| File name: | image.exe |
| Full analysis: | https://app.any.run/tasks/78d0d169-7b6a-4775-b037-9b5bd64b87ff |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 30, 2020, 17:38:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C57CA9CB0FDE71F074A1DA63C327CE3F |
| SHA1: | E6AF2383E6C375C1ECAF5E412271DFBB0A97B36B |
| SHA256: | 58505CA17B261822BFC5FCF1D73E532917EB7A3EA24917AA64970F76F0B8BE3B |
| SSDEEP: | 3072:NvZxHZ6G3kLu7NQz8jz2D4/m162izYdqynuQ0mrnN5t5Gnrn4XNjh+Pc+Ga++Bnn:Nvx6GwQQz8M42wzYdqynzbGn7UjE |
MALICIOUS
Application was dropped or rewritten from another process
- ab.exe (PID: 2492)
- bb.exe (PID: 2224)
- scvhost.exe (PID: 3784)
Changes the autorun value in the registry
- ab.exe (PID: 2492)
ASYNCRAT was detected
- scvhost.exe (PID: 3784)
SUSPICIOUS
Creates files in the user directory
- image.exe (PID: 2212)
- ab.exe (PID: 2492)
Starts CMD.EXE for commands execution
- image.exe (PID: 2212)
- ab.exe (PID: 2492)
Executable content was dropped or overwritten
- image.exe (PID: 2212)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1148)
Creates files in the user directory
- WINWORD.EXE (PID: 1148)
Manual execution by user
- WINWORD.EXE (PID: 1148)
- taskmgr.exe (PID: 2964)
Reads settings of System Certificates
- scvhost.exe (PID: 3784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:05:20 09:46:10+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 35328 |
| InitializedDataSize: | 138752 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7ee4 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
| CompanyName: | none[none] |
| FileDescription: | - |
| FileVersion: | 1. 0. 0. 1 |
| LegalCopyright: | none[none] |
| ProductName: | - |
| ProductVersion: | 1. 0. 0. 1 |
Total processes
48
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | timeout 5 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
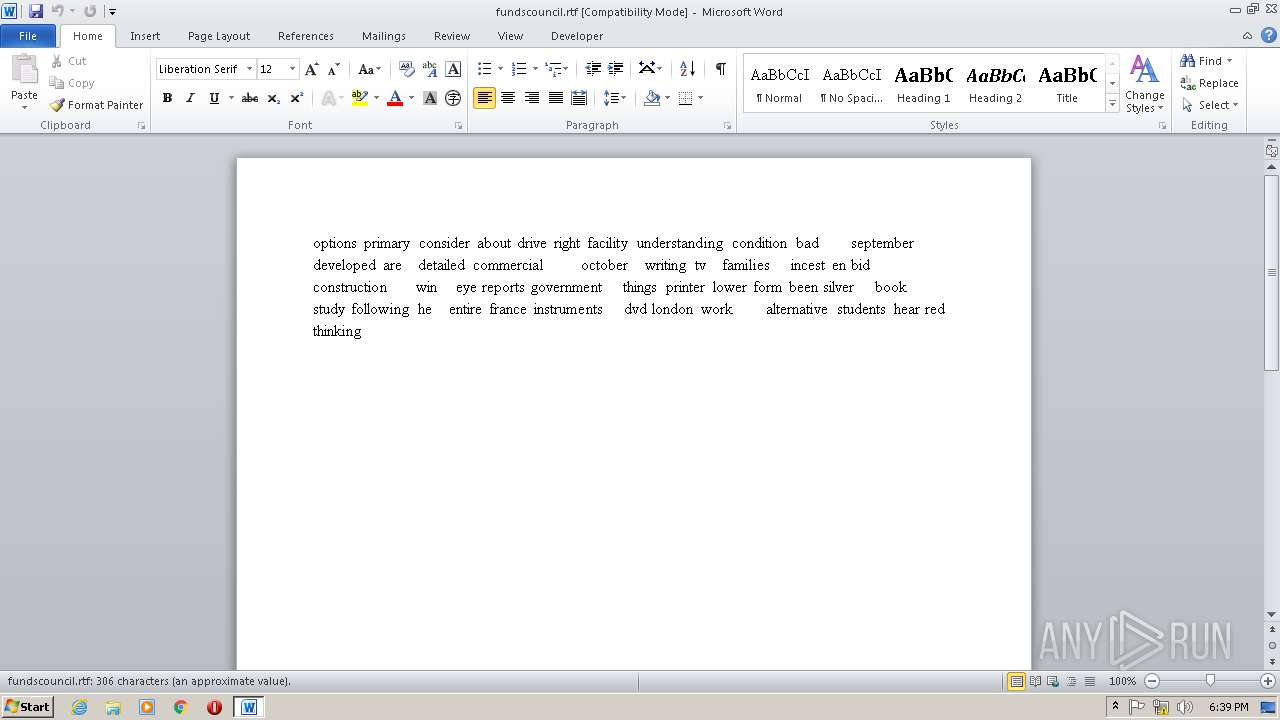
| 1148 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\fundscouncil.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1744 | timeout 5 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2212 | "C:\Users\admin\AppData\Local\Temp\image.exe" | C:\Users\admin\AppData\Local\Temp\image.exe | explorer.exe | ||||||||||||
User: admin Company: none[none] Integrity Level: MEDIUM Exit code: 0 Version: 1. 0. 0. 1 Modules
| |||||||||||||||
| 2224 | bb.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Themes\bb.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2284 | cmd /c ""C:\Users\admin\AppData\Local\Temp\tmpED71.tmp.bat"" | C:\Windows\system32\cmd.exe | — | ab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2492 | ab.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Themes\ab.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.3.9600.17415 Modules
| |||||||||||||||
| 2876 | cmd /c ""C:\Users\admin\AppData\Roaming\Untitled1.bat" > NUL" | C:\Windows\system32\cmd.exe | — | image.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2964 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3024 | timeout 3 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 494
Read events
761
Write events
588
Delete events
145
Modification events
| (PID) Process: | (2492) ab.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2492) ab.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (2492) ab.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
| (PID) Process: | (2492) ab.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dnsapi.dll,-103 |
Value: Domain Name System (DNS) Server Trust | |||
| (PID) Process: | (2492) ab.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-843 |
Value: BitLocker Drive Encryption | |||
| (PID) Process: | (2492) ab.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\fveui.dll,-844 |
Value: BitLocker Data Recovery Agent | |||
| (PID) Process: | (1148) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 2($ |
Value: 322824007C040000010000000000000000000000 | |||
| (PID) Process: | (1148) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1148) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1148) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
Executable files
2
Suspicious files
0
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1148 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD083.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2492 | ab.exe | C:\Users\admin\AppData\Roaming\scvhost.exe | — | |
MD5:— | SHA256:— | |||
| 1148 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\fundscouncil.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2212 | image.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Themes\ab.exe | executable | |
MD5:— | SHA256:— | |||
| 2212 | image.exe | C:\Users\admin\AppData\Roaming\Untitled1.bat | text | |
MD5:— | SHA256:— | |||
| 2212 | image.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Themes\bb.exe | executable | |
MD5:— | SHA256:— | |||
| 1148 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1148 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 1148 | WINWORD.EXE | C:\Users\admin\Desktop\~$ndscouncil.rtf | pgc | |
MD5:— | SHA256:— | |||
| 2492 | ab.exe | C:\Users\admin\AppData\Local\Temp\tmpED71.tmp.bat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2224 | bb.exe | 176.57.68.202:7073 | 1.ngprince.com | — | — | unknown |
3784 | scvhost.exe | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
3784 | scvhost.exe | 185.206.212.36:7071 | — | LeaseWeb Netherlands B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
1.ngprince.com |
| malicious |
dns.msftncsi.com |
| shared |
pastebin.com |
| malicious |