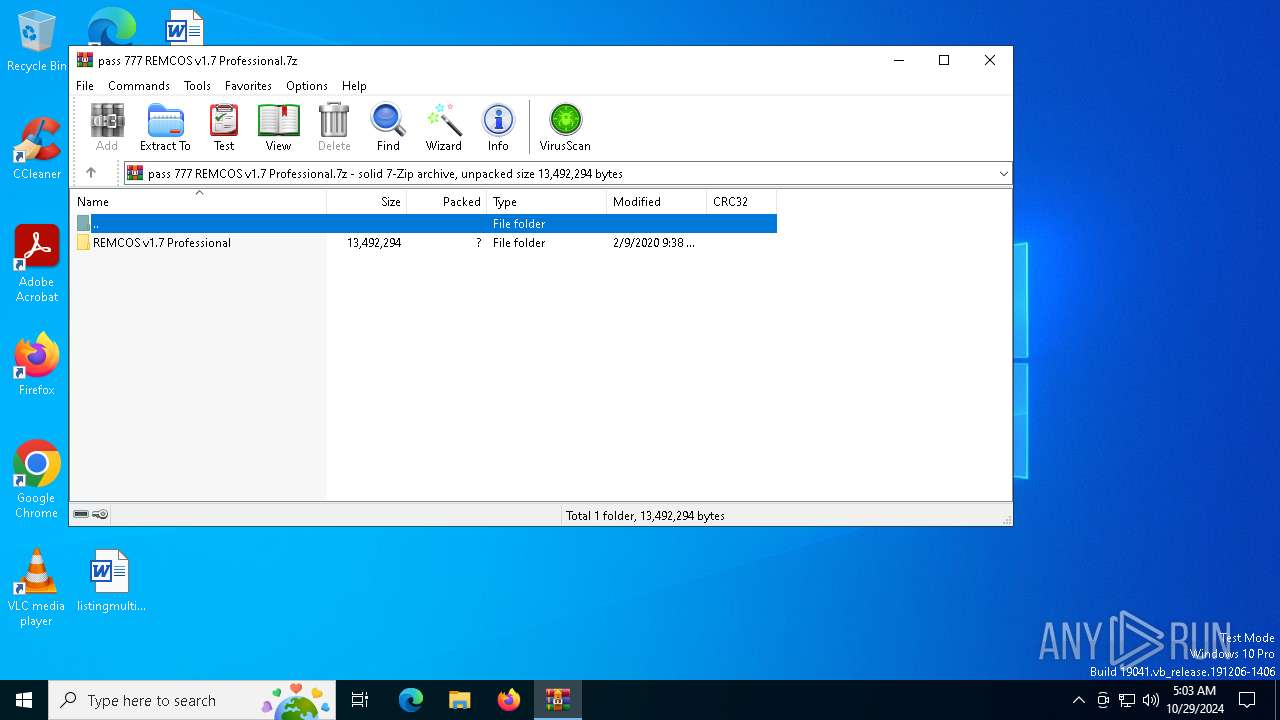
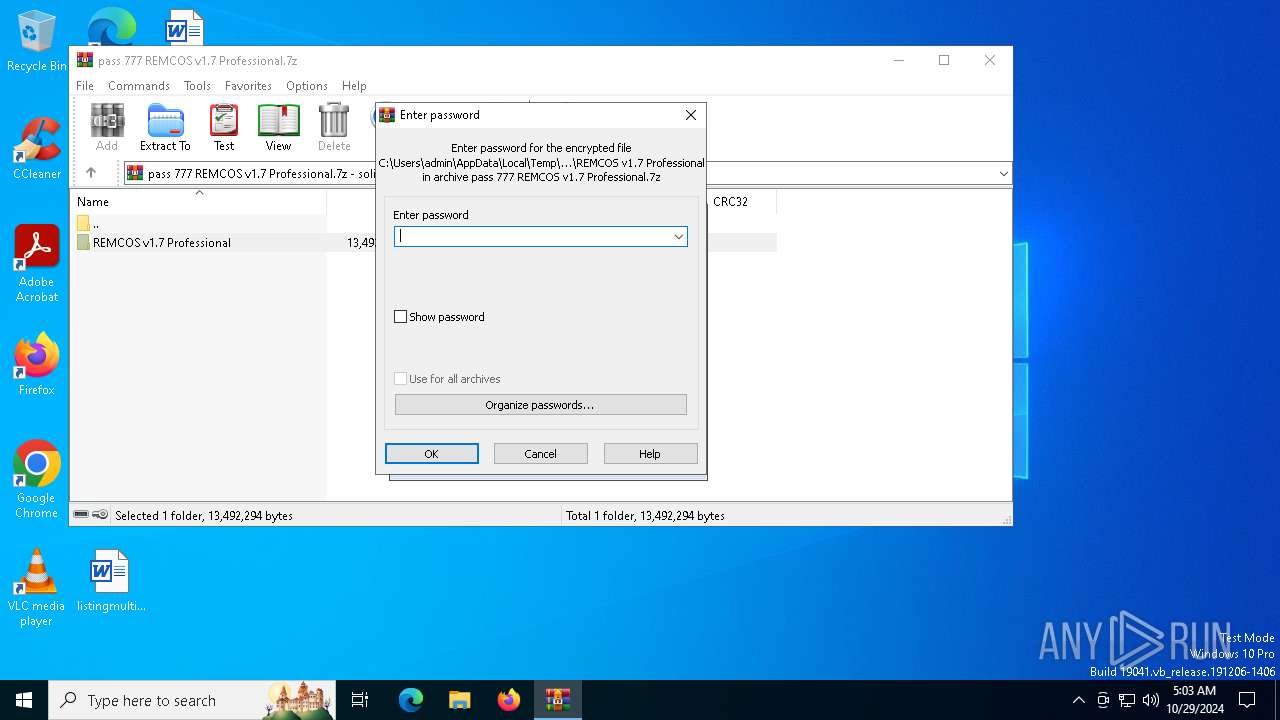
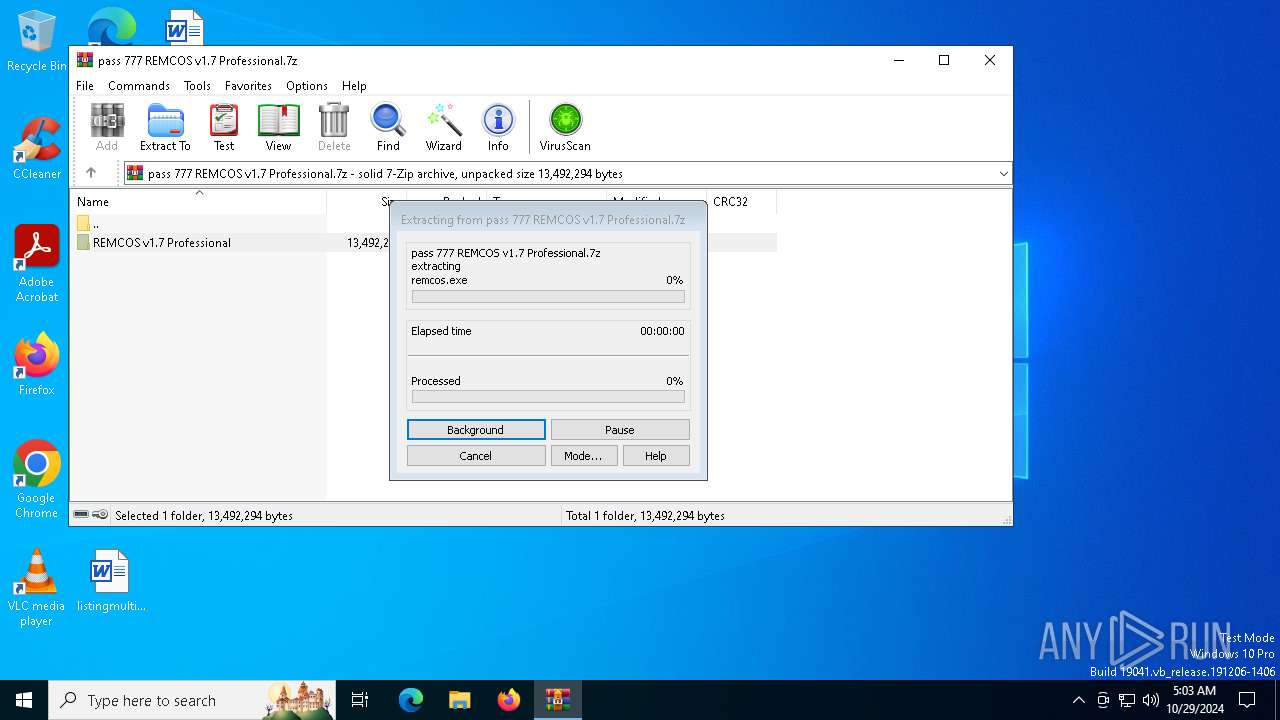
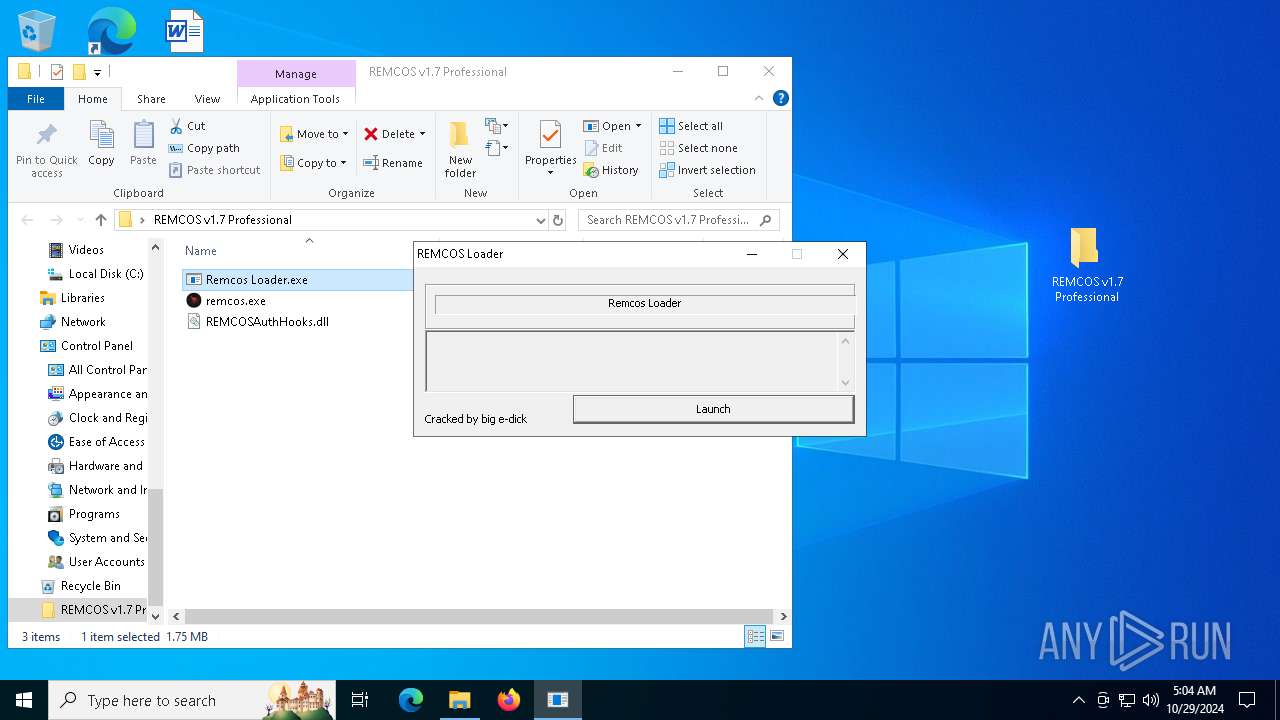
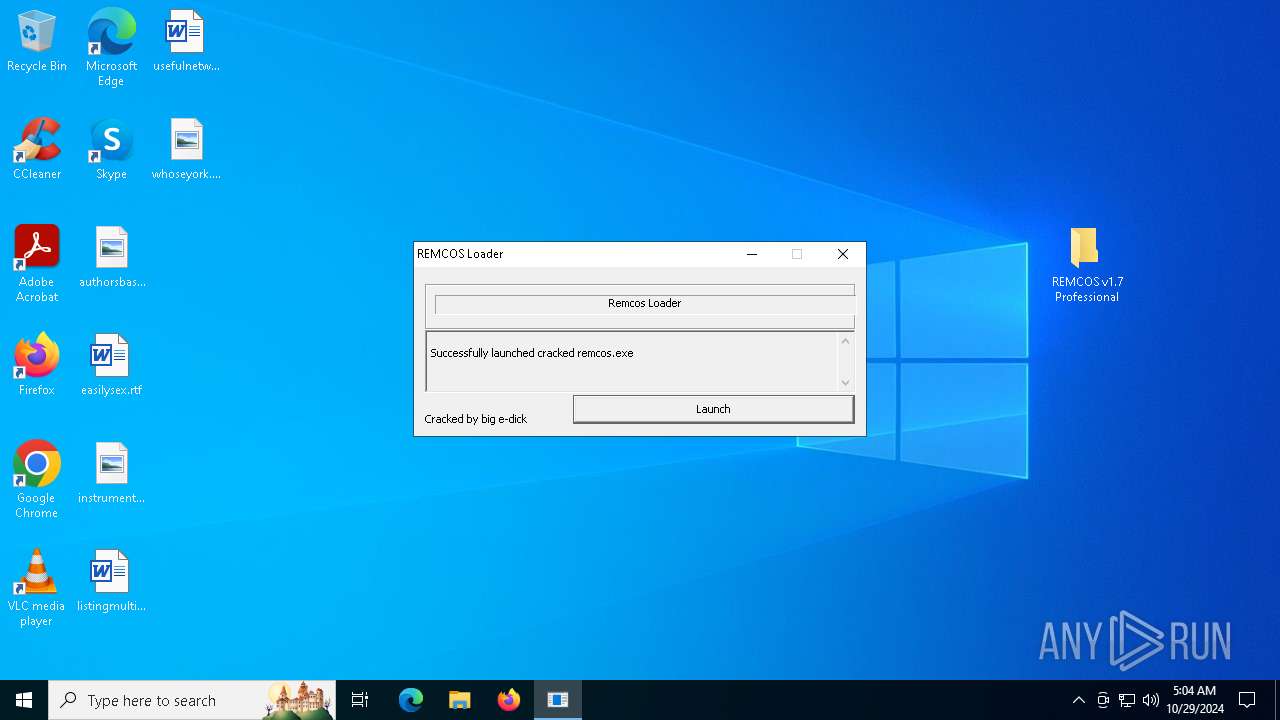
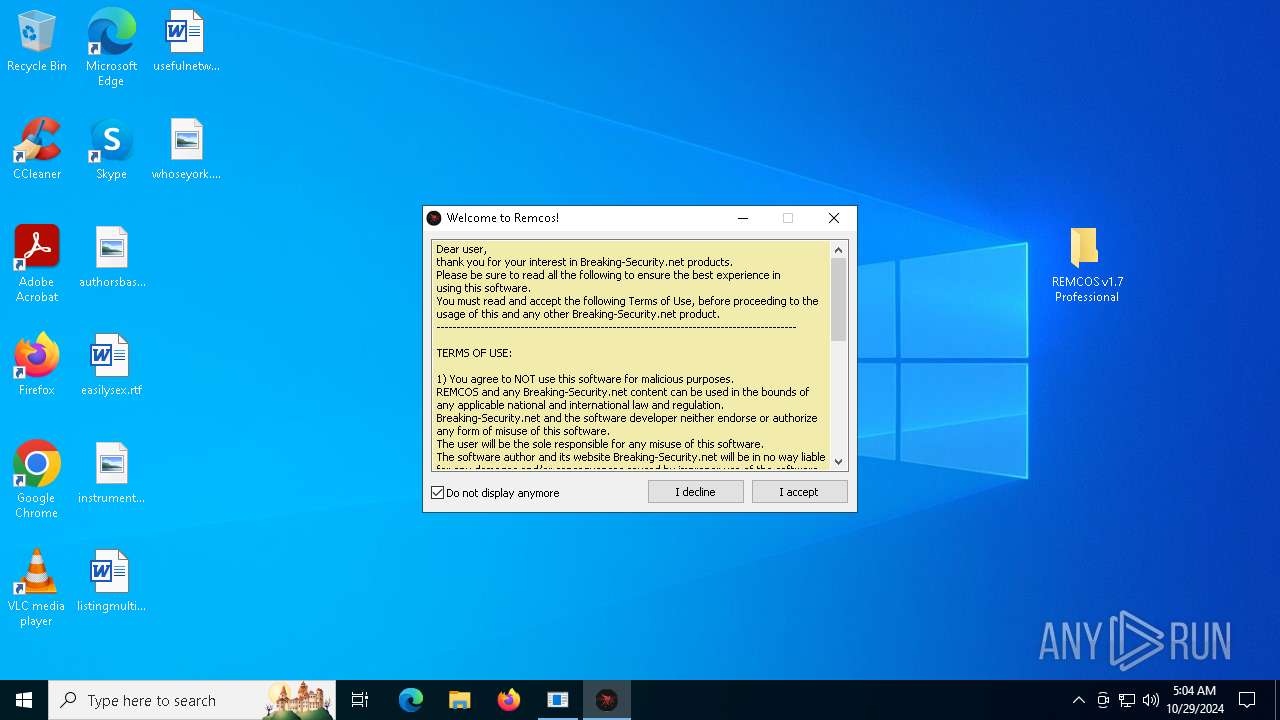
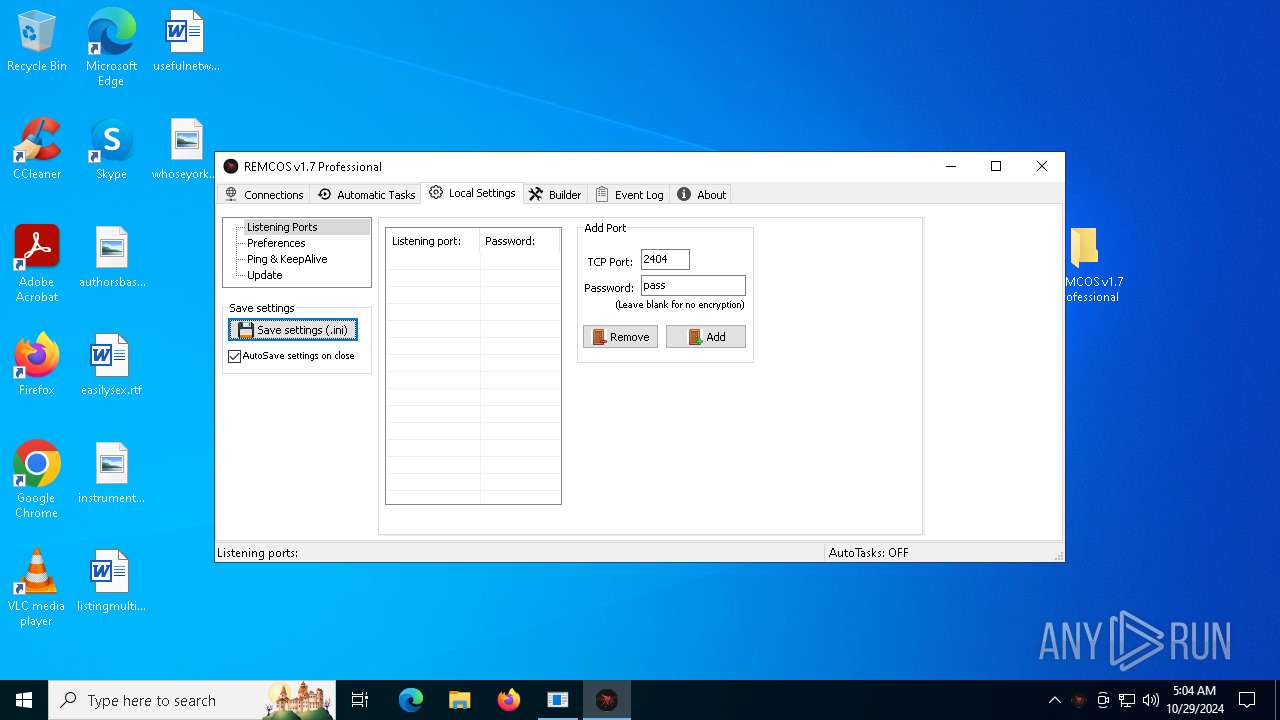
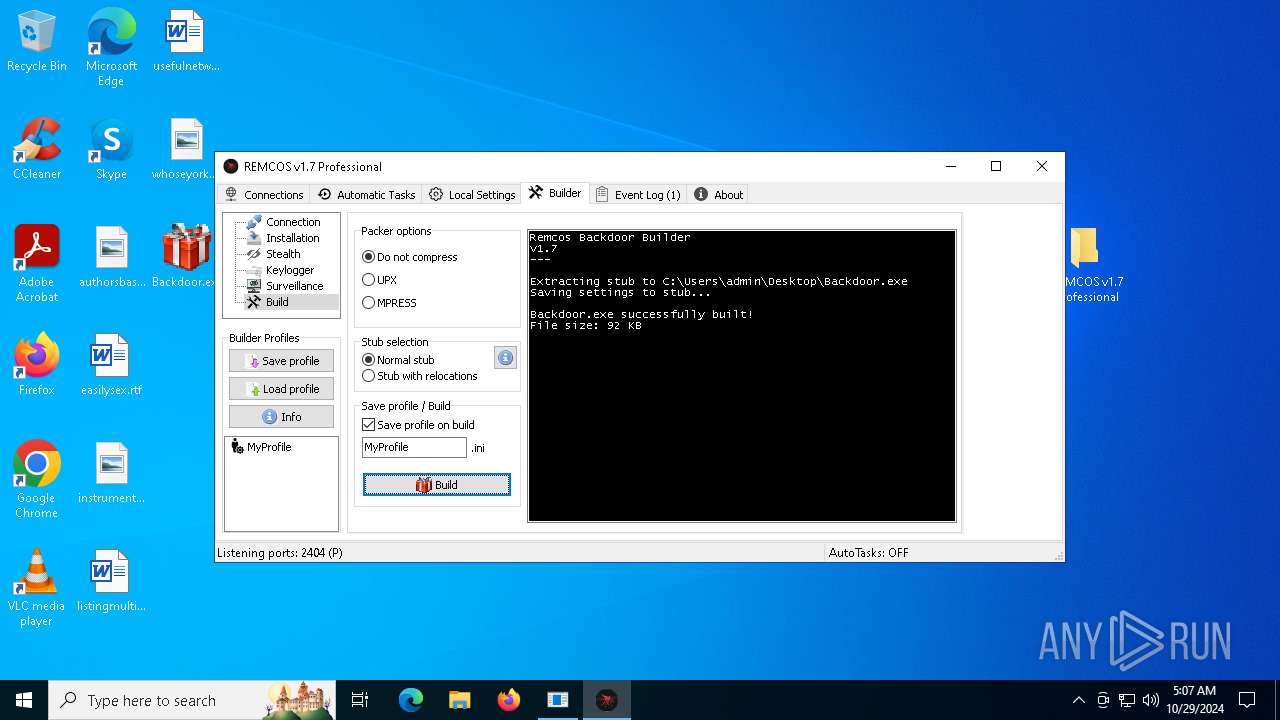
| File name: | pass 777 REMCOS v1.7 Professional.7z |
| Full analysis: | https://app.any.run/tasks/f4ebac30-e49f-4164-9915-b72ae05de426 |
| Verdict: | Malicious activity |
| Threats: | Remcos is a commercially distributed remote administration and surveillance tool that has been widely observed in unauthorized deployments, where threat actors use it to perform remote actions on compromised machines. It is actively maintained by its vendor, with new versions and feature updates released on a frequent, near-monthly basis. |
| Analysis date: | October 29, 2024, 05:03:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 693B32731934F4F42946E5E1BE1EFD0F |
| SHA1: | 44E5A39F928E8119DEBB3763FBAA9200862E961E |
| SHA256: | 5816FFAD0307E947580E8B61BC3B7A3FEEDD945F00B7CCFAE56BA8564832C57A |
| SSDEEP: | 196608:L9tYskxWGqOHlFLE8Ef+fBFIT7As2qgrQiWyLWaVwOUZzDFfCnwUapgqnwrk0:ptYs0WGqO/Q8dfBFSkzTUiWyxmZv1gaY |
MALICIOUS
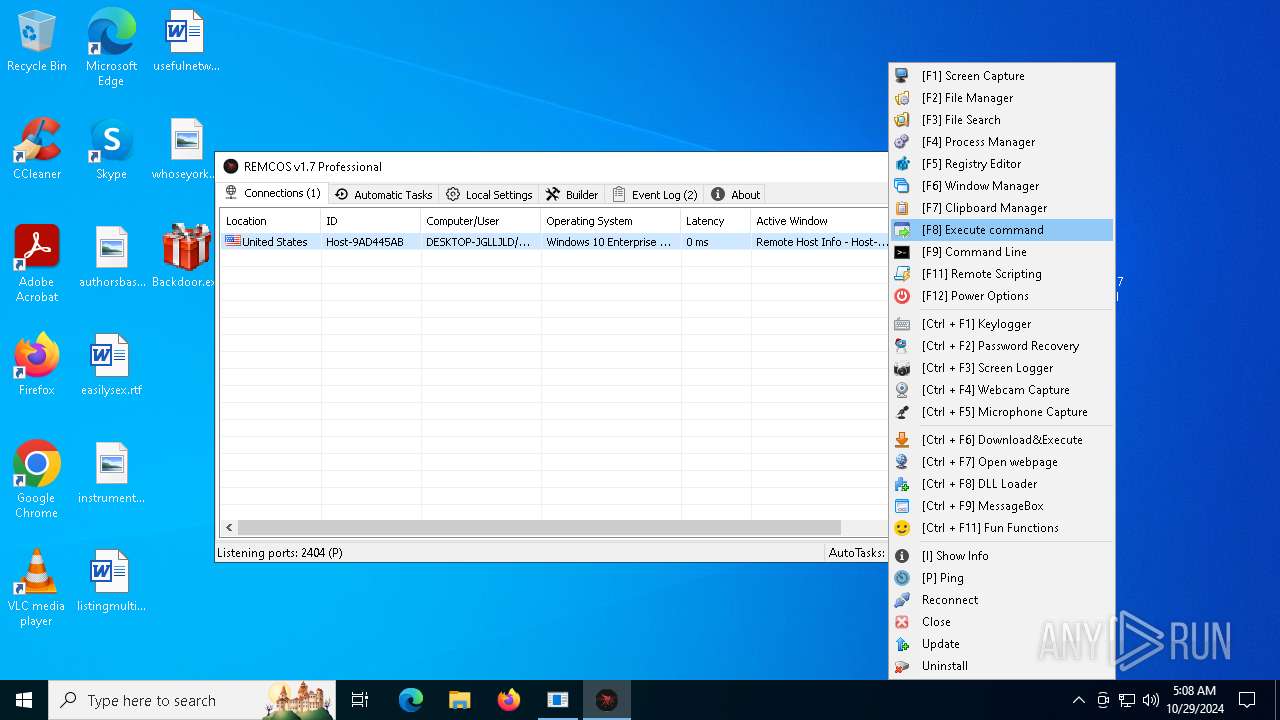
Runs injected code in another process
- remcos.exe (PID: 4144)
Application was injected by another process
- explorer.exe (PID: 4616)
REMCOS has been detected (YARA)
- remcos.exe (PID: 4144)
- Reg.exe (PID: 5596)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 6680)
Reads security settings of Internet Explorer
- remcos.exe (PID: 4144)
Executable content was dropped or overwritten
- remcos.exe (PID: 4144)
- Backdoor.exe (PID: 2196)
Executing commands from a ".bat" file
- Backdoor.exe (PID: 2196)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2708)
Starts CMD.EXE for commands execution
- Backdoor.exe (PID: 2196)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6680)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4616)
The process uses the downloaded file
- WinRAR.exe (PID: 6680)
- explorer.exe (PID: 4616)
Manual execution by a user
- Remcos Loader.exe (PID: 6208)
- Backdoor.exe (PID: 6900)
- Backdoor.exe (PID: 2196)
Checks supported languages
- Remcos Loader.exe (PID: 6208)
- remcos.exe (PID: 4144)
Reads the computer name
- Remcos Loader.exe (PID: 6208)
- remcos.exe (PID: 4144)
VMProtect protector has been detected
- Remcos Loader.exe (PID: 6208)
Checks proxy server information
- remcos.exe (PID: 4144)
FSG packer has been detected
- remcos.exe (PID: 4144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
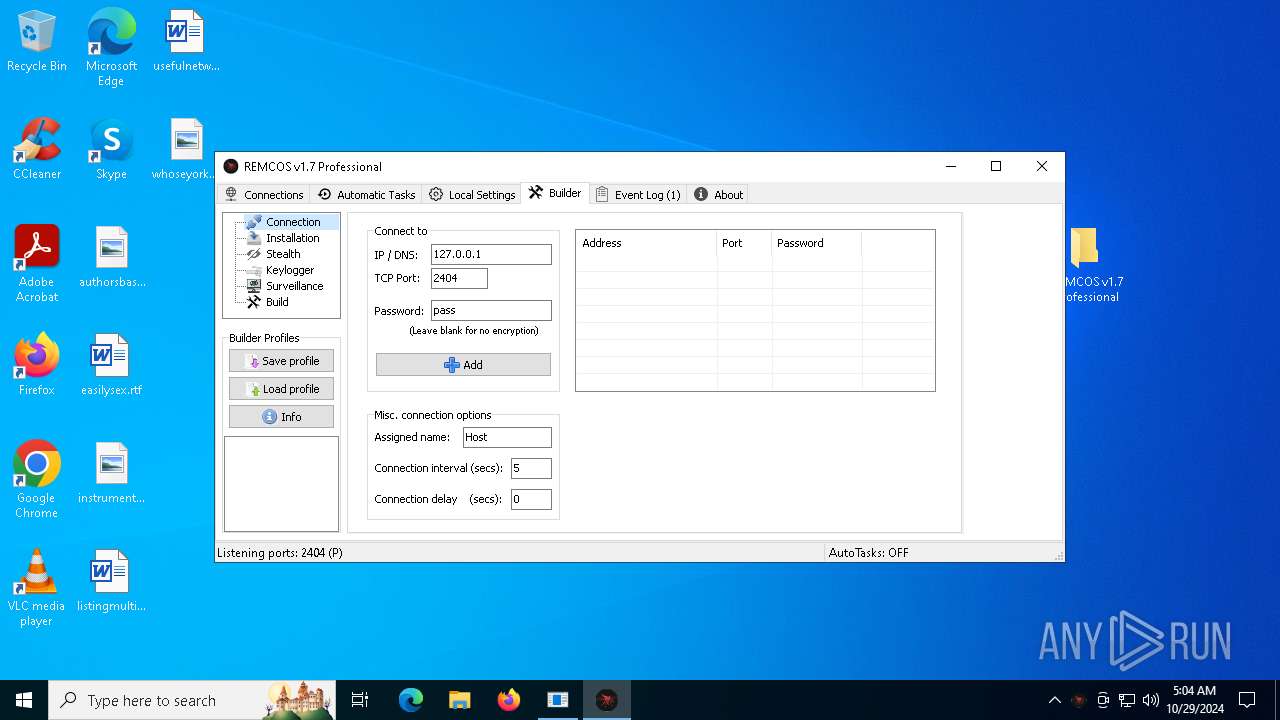
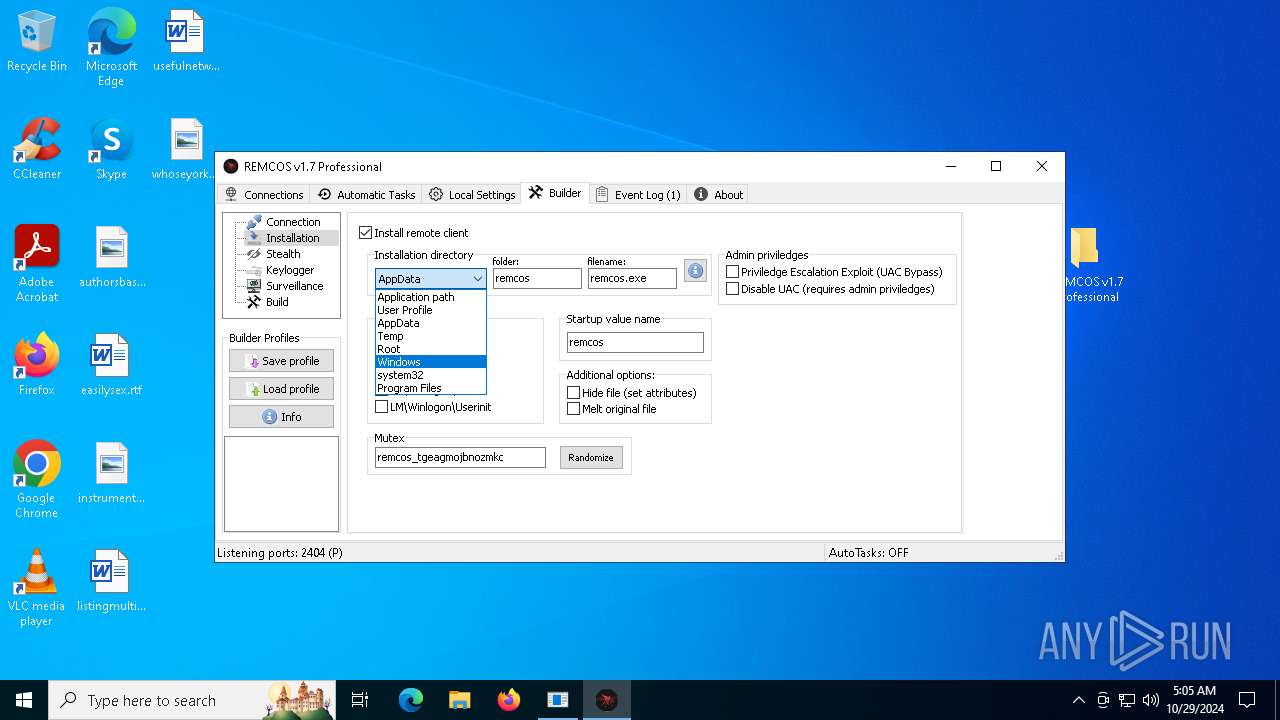
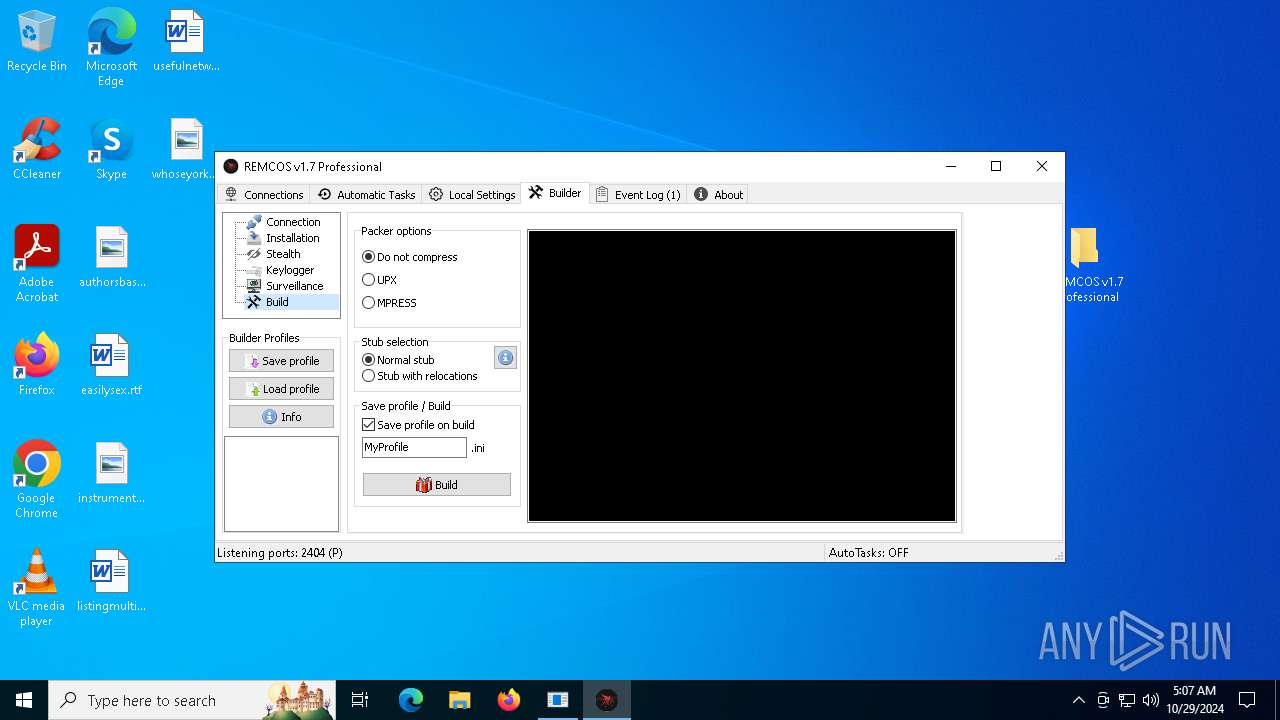
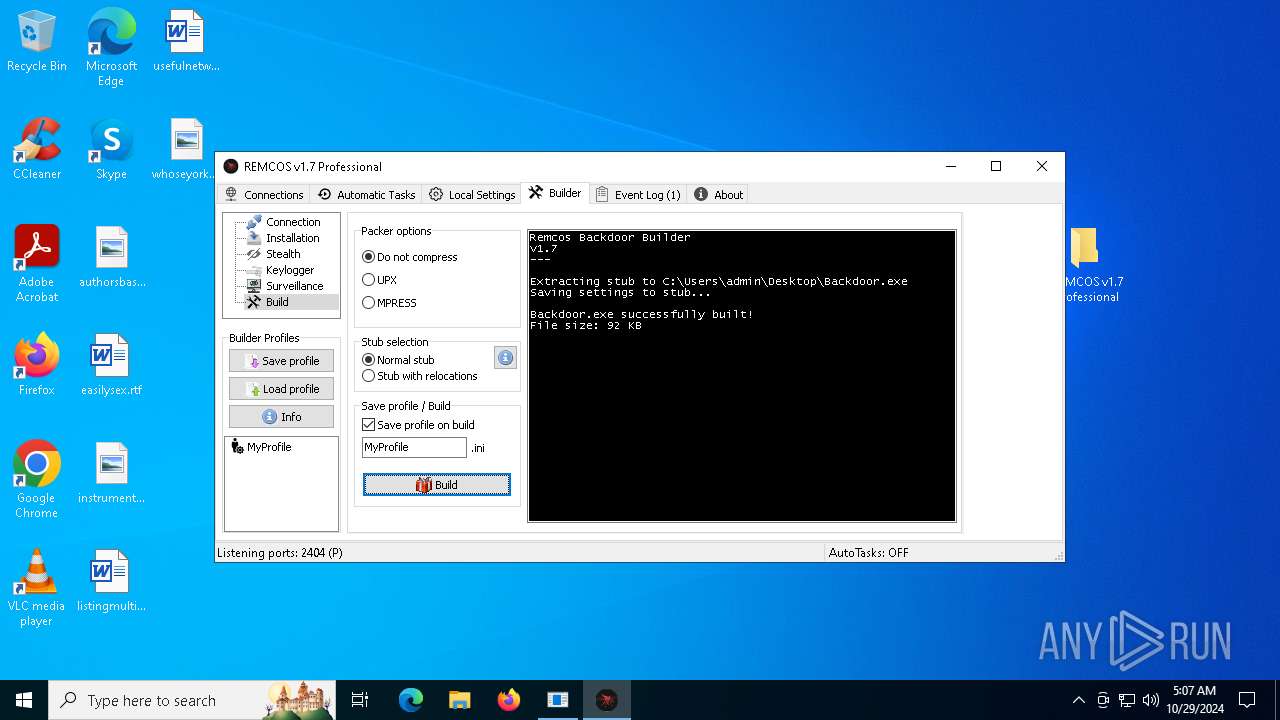
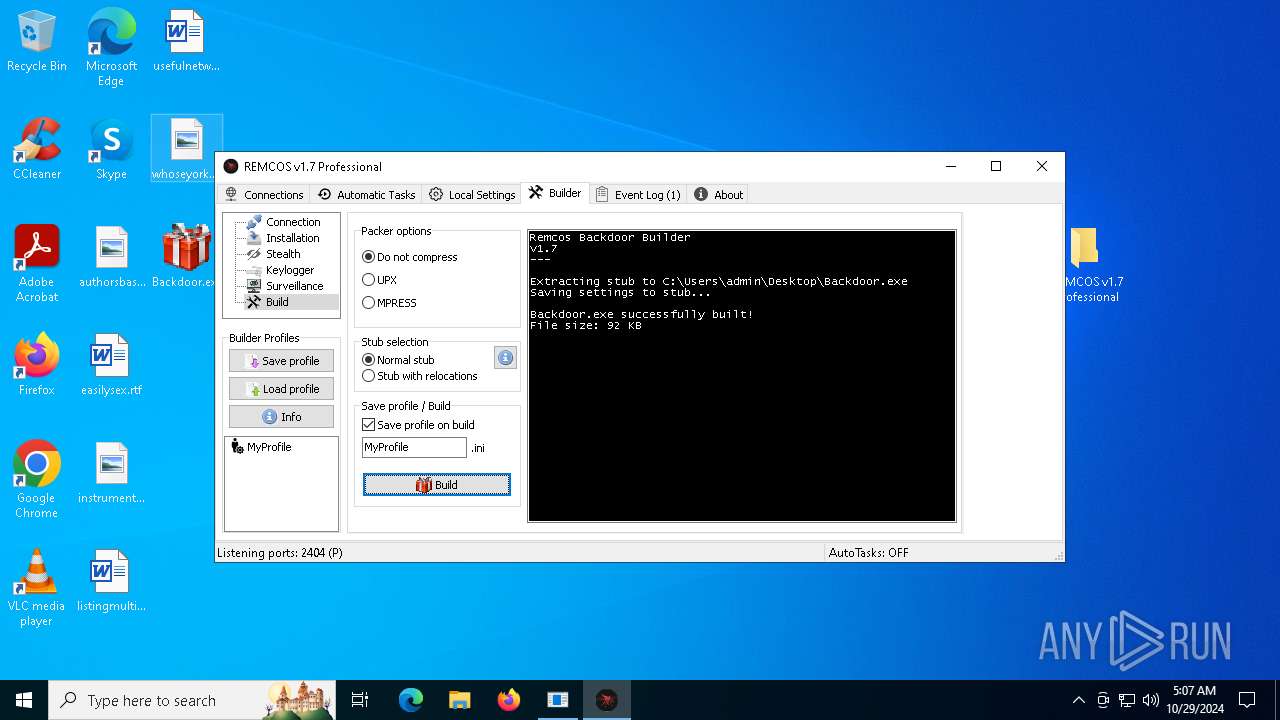
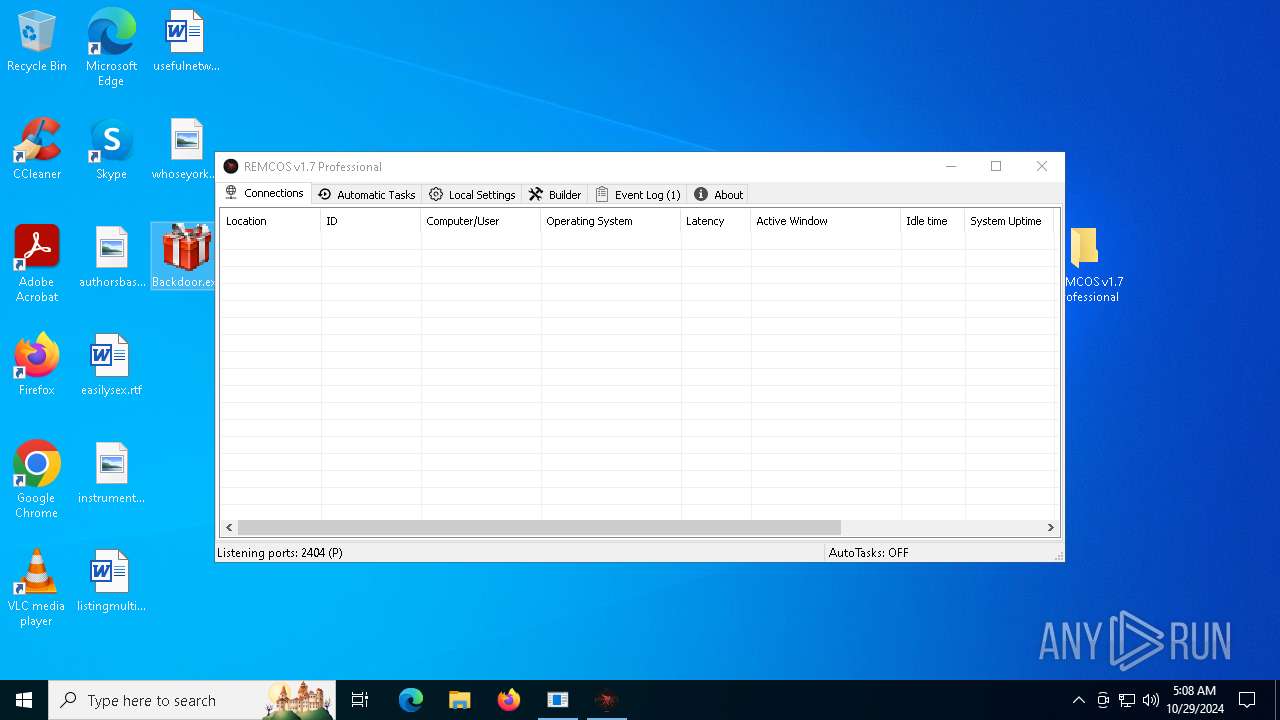
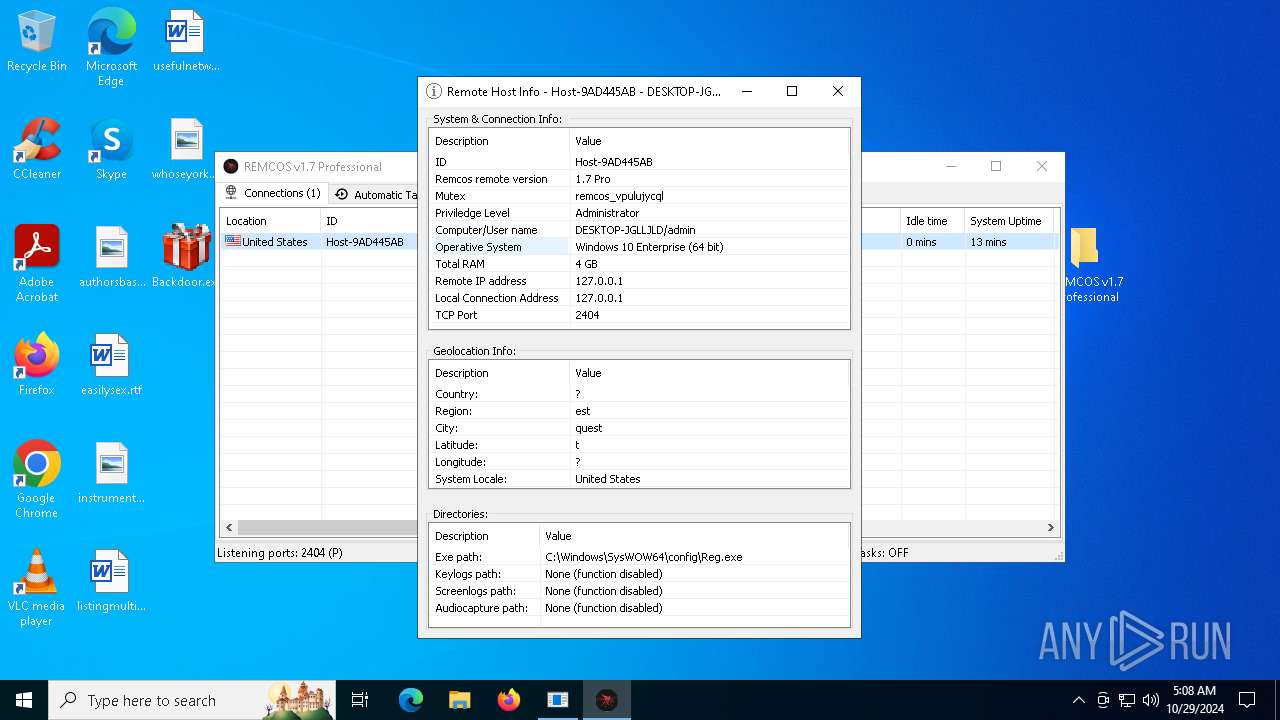
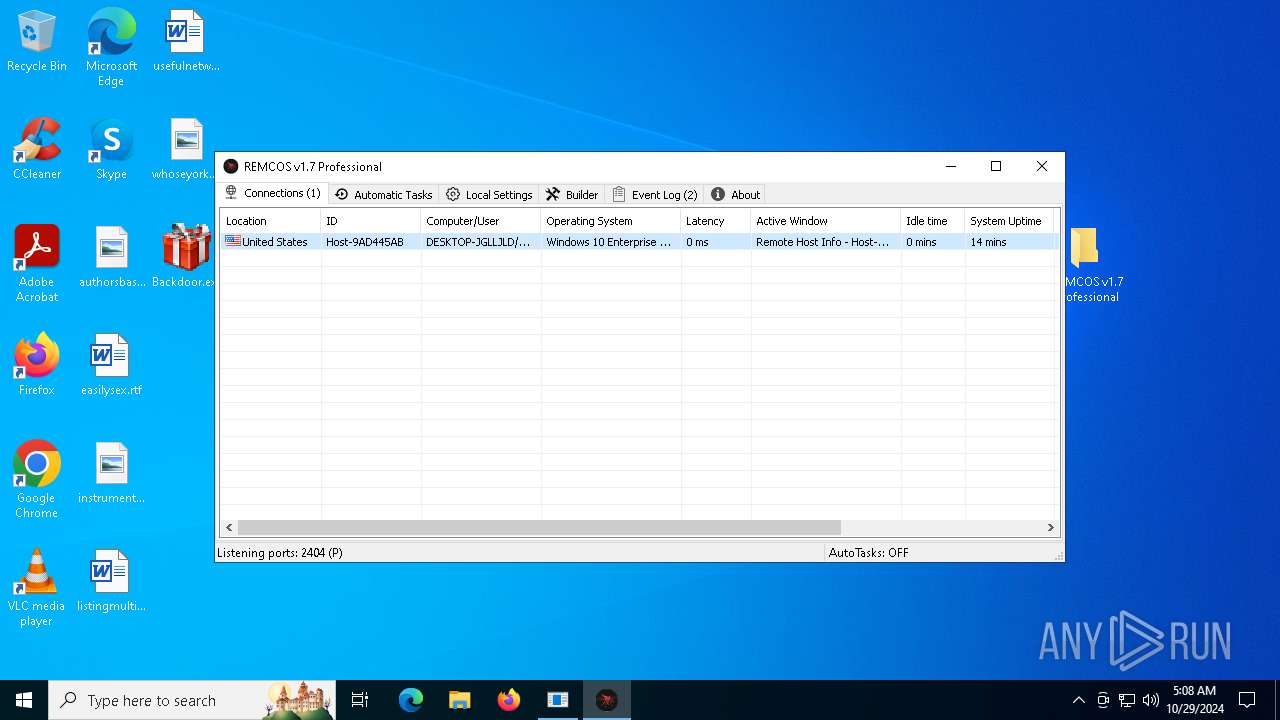
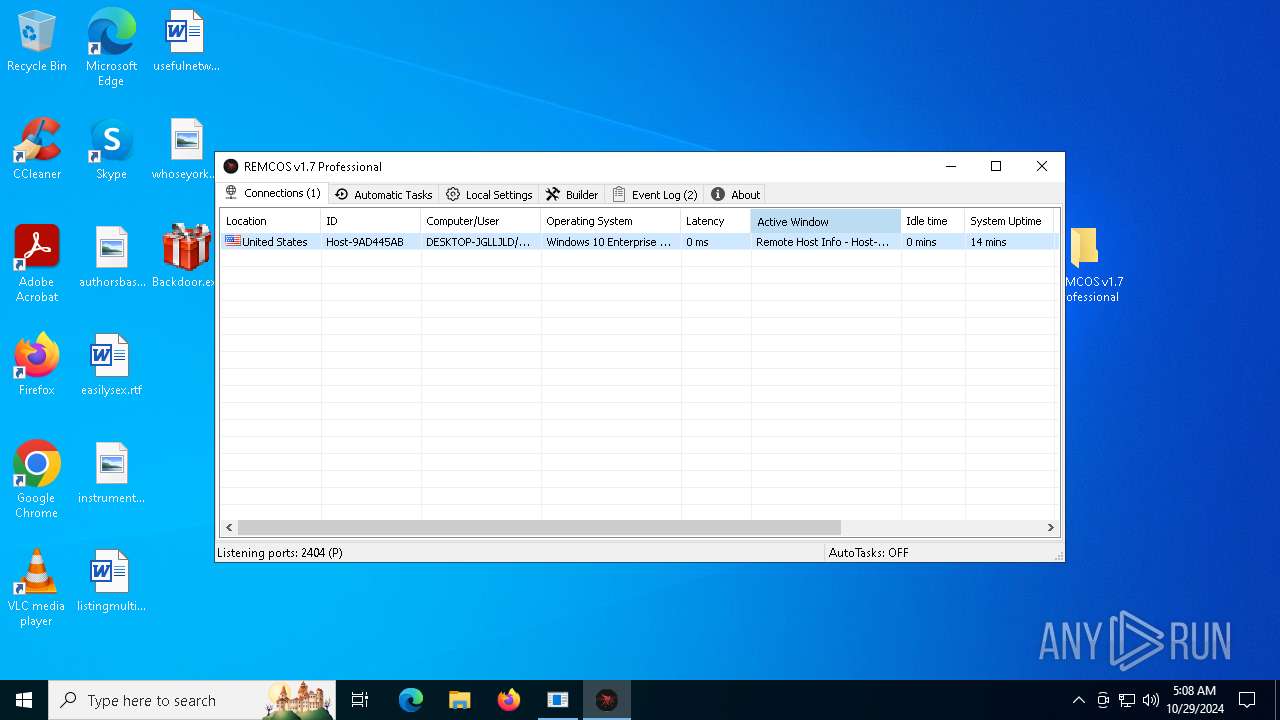
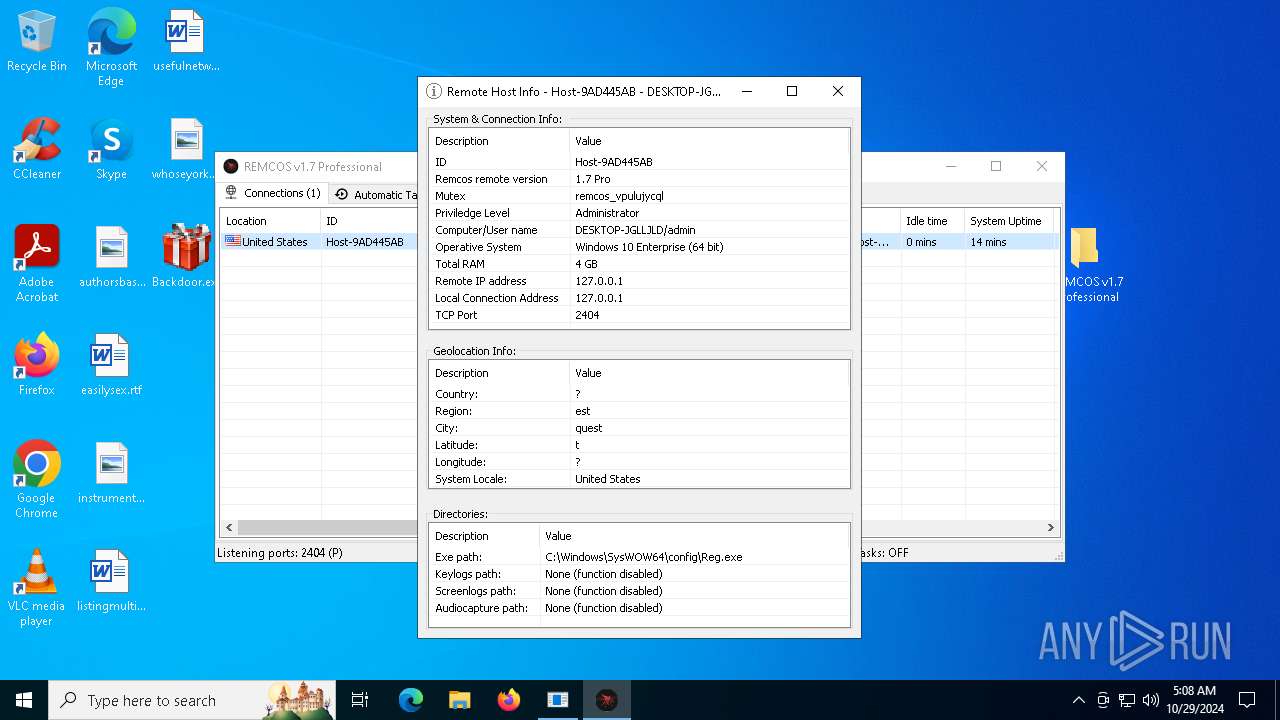
Remcos
(PID) Process(5596) Reg.exe
C2 (1)127.0.0.1:2404
BotnetHost
Options
Connect_interval5
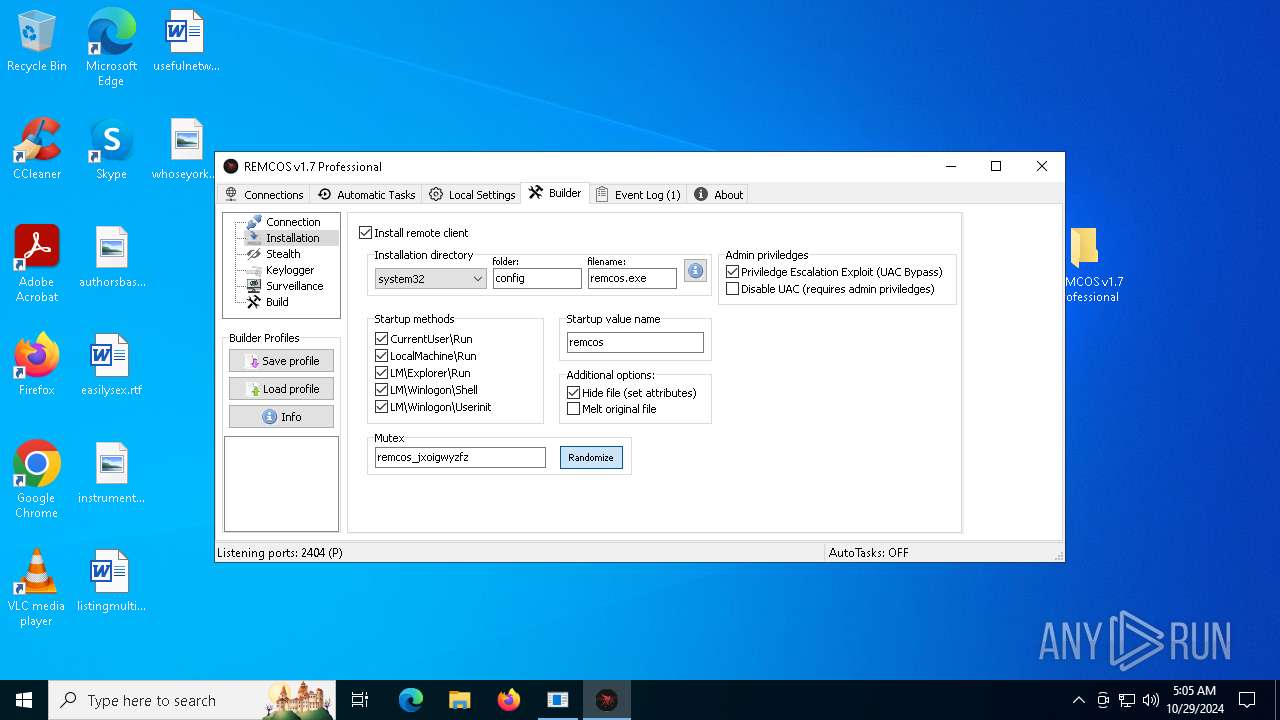
Install_flagTrue
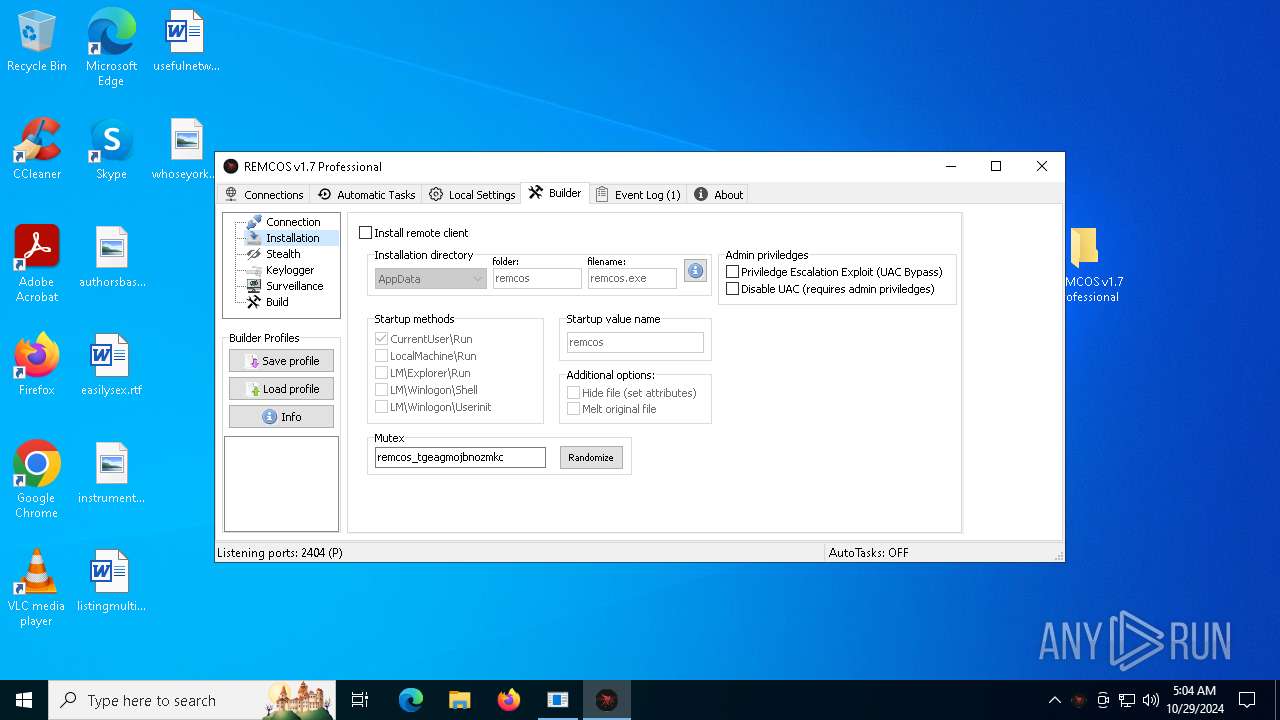
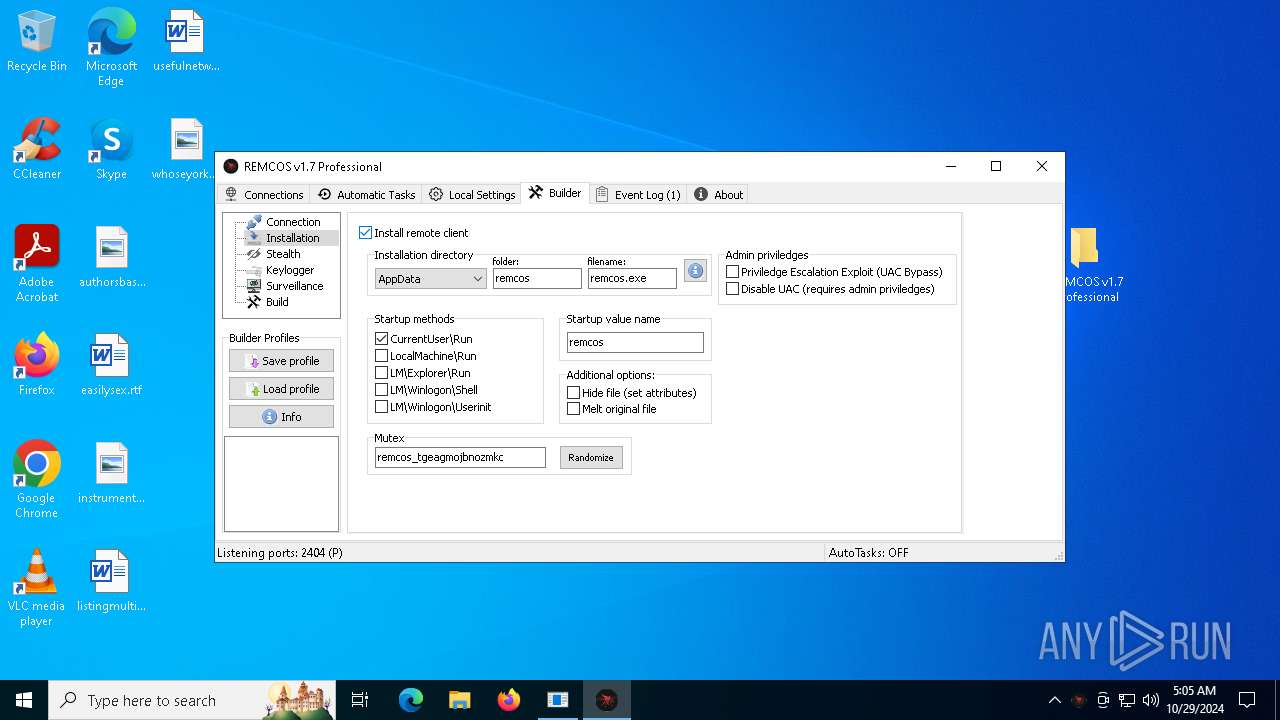
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\RunTrue
Install_HKLM\Winlogon\ShellTrue
Install_HKLM\Winlogon\UserinitTrue
Setup_pathSystem32
Copy_fileReg.exe
Startup_valueremcos
Hide_fileTrue
Mutex_nameremcos_vpulujycql
Keylog_flag0
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
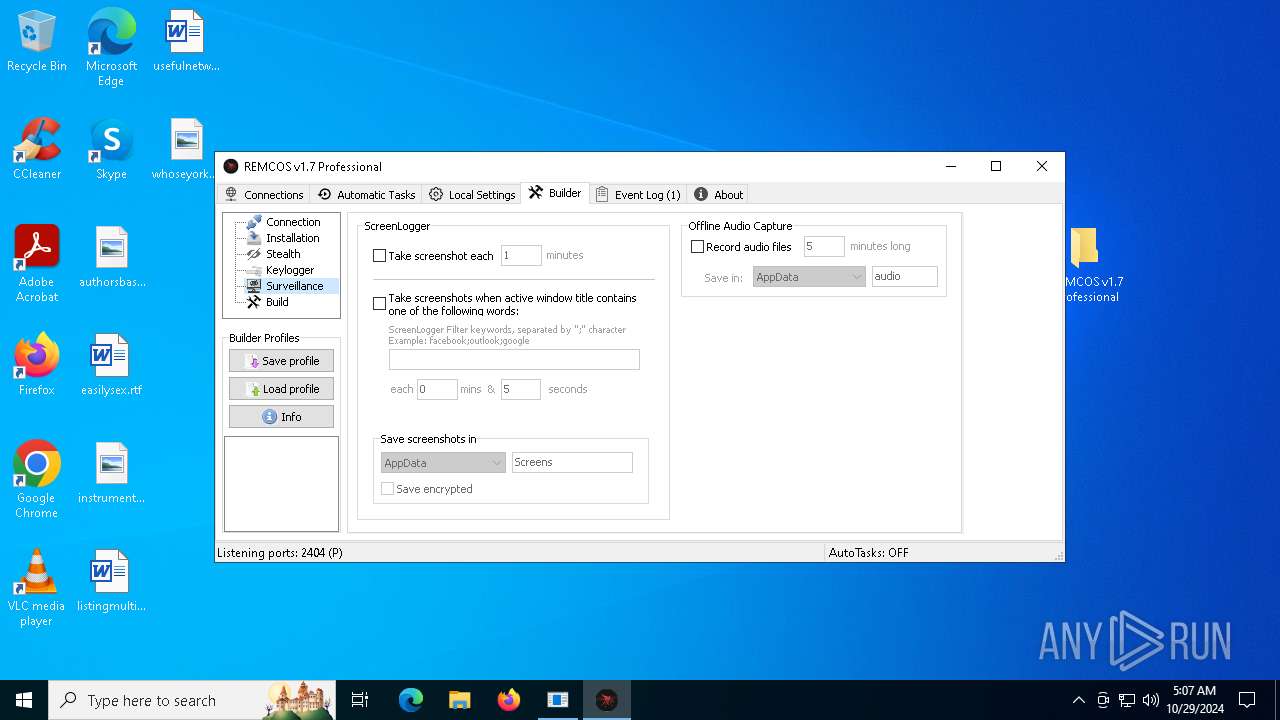
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreens
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_diraudio
Connect_delay0
Copy_dirconfig
Keylog_dirremcos
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2020:02:09 09:38:02+00:00 |
| ArchivedFileName: | REMCOS v1.7 Professional |
Total processes
142
Monitored processes
16
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1156 | "C:\Windows\SysWOW64\eventvwr.exe" | C:\Windows\SysWOW64\eventvwr.exe | Backdoor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Event Viewer Snapin Launcher Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1588 | PING 127.0.0.1 -n 2 | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2140 | "C:\Windows\SysWOW64\eventvwr.exe" | C:\Windows\SysWOW64\eventvwr.exe | — | Backdoor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Event Viewer Snapin Launcher Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2196 | "C:\Users\admin\Desktop\Backdoor.exe" | C:\Users\admin\Desktop\Backdoor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 2708 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\install.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Backdoor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 3648 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4144 | "C:\Users\admin\Desktop\REMCOS v1.7 Professional\remcos.exe" | C:\Users\admin\Desktop\REMCOS v1.7 Professional\remcos.exe | Remcos Loader.exe | ||||||||||||
User: admin Company: Breaking-Security.net Integrity Level: MEDIUM Description: REMCOS Remote Control & Surveillance Version: 1.7.0.0 Modules
| |||||||||||||||
| 4432 | "C:\Program Files (x86)\Internet Explorer\iexplore.exe" | C:\Program Files (x86)\Internet Explorer\iexplore.exe | — | Reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Version: 11.00.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4616 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 017
Read events
9 944
Write events
69
Delete events
4
Modification events
| (PID) Process: | (4616) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000602E8 |
| Operation: | write | Name: | VirtualDesktop |
Value: 100000003030445671D90A7D3588864C9F3CEA9EBAB7B4A7 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\pass 777 REMCOS v1.7 Professional.7z | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4616) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 0000000000000000000000000000000003000100010001000F000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C000000140000000000000061007500740068006F0072007300620061007300650064002E006A00700067003E00200020000000110000000000000065006100730069006C0079007300650078002E007200740066003E00200020000000180000000000000069006E0073007400720075006D0065006E0074007300630068006500610070002E006A00700067003E0020002000000017000000000000006C0069007300740069006E0067006D0075006C007400690070006C0065002E007200740066003E002000200000001600000000000000750073006500660075006C006E006500740077006F0072006B0073002E007200740066003E002000200000001100000000000000770068006F007300650079006F0072006B002E006A00700067003E002000200000001C00000000000000520045004D0043004F0053002000760031002E0037002000500072006F00660065007300730069006F006E0061006C003E005C0020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000000F00000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D00000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000006041000000400E00 | |||
| (PID) Process: | (4616) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
Executable files
8
Suspicious files
4
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4616 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6680.4247\REMCOS v1.7 Professional\remcos.exe | executable | |
MD5:ED1E424EA6F625968A334377E8AC629F | SHA256:1E5375B400F68C422804703390489B2CF3968C2A8BCCB0B5B3C55FE1D2E3C991 | |||
| 4144 | remcos.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\gettime[1].htm | text | |
MD5:D19021C3E24FFF276CE831D27901DB2B | SHA256:A51CE6D2543445BDA96479C74113F63C5FBA8C1DF87B0628D983683CB8970F82 | |||
| 6680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6680.4247\REMCOS v1.7 Professional\desktop.ini | text | |
MD5:38D746FE40448323E9AEA314D98082E8 | SHA256:CEA6578E3D4BDD55A11FA566AC3CFB469A7E54DB1E80415E410D0C0F197E7094 | |||
| 4616 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:DB6C6A695DCAF1947ED4204EF7A57A31 | SHA256:82E2564205AF399D48E91F6C628281CE63A0E9B86529A58309A8F52D26AD0216 | |||
| 6680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6680.4247\REMCOS v1.7 Professional\REMCOSAuthHooks.dll | executable | |
MD5:A329F92AD3B9311AF3130DBDE81155CE | SHA256:D695A2EE6FCAE64F4D8C4387A0A4C4AAE05D08CE44A52598984673B890D02F27 | |||
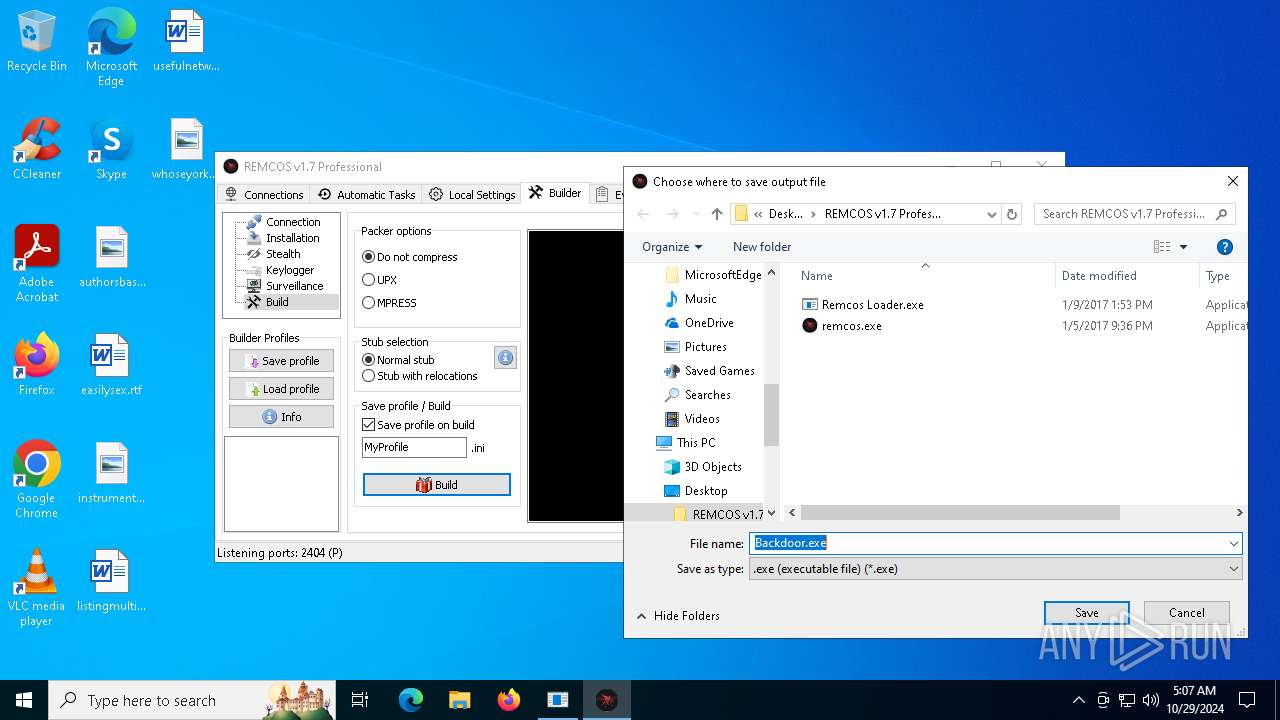
| 4144 | remcos.exe | C:\Users\admin\Desktop\Backdoor.exe | executable | |
MD5:C9E54162155068559973AEFA62A7E6C4 | SHA256:B88F895FCFF3F5939807E26A04D7E8B5FEEA2BB0E8314AE598A3B2DE0A2140C7 | |||
| 4144 | remcos.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\OnlineCheck_MT[1].htm | text | |
MD5:442D4F5216CD9DA1FD121655A23E8843 | SHA256:0A3706B1424059F3F718B8FBAA2DD145EA0FD1F8D950744CA78C7B32D2DFA4A8 | |||
| 4144 | remcos.exe | C:\Users\admin\Desktop\REMCOS v1.7 Professional\BuilderProfiles\MyProfile.ini | text | |
MD5:E2D57396C13D597855EB6FEA1122667A | SHA256:6422F98D8A559EC4F886892A806B427AF84B8814A114CDE4BBEC14B6B0B9AC50 | |||
| 6428 | mmc.exe | C:\Users\admin\AppData\Local\Microsoft\Event Viewer\RecentViews | binary | |
MD5:785FB8E1B562E2FCC8C0C0C6572EE3D7 | SHA256:5607B57C3C58070F54B8F68FA22808F9AD14C60BBF05F00DA92A162585C3C562 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
44
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6268 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 178.237.33.50:80 | http://www.geoplugin.net/json.gp?ip=127.0.0.1 | unknown | — | — | whitelisted |
6244 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.25:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 104.126.37.185:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6384 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6384 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report