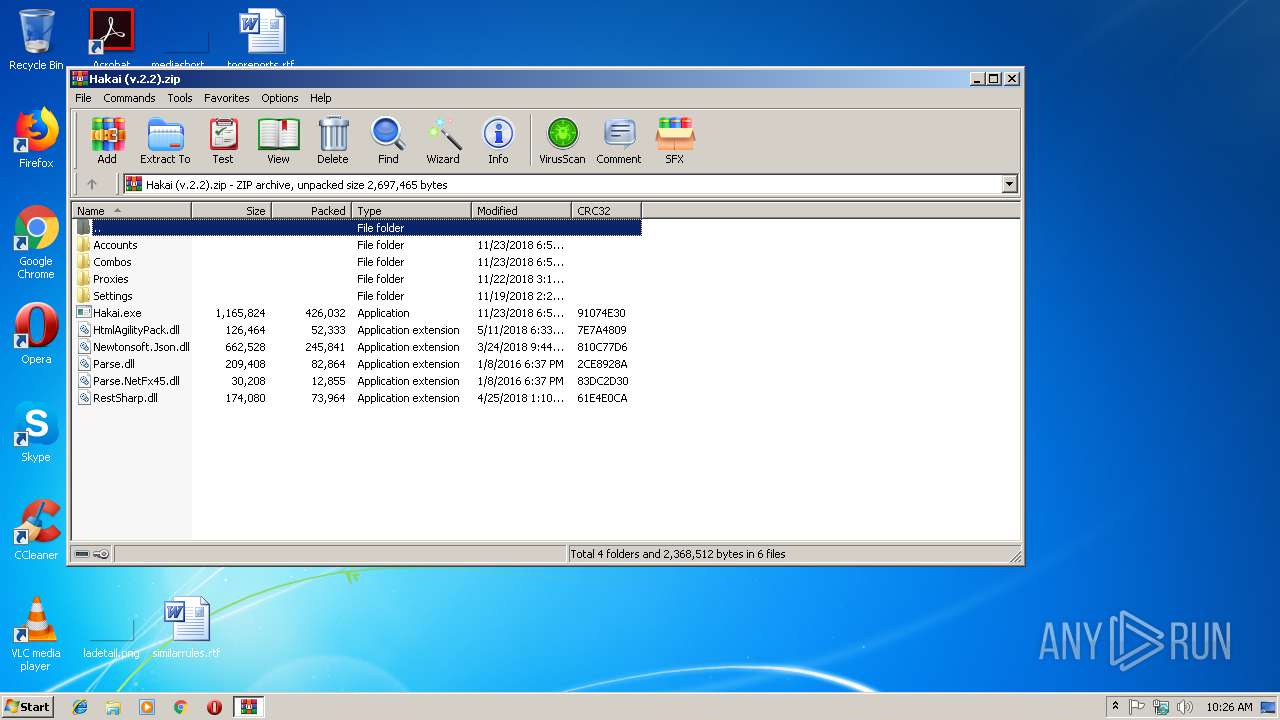
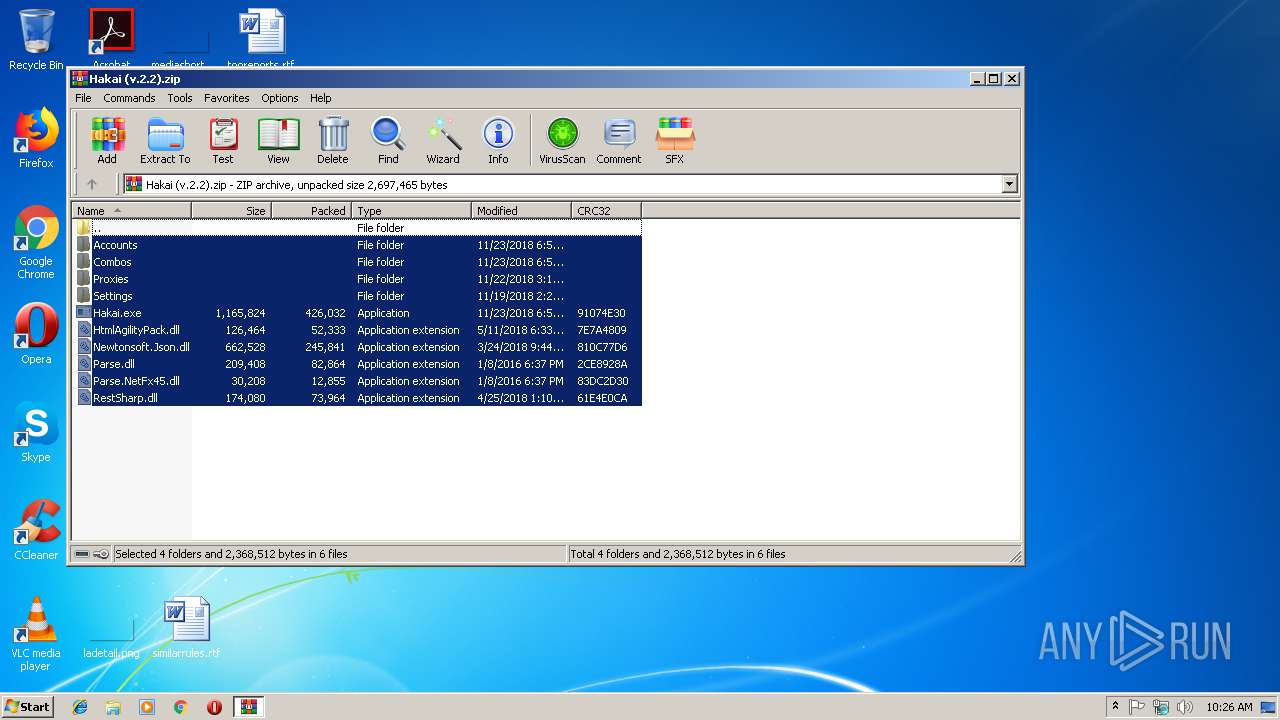
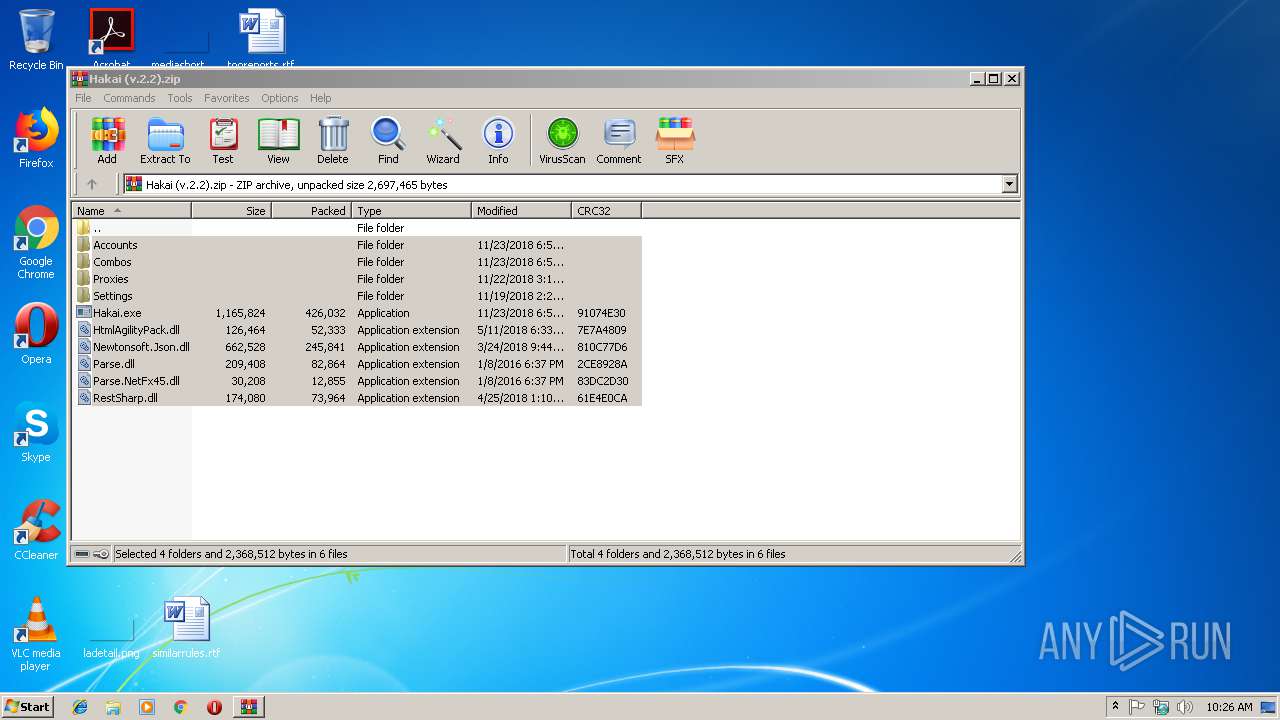
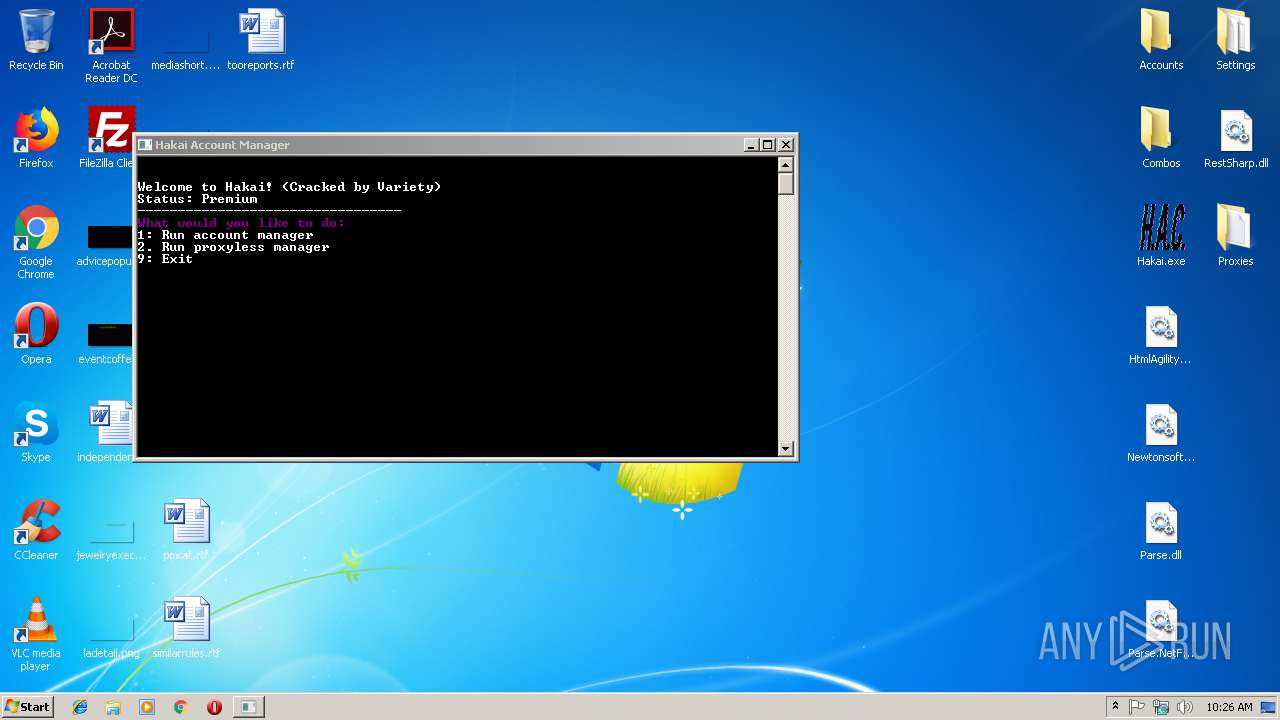
| File name: | Hakai (v.2.2).zip |
| Full analysis: | https://app.any.run/tasks/71600c0c-b6e9-4805-bc67-a71e2211bf4c |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | November 23, 2018, 10:26:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | A9707853B393AC96296DFCB0F9F9429A |
| SHA1: | 5D8FA3EFC649511131EAD08465F68FFE8EA38A21 |
| SHA256: | 5AC128BBCDED360845A2513FD1F37F5C3E8A99754F54B9731FF3D3C6FAAFA643 |
| SSDEEP: | 24576:uN8iAIeyatlhrDneDNldeFKL1Y1qr3Vwdcbsarxn9HrRT3JFpNZz0TnTF:k8iATTtlhvn4NldR5Y1qRuSsalnR9JFK |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1020)
Application was dropped or rewritten from another process
- Hakai.exe (PID: 2852)
- EBFile_1.exe (PID: 2656)
Detected Hawkeye Keylogger
- Hakai.exe (PID: 2852)
Changes the autorun value in the registry
- Hakai.exe (PID: 2852)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2700)
- Hakai.exe (PID: 2852)
Connects to SMTP port
- Hakai.exe (PID: 2852)
Creates files in the user directory
- Hakai.exe (PID: 2852)
Checks for external IP
- Hakai.exe (PID: 2852)
Executes scripts
- Hakai.exe (PID: 2852)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 364)
INFO
Reads settings of System Certificates
- Hakai.exe (PID: 2852)
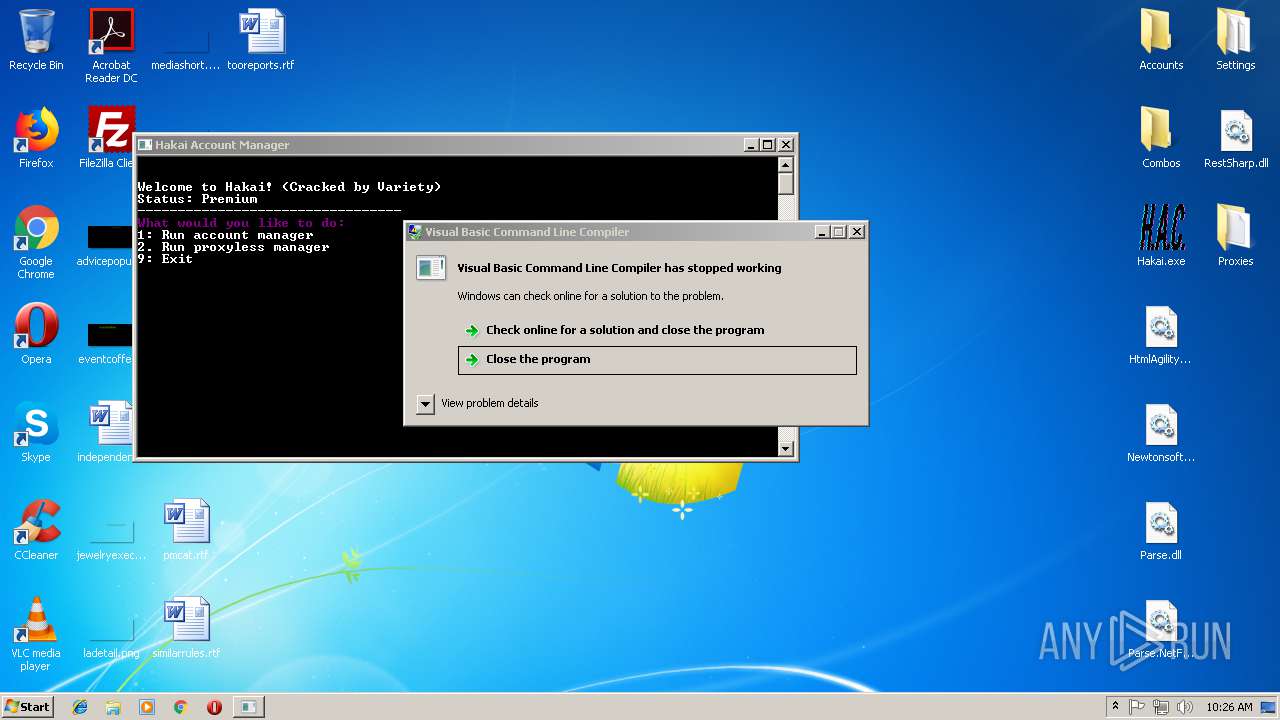
Application was crashed
- vbc.exe (PID: 3296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:11:23 01:54:26 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Combos/ |
Total processes
42
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | Hakai.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 1020 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2656 | "C:\Users\admin\AppData\Local\Temp\EBFile_1.exe" | C:\Users\admin\AppData\Local\Temp\EBFile_1.exe | — | Hakai.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Hakai Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2700 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Hakai (v.2.2).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\Hakai.exe" | C:\Users\admin\Desktop\Hakai.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Microsoft Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3296 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | Hakai.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 3221225477 Version: 8.0.50727.5420 Modules
| |||||||||||||||
Total events
1 265
Read events
1 216
Write events
49
Delete events
0
Modification events
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Hakai (v.2.2).zip | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
3
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Proxies\HTTP.txt | — | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Hakai.exe | — | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\HtmlAgilityPack.dll | — | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Newtonsoft.Json.dll | — | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Parse.dll | — | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Parse.NetFx45.dll | — | |
MD5:— | SHA256:— | |||
| 364 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holderwb.txt | — | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Settings\DiscordWebhook.json | text | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Settings\AutoTransfer.json | text | |
MD5:— | SHA256:— | |||
| 2700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2700.30528\Settings\Settings.json | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2852 | Hakai.exe | GET | 403 | 104.16.17.96:80 | http://whatismyipaddress.com/ | US | text | 100 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2852 | Hakai.exe | 104.16.17.96:80 | whatismyipaddress.com | Cloudflare Inc | US | shared |
2852 | Hakai.exe | 74.208.5.15:587 | smtp.mail.com | 1&1 Internet SE | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
whatismyipaddress.com |
| shared |
smtp.mail.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2852 | Hakai.exe | A Network Trojan was detected | MALWARE [PTsecurity] Spyware.HawkEyeKeyLogger (IP Chck) |
2 ETPRO signatures available at the full report