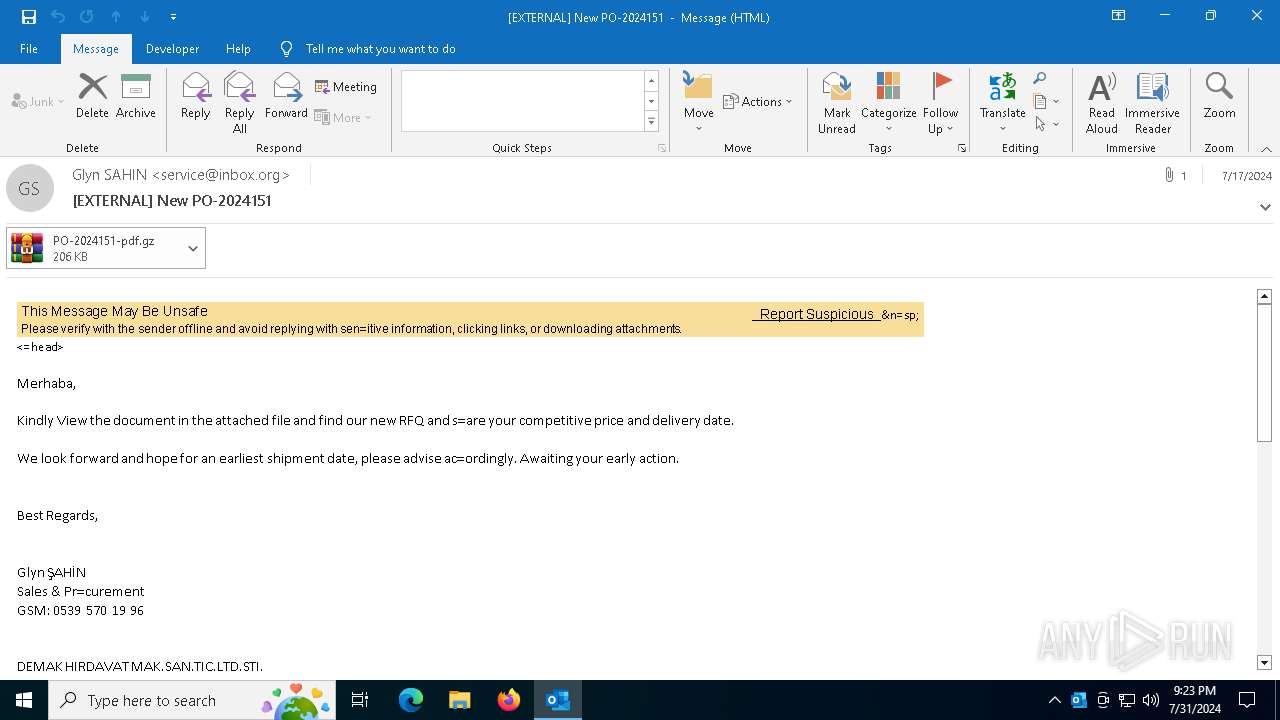
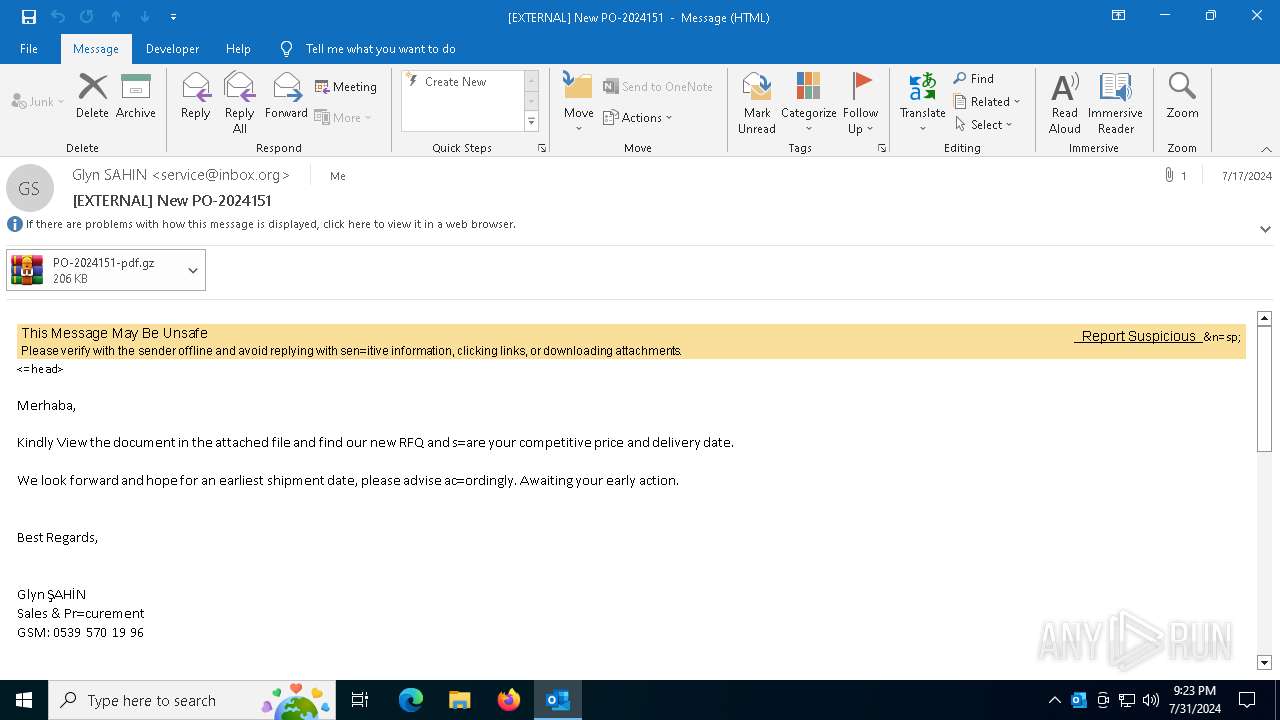
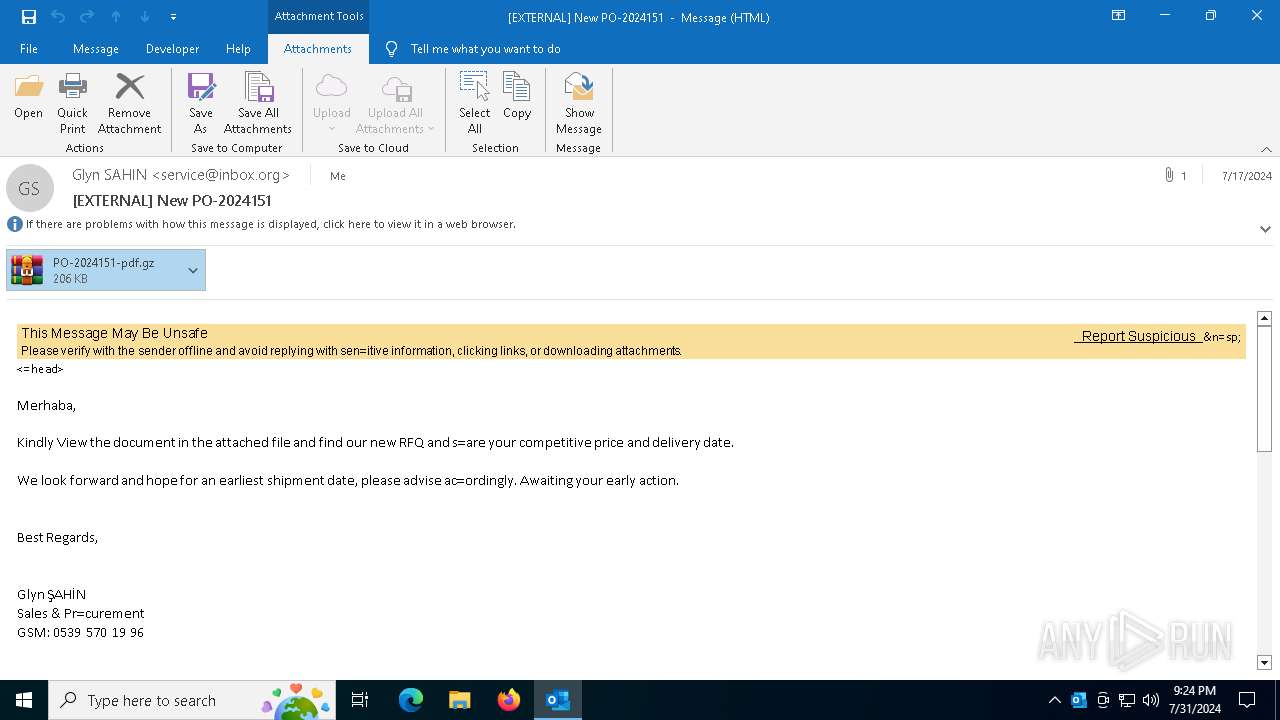
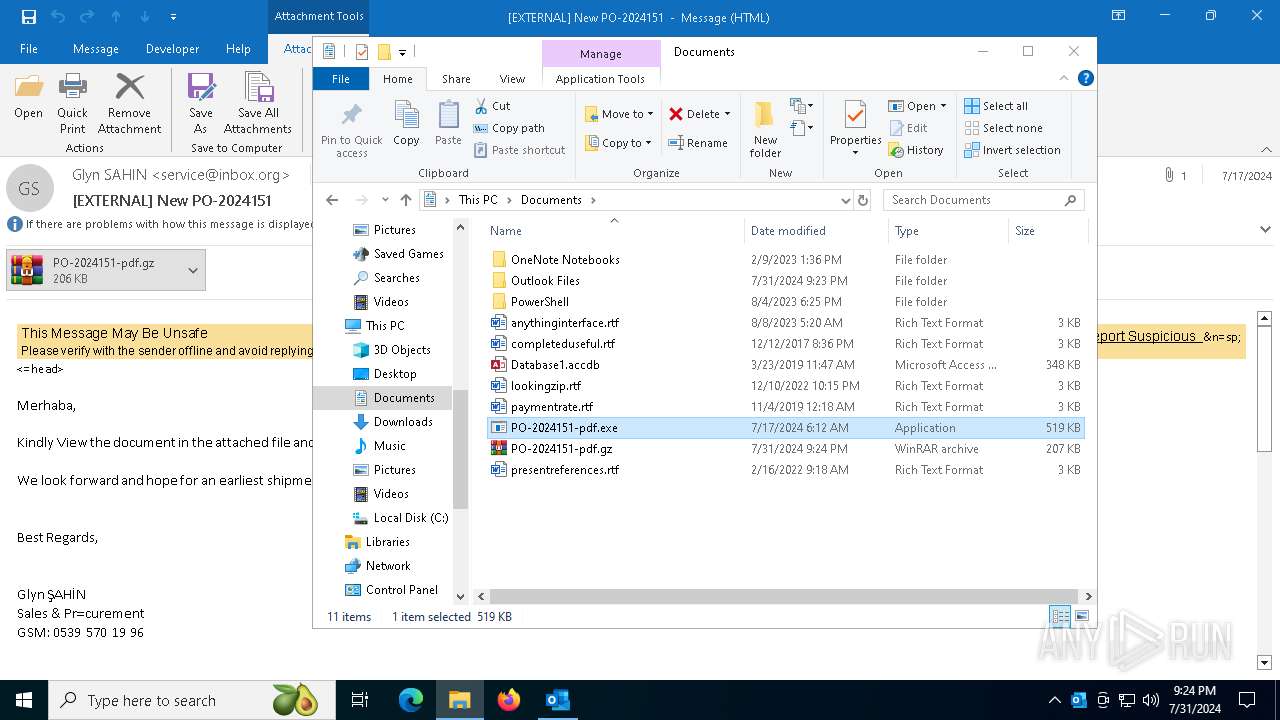
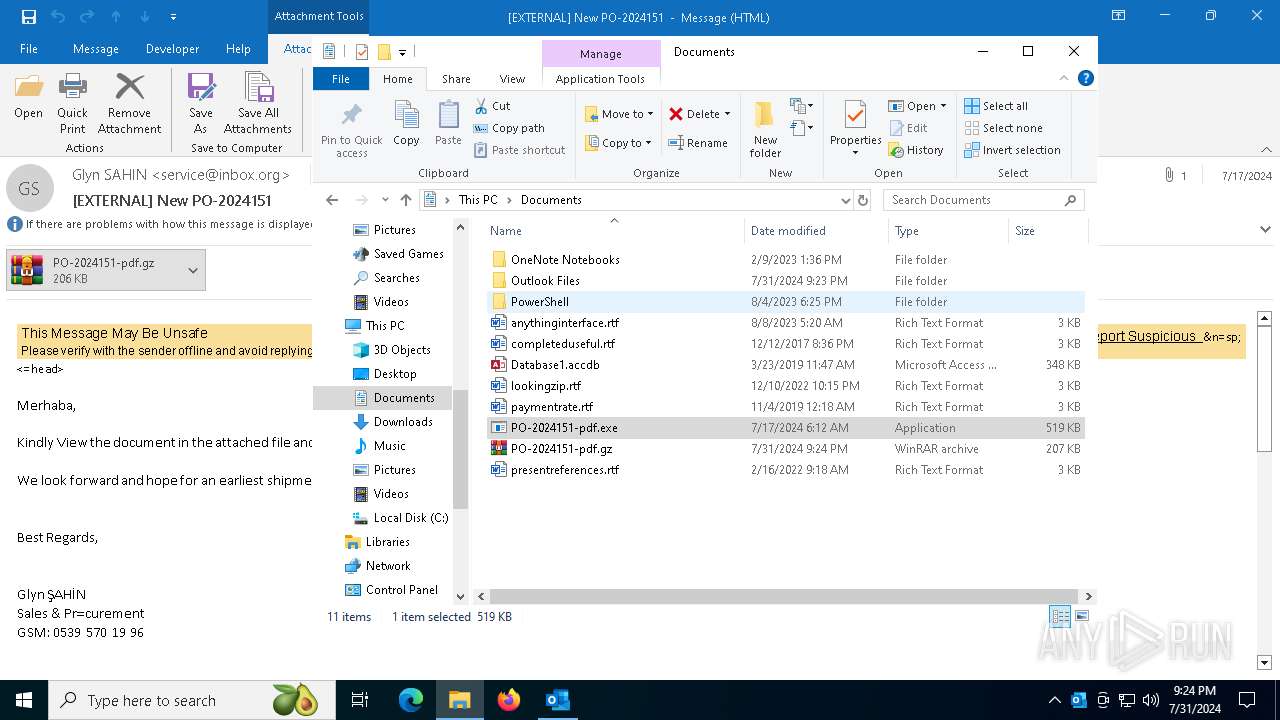
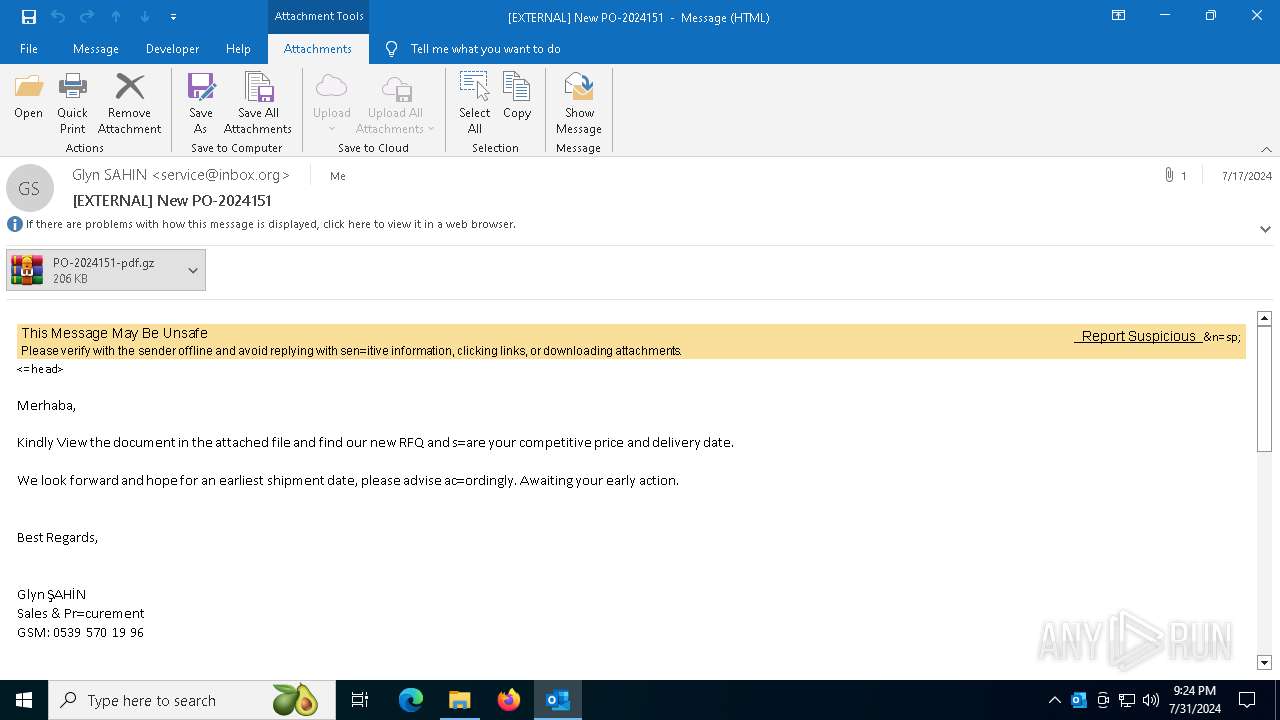
| File name: | 20240717_205310_NdlRJ8ZoJbD8waq6JsjzU4EU71d1LBwC.eml |
| Full analysis: | https://app.any.run/tasks/b76d7b21-d0ca-4f16-9aa9-12e9eb58381e |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | July 31, 2024, 21:23:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF, LF line terminators |
| MD5: | 8042F688BDA12F2AD459F81C0E93B0E3 |
| SHA1: | EB22397DD529C01EA0A6A23216F63A4577AC15DB |
| SHA256: | 5B131D15EF4D116A3EFBC6655CC670DE9CDCB899CCB13425DF31A3807EB6CA1B |
| SSDEEP: | 6144:J760q3uRrNF3hRdUg11mO+mRKqc/oAnIxe0iQOCUiGJ7XM7mXrA:J7q3wrNF3hjb3z+8xcsSfCUlNqt |
MALICIOUS
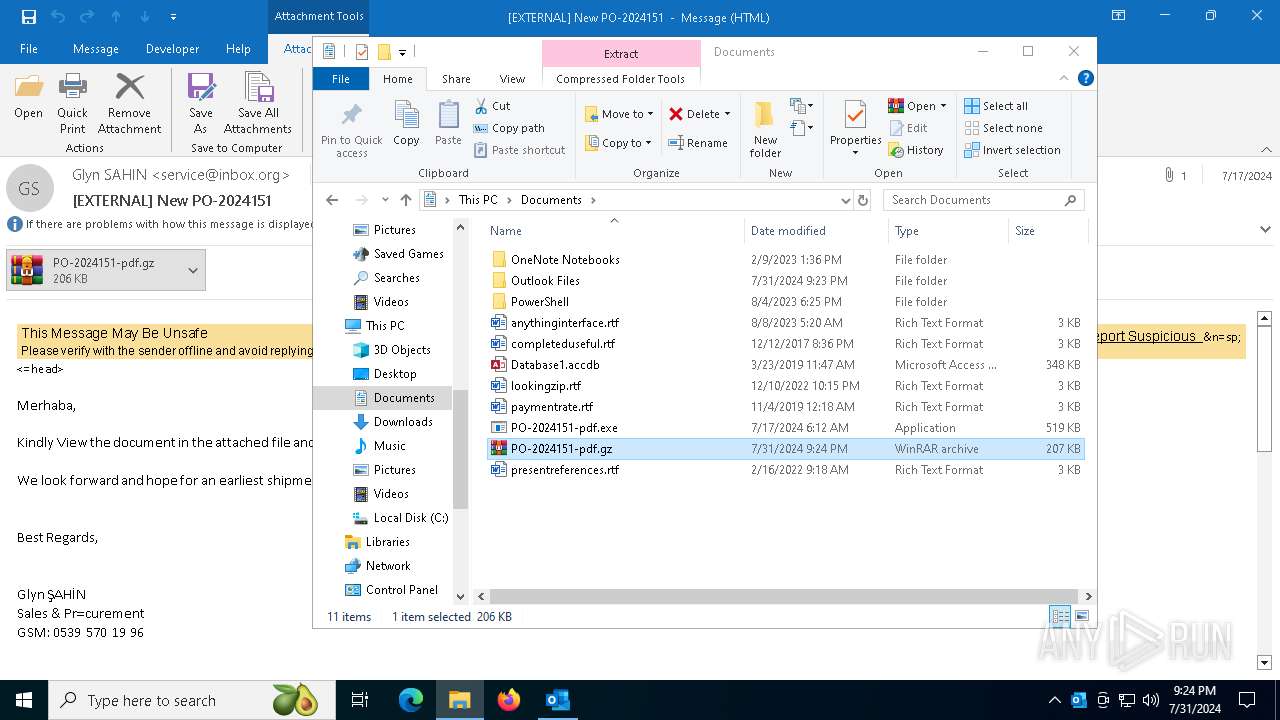
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 6400)
FORMBOOK has been detected (YARA)
- control.exe (PID: 2456)
The DLL Hijacking
- WerFault.exe (PID: 4560)
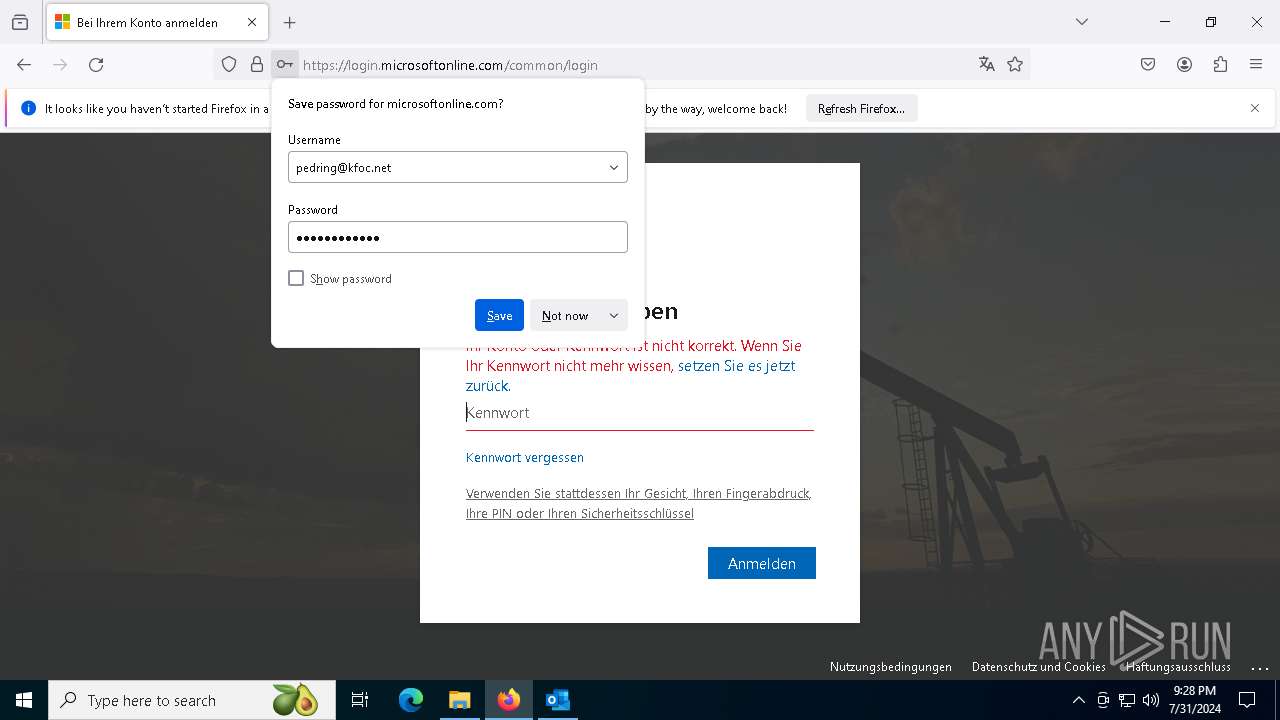
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2256)
Connects to the CnC server
- explorer.exe (PID: 4552)
- firefox.exe (PID: 7072)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 4552)
- firefox.exe (PID: 7072)
SUSPICIOUS
Reads security settings of Internet Explorer
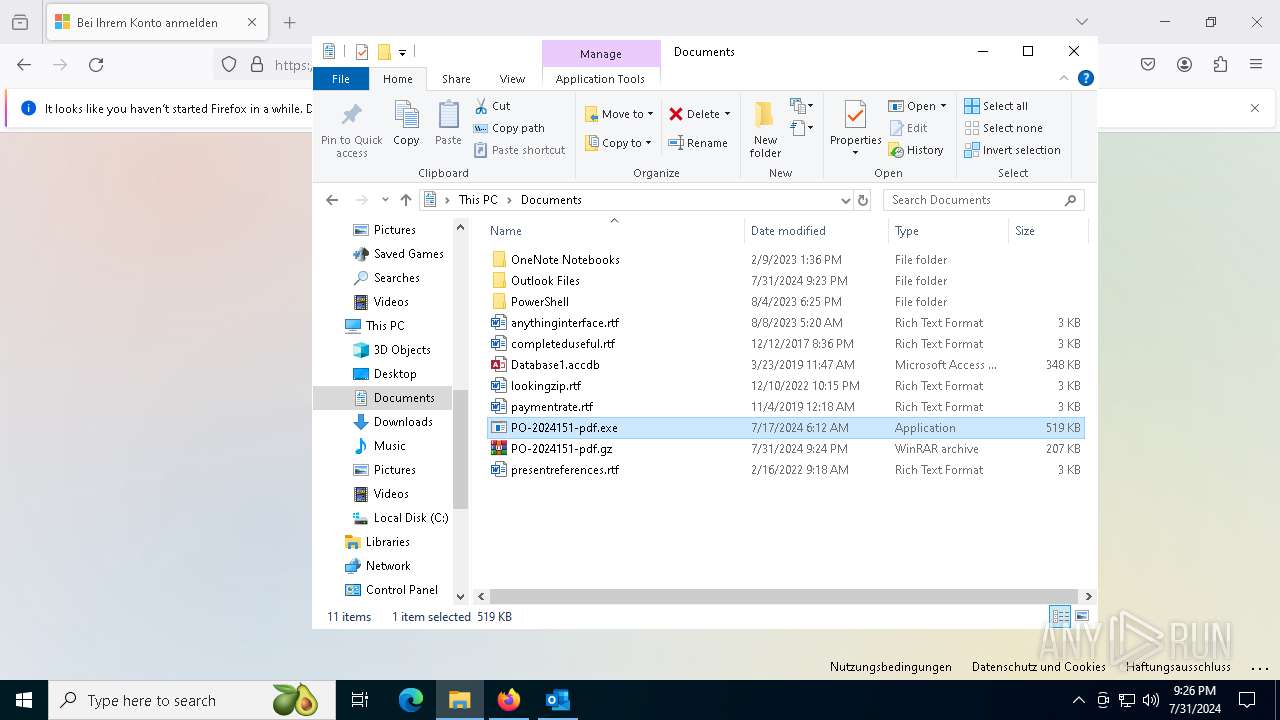
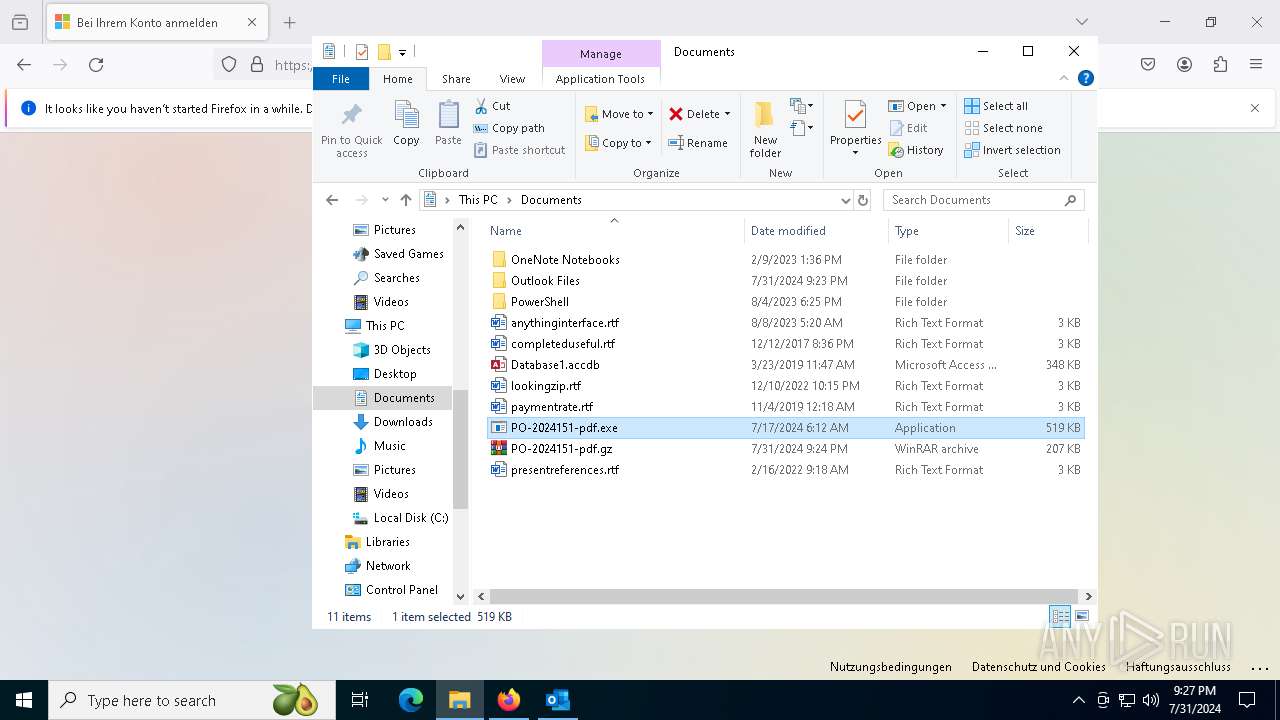
- PO-2024151-pdf.exe (PID: 5084)
- PO-2024151-pdf.exe (PID: 7456)
- PO-2024151-pdf.exe (PID: 5092)
- PO-2024151-pdf.exe (PID: 3136)
- PO-2024151-pdf.exe (PID: 4160)
Checks Windows Trust Settings
- PO-2024151-pdf.exe (PID: 5084)
- PO-2024151-pdf.exe (PID: 7456)
- PO-2024151-pdf.exe (PID: 5092)
- PO-2024151-pdf.exe (PID: 3136)
- PO-2024151-pdf.exe (PID: 4160)
Deletes system .NET executable
- cmd.exe (PID: 1448)
Starts CMD.EXE for commands execution
- control.exe (PID: 2456)
Executes application which crashes
- PO-2024151-pdf.exe (PID: 5084)
- firefox.exe (PID: 2092)
- PO-2024151-pdf.exe (PID: 7456)
- PO-2024151-pdf.exe (PID: 3136)
- PO-2024151-pdf.exe (PID: 5092)
- PO-2024151-pdf.exe (PID: 4160)
Loads DLL from Mozilla Firefox
- WerFault.exe (PID: 4560)
Suspicious use of NETSH.EXE
- explorer.exe (PID: 4552)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 4552)
- firefox.exe (PID: 7072)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
- control.exe (PID: 2456)
Reads the computer name
- TextInputHost.exe (PID: 6240)
- PO-2024151-pdf.exe (PID: 5084)
- MSBuild.exe (PID: 6200)
- PO-2024151-pdf.exe (PID: 7456)
- MSBuild.exe (PID: 3476)
- MSBuild.exe (PID: 7652)
- PO-2024151-pdf.exe (PID: 3136)
- MSBuild.exe (PID: 6852)
- PO-2024151-pdf.exe (PID: 4160)
- MSBuild.exe (PID: 6904)
- PO-2024151-pdf.exe (PID: 5092)
Manual execution by a user
- WinRAR.exe (PID: 2044)
- PO-2024151-pdf.exe (PID: 5084)
- autoconv.exe (PID: 644)
- autoconv.exe (PID: 2324)
- autoconv.exe (PID: 4784)
- firefox.exe (PID: 7024)
- autoconv.exe (PID: 5552)
- control.exe (PID: 2456)
- PO-2024151-pdf.exe (PID: 7456)
- autochk.exe (PID: 6908)
- netsh.exe (PID: 4232)
- PO-2024151-pdf.exe (PID: 5092)
- cmstp.exe (PID: 7676)
- PO-2024151-pdf.exe (PID: 3136)
- rundll32.exe (PID: 6784)
- PO-2024151-pdf.exe (PID: 4160)
- systray.exe (PID: 5400)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2044)
- firefox.exe (PID: 7072)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2044)
- firefox.exe (PID: 7072)
Checks proxy server information
- PO-2024151-pdf.exe (PID: 5084)
- WerFault.exe (PID: 3268)
- control.exe (PID: 2456)
- PO-2024151-pdf.exe (PID: 7456)
- WerFault.exe (PID: 2204)
- PO-2024151-pdf.exe (PID: 5092)
- WerFault.exe (PID: 6376)
- PO-2024151-pdf.exe (PID: 3136)
- PO-2024151-pdf.exe (PID: 4160)
- WerFault.exe (PID: 6176)
- WerFault.exe (PID: 3984)
Checks supported languages
- PO-2024151-pdf.exe (PID: 5084)
- MSBuild.exe (PID: 6200)
- PO-2024151-pdf.exe (PID: 7456)
- MSBuild.exe (PID: 3476)
- PO-2024151-pdf.exe (PID: 5092)
- TextInputHost.exe (PID: 6240)
- MSBuild.exe (PID: 7652)
- PO-2024151-pdf.exe (PID: 3136)
- PO-2024151-pdf.exe (PID: 4160)
- MSBuild.exe (PID: 6904)
- MSBuild.exe (PID: 6852)
Reads the machine GUID from the registry
- PO-2024151-pdf.exe (PID: 5084)
- PO-2024151-pdf.exe (PID: 7456)
- PO-2024151-pdf.exe (PID: 5092)
- PO-2024151-pdf.exe (PID: 3136)
- PO-2024151-pdf.exe (PID: 4160)
Creates files or folders in the user directory
- WerFault.exe (PID: 3268)
- PO-2024151-pdf.exe (PID: 5084)
- WerFault.exe (PID: 4560)
- WerFault.exe (PID: 2204)
- WerFault.exe (PID: 6376)
- WerFault.exe (PID: 6176)
- WerFault.exe (PID: 3984)
Reads the software policy settings
- PO-2024151-pdf.exe (PID: 5084)
- WerFault.exe (PID: 3268)
- WerFault.exe (PID: 2204)
- WerFault.exe (PID: 6376)
- WerFault.exe (PID: 6176)
- WerFault.exe (PID: 3984)
Application launched itself
- firefox.exe (PID: 7024)
- firefox.exe (PID: 7072)
Reads Microsoft Office registry keys
- firefox.exe (PID: 7072)
- explorer.exe (PID: 4552)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 6400)
- WinRAR.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(2456) control.exe
C2www.dmvdrivingpermit.com/mu94/
Strings (79)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
f-end
Decoy C2 (64)thenextamendment.net
automatiza.xyz
psikologhazelgungor.com
90857.net
robertoblondetrealtor.site
rv0awy.rest
74657.ooo
adigidea.com
world-healing.online
health4world.com
shyan.fun
anviltotable.com
vinger.online
juizltd.com
twmk.asia
cakescrushbyruby.com
listxtreme.com
00050026.xyz
finessedesignhouse.com
jsmm-27.xyz
privet128.band
wyhl668.top
crystalcornerdesignn.com
kameltoe2024.xyz
mwquas.xyz
bt365860.com
c2r2h.xyz
bregylzj.xyz
dxlhu.asia
mythandbody.com
7y-sorte.net
gameogem.com
yourhug.xyz
reviewfreak.net
langitwin.lol
jkku2.rest
het789.com
cn00417984.shop
ry5ls1e02ai.top
cathedrals.shop
kaaatooni.com
ctventure.net
50732650.com
699519f.xyz
sailors.solutions
couples-therapy-39471.bond
eco-liga.com
youngtv.net
31hum.com
cocaincoutre.com
kzliw.xyz
online-business-70709.bond
cleliasfamilychildcare.com
commonhype.dev
tufabricadefiestas.com
playstayaussie.com
best-precious.com
kbk99.fun
cprcertificationcoach.com
mysleepfriend.shop
bt365437.com
rajasusu.pics
youtuberjumpstart.com
bfgj46578456454.vip
TRiD
| .eml | | | E-Mail message (Var. 3) (100) |
|---|
Total processes
206
Monitored processes
59
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | "C:\Windows\SysWOW64\autoconv.exe" | C:\Windows\SysWOW64\autoconv.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Conversion Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=7632 -childID 11 -isForBrowser -prefsHandle 7708 -prefMapHandle 7356 -prefsLen 31978 -prefMapSize 244343 -jsInitHandle 1516 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f927592b-97c6-4dec-a4ad-3496e519428b} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 18d71dcb690 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6516 -childID 13 -isForBrowser -prefsHandle 7616 -prefMapHandle 6692 -prefsLen 31978 -prefMapSize 244343 -jsInitHandle 1516 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {32248109-8216-49cc-afde-167bcd88bec0} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 18d71dcbbd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1140 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2952 -childID 1 -isForBrowser -prefsHandle 2944 -prefMapHandle 2940 -prefsLen 30953 -prefMapSize 244343 -jsInitHandle 1516 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8a3b7564-f8e7-40b7-82bf-1b1f8ccb2589} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 18d71c54150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1448 | /c del "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\SysWOW64\cmd.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Documents\PO-2024151-pdf.gz" C:\Users\admin\Documents\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2292 -parentBuildID 20240213221259 -prefsHandle 2284 -prefMapHandle 2276 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {5b497404-93ef-4596-bdae-240d52872997} 7072 "\\.\pipe\gecko-crash-server-pipe.7072" 18d5f982b10 socket | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2204 | C:\WINDOWS\system32\WerFault.exe -u -p 7456 -s 1652 | C:\Windows\System32\WerFault.exe | PO-2024151-pdf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Windows\SysWOW64\autoconv.exe" | C:\Windows\SysWOW64\autoconv.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Auto File System Conversion Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
105 269
Read events
104 537
Write events
631
Delete events
101
Modification events
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6400 |
| Operation: | write | Name: | 0 |
Value: 0B0E109B12FDEA873DA649973596D7E76B6020230046C4A79D87FFF1B8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118032D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
3
Suspicious files
216
Text files
56
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6400 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olk5F13.tmp | binary | |
MD5:0FEAF06AFE018C82C7FA4E69CBA2CBAA | SHA256:78B0F216563FFEB18B2ACE6E8B213DD34BEFDD6AFB148B4488C281584CBF1827 | |||
| 6400 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:61CEAD788456AD5C0C9B3ADD8C99CAD1 | SHA256:A9F2559BEC87B5DE60ED52D821672E2898F3BB5625049CB02D5E2541FF2E92D3 | |||
| 6400 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:F8A3D4C2B8EBF7DBDD3E2A8892F73A01 | SHA256:8593F6EF4354D27BBC8651F994531D11731A5C01FCE720E41359C8F9B94E82E4 | |||
| 6400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\4ZDUEU4U\PO-2024151-pdf.gz:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 6400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\4ZDUEU4U\PO-2024151-pdf.gz | compressed | |
MD5:0EA592C3E87FAA2C1DE7C1C64072C977 | SHA256:E8870479E9CD0F28C1A0E8E721110E812353B5416AA1A2CD858D3C26D4755FA9 | |||
| 6400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:5EAD2891A161AD0BF08C061082380C58 | SHA256:2B1F82A0FCD074E295B1C4F566EC3BD431141F8945FEA626233485D68CFAE6BE | |||
| 3268 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_PO-2024151-pdf.e_8c13c9dd4c53ac4bc937c29c28f6d29a9b2c7_2f6b6b63_1c70201b-ab2f-44f6-98bb-d0284633d67b\Report.wer | — | |
MD5:— | SHA256:— | |||
| 3268 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\PO-2024151-pdf.exe.5084.dmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
188
DNS requests
244
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4920 | svchost.exe | GET | 304 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6400 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6148 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6272 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5084 | PO-2024151-pdf.exe | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
7072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7072 | firefox.exe | POST | 200 | 195.138.255.19:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
7072 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4084 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1928 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6400 | OUTLOOK.EXE | 52.123.243.86:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6400 | OUTLOOK.EXE | 23.50.131.25:443 | omex.cdn.office.net | Akamai International B.V. | DE | unknown |
6400 | OUTLOOK.EXE | 52.111.231.13:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
4084 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5336 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .ms__auth .net) |
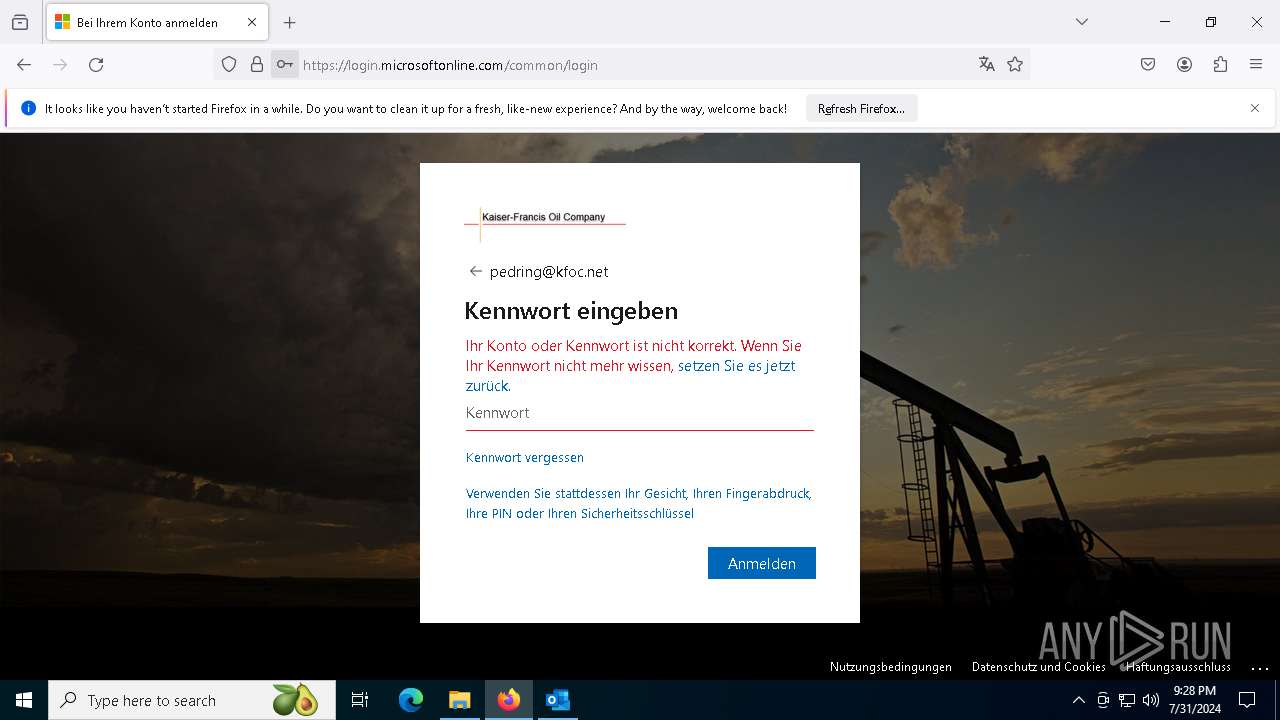
2256 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain has been detected |
7072 | firefox.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Microsoft Entra seamless single sign-on (autologon .microsoftazuread-sso .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .ms__auth .net) |
2256 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain has been detected |
7072 | firefox.exe | Potentially Bad Traffic | ET HUNTING Request to .XYZ Domain with Minimal Headers |
7072 | firefox.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |
4552 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE FormBook CnC Checkin (GET) |