_Vorte.exe (PID: 720)
- Hashrate_Vorte.exe (PID: 4892)
- Hashrate_Vorte.exe (PID: 8136)
- Hashrate_Vorte.exe (PID: 668)
Checks supported languages
- msiexec.exe (PID: 7388)
Manages system restore points
- SrTasks.exe (PID: 720)
- SrTasks.exe (PID: 456)
- SrTasks.exe (PID: 7788)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7388)
Reads the computer name
- msiexec.exe (PID: 7388)
Application launched itself
- chrome.exe (PID: 5384)
- msedge.exe (PID: 7788)
- msedge.exe (PID: 7364)
- msedge.exe (PID: 5744)
Manual execution by a user
- msedge.exe (PID: 7788)
- AddInProcess.exe (PID: 4988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Haresfoot |
| Author: | Royal Sago |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Haresfoot. |
| Template: | Intel;1033 |
| RevisionNumber: | {71B4DCC1-8B49-48FD-91C3-056E1BABEE03} |
| CreateDate: | 2025:05:13 07:23:28 |
| ModifyDate: | 2025:05:13 07:23:28 |
| Pages: | 500 |
| Words: | 10 |
| Software: | WiX Toolset (4.0.0.0) |
| Security: | Read-only recommended |
Total processes
251
Monitored processes
106
Malicious processes
18
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AddInProcess.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1932 --field-trial-handle=1936,i,7426012092182709016,2149350859689924339,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 456 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:12 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5464 --field-trial-handle=2260,i,252249367225011317,15916974228722587920,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 668 | C:\ProgramData\WBFSystem_test\Hashrate_Vorte.exe | C:\ProgramData\WBFSystem_test\Hashrate_Vorte.exe | Hashrate_Vorte.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneNote Exit code: 0 Version: 14.0.4763.1000 Modules
| |||||||||||||||
| 680 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | SF32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x290,0x294,0x298,0x288,0x2a0,0x7ffc897e5fd8,0x7ffc897e5fe4,0x7ffc897e5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 720 | C:\ProgramData\uploadpluginid\Hashrate_Vorte.exe | C:\ProgramData\uploadpluginid\Hashrate_Vorte.exe | Hashrate_Vorte.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneNote Exit code: 0 Version: 14.0.4763.1000 Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5388 --field-trial-handle=2260,i,252249367225011317,15916974228722587920,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
30 088
Read events
29 242
Write events
788
Delete events
58
Modification events
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000007830F20372C8DB01DC1C0000081D0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000007830F20372C8DB01DC1C0000081D0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000005BB7390472C8DB01DC1C0000081D0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000005BB7390472C8DB01DC1C0000081D0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000601B3C0472C8DB01DC1C0000081D0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000024E2400472C8DB01DC1C0000081D0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000ADFAE20472C8DB01DC1C0000081D0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7388) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000695EE50472C8DB01DC1C0000A81D0000E803000001000000000000000000000044B3C1F6959A91488246422737B29E6400000000000000000000000000000000 | |||
| (PID) Process: | (7448) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000081A1F30472C8DB01181D0000381D0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
67
Suspicious files
362
Text files
115
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7388 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7388 | msiexec.exe | C:\Windows\Installer\10fd2e.msi | — | |
MD5:— | SHA256:— | |||
| 7388 | msiexec.exe | C:\Windows\Installer\10fd30.msi | — | |
MD5:— | SHA256:— | |||
| 7388 | msiexec.exe | C:\Users\admin\AppData\Local\Diphtheria\SF32.exe | executable | |
MD5:1F166F5C76EB155D44DD1BF160F37A6A | SHA256:2D13424B09BA004135A26CCD60B64CDD6917D80CE43070CBC114569EAE608588 | |||
| 7388 | msiexec.exe | C:\Windows\Temp\~DFA83645F63DBC3F56.TMP | binary | |
MD5:DA9EFCEE4943245BDDA330748C47E9D7 | SHA256:9027200374B6304276132049B384877F6CB40C799370938034E18FEAE8F3E108 | |||
| 7388 | msiexec.exe | C:\Users\admin\AppData\Local\Diphtheria\sqlite3.dll | executable | |
MD5:90ED24DFD07D01E63F0E78F2B3F5AB54 | SHA256:38042B5C4CD510F35E5D619FC8DE11B687C5ED935FFA209426937F47CD84E7D4 | |||
| 7388 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:DA9EFCEE4943245BDDA330748C47E9D7 | SHA256:9027200374B6304276132049B384877F6CB40C799370938034E18FEAE8F3E108 | |||
| 7388 | msiexec.exe | C:\Windows\Installer\MSIFE09.tmp | binary | |
MD5:CC62C7EA522DB4BBC1E875E88592CDBA | SHA256:8D6FF039687DB80B397C651CC8FA77C5D7162C8FBE3E8D23704FBE3BCFF38312 | |||
| 7388 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{f6c1b344-9a95-4891-8246-422737b29e64}_OnDiskSnapshotProp | binary | |
MD5:D7E1A2F6C0695D5738DD6DA2DA88DAB4 | SHA256:B9FA003C0E53F6FB05222014EC162D89D3062655BC603D6C7154D4E92C85608A | |||
| 7388 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:D7E1A2F6C0695D5738DD6DA2DA88DAB4 | SHA256:B9FA003C0E53F6FB05222014EC162D89D3062655BC603D6C7154D4E92C85608A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
92
DNS requests
72
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4696 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2800 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747702796&P2=404&P3=2&P4=HDwEu4f1OV0%2fZiz1vKKh0JIDd6hqDzATO9iQQ3g6dgZlQTakPYePzYLHP50xFpA8n9%2bukQdyFZO4mEEsF9GXkw%3d%3d | unknown | — | — | whitelisted |
2800 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747702796&P2=404&P3=2&P4=HDwEu4f1OV0%2fZiz1vKKh0JIDd6hqDzATO9iQQ3g6dgZlQTakPYePzYLHP50xFpA8n9%2bukQdyFZO4mEEsF9GXkw%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4696 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7896 | ThrIndex.exe | POST | 200 | 196.251.89.67:80 | http://196.251.89.67/Di0Her478/index.php | unknown | — | — | unknown |
2800 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747702796&P2=404&P3=2&P4=HDwEu4f1OV0%2fZiz1vKKh0JIDd6hqDzATO9iQQ3g6dgZlQTakPYePzYLHP50xFpA8n9%2bukQdyFZO4mEEsF9GXkw%3d%3d | unknown | — | — | whitelisted |
2800 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1747702796&P2=404&P3=2&P4=HDwEu4f1OV0%2fZiz1vKKh0JIDd6hqDzATO9iQQ3g6dgZlQTakPYePzYLHP50xFpA8n9%2bukQdyFZO4mEEsF9GXkw%3d%3d | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7976 | svchost.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 19 |
8060 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
8060 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
8060 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
8060 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
7148 | ByteS.exe | Malware Command and Control Activity Detected | LOADER [ANY.RUN] PureLoader Download Attempt (LOAD) |
7896 | ThrIndex.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 41 |
7896 | ThrIndex.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
4988 | AddInProcess.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
7896 | ThrIndex.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |