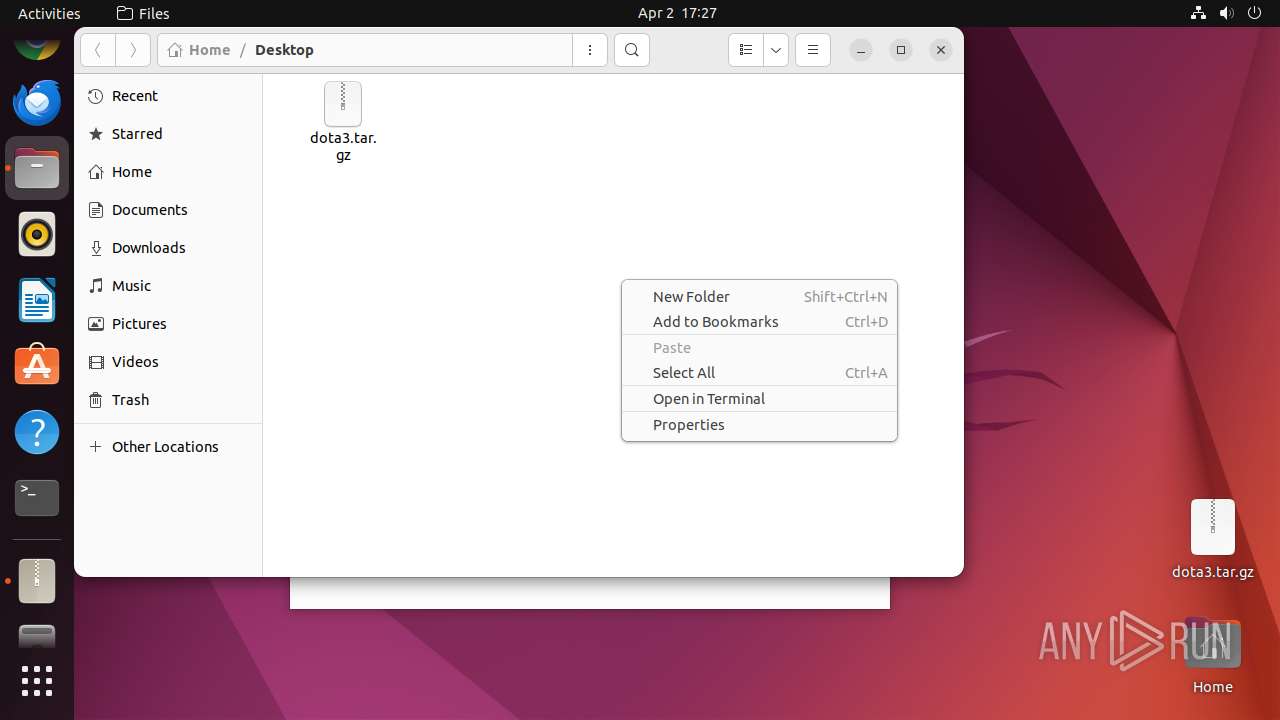
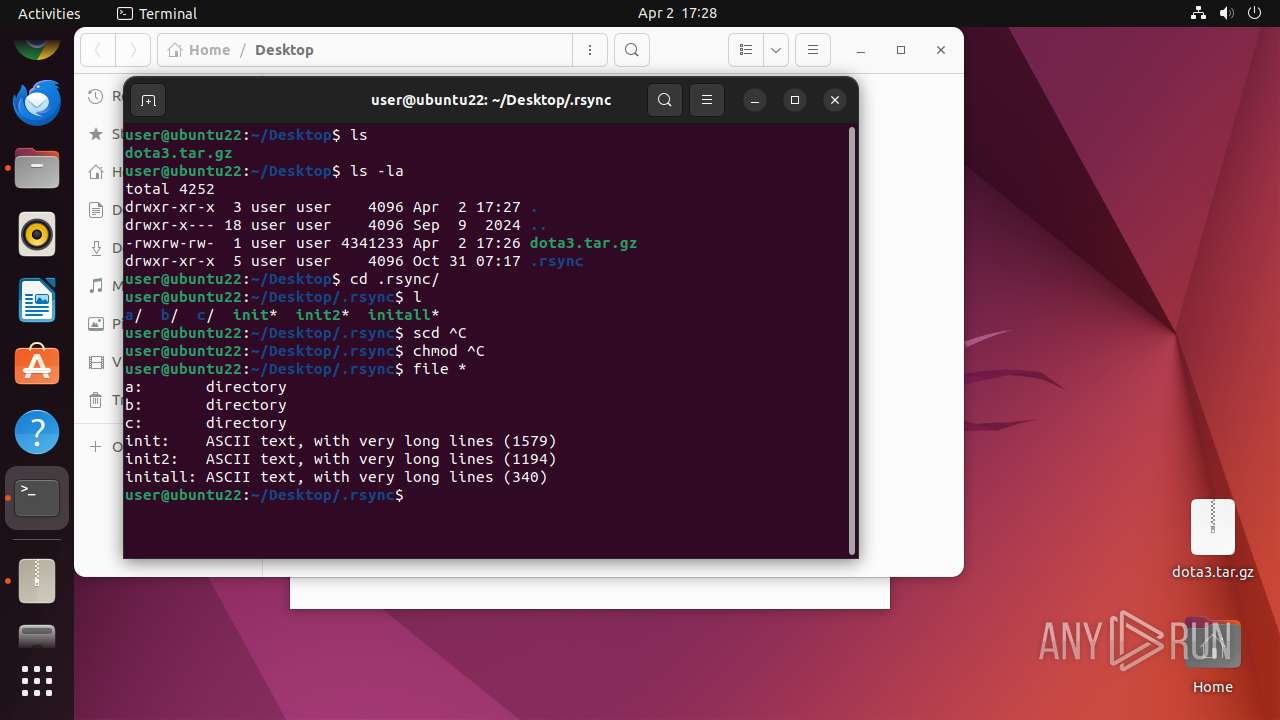
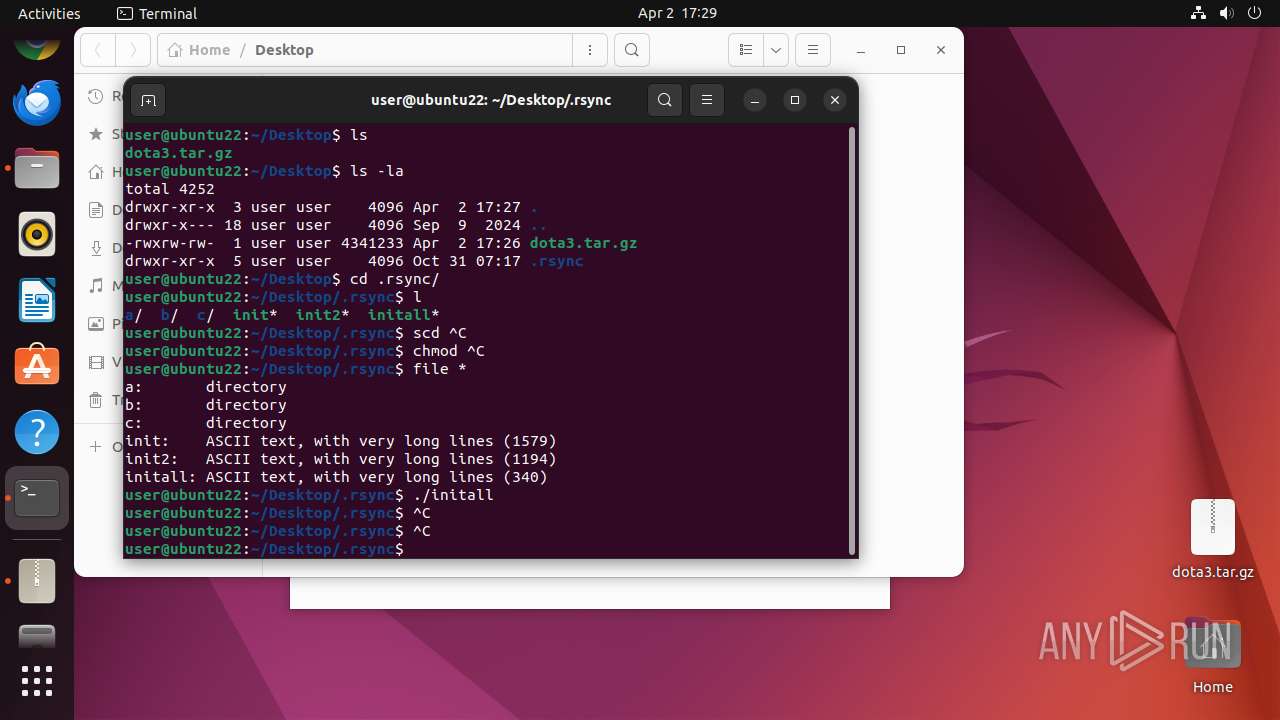
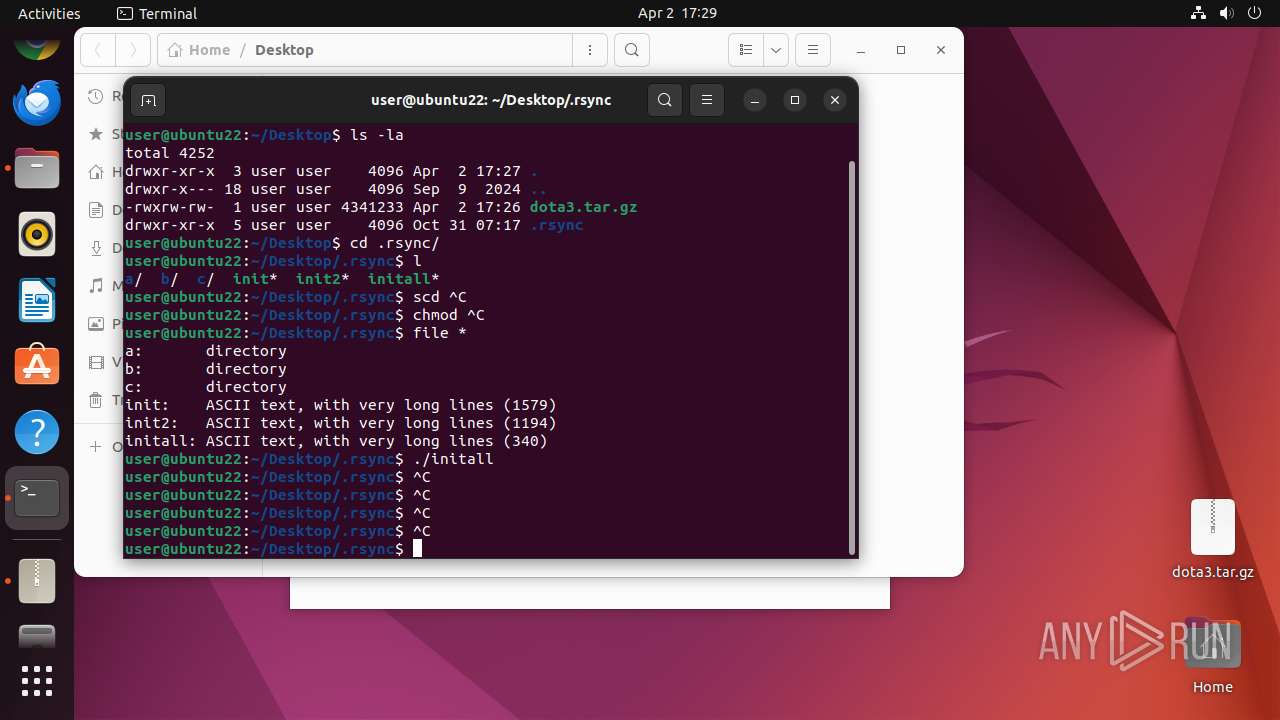
| File name: | dota3.tar.gz |
| Full analysis: | https://app.any.run/tasks/8b75f106-515d-4977-ab38-bb007d02a761 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | April 02, 2025, 16:26:35 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, from Unix, original size modulo 2^32 4505600 |
| MD5: | A8AF9AF2BEDFAABA970A181074396206 |
| SHA1: | 6F7DF5E851CEF484A357BB5F8FA45B7BAC13DD02 |
| SHA256: | 5A3291A81D961053FCB5495973C5AA9755AE4B54A689947914489F7FB4FE7F71 |
| SSDEEP: | 98304:qKKVNp7ZFELTtoHBJunbeDMYNc8sYI6r7XK30l8vcQOlMvgY/Rwft4+L4oKbU70X:HJnKk+k5l |
MALICIOUS
Attempting to connect via SSH
- kthreadadd64 (PID: 40057)
Attempting to scan the network
- kthreadadd64 (PID: 40057)
TELNETSCAN has been detected (SURICATA)
- kthreadadd64 (PID: 40057)
EXPLOIT has been detected (SURICATA)
- kthreadadd64 (PID: 40057)
SUSPICIOUS
Executes the "rm" command to delete files or directories
- dash (PID: 39690)
- dash (PID: 39639)
- dash (PID: 39755)
- dash (PID: 39699)
- dash (PID: 39892)
- dash (PID: 39891)
- dash (PID: 40004)
- dash (PID: 40011)
- dash (PID: 40041)
- dash (PID: 40585)
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 39599)
Reads passwd file
- ls (PID: 39624)
- file-roller (PID: 39508)
- top (PID: 39719)
- ps (PID: 39967)
- crontab (PID: 40026)
- crontab (PID: 40027)
- ps (PID: 39971)
- kthreadadd64 (PID: 40057)
Gets information about currently running processes
- dash (PID: 39639)
- dash (PID: 39718)
- dash (PID: 39699)
- dash (PID: 39688)
- dash (PID: 39755)
- dash (PID: 39892)
- dash (PID: 40029)
Checks type of computer hardware (uname)
- dash (PID: 39708)
- dash (PID: 40053)
- dash (PID: 40041)
Removes file immutable attribute
- dash (PID: 39755)
- dash (PID: 39891)
- dash (PID: 40004)
- dash (PID: 40011)
Uses base64 (probably to encode stolen data or decode malicious payload)
- dash (PID: 39688)
- dash (PID: 39891)
Checks all system information (uname)
- perl (PID: 39991)
- perl (PID: 39986)
Modifies Cron jobs
- dash (PID: 39639)
Checks DMI information (probably VM detection)
- .kswapd00 (PID: 40602)
- kswapd00 (PID: 40604)
Reads /proc/mounts (likely used to find writable filesystems)
- kswapd00 (PID: 40604)
- .kswapd00 (PID: 40602)
Uses tools that copy files from or to remote systems
- dash (PID: 40053)
Potential Corporate Privacy Violation
- kthreadadd64 (PID: 40057)
Connects to unusual port
- kthreadadd64 (PID: 40057)
Connects to SSH
- kthreadadd64 (PID: 40057)
INFO
Checks timezone
- ls (PID: 39624)
- file-roller (PID: 39508)
- ps (PID: 39967)
- ps (PID: 39971)
- crontab (PID: 40026)
- crontab (PID: 40027)
Creates file in the temporary folder
- kswapd00 (PID: 40604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 0000:00:00 00:00:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | Unix |
Total processes
662
Monitored processes
438
Malicious processes
8
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 39506 | /bin/sh -c "DISPLAY=:0 sudo -iu user file-roller /home/user/Desktop/dota3\.tar\.gz " | /usr/bin/dash | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 9 | ||||
| 39507 | sudo -iu user file-roller /home/user/Desktop/dota3.tar.gz | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 39508 | file-roller /home/user/Desktop/dota3.tar.gz | /usr/bin/file-roller | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 39509 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39542 | /lib/systemd/systemd-hostnamed | /usr/lib/systemd/systemd-hostnamed | — | systemd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39544 | /usr/libexec/gvfsd-network --spawner :1.6 /org/gtk/gvfs/exec_spaw/1 | /usr/libexec/gvfsd-network | — | gvfsd |
User: user Integrity Level: UNKNOWN | ||||
| 39553 | /usr/libexec/gvfsd-smb-browse --spawner :1.6 /org/gtk/gvfs/exec_spaw/2 | /usr/libexec/gvfsd-smb-browse | gvfsd | |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39559 | /usr/libexec/gvfsd-dnssd --spawner :1.6 /org/gtk/gvfs/exec_spaw/3 | /usr/libexec/gvfsd-dnssd | — | gvfsd |
User: user Integrity Level: UNKNOWN | ||||
| 39568 | /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only | /usr/bin/dbus-daemon | — | dbus-daemon |
User: user Integrity Level: UNKNOWN Exit code: 9 | ||||
| 39569 | /usr/bin/nautilus --gapplication-service | /usr/bin/nautilus | — | dbus-daemon |
User: user Integrity Level: UNKNOWN | ||||
Executable files
0
Suspicious files
4
Text files
57
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 39508 | file-roller | /home/user/.local/share/recently-used.xbel | xml | |
MD5:— | SHA256:— | |||
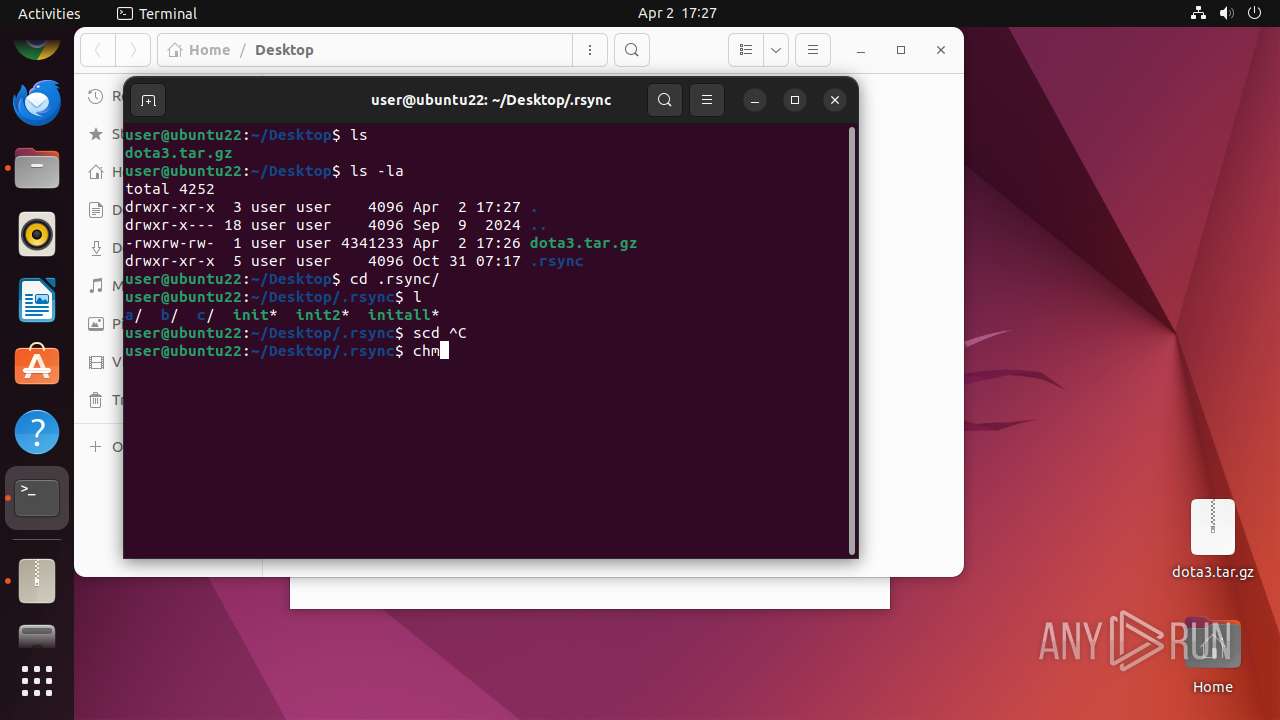
| 39508 | file-roller | /home/user/Desktop/.rsync/init2 | text | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/b/run | text | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/b/a | text | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/b/stop | text | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/a/init01 | text | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/a/run | text | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/a/a | text | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/a/kswapd00 | binary | |
MD5:— | SHA256:— | |||
| 39508 | file-roller | /home/user/Desktop/.rsync/a/stop | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
63 004
DNS requests
21
Threats
58 474
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
488 | NetworkManager | GET | 204 | 185.125.190.48:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
— | — | POST | 200 | 185.125.188.54:443 | https://api.snapcraft.io/v2/snaps/refresh | unknown | tss | 45.3 Kb | whitelisted |
— | — | POST | 200 | 185.125.188.54:443 | https://api.snapcraft.io/v2/snaps/refresh | unknown | tss | 45.3 Kb | whitelisted |
— | — | POST | 200 | 185.125.188.58:443 | https://api.snapcraft.io/v2/snaps/refresh | unknown | tss | 45.3 Kb | whitelisted |
— | — | POST | 200 | 185.125.188.54:443 | https://api.snapcraft.io/api/v1/snaps/auth/nonces | unknown | binary | 54 b | whitelisted |
— | — | POST | 200 | 185.125.188.55:443 | https://api.snapcraft.io/api/v1/snaps/auth/nonces | unknown | binary | 53 b | whitelisted |
— | — | POST | 200 | 185.125.188.58:443 | https://api.snapcraft.io/v2/snaps/refresh | unknown | binary | 45.2 Kb | whitelisted |
— | — | POST | 200 | 185.125.188.59:443 | https://api.snapcraft.io/api/v1/snaps/auth/sessions | unknown | binary | 587 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.96:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.96:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
— | — | 169.150.255.183:443 | odrs.gnome.org | — | GB | whitelisted |
— | — | 207.211.211.26:443 | odrs.gnome.org | — | US | whitelisted |
— | — | 185.125.188.58:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
39553 | gvfsd-smb-browse | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 179.43.139.84:80 | — | Private Layer INC | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
google.com |
| whitelisted |
14.100.168.192.in-addr.arpa |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
39988 | perl | Misc activity | ET INFO IRC Nick change on non-standard port |
39993 | perl | Generic Protocol Command Decode | SURICATA HTTP request header invalid |
39993 | perl | Misc activity | ET INFO IRC Nick change on non-standard port |
39988 | perl | Generic Protocol Command Decode | SURICATA HTTP request header invalid |
40057 | kthreadadd64 | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
39993 | perl | Misc activity | ET INFO IRC Nick change on non-standard port |
40057 | kthreadadd64 | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
40057 | kthreadadd64 | Attempted Information Leak | ET SCAN Potential SSH Scan OUTBOUND |
39988 | perl | Misc activity | ET INFO IRC Nick change on non-standard port |