| File name: | 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe |
| Full analysis: | https://app.any.run/tasks/0090ba7f-4109-4761-a0fa-b4888832f68b |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | July 03, 2024, 09:27:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 0B3D97B11E440029D52B34AE6798CFBC |
| SHA1: | F6EC97CAC5DD7FD597ABC69BEFEE89262B1D0EC1 |
| SHA256: | 5B225235D021E0BD9075A79ED7EEAA67E3A360BA9DE6C4D2DB3EE23026A26A2D |
| SSDEEP: | 98304:ksq209v8bORrWUURgzEejD3PMus6bvWpzAkogh7M98me8hxyUZI9qn1myRmo9zWs:o5PKF |
MALICIOUS
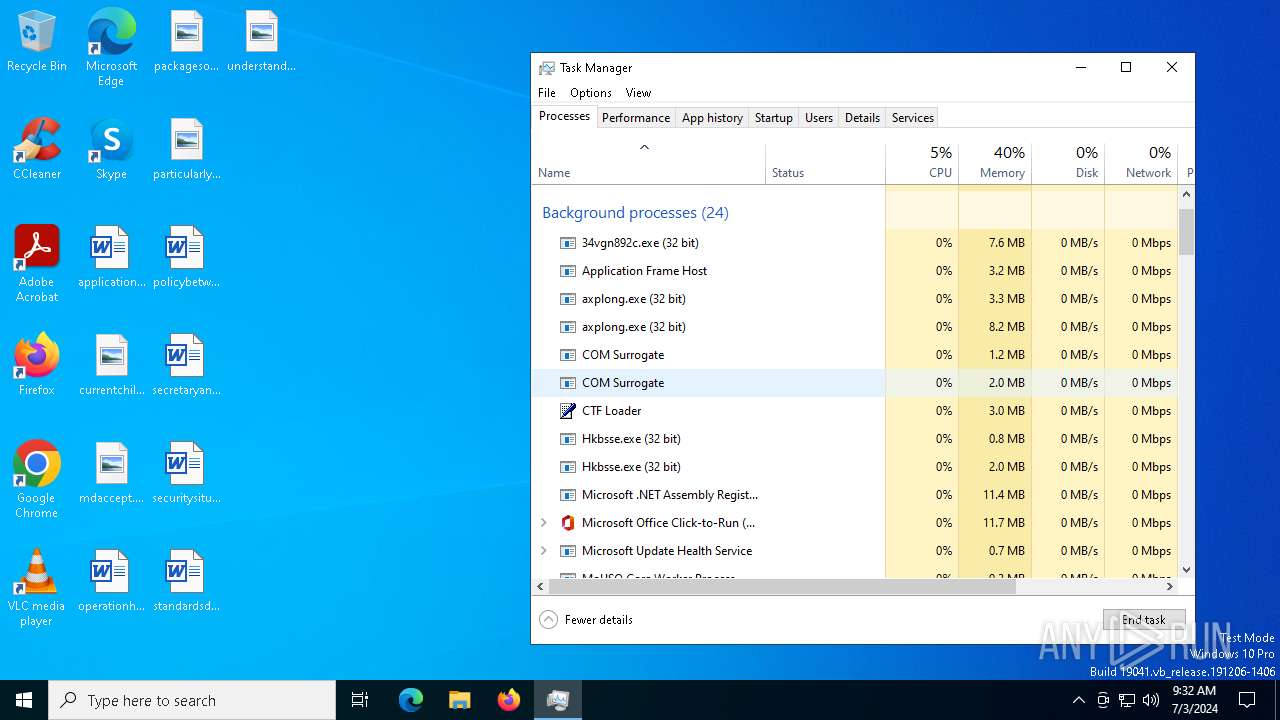
Drops the executable file immediately after the start
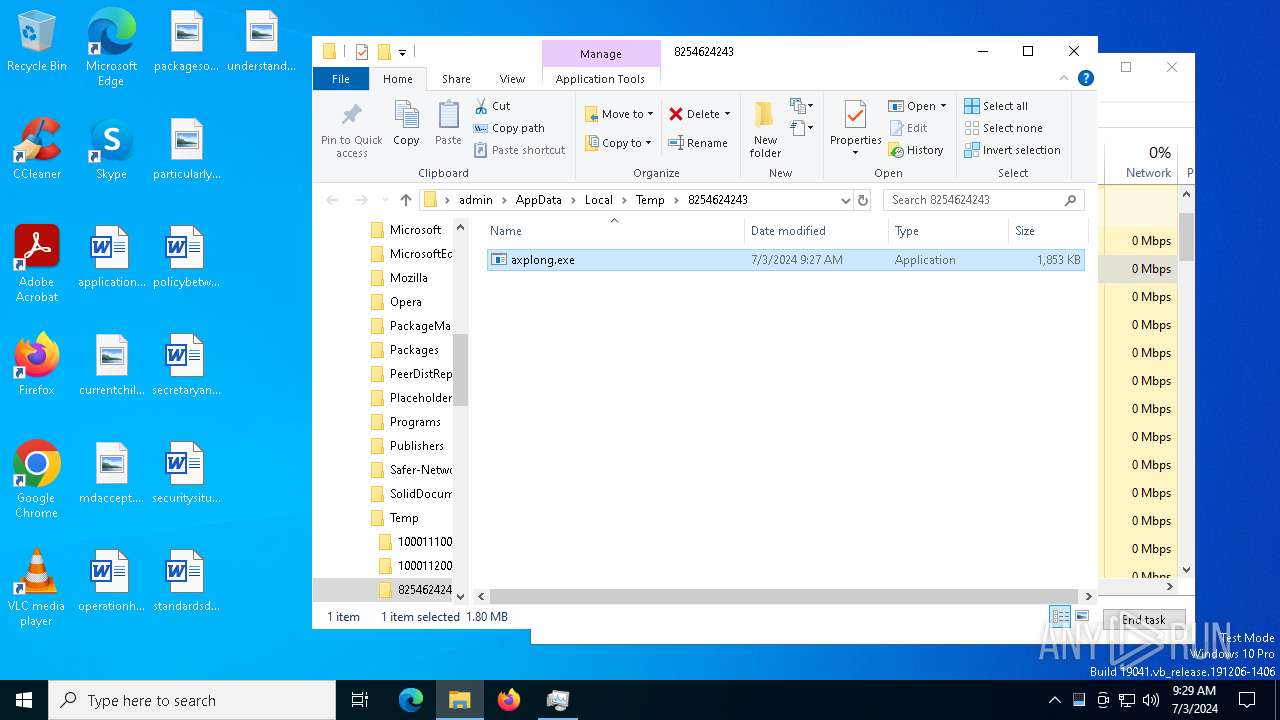
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
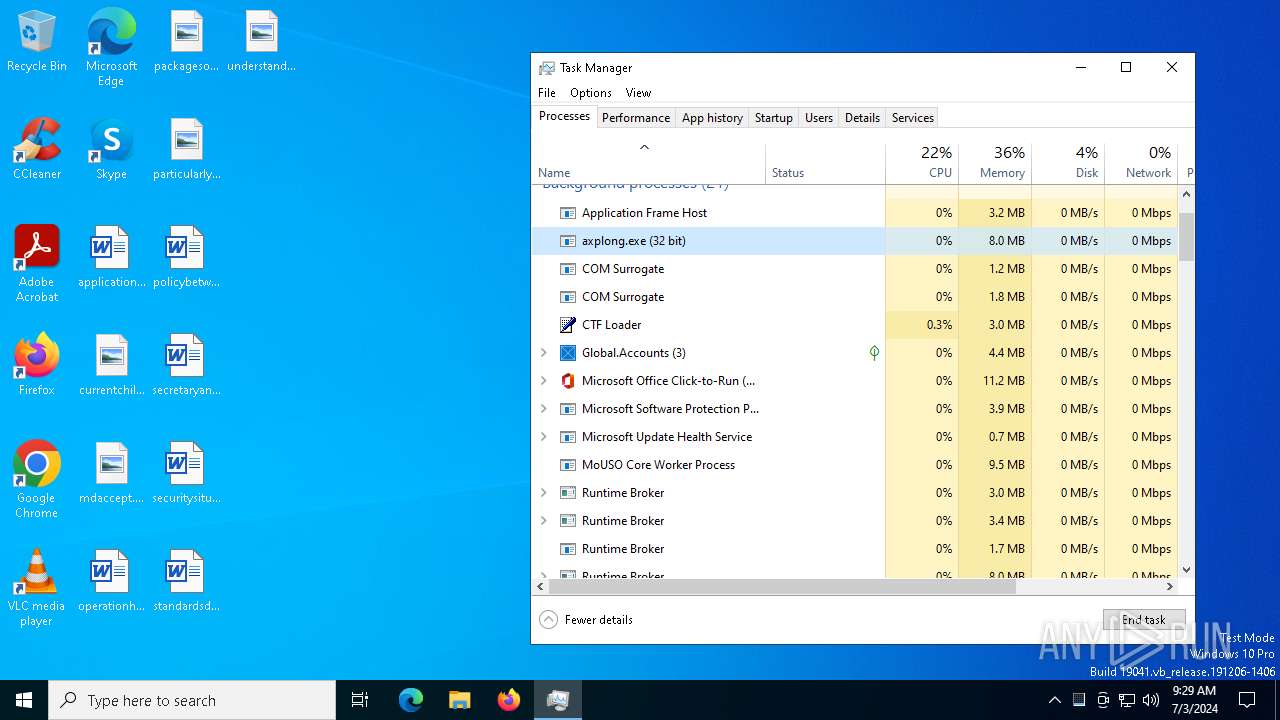
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- Freshbuild.exe (PID: 5940)
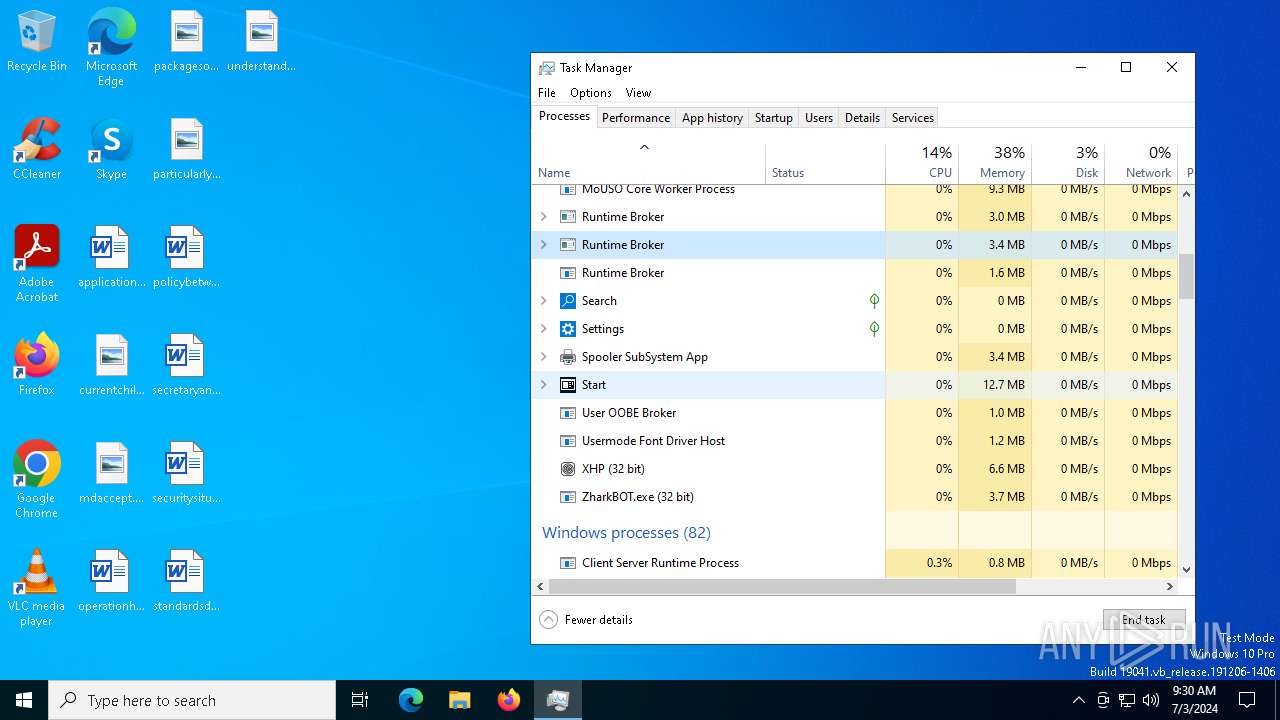
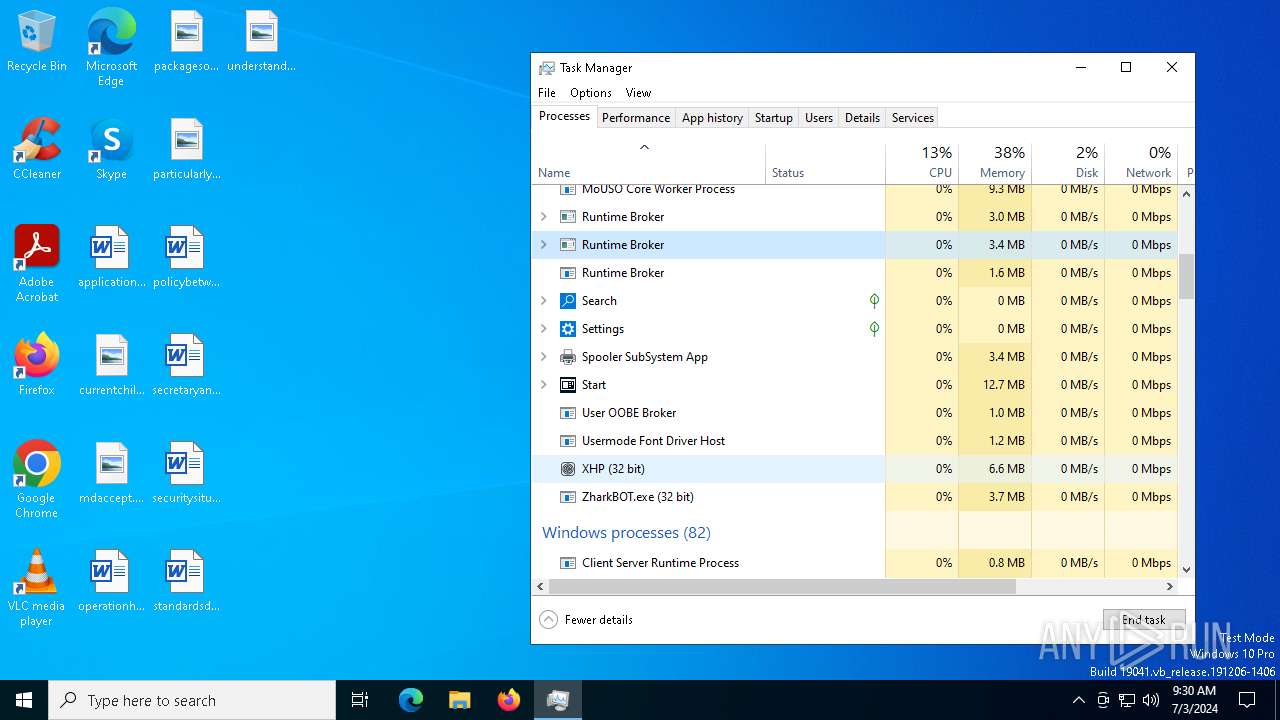
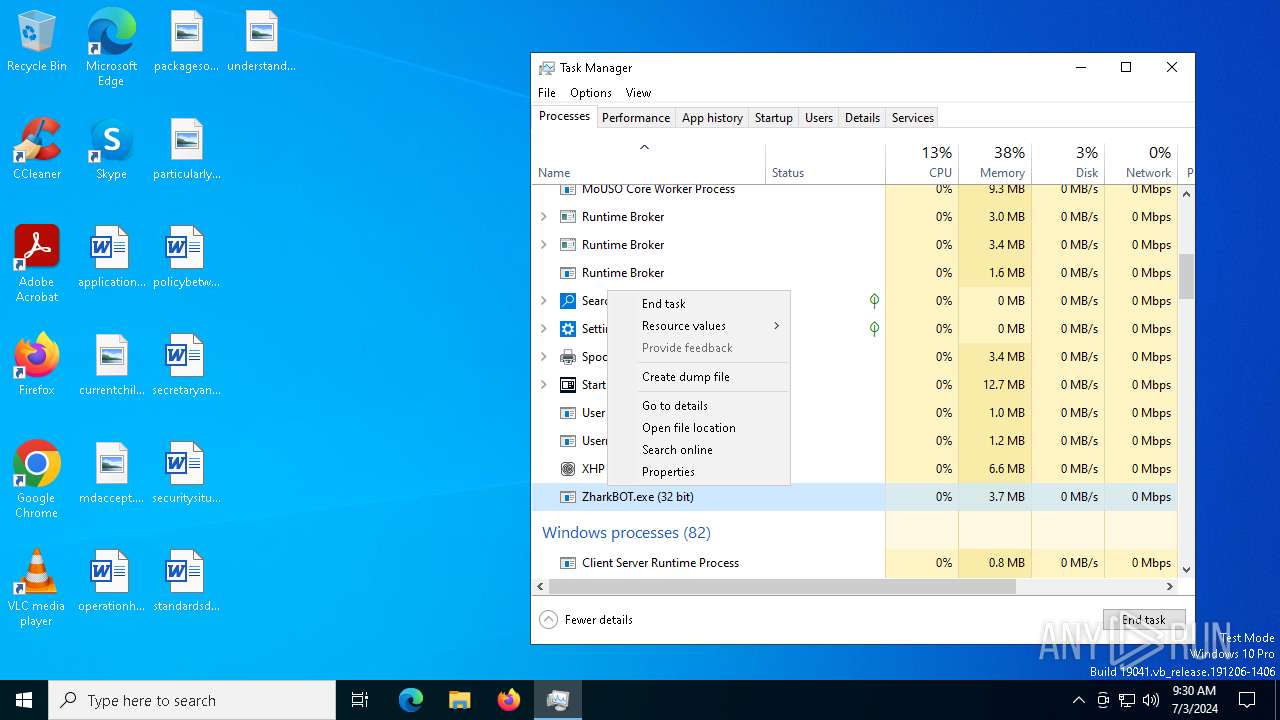
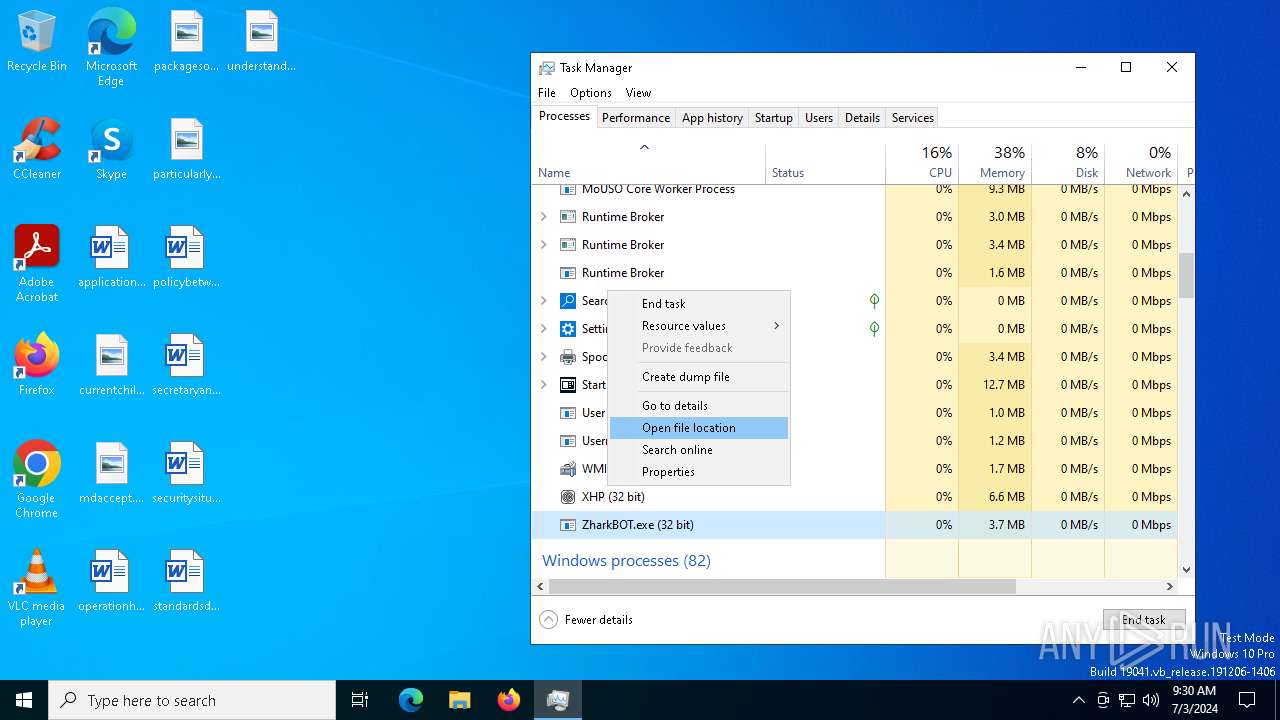
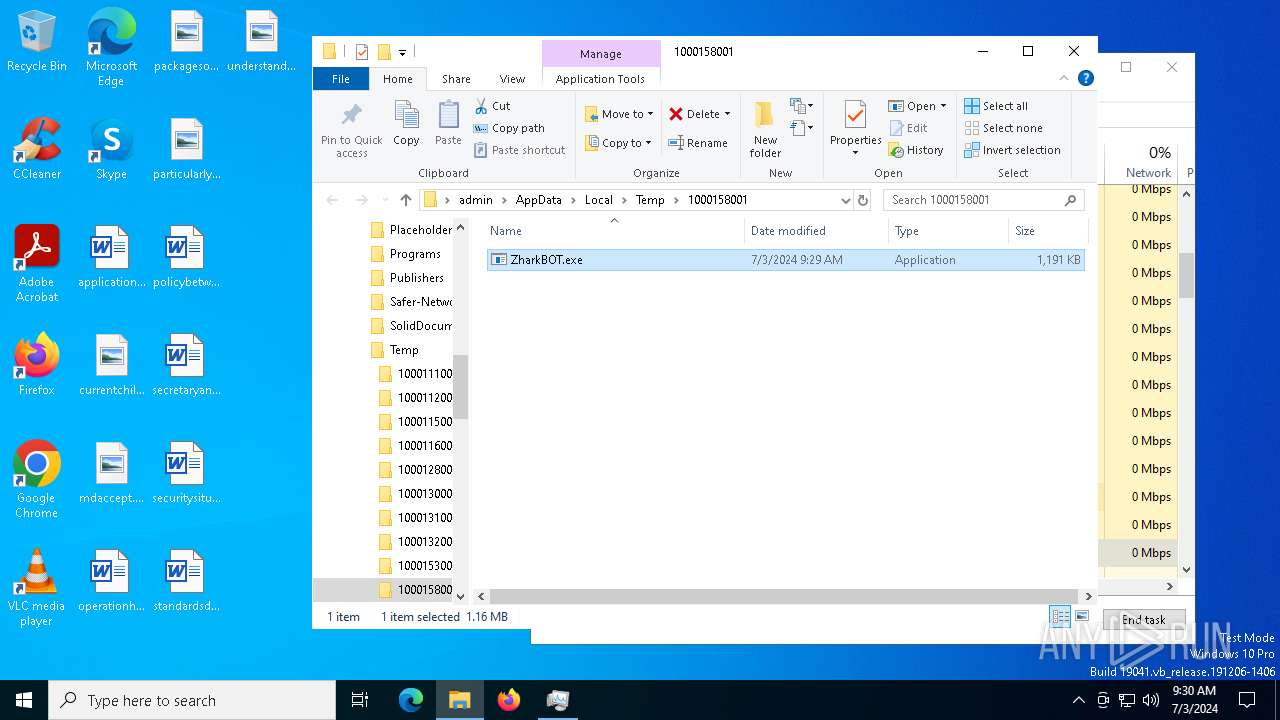
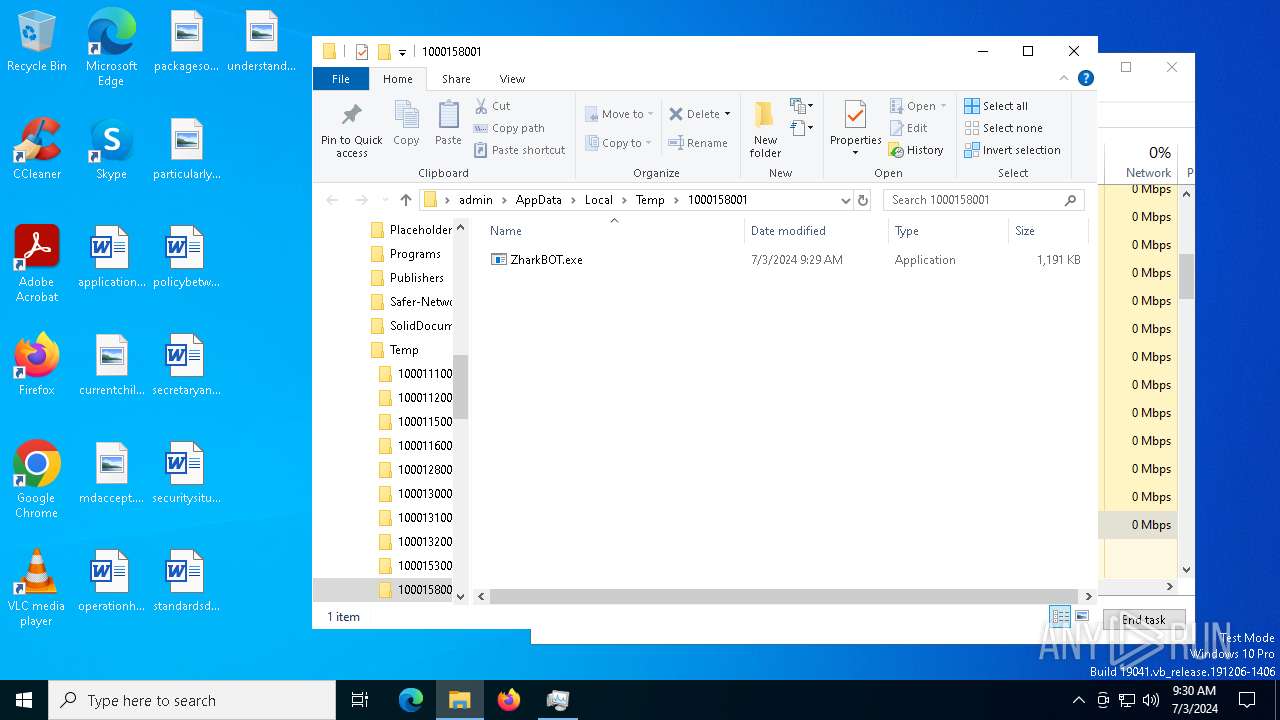
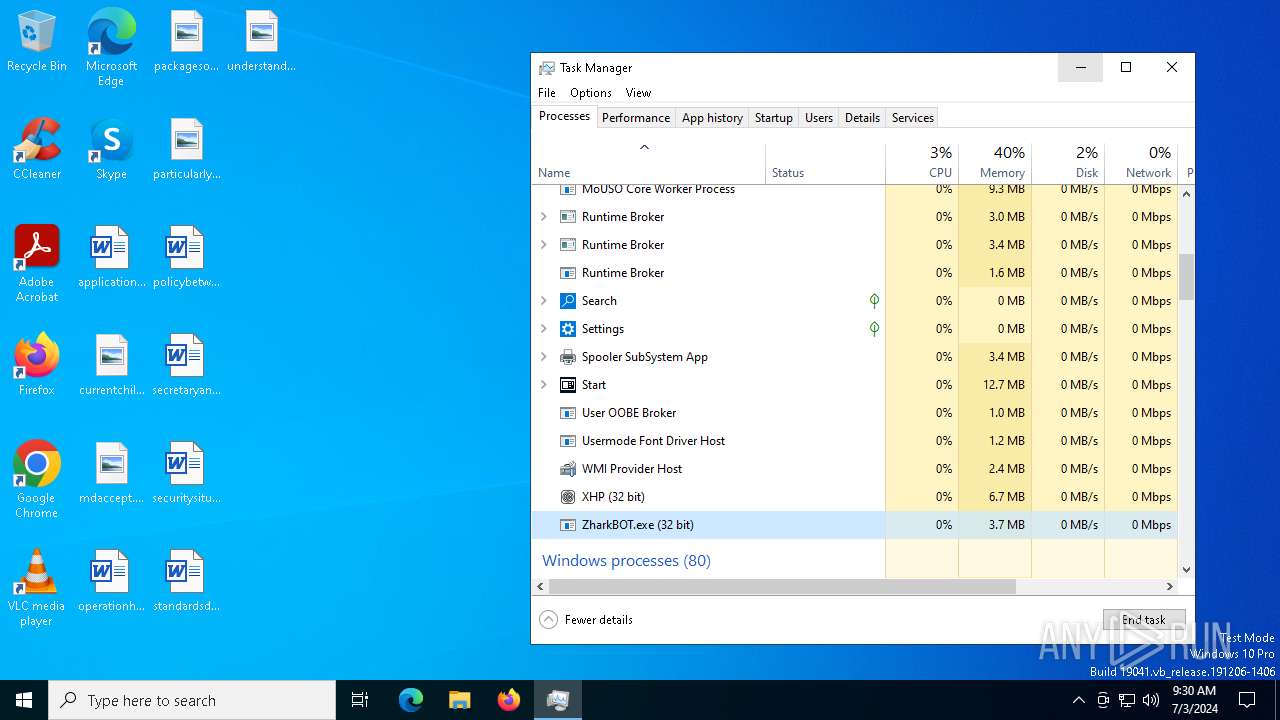
- ZharkBOT.exe (PID: 1960)
Connects to the CnC server
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
AMADEY has been detected (SURICATA)
- axplong.exe (PID: 4220)
- Hkbsse.exe (PID: 2276)
AMADEY has been detected (YARA)
- axplong.exe (PID: 4220)
- Hkbsse.exe (PID: 2276)
STEALC has been detected (SURICATA)
- stealc_zov.exe (PID: 4688)
Amadey has been detected
- Freshbuild.exe (PID: 5940)
- Hkbsse.exe (PID: 2276)
- Hkbsse.exe (PID: 8)
- Hkbsse.exe (PID: 2208)
- Hkbsse.exe (PID: 5576)
Steals credentials from Web Browsers
- stealc_zov.exe (PID: 4688)
REDLINE has been detected (YARA)
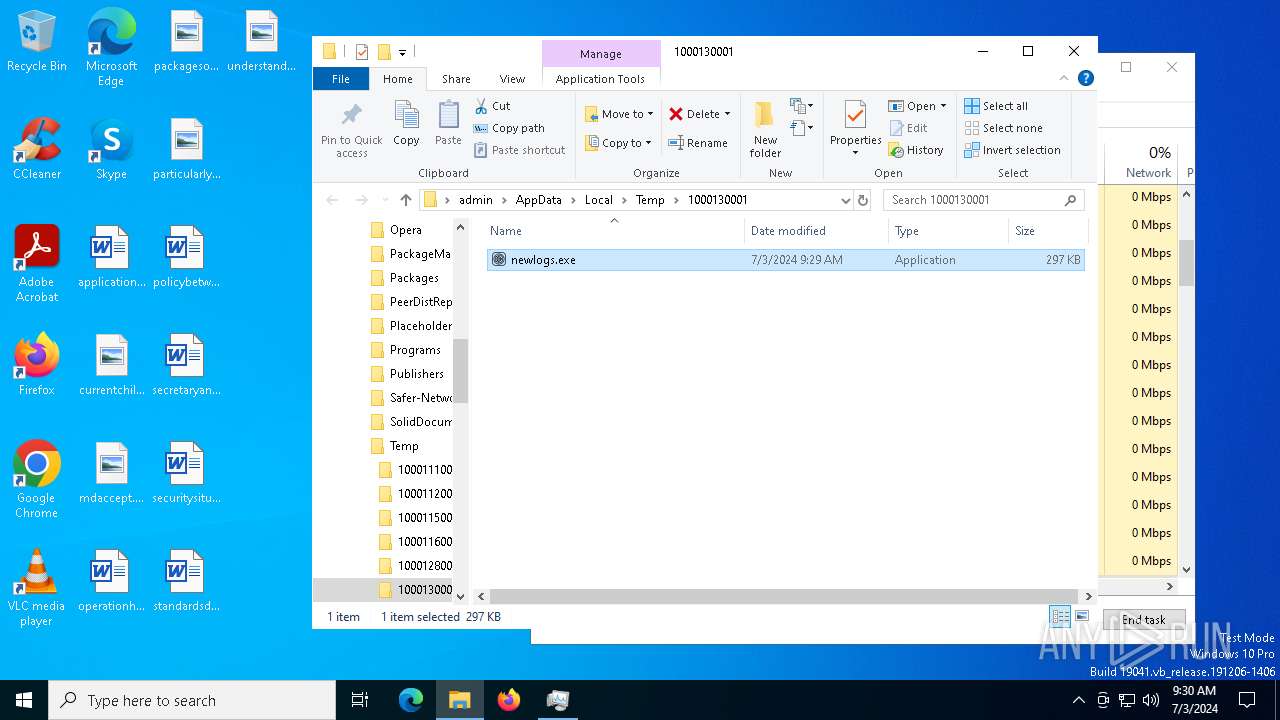
- RegAsm.exe (PID: 3680)
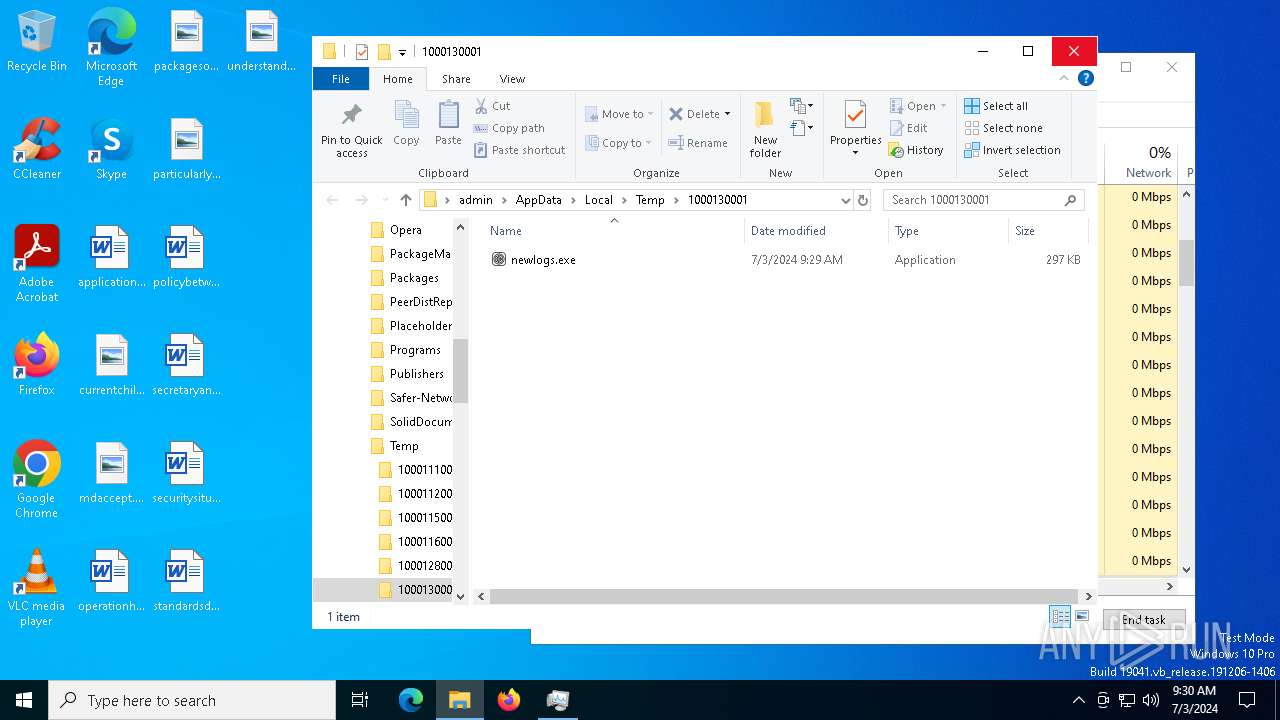
- newlogs.exe (PID: 3888)
LUMMA has been detected (SURICATA)
- BitLockerToGo.exe (PID: 5980)
Changes the autorun value in the registry
- 34vgn892c.exe (PID: 4756)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 5980)
- stealc_zov.exe (PID: 4688)
SUSPICIOUS
Executable content was dropped or overwritten
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- Freshbuild.exe (PID: 5940)
- ZharkBOT.exe (PID: 1960)
Reads the BIOS version
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- axplong.exe (PID: 2088)
- axplong.exe (PID: 4852)
- axplong.exe (PID: 1992)
- axplong.exe (PID: 3840)
Reads the date of Windows installation
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- Freshbuild.exe (PID: 5940)
Reads security settings of Internet Explorer
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- Freshbuild.exe (PID: 5940)
- Hkbsse.exe (PID: 2276)
- 34vgn892c.exe (PID: 4756)
Starts itself from another location
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- Freshbuild.exe (PID: 5940)
- ZharkBOT.exe (PID: 1960)
Connects to the server without a host name
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- 34vgn892c.exe (PID: 4756)
Contacting a server suspected of hosting an CnC
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- Hkbsse.exe (PID: 2276)
- BitLockerToGo.exe (PID: 5980)
Checks Windows Trust Settings
- axplong.exe (PID: 4220)
The process executes via Task Scheduler
- axplong.exe (PID: 2088)
- Hkbsse.exe (PID: 8)
- axplong.exe (PID: 4852)
- Hkbsse.exe (PID: 2208)
- axplong.exe (PID: 1992)
- Hkbsse.exe (PID: 5576)
- axplong.exe (PID: 3840)
Connects to unusual port
- axplong.exe (PID: 4220)
- newlogs.exe (PID: 3888)
- RegAsm.exe (PID: 3680)
Potential Corporate Privacy Violation
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
Process requests binary or script from the Internet
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
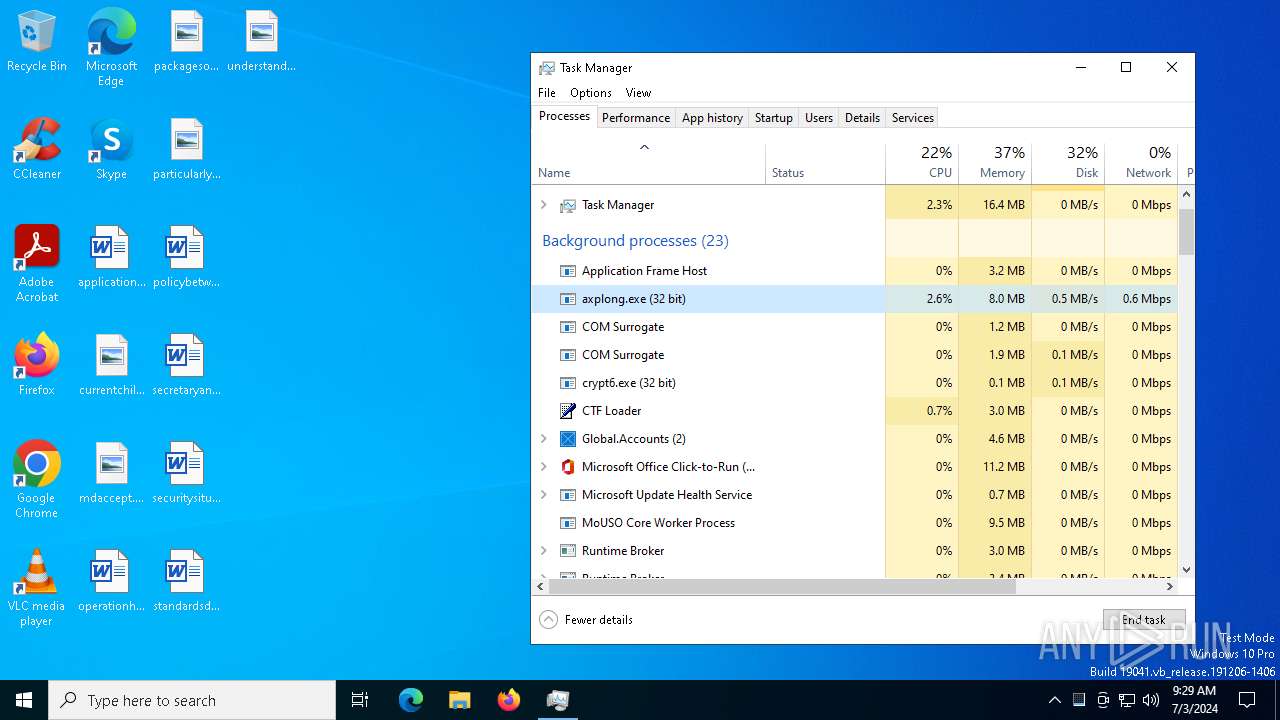
Executes application which crashes
- crypt6.exe (PID: 5636)
Windows Defender mutex has been found
- stealc_zov.exe (PID: 4688)
Searches for installed software
- stealc_zov.exe (PID: 4688)
- BitLockerToGo.exe (PID: 5980)
The process drops Mozilla's DLL files
- stealc_zov.exe (PID: 4688)
Process drops legitimate windows executable
- stealc_zov.exe (PID: 4688)
The process drops C-runtime libraries
- stealc_zov.exe (PID: 4688)
The process checks if it is being run in the virtual environment
- ZharkBOT.exe (PID: 1960)
- 34vgn892c.exe (PID: 4756)
There is functionality for VM detection (VMWare)
- 34vgn892c.exe (PID: 4756)
There is functionality for VM detection (Parallels)
- 34vgn892c.exe (PID: 4756)
INFO
Checks supported languages
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- axplong.exe (PID: 2088)
- crypt6.exe (PID: 5636)
- RegAsm.exe (PID: 3680)
- newlogs.exe (PID: 3888)
- stealc_zov.exe (PID: 4688)
- newbuild.exe (PID: 752)
- Freshbuild.exe (PID: 5940)
- ZharkBOT.exe (PID: 1960)
- Hkbsse.exe (PID: 2276)
- Hkbsse.exe (PID: 8)
- axplong.exe (PID: 4852)
- 34vgn892c.exe (PID: 4756)
- BitLockerToGo.exe (PID: 5980)
- Hkbsse.exe (PID: 2208)
- axplong.exe (PID: 1992)
- Hkbsse.exe (PID: 5576)
- axplong.exe (PID: 3840)
Reads Environment values
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- Freshbuild.exe (PID: 5940)
- Hkbsse.exe (PID: 2276)
- ZharkBOT.exe (PID: 1960)
- 34vgn892c.exe (PID: 4756)
Reads the computer name
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- RegAsm.exe (PID: 3680)
- newlogs.exe (PID: 3888)
- Freshbuild.exe (PID: 5940)
- ZharkBOT.exe (PID: 1960)
- Hkbsse.exe (PID: 2276)
- 34vgn892c.exe (PID: 4756)
- stealc_zov.exe (PID: 4688)
- BitLockerToGo.exe (PID: 5980)
Process checks computer location settings
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- Freshbuild.exe (PID: 5940)
Create files in a temporary directory
- 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe (PID: 1412)
- axplong.exe (PID: 4220)
- Freshbuild.exe (PID: 5940)
Checks proxy server information
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- WerFault.exe (PID: 4772)
- Hkbsse.exe (PID: 2276)
- 34vgn892c.exe (PID: 4756)
Reads the machine GUID from the registry
- axplong.exe (PID: 4220)
- RegAsm.exe (PID: 3680)
- newlogs.exe (PID: 3888)
Creates files or folders in the user directory
- axplong.exe (PID: 4220)
- stealc_zov.exe (PID: 4688)
- WerFault.exe (PID: 4772)
Themida protector has been detected
- axplong.exe (PID: 4220)
Reads the software policy settings
- axplong.exe (PID: 4220)
- WerFault.exe (PID: 4772)
- BitLockerToGo.exe (PID: 5980)
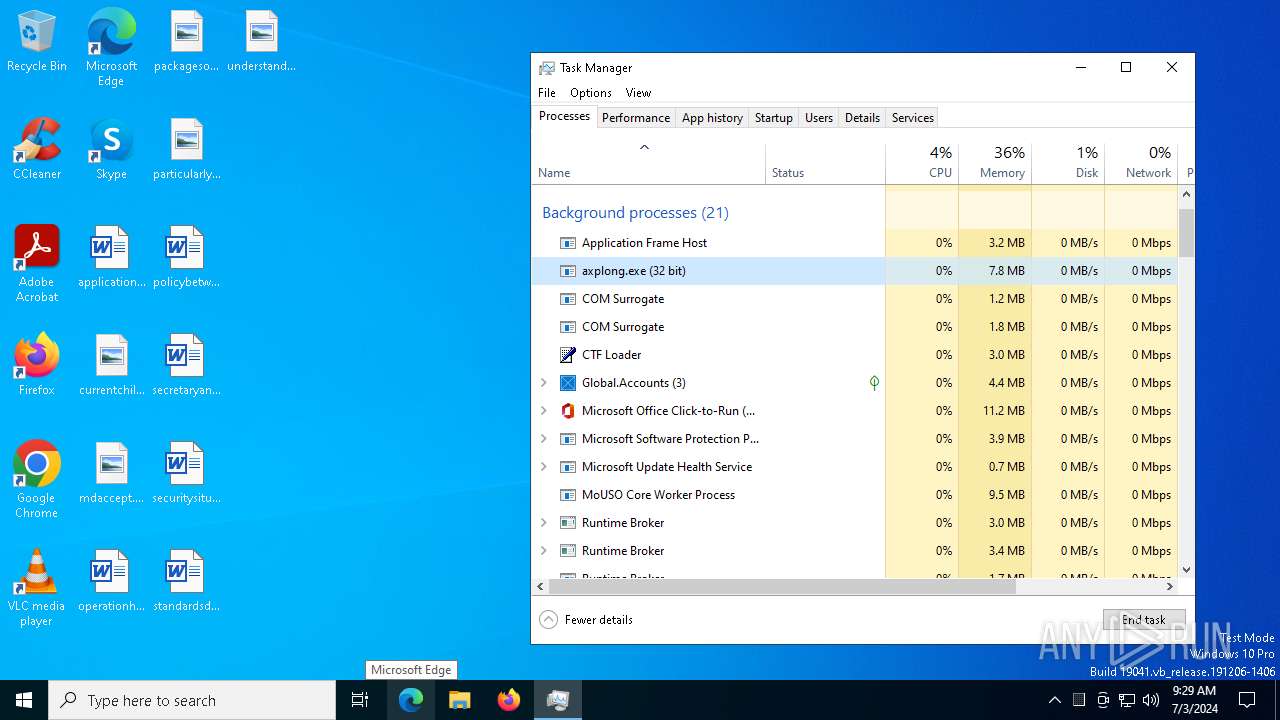
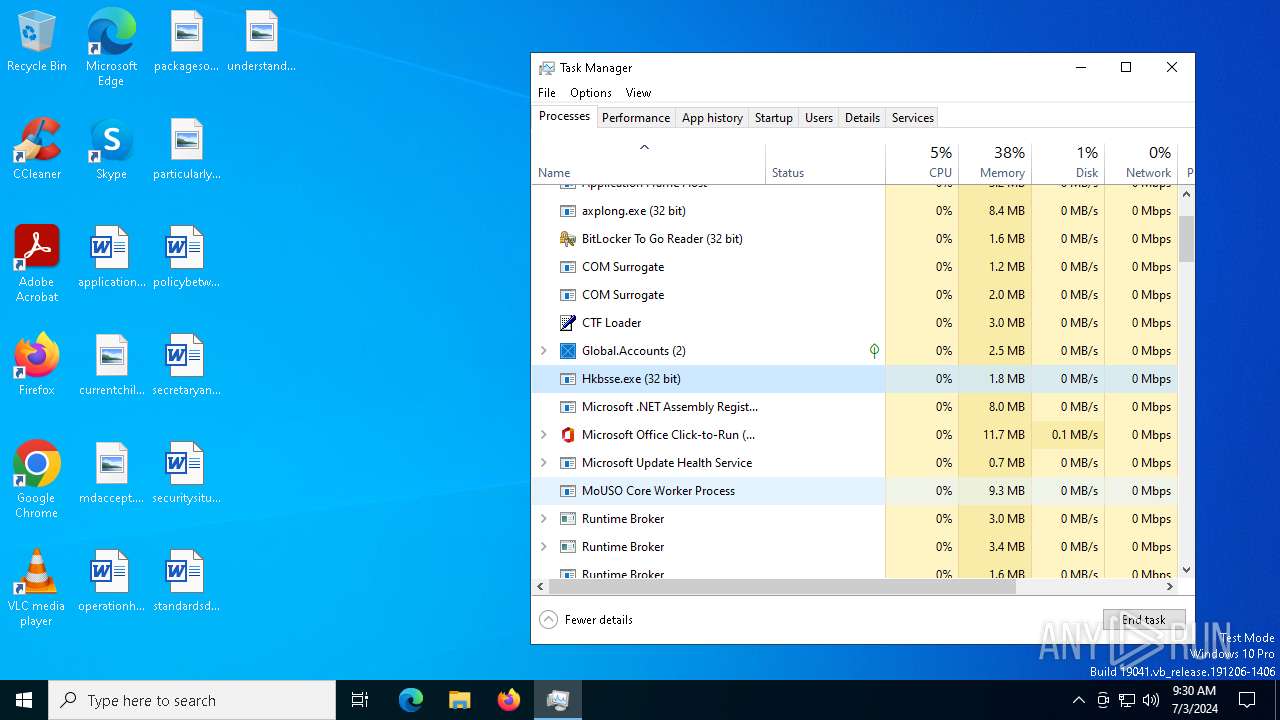
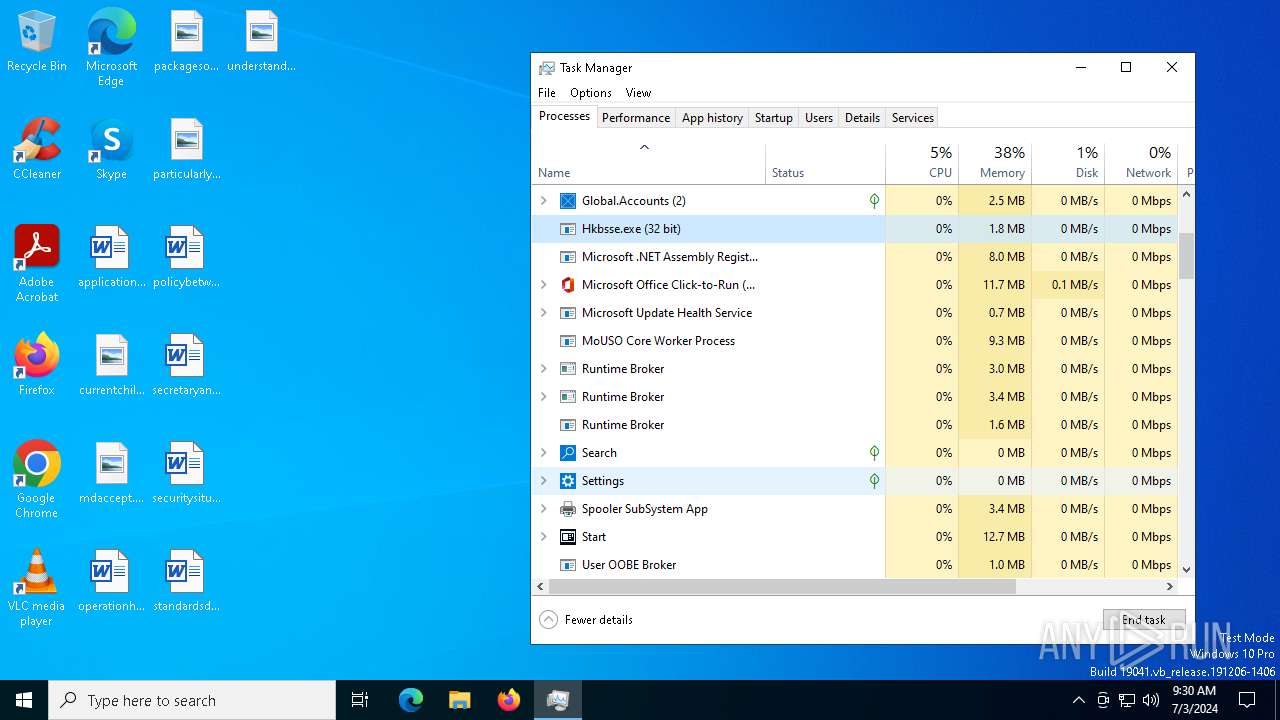
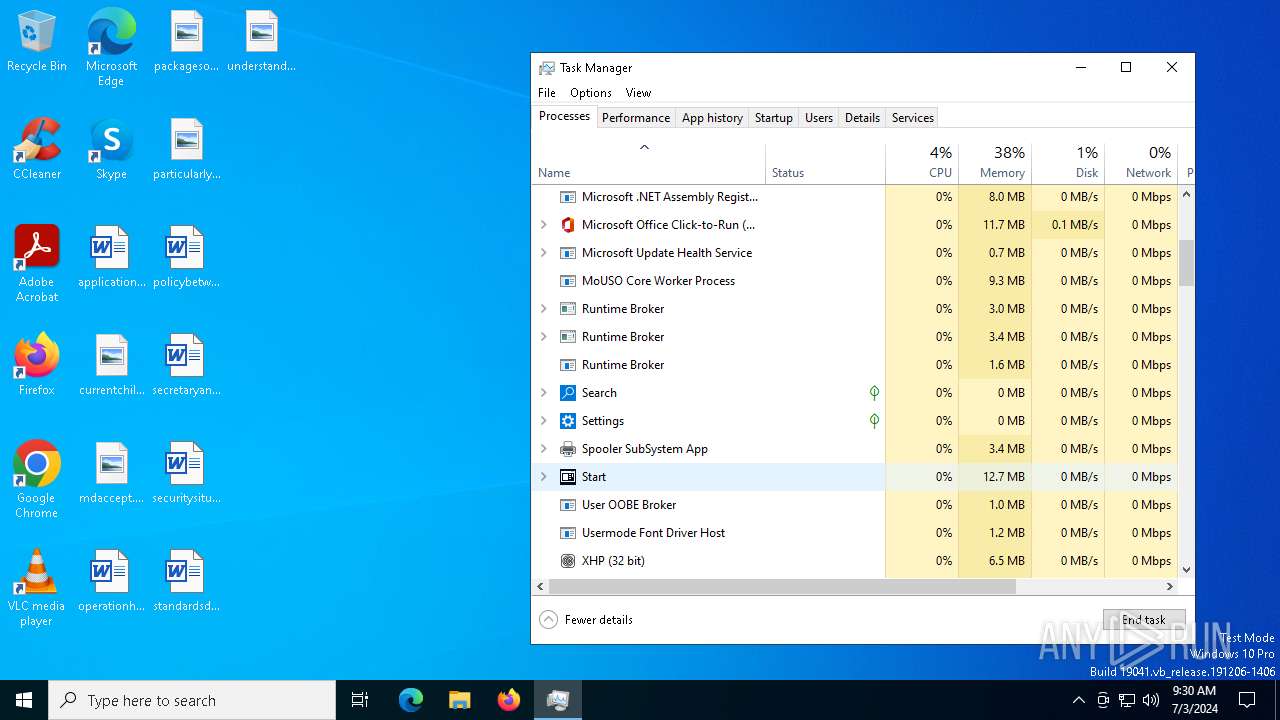
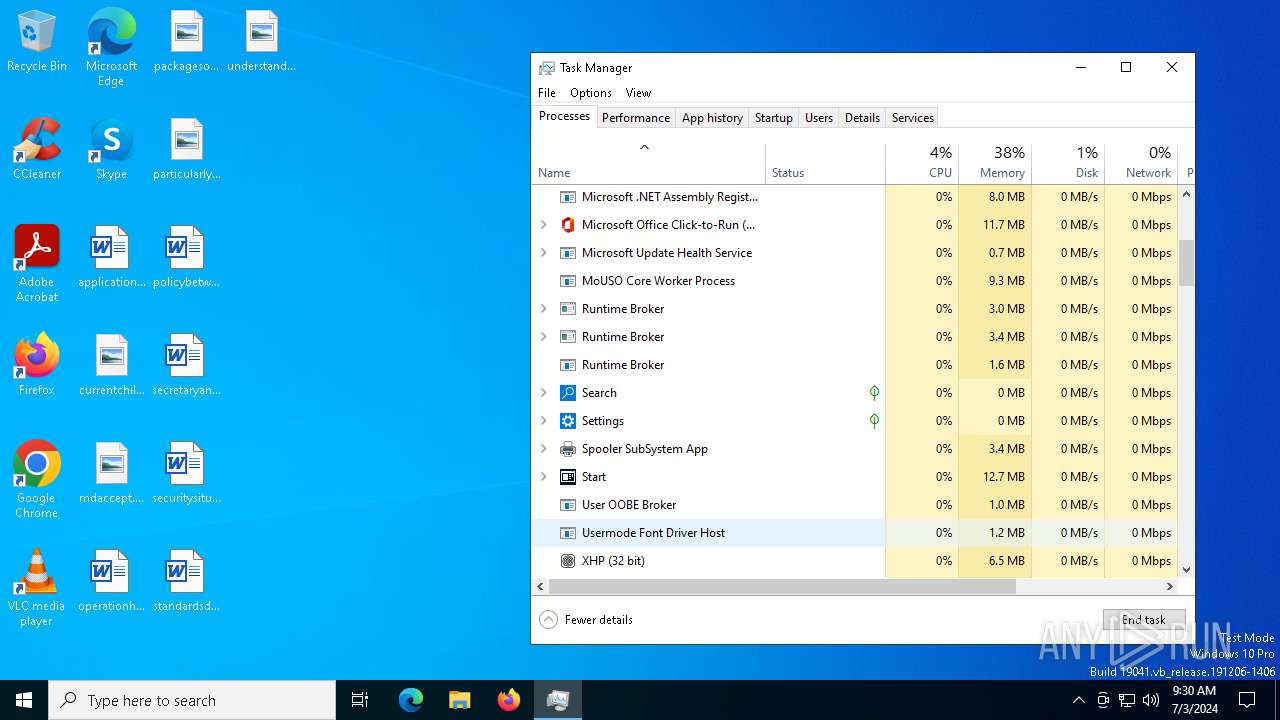
Manual execution by a user
- Taskmgr.exe (PID: 5956)
- Taskmgr.exe (PID: 1436)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 1436)
Reads CPU info
- stealc_zov.exe (PID: 4688)
Reads product name
- stealc_zov.exe (PID: 4688)
Creates files in the program directory
- stealc_zov.exe (PID: 4688)
- ZharkBOT.exe (PID: 1960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(4220) axplong.exe
C277.91.77.81
URLhttp://77.91.77.81/Kiru9gu/index.php
Version4.30
Options
Drop directory8254624243
Drop nameaxplong.exe
Strings (113)2019
un:
.jpg
Content-Type: application/x-www-form-urlencoded
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
vs:
4.30
/Kiru9gu/index.php
Avira
&unit=
=
-executionpolicy remotesigned -File "
<c>
:::
rundll32
" && timeout 1 && del
POST
dm:
ESET
2022
Comodo
"taskkill /f /im "
st=s
-%lu
Bitdefender
2016
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
&& Exit"
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
d1
Powershell.exe
axplong.exe
ComputerName
sd:
" && ren
<d>
r=
\App
ProgramData\
https://
WinDefender
#
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
id:
pc:
/k
Content-Type: multipart/form-data; boundary=----
VideoID
wb
rb
lv:
Startup
------
\0000
AVAST Software
77.91.77.81
GetNativeSystemInfo
rundll32.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
cmd /C RMDIR /s/q
Main
ProductName
\
SOFTWARE\Microsoft\Windows NT\CurrentVersion
av:
+++
-unicode-
&&
e0
cmd
bi:
DefaultSettings.XResolution
AVG
os:
--
Norton
S-%lu-
?scr=1
Content-Disposition: form-data; name="data"; filename="
"
8254624243
kernel32.dll
GET
DefaultSettings.YResolution
SYSTEM\ControlSet001\Services\BasicDisplay\Video
|
ps1
/Plugins/
dll
og:
Sophos
%-lu
Programs
abcdefghijklmnopqrstuvwxyz0123456789-_
random
------
Panda Security
0123456789
cred.dll|clip.dll|
Rem
CurrentBuild
http://
Kaspersky Lab
ar:
%USERPROFILE%
shell32.dll
360TotalSecurity
Doctor Web
e1
(PID) Process(2276) Hkbsse.exe
C2185.172.128.116
URLhttp://185.172.128.116/Mb3GvQs8/index.php
Version4.30
Options
Drop directoryb66a8ae076
Drop nameHkbsse.exe
Strings (113)2019
un:
.jpg
Content-Type: application/x-www-form-urlencoded
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
vs:
4.30
Avira
&unit=
=
-executionpolicy remotesigned -File "
<c>
:::
Hkbsse.exe
rundll32
" && timeout 1 && del
POST
dm:
ESET
2022
Comodo
"taskkill /f /im "
st=s
-%lu
Bitdefender
2016
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
&& Exit"
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
d1
Powershell.exe
ComputerName
sd:
" && ren
<d>
r=
\App
ProgramData\
https://
WinDefender
#
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
id:
pc:
/k
Content-Type: multipart/form-data; boundary=----
VideoID
wb
rb
lv:
Startup
------
\0000
AVAST Software
GetNativeSystemInfo
rundll32.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
cmd /C RMDIR /s/q
Main
ProductName
\
SOFTWARE\Microsoft\Windows NT\CurrentVersion
av:
+++
-unicode-
&&
e0
cmd
bi:
DefaultSettings.XResolution
AVG
os:
--
Norton
S-%lu-
?scr=1
Content-Disposition: form-data; name="data"; filename="
"
kernel32.dll
GET
DefaultSettings.YResolution
SYSTEM\ControlSet001\Services\BasicDisplay\Video
185.172.128.116
|
ps1
/Plugins/
dll
og:
b66a8ae076
Sophos
%-lu
Programs
/Mb3GvQs8/index.php
abcdefghijklmnopqrstuvwxyz0123456789-_
random
------
Panda Security
0123456789
cred.dll|clip.dll|
Rem
CurrentBuild
http://
Kaspersky Lab
ar:
%USERPROFILE%
shell32.dll
360TotalSecurity
Doctor Web
e1
RedLine
(PID) Process(3680) RegAsm.exe
C2 (1)4.185.56.82:42687
BotnetLiveTraffoc
Options
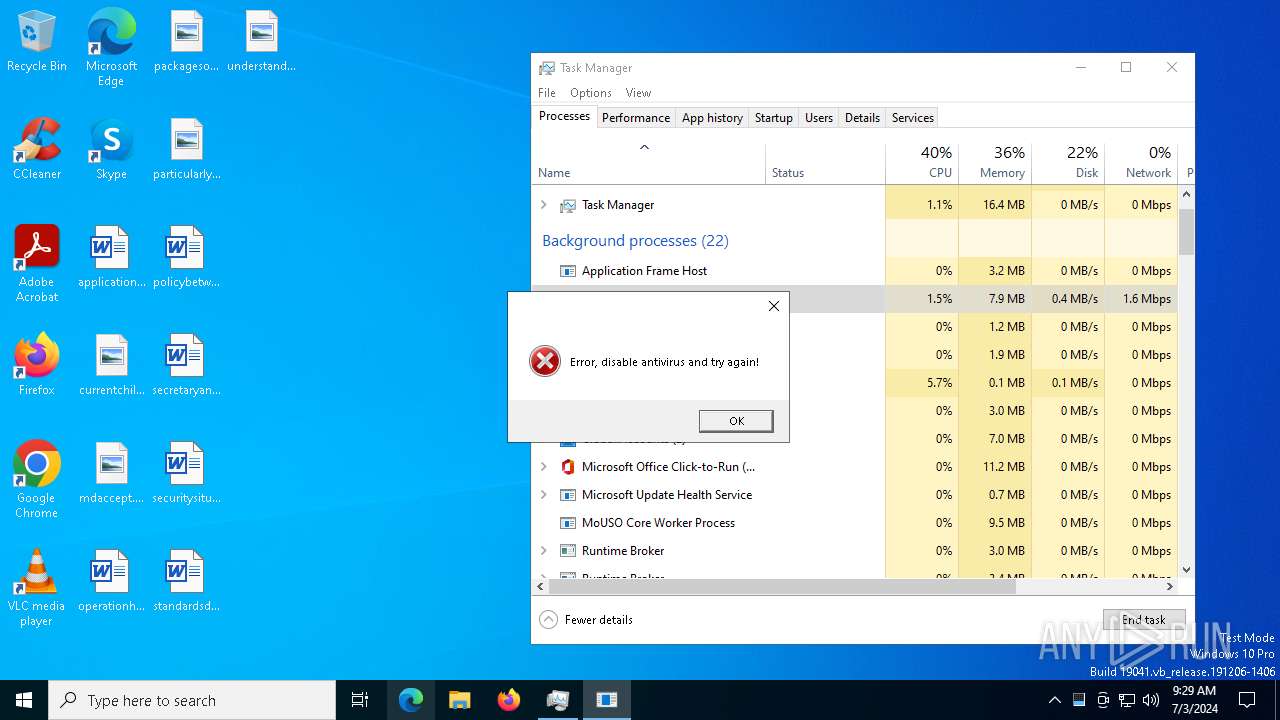
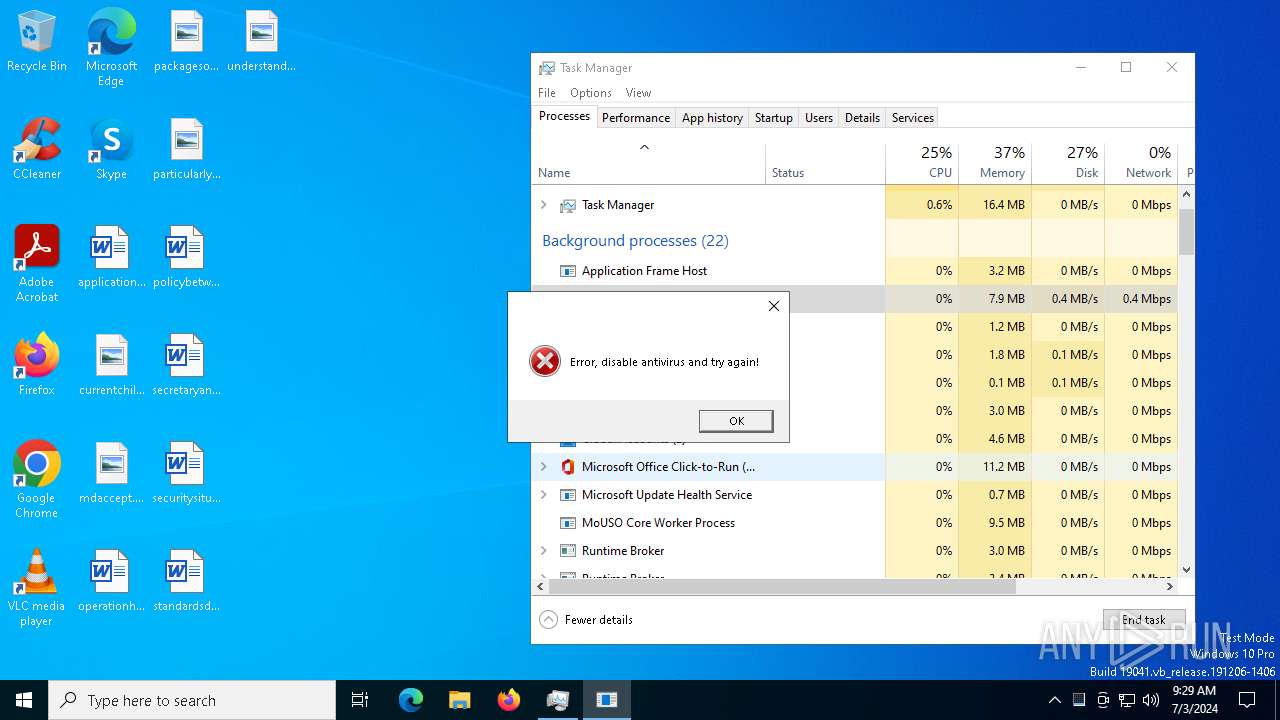
ErrorMessageError, disable antivirus and try again!
Keys
XorUglied
(PID) Process(3888) newlogs.exe
C2 (1)85.28.47.7:17210
Botnetnewlogs
Options
ErrorMessage
Keys
XorCablings
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:06:04 08:24:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 320512 |
| InitializedDataSize: | 116224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4b2000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
164
Monitored processes
24
Malicious processes
19
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe" | C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 752 | "C:\Users\admin\AppData\Local\Temp\1000132001\newbuild.exe" | C:\Users\admin\AppData\Local\Temp\1000132001\newbuild.exe | — | axplong.exe | |||||||||||
User: admin Company: Chrome Password Remover Integrity Level: MEDIUM Description: Chrome Password Remover Exit code: 666 Version: 1.1.0.0 Modules
| |||||||||||||||
| 1412 | "C:\Users\admin\AppData\Local\Temp\5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe" | C:\Users\admin\AppData\Local\Temp\5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1436 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1960 | "C:\Users\admin\AppData\Local\Temp\1000158001\ZharkBOT.exe" | C:\Users\admin\AppData\Local\Temp\1000158001\ZharkBOT.exe | axplong.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1992 | "C:\Users\admin\AppData\Local\Temp\8254624243\axplong.exe" | C:\Users\admin\AppData\Local\Temp\8254624243\axplong.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\AppData\Local\Temp\8254624243\axplong.exe" | C:\Users\admin\AppData\Local\Temp\8254624243\axplong.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe" | C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe" | C:\Users\admin\AppData\Local\Temp\b66a8ae076\Hkbsse.exe | Freshbuild.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
Amadey(PID) Process(2276) Hkbsse.exe C2185.172.128.116 URLhttp://185.172.128.116/Mb3GvQs8/index.php Version4.30 Options Drop directoryb66a8ae076 Drop nameHkbsse.exe Strings (113)2019 un: .jpg Content-Type: application/x-www-form-urlencoded SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce exe "
Content-Type: application/octet-stream shutdown -s -t 0 vs: 4.30 Avira &unit= = -executionpolicy remotesigned -File " <c> ::: Hkbsse.exe rundll32 " && timeout 1 && del POST dm: ESET 2022 Comodo "taskkill /f /im " st=s -%lu Bitdefender 2016 SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\ && Exit" SOFTWARE\Microsoft\Windows\CurrentVersion\Run d1 Powershell.exe ComputerName sd: " && ren <d> r= \App ProgramData\ https:// WinDefender # SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName id: pc: /k Content-Type: multipart/form-data; boundary=---- VideoID wb rb lv: Startup ------ \0000 AVAST Software GetNativeSystemInfo rundll32.exe SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders cmd /C RMDIR /s/q Main ProductName \ SOFTWARE\Microsoft\Windows NT\CurrentVersion av: +++ -unicode- && e0 cmd bi: DefaultSettings.XResolution AVG os: -- Norton S-%lu- ?scr=1 Content-Disposition: form-data; name="data"; filename=" " kernel32.dll GET DefaultSettings.YResolution SYSTEM\ControlSet001\Services\BasicDisplay\Video 185.172.128.116 | ps1 /Plugins/ dll og: b66a8ae076 Sophos %-lu Programs /Mb3GvQs8/index.php abcdefghijklmnopqrstuvwxyz0123456789-_ random ------ Panda Security 0123456789 cred.dll|clip.dll| Rem CurrentBuild http:// Kaspersky Lab ar: %USERPROFILE% shell32.dll 360TotalSecurity Doctor Web e1 | |||||||||||||||
| 2708 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 445
Read events
33 136
Write events
308
Delete events
1
Modification events
| (PID) Process: | (1412) 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1412) 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1412) 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1412) 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4220) axplong.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4220) axplong.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4220) axplong.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4220) axplong.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4220) axplong.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4220) axplong.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
31
Suspicious files
25
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1412 | 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe | C:\Users\admin\AppData\Local\Temp\8254624243\axplong.exe | executable | |
MD5:0B3D97B11E440029D52B34AE6798CFBC | SHA256:5B225235D021E0BD9075A79ED7EEAA67E3A360BA9DE6C4D2DB3EE23026A26A2D | |||
| 4220 | axplong.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C31B2498754E340573F1336DE607D619 | binary | |
MD5:D509ABAE05273570229AB9E5AB00E76A | SHA256:5F3C0621C70F8443BB2892A5715503A966106A8C38A5C6818CF4DDE5AEE90F98 | |||
| 4220 | axplong.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | der | |
MD5:552DC6AF3AE6DCA498CF9956056398FE | SHA256:2D7B9BD22AD0BE4420D5ECF7B6285F86CA3A784BF2A8B1F9475BE09AF8B33652 | |||
| 4220 | axplong.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:12670C6363495349B5E545655BA55CD7 | SHA256:934B056419203B600A8CAE54E947046A96B279C2CE6C76AB62553B770B6A643E | |||
| 4220 | axplong.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\whiteheroin[1].exe | executable | |
MD5:88CDC759CB6FECFE270F0C25918FE732 | SHA256:A5EC1058302399DA770F918C41342709675D13B945457E5BF974C80504AAAE0C | |||
| 1412 | 5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe | C:\WINDOWS\Tasks\axplong.job | binary | |
MD5:5AB0A3A0C5F5E2B5B64E78B070437A26 | SHA256:48D38976B465E204EF4E64FF5DEF66A38544FC40484BDED849788CDB498AFCD9 | |||
| 4220 | axplong.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D03E46CD585BBE111C712E6577BC5F07_56B2A1FF8D0F5C5B4060FCF88A1654FE | der | |
MD5:202C078E6E58598FC8537966749EEE3F | SHA256:0336337FACF1186042C4E2C5CBC1708CDF94473AF648BC1E858D8F1D3F1E356C | |||
| 4220 | axplong.exe | C:\Users\admin\AppData\Local\Temp\1000112001\TpWWMUpe0LEV.exe | executable | |
MD5:88CDC759CB6FECFE270F0C25918FE732 | SHA256:A5EC1058302399DA770F918C41342709675D13B945457E5BF974C80504AAAE0C | |||
| 4772 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER8361.tmp.WERInternalMetadata.xml | xml | |
MD5:930F7356966B993CA996B9FC93F511B0 | SHA256:2195CAC940D587CD03B642A3C802781763FB062ED031148A5B66CDC7A14B3467 | |||
| 1436 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
226
DNS requests
35
Threats
65
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6064 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
6064 | svchost.exe | GET | 200 | 23.211.9.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4628 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4220 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
4220 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
4220 | axplong.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/crypt6.exe | unknown | — | — | unknown |
4220 | axplong.exe | POST | 200 | 77.91.77.81:80 | http://77.91.77.81/Kiru9gu/index.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2912 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6064 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3944 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6064 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
6064 | svchost.exe | 23.211.9.92:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4220 | axplong.exe | 77.91.77.81:80 | — | Foton Telecom CJSC | RU | malicious |
4220 | axplong.exe | 104.192.141.1:443 | bitbucket.org | AMAZON-02 | US | unknown |
3040 | OfficeClickToRun.exe | 20.42.73.30:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
bitbucket.org |
| shared |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
bbuseruploads.s3.amazonaws.com |
| shared |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m01.amazontrust.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4220 | axplong.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |
4220 | axplong.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
4220 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4220 | axplong.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4220 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4220 | axplong.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
4220 | axplong.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
4220 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4220 | axplong.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4220 | axplong.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
5b225235d021e0bd9075a79ed7eeaa67e3a360ba9de6c4d2db3ee23026a26a2d.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|