| File name: | setup.msi |
| Full analysis: | https://app.any.run/tasks/8f1b2daf-aa26-41e5-901f-c551b358482e |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | October 16, 2024, 19:24:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
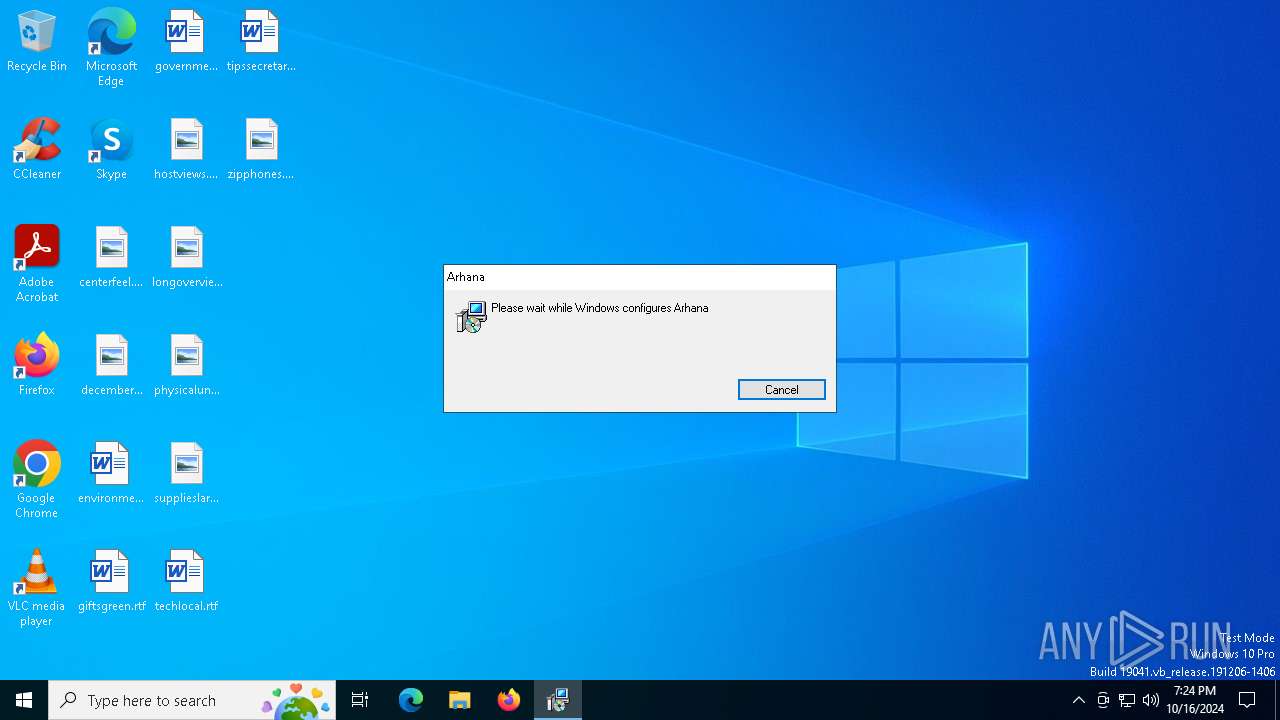
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: This setup package will Install Arhana version 2.2.2, Author: ARH, Keywords: Installer, Comments: This installer database contains the logic and data required to install Arhana., Template: Intel;1033, Revision Number: {AEDB5D85-A9C4-4B31-A45E-2E505DE2843F}, Create Time/Date: Tue Oct 15 05:06:26 2024, Last Saved Time/Date: Tue Oct 15 05:06:26 2024, Number of Pages: 200, Number of Words: 10, Name of Creating Application: Windows Installer XML Toolset (3.11.0.1528), Security: 2 |
| MD5: | CC7CF110BC43165463E51675775A2050 |
| SHA1: | A4A80DC684F61D8EB8BCDE68856E84A16B5EF3D9 |
| SHA256: | 5B95F27FD07D589E652816F564066EAC2424AC744764587E503D5D040ABA3EBA |
| SSDEEP: | 24576:ntg/Qe7QDmsL9rYXJZ3fh+pQBmC6kzMhX+:ntg/Qe7QDmsL9rYXJZ3fh+pQBmC6kzMw |
MALICIOUS
Connects to the CnC server
- DSAWcfProxy.exe (PID: 6688)
- DSAWcfProxy.exe (PID: 6940)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6596)
Application launched itself
- DSAWcfProxy.exe (PID: 2280)
Connects to the server without a host name
- DSAWcfProxy.exe (PID: 6688)
- DSAWcfProxy.exe (PID: 6940)
- DSAWcfProxy.exe (PID: 2280)
Contacting a server suspected of hosting an CnC
- DSAWcfProxy.exe (PID: 6688)
- DSAWcfProxy.exe (PID: 6940)
INFO
Manages system restore points
- SrTasks.exe (PID: 7132)
Reads the computer name
- msiexec.exe (PID: 4072)
Checks supported languages
- msiexec.exe (PID: 4072)
An automatically generated document
- msiexec.exe (PID: 4792)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | This setup package will Install Arhana version 2.2.2 |
| Author: | ARH |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Arhana. |
| Template: | Intel;1033 |
| RevisionNumber: | {AEDB5D85-A9C4-4B31-A45E-2E505DE2843F} |
| CreateDate: | 2024:10:15 05:06:26 |
| ModifyDate: | 2024:10:15 05:06:26 |
| Pages: | 200 |
| Words: | 10 |
| Software: | Windows Installer XML Toolset (3.11.0.1528) |
| Security: | Read-only recommended |
Total processes
146
Monitored processes
12
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | "C:\ProgramData\Arh\DSAWcfProxy.exe" | C:\ProgramData\Arh\DSAWcfProxy.exe | msiexec.exe | ||||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: MEDIUM Description: AutoHotkey Unicode 32-bit Version: 1.1.37.02 Modules
| |||||||||||||||
| 3848 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 4072 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4340 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 4792 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\setup.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6596 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6688 | C:\ProgramData\Arh\DSAWcfProxy.exe C:\ProgramData\Arh\DSAWcfProxy.exe~ | C:\ProgramData\Arh\DSAWcfProxy.exe | DSAWcfProxy.exe | ||||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: MEDIUM Description: AutoHotkey Unicode 32-bit Exit code: 0 Version: 1.1.37.02 Modules
| |||||||||||||||
Total events
5 183
Read events
4 979
Write events
186
Delete events
18
Modification events
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000700D1CFB0020DB01E80F0000A8190000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000700D1CFB0020DB01E80F0000A8190000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000975468FB0020DB01E80F0000A8190000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000975468FB0020DB01E80F0000A8190000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000001FB96AFB0020DB01E80F0000A8190000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000541C6DFB0020DB01E80F0000A8190000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000B0061FFC0020DB01E80F0000A8190000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F0CE23FC0020DB01E80F000074050000E8030000010000000000000000000000DAEF707F8343E547B9D106ED00854EDA00000000000000000000000000000000 | |||
| (PID) Process: | (6596) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000000AF2FFC0020DB01C419000028060000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
2
Suspicious files
19
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4072 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4072 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:EFF3329A1598B19528C35BDF9F3C97C6 | SHA256:2EBE3CB3F2F8F2FAC9BF3261F15B45B127F00C7B4CD632CE61AB7299108F9879 | |||
| 4072 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\DSAWcfProxy.lnk | binary | |
MD5:9FC01B8908D14168B6CF171B54E0170E | SHA256:8F5F76B6B87496E3A60855E34BA7B9E002FE98F7543FDB5C0733098877934777 | |||
| 4072 | msiexec.exe | C:\Windows\Temp\~DF92801128BDAE938D.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 4072 | msiexec.exe | C:\ProgramData\Arh\DSAWcfProxy.ahk | text | |
MD5:672ACEA81E55B00E8659571BDE188196 | SHA256:22D24136B8F0B1B4196B94BAA3CE6CA049ABD318EBFE3FD8A7A8F5566CF7FB28 | |||
| 4072 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:A73892937B1DE65F0E413F163F3063E5 | SHA256:3B0B873DE00B35BE8DD7AFEA25B441896230E3FA9E4846AAF4CC8E38287551D1 | |||
| 4072 | msiexec.exe | C:\Windows\Temp\~DFF1A7F052D7FA8425.TMP | binary | |
MD5:A73892937B1DE65F0E413F163F3063E5 | SHA256:3B0B873DE00B35BE8DD7AFEA25B441896230E3FA9E4846AAF4CC8E38287551D1 | |||
| 4072 | msiexec.exe | C:\Windows\Installer\MSI553.tmp | binary | |
MD5:AD523D9EA8D372B95F27E5F8118FE550 | SHA256:415317B3603C30CF8690695685C8EBF298FE0639335D6C862D6E7C6E72962764 | |||
| 4072 | msiexec.exe | C:\Windows\Installer\9039e.msi | executable | |
MD5:CC7CF110BC43165463E51675775A2050 | SHA256:5B95F27FD07D589E652816F564066EAC2424AC744764587E503D5D040ABA3EBA | |||
| 4072 | msiexec.exe | C:\Windows\Temp\~DF0C67E467696C623E.TMP | binary | |
MD5:A73892937B1DE65F0E413F163F3063E5 | SHA256:3B0B873DE00B35BE8DD7AFEA25B441896230E3FA9E4846AAF4CC8E38287551D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
15
DNS requests
14
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
2280 | DSAWcfProxy.exe | GET | 404 | 66.23.227.33:80 | http://66.23.227.33/649566714 | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2280 | DSAWcfProxy.exe | 66.23.227.33:80 | — | IS-AS-1 | US | malicious |
6688 | DSAWcfProxy.exe | 66.23.227.33:80 | — | IS-AS-1 | US | malicious |
6940 | DSAWcfProxy.exe | 66.23.227.33:80 | — | IS-AS-1 | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2280 | DSAWcfProxy.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |
2280 | DSAWcfProxy.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (AutoHotkey) |
6688 | DSAWcfProxy.exe | Malware Command and Control Activity Detected | ET MALWARE AHK Bot Domain Profiler CnC Activity |
6688 | DSAWcfProxy.exe | Malware Command and Control Activity Detected | ET MALWARE AHK Bot Domain Profiler CnC Activity |
6688 | DSAWcfProxy.exe | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
6940 | DSAWcfProxy.exe | Malware Command and Control Activity Detected | ET MALWARE AHK Bot Domain Profiler CnC Activity |
5 ETPRO signatures available at the full report