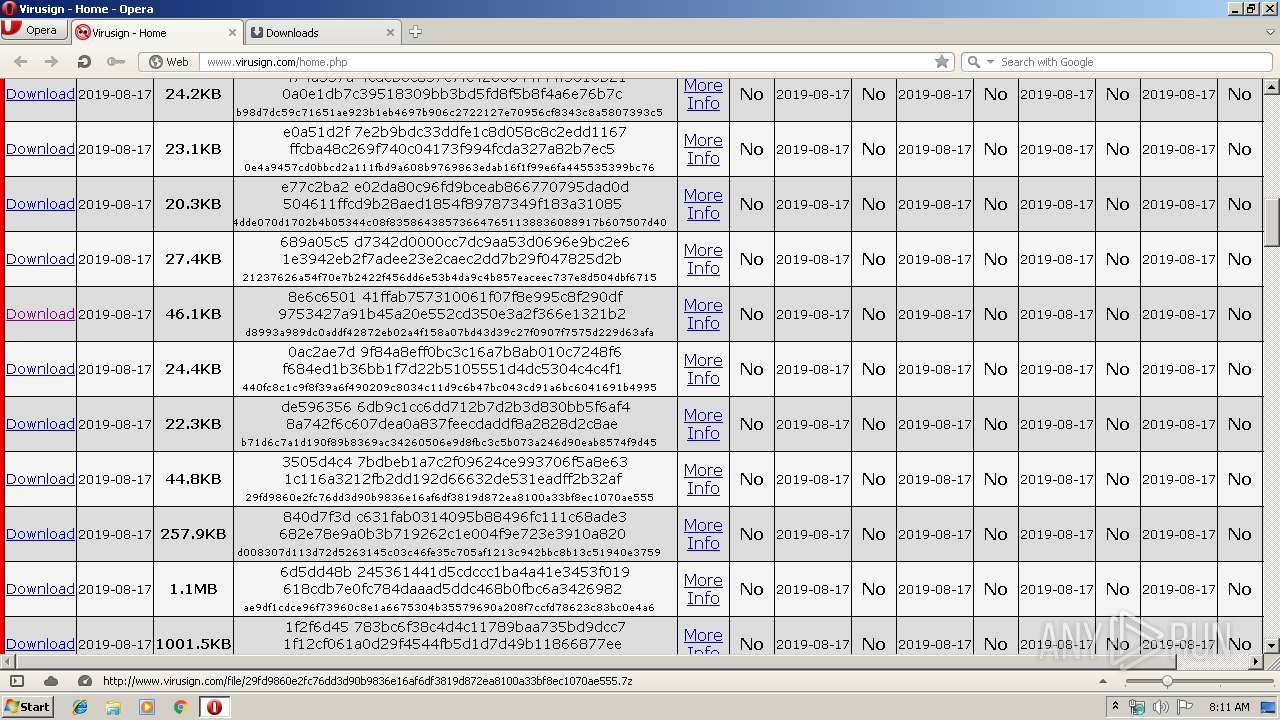
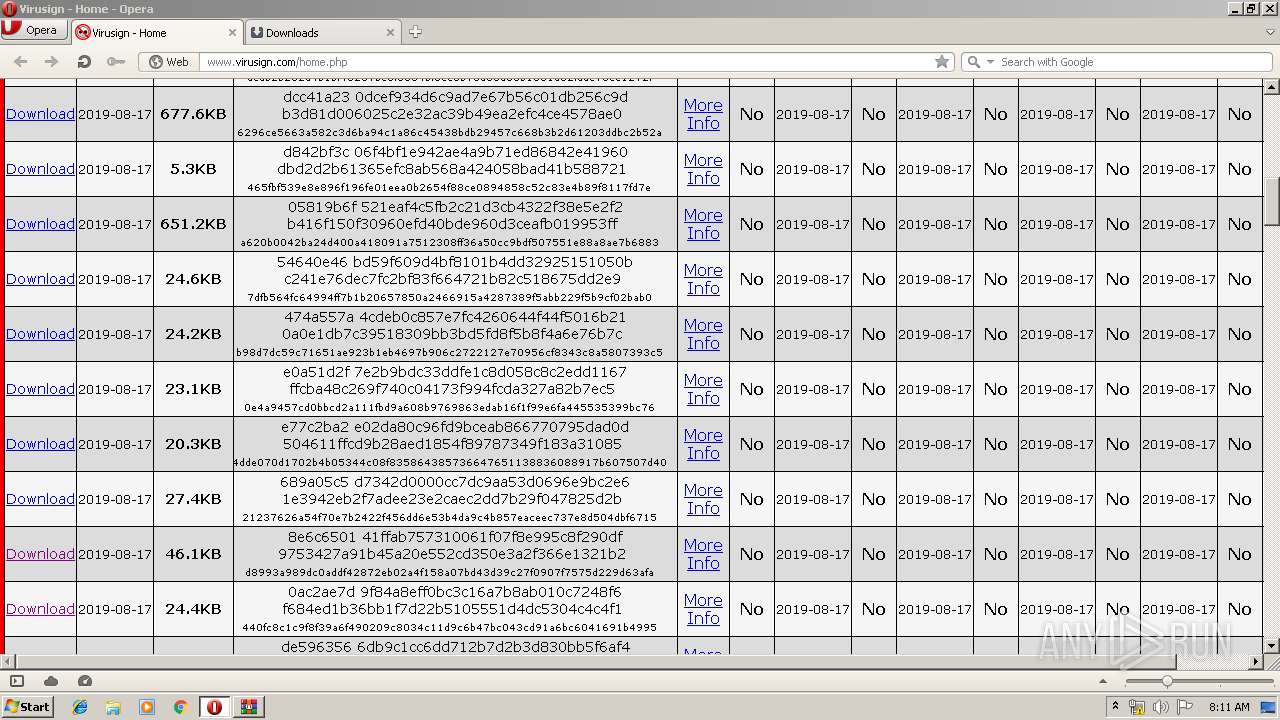
| URL: | http://www.virusign.com/home.php?d=0&r=100&c=hashes&o=date&s=DESC&n=EXACT&p=1 |
| Full analysis: | https://app.any.run/tasks/95f958f3-aece-4293-9fa3-8af72db7aab6 |
| Verdict: | Malicious activity |
| Threats: | Predator, the Thief, is an information stealer, meaning that malware steals data from infected systems. This virus can access the camera and spy on victims, steal passwords and login information, and retrieve payment data from cryptocurrency wallets. |
| Analysis date: | August 18, 2019, 07:10:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | AFE870FE890EADDD806E0B748D2FABC5 |
| SHA1: | 45823F19D01EA267CFD517073C188E6382CDFD89 |
| SHA256: | 5BC92484CDDA53BB9EF2594AC5FE426F633D641683DF215A5FF35EB2663D3F7B |
| SSDEEP: | 3:N1KJS4AXvd9KJwB4L5VpPrvKYy0f22mIgGUn:Cc4AFo++VpPOYy0u2mIgDn |
MALICIOUS
Application was dropped or rewritten from another process
- rjun.exe (PID: 3364)
- Tin86.exe (PID: 3148)
- Tin86.exe (PID: 3704)
PREDATOR was detected
- rjun.exe (PID: 3364)
Connects to CnC server
- rjun.exe (PID: 3364)
SUSPICIOUS
Creates files in the user directory
- rjun.exe (PID: 3364)
Starts CMD.EXE for commands execution
- rjun.exe (PID: 3364)
Application launched itself
- taskmgr.exe (PID: 3468)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1020)
- WinRAR.exe (PID: 3548)
Reads the cookies of Google Chrome
- rjun.exe (PID: 3364)
Starts CMD.EXE for self-deleting
- rjun.exe (PID: 3364)
Reads the cookies of Mozilla Firefox
- rjun.exe (PID: 3364)
Connects to server without host name
- rjun.exe (PID: 3364)
INFO
Creates files in the user directory
- opera.exe (PID: 3528)
Manual execution by user
- taskmgr.exe (PID: 3468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 840 | ping 127.0.0.1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
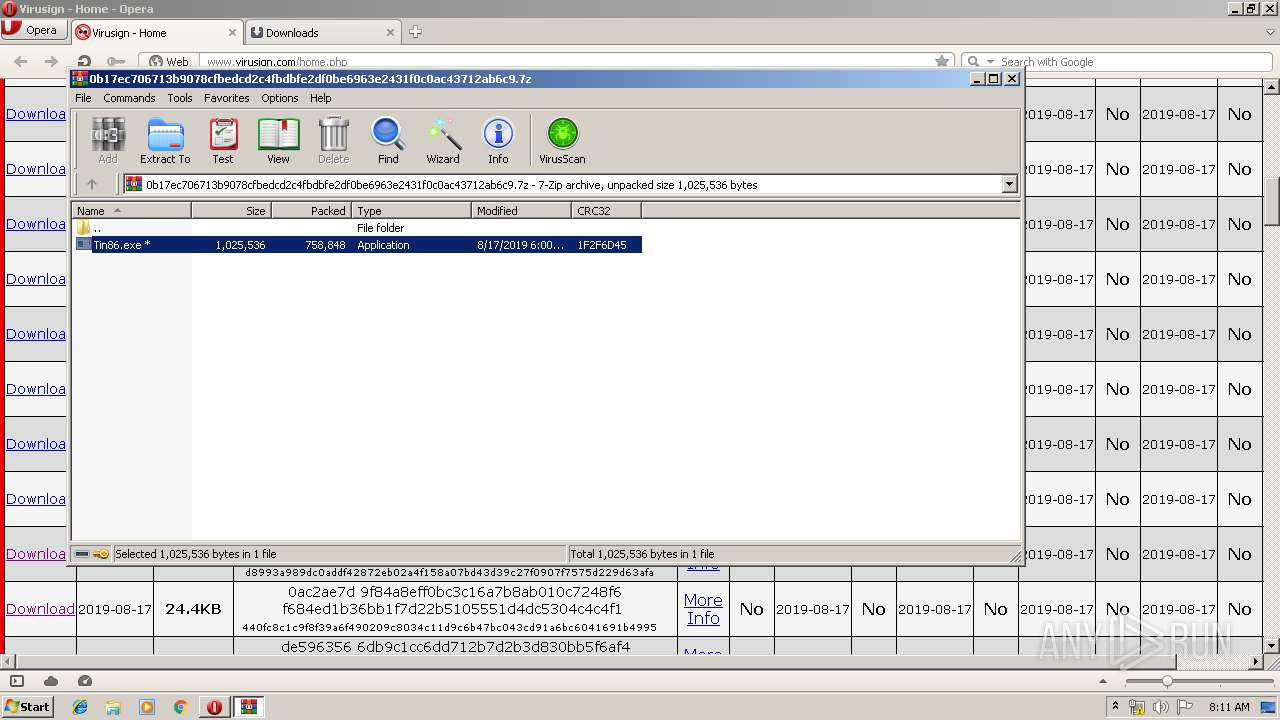
| 1020 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\abd5c22fc4a791e82ab18be6f73858087decf7cfa2798a1fa47e181b386960a5.7z" | C:\Program Files\WinRAR\WinRAR.exe | opera.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\d8993a989dc0addf42872eb02a4f158a07bd43d39c27f0907f7575d229d63afa.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | opera.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
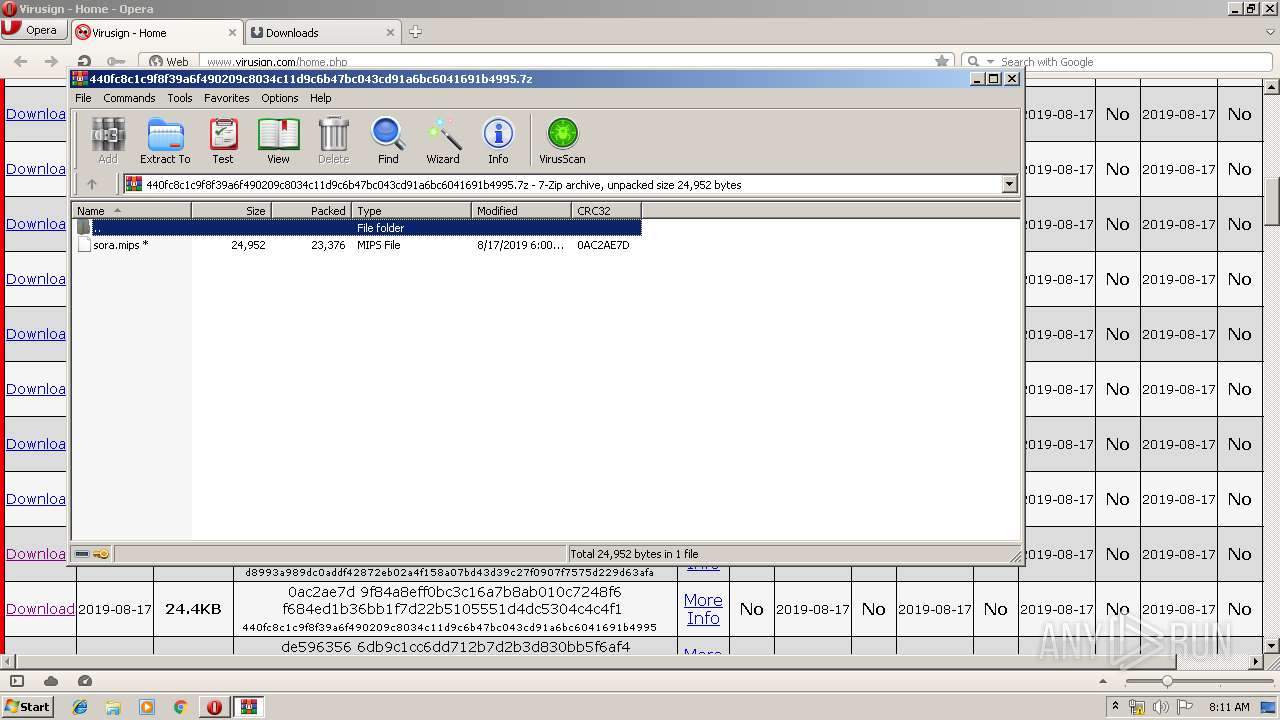
| 2684 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\440fc8c1c9f8f39a6f490209c8034c11d9c6b47bc043cd91a6bc6041691b4995.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | opera.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
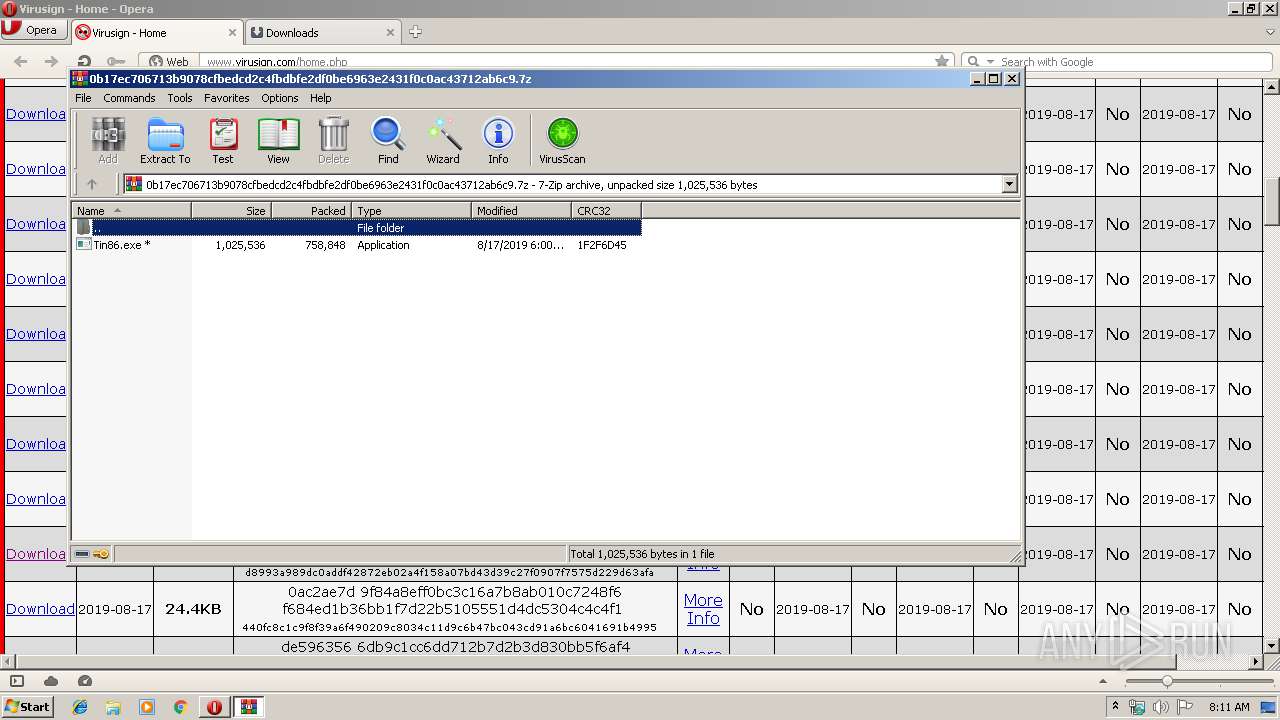
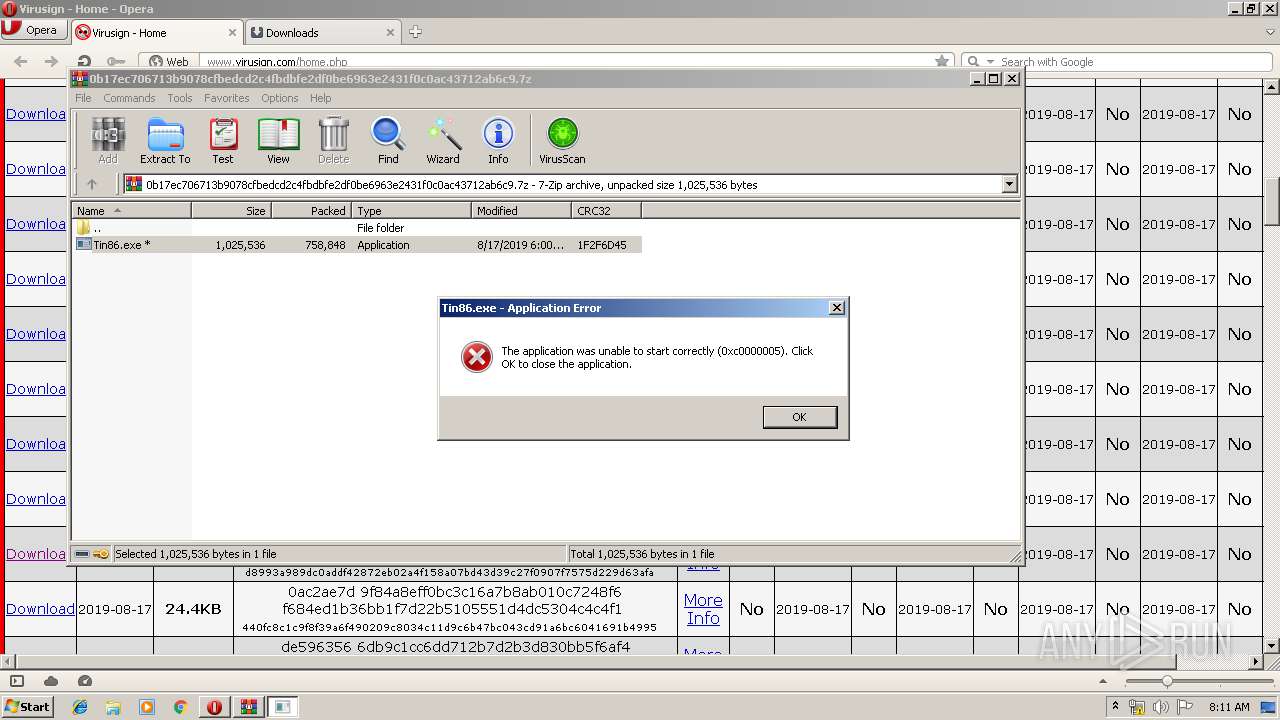
| 3148 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3548.28696\Tin86.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3548.28696\Tin86.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print UI Cache Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3364 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1020.33482\rjun.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1020.33482\rjun.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3460 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\system32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3468 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3528 | "C:\Program Files\Opera\opera.exe" "http://www.virusign.com/home.php?d=0&r=100&c=hashes&o=date&s=DESC&n=EXACT&p=1" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 3548 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\0b17ec706713b9078cfbedcd2c4fbdbfe2df0be6963e2431f0c0ac43712ab6c9.7z" | C:\Program Files\WinRAR\WinRAR.exe | opera.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
2 567
Read events
2 328
Write events
239
Delete events
0
Modification events
| (PID) Process: | (3528) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe "http://www.virusign.com/home.php?d=0&r=100&c=hashes&o=date&s=DESC&n=EXACT&p=1" | |||
| (PID) Process: | (3528) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3528) opera.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3528) opera.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Opera\Opera\temporary_downloads\d8993a989dc0addf42872eb02a4f158a07bd43d39c27f0907f7575d229d63afa.7z | |||
| (PID) Process: | (2668) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
2
Suspicious files
50
Text files
24
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprA0F8.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprA0F9.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprA148.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HVPVSZW18RNQNKMRUMV7.temp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprAE0A.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprE48C.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprE49D.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
11
DNS requests
4
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3528 | opera.exe | GET | — | 178.32.62.43:80 | http://www.virusign.com/images/info_balloon.svg | GB | — | — | whitelisted |
3528 | opera.exe | GET | — | 178.32.62.43:80 | http://www.virusign.com/images/home_blue.svg | GB | — | — | whitelisted |
3528 | opera.exe | GET | — | 178.32.62.43:80 | http://www.virusign.com/images/doc_hashes.svg | GB | — | — | whitelisted |
3528 | opera.exe | GET | — | 178.32.62.43:80 | http://www.virusign.com/images/virusign_logo.svg | GB | — | — | whitelisted |
3528 | opera.exe | GET | 200 | 178.32.62.43:80 | http://www.virusign.com/home.php?d=0&r=100&c=hashes&o=date&s=DESC&n=EXACT&p=1 | GB | html | 15.2 Kb | whitelisted |
3528 | opera.exe | GET | 200 | 178.32.62.43:80 | http://www.virusign.com/images/anti_skull.svg | GB | image | 4.23 Kb | whitelisted |
3528 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
3528 | opera.exe | GET | 200 | 178.32.62.43:80 | http://www.virusign.com/images/transparent.gif | GB | image | 815 b | whitelisted |
3528 | opera.exe | GET | 200 | 178.32.62.43:80 | http://www.virusign.com/images/doc_info.svg | GB | image | 856 b | whitelisted |
3528 | opera.exe | GET | 200 | 178.32.62.43:80 | http://www.virusign.com/images/email.svg | GB | image | 1.22 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3528 | opera.exe | 178.32.62.43:80 | www.virusign.com | OVH SAS | GB | suspicious |
3528 | opera.exe | 185.26.182.94:443 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
3528 | opera.exe | 185.26.182.93:80 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
3364 | rjun.exe | 92.63.192.228:80 | — | IT DeLuxe Ltd. | RU | malicious |
3528 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.virusign.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3528 | opera.exe | Potential Corporate Privacy Violation | ET POLICY Outgoing Basic Auth Base64 HTTP Password detected unencrypted |
3364 | rjun.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/Spy.Agent.PLQ (Predator Stealer) CnC Checkin |
2 ETPRO signatures available at the full report