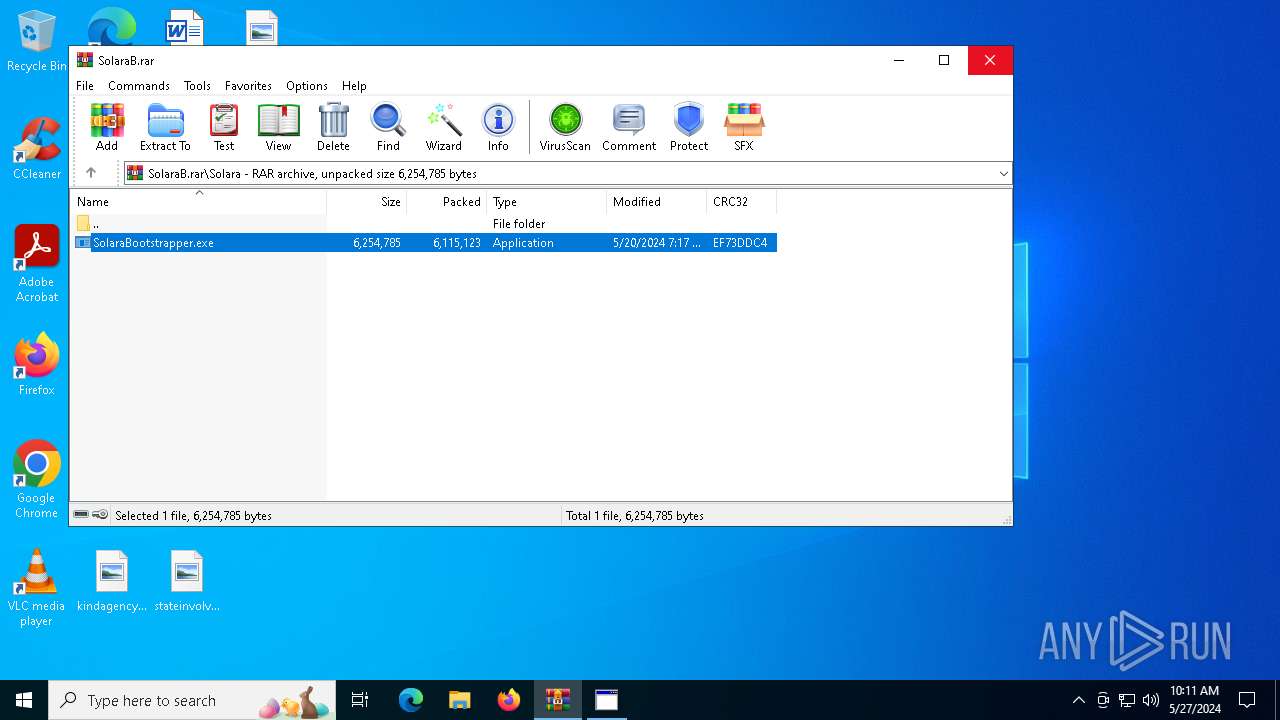
| File name: | SolaraB.rar |
| Full analysis: | https://app.any.run/tasks/9c56940e-1153-478a-8391-cd0c2eac167f |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | May 27, 2024, 10:11:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8326CA9B397A7039B76E6880AC0C075B |
| SHA1: | 1884EA267BB1B41D0337BCF8B9FB10B96EF52719 |
| SHA256: | 5C3C40B88AEBB199399CCF9A6EA330D37BB711487450B55F476D284726D2CF53 |
| SSDEEP: | 98304:e1zlgXvwAtHr3/ni/yHI5rGR6rxfu/cPU1ouhf3TFo0yixyuvsD5FwEM6ir056eC:1ir7Hn9Ao+ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6312)
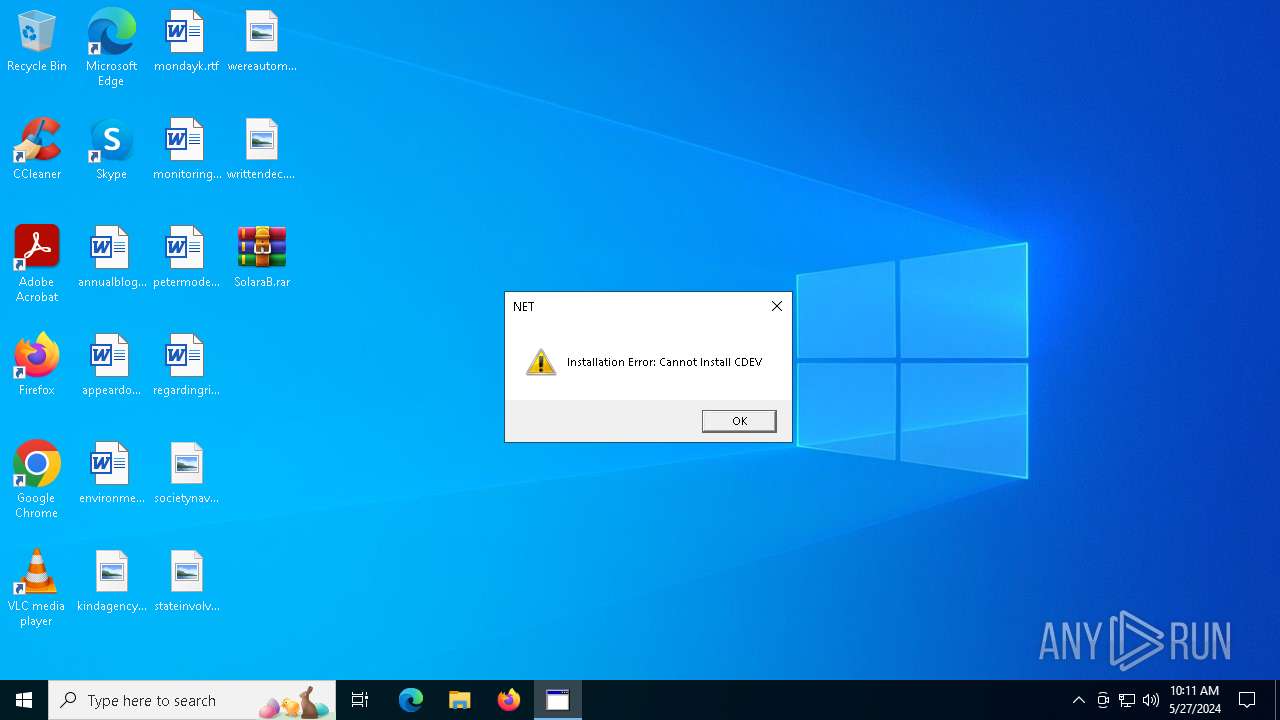
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
BlankGrabber has been detected
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 6952)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 5204)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 1724)
- SolaraBootstrapper.exe (PID: 5720)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 1712)
- MpCmdRun.exe (PID: 5712)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 1712)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6312)
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
Starts a Microsoft application from unusual location
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 6776)
- SolaraBootstrapper.exe (PID: 1016)
- SolaraBootstrapper.exe (PID: 5720)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6312)
The process drops C-runtime libraries
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
Executable content was dropped or overwritten
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
Process drops python dynamic module
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
Application launched itself
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
Starts CMD.EXE for commands execution
- SolaraBootstrapper.exe (PID: 6776)
- SolaraBootstrapper.exe (PID: 5720)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6796)
- cmd.exe (PID: 6888)
- cmd.exe (PID: 5776)
Found strings related to reading or modifying Windows Defender settings
- SolaraBootstrapper.exe (PID: 6776)
- SolaraBootstrapper.exe (PID: 5720)
Changes default file association
- reg.exe (PID: 6952)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 6980)
- cmd.exe (PID: 3592)
Loads Python modules
- SolaraBootstrapper.exe (PID: 5720)
Get information on the list of running processes
- SolaraBootstrapper.exe (PID: 5720)
- cmd.exe (PID: 472)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1724)
- cmd.exe (PID: 1712)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 1724)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 1712)
Script disables Windows Defender's IPS
- cmd.exe (PID: 1712)
INFO
Reads the computer name
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 1016)
- SolaraBootstrapper.exe (PID: 5720)
- MpCmdRun.exe (PID: 5712)
Checks supported languages
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 6776)
- SolaraBootstrapper.exe (PID: 1016)
- SolaraBootstrapper.exe (PID: 5720)
- MpCmdRun.exe (PID: 5712)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6312)
Create files in a temporary directory
- SolaraBootstrapper.exe (PID: 6756)
- SolaraBootstrapper.exe (PID: 6776)
- SolaraBootstrapper.exe (PID: 1016)
- SolaraBootstrapper.exe (PID: 5720)
- MpCmdRun.exe (PID: 5712)
Reads the machine GUID from the registry
- SolaraBootstrapper.exe (PID: 6776)
- SolaraBootstrapper.exe (PID: 5720)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 5204)
Reads Microsoft Office registry keys
- ComputerDefaults.exe (PID: 5204)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2592)
- powershell.exe (PID: 3644)
Reads Internet Explorer settings
- mshta.exe (PID: 6208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
155
Monitored processes
38
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | SolaraBootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1016 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6312.1890\Solara\SolaraBootstrapper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6312.1890\Solara\SolaraBootstrapper.exe | ComputerDefaults.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: EDP Cleanup Exit code: 0 Version: 10.0.19041.4123 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1428 | reg delete hkcu\Software\Classes\ms-settings /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1712 | C:\WINDOWS\system32\cmd.exe /c "powershell Set-MpPreference -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableRealtimeMonitoring $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend && powershell Set-MpPreference -SubmitSamplesConsent 2 & "%ProgramFiles%\Windows Defender\MpCmdRun.exe" -RemoveDefinitions -All" | C:\Windows\System32\cmd.exe | — | SolaraBootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1724 | C:\WINDOWS\system32\cmd.exe /c "powershell -Command Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Local\Temp\Rar$EXa6312.1890\Solara\SolaraBootstrapper.exe'" | C:\Windows\System32\cmd.exe | — | SolaraBootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2592 | powershell Set-MpPreference -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableRealtimeMonitoring $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3592 | C:\WINDOWS\system32\cmd.exe /c "wevtutil qe "Microsoft-Windows-Windows Defender/Operational" /f:text" | C:\Windows\System32\cmd.exe | — | SolaraBootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3644 | powershell -Command Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Local\Temp\Rar$EXa6312.1890\Solara\SolaraBootstrapper.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 046
Read events
23 979
Write events
63
Delete events
4
Modification events
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SolaraB.rar | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6312) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
38
Suspicious files
5
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\VCRUNTIME140.dll | executable | |
MD5:870FEA4E961E2FBD00110D3783E529BE | SHA256:76FDB83FDE238226B5BEBAF3392EE562E2CB7CA8D3EF75983BF5F9D6C7119644 | |||
| 6312 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6312.1890\Solara\SolaraBootstrapper.exe | executable | |
MD5:78B0815A69F61745AD6D13829F770248 | SHA256:A0E125DB0C9AE88EEC78F08128CF7A3250A15C1825891432275623A804212613 | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\_sqlite3.pyd | executable | |
MD5:BB4AA2D11444900C549E201EB1A4CDD6 | SHA256:F44D80AB16C27CA65DA23AE5FDA17EB842065F3E956F10126322B2EA3ECDF43F | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\_hashlib.pyd | executable | |
MD5:4AE75C47DBDEBAA16A596F31B27ABD9E | SHA256:2308EE238CC849B1110018B211B149D607BF447F4E4C1E61449049EAB0CF513D | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\_ctypes.pyd | executable | |
MD5:813FC3981CAE89A4F93BF7336D3DC5EF | SHA256:4AC7FB7B354069E71EBF7FCC193C0F99AF559010A0AD82A03B49A92DEB0F4D06 | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\_socket.pyd | executable | |
MD5:7A31BC84C0385590E5A01C4CBE3865C3 | SHA256:5614017765322B81CC57D841B3A63CBDC88678FF605E5D4C8FDBBF8F0AC00F36 | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\_lzma.pyd | executable | |
MD5:6F810F46F308F7C6CCDDCA45D8F50039 | SHA256:39497259B87038E86C53E7A39A0B5BBBFCEBE00B2F045A148041300B31F33B76 | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\blank.aes | binary | |
MD5:D58B46409C46714F80D774EAF091115F | SHA256:D845D17A149D5E1E9CDE2A2F7B8F5A96D92C7499DC7A9DAC1C5A03D08A986FC5 | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\_ssl.pyd | executable | |
MD5:081C878324505D643A70EFCC5A80A371 | SHA256:FCB70B58F94F5B0F9D027999CCE25E99DDCC8124E4DDCC521CB5B96A52FAAA66 | |||
| 6756 | SolaraBootstrapper.exe | C:\Users\admin\AppData\Local\Temp\_MEI67562\base_library.zip | compressed | |
MD5:EE93CE2F8261BA7510F041619BB2B6F2 | SHA256:41CE839465CF935B821CAFC3A98AFE1C411BF4655AD596442EB66D140CCD502E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
23
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5576 | svchost.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5576 | svchost.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
528 | RUXIMICS.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | — | null:443 | https://blank-gd8g7.in/ | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
528 | RUXIMICS.exe | GET | 200 | 2.16.164.51:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2908 | OfficeClickToRun.exe | POST | 200 | 20.42.65.89:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5576 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
528 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5576 | svchost.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
528 | RUXIMICS.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 2.16.164.51:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5576 | svchost.exe | 2.18.97.123:80 | www.microsoft.com | Akamai International B.V. | FR | unknown |
528 | RUXIMICS.exe | 2.18.97.123:80 | www.microsoft.com | Akamai International B.V. | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
blank-gd8g7.in |
| unknown |
self.events.data.microsoft.com |
| whitelisted |