| File name: | 5b3a41ed8a9a619b4aa18cef611c94b3273671ad464847cbfa600a6571c64431.msi |
| Full analysis: | https://app.any.run/tasks/7db6f047-cbfb-4ed6-aac1-1b2047415a90 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 10, 2024, 10:36:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {A3B69905-389C-4777-92FB-F2E072712230}, Number of Words: 10, Subject: TroxApp, Author: Troxbox Publish, Name of Creating Application: TroxApp, Template: x64;1033, Comments: This installer database contains the logic and data required to install TroxApp., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Mon Jul 8 17:55:21 2024, Last Saved Time/Date: Mon Jul 8 17:55:21 2024, Last Printed: Mon Jul 8 17:55:21 2024, Number of Pages: 450 |
| MD5: | 6E619D3D24F58BFB7BD7E76A4756E258 |
| SHA1: | 890359E1E86525C4C14E975E762239878134B32D |
| SHA256: | 5B3A41ED8A9A619B4AA18CEF611C94B3273671AD464847CBFA600A6571C64431 |
| SSDEEP: | 393216:U88/NM3eBSTDiwDnsVznaoDtACBF2iILPmq:k6tu+nKnrDqCqtLP |
MALICIOUS
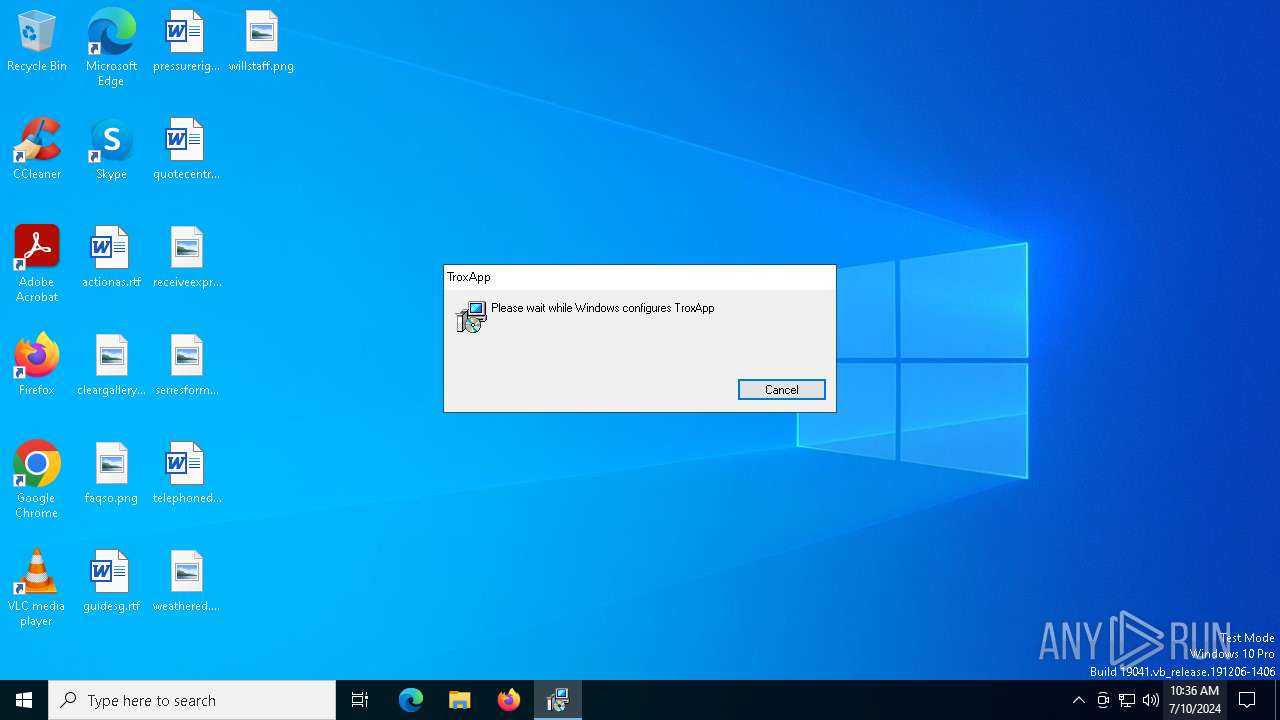
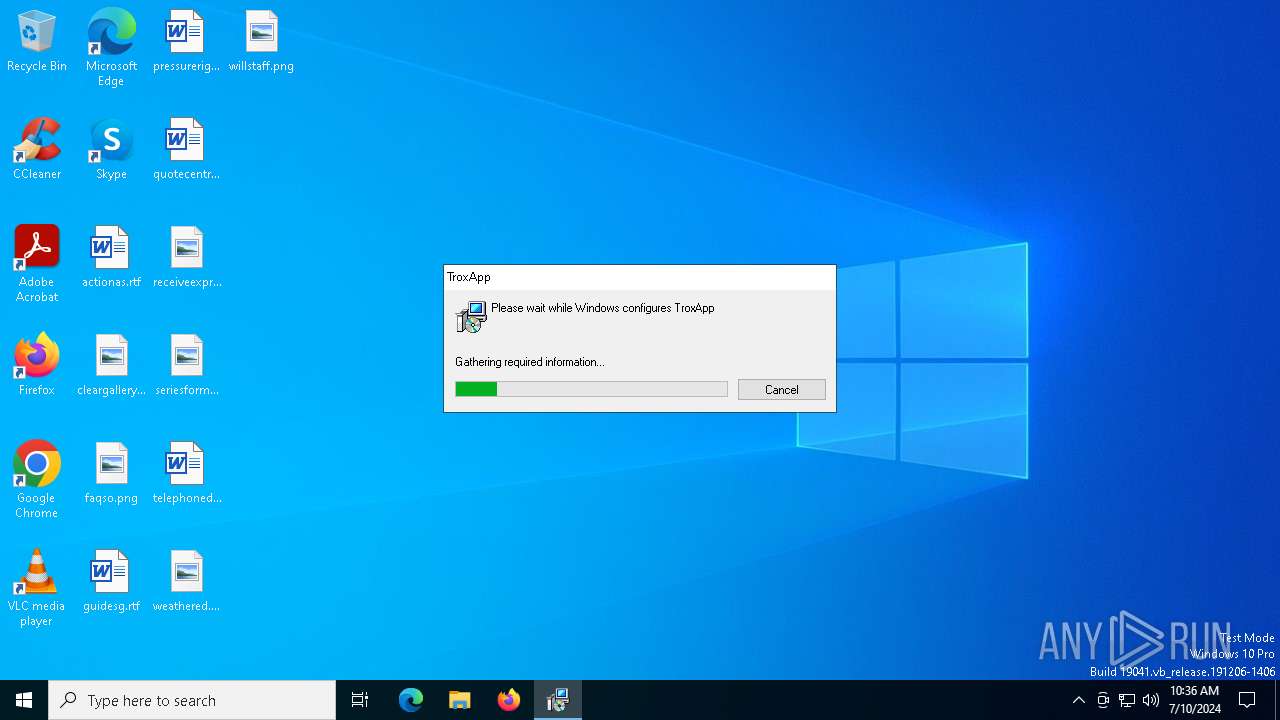
Drops the executable file immediately after the start
- msiexec.exe (PID: 6272)
- UnRAR.exe (PID: 6560)
Run PowerShell with an invisible window
- powershell.exe (PID: 7132)
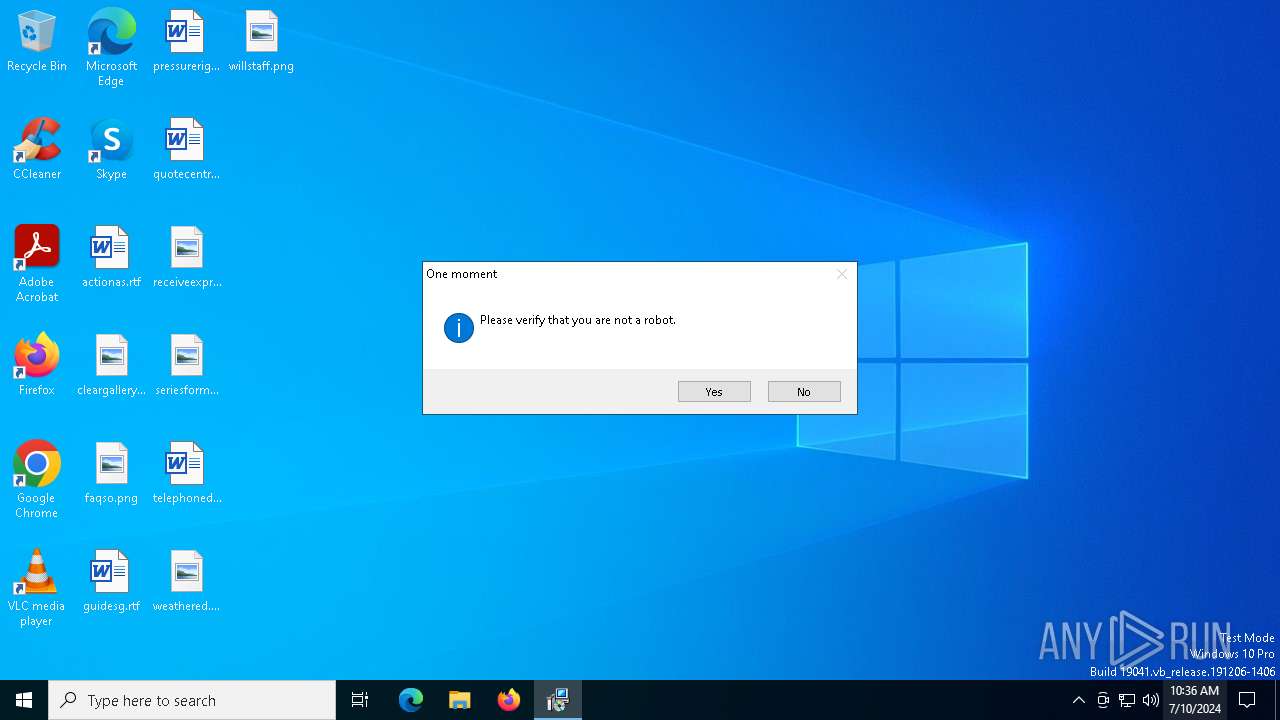
Actions looks like stealing of personal data
- powershell.exe (PID: 7132)
- BitLockerToGo.exe (PID: 1764)
LUMMA has been detected (SURICATA)
- BitLockerToGo.exe (PID: 1764)
SUSPICIOUS
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6324)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6272)
Checks Windows Trust Settings
- msiexec.exe (PID: 6324)
Process drops legitimate windows executable
- msiexec.exe (PID: 6272)
The process drops C-runtime libraries
- msiexec.exe (PID: 6272)
Executes application which crashes
- rnpkeys.exe (PID: 6708)
Executable content was dropped or overwritten
- UnRAR.exe (PID: 6560)
- explorer.exe (PID: 6768)
BASE64 encoded PowerShell command has been detected
- explorer.exe (PID: 6768)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 6768)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 7132)
Base64-obfuscated command line is found
- explorer.exe (PID: 6768)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7132)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 7132)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 7132)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 7132)
Searches for installed software
- BitLockerToGo.exe (PID: 1764)
Contacting a server suspected of hosting an CnC
- BitLockerToGo.exe (PID: 1764)
INFO
An automatically generated document
- msiexec.exe (PID: 6180)
Reads the computer name
- msiexec.exe (PID: 6272)
- msiexec.exe (PID: 6324)
- BitLockerToGo.exe (PID: 1764)
Checks supported languages
- msiexec.exe (PID: 6272)
- msiexec.exe (PID: 6324)
- UnRAR.exe (PID: 6560)
- rnpkeys.exe (PID: 6708)
- svchost.exe (PID: 1828)
- BitLockerToGo.exe (PID: 1764)
Checks proxy server information
- msiexec.exe (PID: 6324)
- explorer.exe (PID: 6768)
- powershell.exe (PID: 7132)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6324)
Creates files or folders in the user directory
- msiexec.exe (PID: 6324)
- msiexec.exe (PID: 6272)
- UnRAR.exe (PID: 6560)
- explorer.exe (PID: 6768)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6272)
Reads the software policy settings
- msiexec.exe (PID: 6324)
- explorer.exe (PID: 6768)
- BitLockerToGo.exe (PID: 1764)
- slui.exe (PID: 6640)
Reads Environment values
- msiexec.exe (PID: 6324)
Creates a software uninstall entry
- msiexec.exe (PID: 6272)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6768)
Create files in a temporary directory
- explorer.exe (PID: 6768)
Disables trace logs
- powershell.exe (PID: 7132)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7132)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7132)
Drops the executable file immediately after the start
- explorer.exe (PID: 6768)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 7132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {A3B69905-389C-4777-92FB-F2E072712230} |
| Words: | 10 |
| Subject: | TroxApp |
| Author: | Troxbox Publish |
| LastModifiedBy: | - |
| Software: | TroxApp |
| Template: | x64;1033 |
| Comments: | This installer database contains the logic and data required to install TroxApp. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2024:07:08 17:55:21 |
| ModifyDate: | 2024:07:08 17:55:21 |
| LastPrinted: | 2024:07:08 17:55:21 |
| Pages: | 450 |
Total processes
154
Monitored processes
16
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1764 | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1828 | "C:\Users\admin\AppData\Local\Temp\almN7rbxCGlw09n\svchost.exe" | C:\Users\admin\AppData\Local\Temp\almN7rbxCGlw09n\svchost.exe | — | explorer.exe | |||||||||||
User: admin Company: Abelssoft Integrity Level: MEDIUM Description: FileCryptor 2024 Exit code: 666 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6180 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\5b3a41ed8a9a619b4aa18cef611c94b3273671ad464847cbfa600a6571c64431.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6324 | C:\Windows\syswow64\MsiExec.exe -Embedding 739FE92DC1E55C03B737787F0F2F1536 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6428 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6560 | "C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\UnRAR.exe" x -p2161183588a "C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\nijboq.rar" "C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\" | C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\UnRAR.exe | msiexec.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: Command line RAR Exit code: 0 Version: 7.1.0 Modules
| |||||||||||||||
| 6568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UnRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6708 | "C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\rnpkeys.exe" | C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\rnpkeys.exe | msiexec.exe | ||||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 3221226505 Version: 115.6.0 Modules
| |||||||||||||||
Total events
23 180
Read events
22 694
Write events
477
Delete events
9
Modification events
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 80180000F54B4111B5D2DA01 | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 4C5D2B4D239BFC5FE3D4B91B653F27C4F4105740ED135C29D02C998B250FED42 | |||
| (PID) Process: | (6272) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6324) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6324) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6324) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6324) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6324) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6324) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6324) msiexec.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
90
Suspicious files
58
Text files
11
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6272 | msiexec.exe | C:\WINDOWS\Installer\1d0ff1.msi | — | |
MD5:— | SHA256:— | |||
| 6272 | msiexec.exe | C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\uiaehuv.rar | — | |
MD5:— | SHA256:— | |||
| 6272 | msiexec.exe | C:\WINDOWS\Installer\MSI10BC.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 6272 | msiexec.exe | C:\WINDOWS\Installer\MSI1224.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 6272 | msiexec.exe | C:\Users\admin\AppData\Roaming\Troxbox Publish\TroxApp\UnRAR.exe | executable | |
MD5:98CCD44353F7BC5BAD1BC6BA9AE0CD68 | SHA256:E51021F6CB20EFBD2169F2A2DA10CE1ABCA58B4F5F30FBF4BAE931E4ECAAC99B | |||
| 6272 | msiexec.exe | C:\WINDOWS\TEMP\~DFA6B2AAFDCB70CFCF.TMP | binary | |
MD5:B778BD868900E8655D55CFE491E36EED | SHA256:E320EB6B7286611ADFFCB28CB81F83AA9A127FC0C8E78A6FF87B30EF7736509F | |||
| 6272 | msiexec.exe | C:\WINDOWS\Installer\MSI12C2.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 6272 | msiexec.exe | C:\WINDOWS\Installer\MSI19CA.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
| 6272 | msiexec.exe | C:\WINDOWS\Installer\MSI136F.tmp | executable | |
MD5:1A2B237796742C26B11A008D0B175E29 | SHA256:81E0DF47BCB2B3380FB0FB58B0D673BE4EF1B0367FD2B0D80AB8EE292FC8F730 | |||
| 6272 | msiexec.exe | C:\WINDOWS\Installer\MSI1283.tmp | executable | |
MD5:B158D8D605571EA47A238DF5AB43DFAA | SHA256:CA763693CC25D316F14A9EBAD80EBF00590329550C45ADB7E5205486533C2504 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
92
DNS requests
28
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6072 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6768 | explorer.exe | GET | 200 | 104.21.68.5:80 | http://hit-1488.com/test_gate0117.php?a=XyLGVaXA1cIfBjj&id=0 | unknown | — | — | unknown |
1792 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1792 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6768 | explorer.exe | GET | 200 | 142.250.185.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
6640 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
6768 | explorer.exe | GET | 301 | 188.114.97.3:80 | http://run-df.com/gAySB.php?cnv_id=false&value=1 | unknown | — | — | unknown |
5116 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6768 | explorer.exe | GET | 200 | 104.21.68.5:80 | http://hit-1488.com/gate2.php?a=xF9FC7UHFPghH50v9OYEx509Qn3PKPOmxoYTbAuMq7R0JCH6%2FZcar2RpHQASgdGu42OpAhKXQIvMociS4WrT5cbJR6IIfS23ebC1ZkexcbI7Q6iBIuLruxQ13CWO5Bj72PpcR2chja%2BZXS9Mi9VRF550YMz%2F11SlZgRjN7yt25%2BLxAEVm3QHFI2aaI8zd0hQcCGppRO3NlbZWjmb%2FnlyKcHJJYzVFBszLJ2effbAFysAlwevycjkZZG%2FR69JFafJKIzQ3vgq%2FV6vnK%2Bg2RdLdmHWsg%3D%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
2140 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1792 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4656 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6072 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
get-license2.com |
| unknown |
c.pki.goog |
| unknown |
hit-1488.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (publicitttyps .shop) |
1764 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (publicitttyps .shop in TLS SNI) |
1764 | BitLockerToGo.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
1764 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (publicitttyps .shop in TLS SNI) |
1764 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (publicitttyps .shop in TLS SNI) |
1764 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (publicitttyps .shop in TLS SNI) |
1764 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (publicitttyps .shop in TLS SNI) |
1764 | BitLockerToGo.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Lumma Stealer Related Domain (publicitttyps .shop in TLS SNI) |
Process | Message |
|---|---|
rnpkeys.exe | Not found |