| File name: | EFTAnubis.exe |
| Full analysis: | https://app.any.run/tasks/41b85e5e-7529-4bfb-8dcd-204f1622de57 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | May 03, 2024, 08:41:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C1E0EB74024AD09C5F3750E58DE67199 |
| SHA1: | 61B531AD13A86C7580D2A4DE36589B3DEEB7BE3B |
| SHA256: | 593C5558CB8B7EE23720B06604DDF701B9239976FE02EAA3652BBCDF5D2EA346 |
| SSDEEP: | 12288:yI8HMtWEkwtyTovkOvGHMBVcuaKc3vVnsmgL8IdQsd6Q7tnJi:/8HoWEkwtuSkWGHMXcDKcfVzgLjdQsdl |
MALICIOUS
Drops the executable file immediately after the start
- EFTAnubis.exe (PID: 3968)
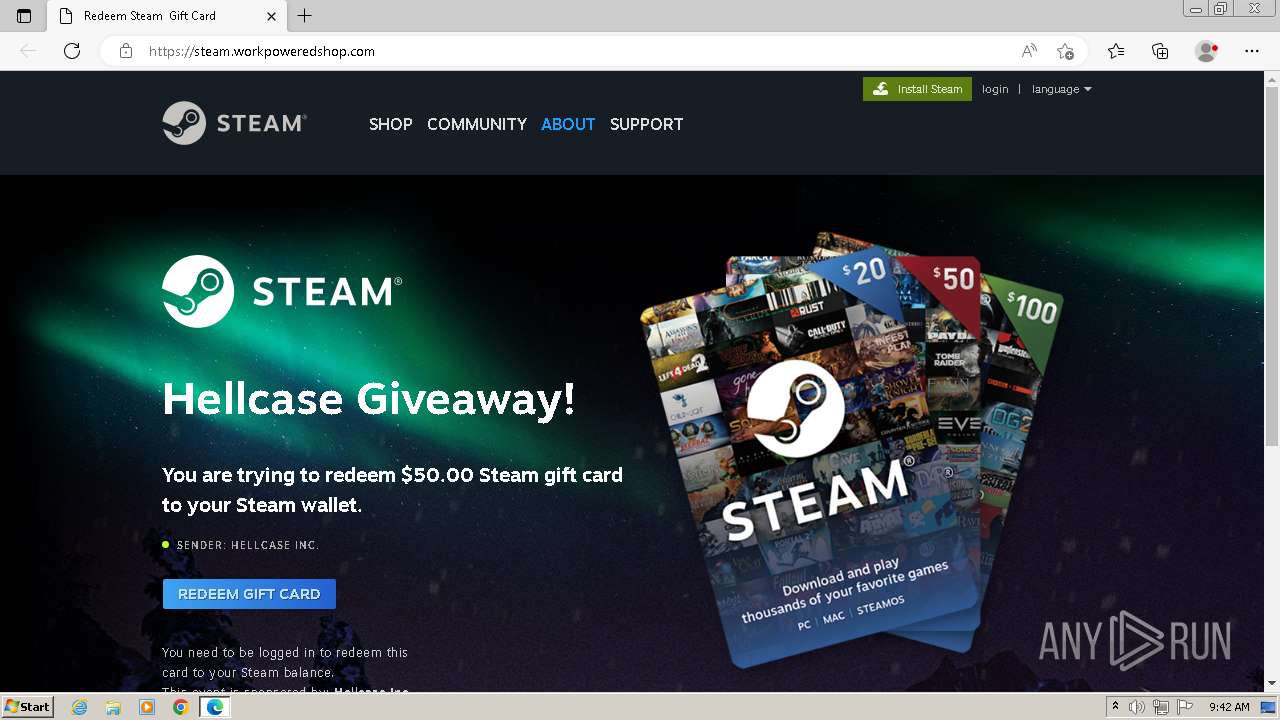
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 3984)
Actions looks like stealing of personal data
- dialer.exe (PID: 3984)
SUSPICIOUS
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 3984)
Searches for installed software
- dialer.exe (PID: 3984)
Connects to unusual port
- dialer.exe (PID: 3984)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 3984)
Reads browser cookies
- dialer.exe (PID: 3984)
Contacting a server suspected of hosting an CnC
- dialer.exe (PID: 3984)
Accesses Microsoft Outlook profiles
- dialer.exe (PID: 3984)
Executable content was dropped or overwritten
- dialer.exe (PID: 3984)
Starts CMD.EXE for commands execution
- e{Zg.exe (PID: 4088)
Reads security settings of Internet Explorer
- e{Zg.exe (PID: 4088)
Executing commands from a ".bat" file
- e{Zg.exe (PID: 4088)
Reads the Internet Settings
- cmd.exe (PID: 1116)
- e{Zg.exe (PID: 4088)
Executed via WMI
- e{Zg.exe (PID: 4088)
INFO
Checks supported languages
- EFTAnubis.exe (PID: 3968)
- wmpnscfg.exe (PID: 4064)
- e{Zg.exe (PID: 4088)
Manual execution by a user
- wmpnscfg.exe (PID: 4064)
Reads the computer name
- wmpnscfg.exe (PID: 4064)
- e{Zg.exe (PID: 4088)
Creates files or folders in the user directory
- dialer.exe (PID: 3984)
Create files in a temporary directory
- e{Zg.exe (PID: 4088)
Application launched itself
- msedge.exe (PID: 2036)
Drops the executable file immediately after the start
- dialer.exe (PID: 3984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:05:13 11:58:23+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.28 |
| CodeSize: | 328192 |
| InitializedDataSize: | 34304 |
| UninitializedDataSize: | 65536 |
| EntryPoint: | 0x508ce |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.6.2.75 |
| ProductVersionNumber: | 2.6.2.75 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| Comments: | TCP/IP Half Open Connection Limit Patch & Monitor |
| CompanyName: | deepxw |
| FileDescription: | TCP-Z, TCP/IP Connection Patch and Monitor. |
| FileVersion: | 2.6.2.75 |
| InternalName: | TCPZ.exe |
| LegalCopyright: | (c) 2009 deepxw. All rights reserved. |
| OriginalFileName: | TCPZ.exe |
| ProductName: | TCP-Z |
| ProductVersion: | 2.6.2.75 |
Total processes
54
Monitored processes
20
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3448 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 616 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1436 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1116 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\aI2DMcnG.bat" " | C:\Windows\System32\cmd.exe | — | e{Zg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1276 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3564 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1660 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1192 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1696 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3648 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2188 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1824 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2148 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1888 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3424 --field-trial-handle=1336,i,2748279690235054932,8377287165795117223,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
7 251
Read events
7 205
Write events
40
Delete events
6
Modification events
| (PID) Process: | (3968) EFTAnubis.exe | Key: | HKEY_CURRENT_USER\Software\SibCode |
| Operation: | write | Name: | sn |
Value: | |||
| (PID) Process: | (4088) e{Zg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4088) e{Zg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4088) e{Zg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4088) e{Zg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2036) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2036) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2036) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2036) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2036) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
Executable files
3
Suspicious files
85
Text files
31
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | — | |
MD5:— | SHA256:— | |||
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b9fb.TMP | — | |
MD5:— | SHA256:— | |||
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10ba3a.TMP | — | |
MD5:— | SHA256:— | |||
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF10bae5.TMP | — | |
MD5:— | SHA256:— | |||
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3984 | dialer.exe | C:\Users\admin\AppData\Local\Microsoft\pY1o.exe | executable | |
MD5:5CD17BEF140FC129ED3D510DF778A0EF | SHA256:2BD06479B563326157FA12FA09DFE82B3F473A802789B9C3E0E20B863E64541F | |||
| 2024 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma~RF10b642.TMP | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 2036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgeCoupons\coupons_data.db\LOG.old~RF10ba0b.TMP | text | |
MD5:B1E05B031BC39D74E7AC1CA69AC72F82 | SHA256:899DE7900989F710A925E38FA5AE4EA2C3B0EF47A1FEEFBF9EB57C21FA513A8E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
31
DNS requests
32
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3984 | dialer.exe | 185.125.50.38:3034 | — | — | RU | unknown |
2036 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
616 | msedge.exe | 13.107.43.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
616 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
616 | msedge.exe | 104.21.21.189:443 | steam.workpoweredshop.com | CLOUDFLARENET | — | unknown |
616 | msedge.exe | 2.19.120.147:443 | steamcommunity-a.akamaihd.net | Akamai International B.V. | DE | unknown |
616 | msedge.exe | 169.150.247.37:443 | cdn.skinbaron.de | — | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
steam.workpoweredshop.com |
| unknown |
edge.microsoft.com |
| whitelisted |
steamcommunity-a.akamaihd.net |
| whitelisted |
cdn.skinbaron.de |
| unknown |
store.cloudflare.steamstatic.com |
| unknown |
cdnjs.cloudflare.com |
| whitelisted |
code.jquery.com |
| whitelisted |
www.bing.com |
| whitelisted |
cookie-cdn.cookiepro.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | STEALER [ANY.RUN] Rhadamanthys SSL Certificate and JA3s |
616 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
6 ETPRO signatures available at the full report