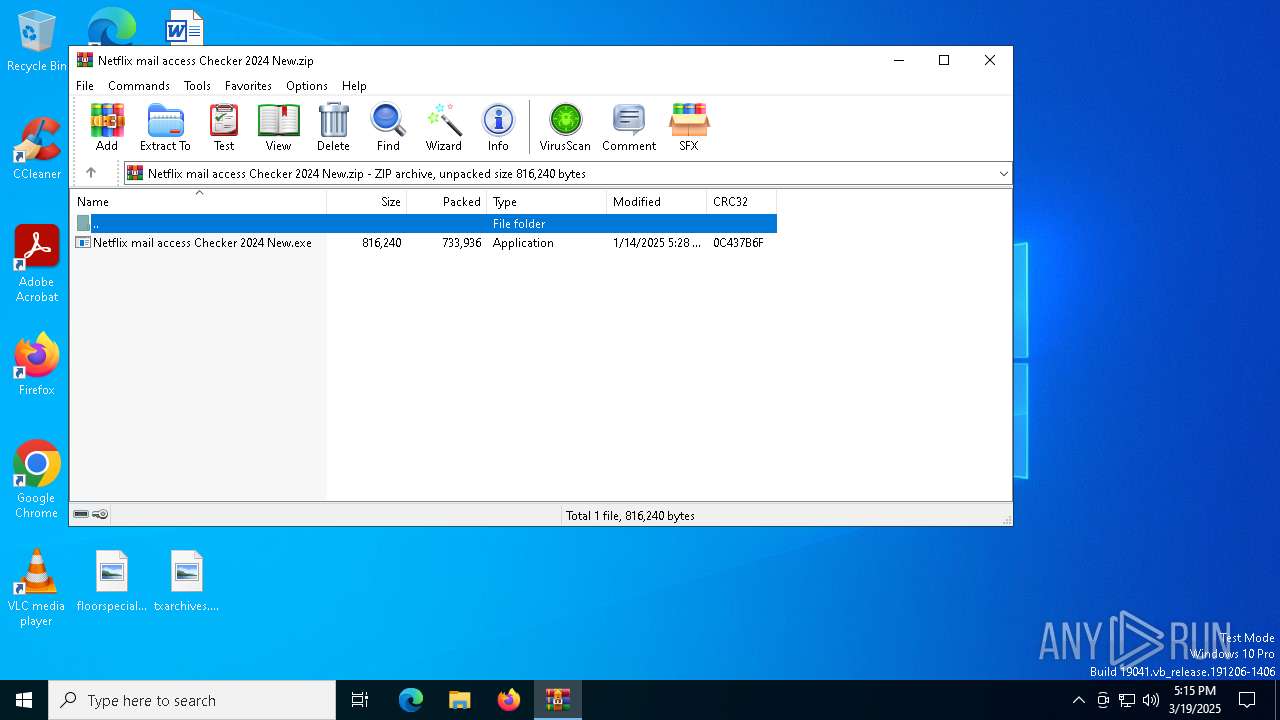
| File name: | Netflix mail access Checker 2024 New.zip |
| Full analysis: | https://app.any.run/tasks/030bf1bd-c9b4-4ba1-81f9-aab8ddae1492 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | March 19, 2025, 17:15:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 764E336C47C9DB6F022C20CFADE97F84 |
| SHA1: | 71CEB70C24263CE9581923DAE76C0C5DA93CC20A |
| SHA256: | 580E0AB776B1CD67982604B2299CBD300ACD81AA1FD71CD66014B20B473E491B |
| SSDEEP: | 24576:/AX6H2/3AmpiZysPm6fXKFVibiPOvTbCSCxgfeM+GhczRXvb5ue+Jv9hzgZFEu/Z:/AX6H2/3AmpYysPm6fXKFVibiGvnCJx/ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6404)
Executing a file with an untrusted certificate
- LpJMbyRVvX.exe (PID: 5324)
- Netflix mail access Checker 2024 New.exe (PID: 8084)
- Netflix mail access Checker 2024 New.exe (PID: 8044)
- LpJMbyRVvX.exe (PID: 1164)
- LpJMbyRVvX.exe (PID: 6668)
Create files in the Startup directory
- ymuCj4bXYI.exe (PID: 6048)
Connects to the CnC server
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
LUMMA mutex has been found
- ymuCj4bXYI.exe (PID: 6048)
SUSPICIOUS
Executes application which crashes
- Netflix mail access Checker 2024 New.exe (PID: 8044)
- LpJMbyRVvX.exe (PID: 6668)
Reads security settings of Internet Explorer
- Netflix mail access Checker 2024 New.exe (PID: 8084)
Application launched itself
- Netflix mail access Checker 2024 New.exe (PID: 8044)
- LpJMbyRVvX.exe (PID: 6668)
Executable content was dropped or overwritten
- Netflix mail access Checker 2024 New.exe (PID: 8084)
- ymuCj4bXYI.exe (PID: 6048)
The process creates files with name similar to system file names
- ymuCj4bXYI.exe (PID: 6048)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
INFO
Reads the computer name
- Netflix mail access Checker 2024 New.exe (PID: 8044)
- LpJMbyRVvX.exe (PID: 1164)
- LpJMbyRVvX.exe (PID: 6668)
Manual execution by a user
- Netflix mail access Checker 2024 New.exe (PID: 8044)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6404)
Checks supported languages
- Netflix mail access Checker 2024 New.exe (PID: 8044)
- LpJMbyRVvX.exe (PID: 1164)
- LpJMbyRVvX.exe (PID: 6668)
- Netflix mail access Checker 2024 New.exe (PID: 8084)
Creates files or folders in the user directory
- ymuCj4bXYI.exe (PID: 6048)
- WerFault.exe (PID: 7244)
- WerFault.exe (PID: 6800)
Autorun file from Startup directory
- ymuCj4bXYI.exe (PID: 6048)
Reads the software policy settings
- LpJMbyRVvX.exe (PID: 1164)
Process checks computer location settings
- Netflix mail access Checker 2024 New.exe (PID: 8084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:14 19:28:56 |
| ZipCRC: | 0x0c437b6f |
| ZipCompressedSize: | 733936 |
| ZipUncompressedSize: | 816240 |
| ZipFileName: | Netflix mail access Checker 2024 New.exe |
Total processes
150
Monitored processes
12
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Users\admin\AppData\Roaming\LpJMbyRVvX.exe" | C:\Users\admin\AppData\Roaming\LpJMbyRVvX.exe | LpJMbyRVvX.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Handler Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5324 | "C:\Users\admin\AppData\Roaming\LpJMbyRVvX.exe" | C:\Users\admin\AppData\Roaming\LpJMbyRVvX.exe | — | LpJMbyRVvX.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Handler Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6048 | "C:\Users\admin\AppData\Roaming\ymuCj4bXYI.exe" | C:\Users\admin\AppData\Roaming\ymuCj4bXYI.exe | Netflix mail access Checker 2024 New.exe | ||||||||||||
User: admin Company: Microsoft Windows Integrity Level: MEDIUM Description: system32 Version: 15.6.13.6 Modules
| |||||||||||||||
| 6404 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Netflix mail access Checker 2024 New.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6668 | "C:\Users\admin\AppData\Roaming\LpJMbyRVvX.exe" | C:\Users\admin\AppData\Roaming\LpJMbyRVvX.exe | Netflix mail access Checker 2024 New.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Handler Exit code: 3221226505 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6800 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6668 -s 848 | C:\Windows\SysWOW64\WerFault.exe | — | LpJMbyRVvX.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7244 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 8044 -s 848 | C:\Windows\SysWOW64\WerFault.exe | — | Netflix mail access Checker 2024 New.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7272 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7304 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 812
Read events
5 794
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Netflix mail access Checker 2024 New.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
4
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7244 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_Netflix mail acc_59d26759e99f1ae51e3da2fc55d262cea2c0fe2_fa85bfd4_cdec4eed-8a96-4c34-be23-b4b3670489a9\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_LpJMbyRVvX.exe_e2e388eac52479c8c56ac4f7a477d3eb85deb31_01d5c145_60e72846-bf55-4b38-aa5a-c5e3a321b3cd\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7244 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Netflix mail access Checker 2024 New.exe.8044.dmp | — | |
MD5:— | SHA256:— | |||
| 6800 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\LpJMbyRVvX.exe.6668.dmp | — | |
MD5:— | SHA256:— | |||
| 6048 | ymuCj4bXYI.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svhost.exe | executable | |
MD5:5AFB8CE4DD3923219BD69BD7B5168D91 | SHA256:F727BBA8D917FA3F129D71745E0741A8511F940B1A6817FF5130AA2F3AE85C79 | |||
| 7244 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE2A1.tmp.dmp | binary | |
MD5:2BE7899267AF114605103D07991DDD12 | SHA256:CB1CEF60C2A8A6C56A542585850DDD3DDC0762B00944E674D7C57B0C42586163 | |||
| 6800 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE35D.tmp.dmp | binary | |
MD5:88B4B6E8567EEA5E5E49E0F9BD343766 | SHA256:2104F8E8A41339DF6C2F33D045E91849A8BC2FEDA1ACCECAD4BAFC5D49EEA19B | |||
| 6404 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6404.33770\Netflix mail access Checker 2024 New.exe | executable | |
MD5:5DCAD19D36E676074DDE4A916BB8971B | SHA256:80FB3DE057CB6FE6982362B59AB22AAAB2F5DEDA3DBA1F4281106FA2CFC76F41 | |||
| 8084 | Netflix mail access Checker 2024 New.exe | C:\Users\admin\AppData\Roaming\ymuCj4bXYI.exe | executable | |
MD5:5AFB8CE4DD3923219BD69BD7B5168D91 | SHA256:F727BBA8D917FA3F129D71745E0741A8511F940B1A6817FF5130AA2F3AE85C79 | |||
| 7244 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE37D.tmp.WERInternalMetadata.xml | xml | |
MD5:BAC67E77BB0229387BCCD78CE7410B1F | SHA256:DA0A0A29F4A5DCE79D946AF0E044CFA7F6C9768BDC512A623A0F34640D7B2B92 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
25
DNS requests
22
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7356 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6476 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6476 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6476 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
stripedre-lot.bond |
| malicious |
strivehelpeu.bond |
| malicious |
crookedfoshe.bond |
| malicious |
immolatechallen.bond |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (crookedfoshe .bond) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (stripedre-lot .bond) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (jarry-deatile .bond) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (jarry-fixxer .bond) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (pain-temper .bond) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (strivehelpeu .bond) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (immolatechallen .bond) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (growthselec .bond) |