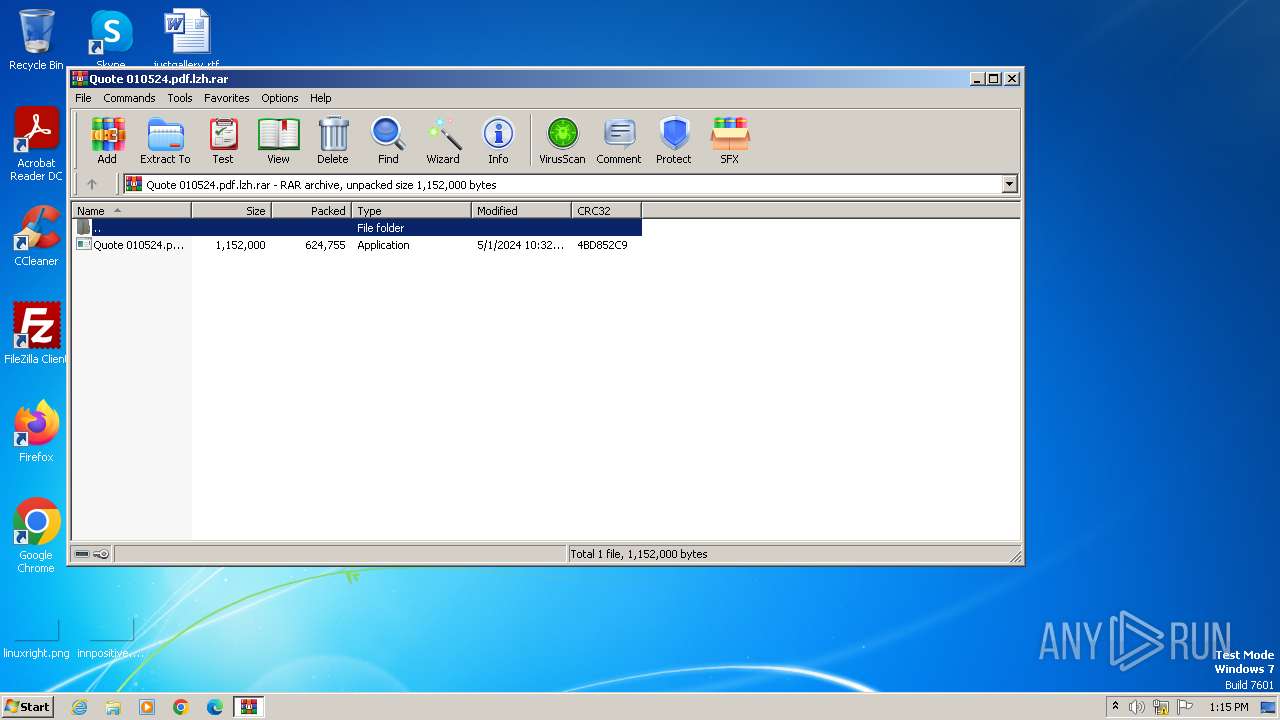
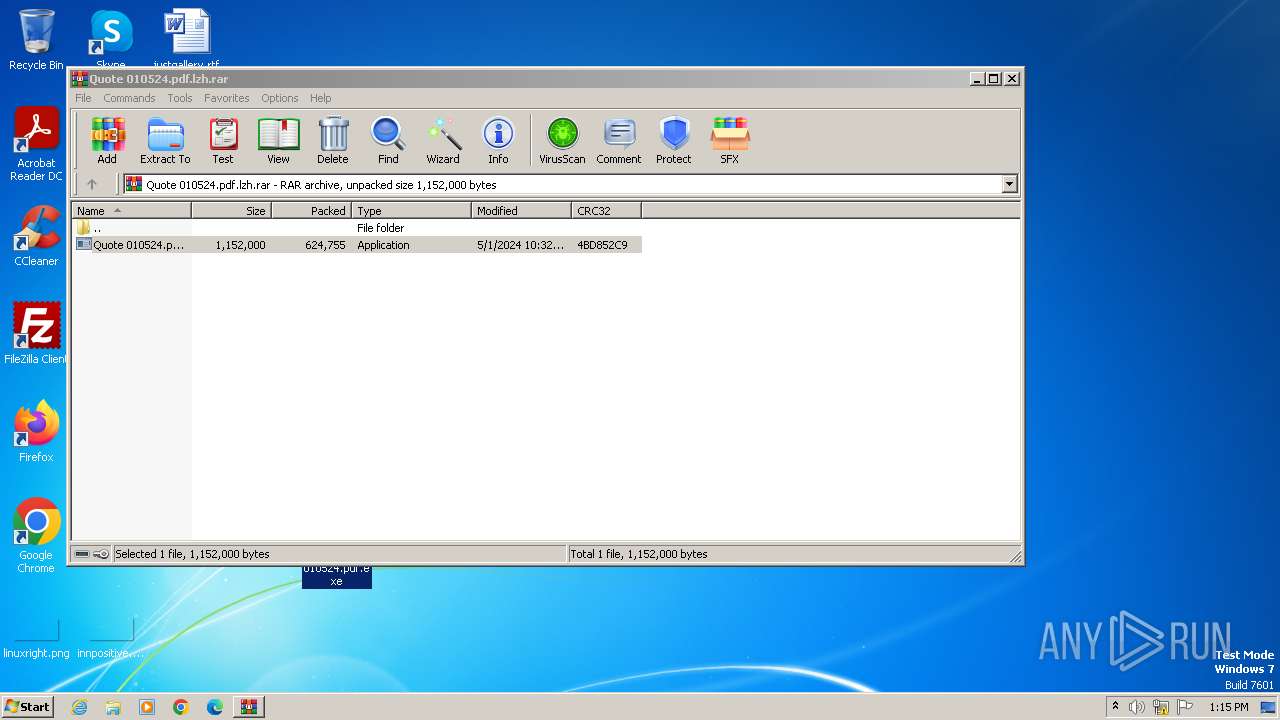
| File name: | Quote 010524.pdf.lzh |
| Full analysis: | https://app.any.run/tasks/f6c87e3d-0eb9-456e-97c8-4b007843bcc2 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 01, 2024, 12:15:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1EBDACA785BA5A0CD48530CF4D9E05A1 |
| SHA1: | 7DC628B461A63CA4D89F746C8CE48B275BE552A1 |
| SHA256: | 5820CBE7645D26B5359BA8D74FA2121A36214146A5ECCBCE9F81B95C9282EEC4 |
| SSDEEP: | 24576:qPuMwRtkqBb1MRvDcyYltJBrrbJyjxLuWdTptLBLzygyPyrPK:qPuMwRtkqBb1MRvoyYltJBfb8lLuWdTy |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3968)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 2072)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 2072)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 2072)
SUSPICIOUS
Connects to SMTP port
- RegSvcs.exe (PID: 2072)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 2072)
Reads settings of System Certificates
- RegSvcs.exe (PID: 2072)
INFO
Manual execution by a user
- Quote 010524.pdf.exe (PID: 4084)
- wmpnscfg.exe (PID: 1112)
Reads mouse settings
- Quote 010524.pdf.exe (PID: 4084)
Checks supported languages
- Quote 010524.pdf.exe (PID: 4084)
- RegSvcs.exe (PID: 2072)
- wmpnscfg.exe (PID: 1112)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Create files in a temporary directory
- Quote 010524.pdf.exe (PID: 4084)
Reads the computer name
- RegSvcs.exe (PID: 2072)
- wmpnscfg.exe (PID: 1112)
Reads Environment values
- RegSvcs.exe (PID: 2072)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 2072)
Reads the software policy settings
- RegSvcs.exe (PID: 2072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(2072) RegSvcs.exe
Protocolsmtp
Hostmail.itzayanaland.com
Port587
Usernamesecuritys@itzayanaland.com
PasswordVxha5,yybO%M ---
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1112 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\Desktop\Quote 010524.pdf.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | Quote 010524.pdf.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Version: 4.8.3761.0 built by: NET48REL1 Modules
AgentTesla(PID) Process(2072) RegSvcs.exe Protocolsmtp Hostmail.itzayanaland.com Port587 Usernamesecuritys@itzayanaland.com PasswordVxha5,yybO%M --- | |||||||||||||||
| 3968 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Quote 010524.pdf.lzh.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4084 | "C:\Users\admin\Desktop\Quote 010524.pdf.exe" | C:\Users\admin\Desktop\Quote 010524.pdf.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 2.0.8.5 Modules
| |||||||||||||||
Total events
7 896
Read events
7 860
Write events
36
Delete events
0
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Quote 010524.pdf.lzh.rar | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
2
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3968.6458\Quote 010524.pdf.exe | executable | |
MD5:914D63AF12A0E88389D204B697D8FE9A | SHA256:93DE3DB7A328B701271DD9F85AE72CD96CA1FA871214C2E1ACF231FDE3C55431 | |||
| 4084 | Quote 010524.pdf.exe | C:\Users\admin\AppData\Local\Temp\hepatoduodenostomy | binary | |
MD5:86C3B59BCEF01CB0E98CDE326B202EEE | SHA256:C0D7C3668EF20769FCE7D71FF7F58DBC81ACE9CD0A006D3D07251D90CB171354 | |||
| 4084 | Quote 010524.pdf.exe | C:\Users\admin\AppData\Local\Temp\aut6CE6.tmp | binary | |
MD5:217AEF56B3ED3A15BAC0E436C11FF791 | SHA256:D68E5B5E900122C44F28C73C93E3774EB23D2B02CC754EC8C7DF699EFDAFCFAF | |||
| 4084 | Quote 010524.pdf.exe | C:\Users\admin\AppData\Local\Temp\aut6CB6.tmp | binary | |
MD5:2EB6F534EE9EB0161EE4EBF4AF9DEB43 | SHA256:0485433888D7EBB699E323D4F3AB3D5E56406A8071CF936261B8F39188BAF627 | |||
| 4084 | Quote 010524.pdf.exe | C:\Users\admin\AppData\Local\Temp\tapestring | text | |
MD5:96217F77EF397ED0473000B1914FCBB3 | SHA256:5DBC5527E129734399B1E43E33C73862D25808B74C681AB348AB0865B2570E24 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2072 | RegSvcs.exe | 107.161.75.133:587 | mail.itzayanaland.com | IWEB-AS | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mail.itzayanaland.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | INFO [ANY.RUN] SMTP email client opens transfer with server (EHLO) |