| File name: | Orden de compra.xlam |
| Full analysis: | https://app.any.run/tasks/15c07060-2d6d-4d98-9e37-d61de5b7cd66 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | July 25, 2024, 19:49:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 4590B84EFCAC4A9804D570F575246E27 |
| SHA1: | 82C7EBAA6F3D4E09C2BF6C2414E3664B90BB0E35 |
| SHA256: | 5C40CEEF86F84DAFD5702A066833B86C7A0067B20C8DADDFF80FF5E1018BA033 |
| SSDEEP: | 24576:ROhpoPmytX56Nlk+YYdnND39BLC0oHW+uv/kTFYGMhwvFLpKrIlN:kpoPmytX5Mk+YYdnND39BLC0oHW+uv/k |
MALICIOUS
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 2496)
Equation Editor starts application (likely CVE-2017-11882)
- EQNEDT32.EXE (PID: 2496)
Reads the value of a key from the registry (SCRIPT)
- wscript.exe (PID: 3512)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3540)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 3540)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 3540)
AGENTTESLA has been detected (YARA)
- AddInProcess32.exe (PID: 2276)
Steals credentials from Web Browsers
- AddInProcess32.exe (PID: 2276)
Actions looks like stealing of personal data
- AddInProcess32.exe (PID: 2276)
SUSPICIOUS
Reads security settings of Internet Explorer
- EQNEDT32.EXE (PID: 2496)
The process executes VB scripts
- EQNEDT32.EXE (PID: 2496)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 3512)
Reads the Internet Settings
- wscript.exe (PID: 3512)
- EQNEDT32.EXE (PID: 2496)
- powershell.exe (PID: 3540)
- AddInProcess32.exe (PID: 2276)
- sipnotify.exe (PID: 1524)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3512)
Suspicious use of symmetric encryption in PowerShell
- wscript.exe (PID: 3512)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 3512)
Cryptography encrypted command line is found
- powershell.exe (PID: 3540)
Access the System.Security .NET namespace (SCRIPT)
- wscript.exe (PID: 3512)
Base64-obfuscated command line is found
- wscript.exe (PID: 3512)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3540)
Connects to the server without a host name
- EQNEDT32.EXE (PID: 2496)
Contacting a server suspected of hosting an Exploit Kit
- powershell.exe (PID: 3540)
Payload loading activity detected
- powershell.exe (PID: 3540)
Checks for external IP
- AddInProcess32.exe (PID: 2276)
Connects to FTP
- AddInProcess32.exe (PID: 2276)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1388)
- sipnotify.exe (PID: 1524)
Accesses Microsoft Outlook profiles
- AddInProcess32.exe (PID: 2276)
Reads settings of System Certificates
- sipnotify.exe (PID: 1524)
INFO
Creates files or folders in the user directory
- EQNEDT32.EXE (PID: 2496)
Checks supported languages
- EQNEDT32.EXE (PID: 2496)
- AddInProcess32.exe (PID: 2276)
- IMEKLMG.EXE (PID: 2068)
- IMEKLMG.EXE (PID: 2060)
- wmpnscfg.exe (PID: 2348)
- wmpnscfg.exe (PID: 2368)
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 2496)
- AddInProcess32.exe (PID: 2276)
Checks proxy server information
- EQNEDT32.EXE (PID: 2496)
Reads the computer name
- EQNEDT32.EXE (PID: 2496)
- AddInProcess32.exe (PID: 2276)
- IMEKLMG.EXE (PID: 2060)
- IMEKLMG.EXE (PID: 2068)
- wmpnscfg.exe (PID: 2348)
- wmpnscfg.exe (PID: 2368)
Manual execution by a user
- EXCEL.EXE (PID: 3088)
- IMEKLMG.EXE (PID: 2060)
- wmpnscfg.exe (PID: 2348)
- IMEKLMG.EXE (PID: 2068)
- wmpnscfg.exe (PID: 2368)
Potential library load (Base64 Encoded 'LoadLibrary')
- powershell.exe (PID: 3540)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- powershell.exe (PID: 3540)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3540)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- powershell.exe (PID: 3540)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- powershell.exe (PID: 3540)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 3540)
Disables trace logs
- powershell.exe (PID: 3540)
- AddInProcess32.exe (PID: 2276)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- powershell.exe (PID: 3540)
Potential modification of remote process state (Base64 Encoded 'SetThreadContext')
- powershell.exe (PID: 3540)
Reads Environment values
- AddInProcess32.exe (PID: 2276)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2068)
- IMEKLMG.EXE (PID: 2060)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1524)
Reads the software policy settings
- sipnotify.exe (PID: 1524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:25 16:21:16 |
| ZipCRC: | 0x0356e658 |
| ZipCompressedSize: | 395 |
| ZipUncompressedSize: | 1341 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | USER |
|---|
XML
| LastModifiedBy: | USER |
|---|---|
| CreateDate: | 2023:08:03 11:34:29Z |
| ModifyDate: | 2023:08:03 11:37:28Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Sheet1 |
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16.03 |
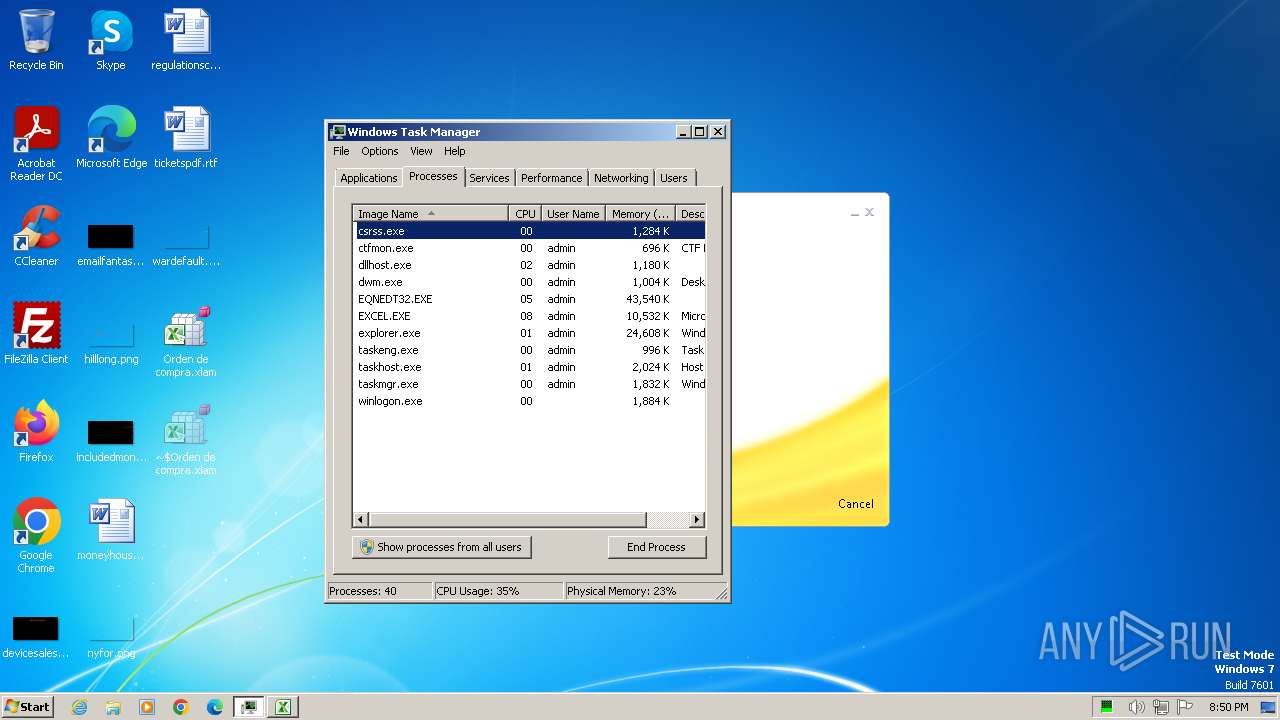
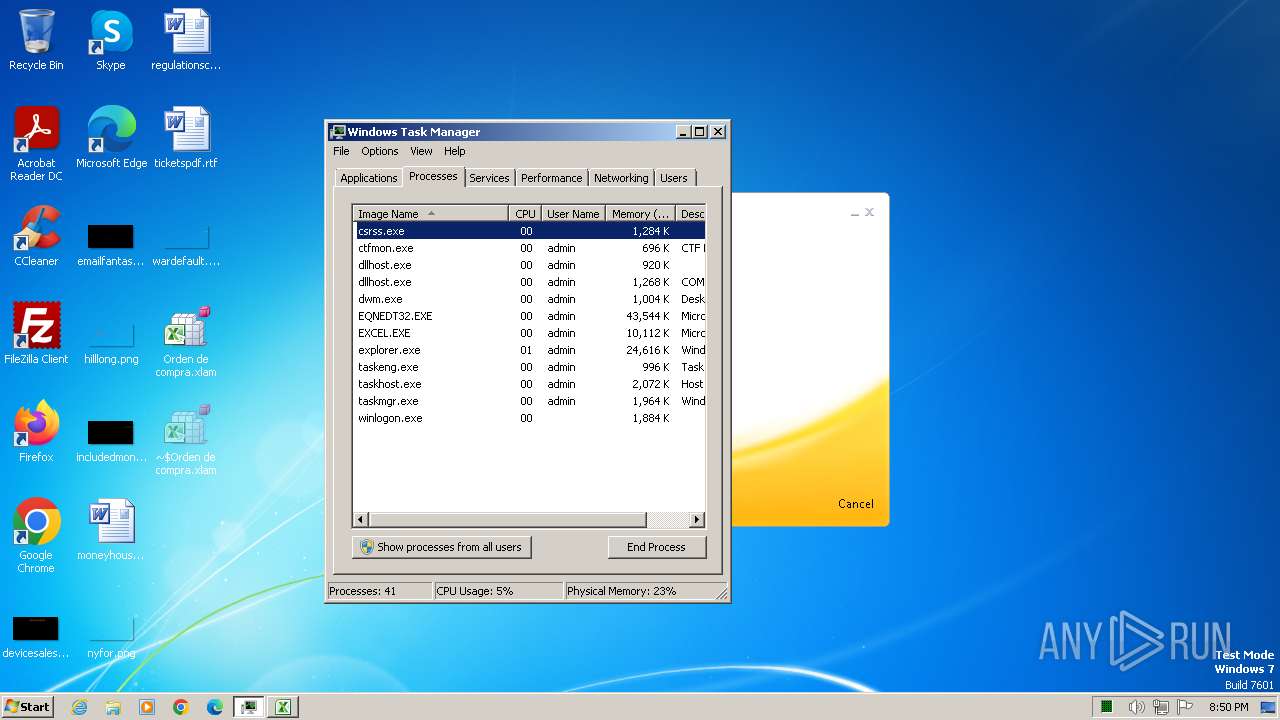
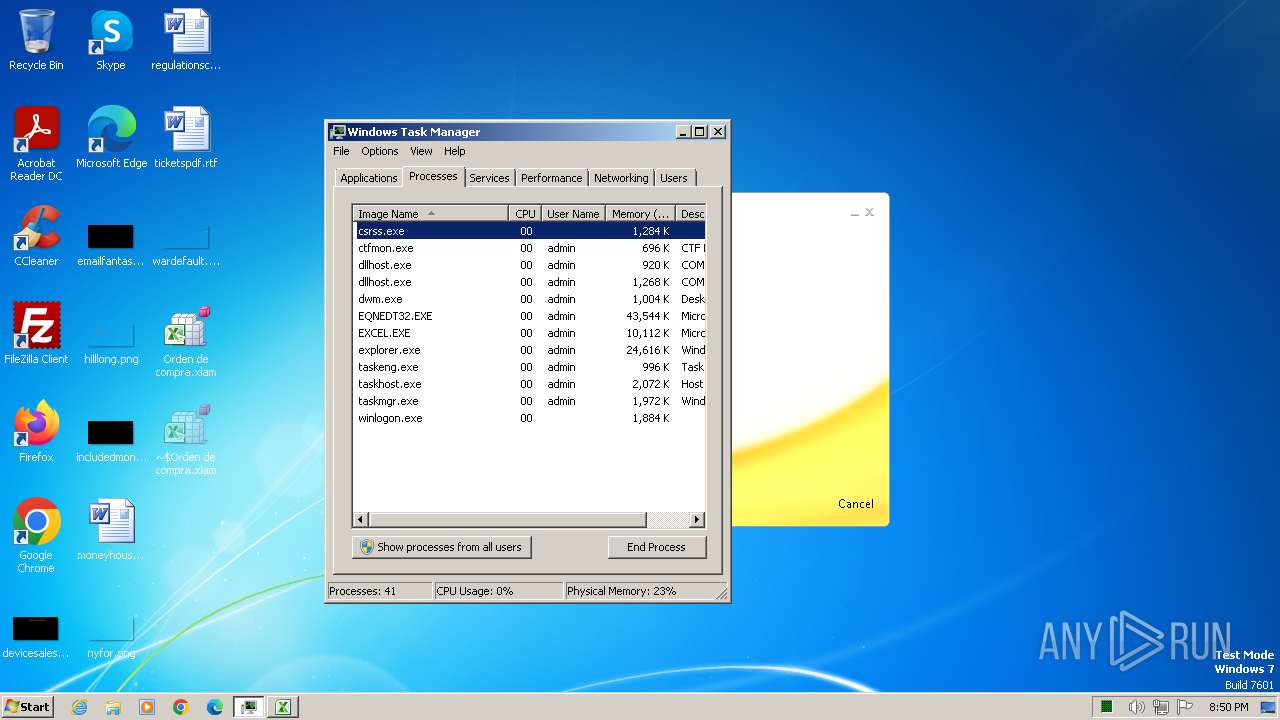
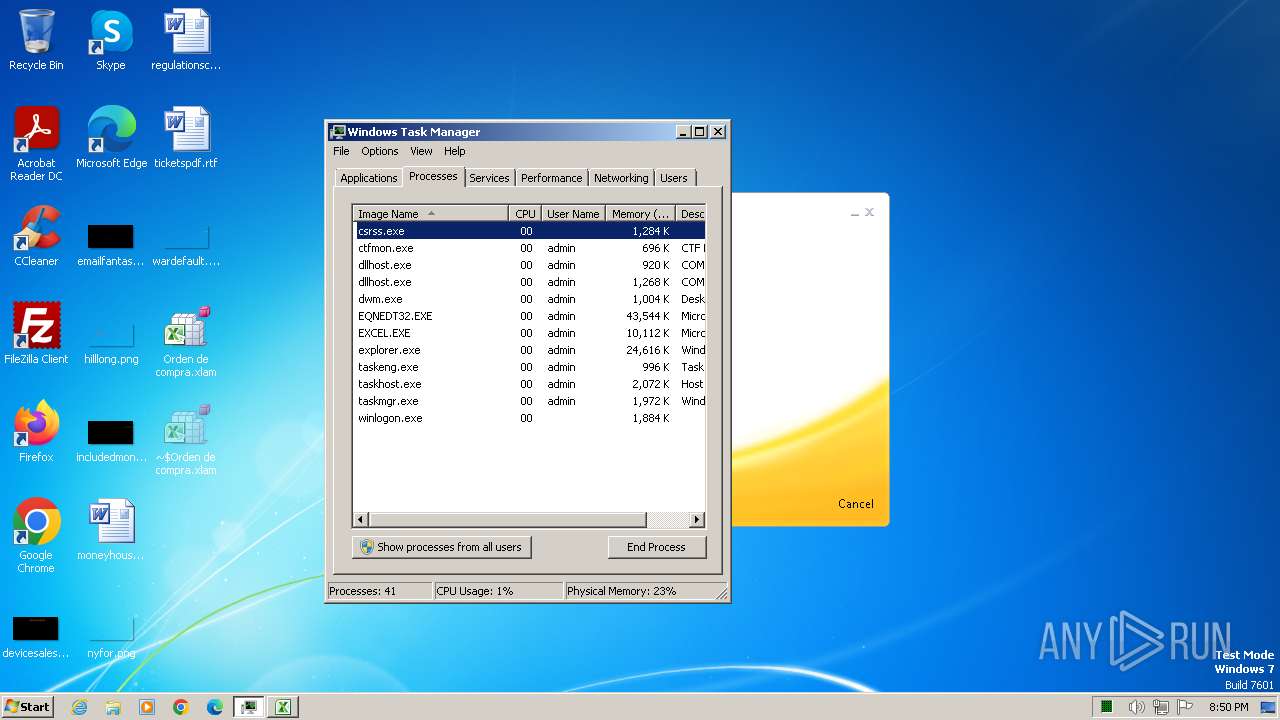
Total processes
99
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2276 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 1073807364 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2496 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\microsoft shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3088 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3512 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\herewgoagain..vbs" | C:\Windows\System32\wscript.exe | — | EQNEDT32.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
18 373
Read events
18 103
Write events
128
Delete events
142
Modification events
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | jh1 |
Value: 6A683100100C0000010000000000000000000000 | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3088) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
4
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3088 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRC04A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3540 | powershell.exe | C:\Users\admin\AppData\Local\Temp\yus0vk3d.ofl.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3088 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:61AB622B6636924580C8CDC7E5F85788 | SHA256:194FB3ADF800C024EBD627850D9FEC545E2C68B6CA5F6C632BF526AEC668C3EB | |||
| 2496 | EQNEDT32.EXE | C:\Users\admin\AppData\Roaming\herewgoagain..vbs | text | |
MD5:C930F9919D538D29300810720CAA8B3F | SHA256:09D786230948EBF09ABB8461040A94387AE3F8F4639F86C33DE1F602089897E1 | |||
| 3540 | powershell.exe | C:\Users\admin\AppData\Local\Temp\kl23lhx1.hnk.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3088 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Orden de compra.xlam.LNK | binary | |
MD5:563BDF6CC7DF90471E8C9FA6D671CB8E | SHA256:B73CD8FFE649F0F01EAF4354E6A38C0180F476F413552C3AC867EDC9726C0DCB | |||
| 1524 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
| 1524 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\en-us.html | html | |
MD5:9752942B57692148B9F614CF4C119A36 | SHA256:E31B834DD53FA6815F396FC09C726636ABF98F3367F0CF1590EF5EB3801C75D1 | |||
| 1524 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\microsoft-logo.png | image | |
MD5:B7C73A0CFBA68CC70C35EF9C63703CE4 | SHA256:1D8B27A0266FF526CF95447F3701592A908848467D37C09A00A2516C1F29A013 | |||
| 1524 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\script.js | text | |
MD5:A2682382967C351F7ED21762F9E5DE9E | SHA256:36B1D26F1EC69685648C0528C2FCE95A3C2DBECF828CDFA4A8B4239A15B644A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
10
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2496 | EQNEDT32.EXE | GET | 200 | 107.175.229.144:80 | http://107.175.229.144/herewgoagain.vbs | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 23.36.76.104:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.36.76.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 96.6.16.217:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3540 | powershell.exe | GET | 200 | 107.175.229.144:80 | http://107.175.229.144/mybase64rdpdpdpd.txt | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 23.36.76.104:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | whitelisted |
1524 | sipnotify.exe | HEAD | 200 | 104.110.23.132:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133664144014210000 | unknown | — | — | whitelisted |
2276 | AddInProcess32.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2496 | EQNEDT32.EXE | 107.175.229.144:80 | — | AS-COLOCROSSING | US | malicious |
1372 | svchost.exe | 23.36.76.104:80 | ctldl.windowsupdate.com | Akamai International B.V. | NO | unknown |
1372 | svchost.exe | 23.36.76.146:80 | crl.microsoft.com | Akamai International B.V. | NO | unknown |
1372 | svchost.exe | 96.6.16.217:80 | www.microsoft.com | AKAMAI-AS | NO | unknown |
3540 | powershell.exe | 207.241.232.195:443 | ia803405.us.archive.org | INTERNET-ARCHIVE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ia803405.us.archive.org |
| whitelisted |
ip-api.com |
| shared |
ftp.horeca-bucuresti.ro |
| malicious |
query.prod.cms.rt.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2496 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host VBS Request |
3540 | powershell.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Unknown EK Landing Feb 16 2015 b64 3 M1 |
1060 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
1060 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2276 | AddInProcess32.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2276 | AddInProcess32.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
3540 | powershell.exe | Potentially Bad Traffic | PAYLOAD [ANY.RUN] Reverse Base64 Encoded EXE Inbound |
1 ETPRO signatures available at the full report