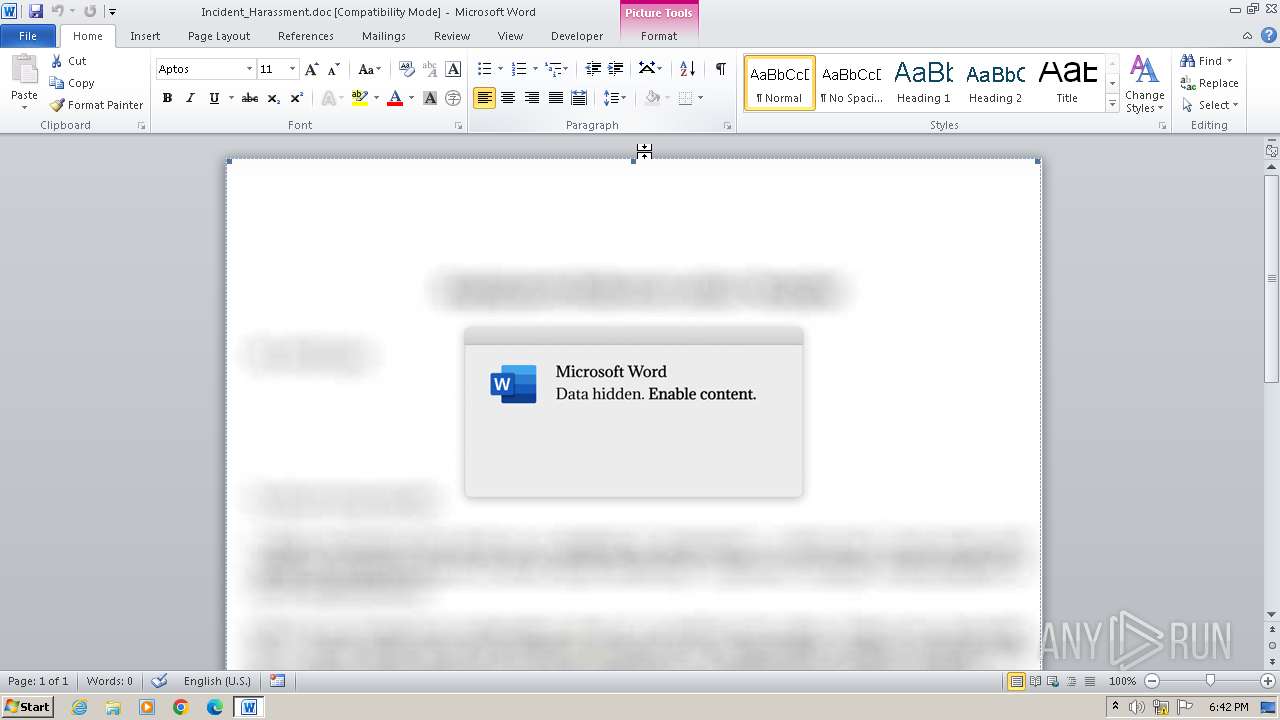
| File name: | Incident_Harassment.doc |
| Full analysis: | https://app.any.run/tasks/f0d3bd69-1a93-4356-a1dd-ee17a2b300c6 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | May 08, 2024, 17:42:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: mob, Template: Normal.dotm, Last Saved By: mob, Revision Number: 3, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Mon Apr 15 15:36:00 2024, Last Saved Time/Date: Mon Apr 15 15:37:00 2024, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | EC7E26A81B6002C53854A1769AD427A6 |
| SHA1: | D43501510CA909818EAC2684A53C9BE609075BAC |
| SHA256: | 57BD8E8606DC579EB8190DC8882C2892EF05636F28BAD0178E04C9BCBDAC5995 |
| SSDEEP: | 49152:XEtkIKEgJAJvpW4XMrCV/L75aWfpmL+n5uS/PudUUHzY:XEtkIKEgCpWnCVz7thlZG |
MALICIOUS
Detects the decoding of a binary file from Base64 (SCRIPT)
- WINWORD.EXE (PID: 3980)
Uses base64 encoding (SCRIPT)
- WINWORD.EXE (PID: 3980)
Accesses environment variables (SCRIPT)
- WINWORD.EXE (PID: 3980)
Gets TEMP folder path (SCRIPT)
- WINWORD.EXE (PID: 3980)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3980)
Unusual execution from MS Office
- WINWORD.EXE (PID: 3980)
SUSPICIOUS
Script creates XML DOM node (SCRIPT)
- WINWORD.EXE (PID: 3980)
Creates XML DOM element (SCRIPT)
- WINWORD.EXE (PID: 3980)
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 3980)
Saves data to a binary file (SCRIPT)
- WINWORD.EXE (PID: 3980)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- WINWORD.EXE (PID: 3980)
Starts application with an unusual extension
- WINWORD.EXE (PID: 3980)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 3980)
Reads settings of System Certificates
- app.com (PID: 1024)
Sets XML DOM element text (SCRIPT)
- WINWORD.EXE (PID: 3980)
Checks for external IP
- app.com (PID: 1024)
Connects to the server without a host name
- app.com (PID: 1024)
INFO
Checks transactions between databases Windows and Oracle
- WINWORD.EXE (PID: 3980)
Drops the executable file immediately after the start
- WINWORD.EXE (PID: 3980)
Reads the computer name
- app.com (PID: 1024)
- wmpnscfg.exe (PID: 2028)
Checks supported languages
- app.com (PID: 1024)
- wmpnscfg.exe (PID: 2028)
Reads the software policy settings
- app.com (PID: 1024)
Reads the machine GUID from the registry
- app.com (PID: 1024)
Manual execution by a user
- wmpnscfg.exe (PID: 2028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | mob |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | mob |
| Software: | Microsoft Office Word |
| CreateDate: | 2024:04:15 15:36:00 |
| ModifyDate: | 2024:04:15 15:37:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 1 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 3 |
| TotalEditTime: | 1 minute |
| Words: | - |
| Characters: | 1 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
36
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1024 | "C:\Users\admin\AppData\Local\Temp\app.com" | C:\Users\admin\AppData\Local\Temp\app.com | WINWORD.EXE | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: MEDIUM Description: 360 Patch Up Version: 8, 6, 0, 1022 Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\Incident_Harassment.doc | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
11 222
Read events
10 418
Write events
553
Delete events
251
Modification events
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | )h? |
Value: 29683F008C0F0000010000000000000000000000 | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
6
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3819.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{D6789D44-4AE8-4BD2-A655-B193BBFCBBAD}.tmp | — | |
MD5:— | SHA256:— | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFF3923165B6F78D35.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF06B71594023EA665.TMP | binary | |
MD5:72F5C05B7EA8DD6059BF59F50B22DF33 | SHA256:1DC0C8D7304C177AD0E74D3D2F1002EB773F4B180685A7DF6BBE75CCC24B0164 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF95E53DD13DA2E9A6.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFC7E1D4472B2C6D90.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:D27D307C9620F0F2B78519B6F5CB7294 | SHA256:8A5E3EC0A17A150FA69946625208F77546C15E5247A4A318EE1F7ADA644FFCF5 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{F655A4BC-66EB-4548-BBE7-F3E12EDCEB7F}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:31DA46C4044C30AD57B8274658315AE0 | SHA256:9D82DCAD3DA0871D16E365E6F06AAF7490AB002A7A58DA773CFDCC7B44F95124 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$cident_Harassment.doc | pgc | |
MD5:62991A446B4AEC2BC48D78B6266A16FD | SHA256:95D98757861435BE0D2CB3780D26D8C8814332624A548A64D65514742D28809E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
9
DNS requests
2
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
1024 | app.com | GET | 500 | 209.182.225.10:80 | http://209.182.225.10/download?id=LosAngeles&module=2&filename=None | unknown | — | — | unknown |
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/gateway | unknown | — | — | unknown |
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
1024 | app.com | POST | — | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
1024 | app.com | POST | 200 | 85.239.53.219:80 | http://85.239.53.219/api/0d5c5f0d-1526-e933-42a7-5ec964719e94/tasks | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1024 | app.com | 104.26.12.205:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
1024 | app.com | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
1024 | app.com | 85.239.53.219:80 | — | BlueVPS OU | US | unknown |
1024 | app.com | 209.182.225.10:80 | — | SHOCK-1 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
— | — | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1024 | app.com | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | A Network Trojan was detected | ET MALWARE Win32/SSLoad Registration Activity (POST) |
— | — | A Network Trojan was detected | ET MALWARE Win32/SSLoad Registration Response |
— | — | A Network Trojan was detected | ET MALWARE Win32/SSLoad Tasking Request (POST) |
— | — | A Network Trojan was detected | ET MALWARE Win32/SSLoad Tasking Response |
— | — | A Network Trojan was detected | ET MALWARE Win32/SSLoad Module Request (GET) |
— | — | A Network Trojan was detected | ET MALWARE Win32/SSLoad Tasking Request (POST) |
— | — | A Network Trojan was detected | ET MALWARE Win32/SSLoad Tasking Request (POST) |