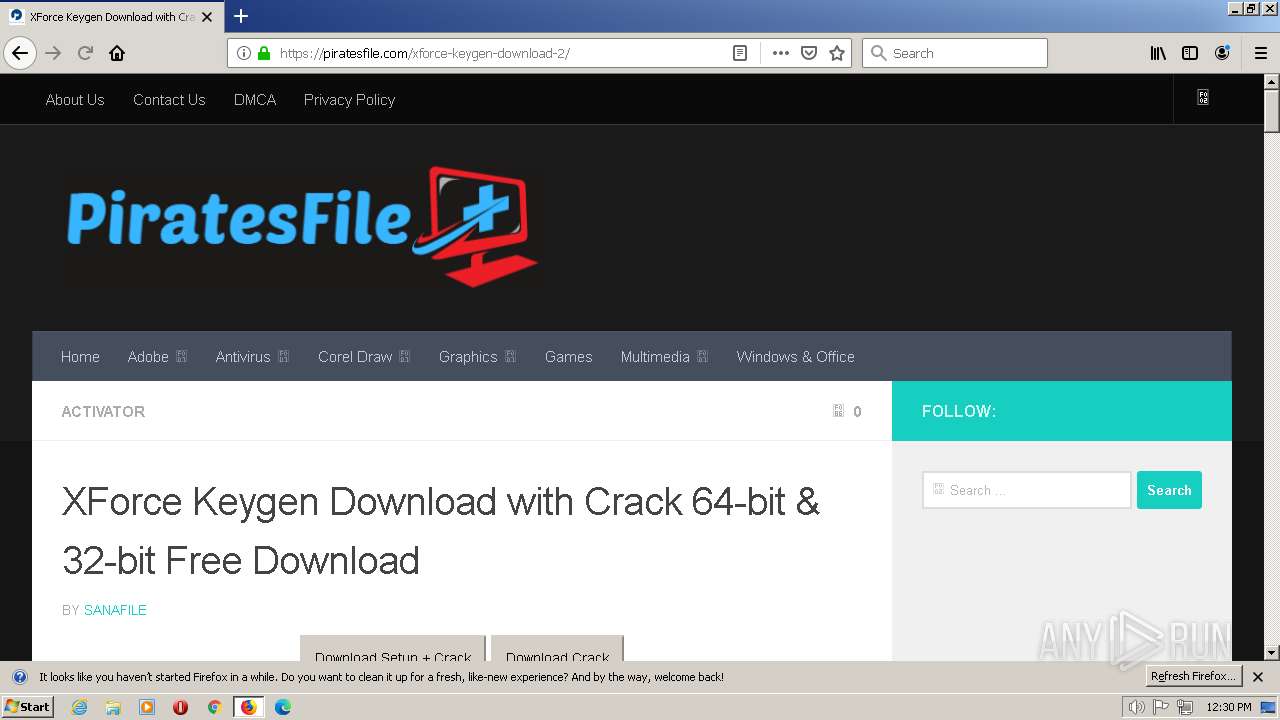
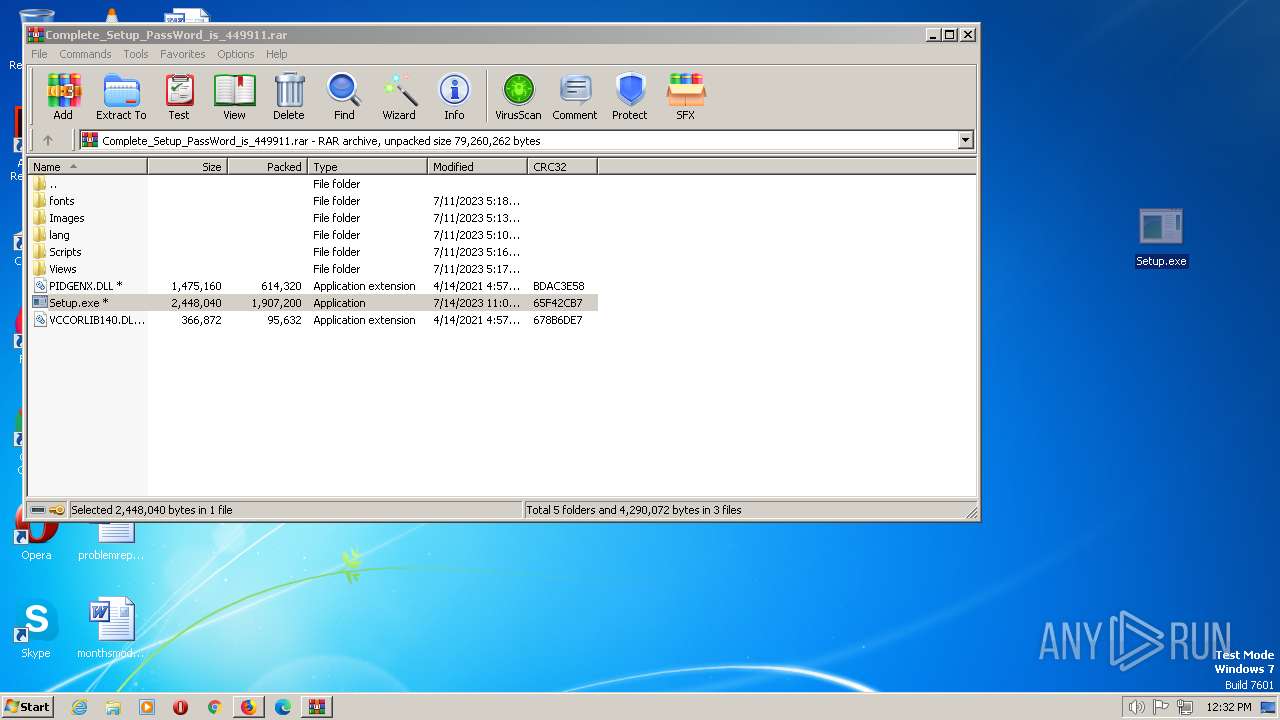
| URL: | https://piratesfile.com |
| Full analysis: | https://app.any.run/tasks/5268ad4c-4673-418d-af15-32d96526201e |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | July 14, 2023, 12:29:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BB55C432A48EA706C1948A009CC2A742 |
| SHA1: | 3D11DDBD6D6F5C01995C0E2D176402C49A4C0E03 |
| SHA256: | 599CFAE969F29452067FE51DA1FD9B25676FFB4BE60575FC401BC92B6D359CE6 |
| SSDEEP: | 3:N8IURv9LGT:2IIvpGT |
MALICIOUS
Application was dropped or rewritten from another process
- Setup.exe (PID: 1888)
LUMMA detected by memory dumps
- MSBuild.exe (PID: 280)
LUMMA was detected
- MSBuild.exe (PID: 280)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 280)
SUSPICIOUS
Reads the Internet Settings
- MSBuild.exe (PID: 280)
Searches for installed software
- MSBuild.exe (PID: 280)
INFO
Application launched itself
- firefox.exe (PID: 2012)
Checks supported languages
- Setup.exe (PID: 1888)
- MSBuild.exe (PID: 280)
Reads the computer name
- Setup.exe (PID: 1888)
- MSBuild.exe (PID: 280)
The process checks LSA protection
- Setup.exe (PID: 1888)
- MSBuild.exe (PID: 280)
The process uses the downloaded file
- firefox.exe (PID: 2012)
- WinRAR.exe (PID: 3344)
Manual execution by a user
- Setup.exe (PID: 1888)
Reads the machine GUID from the registry
- Setup.exe (PID: 1888)
- MSBuild.exe (PID: 280)
Executable content was dropped or overwritten
- firefox.exe (PID: 2012)
- WinRAR.exe (PID: 3344)
Checks proxy server information
- MSBuild.exe (PID: 280)
Creates files or folders in the user directory
- MSBuild.exe (PID: 280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(280) MSBuild.exe
C2skicloud-my.xyz/c2sock
Options
LummaIDKjGtqi--ZUBA
Total processes
50
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MsBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 Modules
Lumma(PID) Process(280) MSBuild.exe C2skicloud-my.xyz/c2sock Options LummaIDKjGtqi--ZUBA | |||||||||||||||
| 320 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2012.20.92194309\232232830" -childID 3 -isForBrowser -prefsHandle 3348 -prefMapHandle 3352 -prefsLen 6545 -prefMapSize 189239 -parentBuildID 20190619235627 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2012 "\\.\pipe\gecko-crash-server-pipe.2012" 3364 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
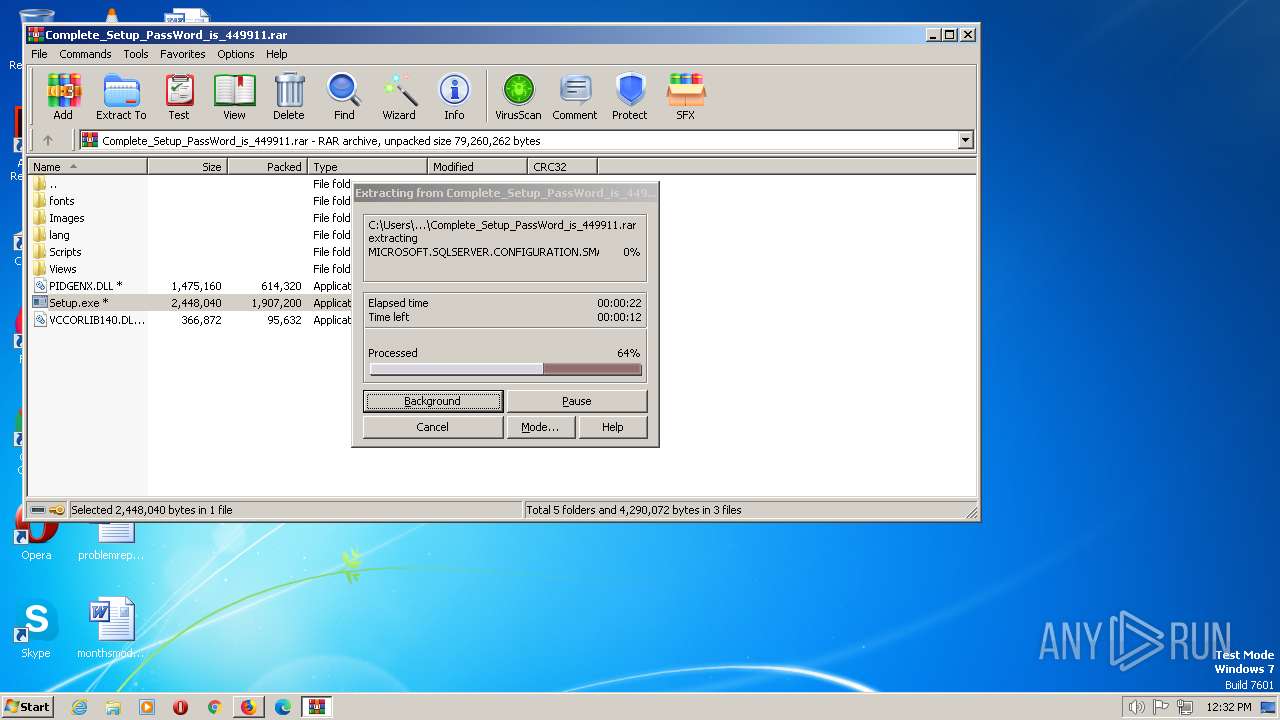
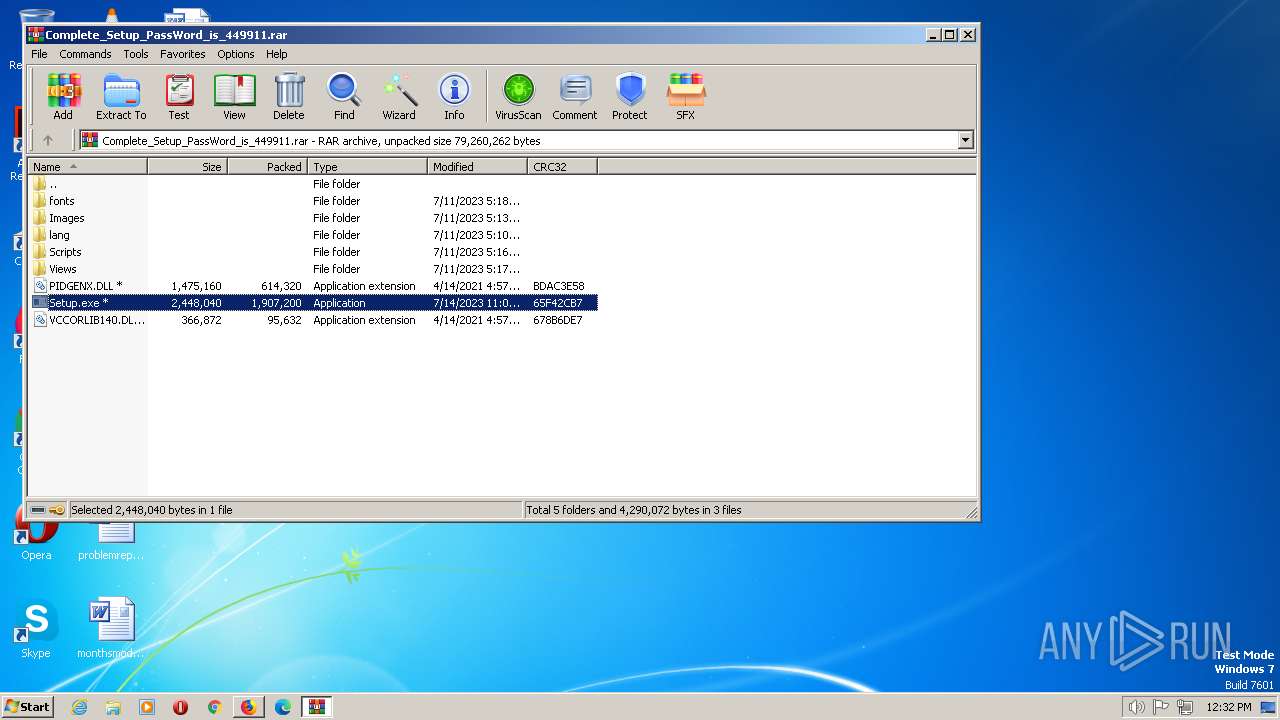
| 1888 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: ESTsoft Corp. Integrity Level: MEDIUM Description: ALZip Exit code: 0 Version: 23.3.9.1 Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2012.0.2089527503\499195641" -parentBuildID 20190619235627 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2012 "\\.\pipe\gecko-crash-server-pipe.2012" 1152 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
| 2012 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://piratesfile.com" | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2012.27.982866288\623919414" -childID 4 -isForBrowser -prefsHandle 3660 -prefMapHandle 3712 -prefsLen 7440 -prefMapSize 189239 -parentBuildID 20190619235627 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2012 "\\.\pipe\gecko-crash-server-pipe.2012" 3280 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
| 2468 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2012.13.940125891\498593619" -childID 2 -isForBrowser -prefsHandle 2292 -prefMapHandle 2704 -prefsLen 5823 -prefMapSize 189239 -parentBuildID 20190619235627 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2012 "\\.\pipe\gecko-crash-server-pipe.2012" 2712 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
| 3144 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2012.3.2054636157\59670426" -childID 1 -isForBrowser -prefsHandle 1896 -prefMapHandle 1904 -prefsLen 1 -prefMapSize 189239 -parentBuildID 20190619235627 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2012 "\\.\pipe\gecko-crash-server-pipe.2012" 1332 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
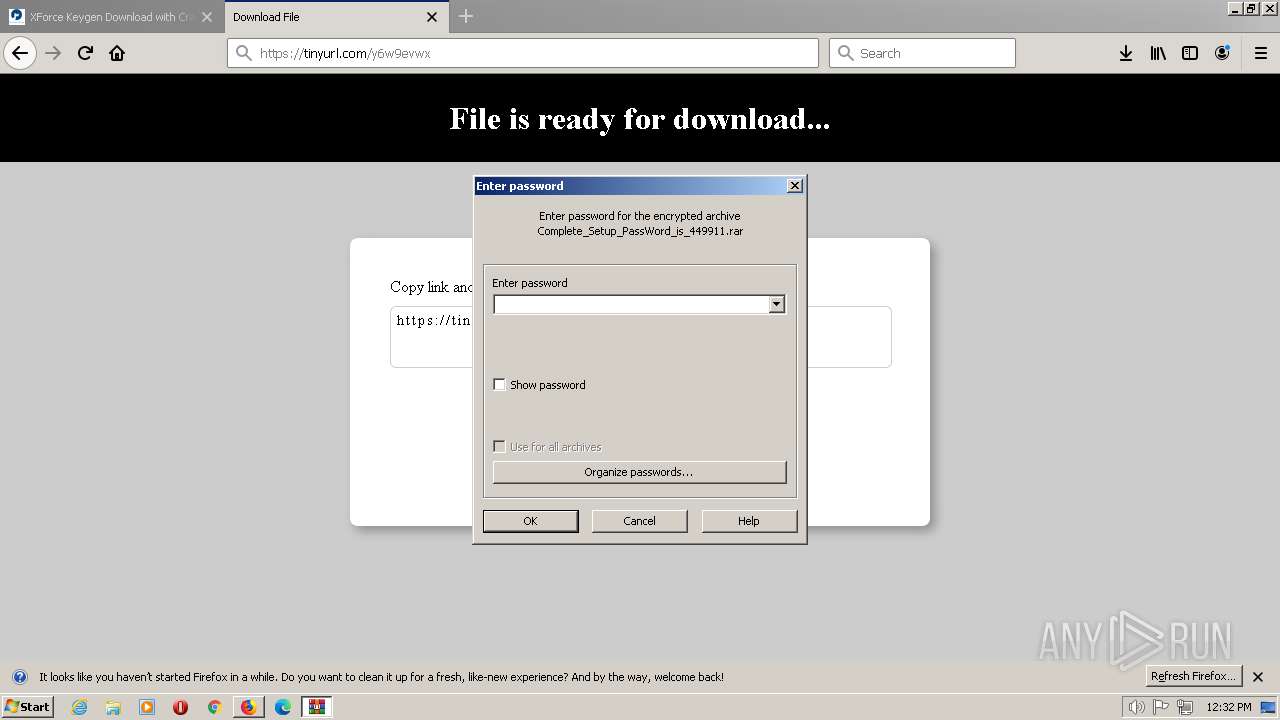
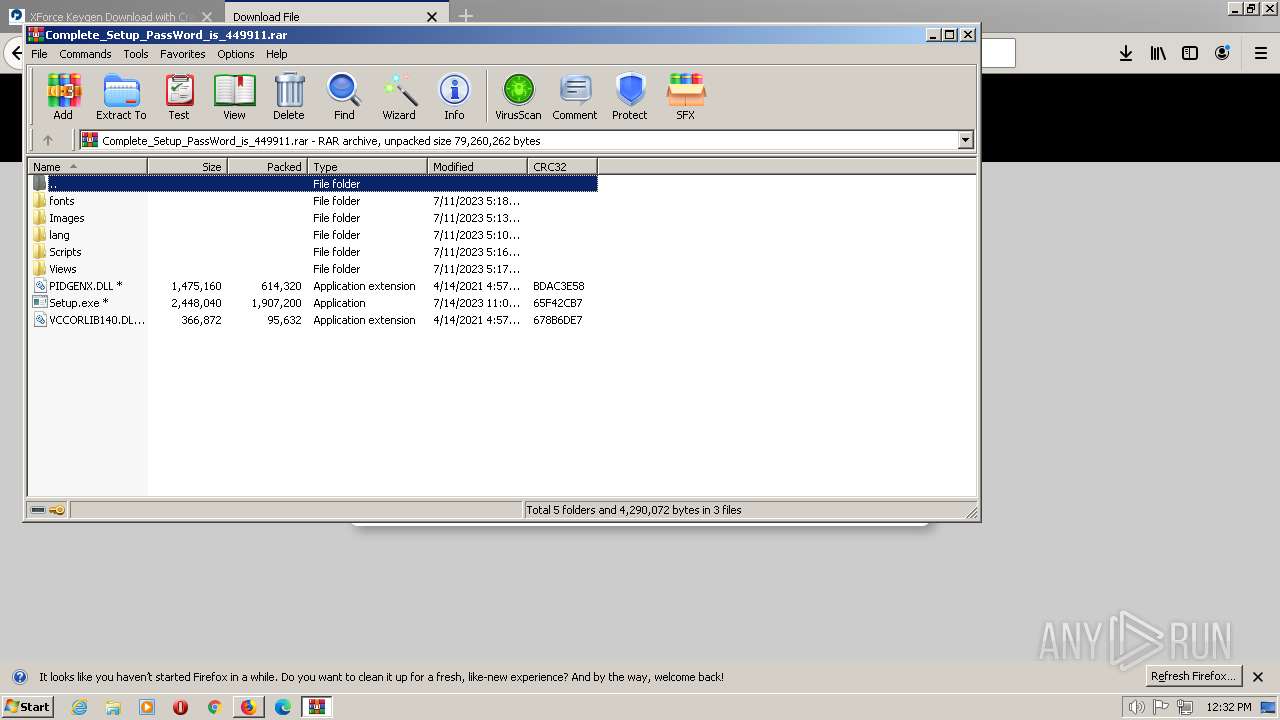
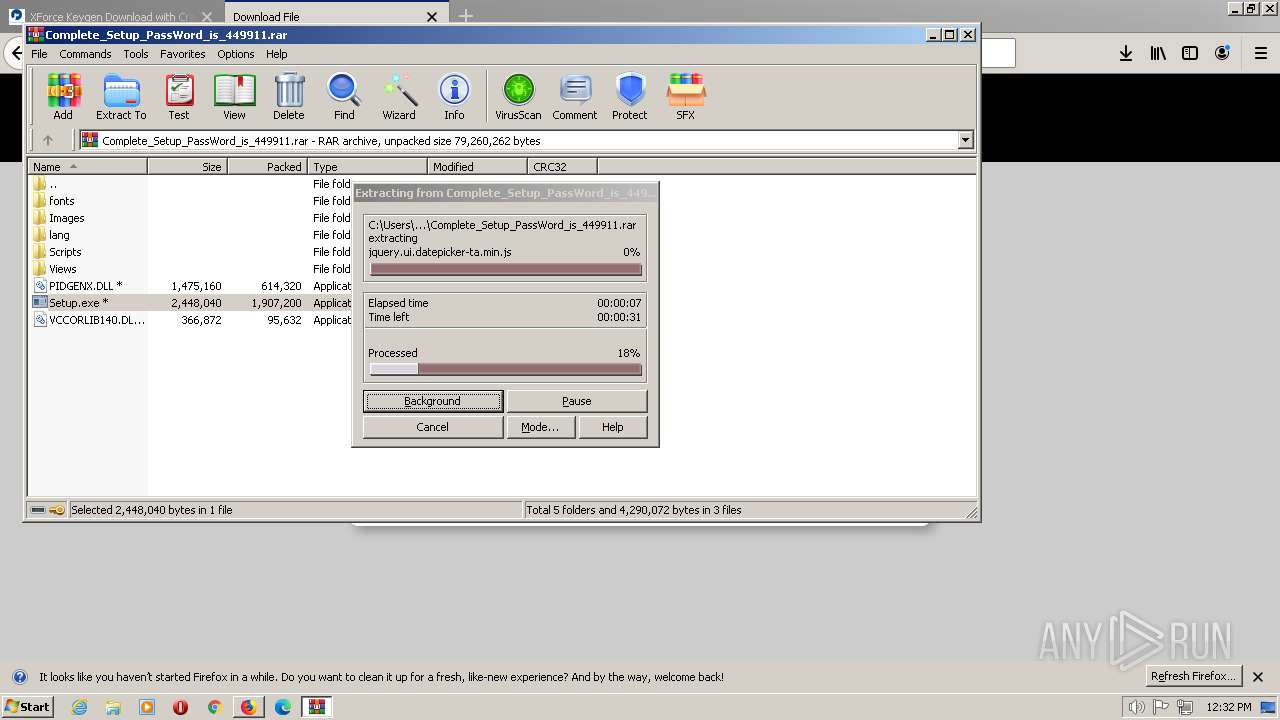
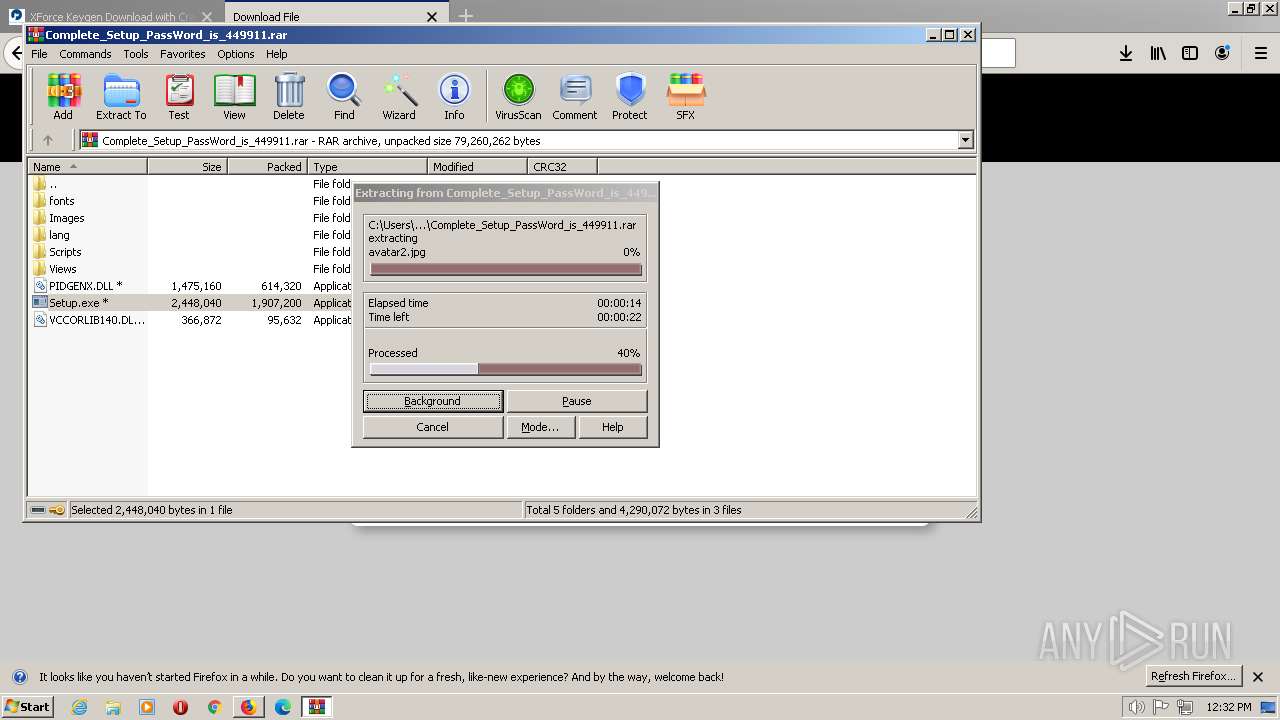
| 3344 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Complete_Setup_PassWord_is_449911.rar" | C:\Program Files\WinRAR\WinRAR.exe | firefox.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3648 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2012.34.2036717300\1431900058" -childID 5 -isForBrowser -prefsHandle 3604 -prefMapHandle 7432 -prefsLen 7498 -prefMapSize 189239 -parentBuildID 20190619235627 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 2012 "\\.\pipe\gecko-crash-server-pipe.2012" 7284 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 67.0.4 Modules
| |||||||||||||||
Total events
6 838
Read events
6 807
Write events
31
Delete events
0
Modification events
| (PID) Process: | (2012) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (2012) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2012) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000008E000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2012) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2012) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2012) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2012) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\155\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3344) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7AndW2K8R2-KB3191566-x64.zip | |||
Executable files
113
Suspicious files
274
Text files
777
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2012 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\startupCache\urlCache-current.bin | binary | |
MD5:6BED2A248268034CA1F73B2925365DE2 | SHA256:A45996AA907815E86366A17ED448F75A584D7B600AA9398E14DE21DFAD3D613A | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\permissions.sqlite-journal | binary | |
MD5:7851637BB557EB8386E826767FEA6D2D | SHA256:7D570D90C69B87AA214A3AA39BC9780167F3F6A714B2F66F7AD3D3452705DEE2 | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\prefs-1.js | text | |
MD5:1759FBCEFAC92AE1A7B8E457ACF71748 | SHA256:5DA473B0E0C84BE5B289DC97C259B98F674E17AF49F4723B4A90F73AA972B739 | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\prefs.js | text | |
MD5:1759FBCEFAC92AE1A7B8E457ACF71748 | SHA256:5DA473B0E0C84BE5B289DC97C259B98F674E17AF49F4723B4A90F73AA972B739 | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\nltxvmn2.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:2B6B5ABCA010270C502C5DD277CD9E7A | SHA256:99DF8717921F70577FCE3386BB7962A804E490C7157F764458001843A1EC606C | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2012 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
76
TCP/UDP connections
156
DNS requests
141
Threats
114
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2012 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r3.o.lencr.org/ | US | binary | 503 b | shared |
2012 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | text | 8 b | whitelisted |
2012 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 471 b | whitelisted |
2012 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r3.o.lencr.org/ | US | binary | 503 b | shared |
2012 | firefox.exe | GET | 200 | 23.53.40.162:80 | http://ciscobinary.openh264.org/openh264-win64-2e1774ab6dc6c43debb0b5b628bdf122a391d521.zip | NL | compressed | 442 Kb | whitelisted |
2012 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r3.o.lencr.org/ | US | binary | 503 b | shared |
2012 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 471 b | whitelisted |
2012 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r3.o.lencr.org/ | US | binary | 503 b | shared |
2012 | firefox.exe | POST | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3 | US | binary | 472 b | whitelisted |
2012 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt | US | text | 8 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2012 | firefox.exe | 188.114.97.3:443 | piratesfile.com | CLOUDFLARENET | NL | malicious |
2012 | firefox.exe | 184.24.77.45:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2012 | firefox.exe | 35.244.181.201:443 | aus5.mozilla.org | GOOGLE | US | suspicious |
2012 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2012 | firefox.exe | 188.114.96.3:443 | piratesfile.com | CLOUDFLARENET | NL | malicious |
2012 | firefox.exe | 34.160.46.54:443 | search.services.mozilla.com | GOOGLE | US | suspicious |
2012 | firefox.exe | 13.32.121.49:443 | snippets.cdn.mozilla.net | AMAZON-02 | US | suspicious |
2012 | firefox.exe | 34.117.65.55:443 | push.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | suspicious |
2012 | firefox.exe | 184.24.77.83:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2012 | firefox.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
piratesfile.com |
| malicious |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
280 | MSBuild.exe | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Win32/Lumma Stealer Configuration Request Attempt |
280 | MSBuild.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Configuration Request Attempt |
280 | MSBuild.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
280 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
280 | MSBuild.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
280 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
280 | MSBuild.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
280 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
280 | MSBuild.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
280 | MSBuild.exe | A Network Trojan was detected | ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2 |
1 ETPRO signatures available at the full report