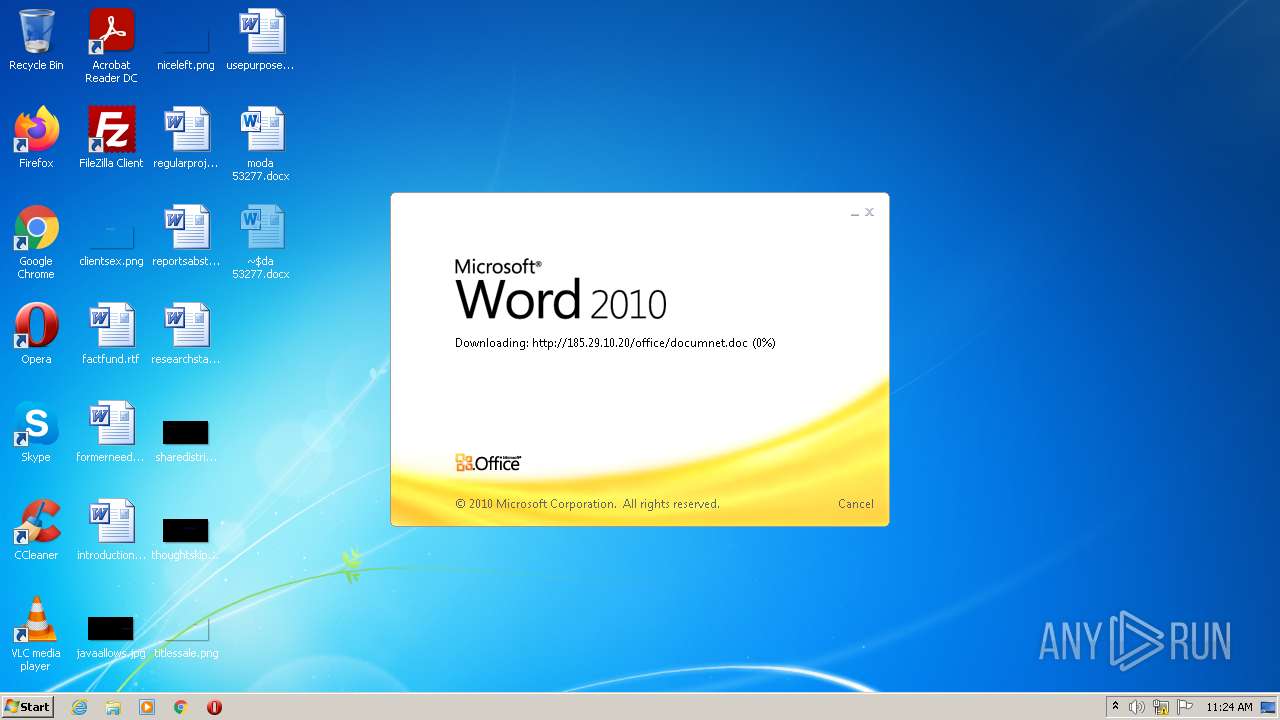
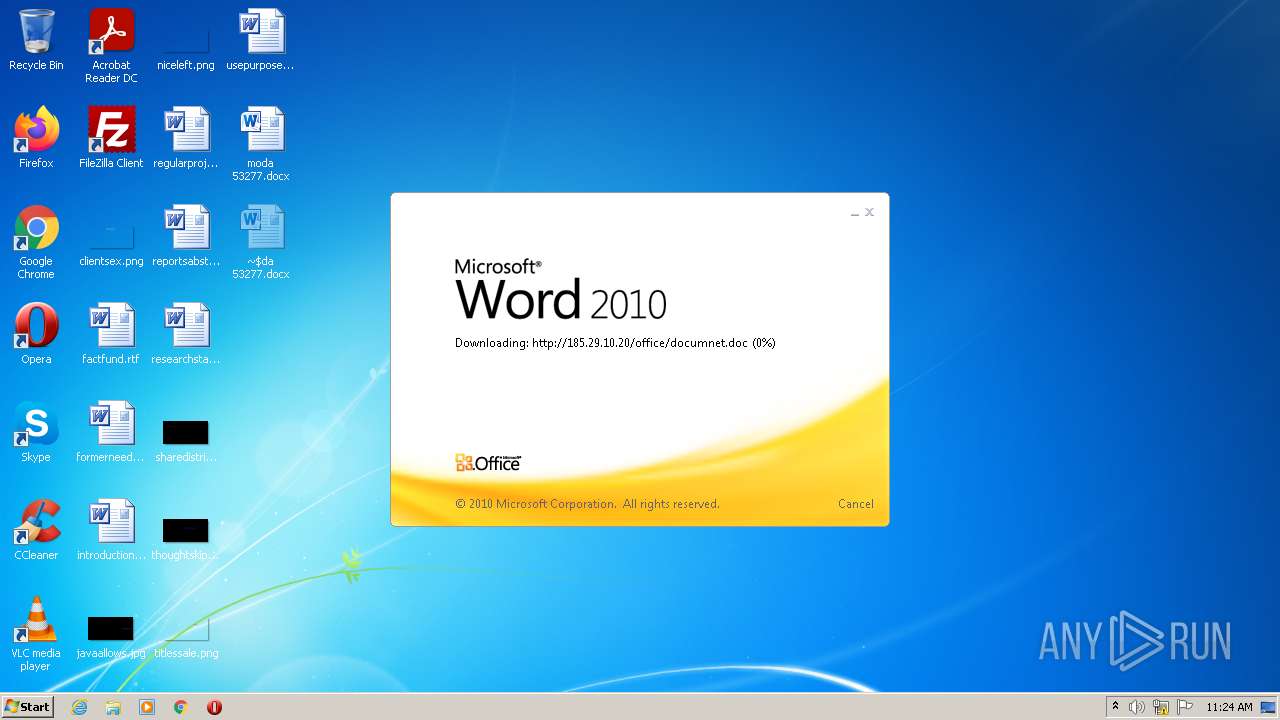
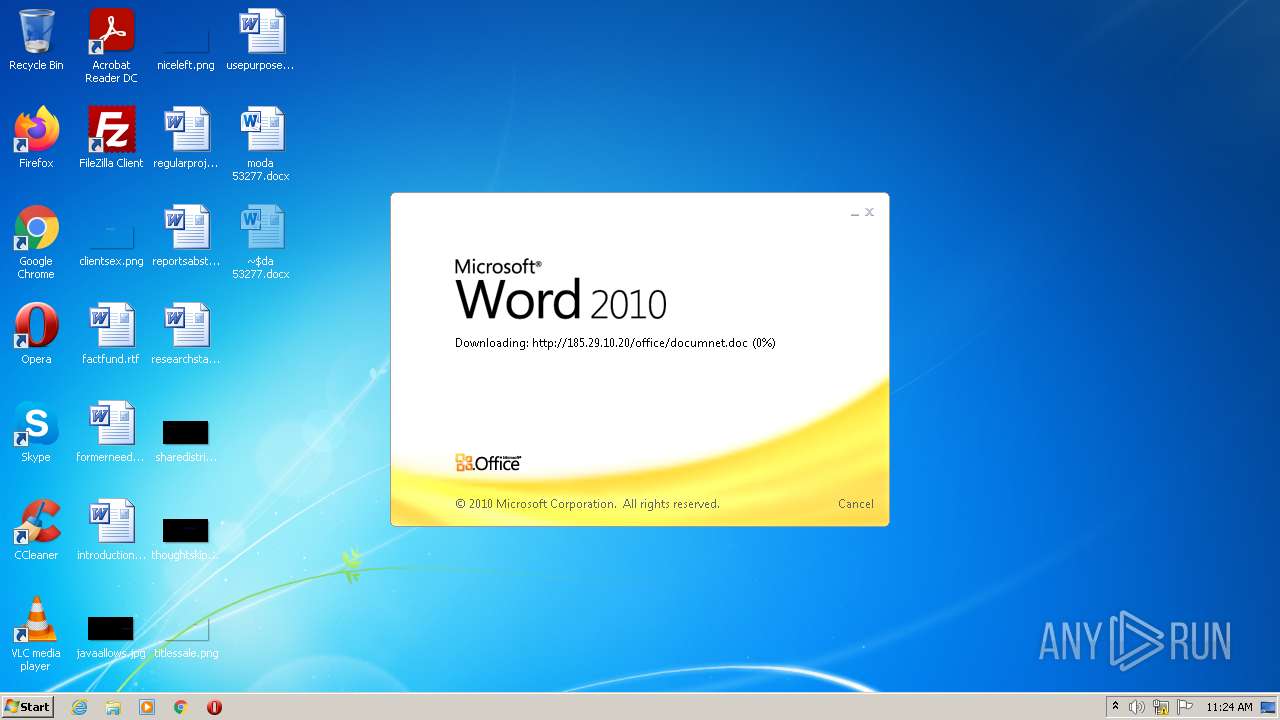
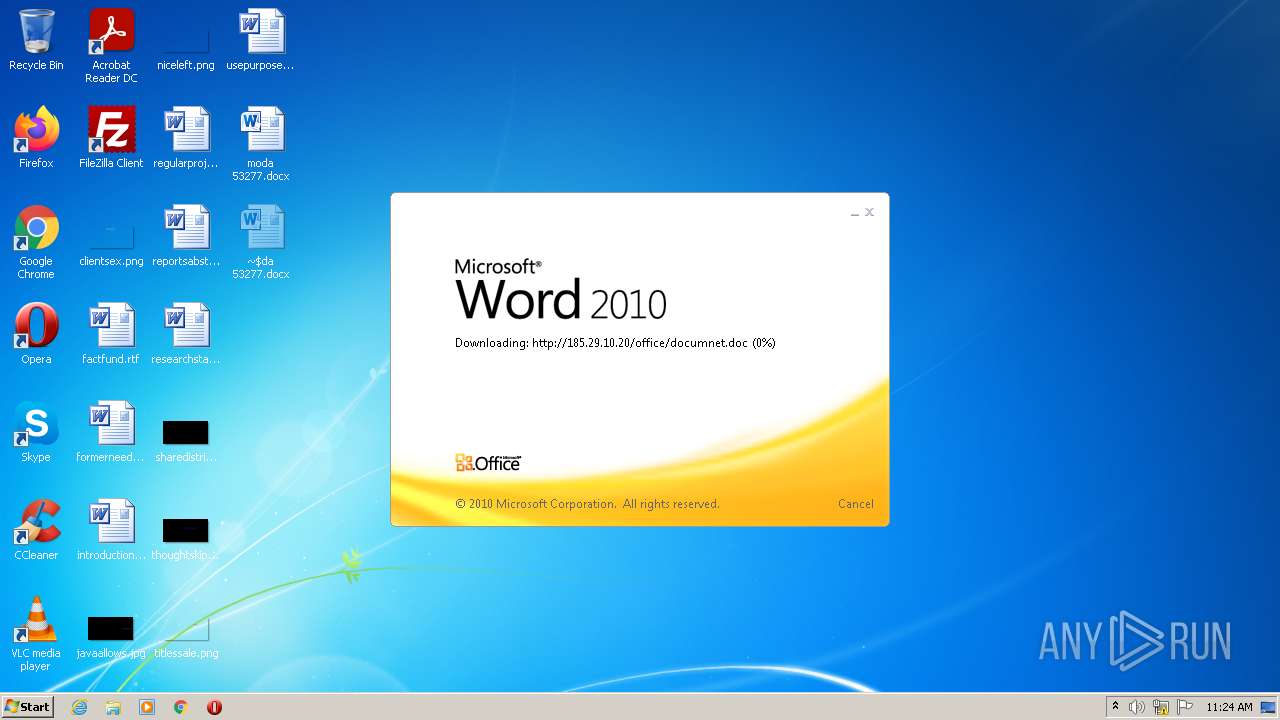
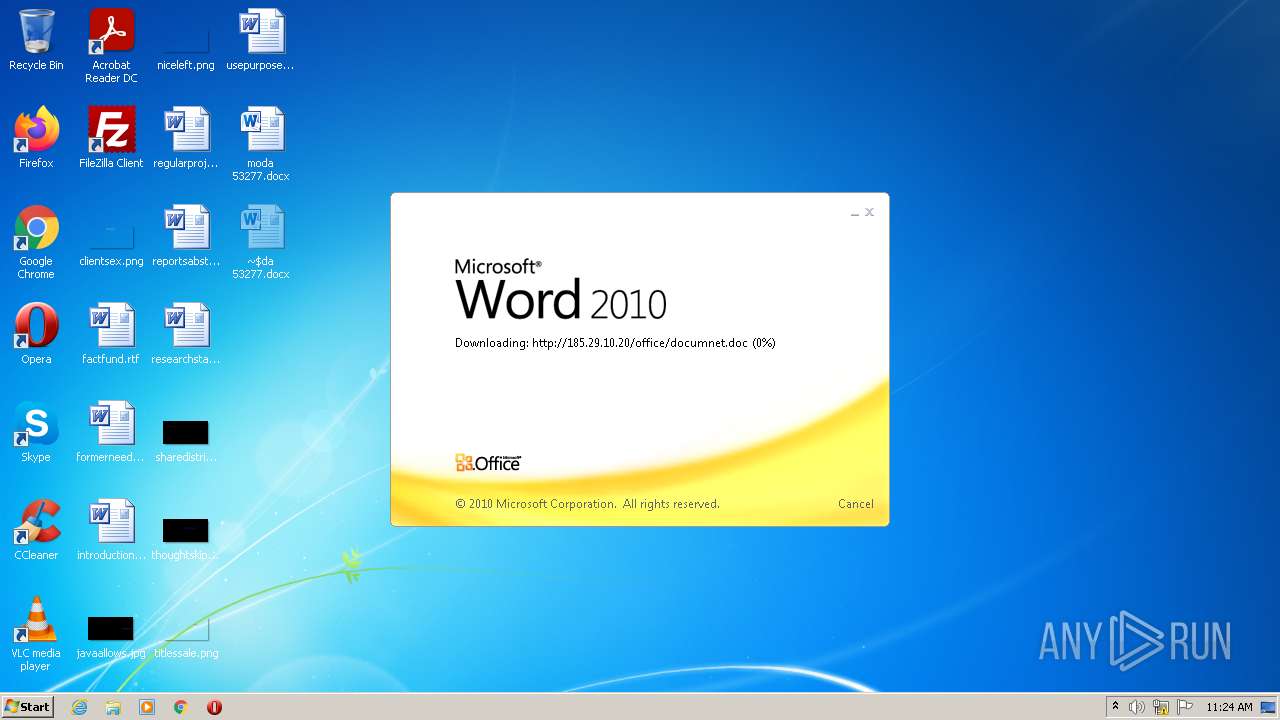
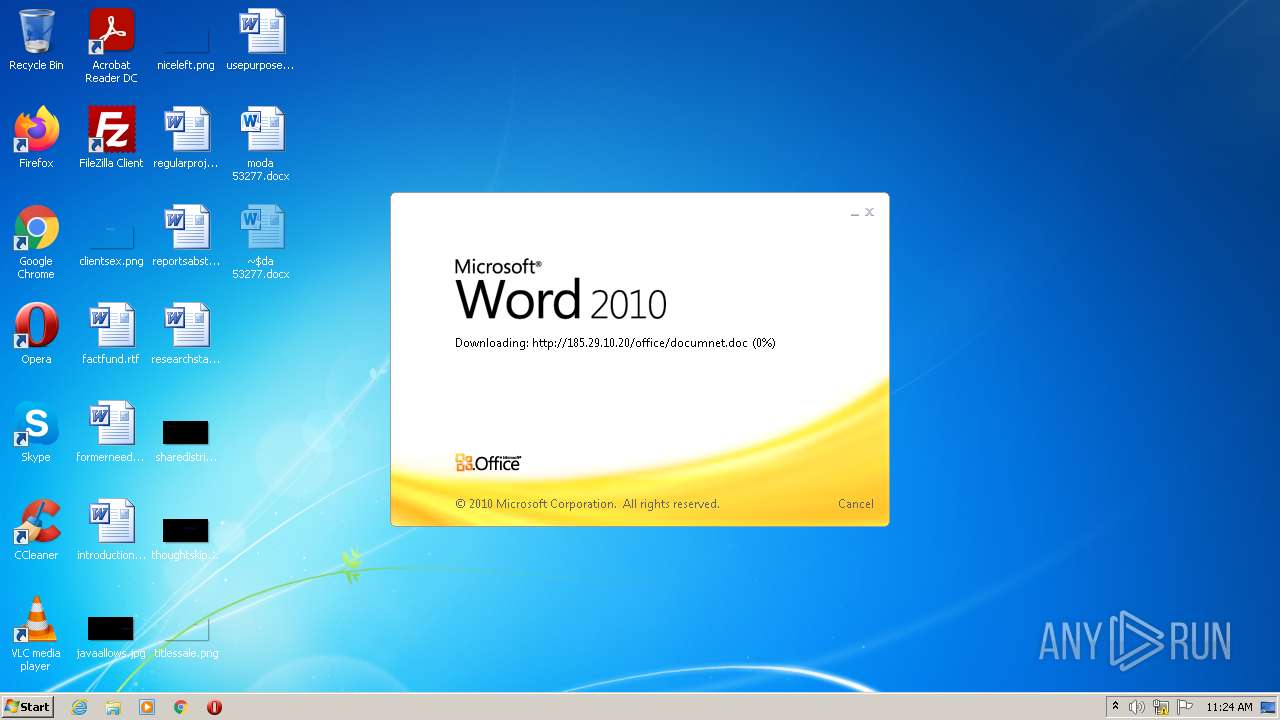
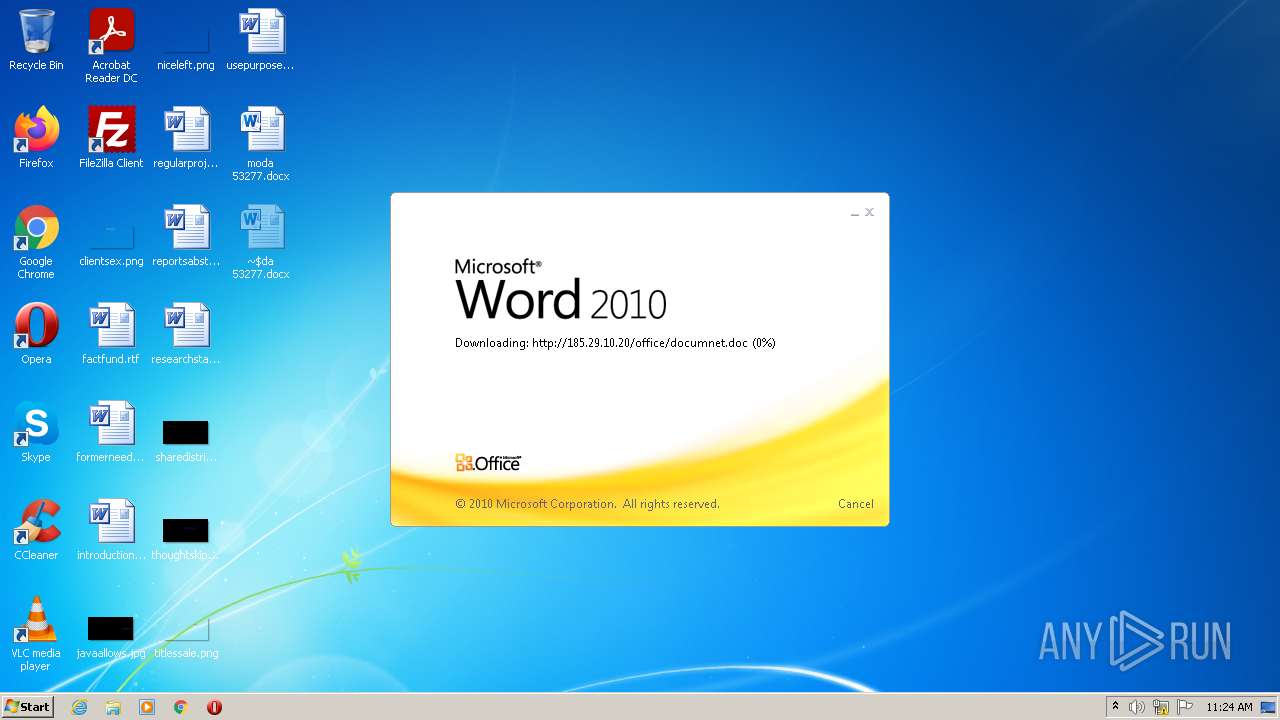
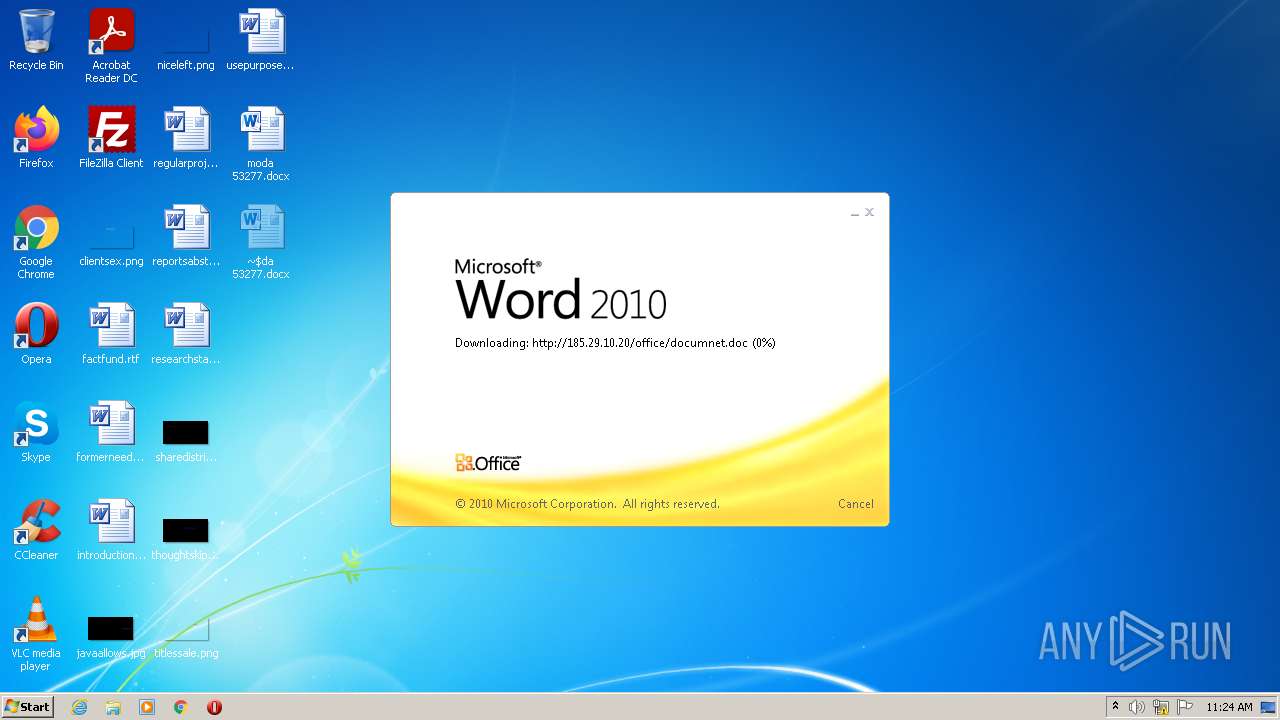
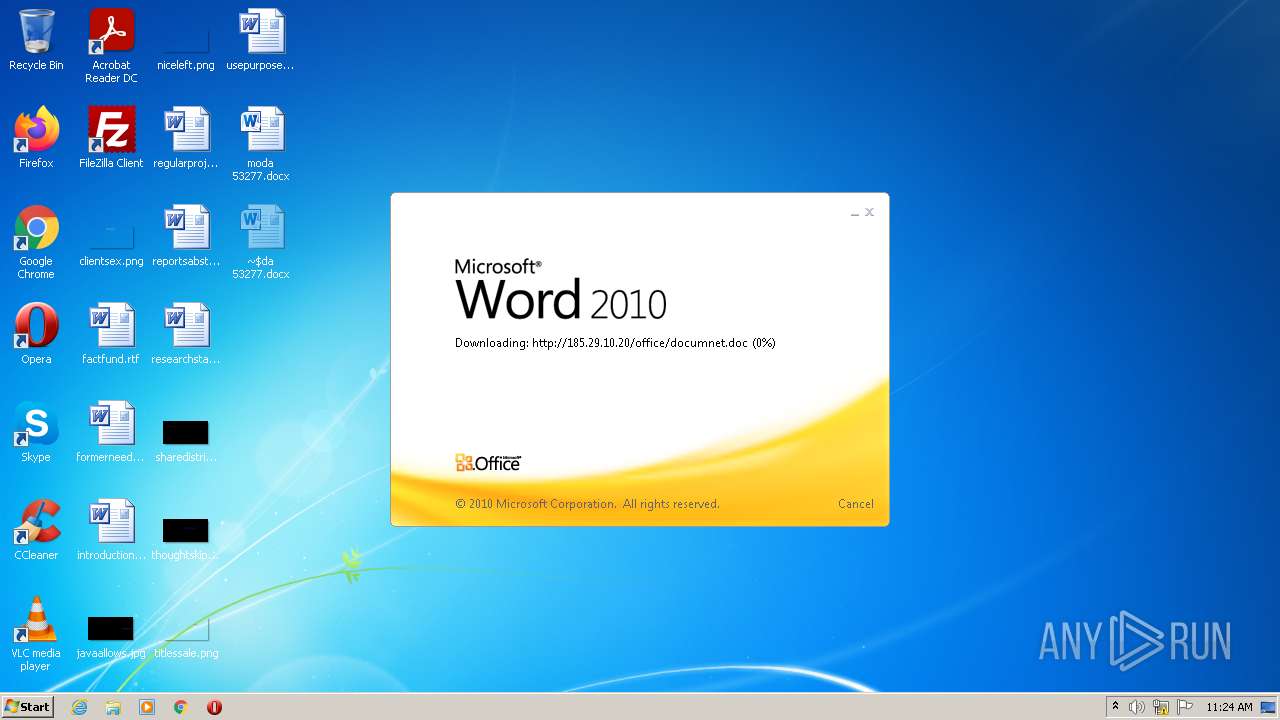
| File name: | moda 53277.docx |
| Full analysis: | https://app.any.run/tasks/0cf8ae18-6de1-48da-9573-53157a856729 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 27, 2022, 10:23:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 8E773257D2BDBA4F419381847D4C2D2F |
| SHA1: | 19ADB078B4842FD999FE54EB875982FDB4FD43E9 |
| SHA256: | 583E4B292BD2A2EE7CFA93E375DD303248FFDB2C2D1F801F87B31283ACA48D54 |
| SSDEEP: | 96:kHcIMm57P678dmGJa6T/n/jNTjM8UGZ1Z4W2qO+ItaT9HkLqBpN6iAEkWmIzGi3x:ScIMmtPypG/bRXUq1O8mamWBXPfxZ31F |
MALICIOUS
Drops executable file immediately after starts
- EQNEDT32.EXE (PID: 948)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 948)
Application was dropped or rewritten from another process
- vbc.exe (PID: 3220)
Changes settings of System certificates
- vbc.exe (PID: 3220)
ASYNCRAT detected by memory dumps
- InstallUtil.exe (PID: 536)
ASYNCRAT was detected
- InstallUtil.exe (PID: 536)
SUSPICIOUS
Reads the computer name
- EQNEDT32.EXE (PID: 948)
- vbc.exe (PID: 3220)
- InstallUtil.exe (PID: 536)
Checks supported languages
- EQNEDT32.EXE (PID: 948)
- vbc.exe (PID: 3220)
- InstallUtil.exe (PID: 536)
Executed via COM
- EQNEDT32.EXE (PID: 948)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 948)
Drops a file with a compile date too recent
- EQNEDT32.EXE (PID: 948)
Reads Environment values
- vbc.exe (PID: 3220)
- InstallUtil.exe (PID: 536)
Adds / modifies Windows certificates
- vbc.exe (PID: 3220)
INFO
Reads the computer name
- WINWORD.EXE (PID: 2956)
Checks supported languages
- WINWORD.EXE (PID: 2956)
- WINWORD.EXE (PID: 3160)
Creates files in the user directory
- WINWORD.EXE (PID: 2956)
Reads settings of System Certificates
- vbc.exe (PID: 3220)
- InstallUtil.exe (PID: 536)
Manual execution by user
- WINWORD.EXE (PID: 3160)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3160)
- WINWORD.EXE (PID: 2956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(536) InstallUtil.exe
C2 (1)80.66.64.151
Ports (1)7070
Version5.0.5
Autorunfalse
MutexVenom_RAT_HVNC_Mutex_Venom RAT_HVNC
CertificateMIICMzCCAZygAwIBAgIVALgbuadTIXCBGx92qk2Pt658vf8pMA0GCSqGSIb3DQEBDQUAMGcxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIxMDExMjE3MzIzNloXDTMxMTAyMjE3MzIzNlowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQAD...
Server_SignatureB/XjFBRiKlO4ES3xsOmsifR+xvtzAS7oOzNO7X0CXGh4WxgOsiHQRNTmLB67KGxp+eEUSv/jyNDDPegkeQcVW7ByXBfyfmTJKEXH/BIHmBgTQlCLi6n33wAQMamYTxELJEXg5bwkGmbC3g5hPoBAGcAa14++/Z8NBA9Fh119Pek=
AntiVMfalse
PasteBinnull
bdosfalse
Botnetvenom clients
Aes_Key49a509e4cda8c0bad6f636694b84afd03828cebb42f150479037411abf985717
SaltVenomByVenom
Install_Folder%AppData%
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
XMP
| Creator: | HP 15 |
|---|
XML
| ModifyDate: | 2022:06:16 07:33:00Z |
|---|---|
| CreateDate: | 2018:03:07 09:39:00Z |
| RevisionNumber: | 2 |
| LastModifiedBy: | 91974 |
| AppVersion: | 12 |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| CharactersWithSpaces: | 5 |
| LinksUpToDate: | No |
| Company: | Grizli777 |
| ScaleCrop: | No |
| Paragraphs: | 1 |
| Lines: | 1 |
| DocSecurity: | None |
| Application: | Microsoft Office Word |
| Characters: | 5 |
| Words: | - |
| Pages: | 1 |
| TotalEditTime: | - |
| Template: | Normal.dotm |
ZIP
| ZipFileName: | [Content_Types].xml |
|---|---|
| ZipUncompressedSize: | 1312 |
| ZipCompressedSize: | 358 |
| ZipCRC: | 0x3795fcdd |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0006 |
| ZipRequiredVersion: | 20 |
Total processes
47
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe | vbc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Framework installation utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
AsyncRat(PID) Process(536) InstallUtil.exe C2 (1)80.66.64.151 Ports (1)7070 Version5.0.5 Autorunfalse MutexVenom_RAT_HVNC_Mutex_Venom RAT_HVNC CertificateMIICMzCCAZygAwIBAgIVALgbuadTIXCBGx92qk2Pt658vf8pMA0GCSqGSIb3DQEBDQUAMGcxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIxMDExMjE3MzIzNloXDTMxMTAyMjE3MzIzNlowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQAD... Server_SignatureB/XjFBRiKlO4ES3xsOmsifR+xvtzAS7oOzNO7X0CXGh4WxgOsiHQRNTmLB67KGxp+eEUSv/jyNDDPegkeQcVW7ByXBfyfmTJKEXH/BIHmBgTQlCLi6n33wAQMamYTxELJEXg5bwkGmbC3g5hPoBAGcAa14++/Z8NBA9Fh119Pek= AntiVMfalse PasteBinnull bdosfalse Botnetvenom clients Aes_Key49a509e4cda8c0bad6f636694b84afd03828cebb42f150479037411abf985717 SaltVenomByVenom Install_Folder%AppData% | |||||||||||||||
| 948 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 2956 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\moda 53277.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3160 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\researchstage.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3220 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | EQNEDT32.EXE | ||||||||||||
User: admin Company: 5H:?CCI@GE7CCD<84D; Integrity Level: MEDIUM Description: =?B4=C75EBAEB7:D Exit code: 0 Version: 5.7.10.12 Modules
| |||||||||||||||
Total events
8 524
Read events
7 380
Write events
804
Delete events
340
Modification events
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | g0< |
Value: 67303C008C0B0000010000000000000000000000 | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2956) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
10
Text files
3
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR90D8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6BB7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{ACB1F9BB-36ED-4A48-A0D4-878C7AA659A3} | binary | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{7A186311-7347-482F-BE38-826074A0D1FF} | binary | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\4D9204EA.doc | binary | |
MD5:— | SHA256:— | |||
| 2956 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\documnet[1].doc | binary | |
MD5:— | SHA256:— | |||
| 948 | EQNEDT32.EXE | C:\Users\Public\vbc.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
12
DNS requests
3
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2956 | WINWORD.EXE | OPTIONS | 200 | 185.29.10.20:80 | http://185.29.10.20/office/ | SE | — | — | malicious |
2956 | WINWORD.EXE | HEAD | 200 | 185.29.10.20:80 | http://185.29.10.20/office/documnet.doc | SE | — | — | malicious |
824 | svchost.exe | PROPFIND | 302 | 185.29.10.20:80 | http://185.29.10.20/ | SE | — | — | malicious |
824 | svchost.exe | OPTIONS | 301 | 185.29.10.20:80 | http://185.29.10.20/office | SE | html | 338 b | malicious |
824 | svchost.exe | OPTIONS | 200 | 185.29.10.20:80 | http://185.29.10.20/office/ | SE | html | 338 b | malicious |
2956 | WINWORD.EXE | HEAD | 200 | 185.29.10.20:80 | http://185.29.10.20/office/documnet.doc | SE | binary | 23.3 Kb | malicious |
2956 | WINWORD.EXE | GET | 200 | 185.29.10.20:80 | http://185.29.10.20/office/documnet.doc | SE | binary | 23.3 Kb | malicious |
824 | svchost.exe | PROPFIND | 301 | 185.29.10.20:80 | http://185.29.10.20/office | SE | html | 338 b | malicious |
824 | svchost.exe | PROPFIND | 301 | 185.29.10.20:80 | http://185.29.10.20/office | SE | html | 338 b | malicious |
824 | svchost.exe | PROPFIND | 405 | 185.29.10.20:80 | http://185.29.10.20/office/ | SE | html | 328 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
948 | EQNEDT32.EXE | 185.29.10.20:80 | — | DataClub S.A. | SE | malicious |
536 | InstallUtil.exe | 80.66.64.151:7070 | — | AB-Telecom Ltd. | RU | malicious |
3220 | vbc.exe | 142.250.184.196:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2956 | WINWORD.EXE | 185.29.10.20:80 | — | DataClub S.A. | SE | malicious |
824 | svchost.exe | 185.29.10.20:80 | — | DataClub S.A. | SE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
www.google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2956 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
2956 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
2956 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Suspicious Request for Doc to IP Address with Terse Headers |
2956 | WINWORD.EXE | A Network Trojan was detected | ET CURRENT_EVENTS CVE-2017-0199 Common Obfus Stage 2 DL |
2956 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Possible RTF File With Obfuscated Version Header |
2956 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
948 | EQNEDT32.EXE | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
948 | EQNEDT32.EXE | A Network Trojan was detected | ET TROJAN MSIL/GenKryptik.FQRH Download Request |
948 | EQNEDT32.EXE | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
948 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
2 ETPRO signatures available at the full report